1. Introduction
This paper discusses the global trend of aging due to the fact that human life has recently been increasing. For inheritance, research has been conducted based on a transparent blockchain [
1,
2,
3,
4,
5], in which the authors sought to research blockchain actively in the field of authentication. Nonetheless, many people encounter legal snags due to problems with a wills of inheritance. In this paper, an artificial intelligence (AI) system is used in various verification works for will and testament identification. Legal issues using artificial intelligence systems have recently arisen and, in addition, inheritance has many needs. In order to verify testament videos and wills, etc. with regard to inheritance, we mostly use core blockchain technologies, also called distributed ledger, which have been around for decades. Blockchain technology is immutable and transparent, and it has properties such as acidity. This allows trust to be established between parties that do not know each other without the need for a trusted third party to intervene, enabling transactions without the help of an intermediary. It also talks about the verification of various General Data Protection Regulations (GDPRs). We use the resilient distributed dataset (RDD); faster Convolutional Neural Networks (CNN) algorithm; legacy inheritance validation deep learning blockchain model, which is a method for researching the industry-leading verification blockchain; and flexible distributed dataset RDD algorithm as a multichannel blockchain platform core algorithm, and propose a legacy heritage inheritance blockchain research architecture [
6,
7,
8,
9,
10] for solving problems. In addition, the RDD faster CNN algorithm is a recent technology in deep learning, and there is a need to verify legal effectiveness for inheritance. However, inheritance is a very sensitive issue, which already has many issues and difficulties that it has inherited. Our objective is to introduce verification work on the blockchain agreement algorithm and a verification algorithm of artificial intelligence faster CNN. Therefore, our research on smart contract love and verification of the latest block chain dataset was conducted using the most accurately verifiable RDD faster CNN algorithm and verified based on the research model based on the Markov Chain Monte Carlo. Finally, our research results were drawn based on a variety of artificial intelligence and blockchain.
2. Related Work
To prevent the denial of certification for inheritance, this study examined the neural engine for the technology and artificial intelligence of blockchain certification and conducted preliminary research on the law, artificial intelligence law, blockchain, and GDPR as the protection of personal information.
2.1. Artificial Intelligent for Raw Data
Artificial intelligence is used to verify wills and identify unequal wills of inheritance. Legal issues that have been resolved using artificial intelligence system are also common these days. Therefore, major countries around the world continue to pursue discussions on artificial intelligence-related policies and legislation by communicating extensively with stakeholders instead of ending discussion in a one-off manner. The EU Commission has formed an independent group of experts to develop guidelines for artificial intelligence ethics, and it plans to continue communicating with stakeholders in the future. Legal discussions for this inheritance are also being carried out actively. In order to accommodate new technologies such as the establishment of a foundation for inheritance, the legal system is being reorganized quickly, strengthening the fairness and accountability of algorithms, and also pushing for legislation to prevent misuse of artificial intelligence. Germany, Japan, and other countries have quickly enacted laws allowing inheritance, and some U.S. state governments have actually legislated measures to regulate the misuse of artificial intelligence. Moreover, leaking of personal information is inevitable in the inheritance of miscalculations. We are preparing for the era of data-based artificial intelligence by promoting the balance of protection and utilization of personal information by strengthening the rights of information subjects, while increasing the level of personal information data and utilization [
11,
12,
13].
In addition, the EU’s GDPR has strengthened the rights of information subjects by allowing the use of aliased information without the consent of the information subjects to enhance the utilization of personal information, while at the same time introducing the right to refuse profiling. We are also creating an autonomous, flexible regulatory system by establishing ethical standards, standardizing, and establishing certification systems for matters considered difficult or premature due to inheritance legislation.
National institutions such as the EU (European Union), international organizations such as the Organization for Economic Cooperation and Development (OECD), the United Nations Educational, Scientific, and Cultural Organization (UNESCO), and organizations such as the Association of Electrical and Electronic Engineers are actively discussing ethical standards for the introduction of artificial intelligence. Therefore, artificial intelligence neuron engines for inheritance are actively used (see
Figure 1).
2.2. Blockchain for Raw Data
There is a huge need to resolve the issue of inheritance. In order to verify these willful images and wills of inheritance, we mostly use core blockchain technologies, also called distributed ledger, which have been around for decades. Blockchain technology is invariant and transparent and has characteristics such as ash acidity. This enables the formation of trust between parties who do not know each other without the need for a reliable third-party intervention and enables setting the transaction price without the assistance of a broker. This increases efficiency through a dramatic reduction in transaction costs. Many people see new possibilities of democracy and market principles, especially in decentralization. Nonetheless, some predict that blockchain technology will bring about fundamental change in the legal system itself; furthermore, some argue that existing laws cannot be applied to relationships regulated by the blockchain. Darn argued that the blockchain would be a means of evasion and crime, including speculation, fraud, money laundering, terrorism, and tax evasion [
14,
15,
16,
17,
18]. In some countries including China, cryptocurrency transactions have become illegal. Such conflict of views has delayed the readjustment of the relevant legal system and increased legal ambiguity. This uncertainty is preventing the development and spread of blockchain technology, which offers many advantages [
19,
20,
21].
Therefore, at this point in time, it is most important to analyze the legal issues surrounding blockchain technology and find a direction for improvement. Because of the versatility of blockchain, the legal issues also vary widely. They are divided into issues that are problematic in the implementation stage of the blockchain-based technology itself and issues that are problematic in the service stage based on the blockchain. In the infrastructure technology stage, privacy or personal information issues are the main problems (see
Figure 2).
2.3. GDPR for Raw Data
In order to claim an inheritance, the Personal Information Protection Act is an important issue. Since the GDPR is not a direct guideline but a regulation, separate implementation legislation by governments was not necessary, and it took effect on 25 May 2018, after a two-year grace period. The GDPR consists of 173 full pages and 99 articles. The text consists of a total of 11 chapters. The purpose of the GDPR is to prescribe the protection of natural persons and the free movement of personal information related to the processing of personal information. It also applies to information controllers or processors outside the EU that deal with the activities of providing goods or services to EU member states, whether paid or free, or with activities related to monitoring activities of EU member states within the EU. Once the GDPR takes full effect, a single regulation will be applied throughout the EU without any implementation legislation by EU member states. Under the GDPR, member states will establish independent supervisory authorities to receive and process personal information-related complaints and impose administrative sanctions, and each member’s supervisory body will cooperate with other regulators in mutual assistance and joint activities. One of the main means of strengthening the level of privacy protection in GDPR is to strengthen the requirements for consent [
22,
23,
24]. Effective consent under the GDPR shall be explicit consent for the purpose for which the personal information collected is used. Strengthening the rights of information subjects, particularly the right to be forgotten, is to be granted the right to require information subjects to delete such information from controllers without undue delay under certain circumstances, such as when the information subject withdraws its consent to personal information processing and there is no longer a legitimate basis for processing. The GDPR guarantees the so-called “data mobility” by recognizing the right to return personal information in a form that makes it easily transferrable to other controllers (see
Figure 3). In addition, the regulation of personal information is an area where such conflicts of interest constantly arise, so effectively disciplining our society in the course of development is not an easy problem to solve. Even in countries where there are already various special laws and general laws on personal information protection, there are many discussions on harmonizing conflicting interests and continuous efforts to improve the law.
In this process, looking at the EU’s legalization process and the resulting GDPR, which are considered to be at a counterpoint with the USA which has a significant impact on the global economy in the area of personal information protection, there could be many implications when gauging the future direction of our legislation. Given this recognition, the Commission examines legal and institutional efforts to regulate the protection of personal information in the EU prior to the enactment of the GDPR, and studies how personal information protection, GDPR, is used for discussions in the legislative process of the GDPR and final inheritance.
