Journal Description
IoT
IoT
is an international, peer-reviewed, open access journal on Internet of Things (IoT) published quarterly online by MDPI.
- Open Access— free for readers, with article processing charges (APC) paid by authors or their institutions
- High Visibility: indexed within ESCI (Web of Science), Scopus, EBSCO, and other databases.
- Rapid Publication: manuscripts are peer-reviewed and a first decision is provided to authors approximately 25.5 days after submission; acceptance to publication is undertaken in 5.3 days (median values for papers published in this journal in the second half of 2025).
- Journal Rank: JCR - Q2 (Telecommunications) / CiteScore - Q1 (Computer Science (miscellaneous))
- Recognition of Reviewers: APC discount vouchers, optional signed peer review, and reviewer names published annually in the journal.
- Journal Clusters of Network and Communications Technology: Future Internet, IoT, Telecom, Journal of Sensor and Actuator Networks, Network, Signals.
Impact Factor:
2.8 (2024);
5-Year Impact Factor:
3.2 (2024)
Latest Articles
Intrusion Detection on the Internet of Things: A Comprehensive Review and Gap Analysis Toward Real-Time, Lightweight, Adaptive, and Autonomous Security
IoT 2026, 7(1), 16; https://doi.org/10.3390/iot7010016 (registering DOI) - 7 Feb 2026
Abstract
The rapid growth of the Internet of Things (IoT) has exposed billions of interconnected, heterogeneous, and resource-constrained devices to increasingly sophisticated threats. To evaluate the readiness of current intrusion detection systems (IDSs), this study reviews 32 recent IoT-IDS proposals spanning conventional, machine-learning, deep-learning,
[...] Read more.
The rapid growth of the Internet of Things (IoT) has exposed billions of interconnected, heterogeneous, and resource-constrained devices to increasingly sophisticated threats. To evaluate the readiness of current intrusion detection systems (IDSs), this study reviews 32 recent IoT-IDS proposals spanning conventional, machine-learning, deep-learning, and hybrid approaches. Each system is assessed against 10 criteria that reflect practical IoT requirements, including real-time performance, latency, lightweight design, detection accuracy, mitigation capabilities, integrated detection-and-mitigation workflows, adaptability, resilience to advanced attacks, validation in realistic environments, and scalability. The results indicate that although many approaches achieve high detection accuracy, most do not meet real-time and lightweight thresholds commonly cited in IoT deployment literature. Mitigation features are often absent, adaptability is rarely implemented, and 29 out of 32 studies rely solely on offline datasets, thereby limiting confidence in their robustness to deployment. Scalability remains the most significant limitation, as none of the reviewed IDSs have tested their performance under realistic multi-node or high-traffic conditions, even though scalability is critical for large IoT ecosystems. Overall, the review suggests that future IoT IDS research should move beyond accuracy-focused models and toward lightweight, adaptive, and autonomous solutions that incorporate mitigation, support real-time inference, and undergo standardized evaluations under real-world operating conditions.
Full article
(This article belongs to the Special Issue Cybersecurity in the Age of the Internet of Things)
Open AccessArticle
Audiovisual Gun Detection with Automated Lockdown and PA Announcing IoT System for Schools
by
Tareq Khan
IoT 2026, 7(1), 15; https://doi.org/10.3390/iot7010015 - 31 Jan 2026
Abstract
►▼
Show Figures
Gun violence in U.S. schools not only causes loss of life and physical injury but also leaves enduring psychological trauma, damages property, and results in significant economic losses. One way to reduce this loss is to detect the gun early, notify the police
[...] Read more.
Gun violence in U.S. schools not only causes loss of life and physical injury but also leaves enduring psychological trauma, damages property, and results in significant economic losses. One way to reduce this loss is to detect the gun early, notify the police as soon as possible, and implement lockdown procedures immediately. In this project, a novel gun detector Internet of Things (IoT) system is developed that automatically detects the presence of a gun either from images or from gunshot sounds, and sends notifications with exact location information to the first responder’s smartphones using the Internet within a second. The device also sends wireless commands using Message Queuing Telemetry Transport (MQTT) protocol to close the smart door locks in classrooms and announce to act using public address (PA) system automatically. The proposed system will remove the burden of manually calling the police and implementing the lockdown procedure during such traumatic situations. Police will arrive sooner, and thus it will help to stop the shooter early, the injured people can be taken to the hospital quickly, and more lives can be saved. Two custom deep learning AI models are used: (a) to detect guns from image data having an accuracy of 94.6%, and (b) the gunshot sounds from audio data having an accuracy of 99%. No single gun detector device is available in the literature that can detect guns from both image and audio data, implement lockdown and make PA announcement automatically. A prototype of the proposed gunshot detector IoT system, and a smartphone app is developed, and tested with gun replicas and blank guns in real-time.
Full article

Figure 1
Open AccessReview
The Network and Information Systems 2 Directive: Toward Scalable Cyber Risk Management in the Remote Patient Monitoring Domain: A Systematic Review
by
Brian Mulhern, Chitra Balakrishna and Jan Collie
IoT 2026, 7(1), 14; https://doi.org/10.3390/iot7010014 - 29 Jan 2026
Abstract
Healthcare 5.0 and the Internet of Medical Things (IoMT) is emerging as a scalable model for the delivery of customised healthcare and chronic disease management, through Remote Patient Monitoring (RPM) in patient smart home environments. Large-scale RPM initiatives are being rolled out by
[...] Read more.
