- Article
Interest as the Engine: Leveraging Diverse Hybrid Propagation for Influence Maximization in Interest-Based Social Networks
- Jian Li,
- Wei Liu and
- Wenxin Jiang
- + 2 authors
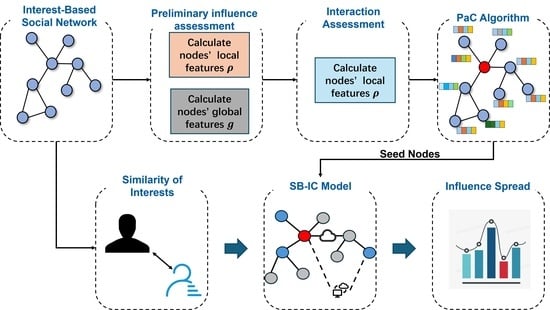
Influence maximization is a crucial research domain in social network analysis, playing a vital role in optimizing information dissemination and managing online public opinion. Traditional IM models focus on network topology, often overlooking user heterogeneity and server-driven propagation dynamics, which often leads to limited model adaptability. To overcome these shortcomings, this study proposes the “Social–Interest Hybrid Influence Maximization” (SIHIM) problem, which explicitly models the joint influence of social topology and user interest in server-mediated propagation, aiming to enhance the effectiveness of information propagation by integrating users’ social relationships and interest preferences. To model this problem, we develop a Server-Based Independent Cascading (SB-IC) model that captures the dynamics of influence propagation. Based on this model, we further propose a novel hybrid centrality algorithm named Pascal Centrality (PaC), which integrates both topological and interest-based attributes to efficiently identify key seed nodes while minimizing influence overlap. Experimental evaluations on ten real-world social network datasets demonstrate that PaC improves influence spread by 5.22% under the standard IC model and by 7.04% under the SB-IC model, outperforming nine state-of-the-art algorithms. These findings underscore the effectiveness and adaptability of the proposed algorithm in complex scenarios.
19 December 2025