2.3.1. Council of Europe Convention 108
Europe has long been discussing the implementation of the Personal Information Protection Act for inheritance. The Council of Europe signed the Convention for the Protection of Individuals with regard to the Automatic Processing of Personal Data in 1981, which is commonly called Convention 108 (CETS No. 108). Convention 108 took effect in 1985, and it is noteworthy in terms of having legal binding force on the member states of the Convention. The agreement also had an important impact on the formation of the EU Data Protection Directive in 1995, which later became a milestone in the EU’s privacy. Convention 108 was ratified by 46 countries out of 47 European Council members, excluding Turkey. In addition, non-members of the European Council were also allowed to join the treaty, however, only Uruguay joined the treaty and ratified it. Convention 108 obliges parties to the Convention to reflect the basic principles under this Convention in domestic law, including the principle on the quality of information; the principle on the protection of special types of information (sensitive information), information security, additional safeguards for information subjects; and the principle of sanctions and relief of legal reserves in the establishment of exceptions and restrictions. In addition, regulations are in place to ensure the transfer of information between countries. However, these regulations have been based on past circumstances that failed to take into account the current high-level information processing environment, and the main contents of the regulations mostly define declarative content in an abstract manner instead of presenting specific criteria. To address this, the European Council established a special committee in 2013 to modernize Convention 108. In addition, such personal information protection needs to be overhauled for inheritance [
25,
26,
27].
2.3.2. U.S.-EU Safe Harbor Framework
The establishment of a legal system for inheritance has an important relationship. In order to meet the adequacy criteria for the transfer of information to third countries set by the EU Information Protection Guidelines, the USA promoted the Safe Harbor Framework to allow the transfer of personal information between countries in the EU and the USA, as U.S. companies complying with this principle would meet the adequacy of the EU Information Protection Guidelines. According to the Safe Harbor principle between the United States and the EU, if a company or organization in the United States voluntarily reports to the U.S. Department of Commerce it has complied with the Safe Harbor principle, it is deemed to be seeking appropriate privacy measures, and it may continue to receive information transfers from the EU. The Safe Harbor principle is the duty to inform the information subject of how the information collected will be used, including choice and on transfer, i.e., transfer only to institutions that follow the appropriate information protection principles, access to information, political rights, deletion rights, and security of information (reasonable integrity of information). In October 2015, however, the new EU-U.S. Privacy Shield which was promoted as the U.S.-EU Safe Harbor Framework was invalidated by a European Court of Justice ruling.
2.3.3. EU-U.S. Privacy Shield Framework
Political consensus has been reached between the EU Commission and the U.S. government for the transfer of new personal information between countries to replace the existing Safe Harbor for inheritance. According to this agreement, the EU Commission drafted the Privacy Shield and released the draft to gather various opinions. After the disclosure, the EU Working Party submitted a statement of opinion on the Privacy Shield, and the European Data Protection Supervisor also released a related opinion. In addition, the European Parliament went through a resolution process on the Privacy Shield. The process of agreeing with the U.S. government on the amendment was completed after revising the Privacy Shield’s draft, reflecting opinions from such agencies. The EU Commission then finalized the final draft of the Privacy Shield. The basic framework of the Privacy Shield is similar to the existing Safe Harbor. In other words, the Privacy Shield also operates under a self-certification system. In order for U.S.-based organizations to join the Privacy Shield system, they must apply to the Department of Commerce and go through self-certification procedures. Although joining the Privacy Shield itself is based on the discretion of the enterprises, once the entity has voluntarily certified and announced compliance with the principles of the Privacy Shield system, it can be enforced by domestic law in the United States. Nonetheless, the detailed principles of the Privacy Shield have been established in a way that expands the rights of information subjects and strengthens information protection as compared with the existing Safe Harbor system. Through the imposition of stronger obligations on companies managing information, companies that join the Privacy Shield system are subject to sanctions if they fail to comply with the Privacy Shield principle and are removed from the Privacy Shield list at the same time. In particular, the requirements for the transfer of personal information to third parties are strict. The Privacy Shield also suggests that the U.S. government provide clear safeguards and fulfill its transparency obligations when accessing information in order to regulate U.S. intelligence agencies’ access to personal information of EU member states, which has been controversial between the EU and the United States. Furthermore, it allows citizens of EU member states to receive relief for personal information infringement; in particular, it introduces an ombudsman system within the U.S. Department of Commerce to establish a compensation or relief system for the people of EU member states in the area of international intelligence activities.
3. Methodology for Research on Blockchain for Validation of Legacy Succession
There are sufficient conditions for many people to miscarry. A legacy requires notarization of a will and is a very complex and legal issue. Thus, this research method involves designing a research model that verifies using smart contours and shading of blockchain, Genesis block, etc.
3.1. Issue Raising
We are changing a lot about heritage, and wills of inheritance. The reason for this is that the social part of society is changing in order to solve legal issues and various problems in the future in preparation for death [
28,
29,
30,
31,
32]. There are so many problems, but heritage and wills are developing considerably and it is also the duty of a lawyer to do a medium escrow. In this paper, however, we would like to determine the research method based on the decentralized system of artificial intelligence neuronal blockchain. In the future, there will be various P2P (Peer To Peer) models and transactions between individuals. In order to match these diverse requirements, our objective is to study block nodes and deep learning techniques.
3.2. Research Methodology
The artificial intelligence blockchain research model is designed to enable getting an inheritance. Depth-first search refers to a graph where in individual elements are oriented in a particular direction and are constructed in a non-circulating structure (see
Figure 4). The DAG (Directed Acyclic Graph) uses phase alignment to represent priorities. Phase alignment is an expression of the order in which work should be done if it is actually done one at a time. In other words, the nodes are arranged in a row, in the order of the tasks. There are conditions for this phase alignment, with the order of the nodes facing from left to right. If there is a reverse node, it cannot be the right sequence of work. The phase alignment can be expressed in many different ways depending on the starting value and, in conclusion, an answer of one is not valid. The edge coming from the directional graph is called incoming outgoing edge. In addition, the number of incoming edges is called outdegree, the number of out-of-indegree edges. The first phase algorithm is simple and intuitive. First, look for nodes with a zero index for all nodes. An index of zero means that there is no work to be preceded by that operation. If more than one exists, choose one of them. Then, remove the edges leaving nodes A and remove A from the graph. Then, again find the node with a zero index on the remaining graph. When finished, remove the corresponding node and its outgoing edge from the graph. Repeating these operations results in reaching the last node and all nodes are phase aligned. For the second phase alignment algorithm, first, set visited to NO for all nodes. This means that no node has been printed yet. After that, create one empty linked list R, because we arrange nodes in the order in which they are sorted using phase and in the order in which they are sorted, using link list. Then, grab one node that you have not visited yet and run the DFS starting from that node. DFS checks the node it visited and runs DFS again if it has not been visited for node x adjacent to it. However, the difference from a typical DFS is the last line. For exiting, the repetition is when you visit all the nodes and have no place to go. The typical DFS has gone back, but here, we add that node to the linked list R.
Here, we briefly describe DFS (depth-first search). An ideologically applied tangle algorithm and a hash graph are applied to the Hedera hash graph. In the depth-first navigation graph, individual elements do not combine multiple transactions into a single block like a blockchain but are interconnected with each other. The depth-first navigation graph is an algorithm that samples the post-probability distribution of the parameter that Markov Chain Monte Carlo would like to know about in a probability space, in order to estimate the state of time t + 1, which is, then, followed by time t, on a time-t basis by random sampling. It is called MCMC for short. The Markov Chain Monte Carlo algorithm and depth-first search technique, a grafting DAG algorithm, were used to enhance the completeness of the algorithm. A method of fully navigating the branch before starting from the root node (or any other node) and moving on to the next branch was employed. This is similar to how to navigate the maze until it can go in one direction, and then, when it becomes impossible to go any further, it comes back to the nearest fork and goes in the other direction, in other words, deep exploration before wide exploration. Choose this method if you want to visit all nodes. Depth-first search (DFS) is simpler than width-first navigation (BFS) [
33,
34,
35,
36,
37]. Simple search speeds themselves are slower than width-first navigation (BFS). Thus, we used the DAG and DFS algorithms.