Healthcare 5.0 and the Internet of Medical Things (IoMT) is emerging as a scalable model for the delivery of customised healthcare and chronic disease management, through Remote Patient Monitoring (RPM) in patient smart home environments. Large-scale RPM initiatives are being rolled out by healthcare providers (HCPs); however, the constrained nature of IoMT devices and proximity to poorly administered smart home technologies create a cyber risk for highly personalised patient data. The recent Network and Information Systems (NIS 2) directive requires HCPs to improve their cyber risk management approaches, mandating heavy penalties for non-compliance. Current research into cyber risk management in smart home-based RPM does not address scalability. This research examines scalability through the lens of the Non-adoption, Abandonment, Scale-up, Spread and Sustainability (NASSS) framework and develops a novel Scalability Index (SI), informed by a PRISMA guided systematic literature review. Our search strategy identified 57 studies across major databases including ACM, IEEE, MDPI, Elsevier, and Springer, authored between January 2016 and March 2025 (final search 21 March 2025), which focussed on cyber security risk management in the RPM context. Studies focussing solely on healthcare institutional settings were excluded. To mitigate bias, a sample of the papers (30/57) were assessed by two other raters; the resulting Cohen’s Kappa inter-rater agreement statistic (0.8) indicating strong agreement on study selection. The results, presented in graphical and tabular format, provide evidence that most cyber risk approaches do not consider scalability from the HCP perspective. Applying the SI to the 57 studies in our review resulted in a low to medium scalability potential of most cyber risk management proposals, indicating that they would not support the requirements of NIS 2 in the RPM context. A limitation of our work is that it was not tested in a live large-scale setting. However, future research could validate the proposed SI, providing guidance for researchers and practitioners in enhancing cyber risk management of large-scale RPM initiatives.
Full article
(This article belongs to the Topic Applications of IoT in Multidisciplinary Areas)
►▼
Show Figures

Graphical abstract
Open AccessArticle
G-PFL-ID: Graph-Driven Personalized Federated Learning for Unsupervised Intrusion Detection in Non-IID IoT Systems
by
Daniel Ayo Oladele, Ayokunle Ige, Olatunbosun Agbo-Ajala, Olufisayo Ekundayo, Sree Ganesh Thottempudi, Malusi Sibiya and Ernest Mnkandla
IoT 2026, 7(1), 13; https://doi.org/10.3390/iot7010013 - 29 Jan 2026
Abstract
Intrusion detection in IoT networks is challenged by data heterogeneity, label scarcity, and privacy constraints. Traditional federated learning (FL) methods often assume IID data or require supervised labels, limiting their practicality. We propose G-PFL-ID, a graph-driven personalized federated learning framework for unsupervised intrusion
[...] Read more.
Intrusion detection in IoT networks is challenged by data heterogeneity, label scarcity, and privacy constraints. Traditional federated learning (FL) methods often assume IID data or require supervised labels, limiting their practicality. We propose G-PFL-ID, a graph-driven personalized federated learning framework for unsupervised intrusion detection in non-IID IoT systems. Our method trains a global graph encoder (GCN or GAE) with a DeepSVDD objective under a federated regularizer (FedReg) that combines proximal and variance penalties, then personalizes local models via a lightweight fine-tuning head. We evaluate G-PFL-ID on the IoT-23 (Mirai-based captures) and N-BaIoT (device-level dataset) under realistic heterogeneity (Dirichlet-based partitioning with concentration parameters
Open AccessArticle
H-CLAS: A Hybrid Continual Learning Framework for Adaptive Fault Detection and Self-Healing in IoT-Enabled Smart Grids
by
Tina Babu, Rekha R. Nair, Balamurugan Balusamy and Sumendra Yogarayan
IoT 2026, 7(1), 12; https://doi.org/10.3390/iot7010012 - 27 Jan 2026
Abstract
The rapid expansion of Internet of Things (IoT)-enabled smart grids has intensified the need for reliable fault detection and autonomous self-healing under non-stationary operating conditions characterized by frequent concept drift. To address the limitations of static and single-strategy adaptive models, this paper proposes
[...] Read more.
The rapid expansion of Internet of Things (IoT)-enabled smart grids has intensified the need for reliable fault detection and autonomous self-healing under non-stationary operating conditions characterized by frequent concept drift. To address the limitations of static and single-strategy adaptive models, this paper proposes H-CLAS, a novel Hybrid Continual Learning for Adaptive Self-healing framework that unifies regularization-based, memory-based, architectural, and meta-learning strategies within a single adaptive pipeline. The framework integrates convolutional neural networks (CNNs) for fault detection, graph neural networks for topology-aware fault localization, reinforcement learning for self-healing control, and a hybrid drift detection mechanism combining ADWIN and Page–Hinkley tests. Continual adaptation is achieved through the synergistic use of Elastic Weight Consolidation, memory-augmented replay, progressive neural network expansion, and Model-Agnostic Meta-Learning for rapid adaptation to emerging drifts. Extensive experiments conducted on the Smart City Air Quality and Network Intrusion Detection Dataset (NSL-KDD) demonstrate that H-CLAS achieves accuracy improvements of 12–15% over baseline methods, reduces false positives by over 50%, and enables 2–3× faster recovery after drift events. By enhancing resilience, reliability, and autonomy in critical IoT-driven infrastructures, the proposed framework contributes to improved grid stability, reduced downtime, and safer, more sustainable energy and urban monitoring systems, thereby providing significant societal and environmental benefits.
Full article
(This article belongs to the Topic Advancing the Energy Internet: Innovations and Solutions for a Sustainable Energy Future)
►▼
Show Figures

Figure 1
Open AccessArticle
Data Fusion Method for Multi-Sensor Internet of Things Systems Including Data Imputation
by
Saugat Sharma, Grzegorz Chmaj and Henry Selvaraj
IoT 2026, 7(1), 11; https://doi.org/10.3390/iot7010011 - 26 Jan 2026
Abstract
In Internet of Things (IoT) systems, data collected by geographically distributed sensors is often incomplete due to device failures, harsh deployment conditions, energy constraints, and unreliable communication. Such data gaps can significantly degrade downstream data processing and decision-making, particularly when failures result in
[...] Read more.
