A Bibliographic Analysis of Research Trends on Privacy in Technology Adoption: Information Synthesis Perspective
Abstract
1. Introduction
2. Literature Review
2.1. Privacy in Technology Adoption
2.2. Related Studies on Privacy in Technology Adoption
2.3. Bibliometric Analysis
3. Methodology
3.1. Research Questions
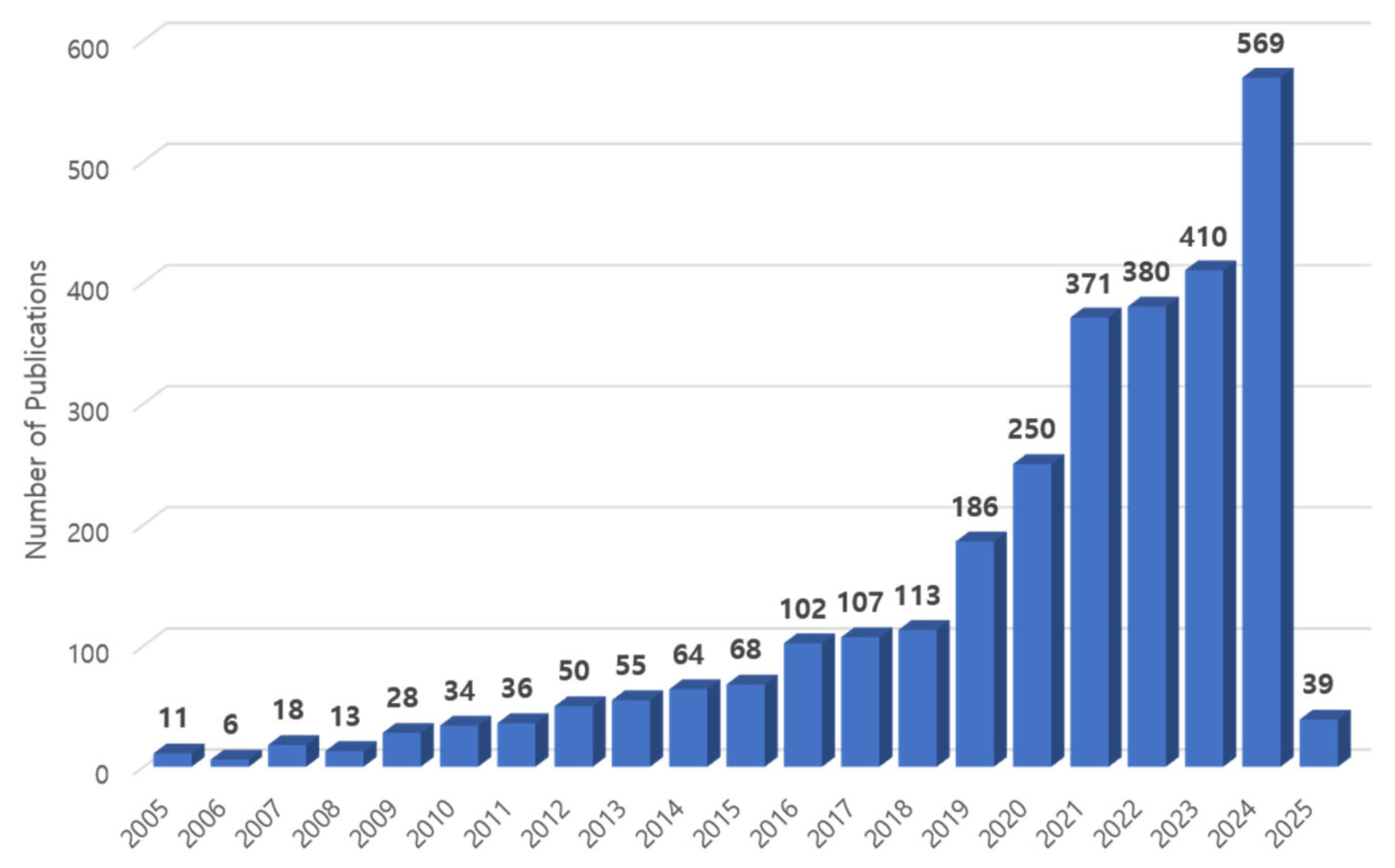
3.2. Data Collection
3.3. Statistical Methods
4. Analysis Results
4.1. Cluster Analysis
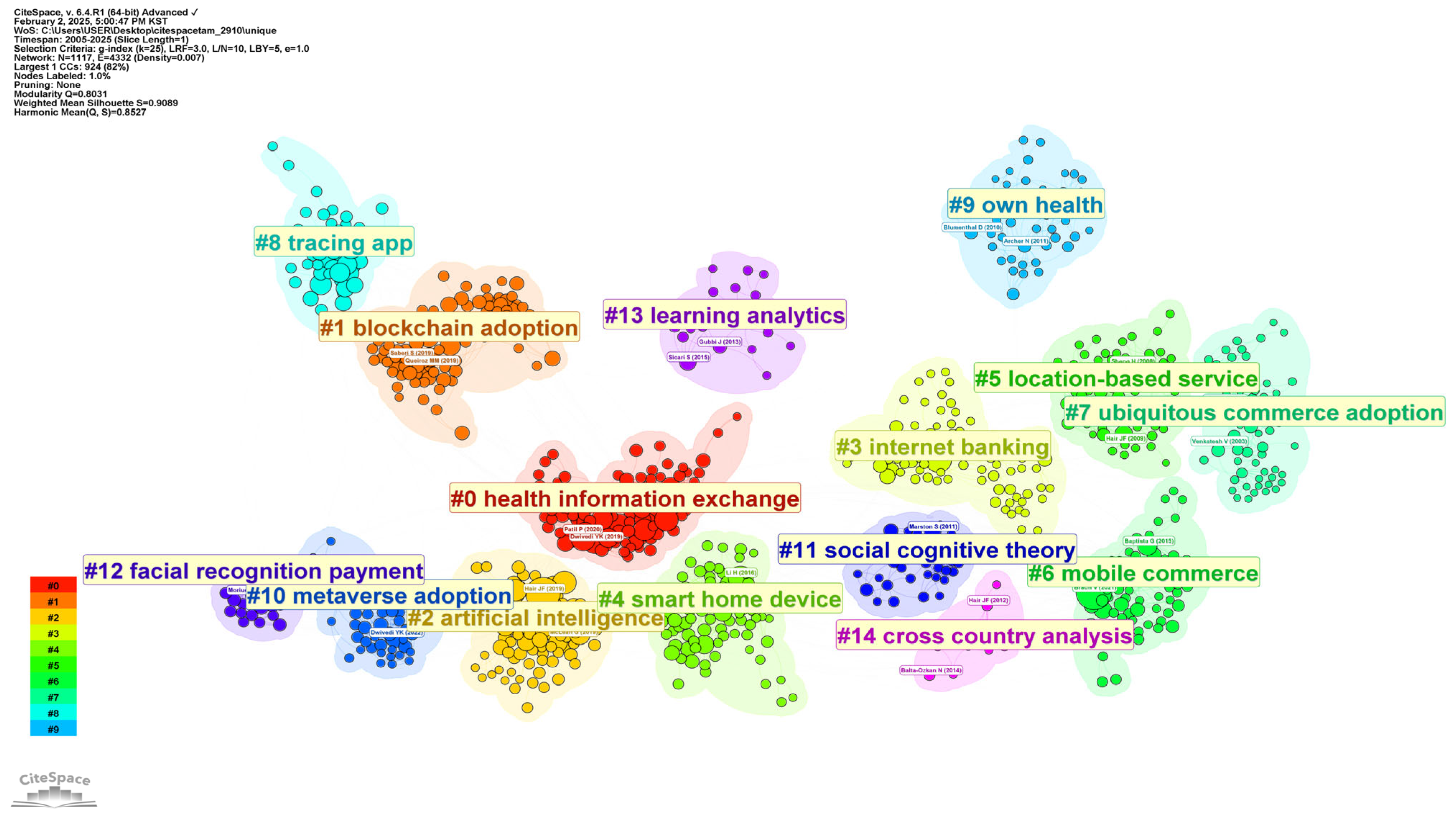
| Custer # | Size | Silhouette | Average Year | Citing Papers | Coverage % |
|---|---|---|---|---|---|
| #0 Health information exchange | 117 | 0.812 | 2017 | Chopdar, P.K. [19]. Adoption of COVID-19 contact tracing app by extending UTAUT theory: Perceived disease threat as moderator. | 21 |
| Alam, M.Z. [32]. Understanding the determinants of mHealth apps adoption in Bangladesh: A SEM-Neural network approach. | 17 | ||||
| Ashrafi, D.M. [33]. Okay google, good to talk to you ... examining the determinants affecting users’ behavioral intention for adopting voice assistants: Does technology self-efficacy matter?. | 17 | ||||
| Bu, F. [34]. Motivating information system engineers’ acceptance of privacy by design in China: an extended UTAUT model. | 13 | ||||
| Colak, H. [35]. How ready are we? Acceptance of internet of things (IoT) technologies by consumers. | 12 | ||||
| #1 Blockchain adoption | 95 | 0.905 | 2018 | Uddin, M.A. [20]. A survey on the adoption of blockchain in IoT: Challenges and solutions. | 13 |
| Rana, N.P. [36]. Analysis of challenges for blockchain adoption within the Indian public sector: An interpretive structural modeling approach. | 13 | ||||
| Moraes, K.K. [37]. Overcoming technological barriers for blockchain adoption in supply chains: A diffusion of innovation (DOI)-informed framework proposal. | 11 | ||||
| Mayer, A.H. [38]. Fogchain: A fog computing architecture integrating blockchain and internet of things for personal health records. | 10 | ||||
| Mukherjee, A.A. [39]. Application of blockchain technology for sustainability development in agricultural supply chain: Justification framework. | 10 | ||||
| #2 Artificial intelligence | 92 | 0.919 | 2020 | Singh, C. [21]. Investigating the acceptance intentions of online shopping assistants in e-commerce interactions: Mediating role of trust and effects of consumer demographics. | 19 |
| Wiangkham, A. [40]. Exploring the drivers for the adoption of metaverse technology in engineering education using PLS-SEM and ANFIS. | 16 | ||||
| Ashrafi, D.M. [33]. Okay google, good to talk to you ... examining the determinants affecting users’ behavioral intention for adopting voice assistants: Does technology self-efficacy matter?. | 14 | ||||
| Acikgoz, F. [41]. Consumer engagement with AI-powered voice assistants: A behavioral reasoning perspective. | 13 | ||||
| Molinillo, S. [42]. Impact of perceived value on intention to use voice assistants: The moderating effects of personal innovativeness and experience. | 12 | ||||
| #3 Internet banking | 89 | 0.876 | 2011 | Hanafizadeh, P. [22]. The mediating role of the dimensions of the perceived risk in the effect of customers’ awareness on the adoption of internet banking in Iran. | 10 |
| Li, H. [43]. Examining individuals’ adoption of healthcare wearable devices: an empirical study from privacy calculus perspective. | 9 | ||||
| Baillette, P. [44]. Bring your own device in organizations: Extending the reversed it adoption logic to security paradoxes for CEOs and end users. | 9 | ||||
| Baillette, P. [45]. BYOD-related innovations and organizational change for entrepreneurs and their employees in SMEs: The identification of a twofold security paradox. | 8 | ||||
| Giovanis, A.N. [46]. An extension of tam model with IDT and security/privacy risk in the adoption of internet banking services in Greece. | 7 | ||||
| #4 Smart home device | 82 | 0.852 | 2016 | Sergueeva, K. [23]. Understanding the barriers and factors associated with consumer adoption of wearable technology devices in managing personal health. | 14 |
| Pal, D. [47]. The future of smartwatches: Assessing the end-users’ continuous usage using an extended expectation-confirmation model. | 13 | ||||
| Pal, D. [48]. Prohibitive factors to the acceptance of internet of things (IoT) technology in society: A smart-home context using a resistive modeling approach. | 12 | ||||
| Peng, C. [49]. Determinants and cross-national moderators of wearable health tracker adoption: A meta-analysis. | 11 | ||||
| Pal, D. [50]. Antecedents of trust and the continuance intention in IoT-based smart products: The case of consumer wearables. | 11 | ||||
| #5 Location-based service | 76 | 0.958 | 2008 | Zhou, T. [24]. The effects of personality traits on user acceptance of mobile commerce. | 14 |
| Zhou, T. [51]. The effect of interactivity on the flow experience of mobile commerce user. | 14 | ||||
