Feature Papers in Algorithms for Multidisciplinary Applications
Share This Topical Collection
Editor
 Prof. Dr. Francesc Pozo
Prof. Dr. Francesc Pozo
 Prof. Dr. Francesc Pozo
Prof. Dr. Francesc Pozo
E-Mail
Website
Collection Editor
Department of Mathematics, Escola d’Enginyeria de Barcelona Est (EEBE), Universitat Politècnica de Catalunya (UPC), Campus Diagonal-Besòs (CDB), Eduard Maristany, 16, 08019 Barcelona, Spain
Interests: structural health monitoring; condition monitoring; piezoelectric transducers; PZT; data science; wind turbines
Special Issues, Collections and Topics in MDPI journals
Topical Collection Information
Dear Colleagues,
Algorithms have been widely used in various fields, including computer science, engineering, medicine, biology, and social sciences. With the development of interdisciplinary research, the need for algorithms that can be applied to multiple fields has become more urgent. Therefore, we are pleased to announce a Topical Collection on “Algorithms for Multidisciplinary Applications”.
This Topical Collection aims to gather the latest advances in algorithms that can be applied in different fields. We welcome contributions that propose new algorithms, analyze the performance of existing algorithms, or apply algorithms to solve real-world problems in multidisciplinary fields. Topics of interest include, but are not limited to, the following:
- Machine learning algorithms for multidisciplinary applications;
- Optimization algorithms for interdisciplinary problems;
- Graph algorithms in social sciences and biology;
- Data structures and algorithms for healthcare applications;
- Algorithms for image and signal processing in engineering and physics;
- Algorithms for natural language processing and information retrieval in humanities and social sciences.
Dr. Francesc Pozo
Guest Editor
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 250 words) can be sent to the Editorial Office for assessment.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Algorithms is an international peer-reviewed open access monthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 1800 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.
Keywords
- machine learning
- optimization
- graph algorithms
- data structures
- signal processing
- image processing
- natural language processing
- information retrieval
- healthcare applications
- interdisciplinary research
Published Papers (33 papers)
Open AccessArticle
Algorithm for Describing Neuronal Electric Operation
by
János Végh
Viewed by 462
Abstract
The development of neuroanatomy and neurophysiology has revealed many new details about neurons’ operation over the past few decades, requiring modifications to their theoretical models. The development of computing technology enables us to consider the fine details the new model requires, but it
[...] Read more.
The development of neuroanatomy and neurophysiology has revealed many new details about neurons’ operation over the past few decades, requiring modifications to their theoretical models. The development of computing technology enables us to consider the fine details the new model requires, but it necessitates a different approach. To achieve that goal, the disciplinarity of science must be revisited for living matter, the theoretical model must be updated, and a series of processes instead of states must be considered; furthermore, new mathematics, algorithms, and computing technologies for the new view are also needed. We provide an algorithm implementing the mathematics of the updated theoretical model that considers the neuronal current to consist of charged ions (and so considers thermodynamic effects) and opens the way for explaining the mechanical, optical, etc., consequence phenomena of the electrical operation. We use a new technology in this effort: a tool designed to achieve extreme accuracy in simulating high-speed electronic circuits. The algorithm applies the cross-disciplinary unified electrical/thermodynamic model, along with an unusual programming method, to provide new insights into neuronal operations, describe the processes that take place in living matter, and determine their computing implementation. As has long been suspected, the faithful simulation of biological processes requires accurately mapping biological time to technical computing time. Therefore, the paper focuses on time handling in biology-targeting computations, especially in large-scale tasks. We also touch on the question of simulating the operation of their network, which is contrasted with that of Spiking Neural Networks. The way technical computing works inhibits efforts to achieve the required accuracy in reproducing the temporal behavior of biological operations using conventional computer programs.
Full article
►▼
Show Figures
Open AccessArticle
Addressing Air Pollution Challenges: An Integrated Algorithmic Approach Towards Safeguarding Built Heritage
by
Dimitrios Mitsos and Vassilis Poulopoulos
Viewed by 1204
Abstract
Air pollution poses significant risks to built heritage, yet traditional methods for diagnosing degradation patterns remain largely fragmented, often relying on isolated data streams and/or subjective comparative interpretations. This study proposes a novel modular workflow that integrates Raman spectroscopy and micro-XRF spectrometry data
[...] Read more.
Air pollution poses significant risks to built heritage, yet traditional methods for diagnosing degradation patterns remain largely fragmented, often relying on isolated data streams and/or subjective comparative interpretations. This study proposes a novel modular workflow that integrates Raman spectroscopy and micro-XRF spectrometry data with user-defined contextual metadata to automate the characterisation of pollution-induced degradation layers on monuments. This method utilises algorithms for peak detection, dimensionality reduction, unsupervised machine learning clustering, variance analysis across centroids, and correlation analysis, as well as steps for data re-encoding and visualisation of the results, allowing for scalable and reproducible analyses on heterogeneous multidimensional datasets. Applied to case studies from Athens, Piraeus, and Eleusis, Greece, the workflow successfully identified pollution sources and degradation patterns, while also quantifying the contribution of features, including contextual variables such as surface orientation and sampling height. The results validate the method’s capacity to combine molecular and elemental data streams, to enhance interpretive clarity, and to minimise manual effort and subjectivity. This work showcases the potential of algorithmic approaches in cultural heritage diagnostics to adapt dynamically and incorporate additional datasets and informs future applications of automated methods in the broader field of heritage science.
Full article
►▼
Show Figures
Open AccessArticle
Algorithm for Determining the Strong Fuzzy Grade of a Hypergroup
by
Yuming Feng and Violeta Leoreanu-Fotea
Cited by 1 | Viewed by 802
Abstract
In this paper, we present an algorithm for determining the strong fuzzy grade of a hypergroup, considering a particular class of hypergroups associated with genetics. A study is carried out depending on the cardinality of the initial hypergroup. The last paragraph of this
[...] Read more.
In this paper, we present an algorithm for determining the strong fuzzy grade of a hypergroup, considering a particular class of hypergroups associated with genetics. A study is carried out depending on the cardinality of the initial hypergroup. The last paragraph of this paper contains the MATLAB R2018b program for the fuzzy grade for cardinals
.
Full article
►▼
Show Figures
Open AccessArticle
Fuzzy Frankot–Chellappa Algorithm for Surface Normal Integration
by
Saeide Hajighasemi and Michael Breuß
Viewed by 1457
Abstract
In this paper, we propose a fuzzy formulation of the classic Frankot–Chellappa algorithm by which surfaces can be reconstructed using normal vectors. In the fuzzy formulation, the surface normal vectors may be uncertain or ambiguous, yielding a fuzzy Poisson partial differential equation that
[...] Read more.
In this paper, we propose a fuzzy formulation of the classic Frankot–Chellappa algorithm by which surfaces can be reconstructed using normal vectors. In the fuzzy formulation, the surface normal vectors may be uncertain or ambiguous, yielding a fuzzy Poisson partial differential equation that requires appropriate definitions of fuzzy derivatives. The solution of the resulting fuzzy model is approached by adopting a fuzzy variant of the discrete sine transform, which results in a fast and robust algorithm for surface reconstruction. An adaptive defuzzification strategy is also introduced to improve noise handling in highly uncertain regions. In experiments, we demonstrate that our fuzzy Frankot–Chellappa algorithm achieves accuracy on par with the classic approach for smooth surfaces and offers improved robustness in the presence of noisy normal data. We also show that it can naturally handle missing data (such as gaps) in the normal field by filling them using neighboring information.