3.2.1. Resilient Distributed Dataset (RDD) Faster CNN Algorithm
Resilient distributed dataset is a read-only collection that is stored and divided into multiple machines in a cluster. Typical Spark programs are inputted into one or more RDDs followed by a series of transformations and transformed into target RDD sets. The word “elastic” means that, when there is a lost partition, Spark can recompute and automatically recover the processing of the RDD. Spark applications, jobs, stages, and tasks similar to MR use a technique called job. It consists of one map and one reduce using a single MapReduce job. Spark’s job is any directional non-circular graph. It consists of a stage (DAG). When Spark is run, the stage is split into multiple tasks, each running in parallel on a distributed RDD partition in the cluster such as the task in MapReduce. The job is always executed within the context of an application (represented by a Spark context instance) that provides RDD and shared variables. The RDDs of the Job performed within the same application can be accessed by other cached RDDs [
38].
3.2.2. Elastic Distributed Dataset RDD Algorithm
Flexible distributed datasets can simultaneously control transmission and action. This method of study provides two kinds of operators, transformation and action, to Spark RDD. Transformation helps to create new RDDs from existing RDDs. Run X (map) immediately. Mapping, grouping, aggregating, redistributing, sampling, RDD joins, and processing RDD set the actions that calculate a specific RDD and produce a certain result. The results are shown or stored externally and executed immediately. To realize RDD as a collection, calculate RDD statistics, sample a certain number of items in RDD, store RDD externally, and identify them as a transformational action. Check the return type, i.e., transformation on RDD. Or, when taking action, this is called the elastic distributed dataset RDD algorithm.
3.2.3. Multichannel Blockchain Platform Core Algorithm
The multichannel blockchain platform core study shows caching so that broadcast variables are serialized and sent to each incubator and can later be accessed whenever a task is needed. Broadcast variables are different from common variables that serialize as part of the closures passed over the network once per task. If Spark memory is sufficient, it will be stored in memory; if it is insufficient, it will be improved to a block generation structure by a channel that uses disk self-developed shading technology. It is also one of the software development methodologies using loosely coupled, designed to minimize dependence between SW modules so that they can be easily combined or dismantled. With this flexible coupling structure, we upgraded to a structure capable of accommodating various consensus algorithms and protocols. We suggest that P2P protocol can be changed for multichannel support, and that a message channel separator of 2 bytes is added to the P2P message header.
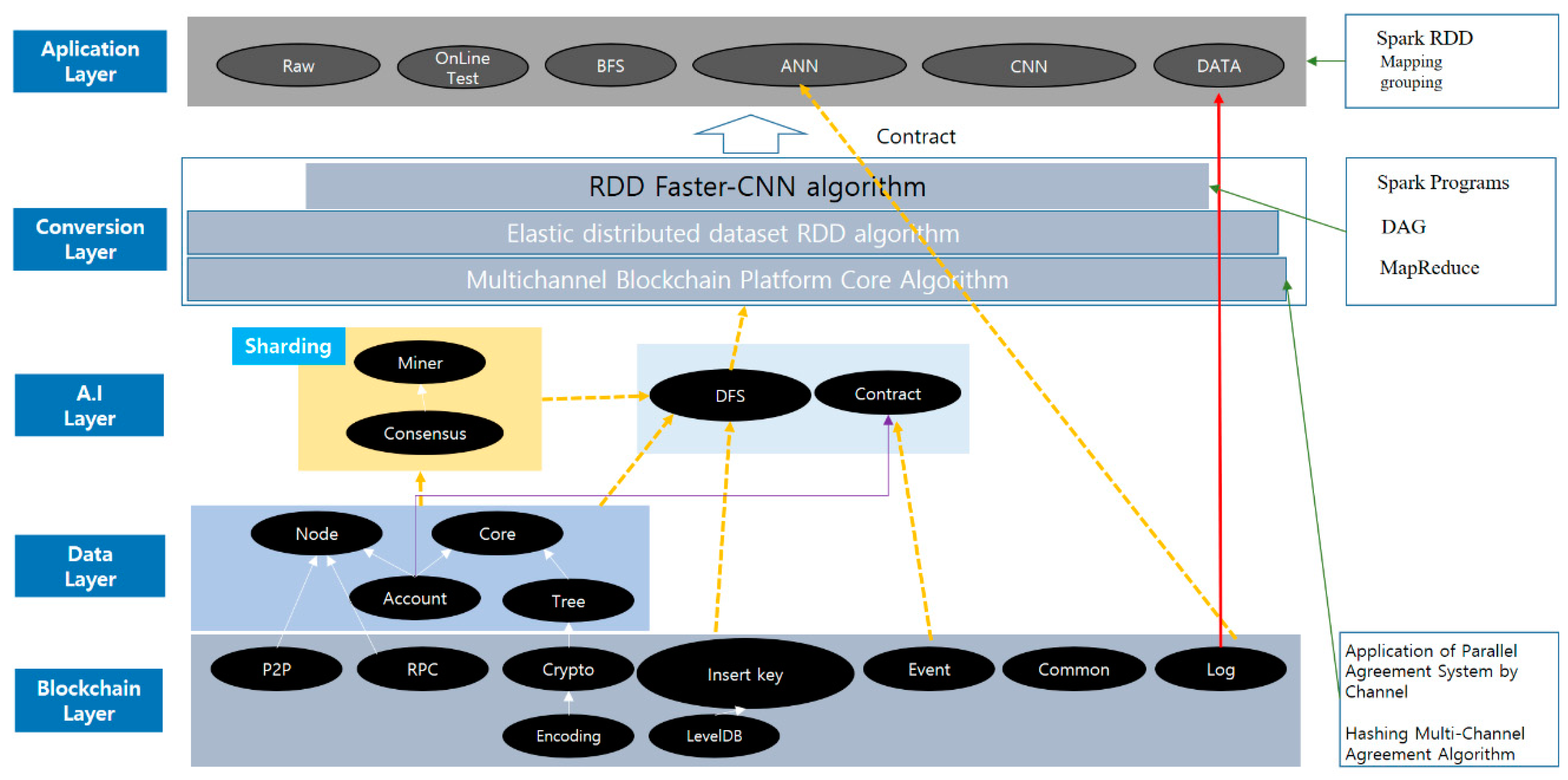
3.3. Legacy Inheritance Blockchain Research Architecture
This architecture, an inheritance blockchain, is designed to communicate between the minimum distance algorithm and the multichannel protocol-based node. A neuron is a nerve cell that forms the nervous system of living things; an artificial neuron is an abstraction of the functions of dendrite, soma, and axon that make up the neurons of living things. Similar to neurons in living things, artificial neural algorithms such as the DFS algorithm are expressed as pseudocode. DFS is similar to that previously seen in pre- and post-order navigation methods of the binary tree, therefore, it is most concise to represent it in recursive. Therefore, if the adjacent nodes visited is NO, it will recursively call itself in to proceed with the search. To return to the higher node here, because it was recursively called, the foreword would leave if it were satisfied. The call is terminated and returned to the function that called itself, where it is returned to the parent node, even if not specified otherwise, because the location is the same as the parent node. If the graph is disconnection or directional, DFS may not visit all nodes. In that case, repeat DFS and visit all nodes. A table is a special function called a hash function that specifies where to store it. The hash function algorithm is also cited. Hash tables use large arrays. A hash table has m slots from 0 to m − 1.
where U refers to a set of all possible keys, and m means the size of the table. The function that converts the key value into the appropriate index is called the hash function (h). For example, the easiest way to create a hash function is to assume that U is a set of positive integers, and that m is the size of the table. The index can be derived as follows:
This hash function always results in indices from 0 to m − 1. However, these functions are not actually used well because many important shortcomings occur (see
Figure 5).