| Zhou, T. [26]. Examining continuous usage of location-based services from the perspective of perceived justice. | 13 | ||||
| Zhou, T. [25]. An empirical examination of user adoption of location-based services. | 13 | ||||
| Alaiad, A. [52]. The determinants of home healthcare robots adoption: An empirical investigation. | 9 | ||||
| Zhou, T. [53]. The impact of privacy concern on user adoption of location-based services. | 9 | ||||
| #6 Mobile commerce | 63 | 0.985 | 2014 | Lu, J. [28]. How do post-usage factors and espoused cultural values impact mobile payment continuation? | 13 |
| Lu, J. [29]. Comparison of mobile shopping continuance intention between China and USA from an espoused cultural perspective. | 12 | ||||
| Ooi, K. [54]. Unfolding the privacy paradox among mobile social commerce users: A multi-mediation approach. | 11 | ||||
| Chopdar, P.K. [55]. Mobile shopping apps adoption and perceived risks: A cross-country perspective utilizing the unified theory of acceptance and use of technology. | 8 | ||||
| Palos-Sanchez, P. [56]. The effect of internet searches on afforestation: The case of a green search engine. | 8 | ||||
| #7 Ubiquitous commerce adoption | 51 | 0.915 | 2004 | Sheng, H. [30]. An experimental study on ubiquitous commerce adoption: Impact of personalization and privacy concerns. | 13 |
| Katos, V. [57]. Modeling corporate wireless security and privacy. | 11 | ||||
| Dinev, T. [58]. Is there an on-line advertisers’ dilemma? A study of click fraud in the pay-per-click model. | 10 | ||||
| Xu, H. [59]. The role of push-pull technology in privacy calculus: The case of location-based services. | 9 | ||||
| Carter, L. [60]. The utilization of e-government services: Citizen trust, innovation and acceptance factors. | 8 | ||||
| #8 Tracing app | 51 | 0.915 | 2020 | Alkhalifah, A. [31]. Examining the prediction of COVID contact-tracing app adoption using an integrated model and hybrid approach analysis. | 17 |
| Thenoz, E. [61]. The adoption of contact-tracing applications and the integration of a health pass: A prosocial rationality in the privacy calculus? | 12 | ||||
| Trkman, M. [62]. The roles of privacy concerns and trust in voluntary use of governmental proximity tracing applications. | 12 | ||||
| Kuo, K. [63]. Antecedents predicting digital contact tracing acceptance: A systematic review and meta-analysis. | 11 | ||||
| Chopdar, P.K. [19]. Adoption of COVID-19 contact tracing app by extending UTAUT theory: Perceived disease threat as moderator. | 10 | ||||
| #9 Own health | 47 | 0.995 | 2009 | Steele, R. [64]. Personal health record architectures: Technology infrastructure implications and dependencies. | 8 |
| Gartrell, K. [65]. Testing the electronic personal health record acceptance model by nurses for managing their own health a cross-sectional survey. | 8 | ||||
| Gartrell, K. [66]. Electronic personal health record use among nurses in the nursing informatics community. | 6 | ||||
| Gaylin, D.S. [67]. Public attitudes about health information technology, and its relationship to healthcare quality, costs, and privacy. | 5 | ||||
| Blechman, E.A. [68]. Strategic value of an unbound, interoperable PHR platform for rights-managed care coordination. | 5 | ||||
| #10 Metaverse adoption | 45 | 0.946 | 2022 | Wiangkham, A. [40]. Exploring the drivers for the adoption of metaverse technology in engineering education using PLS-SEM and ANFIS. | 13 |
| Abumalloh, R.A. [69]. The adoption of metaverse in the retail industry and its impact on sustainable competitive advantage: Moderating impact of sustainability commitment. | 11 | ||||
| Gupta, R. [70]. Are we ready for metaverse adoption in the service industry? Theoretically exploring the barriers to successful adoption. | 10 | ||||
| Nadeem, W. [71]. What drives metaverse retail environments' (non)usage? A behavioral reasoning theory perspective. | 8 | ||||
| Mahmoud, A.B. [72]. Exploring the public’s beliefs, emotions and sentiments towards the adoption of the metaverse in education: A qualitative inquiry using big data. | 8 | ||||
| #11 Social cognitive theory | 40 | 0.979 | 2012 | Ratten, V. [73]. Cloud computing technology innovation advances: A set of research propositions. | 20 |
| Ratten, V. [74]. A cross-cultural comparison of online behavioral advertising knowledge, online privacy concerns and social networking using the technology acceptance model and social cognitive theory. | 20 | ||||
| Ratten, V. [75]. International consumer attitudes toward cloud computing: A social cognitive theory and technology acceptance model perspective. | 16 | ||||
| Senarathna, I. [76]. Security and privacy concerns for Australian SMEs cloud adoption: Empirical study of metropolitan vs. regional SMEs. | 8 | ||||
| Lim, N. [77]. Cloud computing: The beliefs and perceptions of Swedish school principals. | 6 | ||||