Full article
►▼
Show Figures
Open AccessArticle
Generating Realistic Synthetic Patient Cohorts: Enforcing Statistical Distributions, Correlations, and Logical Constraints
by
Ahmad Nader Fasseeh, Rasha Ashmawy, Rok Hren, Kareem ElFass, Attila Imre, Bertalan Németh, Dávid Nagy, Balázs Nagy and Zoltán Vokó
Viewed by 1553
Abstract
Large, high-quality patient datasets are essential for applications like economic modeling and patient simulation. However, real-world data is often inaccessible or incomplete. Synthetic patient data offers an alternative, and current methods often fail to preserve clinical plausibility, real-world correlations, and logical consistency. This
[...] Read more.
Large, high-quality patient datasets are essential for applications like economic modeling and patient simulation. However, real-world data is often inaccessible or incomplete. Synthetic patient data offers an alternative, and current methods often fail to preserve clinical plausibility, real-world correlations, and logical consistency. This study presents a patient cohort generator designed to produce realistic, statistically valid synthetic datasets. The generator uses predefined probability distributions and Cholesky decomposition to reflect real-world correlations. A dependency matrix handles variable relationships in the right order. Hard limits block unrealistic values, and binary variables are set using percentiles to match expected rates. Validation used two datasets, NHANES (2021–2023) and the Framingham Heart Study, evaluating cohort diversity (general, cardiac, low-dimensional), data sparsity (five correlation scenarios), and model performance (MSE, RMSE, R
2, SSE, correlation plots). Results demonstrated strong alignment with real-world data in central tendency, dispersion, and correlation structures. Scenario A (empirical correlations) performed best (R
2 = 86.8–99.6%, lowest SSE and MAE). Scenario B (physician-estimated correlations) also performed well, especially in a low-dimensions population (R
2 = 80.7%). Scenario E (no correlation) performed worst. Overall, the proposed model provides a scalable, customizable solution for generating synthetic patient cohorts, supporting reliable simulations and research when real-world data is limited. While deep learning approaches have been proposed for this task, they require access to large-scale real datasets and offer limited control over statistical dependencies or clinical logic. Our approach addresses this gap.
Full article
►▼
Show Figures
Open AccessArticle
A Box-Bounded Non-Linear Least Square Minimization Algorithm with Application to the JWL Parameter Determination in the Isentropic Expansion for Highly Energetic Material Simulation
by
Yuri Caridi, Andrea Cucuzzella, Fabio Vicini and Stefano Berrone
Viewed by 1109
Abstract
This work presents a robust box-constrained nonlinear least-squares algorithm for accurately fitting the Jones–Wilkins–Lee (JWL) equation of state parameters, which describes the isentropic expansion of detonation products from high-energy materials. In the energetic material literature, there are plenty of methods that address this
[...] Read more.
This work presents a robust box-constrained nonlinear least-squares algorithm for accurately fitting the Jones–Wilkins–Lee (JWL) equation of state parameters, which describes the isentropic expansion of detonation products from high-energy materials. In the energetic material literature, there are plenty of methods that address this problem, and in some cases, it is not fully clear which method is employed. We provide a fully detailed numerical framework that explicitly enforces Chapman–Jouguet (CJ) constraints and systematically separates the contributions of different terms in the JWL expression. The algorithm leverages a trust-region Gauss–Newton method combined with singular value decomposition to ensure numerical stability and rapid convergence, even in highly overdetermined systems. The methodology is validated through comprehensive comparisons with leading thermochemical codes such as CHEETAH 2.0, ZMWNI, and EXPLO5. The results demonstrate that the proposed approach yields lower residual fitting errors and improved consistency with CJ thermodynamic conditions compared to standard fitting routines. By providing a reproducible and theoretically based methodology, this study advances the state of the art in JWL parameter determination and improves the reliability of energetic material simulations.
Full article
►▼
Show Figures
Open AccessArticle
Effective Detection of Malicious Uniform Resource Locator (URLs) Using Deep-Learning Techniques
by
Yirga Yayeh Munaye, Aneas Bekele Workneh, Yenework Belayneh Chekol and Atinkut Molla Mekonen
Cited by 1 | Viewed by 2486
Abstract
The rapid growth of internet usage in daily life has led to a significant increase in cyber threats, with malicious URLs serving as a common cybercrime. Traditional detection methods often suffer from high false alarm rates and struggle to keep pace with evolving
[...] Read more.
The rapid growth of internet usage in daily life has led to a significant increase in cyber threats, with malicious URLs serving as a common cybercrime. Traditional detection methods often suffer from high false alarm rates and struggle to keep pace with evolving threats due to outdated feature extraction techniques and datasets. To address these limitations, we propose a deep learning-based approach aimed at developing an effective model for detecting malicious URLs. Our proposed method, the Char2B model, leverages a fusion of BERT and CharBiGRU embedding, further enhanced by a Conv1D layer with a kernel size of three and unit-sized stride and padding. After combining the embedding, we used the BERT model as a baseline for comparison. The study involved collecting a dataset of 87,216 URLs, comprising both benign and malicious samples sourced from the open project directory (DMOZ), PhishTank, and Any.Run. Models were trained using the training set and evaluated on the test set using standard metrics, including accuracy, precision, recall, and F1-score. Through iterative refinement, we optimized the model’s performance to maximize its effectiveness. As a result, our proposed model achieved 98.50% accuracy, 98.27% precision, 98.69% recall, and a 98.48% F1-score, outperforming the baseline BERT model. Additionally, the false positive rate of our model was 0.017 better than the baseline model’s 0.018. By effectively extracting and utilizing informative features, the model accurately classified URLs into benign and malicious categories, thereby improving detection capabilities. This study highlights the significance of our deep learning approach in strengthening cybersecurity by integrating advanced algorithms that enhance detection accuracy, bolster defense mechanisms, and contribute to a safer digital environment.
Full article
►▼
Show Figures
Open AccessArticle
Learning Analytics in a Non-Linear Virtual Course
by
Jhon Mercado, Carlos Mendoza-Cardenas, Luis Fletscher and Natalia Gaviria-Gomez
Viewed by 1278
Abstract
Researchers have extensively explored learning analytics in online courses, primarily focusing on linear course structures where students progress sequentially through lessons and assessments. However, non-linear courses, which allow students to complete tasks in any order, present unique challenges for learning analytics due to
[...] Read more.
Researchers have extensively explored learning analytics in online courses, primarily focusing on linear course structures where students progress sequentially through lessons and assessments. However, non-linear courses, which allow students to complete tasks in any order, present unique challenges for learning analytics due to the variability in course progression among students. This study proposes a method for applying learning analytics to non-linear, self-paced MOOC-style courses, addressing early performance prediction and online learning pattern detection. The novelty of our approach lies in introducing a personalized feature aggregation that adapts to each student’s progress rather than being defined at fixed timelines. We evaluated three types of features—engagement, behavior, and performance—using data from a non-linear large-scale Moodle course designed to prepare high school students for a public university entrance exam. Our approach predicted early student performance, achieving an F1-score of 0.73 at a 20% cumulative weight assessment. Feature importance analysis revealed that performance and behavior were the strongest predictors, while engagement features, such as time spent on educational resources, also played a significant role. In addition to performance prediction, we conducted a clustering analysis that identified four distinct online learning patterns recurring across various cumulative weight assessments. These patterns provide valuable insights into student behavior and performance and have practical implications, enabling educators to deliver more personalized feedback and targeted interventions to meet individual student needs.
