1. Introduction
Nowadays, electronic warfare (EW) is an emerging field that is growing at a rapid pace. In this context, securing communication between various embedded systems such as UAVs and base stations can easily fall victim to various types of advanced enemy jamming. To protect and immunize these communication links, various techniques can be used, ranging from statistical methods to machine learning. The paper published in [
1] shows that UAVs generally use wireless networks such as Wi-Fi, Long-Term Evolution (LTE) and fifth-generation (5G) technology. Among these, 5G systems predominantly use OFDM modulation techniques for their immunity to jamming interference. However, this modulation technique is still limited against selective interference of the transmission signal, as in the case of reactive jamming, which only works when there is active transmission between the drone and the base station receiver, making it very difficult to intercept this type of jamming.
Currently, machine learning (ML) techniques are widely used to detect various types of jamming in OFDM UAVs. The authors proposed in [
2] six conventional ML algorithms—decision tree (DT), k-nearest neighbors (KNN), logistic regression (LR), multilayer perceptron (MLP), naïve Bayes (NB), and random forest (RF)—to detect four basic proactive jamming signals, namely, Barrage, Tone, Success pulse, and P-aware. All algorithms were quantitatively validated with measurements, including detection and false-alarm rates, and the results revealed that interference was detected and classified with 92.2% confidence and a false-alarm rate of 1.35%.
Exploring further into the embedded ML, we find that Viana in [
3] offers a principal component analysis (PCA)-featured transformer for 5G-UAV networks. The PCA compresses the RSSI/SINR time series, and the transformer captures the long dependencies. This approach is characterized by detecting complex scenarios (multiple jammers, variable channels), but it requires memory and computational power, which poses the problem of embedding it in a microcontroller. The authors in [
4] applied several ML algorithms, including AlexNet, VGG16, ResNet-50, and EfficientNet-B0, based on spectrogram signal images in their training and testing phases to detect the same types of jamming attacks treated in [
2]. The detection rate of all ML algorithms was around 99%. In the paper proposed in [
4], a 3.20 GHz central processing unit (CPU) with 128 GB RAM and a Tesla P100 graphics processing unit (GPU) with 16 GB RAM were used to train and test the ML models. In reality, most commercial drones do not have microprocessors suitable for techniques such as deep learning and machine learning. This raises questions about the actual implementation in commercial drones, which generally use limited and restricted hardware.
In [
5], the authors simulated three types of interference, including constant, reactive, and random, using the Network Simulator-3 (ns-3) environment and trained five ML algorithms. The gradient boosting model showed 93–95% detection accuracy, and random forest showed 91% accuracy. The approach uses a synthetic dataset that does not take into consideration environmental noise and fading effects.
The state of the art shows that ML methods used for reactive jamming detection are computationally intensive and less effective when the environment changes abruptly or contains significant AWGN. Therefore, an area for improvement compared to the literature is the lack of simple methods that can manage multiple features simultaneously and efficiently, such as signal energy and variation in signal complexity over multiple samples.
From another angle, some recent studies of reactive jamming detection use probabilistic methods that better account for the uncertainty associated with the radio channel by avoiding dependence on data and its environment.
In his study [
6], Altun employed a statistical test dedicated to OFDM-IM by utilizing the energy distribution between active and inactive subcarriers to detect the intrusion of a reactive jammer. This method proved to be simple and interpretable but was sensitive to additive noise and required accurate calibration of thresholds.
The authors in [
7] implemented a Hidden Markov Model (HMM) that uses the received signal strength as a binary clean/jammed string and estimates the parameters using Expectation and Maximization (EM). This method achieved detection probabilities greater than 95% for average SNR values ranging from −10 dB to −4 dB. However, the performance of this probabilistic model decreased when the fraction of victim frames was very short and when the noise distribution deviated from the Gaussian shape.
The authors in [
8] used the Sequential Probability Ratio Test (SPRT), which is fed with bit errors associated with radio frequency interference received signal strength (RSS) to distinguish between ambient and real noise. This method can detect jamming in near real time, but it requires an accurate measurement of the RSS per bit and is sensitive to sudden fluctuations in data traffic.
Spühler in [
9] proposed a statistical method based on the difference between the predicted packet delivery ratio (PDR) and the actually observed PDR. They used preamble symbols and were able to keep the total detection error (FP + FN) below 8% even when the jammer attacked all of the transmitted packets. The method is very simple, but it does not work if the preamble is also corrupted, and even more so if the received signals are fluctuating too much to estimate the expected PDR.
From a more theoretical point of view, Thai in his study [
10] created a Trigger Identification Service, which is a non-adaptive fault-tolerant group testing scheme that uses specific transmission patterns to identify a subset of nodes that will trigger a reactive jammer. This solution has been demonstrated analytically, but it seems to be difficult to implement once the network grows.
Based on a 2 × 2 free-space-optical multiple-input multiple-output (MIMO) link, Sliti et al. in [
11] monitored the multichannel ratio (MCR) between two receiver apertures. Any significant deviation above the threshold indicates an interference attempt, and the same ratio is used to subtract the interference from the desired signal. Simulations in log-normal free-space-optical (FSO) channels showed that recalculating the MCR removed approximately 90% of the interference power every five samples, but this efficiency decreased as the interference-to-signal ratio increased. Although the method is lightweight, its assumption of quasi-static channels and a single-antenna attacker could weaken robustness in swarms of fast-moving UAVs facing smarter jammers.
Additionally, within UAV swarms using Impulse Radio Ultra-Wide-band (IR-UWB) links, Gupta et al. [
12] applied thresholding on Channel State Information (CSI) together with lightweight machine learning models to detect jamming attacks in real time while preserving range accuracy. However, the inherent specificity of IR-UWB limits the direct transfer of this approach to OFDM systems.
Zeng, in his tutorial [
13], showed that UAV platforms operate under severe size, weight, and power (SWaP) constraints that directly cap on-board computing power and energy. In contrast, Li [
4], Ray [
14], and Immonen [
15] described deep learning-based jamming or modulation classifiers that achieve high accuracies from spectrogram inputs and large datasets, but their methods require GPU-accelerated training and memory footprints that are incompatible with microcontroller-class hardware. In addition, the study of Perenda [
16] highlights the vulnerability of these models to channel/material domain shifts and proposes dedicated augmentation schemes, while Deng [
17] confirms the need for transfer and adaptation pipelines to restore robustness. In this context, Ray [
14] and Immonen [
15] emphasize that a detector based on low-order statistics and closed-form decision rules guarantees deterministic time/space complexity and interpretable decisions, making it suitable for real-time embedded systems under SWaP constraints. These elements justify, in line with Zeng’s analysis [
13], the option of a lightweight statistical approach for reactive jamming detection on resource-constrained UAVs.
