Abstract
Unmanned-aerial-vehicle (UAV)-aided data collection for Internet of Things applications has attracted increasing attention. This paper investigates motion planning for UAV collecting low-power ground sensor node (SN) data in a dynamic jamming environment. We targeted minimizing the flight energy consumption via optimization of the UAV trajectory while considering the indispensable constraints which cover the collection data demodulation threshold, obstacle avoidance, data collection volume, and motion principle. Firstly, we formulate the UAV-aided data collection problem as an energy consumption minimization problem. To solve this nonconvex optimization problem, we rewrite the original problem by introducing relaxation variables and constructing equivalence constraints to obtain a new relaxation convex problem, which can be solved iteratively using the successive convex approximation (SCA) method. However, SCA is susceptible to initial values, especially in dynamic environments where fixed initial values may lead to a wide range of results, making it difficult to obtain a truly optimal solution to the optimization problem. To solve the initial value problem in dynamic environments, we further propose a communication-flight-corridor(CFC)-based initial path generation method to improve the reliability and convergence speed of the SCA method by constructing reliable communication regions and resilient secure paths in real time. Finally, simulation results validate the performance of the proposed algorithm compared to the benchmark algorithms under different parameter configurations.
1. Introduction
1.1. Background
Recently, communication supported by unmanned aerial vehicles (UAVs) has become an attractive technology in the field of wireless sensor networks (WSNs) for highly efficient data collection [1,2,3]. Most sensor nodes (SNs) are battery powered and deployed in a specific geographical area to sense and transmit the sensed information. At times, it is impractical to let these devices transmit or relay their sensed data to the base station through a multi-hop relay because of the high consumption of transmission energy. In the worst-case scenario, they may be out of range of each other’s transmissions, particularly in the case of interference. As a result, it can be very challenging to gather sensing data from such SNs and process them in time to help humans more efficiently. Sensor nodes (SNs) are processed in a timely manner to assist humans better in making decisions and responding to monitoring scenarios [4].
In this paper, we investigate the issue of the motion planning for UAV collecting low-power ground sensor node (SN) data in a dynamic jamming environment based on the following observation. In the past work, UAV-aided data collection scenarios were usually limited to simple path planning, which did not fully consider the principle of motion. Moreover, most of the past works are static environments or consider one-time offline global planning, and there is little research on dynamic environments that require real-time processing. Therefore, the research in this paper will build on past research to fully consider the motion constraints of UAVs and real-time planning in dynamic environments. We use the mobility and flexibility of UAVs for SN data collection. When the UAV flies into the effective communication range of the SN (satisfying the demodulation threshold), it is activated to transmit data within the effective communication range. To achieve full autonomy in UAV data collection, we have taken several aspects into account in the design. Firstly, the motion planning plays an essential role in generating safe and smooth motions which consider motion primitives, flight energy consumption, and flight time during the data collection mission [5]. Secondly, to ensure that the data can be collected to meet the demodulation threshold, it is also necessary to consider the effective communication area [6].
1.2. Prior Work
We focus on past work from two fields: motion planning and data collection. To generate smooth and safe trajectories for UAVs online, the authors in [7,8] presented the extraction of free space in the configuration space and utilized a range of convex shapes to represent the free space. The motion planning problem is formulated as restricting motion trajectories to convex graphs through convex optimization, which can be solved directly with a dedicated toolbox. However, the size of the area in which the convex shapes are constructed directly affects the local optimality of the trajectory. The authors in [9] proposed a zoning method that can be combined with a multi-stage optimal control formulation to accommodate complex forms of unobstructed areas in unstructured environments due to the presence of multiple obstacles within the predicted range. This method can effectively increase the free space for UAV planning. Other authors have proposed methods that are simpler and faster to calculate, such as the geometry-based method in [10], which constructs convex polyhedra by means of ellipsoidal expansion.
Moreover, to constrain effectively the entire trajectory within the convex shape together with its derivatives in the feasible space under the hard constraint, the authors in [11] employed a piecewise Bézier curve on the basis of Bernoulli’s polynomial to express the flight trajectory of the UAV. However, the order of the Bézier curve increases with the increase of control points, and a higher order can easily result in an “ill-conditioned” trajectory. To solve the problem of pathological Bézier curves under higher-order polynomials, the authors in [12] introduced B-spline curves, which have the advantages of Bézier curves while still being applicable to higher-order polynomial curves.