In Internet of Things (IoT) systems, data collected by geographically distributed sensors is often incomplete due to device failures, harsh deployment conditions, energy constraints, and unreliable communication. Such data gaps can significantly degrade downstream data processing and decision-making, particularly when failures result in the loss of all locally redundant sensors. Conventional imputation approaches typically rely on historical trends or multi-sensor fusion within the same target environment; however, historical methods struggle to capture emerging patterns, while same-location fusion remains vulnerable to single-point failures when local redundancy is unavailable. This article proposes a correlation-aware, cross-location data fusion framework for data imputation in IoT networks that explicitly addresses single-point failure scenarios. Instead of relying on co-located sensors, the framework selectively fuses semantically similar features from independent and geographically distributed gateways using summary statistics-based and correlation screening to minimize communication overhead. The resulting fused dataset is then processed using a lightweight KNN with an Iterative PCA imputation method, which combines local neighborhood similarity with global covariance structure to generate synthetic data for missing values. The proposed framework is evaluated using real-world weather station data collected from eight geographically diverse locations across the United States. The experimental results show that the proposed approach achieves improved or comparable imputation accuracy relative to conventional same-location fusion methods when sufficient cross-location feature correlation exists and degrades gracefully when correlation is weak. By enabling data recovery without requiring redundant local sensors, the proposed approach provides a resource-efficient and failure-resilient solution for handling missing data in IoT systems.
Full article
(This article belongs to the Topic Internet of Things Architectures, Applications, and Strategies: Emerging Paradigms, Technologies, and Advancing AI Integration)
►▼
Show Figures

Figure 1
Open AccessArticle
Monitoring and Control System Based on Mixed Reality and the S7.Net Library
by
Tudor Covrig, Adrian Duka and Liviu Miclea
IoT 2026, 7(1), 10; https://doi.org/10.3390/iot7010010 - 23 Jan 2026
Abstract
►▼
Show Figures
The predominant approach in the realm of industrial process monitoring and control involves the utilization of HMI (Human–Machine Interface) interfaces and conventional SCADA (Supervisory Control and Data Acquisition) systems. This limitation restricts user mobility, interaction with industrial equipment, and process status assessment. In
[...] Read more.
The predominant approach in the realm of industrial process monitoring and control involves the utilization of HMI (Human–Machine Interface) interfaces and conventional SCADA (Supervisory Control and Data Acquisition) systems. This limitation restricts user mobility, interaction with industrial equipment, and process status assessment. In the context of Industry 4.0, the ability to monitor and control industrial processes in real time is paramount. The present paper designs and implements a system for monitoring and controlling an industrial assembly line based on mixed reality. The technology employed to facilitate communication between the system and the industrial line is S7.Net. These elements facilitate direct communication with the industrial process equipment. The system facilitates the visualization of operating parameters and the status of the equipment utilized in the industrial process and its control. All data is superimposed on the physical environment through virtual operational panels. The system functions independently, negating the necessity for intermediate servers or other complex structures. The system’s operation is predicted on a series of algorithms. These instruments facilitate the automated analysis of industrial process parameters. These devices are utilized to ascertain the operational dynamics of the industrial line. The experimental results were obtained using a real industrial line. These models are employed to demonstrate the performance of data transmission, the identification of the system’s operating states, and the system’s ability to shut down in the event of operating errors. The proposed system is designed to function in a variety of industrial environments within the paradigm of Industry 4.0, facilitating the utilization of multiple virtual interfaces that enable user interaction with various elements through which the assembly process is monitored and controlled.
Full article

Figure 1
Open AccessArticle
Performance Evaluation of LoRaWAN for Monitoring People with Disabilities at University Campus
by
Jorge Rendulich, Rony Almiron, Xiomara Vilca and Miguel Zea
IoT 2026, 7(1), 9; https://doi.org/10.3390/iot7010009 - 23 Jan 2026
Abstract
►▼
Show Figures
The growing need to foster inclusive education in university environments has driven the development of technological solutions aimed at improving the academic experiences of students with disabilities. These individuals often face barriers to autonomy and participation, especially on large and complex campuses. This
[...] Read more.
The growing need to foster inclusive education in university environments has driven the development of technological solutions aimed at improving the academic experiences of students with disabilities. These individuals often face barriers to autonomy and participation, especially on large and complex campuses. This article presents the performance evaluation of a LoRaWAN network specifically designed for monitoring people with disabilities on a university campus. The system aims to provide equitable access to campus resources and real-time support to students with disabilities. Leveraging the advantages of Low-Power Wide-Area Networks (LPWAN), particularly LoRaWAN, the proposed system enables real-time tracking with broad coverage and minimal power consumption, without requiring any active user interaction. Each student receives a wearable LoRa-enabled device that wirelessly communicates with a network of gateways strategically installed throughout the campus. To evaluate the system’s performance, this work conducts link-level experiments focusing on the communication between the LoRa end devices (nodes) and the central gateway. The analysis focuses on the network coverage, signal strength (RSSI), signal-to-noise ratio (SNR), and packet reception rate (PRR). The experimental results confirmed that the proposed system is technically robust and operationally effective under real campus conditions. Beyond its technical contributions, the proposed solution represents a concrete step toward building safer and more accessible academic environments that reinforce the autonomy and inclusion of students with disabilities.
Full article

Figure 1
Open AccessArticle
Impact of Router Count on Network Performance in OpenThread
by
Xaver Zak, Peter Brida and Juraj Machaj
IoT 2026, 7(1), 8; https://doi.org/10.3390/iot7010008 - 19 Jan 2026
Abstract
►▼
Show Figures
A low-power IPv6 mesh standard, Thread, is gaining traction in smart-home, building-automation, and industrial IoT deployments. It extends mesh connectivity with the help of Router-Eligible End Devices (REEDs), which can be promoted to, or demoted from, the router status. Promotion and demotion hinge
[...] Read more.