| #12 Facial recognition payment | 22 | 0.961 | 2021 | Yu, T. [78]. Convenient or risky? Investigating the behavioral intention to use facial recognition payment in smart hospitals. | 16 |
| Yu, T. [79]. Acceptance of or resistance to facial recognition payment: A systematic review. | 14 | ||||
| Chen, H. [80]. Bridging the intention-behavior gap in facial recognition payment from an innovation resistance perspective: A mixed-method approach. | 8 | ||||
| Hwang, J. [81]. An integrated model of artificial intelligence (AI) facial recognition technology adoption based on perceived risk theory and extended TPB: A comparative analysis of US and South Korea. | 8 | ||||
| Wang, M. [82]. Exploring college students’ risk perception and acceptance intention of facial recognition technology in China. | 7 | ||||
| Lyu, T. [83]. Understanding people’s intention to use facial recognition services: The roles of network externality and privacy cynicism. | 7 | ||||
| #13 Learning analytics | 20 | 0.997 | 2014 | Hassan, A.M. [84]. Urban transition in the era of the internet of things: Social implications and privacy challenges. | 4 |
| Burhan, M. [85]. IoT elements, layered architectures and security issues: A comprehensive survey. | 4 | ||||
| Fortino, G. [86]. Using trust and local reputation for group formation in the cloud of things. | 4 | ||||
| Chaurasia, S.S. [87]. Big data academic and learning analytics: Connecting the dots for academic excellence in higher education. | 4 | ||||
| Karampela, M. [88]. Personal health data: A systematic mapping study. | 3 | ||||
| #14 Cross country analysis | 11 | 0.964 | 2013 | Tavares, J. [89]. Electronic health record portal adoption: A cross-country analysis. | 5 |
| Ho, S.M. [90]. Trust or consequences? Causal effects of perceived risk and subjective norms on cloud technology adoption. | 4 | ||||
| Saadi, M.R. [91]. Prioritization of citizens’ preferences for using mobile government services the analytic hierarchy process (AHP) approach. | 3 | ||||
| Kim, Y. [92]. A study on the adoption of IoT smart home service: Using value-based adoption model. | 2 |
4.2. Timeline Analysis
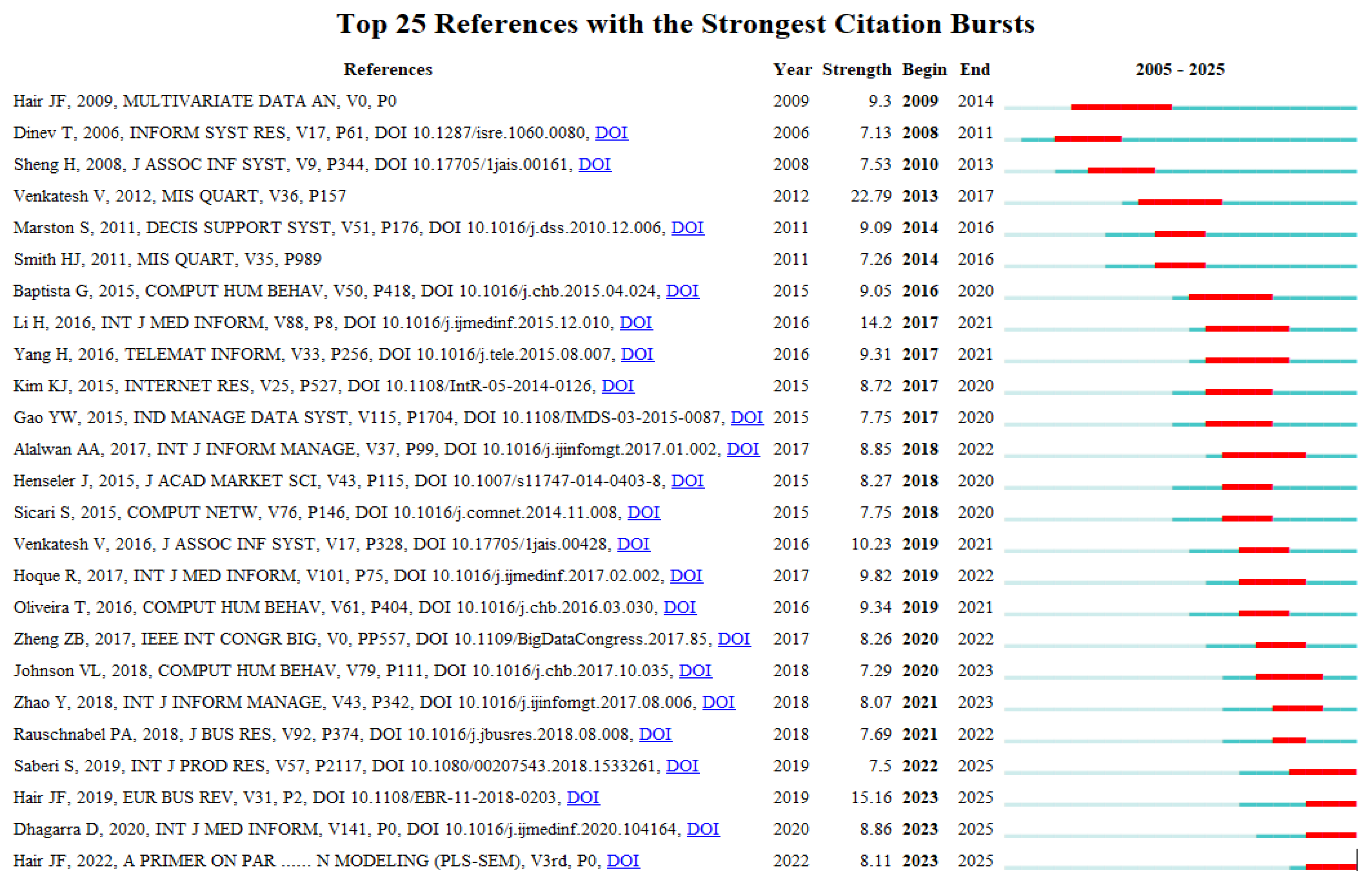
4.3. Burst Detection Analysis
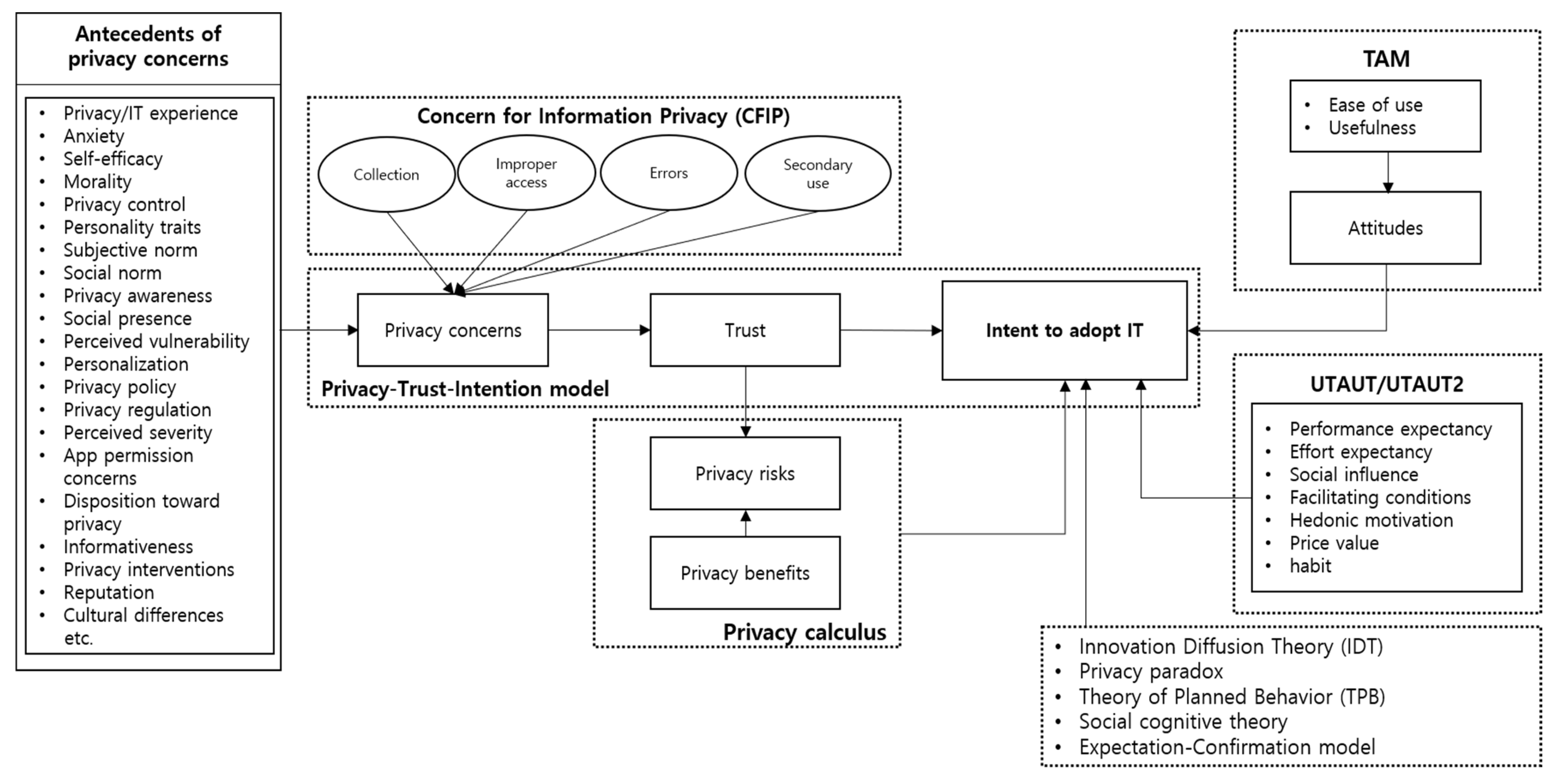
4.4. Framework for Research
5. Discussions
6. Concluding Remarks
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Jang, S.J.; Lee, C.W. Digital entrepreneurial orientation, technology absorptive capacity, and digital innovation on business performance. Systems 2025, 13, 300. [Google Scholar] [CrossRef]
- Shu, S.; Liu, Y. Looking back to move forward: A bibliometric analysis of consumer privacy research. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 727–747. [Google Scholar] [CrossRef]
- Sharma, H.; Srivastava, P.R.; Jasimuddin, S.M.; Zhang, Z.J.; Jebabli, I. Privacy concerns in tourism: A systematic literature review using machine learning approach and bibliometric analysis. Tour. Rev. 2024, 79, 1105–1125. [Google Scholar] [CrossRef]
- Ali, A.S.; Zaaba, Z.F.; Singh, M.M. The rise of “security and privacy”: Bibliometric analysis of computer privacy research. Int. J. Inf. Secur. 2024, 23, 863–885. [Google Scholar] [CrossRef]
- Ouyang, T.; Yang, J.; Gu, Z.; Zhang, L.; Wang, D.; Wang, Y.; Yang, Y. Research on privacy protection in the context of healthcare data based on knowledge map. Medicine 2024, 103, e39370. [Google Scholar] [CrossRef]
- Valencia-Arias, A.; González-Ruiz, J.D.; Flores, L.V.; Vega-Mori, L.; Rodríguez-Correa, P.; Santos, G.S. Machine learning and blockchain: A bibliometric study on security and privacy. Information 2024, 15, 25. [Google Scholar] [CrossRef]
- Amin, M.; Kim, S.; Rishat, M.A.S.A.; Tang, Z.; Ahn, H. A systematic literature review of privacy information disclosure in AI-integrated Internet of Things (IoT) technologies. Sustainability 2025, 17, 8. [Google Scholar] [CrossRef]
- Warren, S.D.; Brandeis, D.L. The right to privacy. Harv. Law Rev. 1989, 4, 193–220. [Google Scholar] [CrossRef]
- Dinev, T.; Hart, P. An extended privacy calculus model for e-commerce transactions. Inf. Syst. Res. 2006, 17, 61–80. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 4th ed.; The Free Press: New York, NY, USA, 1983. [Google Scholar]
- Dwyer, C.; Hiltz, S.R.; Passerini, K. Trust and privacy concern within social networking sites: A comparison of Facebook and Myspace. In Proceedings of the Thirteenth Americas Conference on Information Systems, Keystone, CO, USA, 9–12 August 2007. [Google Scholar]
- Chatterjee, S.; Kharagpur, I. Factors impacting behavioral intention of users to adopt IoT in India: From security and privacy perspective. Int. J. Inf. Secur. Priv. 2020, 14, 92–112. [Google Scholar] [CrossRef]
- Salih, L.; Tarhini, A.; Acikgoz, F. AI-enabled service continuance: Roles of trust and privacy risk. J. Comput. Inf. Syst. 2025, 65, 1–16. [Google Scholar] [CrossRef]
