- Article
Blockchain-Based Solution for Privacy-Preserving SIM Card Registration
- Babe Haiba and
- Najat Rafalia
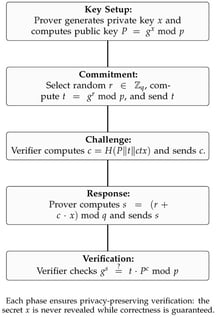
Mandatory SIM card registration, while essential to regulatory oversight and national security, continues to raise significant privacy concerns due to the centralized collection and storage of sensitive user data by Mobile Network Operators (MNOs). This paper introduces a novel framework that combines blockchain technology with Zero-Knowledge Proofs (ZKPs) to enable secure and privacy-preserving identity verification during SIM registration. The proposed system allows users to authenticate their identity attributes without revealing any personal information, effectively minimizing direct data access by MNOs or intermediaries. A smart contract deployed on the blockchain enforces regulatory policies while ensuring the transparency, immutability, and auditability of all registration events. By removing single points of failure and minimizing trust in centralized authorities, this work offers a cryptographically secure and regulation-compliant solution, with scalability supported by its modular design for next-generation digital identity management in telecommunications infrastructures.
9 February 2026