As such, legacy inheritance blockchain architecture uses the necessary algorithms along with deep learning’s artificial neural network. This architecture is connected to the application layer based on the mapping and grouping methods of the Spark RDD model. Conversion layer’s RDD faster CNN algorithm also follows the values of Spark programs, MapReduce technology, and DAG. In addition, the application of parallel agreement system by channel and the hashing multichannel agreement algorithm have algorithms that apply to all algorithms belonging to the multichannel blockchain platform core algorithm.
3.3.1. Application of Parallel Agreement System by Channel
The block generator random selection algorithm is applied to at least three and up to 21 units and carries out parallel agreement by channels. The following channel balance optimization module randomly selects nodes with superior equity and computing resources. It also designs and implements an isolation message structure that only receives and executes channel-related messages and smart contracts subscribed to by nodes during multichannel. A channel balancer is an optimization module that considers the storage on a limited number of nodes to determine how many channels to allocate to how many nodes. An algorithm for channel assignment is required. The channel merge model is also joined with DFS (depth-first search) as a circuit algorithm. The order, preorder, and post order of the binary tree are all designed with DFS. Visiting the adjacent node of the graph, the DFS continues to enter the adjacent node of the node again and returns when the end is reached; it is designed very safely, and its performance is excellent. As with BFS, there must be a starting point, s, and the current node is checked as visited; if any of the adjacent nodes exist, the DFS goes to that node. The operation above is repeated continuously; when the end is reached, it comes back. If you have unvisited, you will go into that node and repeat the previous operation again. Eventually, when all turns are completed, they return to the starting node, s, and end if there are no more places to go, design these blockchain artificial intelligence nodes.
3.3.2. Hashing Multichannel Agreement Algorithm
In studying artificial intelligence multichannel, conflicts between data can occur. The reason for the collision is that only one data can be stored in a single slot, and chaining is used to prevent this. The data stored in each slot is made into a link list so that a lot of data can be stored. In other words, the slot will only have the address value of the first link list.
- (a)
Insert key
- −
Insert key, k, at the front of the list T[h(k)], time complexity O;
- −
If duplicate keys can come in and duplicate storage is not allowed, the list should be searched on insertion;
- −
Thus, the time complexity is proportional to the length of the link list.
- (b)
Searching for keys
- −
Search for and delete keys from the list T[h(k)];
- −
Time complexity is proportional to the length of the list in which the key is stored.
- (c)
Delete key
- −
Search for and delete keys from the list T[h(k)];
- −
Once the key has been retrieved and found, it can be deleted at O time.
It is also designed using ANN and hashing of artificial intelligence. It is a layer that contains many neurons. Among them, single layer ANN is the only layer made of neurons. It shows the structure of single layer ANN, with each circle indicating one neuron; the arrow indicates a neuron is connected. At this time, each connection is given a weight. There are certainly two layers in ANN, which makes you wonder why they are called single layer. While all ANNs have layers called input layers, the layer consisting of actual neurons in ANN uses output layers and hashing because the input layer simply conveys the given data.
3.3.3. Cross Entropy Error CPython
Cross entropy designs source codes that implement values of logs in Python and C languages. It supports preprocessing in the form of intermediate compilation, but it is not suitable because it does not support functional constraints in the aspect of the implementer.
3.4. Legacy Inheritance Blockchain Design
The inheritance artificial intelligence blockchain implements a channel-independent smart contract. Smart contracts for each channel cannot be called from other channels, and independent sandboxes are software management strategies that isolate critical system resources and other programs in an application, i.e., store and manage in the sandbox and design and implement mutual access control with operating system user and directory separation. It also implements multichannel blockchain application programming interface (API) and software development kit (SDK), provides multichannel node and information inquiry, transaction request, and smart contract distribution and execution API, and develops SDK by program development language. In addition, the blockchain installation and management tool works with the blockchain installation management module for the installation and management of the blockchain through web services to store the installation information in the database and to install the blockchain on the server to be installed. In addition, the command line interface for operating system-level scripts (command line interface) for the automatic installation of the blockchain and the generation of initial data adopts the way users and computers interact through terminals. Moreover, in designing the minimum path algorithm, BFS can do more than just visit all nodes on the graph, it gives the shortest path length for each node because the shortest path from s to the node belonging to Li is i. Thus, the following input outputs can be obtained as shown in
Figure 6.
- (a)
Input: Directional or no-way graph G = (V,E), and start node s belong to V;
- (b)
Output: for all nodes v.
- −
d(v) = the length (number of edges) of the shortest path from s to v,
- −
π(v) = the last node of v on the shortest path from s to v.
The pseudocode above is the code specifying d(v) and π(v).
3.5. Validated Unified Modeling Language (UML) and Source Code Designs
The unified modeling language (UML) design for inheritance is designed through class diagram. Neural model structure classes are inherited from block structures. Multi structure gets the value of the name and task. The channing structure receives each of the appends and the MaskCnnn structure (see
Figure 7).
Source codes are registered in Github (
https://github.com/erikzhang/leveldb), where various versions exist, and required source codes (
Figure 8) are verified by dividing the code in various directions into input, direct or no-way graphic G = (V,E) and start node belongs to V and output, for all nodes v (see
Figure 9).
4. Performance Evaluation and Limitations of the Research
4.1. Experimental Environment
4.1.1. Establishment of Operating Server Environment
In most cases, servers are built using Linux-affiliated operating systems.
The following are the programs that should be installed on the server:
In addition, various tools can be installed on the web server to support the function of the web application. To deploy a server, and then a web project to it, see Deploy a project.
4.1.2. CentOS 7.2 Server Installation (CentOS Download)
Minimal ISO;
Everything ISO;
DVD ISO.
We install and work on the Minimal ISO version here.
4.2. Experimental Conditions
Measure the total number of transactions processed per second per channel and measure the maximum value of a multichannel that can be created.
In addition, measure the time it takes for transactions to be processed, which cause changes in the state of two or more channels being managed (see
Table 1).