- Freeman, L.C. A set of measures of centrality based on betweenness. Sociometry 1977, 40, 35–41. [Google Scholar] [CrossRef]
- Lim, H.J.; Suh, C.K. Visualization of the intellectual structure on the internet of things focuses on the industry 4.0. J. Korea Ind. Inf. Syst. Res. 2022, 27, 127–140. [Google Scholar] [CrossRef]
- Sood, S.K.; Rawat, K.S.; Kumar, D. Analytical mapping of information and communication technology in emerging infectious diseases using CiteSpace. Telemat. Inform. 2022, 69, 101796. [Google Scholar] [CrossRef] [PubMed]
- Kleinberg, J. Bursty and hierarchical structure in streams. In Proceedings of the Eighth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Edmonton, Canada, 23–26 July 2002; pp. 91–101. [Google Scholar] [CrossRef]
- Chen, C. Science mapping: A systematic review of the literature. J. Data Inf. Sci. 2017, 2, 1–40. [Google Scholar] [CrossRef]
- Chopdar, P.K. Adoption of COVID-19 contact tracing app by extending UTAUT theory: Perceived disease threat as moderator. Health Policy Technol. 2022, 11, 100651. [Google Scholar] [CrossRef] [PubMed]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in IoT: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Singh, C.; Dash, M.K.; Sahu, R.; Kumar, A. Investigating the acceptance intentions of online shopping assistants in e-commerce interactions: Mediating role of trust and effects of consumer demographics. Heliyon 2024, 10, e25031. [Google Scholar] [CrossRef]
- Hanafizadeh, P.; Khedmatgozar, H.R. The mediating role of the dimensions of the perceived risk in the effect of customers’ awareness on the adoption of Internet banking in Iran. Electron. Commer. Res. 2012, 12, 151–175. [Google Scholar] [CrossRef]
- Sergueeva, K.; Shaw, N.; Lee, S.H. Understanding the barriers and factors associated with consumer adoption of wearable technology devices in managing personal health. Can. J. Adm. Sci. 2020, 37, 45–60. [Google Scholar] [CrossRef]
- Zhou, T.; Lu, Y. The effects of personality traits on user acceptance of mobile commerce. Int. J. Hum. Comput. Interact. 2011, 27, 545–561. [Google Scholar] [CrossRef]
- Zhou, T. An empirical examination of user adoption of location-based services. Electron. Commer. Res. 2013, 13, 25–39. [Google Scholar] [CrossRef]
- Zhou, T. Examining continuous usage of location-based services from the perspective of perceived justice. Inf. Syst. Front. 2013, 15, 141–150. [Google Scholar] [CrossRef]
- Jang, S.H.; Lee, C.W. The impact of location-based service factors on usage intentions for technology acceptance: The moderating effect of innovativeness. Sustainability 2018, 10, 1876. [Google Scholar] [CrossRef]
- Lu, J.; Wei, J.; Yu, C.; Liu, C. How do post-usage factors and espoused cultural values impact mobile payment continuation? Behav. Inf. Technol. 2017, 36, 140–164. [Google Scholar] [CrossRef]
- Lu, J.; Yu, C.; Liu, C.; Wei, J. Comparison of mobile shopping continuance intention between China and USA from an espoused cultural perspective. Comput. Hum. Behav. 2017, 75, 130–146. [Google Scholar] [CrossRef]
- Sheng, H.; Nah, F.F.H.; Siau, K. An experimental study on ubiquitous commerce adoption: Impact of personalization and privacy concerns. J. Assoc. Inf. Syst. 2008, 9, 344–376. [Google Scholar] [CrossRef]
- Alkhalifah, A.; Bukar, U.A. Examining the prediction of COVID-19 contact-tracing app adoption using an integrated model and hybrid approach analysis. Front. Public Health 2022, 10, 847184. [Google Scholar] [CrossRef]
- Alam, M.Z.; Hu, W.; Kaium, M.A.; Hoque, M.R.; Alam, M.M.D. Understanding the determinants of mHealth apps adoption in Bangladesh: A SEM–neural network approach. Technol. Soc. 2020, 61, 101255. [Google Scholar] [CrossRef]
- Ashrafi, D.M.; Easmin, R. Okay Google, good to talk to you … examining the determinants affecting users’ behavioral intention for adopting voice assistants: Does technology self-efficacy matter? Int. J. Innov. Technol. Manag. 2023, 20, 2350004. [Google Scholar] [CrossRef]
- Bu, F.; Wang, N.; Jiang, B.; Jiang, Q. Motivating information system engineers’ acceptance of privacy by design in China: An extended UTAUT model. Int. J. Inf. Manag. 2021, 60, 102358. [Google Scholar] [CrossRef]
- Colak, H.; Kağnicioğlu, C.H. How ready are we? Acceptance of Internet of Things (IoT) technologies by consumers. Eskişehir Osmangazi Univ. J. Econ. Adm. Sci. 2021, 16, 401–426. [Google Scholar] [CrossRef]
- Rana, N.P. Analysis of challenges for blockchain adoption within the Indian public sector: An interpretive structural modelling approach. Inf. Technol. People 2022, 35, 548–576. [Google Scholar] [CrossRef]
- Moraes, K.K.; Devós Ganga, G.M.; Filho, M.G.; Santa-Eulalia, L.A.; Tortorella, G.L. Overcoming technological barriers for blockchain adoption in supply chains: A diffusion of innovation (DOI)-informed framework proposal. Supply Chain Manag. Int. J. 2025, 30, 19–49. [Google Scholar] [CrossRef]