Beyond detection, resilience to jamming requires intelligent allocation of resources in a contested environment. Recent deep reinforcement learning studies jointly optimize transmit power, channel/carrier selection, beamforming and IRS phases to maintain Quality of Service (QoS) while maximizing energy efficiency. For example, Ma et al. [
18] modeled energy efficiency maximization in an RSMA-IRS system for ISAC and learned a proximal control policy that simultaneously adjusts transmitter-side beamforming and Intelligent Reflecting Surface (IRS) phases under service constraints.
Building on previous work in the literature, this study proposes a method that combines two key parameters: the local root-mean-square (RMS) energy, used to flag sudden changes in the received signal, and the Sevcik fractal dimension (SFD), which serves as a complexity detector for that signal. The final decision is made by computing the Mahalanobis distance between the current feature vector and a baseline distribution, enabling robust outlier-based discrimination of jamming events. The simulation results show that the proposed approach achieved a detection accuracy above 99%, with minimal false negative and false positive rates.
As a second key contribution, we replaced the conventional single fixed threshold with a self-adjusting threshold, enabling the proposed algorithm to automatically track variations in the jamming landscape and remain effective across a broad spectrum of real-world conditions. We show that the method couples high detection accuracy with very modest computational demands, making it deployable on unmanned aircraft with limited onboard resources.
The approach blends the Sevcik fractal dimension with local effective energy, equips them with an adaptive threshold for added flexibility, and proves its value under realistic stressors such as a Rayleigh channel with reactive jamming through targeted simulation campaigns.
The rest of the article is organized as follows.
Section 2 presents the reactive interference models commonly used to defeat UAV missions.
Section 3 presents the methods and models used to simulate OFDM signals and reactive jamming and the detection model used. Finally,
Section 4 shows an analysis of the evaluation results.
3. Methodology
Wilhelm in [
20] showed that reactive jamming is among the most insidious threats to OFDM communication, as it is extremely difficult to detect due to its minimal activation time and maximal energy efficiency. The method presented in this article is based on a mathematical model of this instantaneous interference. We model (i) the activation process based on excess received energy, (ii) a response delay
that mimics the hardware latency observed in software-defined radios (SDRs), and (iii) additive white Gaussian noise (AWGN) with power
determined by the jammer-to-signal ratio (JSR). This model is then used to derive the detection features (RMS energy and Sevcik fractal dimension, FD) and to calibrate the adaptive thresholds.
3.1. Signal Model
Consider a complex OFDM signal passing through a time-selective channel and disturbed by additive Gaussian noise AWGN ∼.
denotes a circularly symmetric complex Gaussian with mean zero and variance .
The receiver observes
where is the received signal before any jamming activity;
is the transmitted OFDM symbol;
is the Rayleigh channel impulse response;
∼ is the AWGN, or additive white Gaussian noise;
“∗” is the discrete convolution.
An OFDM signal with 64 carriers and a cyclic prefix corresponding to 16 is sampled at
At this sampling frequency, and the subcarrier spacing is 312.5 kHz (fs/64), which is a value often chosen for OFDM UAVs links with low data rates. This choice reproduces a compact OFDM scheme, which is commonly used in low-speed UAV systems, where the useful width (5 MHz) can be achieved by sub-carrier in-band filtering while maintaining the standard SDR sampling rate. Recent work on UAV links such as [
21] confirms the use of a comparable bandwidth for the OFDM/SC-FDM physical layer. In addition, several technical studies, such as [
22], confirm that a sampling rate of 20 mega-samples per second (MS/s) is an important parameter when modeling or mapping an OFDM link in UAVs.
Each frame (
) is followed by a silence of equal duration. Then, the reactive jammer is launched with variable parameters as follows:
The interval
covers the full spectrum of hazards, from stealth interference (−40 dB below the signal) to near handheld 10 W interference (+40 dB) at the receiver). The ranges suggested are of the same order of magnitude as those found by reactive LoraWan jamming tests used in [
23].
The frequency offset also ranges from 0 (full channel) to 500 kHz (≈13 subcarriers), allowing testing of both full channel jamming and off-tone attacks with no observations or partial offset. In [
24], the authors showed that such a spacing is sufficient to seriously degrade OFDM synchronization.
The initial phase of the jammer, noted
, is modeled as a uniform random variable to represent the lack of synchronization, both at the carrier and symbol clock, between the jammer and the OFDM target link. A reactive jammer starts operation without prior locking of the Phase-Locked Loop (PLL). By scanning the entire domain
, the simulation covers all phase-shift configurations (constructive, destructive, or intermediate), which avoids distortions caused by arbitrary phase alignment and faithfully reproduces real operating conditions in which neither the UAV receiver’s PLL nor the attacker’s PLL can converge within the duration of a single OFDM symbol. This assumption is corroborated by Rahbari in [
25], who demonstrated that a swift reactive jammer can inject interference in less than one OFDM symbol (≈4 μs) after frame detection, leaving no time for a carrier-phase lock.
3.2. The Activation Process Based on the Excess Received Energy
The reactive jammer remains silent as long as no significant radio activity is detected. Its activation is triggered as soon as the RMS energy observed in the current window exceeds the adaptive threshold. ε
k. The hypothesis test is written as follows:
For frame
k, we use
where
is the current analysis window, and
is the preceding silence segment.
is the sample;
A and
B delimit the current window. Therein, we also define the following:
L: Integer length (in samples) of the silence segment used to estimate the noise variance.
m: Sample index that ranges over the silence segment , i.e., .
n: Sample index that ranges over the analysis window , i.e., .
We determine the maximum probability of a false alarm
, and the noise variance is estimated in situ
on the silence section in front of the useful frame as follows:
The resulting threshold, calculated according to the Neyman–Pearson criterion, is
The settles the ratio sensibility/false positives. With samples, the duration of an OFDM frame is μs. of ensures that, on average, less than one parasitic activation occurs every ms, which is a false-alarm frequency well below RF reconfiguration times. The , derived from the Neyman–Pearson criterion, ensures an optimal compromise between sensitivity and false alarms. It limits spurious activations to a frequency well below RF reconfiguration delays, guaranteeing practical robustness.
Then, the reactive jammer switches to the
ON state during the current sub-frame. A fixed delay is injected to reproduce hardware response latency (RF detection, as well as decision and switching times).
where is the FFT size;
is the cyclic prefix;
is the delay (in samples) before jammer transmission.