Collecting data from ground-based distributed SNs is among the crucial technologies for WSNs. The typical objectives of trajectory optimization are to minimize the mission time of the UAV [13,14,15], minimize energy consumption during the flight [16,17,18], maximize the amount of collected data [19,20], and maximize the amount of served sensors [21]. In addition to the basic UAV motion constraint, the data volume constraint is essential in all published research studies of UAV data collection. It is usually a non-convex constraint. In some studies, the communication rate required to meet the demodulation requirements is further considered, which is also non-convex. To deal with these non-convex optimization problems, design equivalence problems or relaxation problems as well as the transformation of constraints into penalty terms into optimization objectives have commonly been used in research. The successive convex approximation (SCA) [21] and some heuristic algorithms (e.g., PSO [22] and GE [23]) are commonly used to solve the trajectory. However, neither the SCA nor the heuristic algorithm can obtain a globally optimal solution, and the resulting local solution is strongly influenced by the initial value.
Inspired by the problems in past work, we focus on path planning and trajectory optimization considering UAV motion constraints in a dynamic jamming environment, which can be combined as motion planning. In our study, we first analyze the communication link [18,24] between the UAV and the ground sensors and formulate the optimization problem of minimizing the energy consumption, which considers the collection data demodulation threshold, obstacle avoidance, data collection volume, and motion principle. Then, we relaxed this non-convex optimization problem by introducing relaxation variables and constructing equivalence constraints. Further, to solve the initial value problem of SCA during replanning in dynamic environments, we propose a communication-flight-corridor (CFC)-based initialized path generation method, which enables the SCA algorithm to converge to the optimal value quickly. Finally, the optimized path points were subjected to a B-spline curve.
1.3. Contributions and Organization
The goal of this study is the examination of UAV-aided data collection from deployed low-power ground SNs in dynamic jamming environments. The motion planning of the UAV is designed by considering the communication capability, motion primitives, and the low-power SNs when the sensors transmit data. The major contributions of this paper are as follows:
- An optimization framework was developed to minimize the energy consumption of UAV data collection tasks with communication link quality while maintaining constraints such as the maximum UAV speed, obstacle avoidance, and minimum data requirements per SNs.
- Based on the introduction of relaxation variables and the application of SCA, we rewrite the nonconvex constraints of the original problem and fit the discrete points through B-spline curves. To ensure that it is applicable to dynamic environments, we further devise a motion planning approach, which is dependent on reprogramming and updated in real time with a dynamic jamming environment.
- We present a CFC-based path initialization method, which enables the initial path to meet the constraints on the communication rate and the amount of collected data. In addition, we present a safe flight path correction method based on a geometric method for fast obstacle avoidance, which ensures that the initial path is safe.
- Simulation results validate the performance of the proposed algorithm under different parameter configurations and compare to the benchmark algorithms.
The remainder of this paper is structured as follows: In Section 2, we describe the investigated scenario and formulate the optimization problem through path discretization. Section 3 presents the designed non-convex solution for the problem. The simulation results in Section 4 validate the effectiveness of the presented algorithm. Lastly, the paper is summarized in Section 5.
2. Problem Statement and Formulation
In this study, a UAV is dispatched to collect data from a low-power SN on the ground. The data collection is performed with a time-division multiple-access protocol. Figure 1 shows the scenario: The UAV is flying at low altitude in a smart city. The wireless communication system comprises K SNs represented by the set , and the location of the SN k is represented by . The transmitted power for each of the low-power SNs is fixed at . We consider the position of the SNs fixed and known for the trajectory design of the UAV. In practice, the position of the SNs can be obtained from the system database or identified with standard positioning techniques, such as with BeiDou systems or GPS [25]. In our scenario, the UAV arrives in the effective range of communication of the SN and activates the sensors for data transmission. It should be noted that the flight altitude of the UAV depends on the environment. Hence, it is simultaneously subject to air control by the local authorities. The complete flight altitude range is . The completion time of the data collection task is T, while the 3D trajectory of the UAV is denoted by , with . The completion time T is discretized into N sufficiently small and equal time slots with time discretization in which represents the length of the slot and . We introduce , in which is a variable. Consequently, the trajectory of the UAV in the 3D space in the n-th slot is expressed as follows: . In addition, unlike in prior studies, there are no-fly zones that are blocked by obstacles or interference sources. These are represented by the set, and the location of the projected center of the no-fly zone m is . For descriptive purposes, we refer to the no-fly zones as “obstacles” in what follows. Furthermore, there are J jammers in the environment, which are represented by the set , and the position of the j-th jammer is . We assume that the position of the jammers is dynamic at a fixed height, which can obtain the location technology according to the radiation source [26,27].