A low-power IPv6 mesh standard, Thread, is gaining traction in smart-home, building-automation, and industrial IoT deployments. It extends mesh connectivity with the help of Router-Eligible End Devices (REEDs), which can be promoted to, or demoted from, the router status. Promotion and demotion hinge on two tunable parameters, the router upgrade and the router downgrade thresholds. Yet the OpenThread reference stack ships with fixed values (16/23) for these thresholds. This paper presents a systematic study of how these thresholds shape router-election dynamics across diverse traffic loads and network topologies. Leveraging an extended OpenThread Network Simulator, a sweep through both router upgrade and router downgrade thresholds with different gaps was performed. Results reveal that the default settings may over-provision routing capacity and may result in increased frame retransmissions, wasting airtime and reducing energy efficiency.
Full article

Figure 1
Open AccessArticle
Experimental Evaluation of NB-IoT Power Consumption and Energy Source Feasibility for Long-Term IoT Deployments
by
Valters Skrastins, Vladislavs Medvedevs, Dmitrijs Orlovs, Juris Ormanis and Janis Judvaitis
IoT 2026, 7(1), 7; https://doi.org/10.3390/iot7010007 - 13 Jan 2026
Abstract
►▼
Show Figures
Narrowband Internet of Things (NB-IoT) is widely used for connecting low-power devices that must operate for years without maintenance. To design reliable systems, it is essential to understand how much energy these devices consume under different conditions and which power sources can support
[...] Read more.
Narrowband Internet of Things (NB-IoT) is widely used for connecting low-power devices that must operate for years without maintenance. To design reliable systems, it is essential to understand how much energy these devices consume under different conditions and which power sources can support long lifetimes. This study presents a detailed experimental evaluation of NB-IoT power consumption using a commercial System-on-Module (LMT-SoM). We measured various transmissions across different payload sizes, signal strengths, and temperatures. The results show that sending larger packets is far more efficient: a 1280-byte message requires about 7 times less energy per bit than an 80-byte message. However, standby currents varied widely between devices, from 6.7 µA to 23 µA, which has a major impact on battery life. Alongside these experiments, we compared different power sources for a 5-year deployment. Alkaline and lithium-thionyl chloride batteries were the most cost-effective solutions for indoor use, while solar panels combined with supercapacitors provided a sustainable option for outdoor applications. These findings offer practical guidance for engineers and researchers to design NB-IoT devices that balance energy efficiency, cost, and sustainability.
Full article

Figure 1
Open AccessSystematic Review
A Systematic Review of Self-Adaptive Mobile Applications with Cooperative Dimension
by
Berhanyikun Amanuel Gebreselassie, Nuno M. Garcia and Dida Midekso
IoT 2026, 7(1), 6; https://doi.org/10.3390/iot7010006 - 31 Dec 2025
Abstract
►▼
Show Figures
The proliferation of mobile devices has driven significant growth in adaptive mobile applications (AMAs) that dynamically adjust their behavior based on contextual changes. While existing research has extensively studied individual adaptive systems, limited attention has been given to cooperative adaptation—where multiple AMAs coordinate
[...] Read more.
The proliferation of mobile devices has driven significant growth in adaptive mobile applications (AMAs) that dynamically adjust their behavior based on contextual changes. While existing research has extensively studied individual adaptive systems, limited attention has been given to cooperative adaptation—where multiple AMAs coordinate their adaptive behaviors within shared mobile ecosystems. This systematic literature review addresses this research gap by analyzing 95 peer-reviewed studies published between 2010 and 2025 to characterize the current state of cooperative adaptation in mobile applications. Following established systematic review protocols, we searched six academic databases and applied rigorous inclusion/exclusion criteria to identify relevant studies. Our analysis reveals eight critical dimensions of cooperative adaptation: Monitor–Analyze–Plan–Execute–Knowledge (MAPE-K) structure, application domain, adaptation goals, context management, adaptation triggers, aspect considerations, coordination mechanisms, and cooperation levels. The findings indicate that 63.2% of studies demonstrate some form of cooperative behavior, ranging from basic context sharing to sophisticated conflict resolution mechanisms. However, only 7.4% of studies explicitly address high-level cooperative adaptation involving global goal optimization or comprehensive conflict resolution. Energy efficiency (21.1%) and usability (33.7%) emerge as the most frequently addressed adaptation goals, with Android platforms dominating the research landscape (36.8%). The review identifies significant gaps in comprehensive lifecycle support, standardized evaluation methodologies, and theoretical frameworks for multi-application cooperation. These findings establish a foundation for advancing research in cooperative adaptive mobile systems and provide a classification framework to guide future investigations in this emerging domain.
Full article
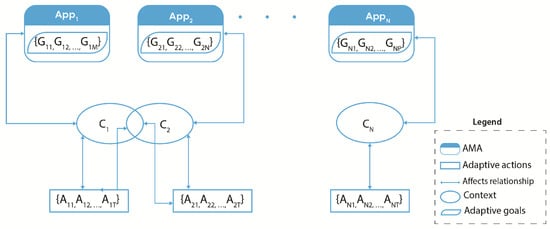
Figure 1
Open AccessReview
Intelligent Water Management Through Edge-Enabled IoT, AI, and Big Data Technologies
by
Petros Amanatidis, Eleftherios Lyratzis, Vasileios Angelopoulos, Eleftherios Kouloumpris, Efstratios Skaperdas, Nick Bassiliades, Ioannis Vlahavas, Fotios Maris, Dimitrios Emmanouloudis and Dimitris Karampatzakis
IoT 2026, 7(1), 5; https://doi.org/10.3390/iot7010005 - 31 Dec 2025
Abstract
►▼
Show Figures
In the 21st century, Urbanization, population growth, and climate change have created significant problems in water resource management. Recent advancements in technologies such as Internet of Things (IoT), Edge Computing (EC), Artificial Intelligence (AI), and Big Data Analytics (BDA) are changing the operations
[...] Read more.