Experiments with SDR devices show that there is often a material delay of 12–16 μs between the detection of radioactivity by the receiver and the first noise emission by the transmitter. Shin, in his study [
26], reported a typical response time of 15 μs to Universal Software Radio Peripheral (USRP)-B210/N210 for an 802.11 n Wi-Fi jammer, while Wilhelm in [
20] measured an initialization time of about 15 μs on the field-programmable gate array (FPGA) and the USRP-N210 after the decision.
Using 20 MS/s, an OFDM symbol (, and ) lasted 4 µs. Therefore, = 320 samples corresponds to 16 µs at 20 MS/s, which reflects the latencies measured on SDR platforms (12–16 µs on USRP-B210/N210). This choice is theoretically based on the OFDM symbol duration (4 µs) and corresponds to four symbols. With this configuration, the simulation becomes more destructive, as it avoids preambles and targets the payload directly.
From a functional point of view, several studies recommend a deliberate offset of three to four symbols to avoid jamming the preamble. This leaves the victim station to complete its synchronization, after which it destroys only the payload, which is a scenario considered by authors in [
19] to be the most difficult to detect.
Then, the jamming is effectively injected into the sampling window, whose limits are noted (js, je) as follows:
where 3.3. Analytical Form of the Jamming Signal
During activation, the reactive jammer emits a complex white noise defined as follows:
3.4. Signal Received with Jamming
The merged signal at the detector input is
Explicitly, it is defined as
3.5. Feature Extraction
The method adopted for reactive jamming detection is based firstly on splitting the received signal into small sample windows. Then, for each window, two parameters are calculated: the energy and fractal dimension. These two features are estimated directly in the time domain on sliding windows. This method avoids any recourse to FFT, which reduces complexity to
and guarantees real-time implementation on a digital signal processor (DSP) or low-power microcontroller, such as the case in [
27], where twelve features have been extracted from the time domain of the received signal in order to reduce processing and calculation complexity.
Detecting reactive jamming in UAVs RF links requires descriptors capable of capturing both energy bursts and structural irregularity in the interfered signal, which are two dynamics already exploited in frequency hopping systems for interference recognition, as reported by the authors of the published study [
28]. According to a contribution done by Zeng in [
29], RMS energy is the basic non-coherent indicator for detecting the presence of a signal, since it only requires knowledge or estimation of the noise power. Furthermore, published work [
30] by Cortés-Leal points out that, in practice, energy-related metrics such as RSSI and node energy consumption vary in characteristic ways under attack and serve as reliable symptoms for operational detectors. Concerning complexity measurement, Sevcik proposed the fractal dimension (SFD) which, as recalled in [
31], normalizes the signal into the unit square and estimates its curve length, making it a fast and inexpensive estimator. More broadly, the authors in [
32] show that the fractal dimension applied to waveforms is a powerful tool for the detection of transients, with an accuracy/robustness trade-off depending on the algorithm chosen, which motivates its use as a feature sensitive to fast interference-induced disturbances. Finally, comparative studies published by authors in [
33] demonstrate that SFD efficiently discriminates modulated signals while displaying the shortest execution time among several fractal dimension variants, thus reinforcing its relevance for embedded implementations. In sum, RMS energy ensures sensitivity to the power increases expected during reactive jamming, SFD captures the increase in pattern irregularity, and their combination, validated by the literature, remains an ambitious choice for reactive jamming detection in UAVs.
3.5.1. Sliding Windowing
The signal received
is segmented using a rectangular window
samples, which is shifted by
samples. This length corresponds to 51.2 µs at 20 MS/s, which is a compromise that is long enough to reduce the variance of the estimators but short enough to detect brief bursts, giving the following:
where 3.5.2. Local Energy
For each window, signal intensity is quantified using the root mean square (RMS) and then converted into decibels as follows:
with
and
being regularization terms to avoid
, which corresponds to the IEEE-754 double-precision floor scale. This metric captures the power surges introduced by the reactive jammer, even for moderate signal-to-jammer ratios (SJRs).
3.5.3. Fractal Dimension
Sevcik’s fractal dimension is used to estimate the geometric complexity of the signal. is calculated from standardized envelopes.
where the cumulative length
of the normalized curve is
The temporal roughness is strongly affected and increased by the injection of high-power additive Gaussian noise. rises above the median computed over the quiet intervals, highlighting a second discrimination criterion orthogonal to the energy.
3.6. Decision Making Using Mahalanobis Distance
Detecting reactive jamming introduced into traffic requires adaptive thresholds that can cope with rapid channel fluctuations and changes in background noise depending on environmental conditions. In [
34], they demonstrated that thresholds based on fixed limits quickly become obsolete as SNR or AWGN changes. This part proposes adaptive thresholds based on local OFDM frame statistics, which are complemented by multiscale analysis to reduce the detection delay.
After extraction, each window is represented b the vector
where
is the local energy defined in Equation (
10), and
is the fractal dimension defined in Equation (
11). The objective of this part is that the algorithm should be able to differentiate between jammed windows and normal windows.
For each frame
t, the reference set
is computed from the windows belonging to the silence interval post-OFDM. The mean and covariance are then predicted as follows:
where
The addition of the term
corresponds to a Tikhonov-type regularization, commonly used to stabilize the inversion of covariance matrices estimated from a limited number of samples. This patch prevents numerical degeneration when
is small, guaranteeing the definite positivity of
. This is standard practice in statistical signal processing and machine learning, where it ensures the robustness of Mahalanobis distance estimators in the face of singularity.
For each window in the frame, the Mahalanobis distance is calculated, as shown in [
35], as follows:
Under the null hypothesis
(no jamming), the test statistic
still follows a
law when the background noise is strictly Gaussian. Rather than relying on a fixed theoretical quantile, we re-estimate the decision threshold
frame-by-frame from the most recent silent windows
as follows:
where
denotes the empirical
quantile of the set of silent-window distances within frame
t. This adaptive rule guarantees a constant false-alarm probability, even under slow noise or channel drifts.
We keep
for long windows (
,
) and short windows (
,
), respectively. The choice of
and
is the result of a compromise between the speed of detection and the control of the false-alarm rate. On the long scale, a more permissive value (
) preserves the sensitivity in the presence of slow noise and channel drifts, while on the short scale, a stricter threshold (
) limits the inflation of false positives induced by the higher variance of estimators over reduced windows. This differentiation of
levels is in line with the principles of multi-scale CFAR described in the literature on adaptive detection by the authors in [
36]. Then, the binary decision becomes the following:
3.7. Multi-Scale Fusion
Two independent Mahalanobis detectors operate in parallel:
where the adaptive thresholds
and
are the
quantiles of the silent-window distances at the long and short scales (see Equation (
16)).