4.3. Classification of Motions
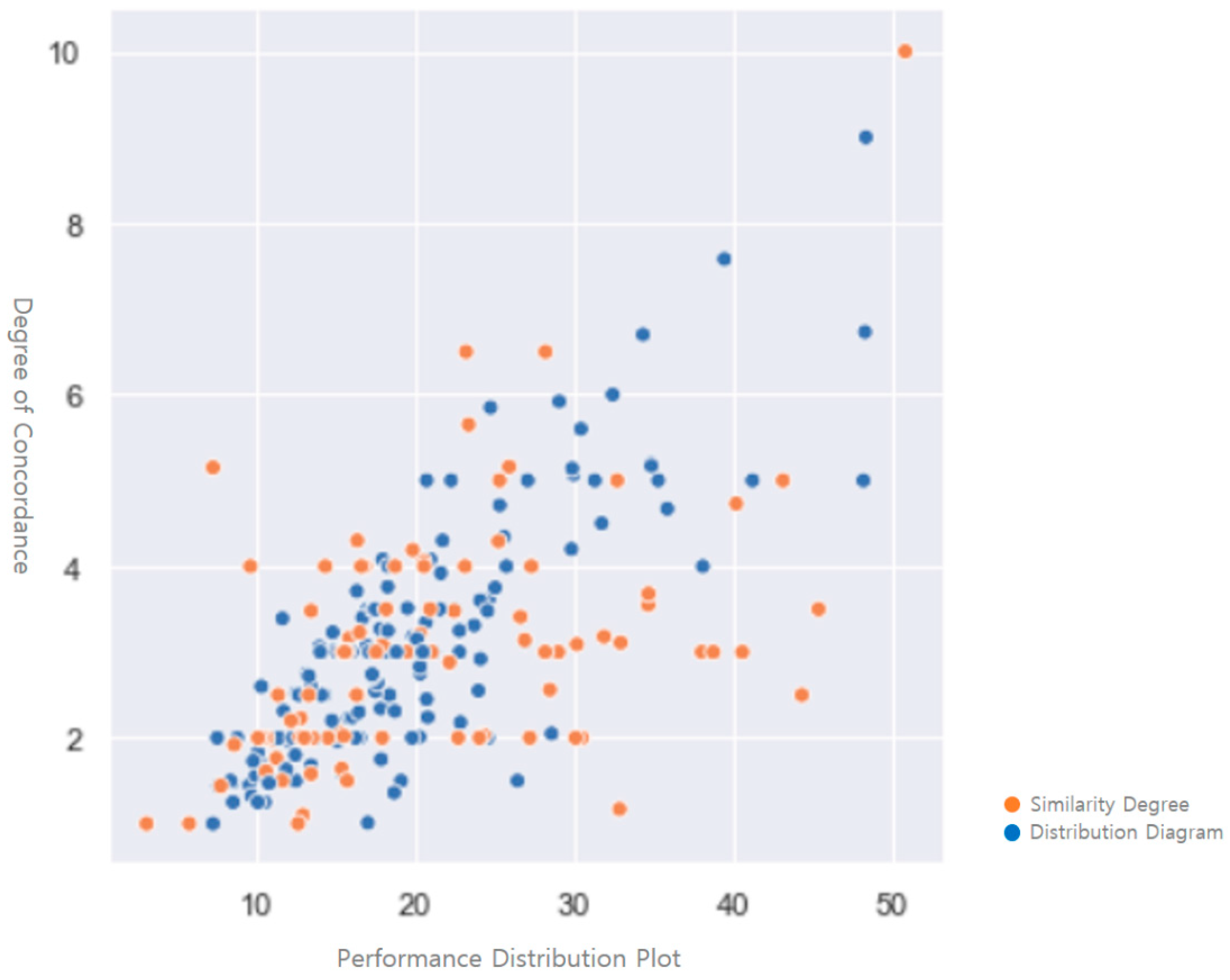
Using the artificial intelligence CNN algorithm, a block node was constructed for the suicide blockchain, and the first 150 nodes were designed to detect P2P between nodes using ANN and hashing of artificial intelligence. It is a layer that contains many neurons. Among them, single layer ANN is the only layer made of neurons. It shows the structure of single layer ANN, with each circle indicating one neuron; an arrow indicates a neuron is connected (see
Figure 10).
At this time, each connection is given weight; based on technology, an event-based health management system, a multichain block creation and maintenance protocol, and multichannel communication protocol were developed. The transaction parallel processing optimization and dynamic channel management modules were tested and verified by demonstration (see
Figure 11).
5. Discussion and Future Application Model
5.1. Discussion
In this paper, inheritance, wills, etc. are thought to be traded safely. There is still a lack of assessment platforms that can be evaluated for safe assets to inherit via wills and heritage. Everything should be fair and transparent. It was verified and tested using an AI blockchain agreement node, which is transparent, impartial, and decentralized. In addition, experimental data showed that the results of experiments using these verification