-
 Anomaly Detection Against Fake Base Station Threats Using Machine Learning
Anomaly Detection Against Fake Base Station Threats Using Machine Learning -
 A Lightweight Multimodal Framework for Misleading News Classification Using Linguistic and Behavioral Biometrics
A Lightweight Multimodal Framework for Misleading News Classification Using Linguistic and Behavioral Biometrics -
 The Erosion of Cybersecurity Zero-Trust Principles Through Generative AI: A Survey on the Challenges and Future Directions
The Erosion of Cybersecurity Zero-Trust Principles Through Generative AI: A Survey on the Challenges and Future Directions -
 Perceiving Digital Threats and Artificial Intelligence: A Psychometric Approach to Cyber Risk
Perceiving Digital Threats and Artificial Intelligence: A Psychometric Approach to Cyber Risk
Journal Description
Journal of Cybersecurity and Privacy
Journal of Cybersecurity and Privacy
is an international, peer-reviewed, open access journal on all aspects of computer, systems, and information security, published bimonthly online by MDPI.
- Open Access— free for readers, with article processing charges (APC) paid by authors or their institutions.
- High Visibility: indexed within ESCI (Web of Science), Scopus, EBSCO, and other databases.
- Rapid Publication: manuscripts are peer-reviewed and a first decision is provided to authors approximately 21.5 days after submission; acceptance to publication is undertaken in 4.8 days (median values for papers published in this journal in the second half of 2025).
- Journal Rank: CiteScore - Q1 (Computer Science (miscellaneous))
- Recognition of Reviewers: APC discount vouchers, optional signed peer review, and reviewer names published annually in the journal.
- Journal Cluster of Information Systems and Technology: Analytics, Applied System Innovation, Cryptography, Data, Digital, Informatics, Information, Journal of Cybersecurity and Privacy and Multimedia.
Latest Articles
Secure Local Communication Between Browser Clients and Resource-Constrained Embedded IoT Devices
J. Cybersecur. Priv. 2026, 6(1), 9; https://doi.org/10.3390/jcp6010009 (registering DOI) - 1 Jan 2026
Abstract
This contribution outlines a completely new, fully local approach for secure web-based device control on the basis of browser inter-window messaging. Modern smart home IoT (Internet of Things) devices are commonly controlled with proprietary mobile applications via remote servers, which can have significant
[...] Read more.
This contribution outlines a completely new, fully local approach for secure web-based device control on the basis of browser inter-window messaging. Modern smart home IoT (Internet of Things) devices are commonly controlled with proprietary mobile applications via remote servers, which can have significant adverse implications for the end user. Given that many IoT devices in use today are limited in both available memory and processing speed, standard approaches such as HTTPS-based transport security are not always feasible and a need for more suitable alternatives for such constrained devices arises. The proposed local method for lightweight and secure web-based device control using inter-window messaging leverages existing standard web technologies to enable a maximum degree of privacy, choice, and sustainability within the smart home ecosystem. The implemented proof-of-concept shows that it is feasible to meet essential security objectives in a local web IoT control context while utilizing less than a kilobyte of additional memory compared to an unsecured solution, thereby promoting sustainability through hardening of the control protocols used by existing devices with too few resources for implementing standard web cryptography. In this way, the present work contributes to achieving the vision of a fully open and secure local smart home.
Full article
(This article belongs to the Section Security Engineering & Applications)
Open AccessArticle
An In-Depth Measurement of Security and Privacy Risks in the Free Live Sports Streaming Ecosystem
by
Nithiya Muruganandham, Yogesh Sharma and Sina Keshvadi
J. Cybersecur. Priv. 2026, 6(1), 8; https://doi.org/10.3390/jcp6010008 (registering DOI) - 1 Jan 2026
Abstract
Free live sports streaming (FLS) services attract millions of users who, driven by the excitement of live events, often engage with these high-risk platforms. Although these platforms are widely perceived as risky, the specific threats they pose have lacked large-scale empirical analysis. This
[...] Read more.
Free live sports streaming (FLS) services attract millions of users who, driven by the excitement of live events, often engage with these high-risk platforms. Although these platforms are widely perceived as risky, the specific threats they pose have lacked large-scale empirical analysis. This paper addresses this gap through a comprehensive study of the FLS ecosystem, conducted during two major international sporting events (UCL playoffs and NHL Stanley Cup Playoffs, 2024–2025 season). We analyze the infrastructure, security threats, and privacy violations that define this space. Analysis of 260 unique domains uncovers systemic security risks, including drive-by downloads delivering persistent malware, and widespread privacy violations, such as invasive device fingerprinting that disregards regulations like the General Data Protection Regulation (GDPR). Furthermore, we map the ecosystem’s resilient infrastructure, identifying eight clusters of co-owned domains. These findings imply that effective countermeasures must target the centralized infrastructure and ephemeral nature of the FLS ecosystem beyond traditional blocking.
Full article
(This article belongs to the Section Privacy)
►▼
Show Figures
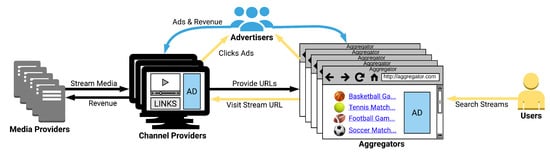
Figure 1
Open AccessCommunication
Engineering Explainable AI Systems for GDPR-Aligned Decision Transparency: A Modular Framework for Continuous Compliance
by
Antonio Goncalves and Anacleto Correia
J. Cybersecur. Priv. 2026, 6(1), 7; https://doi.org/10.3390/jcp6010007 - 30 Dec 2025
Abstract
Explainability is increasingly expected to support not only interpretation, but also accountability, human oversight, and auditability in high-risk Artificial Intelligence (AI) systems. However, in many deployments, explanations are generated as isolated technical reports, remaining weakly connected to decision provenance, governance actions, audit logs,
[...] Read more.
Explainability is increasingly expected to support not only interpretation, but also accountability, human oversight, and auditability in high-risk Artificial Intelligence (AI) systems. However, in many deployments, explanations are generated as isolated technical reports, remaining weakly connected to decision provenance, governance actions, audit logs, and regulatory documentation. This short communication introduces XAI-Compliance-by-Design, a modular engineering framework for explainable artificial intelligence (XAI) systems that routes explainability outputs and related technical traces into structured, audit-ready evidence throughout the AI lifecycle, designed to align with key obligations under the European Union Artificial Intelligence Act (EU AI Act) and the General Data Protection Regulation (GDPR). The framework specifies (i) a modular architecture that separates technical evidence generation from governance consumption through explicit interface points for emitting, storing, and querying evidence, and (ii) a Technical–Regulatory Correspondence Matrix—a mapping table linking regulatory anchors to concrete evidence artefacts and governance triggers. As this communication does not report measured results, it also introduces an Evidence-by-Design evaluation protocol defining measurable indicators, baseline configurations, and required artefacts to enable reproducible empirical validation in future work. Overall, the contribution is a practical blueprint that clarifies what evidence must be produced, where it is generated in the pipeline, and how it supports continuous compliance and auditability efforts without relying on post hoc explanations.
Full article
(This article belongs to the Special Issue Data Protection and Privacy)
►▼
Show Figures