Full article
►▼
Show Figures
Open AccessSystematic Review
Advancements in Non-Destructive Detection of Biochemical Traits in Plants Through Spectral Imaging-Based Algorithms: A Systematic Review
by
Aleksander Dabek, Lorenzo Mantovani, Susanna Mirabella, Michele Vignati and Simone Cinquemani
Cited by 1 | Viewed by 1489
Abstract
This paper provides a comprehensive overview of the state of the art non-destructive methods for detecting plant biochemical traits through spectral imaging of leafy greens. It offers insights into the various detection techniques and their effectiveness. The review emphasizes the algorithms used for
[...] Read more.
This paper provides a comprehensive overview of the state of the art non-destructive methods for detecting plant biochemical traits through spectral imaging of leafy greens. It offers insights into the various detection techniques and their effectiveness. The review emphasizes the algorithms used for spectral data analysis, highlighting advancements in computational methods that have contributed to improving detection accuracy and efficiency. This systematic review, following the PRISMA 2020 guidelines, explores the applications of non-destructive measurements, techniques, and algorithms, including hyperspectral imaging and spectrometry for detecting a wide range of chemical compounds and elements in lettuce, basil, and spinach. This review focuses on studies published from 2019 onward, focusing on the detection of compounds such as chlorophyll, carotenoids, nitrogen, nitrate, and anthocyanin. Additional compounds such as phosphorus, vitamin C, magnesium, glucose, sugar, water content, calcium, soluble solid content, sulfur, and pH are also mentioned, although they were not the primary focus of this study. The techniques used are showcased and highlighted for each compound, and the accuracies achieved are presented to demonstrate effective detection.
Full article
►▼
Show Figures
Open AccessReview
Unmanned Aerial Vehicles (UAV) Networking Algorithms: Communication, Control, and AI-Based Approaches
by
Mien L. Trinh, Dung T. Nguyen, Long Q. Dinh, Mui D. Nguyen, De Rosal Ignatius Moses Setiadi and Minh T. Nguyen
Cited by 7 | Viewed by 5879
Abstract
This paper focuses on algorithms and technologies for unmanned aerial vehicles (UAVs) networking across different fields of applications. Given the limitations of UAVs in both computations and communications, UAVs usually need algorithms for either low latency or energy efficiency. In addition, coverage problems
[...] Read more.
This paper focuses on algorithms and technologies for unmanned aerial vehicles (UAVs) networking across different fields of applications. Given the limitations of UAVs in both computations and communications, UAVs usually need algorithms for either low latency or energy efficiency. In addition, coverage problems should be considered to improve UAV deployment in many monitoring or sensing applications. Hence, this work firstly addresses common applications of UAV groups or swarms. Communication routing protocols are then reviewed, as they can make UAVs capable of supporting these applications. Furthermore, control algorithms are examined to ensure UAVs operate in optimal positions for specific purposes. AI-based approaches are considered to enhance UAV performance. We provide either the latest work or evaluations of existing results that can suggest suitable solutions for specific practical applications. This work can be considered as a comprehensive survey for both general and specific problems associated with UAVs in monitoring and sensing fields.
Full article
►▼
Show Figures
Open AccessArticle
User Armor: An Extension for AppArmor
by
Mario Alviano and Pierpaolo Sestito
Viewed by 2236
Abstract
AppArmor is a mandatory access control (MAC) system for Linux based on profiles. It focuses on protecting processes, without differentiating profiles based on the users running the processes themselves. Moreover, it does not implement inheritance mechanisms to simplify the management of profiles and
[...] Read more.
AppArmor is a mandatory access control (MAC) system for Linux based on profiles. It focuses on protecting processes, without differentiating profiles based on the users running the processes themselves. Moreover, it does not implement inheritance mechanisms to simplify the management of profiles and avoid the duplication of rules. This work introduces UserArmor, an extension of AppArmor that overcomes the aforementioned limitations by allowing specific profiles to be associated with users and implementing an inheritance system to reduce complexity, improve reusability, and ensure consistency in security rules. An application to Answer Set Programming is discussed.
Full article
►▼
Show Figures
Open AccessArticle
A Continuous Monitoring and Reallocation Method for Successful Decisions in Change Management
by
Fotios Panagiotopoulos and Vassilios Chatzis
Cited by 1 | Viewed by 1068
Abstract
Businesses and organizations often struggle to cope in a rapidly changing and competitive environment, requiring changes with increasing frequency and complexity. The evolution of information systems has enabled direct access to information and data, which can be utilized for the effective implementation of
[...] Read more.
Businesses and organizations often struggle to cope in a rapidly changing and competitive environment, requiring changes with increasing frequency and complexity. The evolution of information systems has enabled direct access to information and data, which can be utilized for the effective implementation of changes. This usually requires managing resistance to change, which is often presented by employees. The aim of this study is to address the problem of change management in order to limit the decline in overall performance during the critical period of change and to accelerate the implementation of change. This study provides a new innovative approach to managing employee resistance during the change process based on a continuous monitoring and reallocation algorithm. The proposed method introduces the idea of solving the human resource allocation problem by continuously readjusting staff allocation during the change process. The Hungarian algorithm is used to optimize assignments. In this way, the resistance of each employee is taken into account regularly, and the assignment can be altered in the early stages of change. The new method is mathematically formulated and described in detail through an algorithm, which is then used in experiments. The proposed method of frequently reallocating human resources to tasks leads to better overall performance and improves decision making during change processes. The experimental results show that the new approach significantly increases the total performance by up to 124% when compared to existing change management approaches and reduces the time required to achieve the desired state by up to 20%. Thus, the enhanced management of human resistance to change provides distinct advantages over traditional methods by ensuring more dynamic, timely, and adaptive resource allocation during the change period, ultimately leading to successful decision making and sustainable change management.
Full article
►▼
Show Figures
Open AccessArticle
IMM Filtering Algorithms for a Highly Maneuvering Fighter Aircraft: An Overview
by
M. N. Radhika, Mahendra Mallick and Xiaoqing Tian
Cited by 11 | Viewed by 2894
Abstract
The trajectory estimation of a highly maneuvering target is a challenging problem and has practical applications. The interacting multiple model (IMM) filter is a well-established filtering algorithm for the trajectory estimation of maneuvering targets. In this study, we present an overview of IMM
[...] Read more.