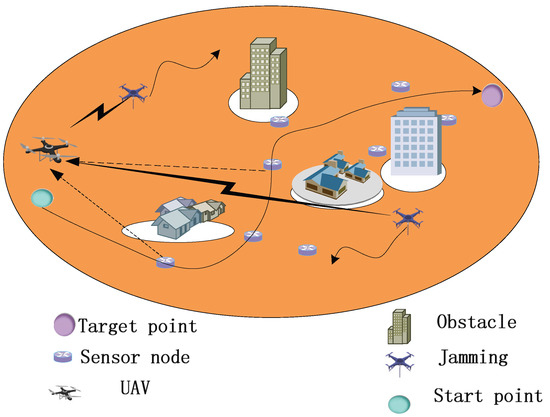
Figure 1.
UAV-aided Data Collection with Dynamic Jamming.
2.1. Channel Model
The communication channel of the UAV has a crucial influence on data collection. Thus, we present the channel model first. The distance between the UAV and jammer j in the n-th slot is as follows:
The distance between the UAV and SN k in the n-th slot is as follows:
We assume that the G2A channel comprises large- and small-scale fading. Small-scale fading is regarded as an identically distributed and independent Rician channel, and the Rice factor is ; the channel coefficient can be expressed as follows:
where and are the path-loss coefficients and small-scale fading, respectively. We can express the path-loss coefficient as follows:
where is the mean channel power gain over the reference distance m, and is the path-loss exponent, which typically exceeds 2 for a Rician fading channel. Small-scale fading consists of the LoS component , where , and a random NLoS component , where . Small-scale fading is determined as follows:
Assuming that each jammer is transmitting at a constant power , the instantaneous signal to interference plus noise ratio (SINR) of the SN k is as follows:
where , which is a random variable that obeys a non-central distribution. To simplify the optimization problem presented below, we further perform the homogeneous approximation of the SINR function, which considers the expected value of the SINR and yields the following result:
where
where is the signal model parameter, which, in general, can be set to 1. Moreover, is a Bessel function of order zero. and are constants in each independent simulation that can be generated according to the Rician channel model. When the time slot is sufficiently small or when the flight speed is low, we consider the position of the UAV a fixed point in each time slot. The expected information rate (bits/s) between the UAV and SN k in the n-th slot is represented as follows:
where B is the total channel bandwidth in Hz, and represents the noise power spectral density.
2.2. Motion Primitives
The set is a dynamical system composed of the 3-D position, acceleration, and velocity: . According to [28], the differential flatness of the UAV allows us to build control inputs from a 1-D time-parameterized polynomial trajectory that is independently specified on each axis. The discrete state over the entire task period can be , , and . The control variable input for the system is the jerk: . According to the equation of motion, the following correlations can be acquired:
The matrix forms are as follows:
where
in which is the initial position, is the initial velocity, and is the initial acceleration.
2.3. Problem Formulation
The optimization goal is to minimize the energy consumption and flight time of the UAVs when performed data collection missions. The optimization goal is to keep the flight time and energy consumption of the UAV minimal while collecting data. The energy consumption of a UAV typically comprises two major components: the propulsion energy and communication-related energy [18]. The latter consists of the energy utilized for communication circuits, signal radiation/reception, signal processing, and so on. For the purpose of this study, we consider the communication-related energy constant. To maintain the UAV at high altitude and to support its motion, propulsion energy is consumed. Typically, the propulsion energy depends on the flight speed, acceleration, jerk of the UAV, and so on. We take interest in the effort or smoothness of the trajectory, i.e., the square -norm of the control input , and , which represent the energy cost in a dynamic system. Hence, we express the energy optimization function as below:
where represents the smoothness and energy consumption of the UAV trajectory. is the identity matrix; , , are the weighting factors. The does not need to be considered in the optimization. Therefore, we formulate the optimization problem as follows:
and
where (26a), (26b) and (26c) are the UAV motion primitives based on model prediction. (26d) and (26e) are the motion constraints of the UAV, which limit the range of the maximum velocity and maximum acceleration: and and . (26f) is the height constraint of the UAV, and (26g) and (26h) are the start and end state constraints. (26i) represents the collected data amount of the k-th sensor, where is the effective collection indication, and is the minimum collection requirement. (26j) is the minimum communication rate of the sensor given according to the actual communication system. Moreover, (26k) is the obstacle avoidance constraint, which is usually a non-convex constraint that limits the UAV motions to a safe area. The formulated problem P0 is difficult to solve directly for the following reasons: (i) The mission completion time of UAVs is closely related to the dimensions of other state variables, which make it difficult to determine the constraints; (ii) the constraints (26i) and (26k) are non-convex. To this end, we solve this problem through the introduction of slack variables and the use of SCA.