Figure 1
Open AccessReview
A Survey on Acoustic Side-Channel Attacks: An Artificial Intelligence Perspective
by
Benjamin Quattrone and Youakim Badr
J. Cybersecur. Priv. 2026, 6(1), 6; https://doi.org/10.3390/jcp6010006 - 29 Dec 2025
Abstract
Acoustic Side-Channel Attacks (ASCAs) exploit the sound produced by keyboards and other devices to infer sensitive information without breaching software or network defenses. Recent advances in deep learning, large language models, and signal processing have greatly expanded the feasibility and accuracy of these
[...] Read more.
Acoustic Side-Channel Attacks (ASCAs) exploit the sound produced by keyboards and other devices to infer sensitive information without breaching software or network defenses. Recent advances in deep learning, large language models, and signal processing have greatly expanded the feasibility and accuracy of these attacks. To clarify the evolving threat landscape, this survey systematically reviews ASCA research published between January 2020 and February 2025. We categorize modern ASCA methods into three levels of text reconstruction—individual keystrokes, short text (words/phrases), and long-text regeneration— and analyze the signal processing, machine learning, and language-model decoding techniques that enable them. We also evaluate how environmental factors such as microphone placement, ambient noise, and keyboard design influence attack performance, and we examine the challenges of generalizing laboratory-trained models to real-world settings. This survey makes three primary contributions: (1) it provides the first structured taxonomy of ASCAs based on text generation granularity and decoding methodology; (2) it synthesizes cross-study evidence on environmental and hardware factors that fundamentally shape ASCA performance; and (3) it consolidates emerging countermeasures, including Generative Adversarial Network-based noise masking, cryptographic defenses, and environmental mitigation, while identifying open research gaps and future threats posed by voice-enabled IoT and prospective quantum side-channels. Together, these insights underscore the need for interdisciplinary, multi-layered defenses against rapidly advancing ASCA techniques.
Full article
(This article belongs to the Topic Recent Advances in Artificial Intelligence for Security and Security for Artificial Intelligence)
►▼
Show Figures

Figure 1
Open AccessArticle
From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain
by
Robert Kopal, Bojan Alikavazović and Zlatan Morić
J. Cybersecur. Priv. 2026, 6(1), 5; https://doi.org/10.3390/jcp6010005 - 26 Dec 2025
Abstract
The Cyber Kill Chain (CKC) is a prevalent concept in cyber defense; nevertheless, its emphasis on post-reconnaissance phases limits the capacity to foresee attacker activities outside the organizational boundary. This study introduces and empirically substantiates a pre-chain phase, referred to as contextual anticipation,
[...] Read more.
The Cyber Kill Chain (CKC) is a prevalent concept in cyber defense; nevertheless, its emphasis on post-reconnaissance phases limits the capacity to foresee attacker activities outside the organizational boundary. This study introduces and empirically substantiates a pre-chain phase, referred to as contextual anticipation, which broadens the temporal framework of the CKC by methodically identifying subtle yet actionable signals prior to reconnaissance. The methodology combines the STEMPLES+ framework for socio-technical scanning with General Morphological Analysis (GMA), generating internally coherent scenarios that are translated into Indicators of Threats (IOT). These indicators connect contextual triggers to threshold-based monitoring activities and established courses of action, forming a reproducible and auditable relationship between foresight analysis and operational defense. The application of three illustrative cases—a banking merger, the distribution of a phishing kit in underground marketplaces, and wartime contribution scams—illustrated that contextual anticipation consistently provided quantifiable lead-time benefits varying from several days to six weeks. This proactive stance enabled measures such as registrar takedowns, targeted awareness campaigns, and anticipatory monitoring before distribution and exploitation. By formalizing CKC-0 as an integrated socio-technical phase, the research enhances cybersecurity practice by demonstrating how diffuse contextual drivers can be converted into organized, actionable mechanisms for proactive resilience.
Full article
(This article belongs to the Section Security Engineering & Applications)
►▼
Show Figures