The trajectory estimation of a highly maneuvering target is a challenging problem and has practical applications. The interacting multiple model (IMM) filter is a well-established filtering algorithm for the trajectory estimation of maneuvering targets. In this study, we present an overview of IMM filtering algorithms for tracking a highly-maneuverable fighter aircraft using an air moving target indicator (AMTI) radar on another aircraft. This problem is a nonlinear filtering problem due to nonlinearities in the dynamic and measurement models. We first describe single-model nonlinear filtering algorithms: the extended Kalman filter (EKF), unscented Kalman filter (UKF), and cubature Kalman filter (CKF). Then, we summarize the IMM-based EKF (IMM-EKF), IMM-based UKF (IMM-UKF), and IMM-based CKF (CKF). In order to compare the state estimation accuracies of the IMM-based filters, we present a derivation of the posterior Cramér-Rao lower bound (PCRLB). We consider fighter aircraft traveling with accelerations 3
g, 4
g, 5
g, and 6
g and present numerical results for state estimation accuracy and computational cost under various operating conditions. Our results show that under normal operating conditions, the three IMM-based filters have nearly the same accuracy. This is due to the accuracy of the measurements of the AMTI radar and the high data rate.
Full article
►▼
Show Figures
Open AccessArticle
Algorithms of Cross-Domain Redundancy Management for Resilient of Dual-Priority Critical Communication Systems
by
Igor Kabashkin
Cited by 2 | Viewed by 3342
Abstract
The paper presents models for managing cross-domain redundancy to enhance the reliability of two priority communication channels within critical infrastructure systems. Employing Markov chain models, the paper analyzes the impact of two distinct redundancy management strategies: a unified reserve pool and a separate
[...] Read more.
The paper presents models for managing cross-domain redundancy to enhance the reliability of two priority communication channels within critical infrastructure systems. Employing Markov chain models, the paper analyzes the impact of two distinct redundancy management strategies: a unified reserve pool and a separate pool approach with cross-domain resource sharing. The study introduces reliability improvement factors to quantify system performance, exploring their dependency on the number of additional redundant elements, their inherent reliability, and the chosen strategy for managing cross-domain redundancy. An air traffic control system serves as a case study of the application of the proposed management algorithms. Results indicate that the integration of resources from different priority domains significantly improves communication reliability. The findings may be useful for the design and operation of secure communication networks.
Full article
►▼
Show Figures
Open AccessArticle
Joint Optimization of Service Migration and Resource Allocation in Mobile Edge–Cloud Computing
by
Zhenli He, Liheng Li, Ziqi Lin, Yunyun Dong, Jianglong Qin and Keqin Li
Cited by 2 | Viewed by 2783
Abstract
In the rapidly evolving domain of mobile edge–cloud computing (MECC), the proliferation of Internet of Things (IoT) devices and mobile applications poses significant challenges, particularly in dynamically managing computational demands and user mobility. Current research has partially addressed aspects of service migration and
[...] Read more.
In the rapidly evolving domain of mobile edge–cloud computing (MECC), the proliferation of Internet of Things (IoT) devices and mobile applications poses significant challenges, particularly in dynamically managing computational demands and user mobility. Current research has partially addressed aspects of service migration and resource allocation, yet it often falls short in thoroughly examining the nuanced interdependencies between migration strategies and resource allocation, the consequential impacts of migration delays, and the intricacies of handling incomplete tasks during migration. This study advances the discourse by introducing a sophisticated framework optimized through a deep reinforcement learning (DRL) strategy, underpinned by a Markov decision process (MDP) that dynamically adapts service migration and resource allocation strategies. This refined approach facilitates continuous system monitoring, adept decision making, and iterative policy refinement, significantly enhancing operational efficiency and reducing response times in MECC environments. By meticulously addressing these previously overlooked complexities, our research not only fills critical gaps in the literature but also enhances the practical deployment of edge computing technologies, contributing profoundly to both theoretical insights and practical implementations in contemporary digital ecosystems.
Full article
►▼
Show Figures
Open AccessArticle
The Weighted Least-Squares Approach to State Estimation in Linear State Space Models: The Case of Correlated Noise Terms
by
Andreas Galka
Cited by 1 | Viewed by 1900
Abstract
In this article, a particular approach to deriving recursive state estimators for linear state space models is generalised, namely the weighted least-squares approach introduced by Duncan and Horn in 1972, for the case of the two noise processes arising in such models being
[...] Read more.
In this article, a particular approach to deriving recursive state estimators for linear state space models is generalised, namely the weighted least-squares approach introduced by Duncan and Horn in 1972, for the case of the two noise processes arising in such models being cross-correlated; in this context, the fact that in the available literature two different non-equivalent recursive algorithms are presented for the task of state estimation in the aforementioned case is discussed. Although the origin of the difference between these two algorithms can easily be identified, the issue has only rarely been discussed so far. Then the situations in which each of the two algorithms apply are explored, and a generalised Kalman filter which represents a merger of the two original algorithms is proposed. While, strictly speaking, optimal state estimates can be obtained only through the non-recursive weighted least-squares approach, in examples of modelling simulated and real-world data, the recursive generalised Kalman filter shows almost as good performance as the optimal non-recursive filter.
Full article
►▼
Show Figures
Open AccessArticle
Resource Allocation of Cooperative Alternatives Using the Analytic Hierarchy Process and Analytic Network Process with Shapley Values
by
Jih-Jeng Huang and Chin-Yi Chen
Cited by 5 | Viewed by 2761
Abstract
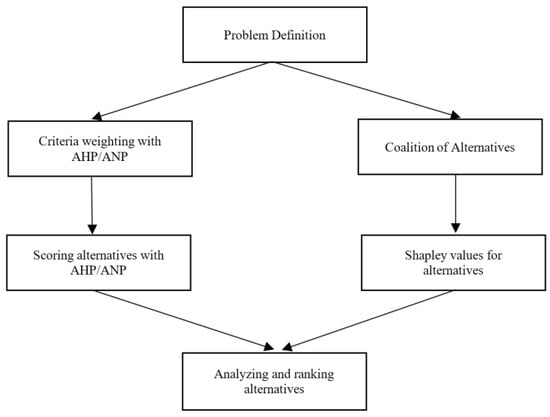
Cooperative alternatives need complex multi-criteria decision-making (MCDM) consideration, especially in resource allocation, where the alternatives exhibit interdependent relationships. Traditional MCDM methods like the Analytic Hierarchy Process (AHP) and Analytic Network Process (ANP) often overlook the synergistic potential of cooperative alternatives. This study introduces
[...] Read more.
Cooperative alternatives need complex multi-criteria decision-making (MCDM) consideration, especially in resource allocation, where the alternatives exhibit interdependent relationships. Traditional MCDM methods like the Analytic Hierarchy Process (AHP) and Analytic Network Process (ANP) often overlook the synergistic potential of cooperative alternatives. This study introduces a novel method integrating AHP/ANP with Shapley values, specifically designed to address this gap by evaluating alternatives on individual merits and their contributions within coalitions. Our methodology begins with defining problem structures and applying AHP/ANP to determine the criteria weights and alternatives’ scores. Subsequently, we compute Shapley values based on coalition values, synthesizing these findings to inform resource allocation decisions more equitably. A numerical example of budget allocation illustrates the method’s efficacy, revealing significant insights into resource distribution when cooperative dynamics are considered. Our results demonstrate the proposed method’s superiority in capturing the nuanced interplay between criteria and alternatives, leading to more informed urban planning decisions. This approach marks a significant advancement in MCDM, offering a comprehensive framework that incorporates both the analytical rigor of AHP/ANP and the equitable considerations of cooperative game theory through Shapley values.