In the 21st century, Urbanization, population growth, and climate change have created significant problems in water resource management. Recent advancements in technologies such as Internet of Things (IoT), Edge Computing (EC), Artificial Intelligence (AI), and Big Data Analytics (BDA) are changing the operations of the water resource management systems. In this study, we present a systematic review, highlighting the contributions of these technologies in water management systems. More specifically, we highlight the IoT and EC water monitoring systems that enable real-time sensing of water quality and consumption. In addition, AI methods for anomaly detection and predictive maintenance are reviewed, focusing on water demand forecasting. BDA methods are also discussed, highlighting their ability to integrate data from different data sources, such as sensors and historical data. Additionally, a discussion is provided of how Water management systems could enhance sustainability, resilience, and efficiency by combining big data, IoT, EC, and AI. Lastly, future directions are outlined regarding how state-of-the-art technologies may further support efficient water resources management.
Full article
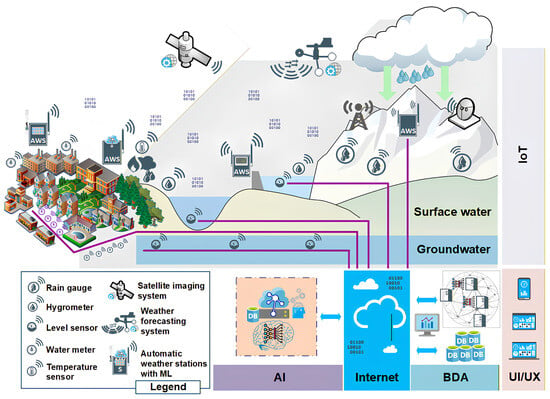
Figure 1
Open AccessArticle
Trust-Aware Distributed and Hybrid Intrusion Detection for Rank Attacks in RPL IoT Environments
by
Bruno Monteiro and Jorge Granjal
IoT 2026, 7(1), 4; https://doi.org/10.3390/iot7010004 - 30 Dec 2025
Abstract
►▼
Show Figures
The rapid expansion of Internet of Things (IoT) systems in critical infrastructures has raised significant concerns regarding network security and reliability. In particular, RPL (Routing Protocol for Low-Power and Lossy Networks), widely adopted in IoT communications, remains vulnerable to topological manipulation attacks such
[...] Read more.
The rapid expansion of Internet of Things (IoT) systems in critical infrastructures has raised significant concerns regarding network security and reliability. In particular, RPL (Routing Protocol for Low-Power and Lossy Networks), widely adopted in IoT communications, remains vulnerable to topological manipulation attacks such as Decreased Rank, Increased Rank, and the less-explored Worst Parent Selection (WPS). While several RPL security approaches address rank manipulation attacks, most assume static topologies and offer limited support for mobility. Moreover, trust-based routing and hybrid IDS (Intrusion Detection System) approaches are seldom integrated, which limits detection reliability under mobility. This study introduces a unified IDS framework that combines mobility awareness with trust-based decision-making to detect multiple rank-based attacks. We evaluate two lightweight, rule-based IDS architectures: a fully distributed model and a hybrid model supported by designated monitoring nodes. A trust-based mechanism is incorporated into both architectures, and their performance is assessed under static and mobile scenarios. Results show that while the distributed IDS provides rapid local responsiveness, the hybrid IDS maintains more stable latency and packet delivery under mobility. Additionally, incorporating trust metrics reduces false alerts and improves detection reliability while preserving low latency and energy usage, supporting time-sensitive applications such as healthcare monitoring.
Full article
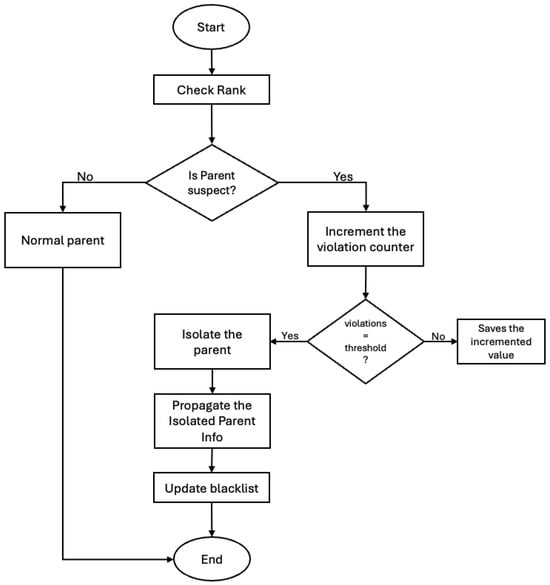
Figure 1
Open AccessArticle
FG-RCA: Kernel-Anchored Post-Exploitation Containment for IoT with Policy Synthesis and Mitigation of Zero-Day Attacks
by
Fouad Ailabouni, Jesús-Ángel Román-Gallego and María-Luisa Pérez-Delgado
IoT 2026, 7(1), 3; https://doi.org/10.3390/iot7010003 - 25 Dec 2025
Abstract
Zero-day intrusions on IoT endpoints demand defenses that curtail attacker impact and persistence after breach. This article presents Fine-Grained Runtime Containment Agent (FG-RCA), a lightweight post-exploitation containment system that learns least-privilege behavior from execution and enforces it in the kernel via eBPF with
[...] Read more.