- Mayer, A.H.; Rodrigues, V.F.; da Costa, C.A.; da Rosa Righi, R.; Roehrs, A.; Antunes, R.S. FogChain: A fog computing architecture integrating blockchain and Internet of Things for personal health records. IEEE Access 2021, 9, 122723–122737. [Google Scholar] [CrossRef]
- Mukherjee, A.A.; Singh, R.K.; Mishra, R.; Bag, S. Application of blockchain technology for sustainability development in agricultural supply chain: Justification framework. Oper. Manag. Res. 2022, 15, 46–61. [Google Scholar] [CrossRef]
- Wiangkham, A.; Vongvit, R. Exploring the drivers for the adoption of metaverse technology in engineering education using PLS-SEM and ANFIS. Educ. Inf. Technol. 2024, 29, 7385–7412. [Google Scholar] [CrossRef]
- Acikgoz, F.; Pérez-Vega, R.; Okumus, F.; Sylos, N. Consumer engagement with AI-powered voice assistants: A behavioral reasoning perspective. Psychol. Mark. 2023, 40, 2226–2243. [Google Scholar] [CrossRef]
- Molinillo, S.; Rejón-Guardia, F.; Anaya-Sánchez, R.; Liébana-Cabanillas, F. Impact of perceived value on intention to use voice assistants: The moderating effects of personal innovativeness and experience. Psychol. Mark. 2023, 40, 2272–2290. [Google Scholar] [CrossRef]
- Li, H.; Wu, J.; Gao, Y.; Shi, Y. Examining individuals’ adoption of healthcare wearable devices: An empirical study from privacy calculus perspective. Int. J. Med. Inform. 2016, 88, 8–17. [Google Scholar] [CrossRef]
- Baillette, P.; Barlette, Y.; Leclercq-Vandelannoitte, A. Bring your own device in organizations: Extending the reversed IT adoption logic to security paradoxes for CEOs and end users. Int. J. Inf. Manag. 2018, 43, 76–84. [Google Scholar] [CrossRef]
- Baillette, P.; Barlette, Y. BYOD-related innovations and organizational change for entrepreneurs and their employees in SMEs: The identification of a twofold security paradox. J. Organ. Change Manag. 2018, 31, 839–854. [Google Scholar] [CrossRef]
- Giovanis, A.N.; Binioris, S.; Polychronopoulos, G. An extension of the TAM model with IDT and security/privacy risk in the adoption of internet banking services in Greece. EuroMed J. Bus. 2012, 7, 24–53. [Google Scholar] [CrossRef]
- Pal, D.; Funilkul, S.; Vanijja, V.; Papasratorn, B. The future of smartwatches: Assessing the end-users’ continuous usage using an extended expectation-confirmation model. Univ. Access Inf. Soc. 2020, 19, 261–281. [Google Scholar] [CrossRef]
- Pal, D.; Zhang, X.; Siyal, S. Prohibitive factors to the acceptance of internet of things (IoT) technology in society: A smart home context using a resistive modelling approach. Technol. Soc. 2021, 66, 101683. [Google Scholar] [CrossRef]
- Peng, C.; Zhao, H.; Zhang, S. Determinants and cross national moderators of wearable health tracker adoption: A meta analysis. Sustainability 2021, 13, 13328. [Google Scholar] [CrossRef]
- Pal, D.; Funilkul, S.; Papasratorn, B. Antecedents of trust and the continuance intention in IoT based smart products: The case of consumer wearables. IEEE Access 2019, 7, 184160–184171. [Google Scholar] [CrossRef]
- Zhou, T. The effect of interactivity on the flow experience of mobile commerce users. Int. J. Mobil. Commun. 2011, 9, 225–242. [Google Scholar] [CrossRef]
- Alaiad, A.; Zhou, L. The determinants of home healthcare robots adoption: An empirical investigation. Int. J. Med. Inform. 2014, 83, 825–840. [Google Scholar] [CrossRef]
- Zhou, T. The impact of privacy concern on user adoption of location-based services. Ind. Manag. Data Syst. 2011, 111, 212–226. [Google Scholar] [CrossRef]
- Ooi, K.B.; Tan, G.W.; Hew, T.S.; Lin, B. Unfolding the privacy paradox among mobile social commerce users: A multi-mediation approach. Behav. Inf. Technol. 2018, 37, 575–595. [Google Scholar] [CrossRef]
- Chopdar, P.K.; Sivakumaran, B. Mobile shopping apps adoption and perceived risks: A cross-country perspective utilizing the Unified Theory of Acceptance and Use of Technology. Comput. Hum. Behav. 2018, 86, 109–128. [Google Scholar] [CrossRef]
- Palos-Sanchez, P.; Saura, J.R.; Palos-Sanchez, P.R. The effect of internet searches on afforestation: The case of a green search engine. Forests 2018, 9, 51. [Google Scholar] [CrossRef]
- Katos, V.; Stavrou, V.; Gritzalis, D. Modeling corporate wireless security and privacy. J. Strateg. Inf. Syst. 2005, 14, 307–321. [Google Scholar] [CrossRef]
- Dinev, T.; Hu, Q.; Yayla, A. Is there an on-line advertisers’ dilemma? A study of click fraud in the pay-per-click model. Int. J. Electron. Commer. 2008, 13, 29–59. Available online: https://www.jstor.org/stable/27751287 (accessed on 11 November 2025). [CrossRef]
- Xu, H.; Teo, H.H.; Tan, B.C.; Agarwal, R. The role of push-pull technology in privacy calculus: The case of location-based services. J. Manag. Inf. Syst. 2009, 26, 135–174. [Google Scholar] [CrossRef]
- Carter, L.; Bélanger, F. The utilization of e-government services: Citizen trust, innovation and acceptance factors. Inf. Syst. J. 2005, 15, 5–25. [Google Scholar] [CrossRef]