Figure 1
Open AccessArticle
Homomorphic Encryption for Confidential Statistical Computation: Feasibility and Challenges
by
Yesem Kurt Peker and Rahul Raj
J. Cybersecur. Priv. 2026, 6(1), 4; https://doi.org/10.3390/jcp6010004 - 25 Dec 2025
Abstract
Statistical confidentiality focuses on protecting data to preserve its analytical value while preventing identity exposure, ensuring privacy and security in any system handling sensitive information. Homomorphic encryption allows computations on encrypted data without revealing it to anyone other than an owner or an
[...] Read more.
Statistical confidentiality focuses on protecting data to preserve its analytical value while preventing identity exposure, ensuring privacy and security in any system handling sensitive information. Homomorphic encryption allows computations on encrypted data without revealing it to anyone other than an owner or an authorized collector. When combined with other techniques, homomorphic encryption offers an ideal solution for ensuring statistical confidentiality. TFHE (Fast Fully Homomorphic Encryption over the Torus) is a fully homomorphic encryption scheme that supports efficient homomorphic operations on Booleans and integers. Building on TFHE, Zama’s Concrete project offers an open-source compiler that translates high-level Python code (version 3.9 or higher) into secure homomorphic computations. This study examines the feasibility of the Concrete compiler to perform core statistical analyses on encrypted data. We implement traditional algorithms for core statistical measures including the mean, variance, and five-point summary on encrypted datasets. Additionally, we develop a bitonic sort implementation to support the five-point summary. All implementations are executed within the Concrete framework, leveraging its built-in optimizations. Their performance is systematically evaluated by measuring circuit complexity, programmable bootstrapping count (PBS), compilation time, and execution time. We compare these results to findings from previous studies wherever possible. The results show that the complexity of sorting and statistical computations on encrypted data with the Concrete implementation of TFHE increases rapidly, and the size and range of data that can be accommodated is small for most applications. Nevertheless, this work reinforces the theoretical promise of Fully Homomorphic Encryption (FHE) for statistical analysis and highlights a clear path forward: the development of optimized, FHE-compatible algorithms.
Full article
(This article belongs to the Special Issue Data Protection and Privacy)
►▼
Show Figures

Figure 1
Open AccessArticle
Digital Resilience and the “Awareness Gap”: An Empirical Study of Youth Perceptions of Hate Speech Governance on Meta Platforms in Hungary
by
Roland Kelemen, Dorina Bosits and Zsófia Réti
J. Cybersecur. Priv. 2026, 6(1), 3; https://doi.org/10.3390/jcp6010003 - 24 Dec 2025
Abstract
Online hate speech poses a growing socio-technological threat that undermines democratic resilience and obstructs progress toward Sustainable Development Goal 16 (SDG 16). This study examines the regulatory and behavioral dimensions of this phenomenon through a combined legal analysis of platform governance and an
[...] Read more.
Online hate speech poses a growing socio-technological threat that undermines democratic resilience and obstructs progress toward Sustainable Development Goal 16 (SDG 16). This study examines the regulatory and behavioral dimensions of this phenomenon through a combined legal analysis of platform governance and an empirical survey conducted on Meta platforms, based on a sample of young Hungarians (N = 301, aged 14–34). This study focuses on Hungary as a relevant case study of a Central and Eastern European (CEE) state. Countries in this region, due to their shared historical development, face similar societal challenges that are also reflected in the online sphere. The combination of high social media penetration, a highly polarized political discourse, and the tensions between platform governance and EU law (the DSA) makes the Hungarian context particularly suitable for examining digital resilience and the legal awareness of young users. The results reveal a significant “awareness gap”: While a majority of young users can intuitively identify overt hate speech, their formal understanding of platform rules is minimal. Furthermore, their sanctioning preferences often diverge from Meta’s actual policies, indicating a lack of clarity and predictability in platform governance. This gap signals a structural weakness that erodes user trust. The legal analysis highlights the limited enforceability and opacity of content moderation mechanisms, even under the Digital Services Act (DSA) framework. The empirical findings show that current self-regulation models fail to empower users with the necessary knowledge. The contribution of this study is to empirically identify and critically reframe this ‘awareness gap’. Moving beyond a simple knowledge deficit, we argue that the gap is a symptom of a deeper legitimacy crisis in platform governance. It reflects a rational user response—manifesting as digital resignation—to opaque, commercially driven, and unaccountable moderation systems. By integrating legal and behavioral insights with critical platform studies, this paper argues that achieving SDG 16 requires a dual strategy: (1) fundamentally increasing transparency and accountability in content governance to rebuild user trust, and (2) enhancing user-centered digital and legal literacy through a shared responsibility model. Such a strategy must involve both public and private actors in a coordinated, rights-based approach. Ultimately, this study calls for policy frameworks that strengthen democratic resilience not only through better regulation, but by empowering citizens to become active participants—rather than passive subjects—in the governance of online spaces.
Full article
(This article belongs to the Special Issue Multimedia Security and Privacy)
►▼
Show Figures