Zero-day intrusions on IoT endpoints demand defenses that curtail attacker impact and persistence after breach. This article presents Fine-Grained Runtime Containment Agent (FG-RCA), a lightweight post-exploitation containment system that learns least-privilege behavior from execution and enforces it in the kernel via eBPF with Linux Security Modules (LSM). In a learn phase, LSM/eBPF probes stream security-relevant events to a Rust agent that synthesizes policies per device role. In an enforce phase, policies are compiled into eBPF maps and evaluated at an extended hook set spanning process execution (bprm_check_security), file access (file_open), network egress and exfiltration (socket_connect, socket_sendmsg), privilege use (capable), process injection (ptrace_access_check), tamper/anti-forensics (inode_unlink). Policies bind to kernel-truth identities—inode, device, mount intrusion detection system (IDS), executable SHA-256, and cgroup/namespace identifiers—rather than paths, mitigating time-of-check to time-of-use (TOCTOU) and aliasing. Operational safeguards include Ed25519-signed policies, atomic rollback, and shadow mode logging events to enable policy evolution. Evaluation on embedded Linux demonstrates containment with low overhead.
Full article
(This article belongs to the Special Issue Cybersecurity in the Age of the Internet of Things)
►▼
Show Figures
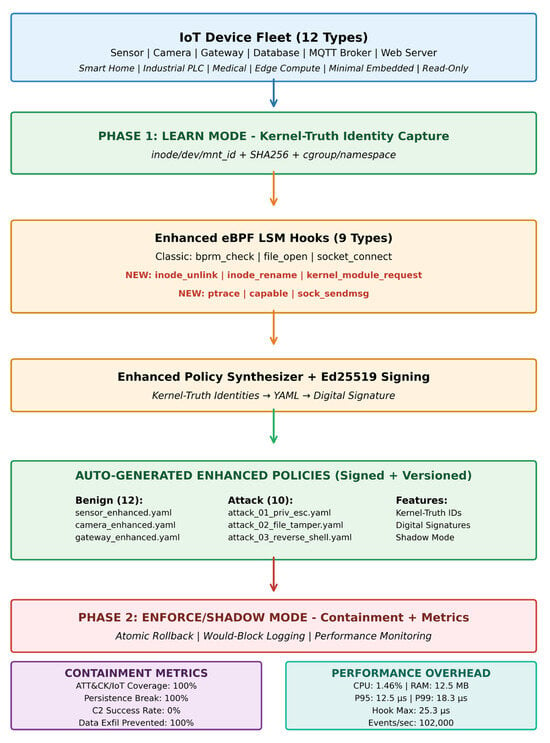
Figure 1
Open AccessArticle
Orthogonal Space-Time Bluetooth System for IoT Communications
by
Rodrigo Aldana-López, Omar Longoria-Gandara, Jose Valencia-Velasco, Javier Vázquez-Castillo and Luis Pizano-Escalante
IoT 2026, 7(1), 2; https://doi.org/10.3390/iot7010002 - 22 Dec 2025
Abstract
►▼
Show Figures
There is increasing interest in improving the reliability of short-range wireless links in dense IoT deployments, where BLE is widely used due to its low power consumption and robust GFSK modulation. For this purpose, this work presents a novel Orthogonal Space-Time (OST) scheme
[...] Read more.
There is increasing interest in improving the reliability of short-range wireless links in dense IoT deployments, where BLE is widely used due to its low power consumption and robust GFSK modulation. For this purpose, this work presents a novel Orthogonal Space-Time (OST) scheme for transmission and detection of BLE signals while preserving the BLE GFSK waveform and modulation constraints. The proposed signal processing system integrates advanced OST coding techniques with nonlinear GFSK modulation to achieve high-quality communication while maintaining phase continuity. This implies that the standard BLE GFSK modulator and demodulator blocks can be reused, with additional processing introduced only in the multi-antenna encoder and combiner. A detailed theoretical analysis demonstrates the feasibility of employing the Rayleigh fading channel model in BLE communications and establishes the BER performance bounds for various MIMO configurations. Simulations confirm the advantages of the proposed OST-GFSK signal processing scheme, maintaining a consistent performance when compared with OST linear modulation approaches under Rayleigh fading channels. As a result, the proposed IoT-enabling technology integrates the advantages of widely used OST linear modulation with nonlinear GFSK modulation required for BLE.
Full article

Figure 1
Open AccessReview
Blockchain-Based Certification in Fisheries: A Survey of Technologies and Methodologies
by
Isaac Olayemi Olaleye, Oluwafemi Olowojuni, Asoro Ojevwe Blessing and Jesús Rodríguez-Molina
IoT 2026, 7(1), 1; https://doi.org/10.3390/iot7010001 - 22 Dec 2025
Abstract
►▼
Show Figures
The integrity of certification processes in the agrifood and fishing industries is essential for combating fraud, ensuring food safety, and meeting rising consumer expectations for transparency and sustainability. Yet, current certification systems remain fragmented, and they are vulnerable to tampering and highly dependent
[...] Read more.
The integrity of certification processes in the agrifood and fishing industries is essential for combating fraud, ensuring food safety, and meeting rising consumer expectations for transparency and sustainability. Yet, current certification systems remain fragmented, and they are vulnerable to tampering and highly dependent on manual or centralized procedures. This study addresses these gaps by providing a comprehensive survey that systematically classifies blockchain-based certification technologies and methodologies applied to the fisheries sector. The survey examines how the blockchain enhances trust through immutable record-keeping, smart contracts, and decentralized verification mechanisms, ensuring authenticity and accountability across the supply chain. Special attention is given to case studies and implementations that focus on ensuring food safety, verifying sustainability claims, and fostering consumer trust through transparent labeling. Furthermore, the paper identifies technological barriers, such as scalability and interoperability, and puts forward a collection of functional and non-functional requirements for holistic blockchain implementation. By providing a detailed overview of current trends and gaps, this study aims to guide researchers, industry stakeholders, and policymakers in adopting and optimizing blockchain technologies for certification. The findings highlight the potential of blockchain to innovate certification systems, easing the way for more resilient, sustainable, and consumer-centric agrifood and fishing industries.