models were about 4500 TPS. Through these experiments, the research results needed in the future were derived. In addition, we need to ensure stable verification and certification of personal information protection that we need. Moreover, the GDPR of Europe is closely related to our lives but is now being followed. In this study, research was conducted to contribute to various future studies based on a model in which such personal information is mounted.
5.2. Application Model
The demonstration model was developed based on the actual model. The empirical model is an asset management system for legacy, wills, etc. These asset management programs are based on artificial intelligence and blockchain for the future.
Figure 12 is the main screen of the asset management and will verification management blockchain management system. The main screen is certified through blockchain authentication.
In
Figure 13, unstructured data, such as video and voice, are inserted so that digital calculation can be controlled.
Figure 14 is a screen that specifies the date when an inheritance and will are made.
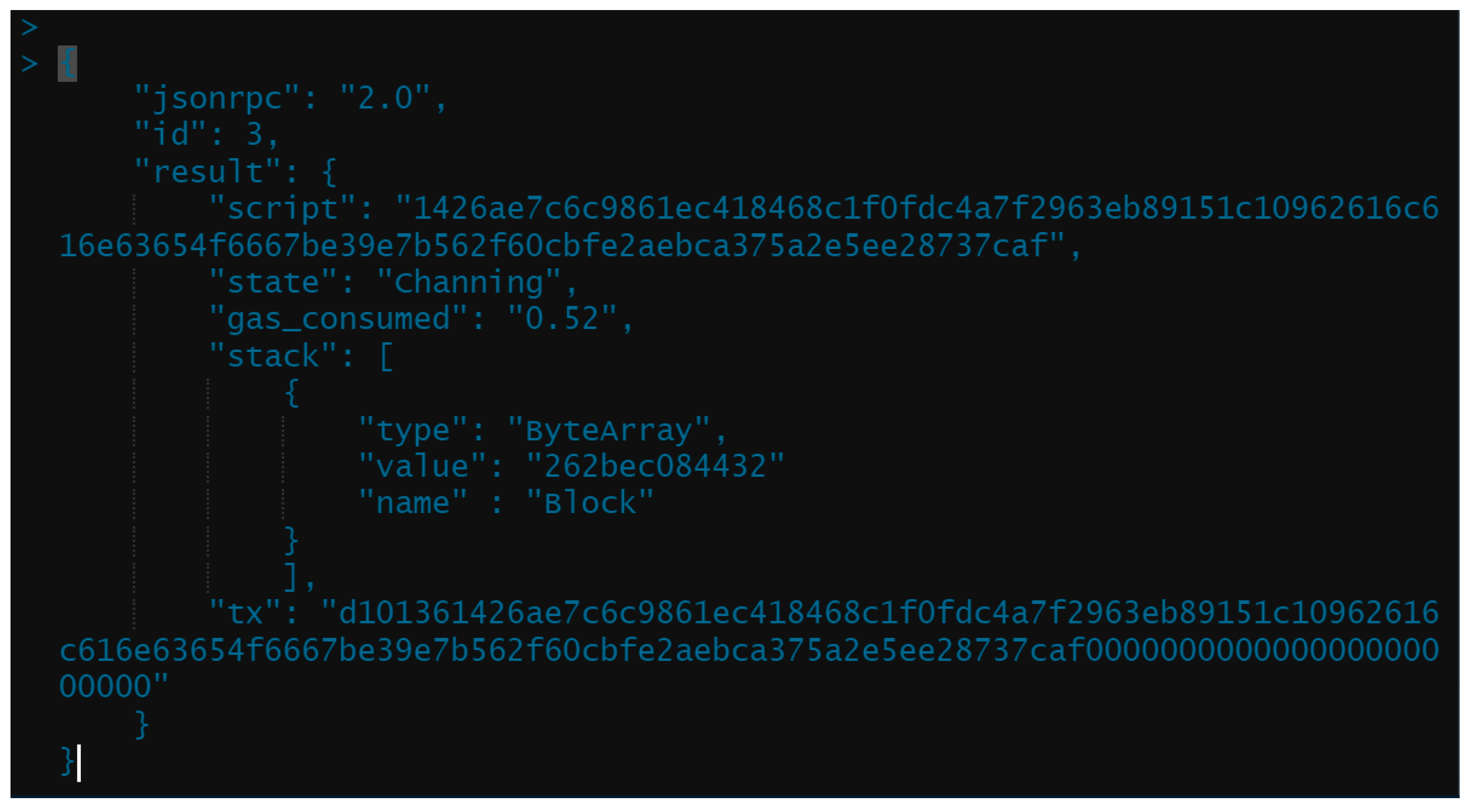
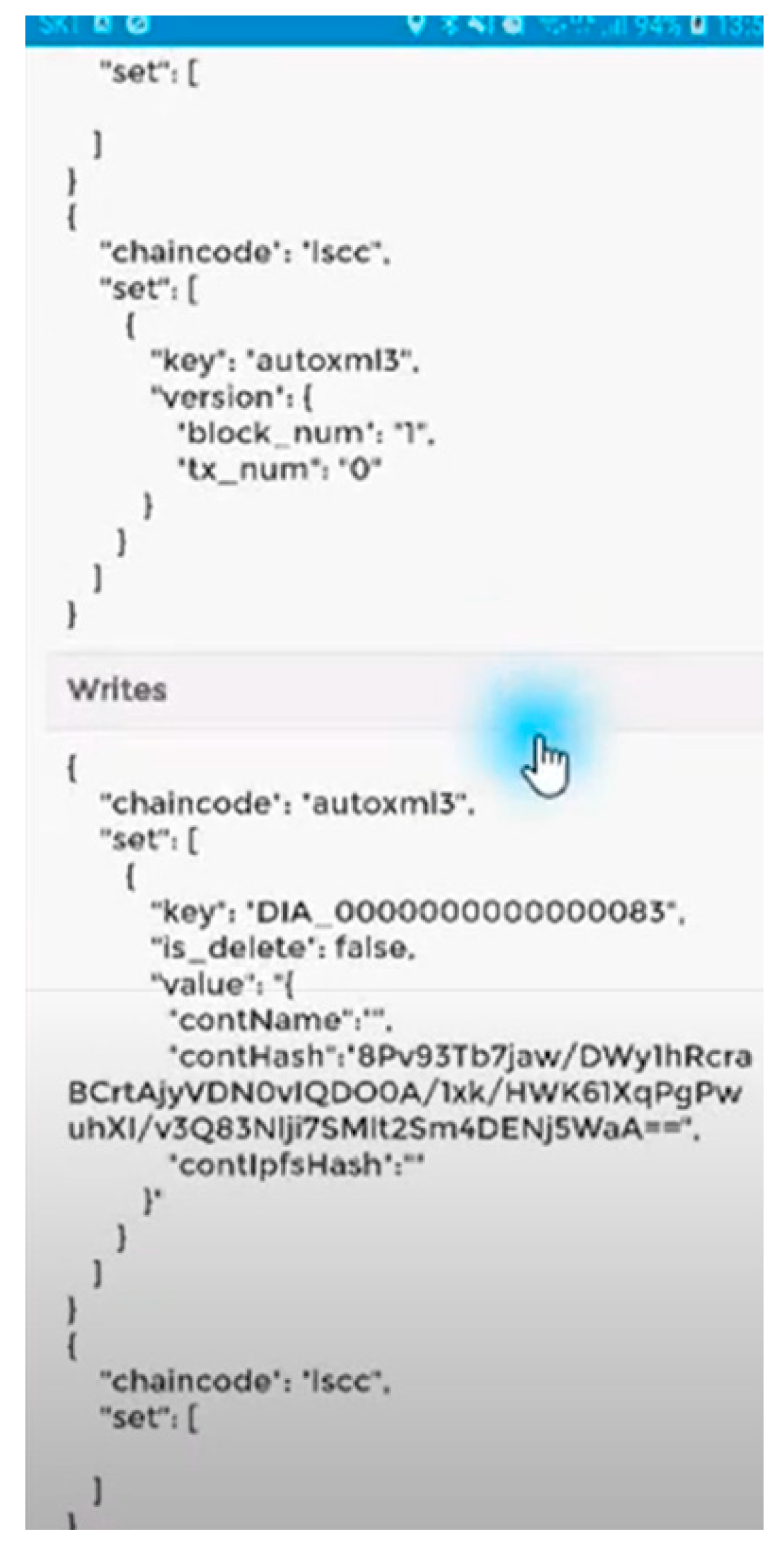
Figure 15 shows the task of creating hash codes by entering the information of the transaction ID into the blockchain node.
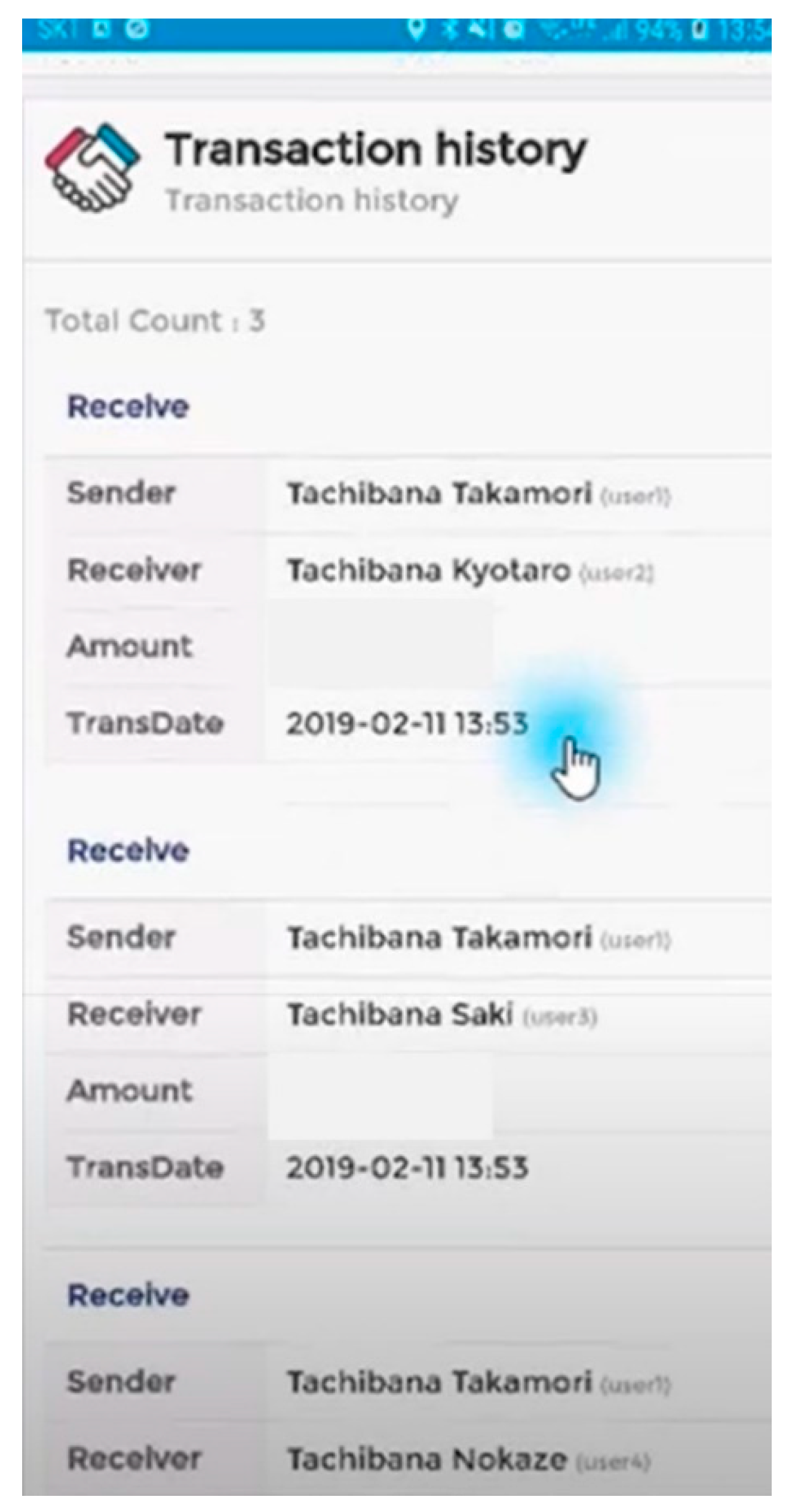
Figure 17 is a scenario of inheritance and smart contract.