Figure 1
Open AccessArticle
Using Secure Multi-Party Computation to Create Clinical Trial Cohorts
by
Rafael Borges, Bruno Ferreira, Carlos Machado Antunes, Marisa Maximiano, Ricardo Gomes, Vítor Távora, Manuel Dias, Ricardo Correia Bezerra and Patrício Domingues
J. Cybersecur. Priv. 2026, 6(1), 2; https://doi.org/10.3390/jcp6010002 - 24 Dec 2025
Abstract
The increasing volume of digital medical data offers substantial research opportunities, though its complete utilization is hindered by ongoing privacy and security obstacles. This proof-of-concept study explores and confirms the viability of using Secure Multi-Party Computation (SMPC) to ensure protection and integrity of
[...] Read more.
The increasing volume of digital medical data offers substantial research opportunities, though its complete utilization is hindered by ongoing privacy and security obstacles. This proof-of-concept study explores and confirms the viability of using Secure Multi-Party Computation (SMPC) to ensure protection and integrity of sensitive patient data, allowing the construction of clinical trial cohorts. Our findings reveal that SMPC facilitates collaborative data analysis on distributed, private datasets with negligible computational costs and optimized data partition sizes. The established architecture incorporates patient information via a blockchain-based decentralized healthcare platform and employs the MPyC library in Python for secure computations on Fast Healthcare Interoperability Resources (FHIR)-format data. The outcomes affirm SMPC’s capacity to maintain patient privacy during cohort formation, with minimal overhead. It illustrates the potential of SMPC-based methodologies to expand access to medical research data. A key contribution of this work is eliminating the need for complex cryptographic key management while maintaining patient privacy, illustrating the potential of SMPC-based methodologies to expand access to medical research data by reducing implementation barriers.
Full article
(This article belongs to the Special Issue Cyber Security and Digital Forensics—2nd Edition)
►▼
Show Figures

Figure 1
Open AccessArticle
Huffman Tree and Binary Conversion for Efficient and Secure Data Encryption and Decryption
by
Suchart Khummanee, Thanapat Cheawchanwattana, Chanwit Suwannapong, Sarutte Atsawaraungsuk and Kritsanapong Somsuk
J. Cybersecur. Priv. 2026, 6(1), 1; https://doi.org/10.3390/jcp6010001 - 22 Dec 2025
Abstract
This study proposes the Huffman Tree and Binary Conversion (HTB) which is a preprocessing algorithm to transform the Huffman tree into binary representation before the encryption process. In fact, HTB can improve the structural readiness of plaintext by combining the Huffman code with
[...] Read more.
This study proposes the Huffman Tree and Binary Conversion (HTB) which is a preprocessing algorithm to transform the Huffman tree into binary representation before the encryption process. In fact, HTB can improve the structural readiness of plaintext by combining the Huffman code with a deterministic binary representation of the Huffman tree. In addition, binary representation of the Huffman tree and the compressed information will be encrypted by standard cryptographic algorithms. Six datasets, divided into two groups (short and long texts), were chosen to evaluate compression behavior and the processing cost. Moreover, AES and RSA are chosen to combine with the proposed method to analyze the encryption and decryption cycles. The experimental results show that HTB introduces a small linear-time overhead. That means, it is slightly slower than applying only the Huffman code. Across these datasets, HTB maintained a consistently low processing cost. The processing time is below one millisecond in both encoding and decoding processes. However, for long texts, the structural conversion cost becomes amortized across larger encoded messages, and the reduction in plaintext size leads to fewer encryption blocks for both AES and RSA. The reduced plaintext size lowers the number of AES encryption blocks by approximately 30–45% and decreases the number of encryption and decryption rounds in RSA. The encrypted binary representation of the Huffman tree also decreased structural ambiguity and reduced the potential exposure of frequency-related metadata. Although HTB does not replace cryptographic security, it enhances the structural consistency of compression. Therefore, the proposed method demonstrates scalability, predictable overhead, and improved suitability for cryptographic workflows.
Full article
(This article belongs to the Section Cryptography and Cryptology)
►▼
Show Figures

Figure 1
Open AccessArticle
Exploring Determinants of Information Security Systems Adoption in Saudi Arabian SMEs: An Integrated Multitheoretical Model
by
Ali Abdu M Dighriri, Sarvjeet Kaur Chatrath and Masoud Mohammadian
J. Cybersecur. Priv. 2025, 5(4), 113; https://doi.org/10.3390/jcp5040113 - 18 Dec 2025
Abstract
High cybersecurity risks and attacks cause information theft, unauthorized access to data and information, reputational damage, and financial loss in small and medium enterprises (SMEs). This creates a need to adopt information security systems of SMEs through innovation and compliance with information security
[...] Read more.
High cybersecurity risks and attacks cause information theft, unauthorized access to data and information, reputational damage, and financial loss in small and medium enterprises (SMEs). This creates a need to adopt information security systems of SMEs through innovation and compliance with information security policies. This study seeks to develop an integrated research model assessing the adoption of InfoSec systems in SMEs based on three existing theories, namely the technology acceptance model (TAM), theory of reasoned action (TRA), and unified theory of acceptance and use of technology (UTAUT). A thorough review of literature identified prior experience, enjoyment of new InfoSec technology, top management support, IT infrastructure, security training, legal-governmental regulations, and attitude as potential determinants of adoption of InfoSec systems. A self-developed and self-administered questionnaire was distributed to 418 employees, mid-level managers, and top-level managers working in SMEs operating in Riyadh, Saudi Arabia. The study found that prior experience, top management support, IT infrastructure, security training, and legal-governmental regulations have a positive impact on attitude toward InfoSec systems, which in turn positively influences the adoption of InfoSec systems. Gender, education, and occupation significantly moderated the impact of some determinants on attitude and, consequently, adoption of InfoSec systems. Such an integrated framework offers actionable insights and recommendations, including enhancing information security awareness and compliance with information security policies, as well as increasing profitability within SMEs. The study findings make considerable theoretical contributions to the development of knowledge and deliver practical contributions towards the status of SMEs in Saudi Arabia.
Full article
(This article belongs to the Section Security Engineering & Applications)
►▼
Show Figures