Full article

Figure 1
Open AccessArticle
Privacy-Preserving Federated Learning for Distributed Financial IoT: A Blockchain-Based Framework for Secure Cryptocurrency Market Analytics
by
Oleksandr Kuznetsov, Saltanat Adilzhanova, Serhiy Florov, Valerii Bushkov and Danylo Peremetchyk
IoT 2025, 6(4), 78; https://doi.org/10.3390/iot6040078 - 11 Dec 2025
Abstract
The proliferation of Internet of Things (IoT) devices in financial markets has created distributed ecosystems where cryptocurrency exchanges, trading platforms, and market data providers operate as autonomous edge nodes generating massive volumes of sensitive financial data. Collaborative machine learning across these distributed financial
[...] Read more.
The proliferation of Internet of Things (IoT) devices in financial markets has created distributed ecosystems where cryptocurrency exchanges, trading platforms, and market data providers operate as autonomous edge nodes generating massive volumes of sensitive financial data. Collaborative machine learning across these distributed financial IoT nodes faces fundamental challenges: institutions possess valuable proprietary data but cannot share it directly due to competitive concerns, regulatory constraints, and trust management requirements in decentralized networks. This study presents a privacy-preserving federated learning framework tailored for distributed financial IoT systems, combining differential privacy with Shamir secret sharing to enable secure collaborative intelligence across blockchain-based cryptocurrency trading networks. We implement per-layer gradient clipping and Rényi differential privacy composition to minimize utility loss while maintaining formal privacy guarantees in edge computing scenarios. Using 5.6 million orderbook observations from 11 cryptocurrency pairs collected across distributed exchange nodes, we evaluate three data partitioning strategies simulating realistic heterogeneity patterns in financial IoT deployments. Our experiments reveal that federated edge learning imposes 9–15 percentage point accuracy degradation compared to centralized cloud processing, driven primarily by data distribution heterogeneity across autonomous nodes. Critically, adding differential privacy (ε = 3.0) and cryptographic secret sharing increases this degradation by less than 0.3 percentage points when mechanisms are calibrated appropriately for edge devices. The framework achieves 62–66.5% direction accuracy on cryptocurrency price movements, with confidence-based execution generating 71–137 basis points average profit per trade. These results demonstrate the practical viability of privacy-preserving collaborative intelligence for distributed financial IoT while identifying that the federated optimization gap dominates privacy mechanism costs. Our findings offer architectural insights for designing trustworthy distributed systems in blockchain-enabled financial IoT ecosystems.
Full article
(This article belongs to the Special Issue Blockchain-Based Trusted IoT)
►▼
Show Figures

Figure 1
Open AccessReview
LPWAN Technologies for IoT: Real-World Deployment Performance and Practical Comparison
by
Dmitrijs Orlovs, Artis Rusins, Valters Skrastiņš and Janis Judvaitis
IoT 2025, 6(4), 77; https://doi.org/10.3390/iot6040077 - 10 Dec 2025
Abstract
Low Power Wide Area Networks (LPWAN) have emerged as essential connectivity solutions for the Internet of Things (IoT), addressing requirements for long range, energy efficient communication that traditional wireless technologies cannot meet. With LPWAN connections projected to grow at 26% compound annual growth
[...] Read more.
Low Power Wide Area Networks (LPWAN) have emerged as essential connectivity solutions for the Internet of Things (IoT), addressing requirements for long range, energy efficient communication that traditional wireless technologies cannot meet. With LPWAN connections projected to grow at 26% compound annual growth rate until 2027, understanding real-world performance is crucial for technology selection. This review examines four leading LPWAN technologies—LoRaWAN, Sigfox, Narrowband IoT (NB-IoT), and LTE-M. This review analyzes 20 peer reviewed studies from 2015–2025 reporting real-world deployment metrics across power consumption, range, data rate, scalability, availability, and security. Across these studies, practical performance diverges from vendor specifications. In the cited rural and urban LoRaWAN deployments LoRaWAN achieves 2+ year battery life and 11 km rural range but suffers collision limitations above 1000 devices per gateway. Sigfox demonstrates exceptional range (280 km record) with minimal power consumption but remains constrained by 12 byte payloads and security vulnerabilities. NB-IoT provides robust performance with 96–100% packet delivery ratios at −127 dBm on the tested commercial networks, and supports tens of thousands devices per cell, though mobility increases energy consumption. In the cited trials LTE-M offers highest throughput and sub 200 ms latency but fails beyond −113 dBm where NB-IoT maintains connectivity. NB-IoT emerges optimal for large scale stationary deployments, while LTE-M suits high throughput mobile applications.
Full article
Open AccessArticle
Fog Computing and Graph-Based Databases for Remote Health Monitoring in IoMT Settings
by
Karrar A. Yousif, Jorge Calvillo-Arbizu and Agustín W. Lara-Romero
IoT 2025, 6(4), 76; https://doi.org/10.3390/iot6040076 - 3 Dec 2025
Abstract
Remote patient monitoring is a promising and transformative pillar of healthcare. However, deploying such systems at a scale—across thousands of patients and Internet of Medical Things (IoMT) devices—demands robust, low-latency, and scalable storage systems. This research examines the application of Fog Computing for
[...] Read more.