The short-scale decisions
are re-sampled onto the long window grid and then combined by logical disjunction as follows:
This logical OR fusion preserves the target false-alarm probabilities for both time scales while capturing jamming events ranging from very brief spikes to bursts lasting several seconds.
Because
and
are updated only once per frame (Equations (
13) and (
14)), each window requires just two scalar multiplications and one comparison. The resulting workload is compatible with real-time execution on low-power DSPs or microcontrollers.
The authors in [
37] demonstrated that updating key metrics in a single frame has been shown to keep CPU, memory, and power budgets very low, making it compatible with real-time execution on modest onboard systems.
A fixed threshold, even if theoretically matched to the law, presumes that the background noise, the receiver-front gain and the propagation channel remain stationary. In practice, every RF chain exhibits gain drift (temperature, aging), every channel undergoes quasi-lognormal slow fading, and the additive noise floor varies with adjacent-band interference. A fixed therefore slides, in real units, away from the optimal decision surface: too low of a value inflates the false-alarm rate, whereas too high of a value blinds the detector to weak or short jamming attempts. By contrast, the adaptive thresholds and are re-anchored at every frame on the empirical distribution of genuinely silent windows. This re-centering guarantees that the test statistic always lies on the same probabilistic scale, whatever the instantaneous SNR.
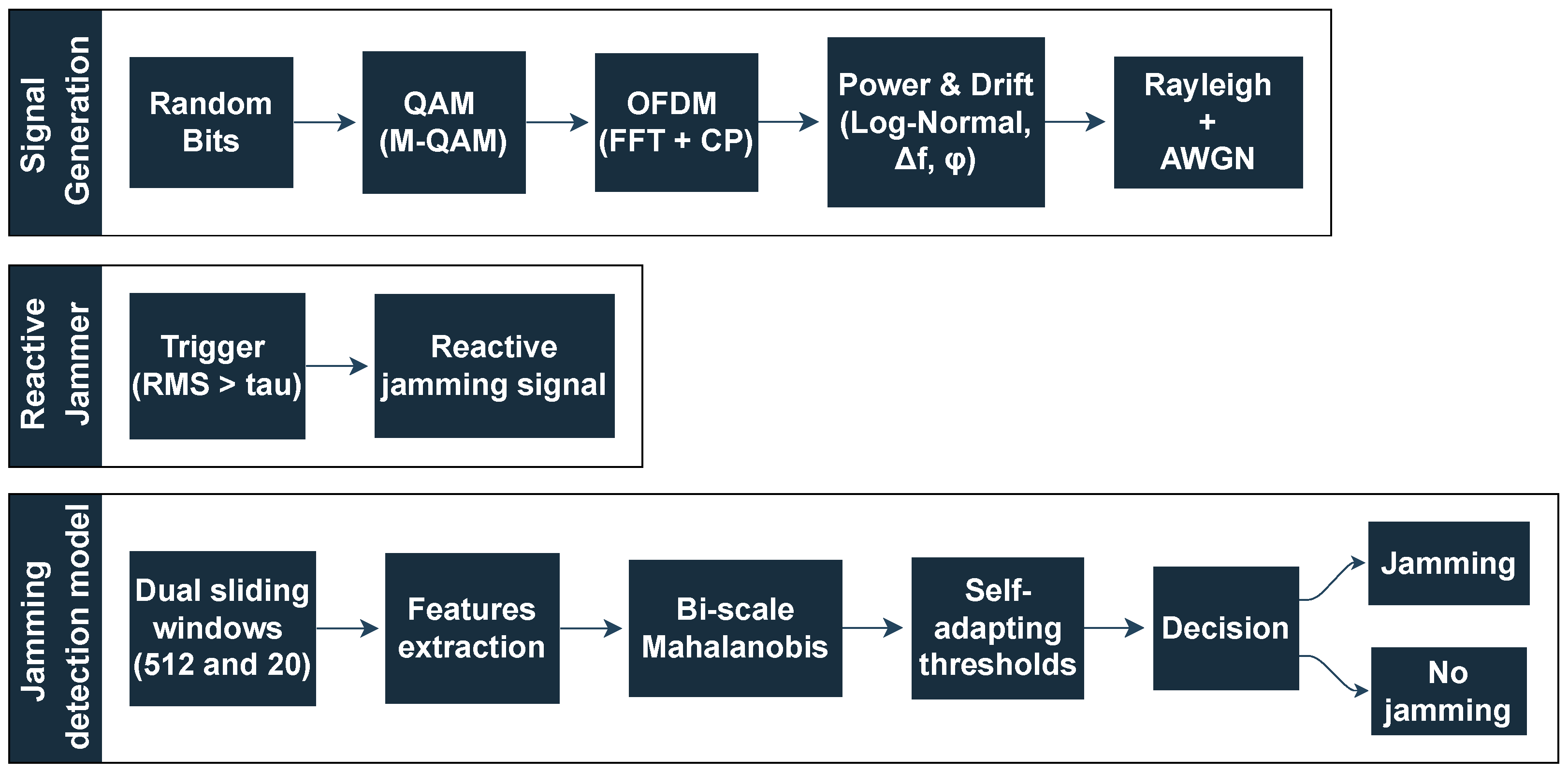
The pipeline in
Figure 1 summarizes the end-to-end reactive jamming detection from the OFDM transmission signal modeling, going through the reactive interference triggering and ending with the implemented detection process.
3.8. Simulation Framework and TX/RX/Jammer Setup
The simulation setup shown below is described in detail in order to ensure clarity and reproducibility.
Consider a transmission frame indexed by k. The emitted power is modeled with its logarithmic expression used for generation. The useful signal is carried by a set of orthogonal subcarriers, and then symbols are mapped and assembled into an OFDM frame. Two multiplicative impairments are applied per frame—a carrier-frequency offset and a phase rotation —which are both drawn from bounded ranges. The useful frame is followed by a deterministic silent interval so that a repeating useful + silence structure spans the entire sequence.
The received signal results from propagation over a time-selective channel modeled as a two-path Rayleigh channel [0, 1, 2 μs] with average earnings [0, −6] dB and maximum Doppler of 10 Hz, followed by AWGN noise at 10 dB measured SNR.
The reactive scrambler makes a frame-by-frame decision via a CFAR energy test applied to the received signal before injection, local noise variance is estimated on the segment of silence immediately preceding the frame, and then a Neyman–Pearson threshold is determined as .
Afterwards, the reactive jammer is triggered if . To model realistic hardware latency (detection decision RF switching chain), injection starts after a fixed delay samples, i.e., 16 μs, and continues until the end of the frame, producing a jamming burst of 144 μs.