Figure 1
Open AccessArticle
Statistical and Multivariate Analysis of the IoT-23 Dataset: A Comprehensive Approach to Network Traffic Pattern Discovery
by
Humera Ghani, Shahram Salekzamankhani and Bal Virdee
J. Cybersecur. Priv. 2025, 5(4), 112; https://doi.org/10.3390/jcp5040112 - 16 Dec 2025
Abstract
The rapid expansion of Internet of Things (IoT) technologies has introduced significant challenges in understanding the complexity and structure of network traffic data, which is essential for developing effective cybersecurity solutions. This research presents a comprehensive statistical and multivariate analysis of the IoT-23
[...] Read more.
The rapid expansion of Internet of Things (IoT) technologies has introduced significant challenges in understanding the complexity and structure of network traffic data, which is essential for developing effective cybersecurity solutions. This research presents a comprehensive statistical and multivariate analysis of the IoT-23 dataset to identify meaningful network traffic patterns and assess the effectiveness of various analytical methods for IoT security research. The study applies descriptive statistics, inferential analysis, and multivariate techniques, including Principal Component Analysis (PCA), DBSCAN clustering, and factor analysis (FA), to the publicly available IoT-23 dataset. Descriptive analysis reveals clear evidence of non-normal distributions: for example, the features src_bytes, dst_bytes, and src_pkts have skewness values of −4.21, −3.87, and −2.98, and kurtosis values of 38.45, 29.67, and 18.23, respectively. These values indicate highly skewed, heavy-tailed distributions with frequent outliers. Correlation analysis revealed a strong positive correlation (0.97) between orig_bytes and resp_bytes, and a strong negative correlation (−0.76) between duration and resp_bytes, while inferential statistics indicate that linear regression provides optimal modeling of data relationships. Key findings show that PCA is highly effective, capturing 99% of the dataset’s variance and enabling significant dimensionality reduction. DBSCAN clustering identifies six distinct clusters, highlighting diverse network traffic behaviors within IoT environments. In contrast, FA explains only 11.63% of the variance, indicating limited suitability for this dataset. These results establish important benchmarks for future IoT cybersecurity research and demonstrate the superior effectiveness of PCA and DBSCAN for analyzing complex IoT network traffic data. The findings offer practical guidance for researchers in selecting appropriate statistical methods for IoT dataset analysis, ultimately supporting the development of more robust cybersecurity solutions.
Full article
(This article belongs to the Special Issue Intrusion/Malware Detection and Prevention in Networks—2nd Edition)
►▼
Show Figures

Figure 1
Open AccessArticle
Quantifying Privacy Risk of Mobile Apps as Textual Entailment Using Language Models
by
Chris Y. T. Ma
J. Cybersecur. Priv. 2025, 5(4), 111; https://doi.org/10.3390/jcp5040111 - 12 Dec 2025
Abstract
Smart phones have become an integral part of our lives in modern society, as we carry and use them throughout a day. However, this “body part” may maliciously collect and leak our personal information without our knowledge. When we install mobile applications on
[...] Read more.
Smart phones have become an integral part of our lives in modern society, as we carry and use them throughout a day. However, this “body part” may maliciously collect and leak our personal information without our knowledge. When we install mobile applications on our smart phones and grant their permission requests, these apps can use sensors embedded in the smart phones and the stored data to gather and infer our personal information, preferences, and habits. In this paper, we present our preliminary results on quantifying the privacy risk of mobile applications by assessing whether requested permissions are necessary based on app descriptions through textual entailment decided by language models (LMs). We observe that despite incorporating various improvements of LMs proposed in the literature for natural language processing (NLP) tasks, the performance of the trained model remains far from ideal.
Full article
(This article belongs to the Section Privacy)
►▼
Show Figures

Figure 1
Open AccessArticle
Leveraging Static Analysis for Feedback-Driven Security Patching in LLM-Generated Code
by
Kamel Alrashedy, Abdullah Aljasser, Pradyumna Tambwekar and Matthew Gombolay
J. Cybersecur. Priv. 2025, 5(4), 110; https://doi.org/10.3390/jcp5040110 - 5 Dec 2025
Abstract
Large language models (LLMs) have shown remarkable potential for automatic code generation. Yet, these models share a weakness with their human counterparts: inadvertently generating code with security vulnerabilities that could allow unauthorized attackers to access sensitive data or systems. In this work, we
[...] Read more.
Large language models (LLMs) have shown remarkable potential for automatic code generation. Yet, these models share a weakness with their human counterparts: inadvertently generating code with security vulnerabilities that could allow unauthorized attackers to access sensitive data or systems. In this work, we propose Feedback-Driven Security Patching (FDSP), wherein LLMs automatically refine vulnerable generated code. The key to our approach is a unique framework that leverages automatic static code analysis to enable the LLM to create and implement potential solutions to code vulnerabilities. Further, we curate a novel benchmark, PythonSecurityEval, that can accelerate progress in the field of code generation by covering diverse, real-world applications, including databases, websites, and operating systems. Our proposed FDSP approach achieves the strongest improvements, reducing vulnerabilities by up to 33% when evaluated with Bandit and 12% with CodeQL and outperforming baseline refinement methods.
Full article
(This article belongs to the Section Security Engineering & Applications)
►▼
Show Figures