Full article
►▼
Show Figures
Open AccessArticle
Theoretical and Empirical Analysis of a Fast Algorithm for Extracting Polygons from Signed Distance Bounds
by
Nenad Markuš and Mirko Sužnjević
Viewed by 1777
Abstract
Recently, there has been renewed interest in signed distance bound representations due to their unique properties for 3D shape modelling. This is especially the case for deep learning-based bounds. However, it is beneficial to work with polygons in most computer graphics applications. Thus,
[...] Read more.
Recently, there has been renewed interest in signed distance bound representations due to their unique properties for 3D shape modelling. This is especially the case for deep learning-based bounds. However, it is beneficial to work with polygons in most computer graphics applications. Thus, in this paper, we introduce and investigate an asymptotically fast method for transforming signed distance bounds into polygon meshes. This is achieved by combining the principles of sphere tracing (or ray marching) with traditional polygonization techniques, such as marching cubes. We provide theoretical and experimental evidence that this approach is of the
computational complexity for a polygonization grid with
cells. The algorithm is tested on both a set of primitive shapes and signed distance bounds generated from point clouds by machine learning (and represented as neural networks). Given its speed, implementation simplicity, and portability, we argue that it could prove useful during the modelling stage as well as in shape compression for storage.
Full article
►▼
Show Figures
Open AccessArticle
A Computational Platform for Automatic Signal Processing for Bender Element Sensors
by
Ionuţ Dragoş Moldovan, Abdalla Almukashfi and António Gomes Correia
Cited by 3 | Viewed by 2350
Abstract
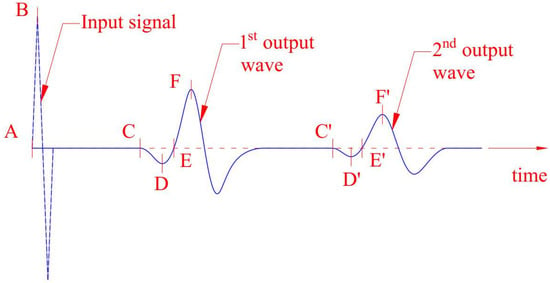
The small strain shear modulus is an important characteristic of geomaterials that can be measured experimentally using piezoelectric sensors (bender elements). However, most conventional signal interpretation techniques are based on the visual observation of the output signal and therefore inherently subjective. Objective techniques
[...] Read more.
The small strain shear modulus is an important characteristic of geomaterials that can be measured experimentally using piezoelectric sensors (bender elements). However, most conventional signal interpretation techniques are based on the visual observation of the output signal and therefore inherently subjective. Objective techniques also exist, like the cross-correlation of the input and output signals, but they lack physical insight, as they rely on the (incorrect) assumption that input and output signals are similar. This paper presents GeoHyTE, the first objective and physically consistent toolbox for the automatic processing of the output signal of bender element sensors. GeoHyTE updates a finite element model of the experiment, iteratively searching for the small strain shear modulus that maximises the correlation between the experimental and numerical output signals. The method is objective, as the results do not depend on the experience of the user, and physically consistent, as the wave propagation process is modelled in full and signals of the same nature (output) are correlated. Moreover, GeoHyTE is nearly insensitive to grossly erroneous input by the user, both in terms of the starting point of the iterative maximisation process and refinement of the finite element model. The results obtained with GeoHyTE are validated against benchmark measurements reported in the literature and experimental data obtained by the authors. A detailed statistical analysis of the results obtained with GeoHyTE and conventional interpretation techniques is also presented.
Full article
►▼
Show Figures
Open AccessArticle
Personalized Advertising in E-Commerce: Using Clickstream Data to Target High-Value Customers
by
Virgilijus Sakalauskas and Dalia Kriksciuniene
Cited by 11 | Viewed by 11428
Abstract
The growing popularity of e-commerce has prompted researchers to take a greater interest in deeper understanding online shopping behavior, consumer interest patterns, and the effectiveness of advertising campaigns. This paper presents a fresh approach for targeting high-value e-shop clients by utilizing clickstream data.
[...] Read more.
The growing popularity of e-commerce has prompted researchers to take a greater interest in deeper understanding online shopping behavior, consumer interest patterns, and the effectiveness of advertising campaigns. This paper presents a fresh approach for targeting high-value e-shop clients by utilizing clickstream data. We propose the new algorithm to measure customer engagement and recognizing high-value customers. Clickstream data is employed in the algorithm to compute a Customer Merit (CM) index that measures the customer’s level of engagement and anticipates their purchase intent. The CM index is evaluated dynamically by the algorithm, examining the customer’s activity level, efficiency in selecting items, and time spent in browsing. It combines tracking customers browsing and purchasing behaviors with other relevant factors: time spent on the website and frequency of visits to e-shops. This strategy proves highly beneficial for e-commerce enterprises, enabling them to pinpoint potential buyers and design targeted advertising campaigns exclusively for high-value customers of e-shops. It allows not only boosts e-shop sales but also minimizes advertising expenses effectively. The proposed method was tested on actual clickstream data from two e-commerce websites and showed that the personalized advertising campaign outperformed the non-personalized campaign in terms of click-through and conversion rate. In general, the findings suggest, that personalized advertising scenarios can be a useful tool for boosting e-commerce sales and reduce advertising cost. By utilizing clickstream data and adopting a targeted approach, e-commerce businesses can attract and retain high-value customers, leading to higher revenue and profitability.
Full article
►▼
Show Figures
Open AccessArticle
Search on an NK Landscape with Swarm Intelligence: Limitations and Future Research Opportunities
by
Ren-Raw Chen, Cameron D. Miller and Puay Khoon Toh
Cited by 2 | Viewed by 2762
Abstract
Swarm intelligence has promising applications for firm search and decision-choice problems and is particularly well suited for examining how other firms influence the focal firm’s search. To evaluate search performance, researchers examining firm search through simulation models typically build a performance landscape. The
[...] Read more.
Swarm intelligence has promising applications for firm search and decision-choice problems and is particularly well suited for examining how other firms influence the focal firm’s search. To evaluate search performance, researchers examining firm search through simulation models typically build a performance landscape. The NK model is the leading tool used for this purpose in the management science literature. We assess the usefulness of the NK landscape for simulated swarm search. We find that the strength of the swarm model for examining firm search and decision-choice problems—the ability to model the influence of other firms on the focal firm—is limited to the NK landscape. Researchers will need alternative ways to create a performance landscape in order to use our full swarm model in simulations. We also identify multiple opportunities—endogenous landscapes, agent-specific landscapes, incomplete information, and costly movements—that future researchers can include in landscape development to gain the maximum insights from swarm-based firm search simulations.
