- Article
Data-Driven Reconstruction of the Singapore Stone: A Numerical Imputation Method of Epigraphic Restoration
- Tehreem Zahra,
- Francesco Perono Cacciafoco and
- Muhammad Tayyab Zamir
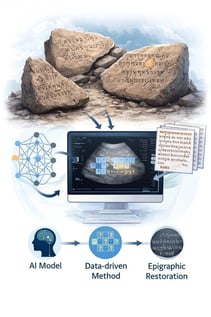
One of the key artefacts of epigraphy in Southeast Asia is the Singapore Stone inscription, which is, unfortunately, in a poor condition. There are huge spaces that separate the readable characters, rendering the text incomplete. This renders a traditional reconstruction and interpretation by philologists extremely challenging. We consider epigraphic restoration as a data-restoration task in this paper. We represent the inscription as a system of categorical symbols, in keeping with the original spatial disposition of characters and spaces. Our model is trained in a conservative, data-driven manner using the observed symbols to learn the local transition statistics, and it takes advantage of this information to make plausible predictions of the most likely characters in missing sequences that are short and well-constrained. The procedure generates a probabilistic hypothesis of restoration, which can be audited, as opposed to one definitive reading. The validation of masked-character recovery demonstrates that the model has a mean top-one error of 53.3%, which represents a significantly worse performance compared with simple baseline methods. The process is focused on interaction and transparency with experts. It relies upon assurance scores and prioritised alternative completions of each proposed reconstruction, as a useful means to produce hypotheses in computational epigraphy and the digital humanities.
7 February 2026