The jamming amplitude is drawn frame by frame according to the law ∼, while the useful signal undergoes independent frequency and phase shifts per frame (∼, ∼).
Two analysis scales are used: a long scale with parameters
and a short scale with parameters
. For each temporal window
w, a two-dimensional feature vector is extracted, consisting of the logarithmic energy
where
is a small regularization constant, and the Sevcik fractal dimension is computed on the signal magnitude
. Window-level labels are obtained by aggregating the ground truth at the window scale (for example, any jamming present within the window implies label 1), thus providing inputs for subsequent two-scale detection stages.
3.9. Channel Model Configuration
The channel introduces small-scale fading, noise, and carrier impairments.
The propagation environment is modeled as a multipath Rayleigh block-fading channel. It consists of a finite set of propagation paths, with each characterized by a specific delay and average gain. The channel is assumed to remain constant during the duration of a frame and to vary independently between frames. A maximum Doppler shift parameter controls the temporal correlation of the fading process, capturing the effect of mobility or oscillator instabilities.
The received signal is further corrupted by additive white Gaussian noise (AWGN). The noise is characterized by a measured signal-to-noise ratio, which determines the variance of the Gaussian distribution added to the received samples. This noise component models thermal and electronic disturbances in the receiver chain.
In addition to fading and noise, carrier impairments are applied at the transmitter side. These include a frequency offset, denoted , and a phase offset, denoted as . Both quantities are modeled as random variables drawn from bounded ranges, to emulate practical imperfections such as oscillator mismatch or residual synchronization errors.
3.10. Adaptive Mahalanobis Detector
The detection algorithm exploits features extracted at two time scales (long and short windows). For each scale, the features are arranged into vectors containing the logarithmic energy and the fractal dimension. Detection is based on the squared Mahalanobis distance, which compares each feature vector
x against a statistical model estimated from silent windows as follows:
where
is the mean vector, and
C is the covariance matrix of features computed over silence-only windows. A constant false-alarm rate (CFAR) is achieved by adapting thresholds per frame.
Additional constraints are imposed for robustness:
A minimum number of silence windows must be available to compute and C.
Guard windows adjacent to potential transitions are excluded.
If silence statistics are insufficient, the test falls back to a fixed threshold.
If these conditions are not satisfied, the threshold falls back to the quantile of a distribution with two degrees of freedom. The final frame-level decision results from the logical fusion of long- and short-window detectors.
The following Algorithm 1 summarizes the complete functioning of the two-scale Mahalanobis detector.
| Algorithm 1 Two-scale detection |
- 1:
Initialize: (frame+silence), ; , - 2:
Global noise.
- 3:
Per-frame noise & CFAR: for k: ; if then ; - 4:
Reactive jamming: if then inject j on last ; set there - 5:
Compose:
- 6:
Windows & features: build ; ; - 7:
Select per frame/scale: ; ; if then ; trim - 8:
Silence stats: ; - 9:
Mahalanobis Distance: for : - 10:
Threshold & decision: ; if undefined then ; - 11:
Fuse: ;
|
3.11. Simulation Setup
The simulations were executed on a workstation equipped with an Intel Core i9-9880H processor (Intel Corporation, Santa Clara, CA, USA; 8 cores, 16 threads, 2.30 GHz) and 32 GB RAM. The entire framework, including signal generation, feature extraction, and Mahalanobis detection, was implemented in MATLAB R2024a with the Communications Toolbox (The MathWorks, Inc., Natick, MA, USA).
4. Simulations and Results
4.1. Overview of the Evaluation Protocol
To assess the proposed bi-scale Mahalanobis detector, we simulated
OFDM frames corrupted by a reactive jammer over a Rayleigh channel (
Table 1). Two window lengths were adopted (512 samples and 20 samples) to capture both macro- and micro-temporal statistics of the received signals. The energy (
E) and Sevcik’s fractal dimension (
) were extracted from every window and fed to the detector under
(long) and
(short). A decision was finally taken by the logical OR between the two scales.
4.2. Confusion Matrix and Core Metrics
The detection model creates for each window a confusion matrix, shown in
Figure 2, which summarizes the detection results for the long and short windows. The detector correctly marked each jamming window with a of recall = 100%. On the other hand, 370 quiet windows were misclassified as jammed (FP/TN = 0.5%), resulting in an accuracy of 99.4% and an F1 score of 99.7%. All results are summarized in
Table 2.
The detection model produces, for each analysis window (long and short), a confusion matrix, as shown in
Figure 2, summarizing the classification of jamming versus quiet intervals. Each window is labeled as either Jam (positive class) or Quiet (negative class). Let
denote true positives (jammed windows correctly detected),
denote false negatives (jammed windows missed),
denote false positives (quiet windows spuriously flagged), and
denote true negatives (quiet windows correctly rejected). In this simulation, all jammed windows were correctly detected so that
, and thus, the window-level recall attained
. Conversely,
quiet windows were misclassified as jammed.
Given the reported internal ratio
, we infer
. This yields an overall accuracy of 99.7% and a harmonic mean
under the stated performance summary. All aggregated results are listed in
Table 2.
The four cells furnish the sufficient statistics for all standard classification metrics.
Precision quantifies the reliability of positive detections:
A high precision indicates a low false-alarm burden on mitigation resources.
Recall captures completeness of detection:
With
, the detector achieves perfect sensitivity, ensuring no jamming window escapes detection.
The overall correctness is measured by
blending performance on both positive and negative classes. When the accuracy is high, it can mask class imbalance; hence, complementary metrics remain essential.
The
score is the harmonic mean balancing precision and recall:
Because the recall is perfect,
is chiefly governed by precision.
The false positive rate (FPR) is
which with
gives
(0.5%). The specificity (true negative rate) is
The absence of false negatives prioritizes operational safety (no missed jamming events). Any remaining improvement leverage lies mainly in reducing to minimize unnecessary countermeasure activations and downstream processing load. Once definitive values and total window counts are finalized, a consistency check should be performed to verify that the triplet numerically aligns with the raw confusion counts.
For every jam onset, the first positive decision occurred, on average,
after the actual jamming start, with only four OFDM symbols at the current sampling frequency. This microsecond responsiveness plainly outperformed the millisecond-level latency reported in recent works that rely on machine learning models [
28], yet it remains to be verified on hardware simulation; convenience must not be mistaken for real-time guarantee.