Figure 1
Open AccessArticle
MalVis: Large-Scale Bytecode Visualization Framework for Explainable Android Malware Detection
by
Saleh J. Makkawy, Michael J. De Lucia and Kenneth E. Barner
J. Cybersecur. Priv. 2025, 5(4), 109; https://doi.org/10.3390/jcp5040109 - 4 Dec 2025
Abstract
As technology advances, developers continually create innovative solutions to enhance smartphone security. However, the rapid spread of Android malware poses significant threats to devices and sensitive data. The Android Operating System (OS)’s open-source nature and Software Development Kit (SDK) availability mainly contribute to
[...] Read more.
As technology advances, developers continually create innovative solutions to enhance smartphone security. However, the rapid spread of Android malware poses significant threats to devices and sensitive data. The Android Operating System (OS)’s open-source nature and Software Development Kit (SDK) availability mainly contribute to this alarming growth. Conventional malware detection methods, such as signature-based, static, and dynamic analysis, face challenges in detecting obfuscated techniques, including encryption, packing, and compression, in malware. Although developers have created several visualization techniques for malware detection using deep learning (DL), they often fail to accurately identify the critical malicious features of malware. This research introduces MalVis, a unified visualization framework that integrates entropy and N-gram analysis to emphasize meaningful structural and anomalous operational patterns within the malware bytecode. By addressing significant limitations of existing visualization methods, such as insufficient feature representation, limited interpretability, small dataset sizes, and restricted data access, MalVis delivers enhanced detection capabilities, particularly for obfuscated and previously unseen (zero-day) malware. The framework leverages the MalVis dataset introduced in this work, a publicly available large-scale dataset comprising more than 1.3 million visual representations in nine malware classes and one benign class. A comprehensive comparative evaluation was performed against existing state-of-the-art visualization techniques using leading convolutional neural network (CNN) architectures, MobileNet-V2, DenseNet201, ResNet50, VGG16, and Inception-V3. To further boost classification performance and mitigate overfitting, the outputs of these models were combined using eight distinct ensemble strategies. To address the issue of imbalanced class distribution in the multiclass dataset, we employed an undersampling technique to ensure balanced learning across all types of malware. MalVis achieved superior results, with 95% accuracy, 90% F1-score, 92% precision, 89% recall, 87% Matthews Correlation Coefficient (MCC), and 98% Receiver Operating Characteristic Area Under Curve (ROC-AUC). These findings highlight the effectiveness of MalVis in providing interpretable and accurate representation features for malware detection and classification, making it valuable for research and real-world security applications.
Full article
(This article belongs to the Section Security Engineering & Applications)
►▼
Show Figures

Figure 1
Open AccessArticle
Towards an End-to-End (E2E) Adversarial Learning and Application in the Physical World
by
Dudi Biton, Jacob Shams, Satoru Koda, Asaf Shabtai, Yuval Elovici and Ben Nassi
J. Cybersecur. Priv. 2025, 5(4), 108; https://doi.org/10.3390/jcp5040108 - 1 Dec 2025
Abstract
The traditional process for learning patch-based adversarial attacks, conducted in the digital domain and later applied in the physical domain (e.g., via printed stickers), may suffer reduced performance due to adversarial patches’ limited transferability between domains. Given that previous studies have considered using
[...] Read more.
The traditional process for learning patch-based adversarial attacks, conducted in the digital domain and later applied in the physical domain (e.g., via printed stickers), may suffer reduced performance due to adversarial patches’ limited transferability between domains. Given that previous studies have considered using film projectors to apply adversarial attacks, we ask: Can adversarial learning (i.e., patch generation) be performed entirely in the physical domain using a film projector? In this work, we propose the Physical-domain Adversarial Patch Learning Augmentation (PAPLA) framework, a novel end-to-end (E2E) framework that shifts adversarial learning from the digital domain to the physical domain using a film projector. We evaluate PAPLA in scenarios, including controlled laboratory and realistic outdoor settings, demonstrating its ability to ensure attack success compared to conventional digital learning–physical application (DL-PA) methods. We also analyze how environmental factors such as projection surface color, projector strength, ambient light, distance, and the target object’s angle relative to the camera affect patch effectiveness. Finally, we demonstrate the feasibility of the attack against a parked car and a stop sign in a real-world outdoor environment. Our results show that under specific conditions, E2E adversarial learning in the physical domain eliminates transferability issues and ensures evasion of object detectors. We also discuss the challenges and opportunities of adversarial learning in the physical domain and identify where this approach is more effective than using a sticker.
Full article
(This article belongs to the Section Privacy)
►▼
Show Figures