| st: | (26a) | |
| (26b) | ||
| (26c) | ||
| (26d) | ||
| (26e) | ||
| (26f) | ||
| (26g) | ||
| (26h) | ||
| (26i) | ||
| (26j) | ||
| (26k) |
3. Global Replanning Based on CFC
3.1. General Framework
The major challenge in optimally solving (P0) is to optimize the variable N and non-convex constraints (26i) and (26k), which involve uncertainty of other optimization variables and indicator functions (26j) with respect to the UAV trajectory. Without affecting the optimality of (P0), the trajectory of the UAV can be considered to constitute only the connecting line segment [6]. This conclusion means that finding the optimal solution to (P0) is comparable to finding an ordered set of waypoints containing positions that represent the start and end points of each segment and to optimizing the instantaneous speed of the UAV on the trajectory linking these waypoints. To this end, as shown in Figure 2, the task time N and trajectory energy consumption are decoupled in the optimization objective. First, minimum time discrete path initialization based on a CFC is proposed under the condition that the minimum discrete-time slot is . Second, we use the SCA algorithm to optimize the global path according to the initialization path. Third, a B-spline method is used to smooth the trajectory in a minimum discrete-time slot, . After executing the trajectory of the time slot , the communication channel state and state information of the UAV itself (including the position, velocity, and acceleration) are re-estimated and updated. Finally, the operation starting from path initialization is repeated until the destination point is reached. We will present the path initialization, path optimization, and B-spline trajectory optimization in more detail.
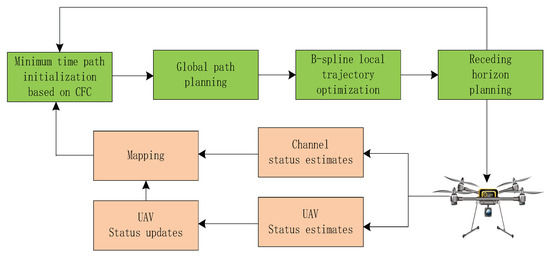
Figure 2.
Block diagram of presented autonomous system.
3.2. Global Path Planning Based on SCA
For the nonconvex problem , we perform the following for the nonconvex constraints (26i), constraints (26j) and constraints (26k). We first introduce the auxiliary variables for constraints (26i) and constraints (26j) in the following equivalent form: For the non-convex problem P0, we perform the following steps for the non-convex constraints (26j) and constraints (26j) and constraints (26k). First, we introduce the auxiliary variables for the constraints (26i) and (26j) with the following equivalent form:
Proof.
Constraint (28) shows that can only be 1 when . Otherwise, it is zero. The minimum amount of data collected constantly must be higher than , and the constraint (28) is only valid when some equal to 1. Hence, the constraints (28) and (29) can make the UAV “pass through” the “surrounding” of each SN during its flight while remaining at a low velocity for a period of time based on the minimum amount of collected data. □
However, constraints (28) and (29) are still non-convex. For , the auxiliary variables and are introduced to obtain the following relation:
where . The auxiliary variables and must meet the following conditions:
For constraint (32), we can rewrite the convex constraint as follows:
However, constraint (33) is still non-convex. We perform a first-order Taylor expansion:
where , and , are the initial values of the r-th iteration. This results in a new convex constraint (36), which is a relaxation of constraint (33):
where . For constraint (31), we further introduce an auxiliary variable , that is less than the first-order Taylor expansion of .