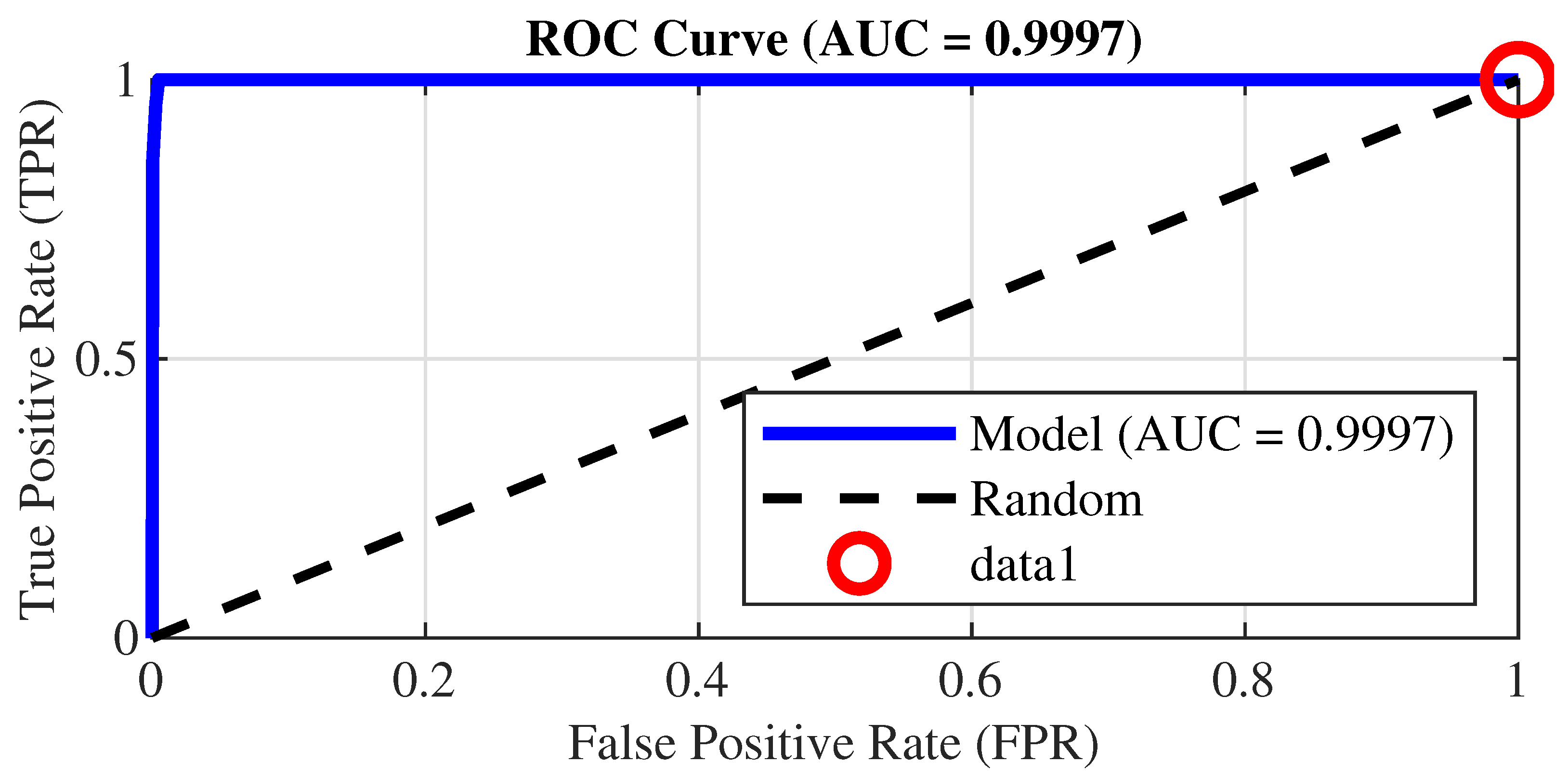
4.3. ROC Curve
Figure 3 shows the detector’s ROC curve rising almost vertically from
to the upper left-hand corner, where it then remained on the ceiling with a rate of true positives
across the entire width. This pattern reveals a near-perfect discrimination capability, which is corroborated by the area under the curve
. In concrete terms, if we select at random one
jamming window and one
silence window, the detector ranks them correctly (
) in 99.97% of cases. Accordingly, the area under the ROC curve is
, which is well above the chance level (
).
Given the total number of windows tested (
), the standard error associated with AUC estimate is
which places the confidence interval at
in
. The probability of the model’s AUC falling below 0.99 is therefore statistically negligible.
4.4. Robustness to Jammer Power
The scatter plot in
Figure 4 shows, for all 5000 frames simulated, the instantaneous power of the jammer
(x axis, dB scale) and the average Mahalanobis distance
calculated over the long and short windows of the bi-scale detector (ordinate axis, linear scale). The almost exponential growth of
between
dB and
dB confirms the sensitivity of the model as soon as jamming exceeds the background noise by approximately 10 dB. The peak observed around
dB corresponds exactly to the time when SJR ratio remains sufficiently balanced to maximize the statistical divergence without inducing
clipping on the communication channel. When
is above 0 dB, the slight decrease in
reflects intra-frame normalization, which means the situation when the jammer becomes dominant, but the overall variance remains controlled, avoiding detector saturation. This non-monotonic response also validates bi-scale dimensioning; it guarantees recall rate of 100% and a precision of 99.4% while preserving a margin against false positives when jamming reaches extreme powers.
4.5. Adaptive Thresholds Dynamics
Figure 5 plots only the first 500 frames so that the frame-to-frame fluctuations can be seen clearly on a single axis. The long-window threshold,
(red), remains in the range between 2 and 6 because it was computed from windows of 512 samples, whose statistics evolve slowly. The short-window threshold,
(orange), spans roughly 10 to 30 with only 20 samples per window; it responded much more sharply to any rapid shift in SNR or noise floor. In both traces, rises correspond to fading or interference peaks, whereas drops mark calmer channel conditions—demonstrating that the quantile update accurately tracks the real-time spread of Mahalanobis distances.
These visible swings underline the weakness of a single, fixed decision level. A constant threshold low enough to capture weak bursts during quiet periods would overshoot the target false-alarm rate whenever the noise increases. Conversely, a level high enough to withstand noisy episodes would miss low-power jamming once the channel quiets down. By recalibrating from silent windows at every frame, the adaptive method keeps the false-alarm probability under control and retains sensitivity across the full spectrum of real-world channel and noise variations without manual re-tuning.
4.6. CPU Time Consumption
To substantiate the claim of low CPU intensity, instrumentation of the CPU time per frame was added to the simulation loop.
Figure 6 plots, for 500 consecutive frames, the processing time per frame of the proposed detector, with a horizontal line serving as an average CPU time budget.