Figure 18 shows the date when the entire inheritance was bequeathed and all the information.
Figure 19 is a screen that captures the entire process on the block.
6. Conclusions and Future Work
This paper is of interest to many people due to the fact that it is about wills of inheritance. Among various studies, however, there is no significant related research. Among them, blockchain can be used in the certification field. Nonetheless, it is true that many people still do not believe in the system, and that the problems of wills and inheritance are giving rise to legal issues. This study dealt with an artificial intelligence system, which was used in various verification works regaring identification of wills, verification, and unequal wills of inheritance. Recently, we attempted to resolve a lot of legal issues using an artificial intelligence system. Inheritance is an issue of many needs. In order to verify these willful images and wills of inheritance, we mostly used core blockchain technologies, also called distributed ledger, which have been around for decades. Blockchain technology is invariant and transparent and has characteristics such as ash acidity. This enables the formation of trust between parties who do not know each other without the need for a reliable third-party intervention and enables setting the transaction price without the assistance of a broker. We also talked about the verification of various GDPRs. Using an RDD faster CNN algorithm and a flexible distributed dataset RDD algorithm, we proposed a multichannel blockchain platform core algorithm, which is a method of research on acid-speed verification blockchain. We also presented a model for solving problems usisng legacy inheritance blockchain research architecture. Blockchain data processing connects this new block to the end of the blockchain, which has been going on for a long time just like the smart contract environment and chain. On the basis of the blockchain and artificial intelligence testing, the distribution plot is good with values close to 2 and 10, and the performance of the blockchain is about 4500 TPS. It also shows empirical models through node-to-node design to verify actual heritage. Implementing this artificial intelligence blockchain-based inheritance system is expected to become the cornerstone of further research.
Author Contributions
Conceptualization, S.-K.K. and J.-H.H.; Data curation, S.-K.K.; Formal analysis, S.-K.K. and J.-H.H.; Funding acquisition, J.-H.H.; Investigation, S.-K.K.; Methodology, J.-H.H.; Project administration, S.-K.K. and J.-H.H.; Resources, S.-K.K.; Software, S.-K.K. and J.-H.H.; Validation, J.-H.H.; Visualization, S.-K.K. and J.-H.H.; Writing—original draft, S.-K.K. and J.-H.H.; Writing—review & editing, J.-H.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (no. 2017R1C1B5077157).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| API | Application programming interface |
| ANN | Article neural network |
| DFS | Dept-first search |
| DNN | Deep neural network |
| GDPR | General Data Protection Regulation |
| EU | European Union |
| OECD | Organization for Economic Cooperation and Development |
| RDD | Resilient distributed dataset |
| SDK | Software development kit |
| UML | Unified modeling language |
| UNESCO | United Nations Educational, Scientific and Cultural Organization |
References
- Darwin, C. The Expression of Emotions in Animals and Man; Lond. Murray: London, UK, 1872. [Google Scholar]
- Eckman, J.; Meltzer, J.D.; Latane, B. Gregariousness in rats as a function of familiarity of environment. J. Personal. Soc. Psychol. 1969, 11, 107. [Google Scholar] [CrossRef]
- Bengio, Y.; Courville, A.; Vincent, P. Representation learning: A review and new perspectives. IEEE Trans. Pattern Anal. Mach. Intell. 2013, 35, 1798–1828. [Google Scholar] [CrossRef] [PubMed]
- Wachsmuth, I.; Lenzen, M.; Knoblich, G. Embodied Communication in Humans and Machines; Oxford University Press: Oxford, UK, 2008. [Google Scholar]
- Picard, R.W. Computer learning of subjectivity. ACM Comput. Surv. 1995, 27, 621–623. [Google Scholar] [CrossRef]
- Bizon, N. Efficiency and Sustainability of the Distributed Renewable Hybrid Power Systems Based on the Energy Internet, Blockchain Technology and Smart Contracts. Sustainability. Available online: https://www.mdpi.com/journal/sustainability/special_issues/Distributed_Renewable_Hybrid_Power_Systems (accessed on 6 May 2020).
- Löbbe, S.; Hackbarth, A. Chapter 15: The Transformation of the German Electricity Sector and the Emergence of New Business Models in Distributed Energy Systems; Elsevier: Amsterdam, The Netherlands, 2017; pp. 287–318. [Google Scholar]
- Keesstra, S.D.; Bouma, J.; Wallinga, J.; Tittonell, P.; Smith, P.; Cerdà, A.; Bardgett, R.D. The significance of soils and soil science towards realization of the United Nations Sustainable Development Goals. Soil 2016, 2, 111–128. [Google Scholar] [CrossRef]
- Chen, Y. Blockchain tokens and the potential democratization of entrepreneurship and innovation. Bus. Horiz. 2017, 61, 567–575. [Google Scholar] [CrossRef]
- Kshetri, N. Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inform. Manag. 2018, 39, 80–82. [Google Scholar] [CrossRef]
- Wang, W.C.; Chang, Y.J.; Wang, H.C. An Application of the Spatial Autocorrelation Method on the Change of Real Estate Prices in Taitung City. ISPRS Int. J. Geo Inf. 2019, 8, 249. [Google Scholar] [CrossRef]
- Jayantha, W.M.; Yung, E.H.K. Effect of Revitalisation of Historic Buildings on Retail Shop Values in Urban Renewal: An Empirical Analysis. Sustainability 2018, 10, 1418. [Google Scholar] [CrossRef]
- Trevor, W. Cosmology of artificial intelligence project: Libraries, makerspaces, community and AI literacy. ACM AI Matters 2020, 4, 134–140. [Google Scholar]
- Seo, Y.S.; Huh, J.H. Automatic emotion-based music classification for supporting intelligent IoT applications. Electronics 2019, 8, 164. [Google Scholar] [CrossRef]
- Watson, D.; Tellegen, A. Toward a consensual structure of mood. Psychol. Bull. 1985, 98, 219–235. [Google Scholar] [CrossRef] [PubMed]
- Huh, J.-H.; Kim, S.-K. The blockchain consensus algorithm for viable management of new and renewable energies. Sustainability 2019, 11, 3184. [Google Scholar] [CrossRef]
- Burford, G.; Hoover, E.; Velasco, I.; Janoušková, S.; Jimenez, A.; Piggot, G.; Harder, M.K. Bringing the “missing pillar” into sustainable development goals: Towards intersubjective values-based indicators. Sustainability 2013, 5, 3035–3059. [Google Scholar] [CrossRef]
- Gisbert, G. Policy: Base sustainable development goals on science. Nature 2012, 491, 35. [Google Scholar]
- Kuo, T.T.; Zavaleta, R.H.; Ohno-Machado, L. Comparison of blockchain platforms: A systematic review and healthcare examples. J. Am. Med. Inform. Assoc. 2019, 26, 462–478. [Google Scholar] [CrossRef] [PubMed]