Full article
►▼
Show Figures
Open AccessArticle
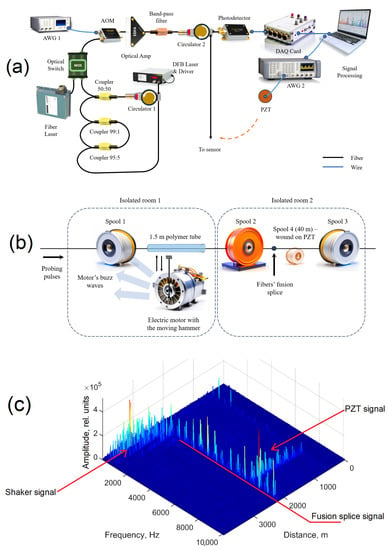
Activation Function Dynamic Averaging as a Technique for Nonlinear 2D Data Denoising in Distributed Acoustic Sensors
by
Artem T. Turov, Fedor L. Barkov, Yuri A. Konstantinov, Dmitry A. Korobko, Cesar A. Lopez-Mercado and Andrei A. Fotiadi
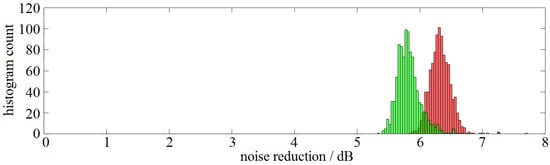
Cited by 21 | Viewed by 3169
Abstract
This work studies the application of low-cost noise reduction algorithms for the data processing of distributed acoustic sensors (DAS). It presents an improvement of the previously described methodology using the activation function of neurons, which enhances the speed of data processing and the
[...] Read more.
This work studies the application of low-cost noise reduction algorithms for the data processing of distributed acoustic sensors (DAS). It presents an improvement of the previously described methodology using the activation function of neurons, which enhances the speed of data processing and the quality of event identification, as well as reducing spatial distortions. The possibility of using a cheaper radiation source in DAS setups is demonstrated. Optimal algorithms’ combinations are proposed for different types of the events recorded. The criterion for evaluating the effectiveness of algorithm performance was an increase in the signal-to-noise ratio (SNR). The finest effect achieved with a combination of algorithms provided an increase in SNR of 10.8 dB. The obtained results can significantly expand the application scope of DAS.
Full article
►▼
Show Figures
Open AccessArticle
From Data to Human-Readable Requirements: Advancing Requirements Elicitation through Language-Transformer-Enhanced Opportunity Mining
by
Pascal Harth, Orlando Jähde, Sophia Schneider, Nils Horn and Rüdiger Buchkremer
Cited by 6 | Viewed by 3107
Abstract
In this research, we present an algorithm that leverages language-transformer technologies to automate the generation of product requirements, utilizing E-Shop consumer reviews as a data source. Our methodology combines classical natural language processing techniques with diverse functions derived from transformer concepts, including keyword
[...] Read more.
In this research, we present an algorithm that leverages language-transformer technologies to automate the generation of product requirements, utilizing E-Shop consumer reviews as a data source. Our methodology combines classical natural language processing techniques with diverse functions derived from transformer concepts, including keyword and summary generation. To effectively capture the most critical requirements, we employ the opportunity matrix as a robust mechanism for identifying and prioritizing urgent needs. Utilizing transformer technologies, mainly through the implementation of summarization and sentiment analysis, we can extract fundamental requirements from consumer assessments. As a practical demonstration, we apply our technology to analyze the ratings of the Amazon echo dot, showcasing our algorithm’s superiority over conventional approaches by extracting human-readable problem descriptions to identify critical user needs. The results of our study exemplify the potential of transformer-enhanced opportunity mining in advancing the requirements-elicitation processes. Our approach streamlines product improvement by extracting human-readable problem descriptions from E-Shop consumer reviews, augmenting operational efficiency, and facilitating decision-making. These findings underscore the transformative impact of incorporating transformer technologies within requirements engineering, paving the way for more effective and scalable algorithms to elicit and address user needs.
Full article
►▼
Show Figures
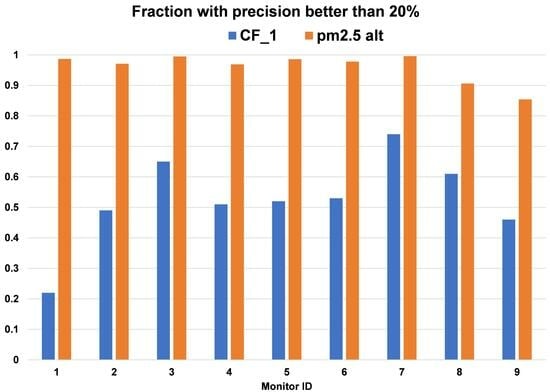
Open AccessArticle
Testing a New “Decrypted” Algorithm for Plantower Sensors Measuring PM2.5: Comparison with an Alternative Algorithm
by
Lance Wallace
Cited by 7 | Viewed by 3001
Abstract
Recently, a hypothesis providing a detailed equation for the Plantower CF_1 algorithm for PM
2.5 has been published. The hypothesis was originally validated using eight independent Plantower sensors in four PurpleAir PA-II monitors providing PM
2.5 estimates from a single site in 2020.
[...] Read more.
Recently, a hypothesis providing a detailed equation for the Plantower CF_1 algorithm for PM
2.5 has been published. The hypothesis was originally validated using eight independent Plantower sensors in four PurpleAir PA-II monitors providing PM
2.5 estimates from a single site in 2020. If true, the hypothesis makes important predictions regarding PM
2.5 measurements using CF_1. Therefore, we test the hypothesis using 18 Plantower sensors from four datasets from two sites in later years (2021–2023). The four general models from these datasets agreed to within 10% with the original model. A competing algorithm known as “pm2.5 alt” has been published and is freely available on the PurpleAir API site. The accuracy, precision, and limit of detection for the two algorithms are compared. The CF_1 algorithm overestimates PM
2.5 by about 60–70% compared to two calibrated PurpleAir monitors using the pm2.5 alt algorithm. A requirement that the two sensors in a single monitor agree to within 20% was met by 85–99% of the data using the pm2.5 alt algorithm, but by only 22–74% of the data using the CF_1 algorithm. The limit of detection (LOD) of the CF_1 algorithm was about 10 times the LOD of the pm2.5 alt algorithm, resulting in 71% of the CF_1 data falling below the LOD, compared to 1 % for the pm2.5 alt algorithm.
Full article
►▼
Show Figures
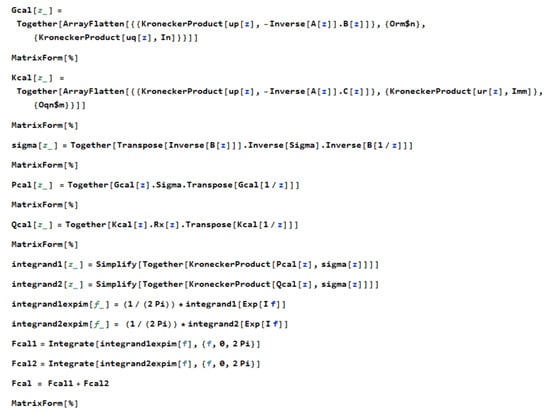
Open AccessArticle
An Algorithm for the Fisher Information Matrix of a VARMAX Process
by
André Klein and Guy Mélard
Cited by 3 | Viewed by 1798
Abstract
In this paper, an algorithm for Mathematica is proposed for the computation of the asymptotic Fisher information matrix for a multivariate time series, more precisely for a controlled vector autoregressive moving average stationary process, or VARMAX process. Meanwhile, we present briefly several algorithms
[...] Read more.
In this paper, an algorithm for Mathematica is proposed for the computation of the asymptotic Fisher information matrix for a multivariate time series, more precisely for a controlled vector autoregressive moving average stationary process, or VARMAX process. Meanwhile, we present briefly several algorithms published in the literature and discuss the sufficient condition of invertibility of that matrix based on the eigenvalues of the process operators. The results are illustrated by numerical computations.