- Thenoz, E.; Chouk, I.; Ferrandi, J.; Gonzalez, C.; Rowe, F.; Siadou-Martin, B. The adoption of contact-tracing applications and the integration of a health pass: A prosocial rationality in the privacy calculus. J. Glob. Inf. Manag. 2023, 31, 1–23. [Google Scholar] [CrossRef]
- Trkman, M.; Popovič, A.; Trkman, P. The roles of privacy concerns and trust in voluntary use of governmental proximity tracing applications. Gov. Inf. Q. 2023, 40, 101787. [Google Scholar] [CrossRef]
- Kuo, K.-M. Antecedents predicting digital contact tracing acceptance: A systematic review and meta-analysis. BMC Med. Inform. Decis. Mak. 2023, 23, 212. [Google Scholar] [CrossRef]
- Steele, R.; Min, K.; Lo, A. Personal health record architectures: Technology infrastructure implications and dependencies. J. Am. Soc. Inf. Sci. Technol. 2012, 63, 1079–1091. [Google Scholar] [CrossRef]
- Gartrell, K.; Trinkoff, A.M.; Storr, C.L.; Wilson, M.L.; Gurses, A.P. Testing the electronic personal health record acceptance model by nurses for managing their own health: A cross-sectional survey. Appl. Clin. Inform. 2015, 6, 224–247. [Google Scholar] [CrossRef]
- Gartrell, K.; Trinkoff, A.M.; Storr, C.L.; Wilson, M.L.; Gurses, A.P. Electronic personal health record use among nurses in the nursing informatics community. Comput. Inform. Nurs. 2015, 33, 306–314. [Google Scholar] [CrossRef] [PubMed]
- Gaylin, D.S.; Moiduddin, A.; Mohamoud, S.; Lundeen, K.; Kelly, J.A. Public attitudes about health information technology, and its relationship to health care quality, costs, and privacy. Health Serv. Res. 2011, 46, 920–938. [Google Scholar] [CrossRef] [PubMed]
- Blechman, E.A.; Raich, P.; Raghupathi, W.; Blass, S. Strategic value of an unbound, interoperable PHR platform for rights-managed care coordination. Commun. Assoc. Inf. Syst. 2012, 30. [Google Scholar] [CrossRef]
- Abumalloh, R.A.; Nilashi, M.; Ooi, K.B.; Wei-Han, G.; Cham, T.-H.; Dwivedi, Y.K.; Hughes, L. The adoption of metaverse in the retail industry and its impact on sustainable competitive advantage: Moderating impact of sustainability commitment. Ann. Oper. Res. 2024, 342, 5–46. [Google Scholar] [CrossRef]
- Gupta, R.; Rathore, B.; Biswas, B.; Jaiswal, M.; Singh, R.K. Are we ready for metaverse adoption in the service industry? Theoretically exploring the barriers to successful adoption. J. Retail. Consum. Serv. 2024, 79, 103882. [Google Scholar] [CrossRef]
- Nadeem, W.; Ashraf, A.R.; Shahid, S. What drives metaverse retail environments (non)usage? A behavioral reasoning theory perspective. Technol. Forecast. Soc. Change 2025, 212, 123945. [Google Scholar] [CrossRef]
- Mahmoud, A.B. Exploring the public’s beliefs, emotions and sentiments towards the adoption of the metaverse in education: A qualitative inquiry using big data. Br. Educ. Res. J. 2024, 50, 2320–2341. [Google Scholar] [CrossRef]
- Ratten, V. Cloud computing technology innovation advances: A set of research propositions. Int. J. Cloud Appl. Comput. 2015, 5, 69–76. [Google Scholar] [CrossRef]
- Ratten, V. A cross-cultural comparison of online behavioural advertising knowledge, online privacy concerns and social networking using the technology acceptance model and social cognitive theory. J. Sci. Technol. Policy Manag. 2015, 6, 25–36. [Google Scholar] [CrossRef]
- Ratten, V. International consumer attitudes toward cloud computing: A social cognitive theory and technology acceptance model perspective. Thunderbird Int. Bus. Rev. 2015, 57, 217–228. [Google Scholar] [CrossRef]
- Senarathna, I.; Yeoh, W.; Warren, M.; Salzman, S. Security and privacy concerns for Australian SMEs cloud adoption: Empirical study of metropolitan vs. regional SMEs. Australas. J. Inf. Syst. 2016, 20, 1–23. [Google Scholar] [CrossRef]
- Lim, N.; Grönlund, Å.; Andersson, A. Cloud computing: The beliefs and perceptions of Swedish school principals. Comput. Educ. 2015, 84, 90–100. [Google Scholar] [CrossRef]
- Yu, T.; Teoh, A.P.; Wang, C.; Bian, Q. Convenient or risky? Investigating the behavioral intention to use facial recognition payment in smart hospitals. Humanit. Soc. Sci. Commun. 2024, 11, 1592. [Google Scholar] [CrossRef]
- Yu, T.; Wang, C.; Bian, Q.; Teoh, A.P. Acceptance of or resistance to facial recognition payment: A systematic review. J. Consum. Behav. 2024, 23, 1–19. [Google Scholar] [CrossRef]
- Chen, H.; Liu, X.; Zhang, Y.; Zhang, S.; Jiao, W. Bridging the intention–behavior gap in facial recognition payment from an innovation resistance perspective: A mixed-method approach. Int. J. Hum.-Comput. Interact. 2025, 41, 8702–8724. [Google Scholar] [CrossRef]
- Hwang, J.; Kim, J.; Joo, K.H.; Choe, J.Y. An integrated model of artificially intelligent (AI) facial recognition technology adoption based on perceived risk theory and extended TPB: A comparative analysis of US and South Korea. J. Hosp. Mark. Manag. 2024, 33, 1071–1099. [Google Scholar] [CrossRef]