Figure 1
Open AccessArticle
Evaluating Privacy Technologies in Digital Payments: A Balanced Framework
by
Ioannis Fragkiadakis, Stefanos Gritzalis and Costas Lambrinoudakis
J. Cybersecur. Priv. 2025, 5(4), 107; https://doi.org/10.3390/jcp5040107 - 1 Dec 2025
Abstract
Privacy enhancement technologies are significant in the development of digital payment systems. At present, multiple innovative digital payment solutions have been introduced and may be implemented globally soon. As cyber threats continue to increase in complexity, security is a crucial factor to consider
[...] Read more.
Privacy enhancement technologies are significant in the development of digital payment systems. At present, multiple innovative digital payment solutions have been introduced and may be implemented globally soon. As cyber threats continue to increase in complexity, security is a crucial factor to consider before adopting any technology. In addition to prioritizing security in the development of digital payment systems, it is essential to address user privacy concerns. Modern digital payment solutions offer numerous advantages over traditional systems; however, they also introduce new considerations that must be accounted for during implementation. These considerations go beyond legislative requirements and encompass new payment methods, including transactions made through mobile devices regardless of internet connectivity. A range of regulations and guidelines exist to ensure user privacy in financial transactions, with the General Data Protection Regulation (GDPR) being particularly notable, while technical reports have thoroughly examined the differences between various privacy-enhancing technologies. Additionally, it is important to note that all legal payment systems are required to maintain information for audit purposes. This paper introduces a comprehensive framework that integrates all critical considerations for selecting appropriate privacy enhancement technologies within digital payment systems, while it utilizes a detailed scoring system designed for convenience and adaptability, allowing it to be employed for purposes such as auditing. Thus, the proposed scoring framework integrates security, GDPR compliance, audit, privacy-preserving technical measures, and operational constraints to assess privacy technologies for digital payments.
Full article
(This article belongs to the Section Privacy)
Open AccessArticle
Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development
by
Colman McGuan, Aadithyan Vijaya Raghavan, Komala M. Mandapati, Chansu Yu, Brian E. Ray, Debbie K. Jackson and Sathish Kumar
J. Cybersecur. Priv. 2025, 5(4), 106; https://doi.org/10.3390/jcp5040106 - 1 Dec 2025
Abstract
In an increasingly interconnected world, cybersecurity professionals play a pivotal role in safeguarding organizations from cyber threats. To secure their cyberspace, organizations are forced to adopt a cybersecurity framework such as the NIST National Initiative for Cybersecurity Education Workforce Framework for Cybersecurity (NICE
[...] Read more.
In an increasingly interconnected world, cybersecurity professionals play a pivotal role in safeguarding organizations from cyber threats. To secure their cyberspace, organizations are forced to adopt a cybersecurity framework such as the NIST National Initiative for Cybersecurity Education Workforce Framework for Cybersecurity (NICE Framework). Although these frameworks are a good starting point for businesses and offer critical information to identify, prevent, and respond to cyber incidents, they can be difficult to navigate and implement, particularly for small-medium businesses (SMBs). To help overcome this issue, this paper identifies the most frequent attack vectors to SMBs (Objective 1) and proposes a practical model of both technical and non-technical tasks, knowledge, skills, abilities (TKSA) from the NICE Framework for those attacks (Objective 2). This research develops a scenario-based curriculum. By immersing learners in realistic cyber threat scenarios, their practical understanding and preparedness in responding to cybersecurity incidents is enhanced (Objective 3). Finally, this work integrates practical experience and real-life skill development into the curriculum (Objective 4). SMBs can use the model as a guide to evaluate, equip their existing workforce, or assist in hiring new employees. In addition, educational institutions can use the model to develop scenario-based learning modules to adequately equip the emerging cybersecurity workforce for SMBs. Trainees will have the opportunity to practice both technical and legal issues in a simulated environment, thereby strengthening their ability to identify, mitigate, and respond to cyber threats effectively. We piloted these learning modules as a semester-long course titled “Hack Lab” for both Computer Science (CS) and Law students at CSU during Spring 2024 and Spring 2025. According to the self-assessment survey by the end of the semester, students demonstrated substantial gains in confidence across four key competencies (identifying vulnerabilities and using tools, applying cybersecurity laws, recognizing steps in incident response, and explaining organizational response preparation) with an average improvement of +2.8 on a 1–5 scale. Separately, overall course evaluations averaged 4.4 for CS students and 4.0 for Law students, respectively, on a 1–5 scale (college average is 4.21 and 4.19, respectively). Law students reported that hands-on labs were difficult, although they were the most impactful experience. They demonstrated a notable improvement in identifying vulnerabilities and understanding response processes.
Full article
(This article belongs to the Section Security Engineering & Applications)
►▼
Show Figures

Figure 1
Open AccessArticle
A Game-Theoretic Approach for Quantification of Strategic Behaviors in Digital Forensic Readiness
by
Mehrnoush Vaseghipanah, Sam Jabbehdari and Hamidreza Navidi
J. Cybersecur. Priv. 2025, 5(4), 105; https://doi.org/10.3390/jcp5040105 - 26 Nov 2025
Abstract
Small and Medium-sized Enterprises (SMEs) face disproportionately high risks from Advanced Persistent Threats (APTs), which often evade traditional cybersecurity measures. Existing frameworks catalogue adversary tactics and defensive solutions but provide limited quantitative guidance for allocating limited resources under uncertainty, a challenge amplified by
[...] Read more.
Small and Medium-sized Enterprises (SMEs) face disproportionately high risks from Advanced Persistent Threats (APTs), which often evade traditional cybersecurity measures. Existing frameworks catalogue adversary tactics and defensive solutions but provide limited quantitative guidance for allocating limited resources under uncertainty, a challenge amplified by the growing use of AI in both offensive operations and digital forensics. This paper proposes a game-theoretic model for improving digital forensic readiness (DFR) in SMEs. The approach integrates the MITRE ATT&CK and D3FEND frameworks to map APT behaviors to defensive countermeasures and defines 32 custom DFR metrics, weighted using the Analytic Hierarchy Process (AHP), to derive utility functions for both attackers and defenders. The main analysis considers a non-zero-sum attacker–defender bimatrix game and yields a single Nash equilibrium in which the attacker concentrates on Impact-oriented tactics and the defender on Detect-focused controls. In a synthetic calibration across ten organizational profiles, the framework achieves a median readiness improvement of 18.0% (95% confidence interval: 16.3% to 19.7%) relative to pre-framework baselines, with targeted improvements in logging and forensic preservation typically reducing key attacker utility components by around 15–30%. A zero-sum variant of the game is also analyzed as a robustness check and exhibits consistent tactical themes, but all policy conclusions are drawn from the empirical non-zero-sum model. Despite relying on expert-driven AHP weights and synthetic profiles, the framework offers SMEs actionable, equilibrium-informed guidance for strengthening forensic preparedness against advanced cyber threats.
Full article
(This article belongs to the Special Issue Cyber Security and Digital Forensics—2nd Edition)
►▼
Show Figures