where , , and . Therefore, a further relaxed form of the constraint (31) can be obtained
Constraint (38) is still a non-convex constraint owing to the product of the indicator function variable and variable . Thus, we continue to relax the indicator function:
The convex constraints can be obtained via a Taylor expansion and for constraints (29), (38) and (40)
where . Thus, we obtain the new convex constraints (41), (42) and (43) of problem P1 after the equivalent transformation and relaxation of constraints (26i) and (26j). In the next step, we continue to deal with the non-convex constraint (26k) of problem P1. The obstacles in the environment are modeled as cylinders. The UAV must keep a certain safe distance to them during its flight. We set the safe distance as . During the task, the UAV should ensure that the distance between the projection coordinates and the center coordinates of the bottom surface of the cylindrical obstacle exceeds the safe distance or that its flight height is much higher than that of the cylinder to ensure a safe flight. The respective safety constraint between the UAV and obstacle m is as follows:
This is an “or” constraint that is non-convex. In addition, represents the two-dimensional coordinates projected by the UAV onto the ground, and is the flight height of the UAV. By introducing the variables 0 and 1, we can express the equivalent form of the constraint (44) as follows:
where C is a big positive constant and are is a binary number. We further relax these binary integer constraints
where . By relaxing and in constraint (48), the new constraints can be obtained as follows:
The relaxation form of the non-convex constraint (51) can be obtained via a Taylor expansion
where is the r-th iteration of . So far, we have dealt with all the non-convex constraints in P0 to obtain the new optimization problem as follows:
| st: | (54a) | |
| (54b) | ||
| (54c) | ||
| (54d) | ||
| (54e) | ||
| (54f) | ||
| (54g) | ||
| (54h) | ||
| (54i) | ||
| (54j) | ||
| (54k) | ||
| (54l) | ||
| (54m) | ||
| (54n) | ||
| (54o) | ||
| (54p) |
Evidently, the problem is a convex optimization problem that can be addressed through the application of standard convex optimization technology or CVX (for instance, the interior-point method). However, some of the constraints in the previously presented optimization problem are sensitive to the initial value after relaxation. Although we have designed a continuous convex approximation method to solve the problem, the influence of the initial value is still not negligible. It will influence the convergence time of the algorithm and the optimal solution. To this end, we designed a CFC-based initialization method, which will be described in detail in the next section.
3.3. Minimum Time Path Initialization Based on CFC
In practice, the communication capability of SNs is limited by the power and environment. It is usually necessary to calculate the communication link under the constraints of the demodulator threshold, bit error rate, receiver sensitivity, and so on to determine the supported communication range. We propose flight path segmentation based on a CFC. Full-speed flight paths are generated according to the trapezoidal criterion [5]. To find the CFC, we define the effective communication area of the SN k free of interferers: , where is the trajectory within the effective communication area of the SN, and is the maximum distance. To produce a convex CFC from the jammers and SN, the following procedures are performed:
- Find the nearest jammer: calculate the distance between all the jammers and SN k, choose the nearest jammer , and let the jamming value of the other jammers be , which is the investigated worst-case scenario we have in mind because the jamming value of interferer j would not surpass in the SN k communication region.
- Find critical points: on the line segment between jammer and the central position of SN k, find a point along the direction of the center of the SN communication circle that will meet the communication rate larger than .
- Find CFC: pass through and ensure that the perpendicular is on a line between jammer and SN k.
The intersection of the half-space on the vertical side of SN k and the communication range of SN k, is the CFC, which is a convex polyhedron. The detailed construction process is described in Algorithm 1. It divides the UAV path into two paths: the communication path and full-speed flight path. The UAV data are collected on the communication path, which is within the effective communication range.
| Algorithm 1: Given the position of SN k and the position of jammer, find . |
|
After acquiring the CFC, the initialization generates discrete points on the path according to the “trapezoidal principle” because we expect the UAV to be as slow as possible when approaching the SN during data collection. Thus, it needs enough time to complete the task. We conduct the analysis for the case of only one SN, as shown in Figure 3 (the green area is the CFC).
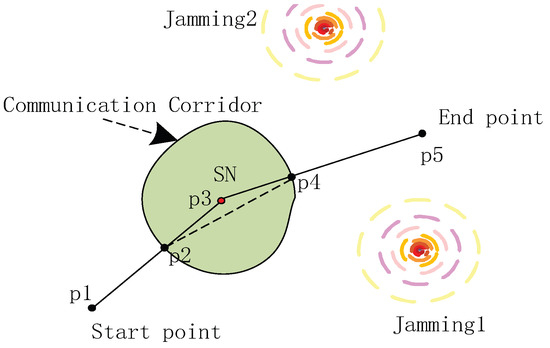
Figure 3.