- Wang, M.; Kang, Y.; Deng, B.; Lan, X. Exploring college students’ risk perception and acceptance intention of facial recognition technology in China. Telemat. Inform. 2024, 95, 102193. [Google Scholar] [CrossRef]
- Lyu, T.; Guo, Y.; Chen, H. Understanding people’s intention to use facial recognition services: The roles of network externality and privacy cynicism. Inf. Technol. People 2024, 37, 1025–1051. [Google Scholar] [CrossRef]
- Hassan, A.M.; Awad, A.I. Urban transition in the era of the Internet of Things: Social implications and privacy challenges. IEEE Access 2018, 6, 36428–36440. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.-S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef]
- Fortino, G.; Messina, F.; Rosaci, D.; Sarné, G.M.L. Using trust and local reputation for group formation in the cloud of things. Future Gener. Comput. Syst. 2018, 89, 804–815. [Google Scholar] [CrossRef]
- Chaurasia, S.S.; Kodwani, D.; Lachhwani, H.; Ketkar, M.A. Big data academic and learning analytics: Connecting the dots for academic excellence in higher education. Int. J. Educ. Manag. 2018, 32, 1099–1117. [Google Scholar] [CrossRef]
- Karampela, M.; Ouhbi, S.; Isomursu, M. Personal health data: A systematic mapping study. Int. J. Med. Inform. 2018, 118, 86–98. [Google Scholar] [CrossRef]
- Tavares, J.; Oliveira, T. Electronic health record portal adoption: A cross-country analysis. BMC Med. Inform. Decis. Mak. 2017, 17, 97. [Google Scholar] [CrossRef]
- Ho, S.M.; Ocasio Velázquez, M.; Booth, C. Trust or consequences? Causal effects of perceived risk and subjective norms on cloud technology adoption. Comput. Secur. 2017, 70, 581–595. [Google Scholar] [CrossRef]
- Saadi, M.R.; Ahmad, S.Z.; Hussain, M. Prioritization of citizens’ preferences for using mobile government services: The analytic hierarchy process (AHP) approach. Transform. Gov. People Process Policy 2017, 11, 476–503. [Google Scholar] [CrossRef]
- Kim, Y.; Park, Y.; Choi, J. A study on the adoption of IoT smart home service: Using value-based adoption model. Total Qual. Manag. Bus. Excell. 2017, 28, 1149–1165. [Google Scholar] [CrossRef]
- Morris, S.A.; Yen, G.; Wu, Z.; Asnake, B. Time line visualization of research fronts. J. Am. Soc. Inf. Sci. Technol. 2003, 54, 413–422. [Google Scholar] [CrossRef]
- Dwivedi, Y.K.; Rana, N.P.; Jeyaraj, A.; Clement, M.; Williams, M.D. Re-examining the Unified Theory of Acceptance and Use of Technology (UTAUT): Towards a revised theoretical model. Inf. Syst. Front. 2019, 21, 719–734. [Google Scholar] [CrossRef]
- Dhagarra, D.; Goswami, M.; Kumar, G. Impact of trust and privacy concerns on technology acceptance in healthcare: An Indian perspective. Int. J. Med. Inform. 2020, 141, 104164. [Google Scholar] [CrossRef] [PubMed]
- McLean, G.; Osei-Frimpong, K. Hey Alexa … examine the variables influencing the use of artificial intelligent in-home voice assistants. Comput. Hum. Behav. 2019, 99, 28–37. [Google Scholar] [CrossRef]
- Hair, J.F.; Risher, J.J.; Sarstedt, M.; Ringle, C.M. When to use and how to report the results of PLS-SEM. Eur. Bus. Rev. 2019, 31, 2–24. [Google Scholar] [CrossRef]
- Venkatesh, V.; Tong, J.Y.L.; Xu, X. Unified theory of acceptance and use of technology: A synthesis and the road ahead. J. Assoc. Inf. Syst. 2016, 17, 328–376. [Google Scholar] [CrossRef]
- Braun, V.; Clarke, V. One size fits all? What counts as quality practice in (reflexive) thematic analysis. Qual. Res. Psychol. 2021, 18, 328–352. [Google Scholar] [CrossRef]
- Venkatesh, V.; Tong, J.Y.L.; Xu, T.X. Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology. MIS Q. 2012, 36, 157–178. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Budi, N.F.A.; Adnan, H.R.; Firmansyah, F.; Hidayanto, A.N.; Kurnia, S.; Purwandari, B. Why do people want to use location-based application for emergency situations? The extension of UTAUT perspectives. Technol. Soc. 2021, 65, 101480. [Google Scholar] [CrossRef]
- Ciftci, O.; Berezina, K.; Soifer, I. Exploring privacy-personalization paradox: Facial recognition systems at business events. Comput. Hum. Behav. 2024, 159, 108335. [Google Scholar] [CrossRef]
- Hoque, R.; Sorwar, G. Understanding factors influencing the adoption of mHealth by the elderly: An extension of the UTAUT model. Int. J. Med. Inform. 2017, 101, 75–84. [Google Scholar] [CrossRef] [PubMed]
- Oliveira, T.; Thomas, M.; Baptista, G.; Campos, F. Mobile payment: Understanding the determinants of customer adoption and intention to recommend the technology. Comput. Hum. Behav. 2016, 61, 404–414. [Google Scholar] [CrossRef]
- Yang, H.; Yu, J.; Zo, H.; Choi, M. User acceptance of wearable devices: An extended perspective of perceived value. Telemat. Inform. 2016, 33, 256–269. [Google Scholar] [CrossRef]
- Hair, J.F.; Black, W.C.; Babin, B.J.; Anderson, R.E. Multivariate Data Analysis, 7th ed.; Pearson Prentice Hall: Upper Saddle River, NJ, USA, 2009. [Google Scholar]