The curve shows minimal CPU consumption for the most part; the time per frame is closely clustered around the global mean 6.875 ms, with a low, steady trend. This plan reflects the low intrinsic cost of the proposed pipeline and constant complexity per window, without trained models. As it stands, the average value and the cloud density around this average indicate a load compatible with real-time execution on embedded targets.
Visible point elevations were rare among the 500 frames and did not alter the nominal regime, with most frames remaining in the immediate vicinity of the mean. The distribution appears asymmetrically right-tailed, which is typical of a light algorithmic core occasionally disturbed by non-recurrent operations. In practice, the cloud’s median and concentration support the idea that the sustained cost is low, with the rare peaks having a negligible cyclical duty.
Deep learning approaches (e.g., convolutional neural networks) have achieved high jamming detection accuracy, especially using spectrogram or IQ-sample representations, but often at the expense of higher computational burden. Li et al., in [
4], developed a spectrogram-based CNN classifier to detect jamming against OFDM receivers on UAVs. The study reported an outstanding accuracy 99.8% detection and 0.03% false alarm with deep CNNs, but a trade-off in processing cost was noted. The training and testing times for the CNN models were significantly higher than those obtained by the conventional ML algorithms, which is attributed to the CNNs’ deep and complex architectures.
In other words, the CNN-based approach required far more computation to achieve its accuracy. For instance, their best CNN (EfficientNet-B0) took on average 0.005 s per frame with a GPU and 0.066 s per frame on a CPU (i.e., 66 ms per OFDM frame) for inference, which is more than 9.6 times higher than the average CPU time observed for the bi-scale Mahalanobis detector. This implies that without GPU acceleration, a deep model might only process 15 frames per second on a CPU, indicating a substantial computational load. Such heavy models involve millions of parameters and numerous matrix operations per evaluation, contributing to high CPU usage.
In positioning the propsed method against the literature, it aligns with the push for “lightweight yet efficient” reactive jamming detection in IoT/UAV networks explained by Alia in [
38]. Unlike deep learning solutions that demand substantial computational resources and hindering scalability in distributed networks, a lightweight statistical detector imposes minimal CPU and energy burden. Thus, the proposed approach can be presented as a lower-cost alternative that sacrifices some complexity in exchange for speed, accuracy, simplicity, and ease of deployment on resource-limited platforms. This is supported by evidence from prior work [
39], such as simple metric-based detectors that have been successfully used to catch jamming with negligible overhead. By operating in the time domain and using an adaptive threshold, the method is also well suited to reactive jamming, which often manifests as subtle changes in the timing or variance of signals. Time-domain anomaly detection can catch the transient interference bursts of reactive jammers quickly, without needing intensive spectral analysis.
4.7. Complexity Analysis
Per-window operation counts are reported for feature extraction (local energy and Sevcik fractal dimension ) and for the frame-level adaptive Mahalanobis decision. Additive operations include both additions and subtractions; divisions, square roots, and logarithms are itemized separately.
4.7.1. Energy on a Window of Length w
Using
with
gives
4.7.2. Sevcik on a Window of Length w
With normalization
and
, then
, and we have
4.7.3. Mahalanobis Distance per Window (Given and )
For feature vector
,
, and
,
The per-frame overhead to estimate
and
C on
s silence windows is linear in
s:
plus a constant-cost
matrix inversion. The adaptive threshold is computed by a quantile of the silent
values (sorting
), with fixed windowing
s bounded per frame; hence, the amortized cost is constant. If desired, the
fallback (
df = 2) yields
per frame.
Let
N be the number of samples. The number of windows at hop
h is
. Since each window incurs a constant number of primitive operations (independent of
N), the total cost scales linearly as
4.7.4. Numerical Counts with Simulation Parameters
For the long windows
and short windows
, we find the following:
| Per Window | Mult | Adds | Divs | Sqrt | Log | Comps |
| Energy () | | 1024 | 1 | 1 | 1 | 0 |
| Sevcik FD () | 511 | 1534 | 513 | 511 | 1 | 1024 |
| Mahalanobis | 6 | 5 | 0 | 0 | 0 | 1 |
| Energy () | | 40 | 1 | 1 | 1 | 0 |
| Sevcik FD () | 19 | 58 | 21 | 19 | 1 | 40 |
With hops , the window counts scale as and , so the aggregate complexity remains linear in N and avoids any term inherent to FFT-based features. This supports real-time feasibility on lightweight embedded UAVs hardware.
5. Quantitative Comparison with State-of-the-Art Methods
In order to reinforce the validity of the proposed contribution, a quantitative comparison with representative reactive jamming detection algorithms from the last decade was conducted. The objective of this section is to position the bi-scale Mahalanobis detector with respect to existing state-of-the-art methods by considering the most relevant performance indicators, namely, the precision, recall, detection latency, and computational requirements.
Several recent proposals illustrate the diversity of approaches in this domain. The “JamShield system” developed by the authors in [
40] exemplifies a dynamic machine-learning based approach capable of online adaptation. When evaluated with real 802.11 traffic, it reported a 88.5% precision and 90.3% recall, with a detection rate of 97.9% and a false-alarm rate of approximately 3.9%. Although robust in realistic conditions, its precision values remain below those of the bi-scale Mahalanobis detector, which consistently exceeds 99%. Nevertheless, JamShield demonstrates the importance of online adaptability and minimal misdetection rates.
Another recent study introduced a lightweight XGBoost-based detector implemented on an STM32H7 microcontroller used by the authors in [
41]. This model employed a reduced set of time-frequency features and achieved 96% precision and 93% recall, with an overall accuracy of 98%. A notable strength of this method was its ultra-low decision latency of 20 μs, which is faster than the 80 μs latency measured for the proposed detector. However, the slight reduction in precision highlights a trade-off between speed and accuracy. The hardware requirements of the XGBoost approach were minimal, making it suitable for embedded deployment.
Deep learning solutions have also been introduced, such as the dual-threshold DNN with wavelet preprocessing designed for 5G New Radio signals. This approach shown by the authors in [
42] achieved 94% precision and 97% recall, corresponding to an AUC greater than 0.95. Despite the strong classification performance, this method required substantial training effort, initially more than 40 h—later reduced to 144 min—and powerful computational platforms. Such requirements significantly limit deployment on lightweight or embedded hardware, whereas the bi-scale Mahalanobis detector executes distance calculations in microseconds without any training overhead.
Complementary efforts can be found in cluster-based detection schemes for wireless sensor networks (WSNs). Ganeshkumar et al. [
43] reported a detection rate of 99.88% in simulation, indicating near-perfect recall. However, no details on latency or hardware feasibility were provided, which limits the relevance of this approach for real-world deployments.