Path initialization based on CFC.
We first connect the starting point to sensor position point and terminal position point . The intersection points of the line segment and CFC are denoted as and . Furthermore, allocates the time and determines the position of discrete points according to the trapezoidal preparation. The UAV accelerates from the initial position to the maximum velocity, remains at the maximum velocity for a while and finally gradually slows down to zero velocity to reach the end point. The total flight time of this period is . In addition, the acceleration period is , the period of uniform movement is , and the period of deceleration is such that , where , , and is the distance of . Therefore, the number of discrete points on the segment can be obtained as follows:
Consequently, the discrete points of segment can be expressed as follows:
and are located in the CFC and can meet the minimum communication rate. We suppose that the time is necessary to collect data at the minimum rate and the requested minimum quantity . This time period comprises two flight paths with the flight times and , respectively:
We let these two trajectories move at a constant speed. Thus, , where and are the distances of and , respectively. We determine and as follows:
where and . and can be processed in the same way. Therefore, we can obtain the initial waypoints of the global plan according to Algorithm 2.
| Algorithm 2: For a given initial position , end position , and position of the jammer and SN, find the initial global discrete path. |
|
It is worth noting that if the UAV enters the CFC during its flight, the discrete points of are not calculated. If the amount of collected data meets the requirements, the UAV and will no longer be calculated. However, the discrete points of the line segment from the position of the UAV to the destination will be calculated directly.
The initial path obtained by the Algorithm 2 does not consider the treatment of obstacles. Therefore, we continue to design a method based on expansion for the treatment of obstacles.
As shown in Figure 4, we first detect the initial path points generated based on the CFC. If these points are within the obstacle area, we move the direction of the vertical line to where these path points are located until a safe distance from the obstacle is found. This is accomplished through the following four steps: (1) Calculate the equation of the line for the neighboring points and on ; (2) calculate the distance from the center of the obstacle to ; (3) determine if the distance is shorter than . Calculate the vertical line going through the point ; (4) search for a point on the vertical line which satisfies that the distance from the obstacle center to is greater than . Use that point as the new . The specific implementation steps are shown in Algorithm 3.
| Algorithm 3: For a given initial CFC path , the position of obstacles , the safe distance , and step factor to find the initial global obstacle avoidance discrete path. |
|
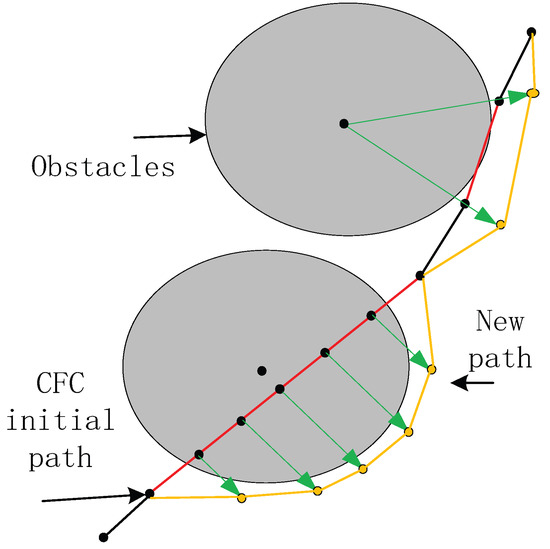
Figure 4.
CFC initial path correction for obstacle avoidance.
3.4. Replanning
Based on the previously presented conclusions regarding the initialization path, we propose an SCA-based solution method for the convex optimization problem P1. The method approximates the optimal solution of the original problem P0 one by one through good initialization values and an iterative method based on Taylor expansions. The specific steps are shown in Algorithm 4. First, we initialize the state of the UAV and mission settings. Subsequently, we generate the communication corridor path and safe flight path for obstacle avoidance as the initial values to solve the optimization problem P1 according to the mission requirements. Good initial values enable the iteration-based SCA algorithm to converge quickly and obtain a local solution. However, in the actual mission environment, the disturbance sources and obstacles may change dynamically, and the path determined at one point in time is not applicable to the whole flight process. For this reason, we propose a planning algorithm based on replanning in which the UAV plans a new trajectory at a certain frequency. The specific process is shown in Algorithm 5.