Remote patient monitoring is a promising and transformative pillar of healthcare. However, deploying such systems at a scale—across thousands of patients and Internet of Medical Things (IoMT) devices—demands robust, low-latency, and scalable storage systems. This research examines the application of Fog Computing for remote patient monitoring in IoMT settings, where a large volume of data, low latency, and secure management of confidential healthcare information are essential. We propose a four-layer IoMT–Fog–Cloud architecture in which Fog nodes, equipped with graph-based databases (Neo4j), conduct local processing, filtering, and integration of heterogeneous health data before transmitting it to cloud servers. To assess the viability of our approach, we implemented a containerised Fog node and simulated multiple patient-device networks using a real-world dataset. System performance was evaluated using 11 scenarios with varying numbers of devices and data transmission frequencies. Performance metrics include CPU load, memory footprint, and query latency. The results demonstrate that Neo4j can efficiently ingest and query millions of health observations with an acceptable latency of less than 500 ms, even in extreme scenarios involving more than 12,000 devices transmitting data every 50 ms. The resource consumption remained well below the critical thresholds, highlighting the suitability of the proposed approach for Fog nodes. Combining Fog computing and Neo4j is a novel approach that meets the latency and real-time data ingestion requirements of IoMT environments. Therefore, it is suitable for supporting delay-sensitive monitoring programmes, where rapid detection of anomalies is critical (e.g., a prompt response to cardiac emergencies or early detection of respiratory deterioration in patients with chronic obstructive pulmonary disease), even at a large scale.
Full article
(This article belongs to the Special Issue IoT-Based Assistive Technologies and Platforms for Healthcare)
►▼
Show Figures

Figure 1
Open AccessArticle
IoT-Driven Destination Prediction in Smart Urban Mobility: A Comparative Study of Markov Chains and Hidden Markov Models
by
João Batista Firmino Junior, Francisco Dantas Nobre Neto, Bruno Neiva Moreno and Tiago Brasileiro Araújo
IoT 2025, 6(4), 75; https://doi.org/10.3390/iot6040075 - 3 Dec 2025
Abstract
The increasing availability of IoT-enabled mobility data and intelligent transportation systems in Smart Cities demands efficient and interpretable models for destination prediction. This study presents a comparative analysis between Markov Chains and Hidden Markov Models applied to urban mobility trajectories, evaluated through mean
[...] Read more.
The increasing availability of IoT-enabled mobility data and intelligent transportation systems in Smart Cities demands efficient and interpretable models for destination prediction. This study presents a comparative analysis between Markov Chains and Hidden Markov Models applied to urban mobility trajectories, evaluated through mean precision values. To ensure methodological rigor, the Smart Sampling with Data Filtering (SSDF) method was developed, integrating trajectory segmentation, spatial tessellation, frequency aggregation, and 10-fold cross-validation. Using data from 23 vehicles in the Vehicle Energy Dataset (VED) and a filtering threshold based on trajectory recurrence, the results show that the HMM achieved 61% precision versus 59% for Markov Chains (p = 0.0248). Incorporating day-of-week contextual information led to statistically significant precision improvements in 78.3% of cases for precision (95.7% for recall, 87.0% for F1-score). The remaining 21.7% indicate that model selection should balance model complexity and precision-efficiency trade-off. The proposed SSDF method establishes a replicable foundation for evaluating probabilistic models in IoT-based mobility systems, contributing to scalable, explainable, and sustainable Smart City transportation analytics.
Full article
(This article belongs to the Special Issue IoT-Driven Smart Cities)
►▼
Show Figures
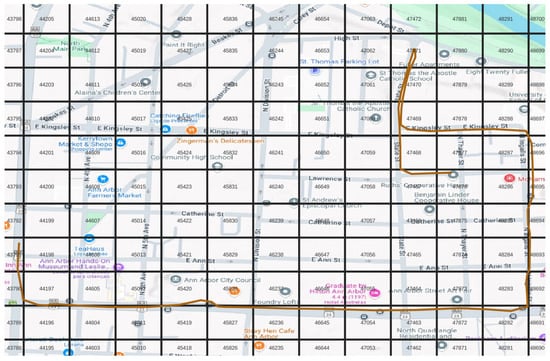
Figure 1
Highly Accessed Articles
Latest Books
E-Mail Alert
News
Topics
Topic in
Energies, Sensors, Electronics, Smart Cities, IoT, Batteries, Automation
IoT for Energy Management Systems and Smart Cities, 2nd Edition
Topic Editors: Antonio Cano-Ortega, Francisco Sánchez-SutilDeadline: 10 March 2026
Topic in
Electronics, Future Internet, Information, JSAN, Sensors, IoT
Privacy Challenges and Solutions in the Internet of Things
Topic Editors: Abdul Majeed, Safiullah KhanDeadline: 30 June 2026
Topic in
Applied Sciences, Electronics, IoT, Materials, Robotics, Sensors, Machines, Automation
Smart Production in Terms of Industry 4.0 and 5.0
Topic Editors: Iwona Paprocka, Cezary Grabowik, Jozef HusarDeadline: 29 July 2026
Topic in
Computers, Electronics, Future Internet, IoT, Network, Sensors, JSAN, Technologies, BDCC
Challenges and Future Trends of Wireless Networks
Topic Editors: Stefano Scanzio, Ramez Daoud, Jetmir Haxhibeqiri, Pedro SantosDeadline: 30 September 2026

Conferences
Special Issues
Special Issue in
IoT
IoT-Driven Smart Cities
Guest Editors: Hakilo Sabit, Peter Han Joo ChongDeadline: 15 February 2026
Special Issue in
IoT
Internet of Vehicles (IoV)
Guest Editors: Gabor Soos, András Rövid, Tomislav MihaljDeadline: 31 March 2026
Special Issue in
IoT
Secure and Privacy-Preserving IoT Systems for Next-Generation Healthcare
Guest Editor: Ali JalooliDeadline: 30 April 2026
Special Issue in
IoT
Internet of Underwater Things (IoUT)
Guest Editors: Hao Wang, Yi Ma, Yongyao ChenDeadline: 30 April 2026