Figure 1
Open AccessArticle
A Lightweight Multimodal Framework for Misleading News Classification Using Linguistic and Behavioral Biometrics
by
Mahmudul Haque, A. S. M. Hossain Bari and Marina L. Gavrilova
J. Cybersecur. Priv. 2025, 5(4), 104; https://doi.org/10.3390/jcp5040104 - 25 Nov 2025
Abstract
The widespread dissemination of misleading news presents serious challenges to public discourse, democratic institutions, and societal trust. Misleading-news classification (MNC) has been extensively studied through deep neural models that rely mainly on semantic understanding or large-scale pretrained language models. However, these methods often
[...] Read more.
The widespread dissemination of misleading news presents serious challenges to public discourse, democratic institutions, and societal trust. Misleading-news classification (MNC) has been extensively studied through deep neural models that rely mainly on semantic understanding or large-scale pretrained language models. However, these methods often lack interpretability and are computationally expensive, limiting their practical use in real-time or resource-constrained environments. Existing approaches can be broadly categorized into transformer-based text encoders, hybrid CNN–LSTM frameworks, and fuzzy-logic fusion networks. To advance research on MNC, this study presents a lightweight multimodal framework that extends the Fuzzy Deep Hybrid Network (FDHN) paradigm by introducing a linguistic and behavioral biometric perspective to MNC. We reinterpret the FDHN architecture to incorporate linguistic cues such as lexical diversity, subjectivity, and contradiction scores as behavioral signatures of deception. These features are processed and fused with semantic embeddings, resulting in a model that captures both what is written and how it is written. The design of the proposed method ensures the trade-off between feature complexity and model generalizability. Experimental results demonstrate that the inclusion of lightweight linguistic and behavioral biometric features significantly enhance model performance, yielding a test accuracy of 71.91 ± 0.23% and a macro F1 score of 71.17 ± 0.26%, outperforming the state-of-the-art method. The findings of the study underscore the utility of stylistic and affective cues in MNC while highlighting the need for model simplicity to maintain robustness and adaptability.
Full article
(This article belongs to the Special Issue Multimedia Security and Privacy)
►▼
Show Figures

Figure 1
Open AccessSystematic Review
Privacy in Flux: A 35-Year Systematic Review of Legal Evolution, Effectiveness, and Global Challenges (U.S./E.U. Focus with International Comparisons)
by
Kong Phang and Jihene Kaabi
J. Cybersecur. Priv. 2025, 5(4), 103; https://doi.org/10.3390/jcp5040103 - 22 Nov 2025
Abstract
Privacy harms have expanded alongside rapid technological change, challenging the adequacy of existing regulatory frameworks. This systematic review (1990–2025) systematically maps documented privacy harms to specific legal mechanisms and observed enforcement outcomes across jurisdictions, using PRISMA-guided methods and ROBIS risk-of-bias assessment. We synthesize
[...] Read more.
Privacy harms have expanded alongside rapid technological change, challenging the adequacy of existing regulatory frameworks. This systematic review (1990–2025) systematically maps documented privacy harms to specific legal mechanisms and observed enforcement outcomes across jurisdictions, using PRISMA-guided methods and ROBIS risk-of-bias assessment. We synthesize evidence on major regimes (e.g., GDPR, COPPA, CCPA, HIPAA, GLBA) and conduct comparative legal analysis across the U.S., E.U., and underexplored regions in Asia, Latin America, and Africa. Key findings indicate increased recognition of data subject rights, persistent gaps in cross-border data governance, and emerging risks from AI/ML/LLMs, IoT, and blockchain, including data breaches, algorithmic discrimination, and surveillance. While regulations have advanced, enforcement variability and fragmented standards limit effectiveness. We propose strategies for harmonization and risk-based, technology-neutral safeguards. While focusing on the U.S. sectoral and E.U. comprehensive models, we include targeted comparisons with Canada (PIPEDA), Australia (Privacy Act/APPs), Japan (APPI), India (DPDPA), Africa (POPIA/NDPR/Kenya DPA), and ASEAN interoperability instruments. This review presents an evidence-based framework for understanding the interplay between evolving harms, emerging technologies, and legal protections, and identifies priorities for strengthening global privacy governance.
Full article
(This article belongs to the Special Issue Data Protection and Privacy)
►▼
Show Figures

Figure A1
Highly Accessed Articles
Latest Books
E-Mail Alert
News
Topics
Topic in
Applied Sciences, Electronics, Informatics, JCP, Future Internet, Mathematics, Sensors, Remote Sensing
Recent Advances in Artificial Intelligence for Security and Security for Artificial Intelligence
Topic Editors: Tao Zhang, Xiangyun Tang, Jiacheng Wang, Chuan Zhang, Jiqiang LiuDeadline: 28 February 2026
Topic in
Applied Sciences, Cryptography, Electronics, Mathematics, Information, Sci, Entropy, JCP
Recent Developments and Applications of Image Watermarking
Topic Editors: Frederic Ros, Pedro M. B. TorresDeadline: 31 July 2026
Topic in
Applied Sciences, Automation, Computers, Electronics, Sensors, JCP, Mathematics
Intelligent Optimization, Decision-Making and Privacy Preservation in Cyber–Physical Systems
Topic Editors: Lijuan Zha, Jinliang Liu, Jian LiuDeadline: 31 August 2026

Special Issues
Special Issue in
JCP
Cloud Security and Privacy
Guest Editors: Martin Gilje Jaatun, Massimiliano Rak, Ferhat Ozgur CatakDeadline: 30 January 2026
Special Issue in
JCP
Applied Cryptography
Guest Editors: Yangguang Tian, Danda B. RawatDeadline: 20 February 2026
Special Issue in
JCP
Intrusion/Malware Detection and Prevention in Networks—2nd Edition
Guest Editors: Feng Wang, Yongning TangDeadline: 10 March 2026
Special Issue in
JCP
Cyber Security and Digital Forensics—3rd Edition
Guest Editors: Mario Antunes, Carlos RabadãoDeadline: 31 May 2026
Topical Collections
Topical Collection in
JCP
Intelligent Security and Privacy Approaches against Cyber Threats
Collection Editor: Nour Moustafa
Topical Collection in
JCP
Machine Learning and Data Analytics for Cyber Security
Collection Editors: Phil Legg, Giorgio Giacinto