| Algorithm 4: SCA-based trajectory planning method for (P1) |
|
| Algorithm 5: Receding horizon planning. |
|
To obtain a more suitable trajectory for the flight control module, we used B-splines to smooth the path in Algorithm 5. path points were chosen as control points for the homogeneous B-spline curve according to the set replanning frequency, which is uniquely identified via its , control points and a knot vector , where . To simplify and improve the efficiency of the trajectory assessment, the B-spline employed in our approach is homogeneous, which implies that each knot has the same time interval between it and its predecessor. We normalize t as follows: . The matrix representation can be used to assess the location [29]:
where is a constant matrix determined by . In our implementation, is set as 3, and the third-order matrix has the following form:
3.5. Convergence and Complexity Analysis
Motion planning of a UAV in a data collection mission with dynamic jamming consists of five main parts: CFC construction, generation of the initial CFC path, generation of a safe path, SCA-based path optimization, and B-spline-based trajectory optimization. The convergence of the algorithm depends mainly on solving the P1 problem, which uses a method based on SCA. Section 2.1.2 in [30] presents an analysis of the convergence of SCA. We set as the limit point of the iterative result produced via Algorithm 4, which met and slater condition holds at the point . Subsequently, becomes a KKT point of P1. First of all, problem P1 indicates that there exist obstacle avoidance constraints of the UAV, speed constraints, initial position constraints, and end position constraints, equation of state constraints, and a quality of communication link or the amount of collected data. Hence, the computational complexity is approximately , where R represents the number of iterations, M is the obstacle number, N is the number of time slots, and K is the SN number. In the construction process of the CFC, the goal is to acquire an effective communication area by applying geometric approaches. The complexity is only associated with the number of sensors and jammers. Thus, its complexity is . In the generation of the CFC initial path and safe path, the calculation volume is also related to the number of obstacles and number of sensors. Thus, the assistance is also . Finally, the B-spline trajectory only computes a local number of control points. Because we can ignore the number of operations, the total complexity is . It is worth mentioning that motion planning in this paper is divided into global path planning and local trajectory optimization.The replanning time of global path planning is 1Hz; that is, it is updated once every second.In the hardware environment mentioned in reference [12], when the main frequency is 3 GHz, for a sensor, when the number of obstacles is 5, the number of interference sources is 2, the number of discrete points is 100, and the calculation time of the algorithm is about 3 ms. Therefore, it can fully support 1 s update frequency of path planning.At the same time, the local trajectory optimization directly selects the path points and adopts the B-spline method for fitting, which takes almost no time and is consistent with the literature [27]. The planning time is about 0.8ms, which can support the update frequency of 1000 Hz.
4. Simulations and Discussion
In this section, we present the results of numerical simulations to compare the algorithm in this paper with the SCA algorithm forinitialization proposed in [6] and the traditional DWA algorithm for dynamic environments. We mainly consider two dynamic sources of interference and several obstacles in the environment. To facilitate the simulation, we simulate a data collection task for an SN. Table A1 lists some crucial parameters and their values. We made some changes to ensure that the SCA algorithm for AStar initialization from [6] is applicable to the scenario presented. In this paper, we divide the path into two segments: the paths between the origin and the SN and between the SN and the end point. The two paths are initialized separately with the A star algorithm. We further interpolate the A star initial path points in order to obtain initial conditions that can meet the required data volume. For the DWA algorithm, we design different cost functions depending on the stage of the task, as shown in Appendix A.
Figure 5 presents the motion plan for 200 kbit data collection in an environment without jamming and environments with static and dynamic jamming. In the jamming-free environment, the SN has the largest communication range, which covers the entire mission path of the UAV. In the static environment, the communication range of the SN is smaller and “pear-shaped”; the UAV can only collect data within this area. The communication range of the SN varies according to the motion of a jammer in a dynamic environment.
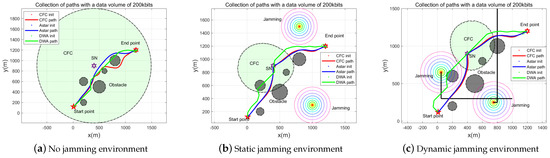
Figure 5.
200 kbit data collection with three algorithms for motion planning in environments without jamming and with static and dynamic jamming.
