-
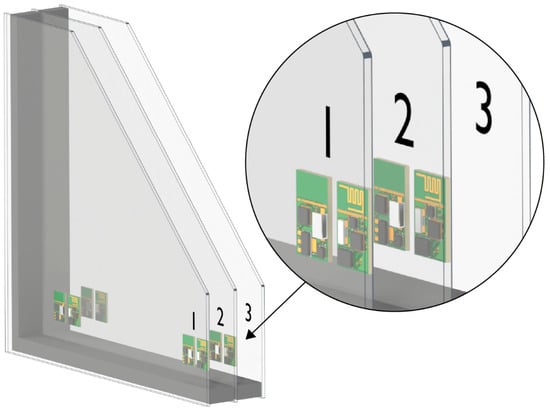
 Securing the SDN Data Plane in Emerging Technology Domains: A Review
Securing the SDN Data Plane in Emerging Technology Domains: A Review -
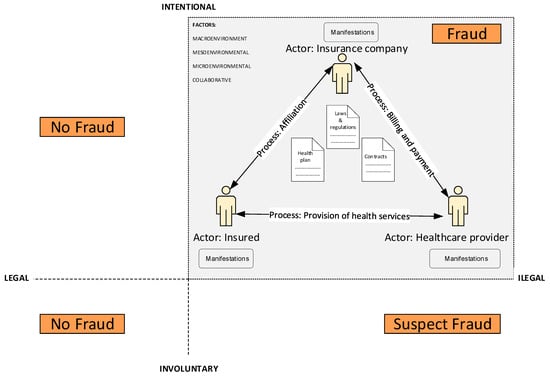
 Towards Proactive Domain Name Security: An Adaptive System for .ro domains Reputation Analysis
Towards Proactive Domain Name Security: An Adaptive System for .ro domains Reputation Analysis -
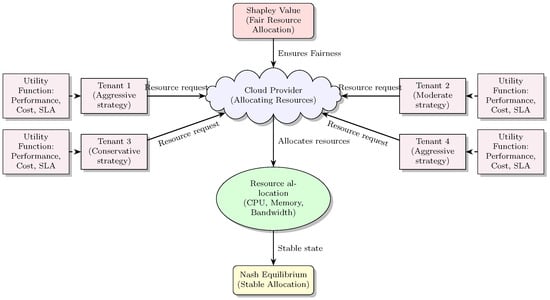
 Intelligent Control Approaches for Warehouse Performance Optimisation in Industry 4.0 Using Machine Learning
Intelligent Control Approaches for Warehouse Performance Optimisation in Industry 4.0 Using Machine Learning -
 AI-Driven Transformations in Manufacturing: Bridging Industry 4.0, 5.0, and 6.0 in Sustainable Value Chains
AI-Driven Transformations in Manufacturing: Bridging Industry 4.0, 5.0, and 6.0 in Sustainable Value Chains -
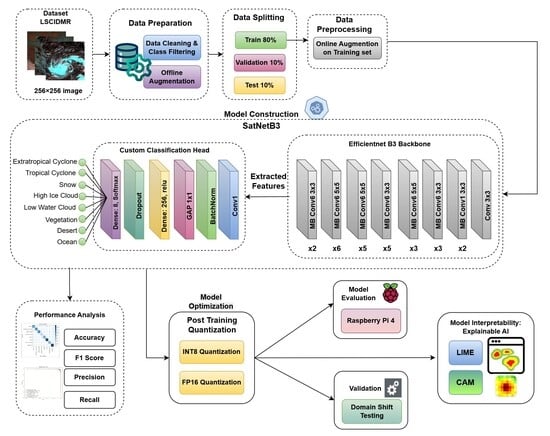
 Intelligent Edge Computing and Machine Learning: A Survey of Optimization and Applications
Intelligent Edge Computing and Machine Learning: A Survey of Optimization and Applications
Journal Description
Future Internet
- Open Access— free for readers, with article processing charges (APC) paid by authors or their institutions.
- High Visibility: indexed within Scopus, ESCI (Web of Science), Ei Compendex, dblp, Inspec, and other databases.
- Journal Rank: JCR - Q2 (Computer Science, Information Systems) / CiteScore - Q1 (Computer Networks and Communications)
- Rapid Publication: manuscripts are peer-reviewed and a first decision is provided to authors approximately 17 days after submission; acceptance to publication is undertaken in 3.6 days (median values for papers published in this journal in the first half of 2025).
- Recognition of Reviewers: reviewers who provide timely, thorough peer-review reports receive vouchers entitling them to a discount on the APC of their next publication in any MDPI journal, in appreciation of the work done.
- Journal Clusters of Network and Communications Technology: Future Internet, IoT, Telecom, Journal of Sensor and Actuator Networks, Network, Signals.
Latest Articles
E-Mail Alert
News
Meet Us Virtually at the 1st International Online Conference on Sensor and Actuator Networks (CSAN 2026), 9–10 July 2026

MDPI Launches the Michele Parrinello Award for Pioneering Contributions in Computational Physical Science

Topics
Deadline: 31 December 2025
Deadline: 31 January 2026
Deadline: 28 February 2026
Deadline: 11 March 2026
Conferences
Special Issues
Deadline: 20 December 2025
Deadline: 31 December 2025
Deadline: 31 December 2025
Deadline: 31 December 2025