Full article
►▼
Show Figures
Open AccessArticle
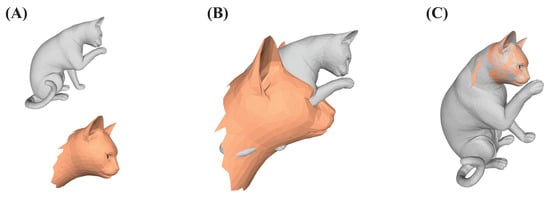
A Physicist’s View on Partial 3D Shape Matching
by
Patrice Koehl and Henri Orland
Cited by 3 | Viewed by 3162
Abstract
A new algorithm is presented to compute nonrigid, possibly partial comparisons of shapes defined by unstructured triangulations of their surfaces. The algorithm takes as input a pair of surfaces with each surface given by a distinct and unrelated triangulation. Its goal is to
[...] Read more.
A new algorithm is presented to compute nonrigid, possibly partial comparisons of shapes defined by unstructured triangulations of their surfaces. The algorithm takes as input a pair of surfaces with each surface given by a distinct and unrelated triangulation. Its goal is to define a possibly partial correspondence between the vertices of the two triangulations, with a cost associated with this correspondence that can serve as a measure of the similarity of the two shapes. To find this correspondence, the vertices in each triangulation are characterized by a signature vector of features. We tested both the LD-SIFT signatures, based on the concept of spin images, and the wave kernel signatures obtained by solving the Shrödinger equation on the triangulation. A cost matrix
C is constructed such that
is the norm of the difference of the signature vectors of vertices
k and
l. The correspondence between the triangulations is then computed as the transport plan that solves the optimal transport or optimal partial transport problem between their sets of vertices. We use a statistical physics approach to solve these problems. The presentation of the proposed algorithm is complemented with examples that illustrate its effectiveness and manageable computing cost.
Full article
►▼
Show Figures
Open AccessArticle
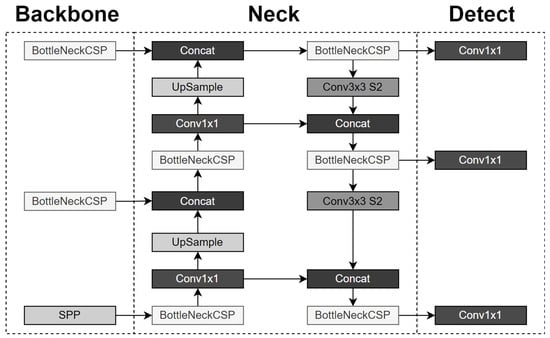
Deep Learning for Detecting Verticillium Fungus in Olive Trees: Using YOLO in UAV Imagery
by
Marios Mamalis, Evangelos Kalampokis, Ilias Kalfas and Konstantinos Tarabanis
Cited by 17 | Viewed by 5029
Abstract
The verticillium fungus has become a widespread threat to olive fields around the world in recent years. The accurate and early detection of the disease at scale could support solving the problem. In this paper, we use the YOLO version 5 model to
[...] Read more.
The verticillium fungus has become a widespread threat to olive fields around the world in recent years. The accurate and early detection of the disease at scale could support solving the problem. In this paper, we use the YOLO version 5 model to detect verticillium fungus in olive trees using aerial RGB imagery captured by unmanned aerial vehicles. The aim of our paper is to compare different architectures of the model and evaluate their performance on this task. The architectures are evaluated at two different input sizes each through the most widely used metrics for object detection and classification tasks (precision, recall, mAP@0.5 and mAP@0.5:0.95). Our results show that the YOLOv5 algorithm is able to deliver good results in detecting olive trees and predicting their status, with the different architectures having different strengths and weaknesses.
Full article
►▼
Show Figures
Open AccessArticle
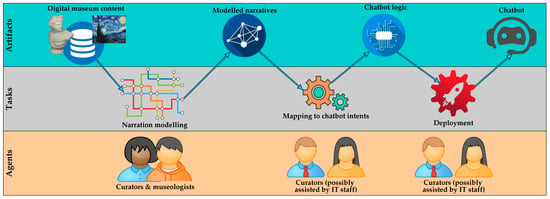
Chatbots for Cultural Venues: A Topic-Based Approach
by
Vasilis Bouras, Dimitris Spiliotopoulos, Dionisis Margaris, Costas Vassilakis, Konstantinos Kotis, Angeliki Antoniou, George Lepouras, Manolis Wallace and Vassilis Poulopoulos
Cited by 7 | Viewed by 4553
Abstract
Digital assistants—such as chatbots—facilitate the interaction between persons and machines and are increasingly used in web pages of enterprises and organizations. This paper presents a methodology for the creation of chatbots that offer access to museum information. The paper introduces an information model
[...] Read more.
Digital assistants—such as chatbots—facilitate the interaction between persons and machines and are increasingly used in web pages of enterprises and organizations. This paper presents a methodology for the creation of chatbots that offer access to museum information. The paper introduces an information model that is offered through the chatbot, which subsequently maps the museum’s modeled information to structures of DialogFlow, Google’s chatbot engine. Means for automating the chatbot generation process are also presented. The evaluation of the methodology is illustrated through the application of a real case, wherein we developed a chatbot for the Archaeological Museum of Tripolis, Greece.
Full article
►▼
Show Figures
Open AccessArticle
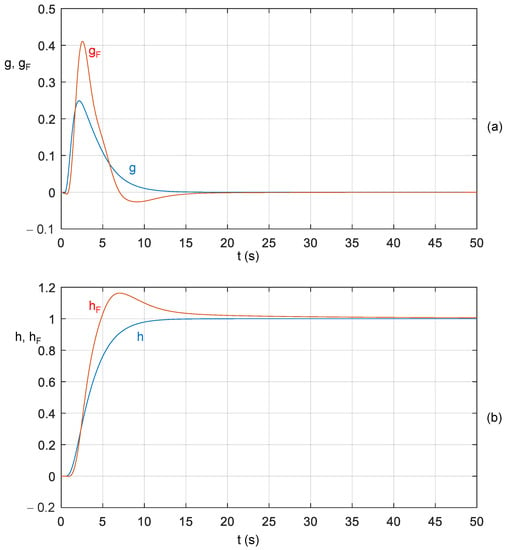
Basis Functions for a Transient Analysis of Linear Commensurate Fractional-Order Systems
by
Dalibor Biolek, Viera Biolková, Zdeněk Kolka and Zdeněk Biolek
Cited by 5 | Viewed by 2255
Abstract
In this paper, the possibilities of expressing the natural response of a linear commensurate fractional-order system (FOS) as a linear combination of basis functions are analyzed. For all possible types of
sα-domain poles, the corresponding basis functions are found, the kernel
[...] Read more.
In this paper, the possibilities of expressing the natural response of a linear commensurate fractional-order system (FOS) as a linear combination of basis functions are analyzed. For all possible types of
sα-domain poles, the corresponding basis functions are found, the kernel of which is the two-parameter Mittag–Leffler function
Eα,β,
β =
α. It is pointed out that there are mutually unambiguous correspondences between the basis functions of FOS and the known basis functions of the integer-order system (IOS) for
α = 1. This correspondence can be used to algorithmically find analytical formulas for the impulse responses of FOS when the formulas for the characteristics of IOS are known. It is shown that all basis functions of FOS can be generated with Podlubny‘s function of type
εk (t,
c;
α,
α), where
c and
k are the corresponding pole and its multiplicity, respectively.