More recently, collaborative detection algorithms (CDRA) for IoT networks have been proposed by Ashraf and Sagheer [
38]. Their method emphasized efficiency rather than raw accuracy, reporting a 17% reduction in energy consumption and a 10% reduction in detection delay compared to prior models. While promising for resource-constrained environments, precision and recall metrics were not explicitly reported, leaving uncertainty regarding detection reliability. In contrast, the bi-scale Mahalanobis detector achieves both high accuracy and computational efficiency.
Overall, the comparative analysis highlights that the bi-scale Mahalanobis detector achieves performance that is at least competitive with, and often superior to, state-of-the-art alternatives. With a precision of approximately 99.4%, recall at similarly high levels, and latency in the order of tens of microseconds, the proposed method demonstrates a favorable balance between accuracy, speed, and simplicity. Unlike deep learning models, it does not incur significant training or hardware costs, and unlike cooperative schemes, it does not require inter-node coordination. These characteristics make the bi-scale Mahalanobis detector highly suitable for real-time applications in resource-constrained platforms such as IoT nodes or embedded devices. A side-by-side tabular comparison of the most representative approaches and their reported metrics is shown below in
Table 3.
5.1. Analytical Baseline: Energy-Only CFAR
To provide a comparator evaluated under identical conditions without relying on external implementations, an analytical baseline was included: a constant false-alarm-rate (EO–CFAR) energy detector applied to the same analysis windows, dataset, and MATLAB configuration as the proposed detector. For each frame, silent windows were used to estimate the reference distribution of the short-window energy . The ON/OFF thresholds were derived from the empirical quantile of the silent-window distribution, and decisions were produced as .
EO–CFAR and the proposed bi-scale Mahalanobis (BM) detector were executed on the same set of 5000 OFDM frames and jamming scenarios. Operating points were aligned by matching the global false-positive rate (FPR) across methods. The following metrics were reported: precision, recall, F1 score, area under the ROC curve (AUC), and mean decision latency per frame. Receiver operating characteristic (ROC) and precision–recall (PR) curves were generated. Uncertainty was quantified using 95% confidence intervals estimated via bootstrap over frames (1000 resamples).
Findings
Under the evaluation protocol of
Section 5.1, the EO–CFAR baseline achieved as shown in
Table 4:
78.4% precision,
98.6% recall,
87.1% F
1, and an AUC of
0.774, with a mean decision latency of
68 μs. By contrast, the proposed bi-scale Mahalanobis (BM) detector reached
99.4% precision,
100% recall,
99.7% F
1, and a
0.9997 AUC at
80 μs. Relative to EO–CFAR, BM improved the precision by
+21.0 percentage points and F
1 by
+12.6 points, while increasing the recall by
+1.4 points and incurring only a
12 μs latency overhead. The low AUC of EO–CFAR indicates limited score separability between jammed and clean windows when using energy alone, which is consistent with susceptibility to transient energy micro-peaks, fading fluctuations, and baseline drift. The BM formulation, combining bi-scale features with adaptive hysteresis, short-term persistence, and drift veto, suppresses isolated positives and yields near-perfect separability without a material latency penalty.
7. Future Work
Future work will therefore (i) port the algorithm to a 168 MHz Cortex-M4 autopilot and a low-cost FPGA to obtain measured latency–throughput–power trade-offs; (ii) extend Monte Carlo trials to negative JSR scenarios and real over-the-air captures; and (iii) integrate the detector with evasive counter-measures such as adaptive waveform hopping to quantify end-to-end link survival probability.
To further increase accuracy beyond 99.4%, it is proposed to add a light decision layer above the Mahalanobis bi-scale detector. This layer is designed to suppress isolated false alarms due to energy micro-peaks to transient shifts in background noise, all while retaining microsecond latency and ease of implementation on embedded hardware. The whole system will remain analytical, with no learning curve and a constant cost per window.
The principle is based on four complementary mechanisms. Firstly, scale-adaptive hysteresis, based on local quantiles, avoids “floating” decisions. Secondly, a coherence gate requires that the local energy and the fractal dimension rise together, thus eliminating energetic bursts. A short time persistence will only validate an alarm if several recent windows converge, filtering out orphaned positives. Finally, a CFAR drift veto will momentarily suspend the decision when the baseline changes abruptly, while silent statistics are re-estimated.
Integration will take place in the post-processing of long- and short-range decisions by replacing the raw OR with an OR conditioned by these tests. The evaluation will report the gain in precision, the impact on recall and latency stability, as well as an ablation isolating the contribution of each mechanism.
The pseudo code that follows Algorithm 2 summarizes the precision-boosting post-processor described above and will be the subject of future work. It builds the design by establishing a frame-adaptive reference for constant false-alarm control, gating detections on the joint rise of energy and fractal complexity, enforcing adaptive hysteresis at both time scales to prevent chatter, applying a short temporal-persistence rule to suppress isolated positives, and introducing a drift veto that withholds decisions during rapid baseline shifts. The final decision arises from a gated fusion of the long and short scales.
| Algorithm 2 Precision-boosted |
bi-scale Mahalanobis (PB-BM) Require: Windowed signal, per-window features (local energy) and (local Sevcik fractal dimension, FD), per-scale Mahalanobis distances and computed from the feature vector against the frame-level reference distribution esti- mated from silent windows. Ensure: Final binary decision for each analysis window w
- 1:
Frame-level CFAR setup (constant false-alarm rate): using silent windows (segments without useful signal) in the current frame, estimate the reference mean and covariance of the feature vectors. Then, for each time scale, compute adaptive quantiles of the silent-window distance distribution and define an ON threshold and an OFF threshold with . - 2:
for each window w do - 3:
Feature-coherence gate: standardize and using frame-local means and standard deviations. Set if both standardized scores are simultaneously elevated relative to their baselines, otherwise . - 4:
for each scale do - 5:
Adaptive hysteresis state : - 6:
if and and then - 7:
▹ activation when distance exceeds ON threshold and features are coherent - 8:
else if and then - 9:
▹ deactivation when distance falls below OFF threshold - 10:
else - 11:
- 12:
end if - 13:
Short temporal persistence: define the persistent decision to be True only if at least K states are True within the most recent M windows (the K-of-M rule), otherwise set . K is the required count and M is the persistence window length. - 14:
end for - 15:
CFAR drift veto: if the median energy of silent windows has shifted by more than a drift threshold over a recent horizon of S frames, refresh the frame-level reference (mean, covariance and quantiles) and set for the current window, otherwise set . controls the sensitivity to baseline changes and S is the drift-checking horizon. - 16:
Fusion: produce the gated OR of the two scales, - 17:
end for
|