- Marston, S.; Li, Z.; Bandyopadhyay, S.; Zhang, J.; Ghalsasi, A. Cloud computing—The business perspective. Decis. Support Syst. 2011, 51, 176–189. [Google Scholar] [CrossRef]
- Baptista, G.; Oliveira, T. Understanding mobile banking: The unified theory of acceptance and use of technology combined with cultural moderators. Comput. Hum. Behav. 2015, 50, 418–430. [Google Scholar] [CrossRef]
- Smith, H.J.; Dinev, T.; Xu, H. Information Privacy Research: An Interdisciplinary Review. MIS Q. 2011, 35, 989–1015. [Google Scholar] [CrossRef]
- Kim, K.-J.; Shin, D.-H. An acceptance model for smart watches: Implications for the adoption of future wearable technology. Internet Res. 2015, 25, 527–541. [Google Scholar] [CrossRef]
- Gao, Y.-W.; Li, H.; Luo, Y. An empirical study of wearable technology acceptance in healthcare. Ind. Manag. Data Syst. 2015, 115, 1704–1723. [Google Scholar] [CrossRef]
- Alalwan, A.A.; Dwivedi, Y.K.; Rana, N.P. Factors influencing adoption of mobile banking by Jordanian bank customers: Extending UTAUT2 with trust. Int. J. Inf. Manag. 2017, 37, 99–110. [Google Scholar] [CrossRef]
- Henseler, J.; Ringle, C.M.; Sarstedt, M. A new criterion for assessing discriminant validity in variance-based structural equation modeling. J. Acad. Market. Sci. 2015, 43, 115–135. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Johnson, D.G.; Verdicchio, M. Why robots should not be treated like animals. Ethics Inf. Technol. 2018, 20, 291–301. [Google Scholar] [CrossRef]
- Zhao, Y.; Ni, Q.; Zhou, R. What factors influence the mobile health service adoption? A meta-analysis and the moderating role of age. Int. J. Inf. Manag. 2018, 43, 342–350. [Google Scholar] [CrossRef]
- Rauschnabel, P.A.; He, J.; Ro, Y.K. Antecedents to the adoption of augmented reality smart glasses: A closer look at privacy risks. J. Bus. Res. 2018, 92, 374–384. [Google Scholar] [CrossRef]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2019, 57, 2117–2135. [Google Scholar] [CrossRef]
- Hair, J.F., Jr.; Hult, G.T.M.; Ringle, C.M.; Sarstedt, M.; Danks, N.P.; Ray, S. Partial Least Squares Structural Equation Modeling (PLS-SEM) Using R: A Workbook; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. User acceptance of computer technology: A comparison of two theoretical models. Manag. Sci. 1989, 35, 982–1003. [Google Scholar] [CrossRef]

| Regions | Freq. | Affiliations | Freq. | Authors | Freq. |
|---|---|---|---|---|---|
| USA | 753 | State University System of Florida | 63 | Dwivedi, Y.K. | 13 |
| China | 388 | Indian Institute of Management (IIM) System | 54 | Esmaeilzadeh, P. | 10 |
| India | 307 | Indian Institute of Technology (IIT)System | 41 | Ziefle, M. | 9 |
| England | 237 | University of Texas System | 39 | Pal, D. | 9 |
| Australia | 200 | University of North Carolina | 35 | Prybutok, V. | 9 |
| Germany | 163 | University of California System | 33 | OOI, K.B. | 8 |
| Saudi Arabia | 161 | University of Toronto | 33 | Rana, N.P. | 8 |
| Canada | 157 | University of London | 29 | Chatterjee, S. | 8 |
| South Korea | 132 | King Saud University | 28 | Oliveira, T. | 7 |
| Malaysia | 125 | Symbiosis International University | 28 | Venkatesh, V. | 7 |
| Publication Titles | Freq. | Fields (Web of Science Categories) | Freq. |
|---|---|---|---|
| IEEE Access | 72 | Computer Science-Information Systems | 597 |
| Computers in Human Behavior | 48 | Business | 394 |
| Journal of Medical Internet Research | 48 | Information Science & Library Science | 308 |
| Sustainability | 41 | Management | 267 |
| Technological Forecasting and Social Change | 36 | Health Care Sciences & Services | 251 |
| Sensors | 32 | Telecommunications | 243 |
| Technology in Society | 30 | Medical Informatics | 229 |
| Journal of Retailing and Consumer Services | 29 | Engineering Electrical Electronic | 227 |
| International Journal of Medical Informatics | 24 | Computer Science, Interdisciplinary Applications | 123 |
| HELIYON | 23 | Computer Science, Theory & Methods | 111 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jang, S.H.; Lee, C.W. A Bibliographic Analysis of Research Trends on Privacy in Technology Adoption: Information Synthesis Perspective. Information 2025, 16, 1027. https://doi.org/10.3390/info16121027
Jang SH, Lee CW. A Bibliographic Analysis of Research Trends on Privacy in Technology Adoption: Information Synthesis Perspective. Information. 2025; 16(12):1027. https://doi.org/10.3390/info16121027
Chicago/Turabian StyleJang, Sung Hee, and Chang Won Lee. 2025. "A Bibliographic Analysis of Research Trends on Privacy in Technology Adoption: Information Synthesis Perspective" Information 16, no. 12: 1027. https://doi.org/10.3390/info16121027
APA StyleJang, S. H., & Lee, C. W. (2025). A Bibliographic Analysis of Research Trends on Privacy in Technology Adoption: Information Synthesis Perspective. Information, 16(12), 1027. https://doi.org/10.3390/info16121027