- Macdonald, M.; Liu-Thorrold, L.; Julien, R. The blockchain: A Comparison of Platforms and Their Uses Beyond Bitcoin. 2017. Available online: https://www.researchgate.net/profile/Lisa_Liu-Thorrold/publication/313249614_The_Blockchain_A_Comparison_of_Platforms_and_Their_Uses_Beyond_Bitcoin/links/5894447baca27231daf63689/The-Blockchain-A-Comparison-of-Platforms-and-Their-Uses-Beyond-Bitcoin.pdf (accessed on 18 September 2020). [CrossRef]
- Beverly, Y.; Garcia-Molina, H. Pay: Micropayments for peer-to-peer systems. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–31 October 2003; ACM: New York, NY, USA, 2003; pp. 300–310. [Google Scholar]
- Savelyev, A. Copyright in the Blockchain era: Promises and Challenges. Comput. Law Secur. Rev. 2018, 34, 550–561. [Google Scholar] [CrossRef]
- Hajer, M.; Nilsson, M.; Raworth, K.; Bakker, P.; Berkhout, F.; De Boer, Y.; Kok, M. Beyond cockpit-ism: Four insights to enhance the transformative potential of the sustainable development goals. Sustainability 2015, 7, 1651–1660. [Google Scholar] [CrossRef]
- Lee, S.; Woo, H.; Shin, Y. Study on Personal Information Leak Detection Based on Machine Learning. Adv. Sci. Lett. 2017, 23, 12818–12821. [Google Scholar] [CrossRef]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Rusu, A.A.; Veness, J.; Bellemare, M.G.; Petersen, S. Human-level control through deep reinforcement learning. Nature 2015, 518, 529–533. [Google Scholar] [CrossRef]
- Wang, H.; He, D.; Ji, Y. Designated-verifier proof of assets for bitcoin exchange using elliptic curve cryptography. Future Gener. Comput. Syst. 2017, 21–24. [Google Scholar] [CrossRef]
- Bełej, M.; Figurska, M. 3D Modeling of Discontinuity in the Spatial Distribution of Apartment Prices Using Voronoi Diagrams. Remote Sens. 2019, 12, 2. [Google Scholar]
- Sodhro, A.H.; Pirbhulal, S.; de Albuquerque, V.H.C. Artificial Intelligence-Driven Mechanism for Edge Computing-Based Industrial Applications. IEEE Trans. Ind. Inform. 2019, 15, 4235–4243. [Google Scholar] [CrossRef]
- Silver, D.; Schrittwieser, J.; Simonyan, K.; Antonoglou, I.; Huang, A.; Guez, A.; Chen, Y. Mastering the game of go without human knowledge. Nature 2017, 550, 354–359. [Google Scholar] [CrossRef]
- DeepMind. AlphaGo Zero: Learning from the Scratch. Available online: https://deepmind.com/blog/alphago-zero-learning-scratch/ (accessed on 27 March 2020).
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerComWorkshops), Kona, HI, USA, 13–17 March 2017. [Google Scholar]
- Imbault, F.; Swiatek, M.; De Beaufort, R.; Plana, R. The green blockchain: Managing decentralized energy production and consumption. In Proceedings of the 2017 IEEE International Conference on Environment and Electrical Engineering and 2017 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Milan, Italy, 6–9 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–5. [Google Scholar]
- Underwood, S. Blockchain beyond Bitcoin; Communications of the ACM; ACM: New York, NY, USA, 2016; Volume 59, pp. 15–17. [Google Scholar]
- Chowdhury, M.J.; Ferdous, M.S.; Biswas, K.; Chowdhury, N.; Kayes, A.; Alazab, M.; Watters, P. A Comparative Analysis of Distributed Ledger Technology Platforms. IEEE Access 2019, 7, 167930–167943. [Google Scholar] [CrossRef]
- Kim, S.K.; Huh, J.H. A Study on the Improvement of Smart Grid Security Performance and Blockchain Smart Grid Perspective. Energies 2018, 11, 1973. [Google Scholar] [CrossRef]
- Livieratos, S.; Vogiatzaki, V.-E.; Cottis, P.G. A Generic Framework for the evaluation of the benefits expected from the smart grid. Energies 2013, 6, 988–1008. [Google Scholar] [CrossRef]
- Park, L.; Jang, Y.; Bae, H.; Lee, J.; Park, C.Y.; Cho, S. Automated energy scheduling algorithms for residential demand response systems. Energies 2017, 10, 1326. [Google Scholar] [CrossRef]
- Kessels, K.; Kraan, C.; Karg, L.; Maggiore, S.; Valkering, P.; Laes, E. Fostering residential demand response through dynamic pricing schemes: A behavioural review of smart grid pilots in Europe. Sustainability 2016, 8, 929. [Google Scholar] [CrossRef]
Figure 1.
Artificial intelligence architecture for raw data.
Figure 1.
Artificial intelligence architecture for raw data.
Figure 2.
Blockchain architecture for raw data.
Figure 2.
Blockchain architecture for raw data.
Figure 3.
General Data Protection Regulations (GDPR) for raw data (source, gdpr.kisa.or.kr/index.do).
Figure 3.
General Data Protection Regulations (GDPR) for raw data (source, gdpr.kisa.or.kr/index.do).
Figure 4.
Legacy inheritance validation deep learning blockchain model.
Figure 4.
Legacy inheritance validation deep learning blockchain model.
Figure 5.
Legacy inheritance blockchain research architecture.
Figure 5.
Legacy inheritance blockchain research architecture.
Figure 6.
Legacy data verification.
Figure 6.
Legacy data verification.
Figure 7.
Validated unified modeling language (UML) for class diagram.
Figure 7.
Validated unified modeling language (UML) for class diagram.
Figure 8.
Verification source code for NeuralModel Asset_id.
Figure 8.
Verification source code for NeuralModel Asset_id.
Figure 9.
Verification source code for block channing.
Figure 9.
Verification source code for block channing.
Figure 10.
Results of distribution and similarity measurement.
Figure 10.
Results of distribution and similarity measurement.
Figure 11.
Blockchain performance data (unit, TPS).
Figure 11.
Blockchain performance data (unit, TPS).
Figure 12.
Main member authentication system.
Figure 12.
Main member authentication system.
Figure 13.
Legacy inheritance verification screen.
Figure 13.
Legacy inheritance verification screen.
Figure 14.
Legacy inheritance smart contract screen.
Figure 14.
Legacy inheritance smart contract screen.
Figure 15.
Legacy inheritance smart contract storage screen.
Figure 15.
Legacy inheritance smart contract storage screen.
Figure 16.
Legacy inheritances smart contract hash storage screen.
Figure 16.
Legacy inheritances smart contract hash storage screen.
Figure 17.
Legacy inheritances smart contract sign storage screen.
Figure 17.
Legacy inheritances smart contract sign storage screen.
Figure 18.
Legacy inheritances smart contract hash storage screen.
Figure 18.
Legacy inheritances smart contract hash storage screen.
Figure 19.
Store inheritances hash tables screen.
Figure 19.
Store inheritances hash tables screen.
Table 1.
Experimental conditions for performance evaluation.
Table 1.
Experimental conditions for performance evaluation.
| Major Performance Spec | Unit | Evaluation Measuring Technique |
|---|
| Concurrent processing Transactions count | TPS | Measures the total number of transactions processed per second per channel |
| Number of concurrent transaction types | EA | Measure the maximum value of a multichannel that can be created |
| Rate of processing transactions that depend on more than one channel | Sec | Measure the time it takes for transactions to be processed, which cause changes in the state of two or more channels being managed |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).