Full article
►▼
Show Figures
Open AccessArticle
Optimized Workflow Framework in Construction Projects to Control the Environmental Properties of Soil
by
Per Lindh and Polina Lemenkova
Cited by 3 | Viewed by 2520
Abstract
To optimize the workflow of civil engineering construction in a harbour, this paper developed a framework of the contaminant leaching assessment carried out on the stabilized/solidified dredged soil material. The specimens included the sampled sediments collected from the in situ fieldwork in Arendal
[...] Read more.
To optimize the workflow of civil engineering construction in a harbour, this paper developed a framework of the contaminant leaching assessment carried out on the stabilized/solidified dredged soil material. The specimens included the sampled sediments collected from the in situ fieldwork in Arendal and Kongshavn. The background levels of the concentration of pollutants were evaluated to assess the cumulative surface leaching of substances from samples over two months. The contamination of soil was assessed using a structured workflow scheme on the following toxic substances, heavy metals—As, Pb, Cd, Cr, Hg, Ni, and Zn; organic compounds—PAH-16 and PCB; and organotin compounds—TBT. The numerical computation and data analysis were applied to the results of geochemical testing creating computerised solutions to soil quality evaluation in civil engineering. Data modelling enabled the estimation of leaching of the contaminants in one year. The estimated leaching of As is 0.9153 mg/m
2, for Ni—2.8178 mg/m
2, for total PAH-16 as 0.0507 mg/m
2, and for TBT—0.00061 mg/m
2 per year. The performance of the sediments was examined with regard to permeability through a series of the controlled experiments. The environmental engineering tests were implemented in the Swedish Geotechnical Institute (SGI) in a triplicate mode over 64 days. The results were compared for several sites and showed that the amount of As is slightly higher in Kongshavn than for Arendal, while the content of Cd, Cr, and Ni is lower. For TBT, the levels are significantly lower than for those at Arendal. The algorithm of permeability tests evaluated the safety of foundation soil for construction of embankments and structures. The optimized assessment methods were applied for monitoring coastal areas through the evaluated permeability of soil and estimated leaching rates of heavy metals, PHB, PACs, and TBT in selected test sites in harbours of southern Norway.
Full article
►▼
Show Figures
Open AccessArticle
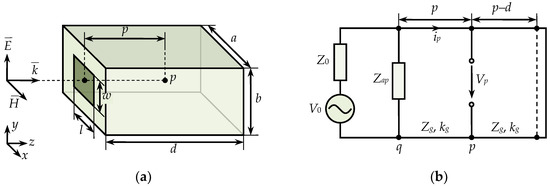
Generalized Algorithm Based on Equivalent Circuits for Evaluating Shielding Effectiveness of Electronic Equipment Enclosures
by
Anton A. Ivanov, Aleksey A. Kvasnikov, Alexander V. Demakov, Maxim E. Komnatnov, Sergei P. Kuksenko and Talgat R. Gazizov
Cited by 2 | Viewed by 2855
Abstract
The article proposes a generalized algorithm for evaluating the shielding effectiveness (SE) of electronic equipment enclosures. The algorithm is based on a number of analytical models that use equivalent circuits to obtain SE values. The article begins with a brief review and interpretation
[...] Read more.
The article proposes a generalized algorithm for evaluating the shielding effectiveness (SE) of electronic equipment enclosures. The algorithm is based on a number of analytical models that use equivalent circuits to obtain SE values. The article begins with a brief review and interpretation of the mathematical formulation used in the algorithm. Then, we describe the proposed algorithm using flowcharts, and we perform its validation. The validation results show that the proposed algorithm has acceptable accuracy and gives SE values comparable to numerical methods or measurements, with much less time costs. The last part of the article presents the software developed to evaluate SE based on analytical models.
Full article
►▼
Show Figures
Open AccessArticle
Random forest Algorithm for the Classification of Spectral Data of Astronomical Objects
by
José-Luis Solorio-Ramírez, Raúl Jiménez-Cruz, Yenny Villuendas-Rey and Cornelio Yáñez-Márquez
Cited by 18 | Viewed by 5669
Abstract
Over time, human beings have built increasingly large astronomical observatories to increase the number of discoveries related to celestial objects. However, the amount of collected elements far exceeds the human capacity to analyze findings without help. For this reason, researchers must now turn
[...] Read more.
Over time, human beings have built increasingly large astronomical observatories to increase the number of discoveries related to celestial objects. However, the amount of collected elements far exceeds the human capacity to analyze findings without help. For this reason, researchers must now turn to machine learning to analyze such data, identifying and classifying transient objects or events within extensive observations of the firmament. Algorithms from the family of random forests (an ensemble of decision trees) have become a powerful tool that can be used to classify astronomical events and objects. This work aims to illustrate the versatility of machine learning algorithms, such as decision trees, to facilitate the identification and classification of celestial bodies by manipulating hyperparameters and studying the attributes of celestial body datasets. By applying a random forest algorithm to a well-known dataset that includes three types of celestial bodies, its effectiveness was compared against some supervised classifiers of the most important approaches (Bayes, nearest neighbors, support vector machines, and neural networks). The results show that random forests are a good alternative for data analysis and classification in astronomical observations.
Full article
►▼
Show Figures
Open AccessArticle
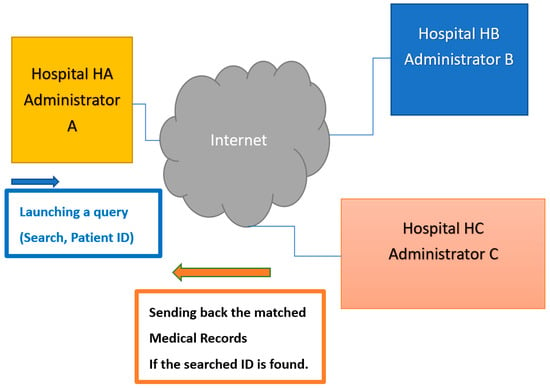
A Privacy-Preserving Symptoms Retrieval System with the Aid of Homomorphic Encryption and Private Set Intersection Schemes
by
Yi-Wei Wang and Ja-Ling Wu
Cited by 5 | Viewed by 2798
Abstract
This work presents an efficient and effective system allowing hospitals to share patients’ private information while ensuring that each hospital database’s medical records will not be leaked; moreover, the privacy of patients who access the data will also be protected. We assume that
[...] Read more.
This work presents an efficient and effective system allowing hospitals to share patients’ private information while ensuring that each hospital database’s medical records will not be leaked; moreover, the privacy of patients who access the data will also be protected. We assume that the thread model of the hospital’s security is semi-honest (i.e., curious but honest), and each hospital hired a trusted medical records department administrator to manage patients’ private information from other hospitals. With the help of Homomorphic Encryption- and Private Set Intersection -related algorithms, our proposed system protects patient privacy, allows physicians to obtain patient information across hospitals, and prevents threats such as troublesome insider attacks and man-in-the-middle attacks.
Full article
►▼
Show Figures