The red dashed line in Figure 6 represents the global path that is initialized via the CFC, the blue dashed line denotes the global path that is initialized via the AStar algorithm, and the green dashed line denotes the local path that is initialized through the DWA. The light green region is the SN’s effective communication range; in the absence of interference, it should be a circle in the 2D top view. The effective communication range of the SN becomes “pear-shaped” when suppressed by two sources of interference. The grey circle is the obstacle, and the 3D shape is a cylinder. Evidently, both the red dashed and blue dashed lines are at safe distances from the obstacle and pass through the SN. This is exactly what we want: a safe initial path to collect data.
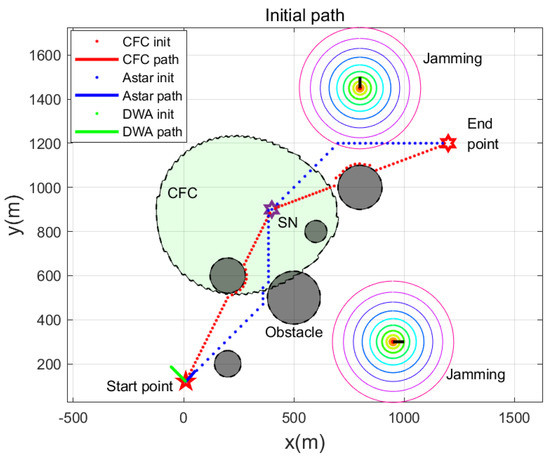
Figure 6.
Initial path.
Figure 7 illustrates the residual amount of data collected by the UAV during the mission. In the jamming-free environment, the CFC and AStar algorithms complete the mission in approximately 25 s, while the DWA algorithm needs 30 s. In the static jamming environment, the CFC and AStar algorithms complete the entire mission in approximately 40 s, whereas the DWA algorithm needs 45 s. In the jamming interference environment, the CFC and AStar algorithms require similar times to complete the task, while the DWA algorithm needs more time.
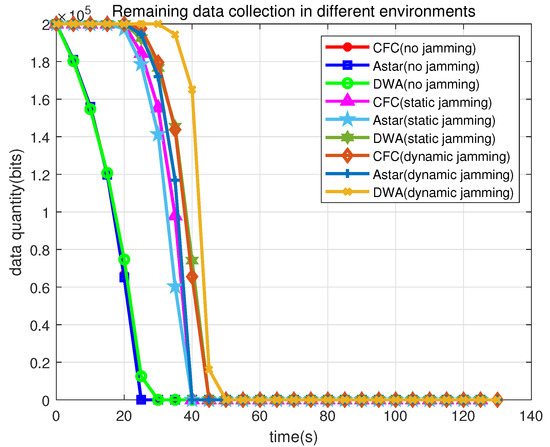
Figure 7.
The residual amount of data collected for three algorithms in different environments.
Figure 8 shows the normalized energy consumption of the UAV. We used the integral of the UAV acceleration to present the UAV energy consumption. According to the figure, the DWA algorithm consumes much more energy than the CFC and AStar algorithms for the three environments. The AStar algorithm consumes slightly less energy than the CFC algorithm in the jamming-free environment, whereas the CFC consumes slightly less energy than the AStar algorithm in the jamming environment. It is also worth noting that the complexity of the AStar algorithm is , while the complexity of the CFC algorithm is only . Therefore, collecting data with the CFC algorithm is much less expensive than with the AStar algorithm.
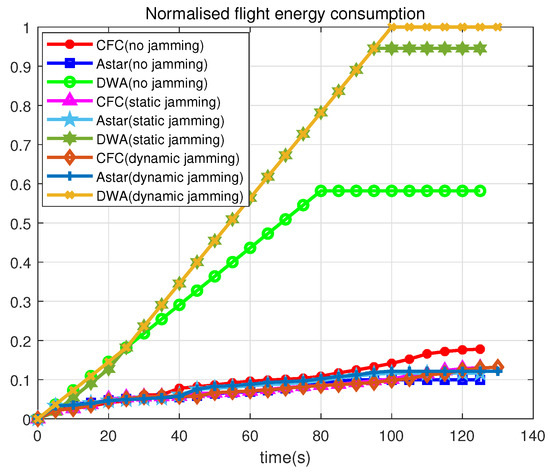
Figure 8.
Variation in flight energy consumption for three algorithms in different environments.
The UAV trajectories for the different required data volumes are shown in Figure 9. Accordingly, the UAV trajectories planned for a required data volume of 0 bits ignore the communication corridors and interference. With growing amount of required data, the UAV trajectory stays in the communication corridor for a longer period of time.
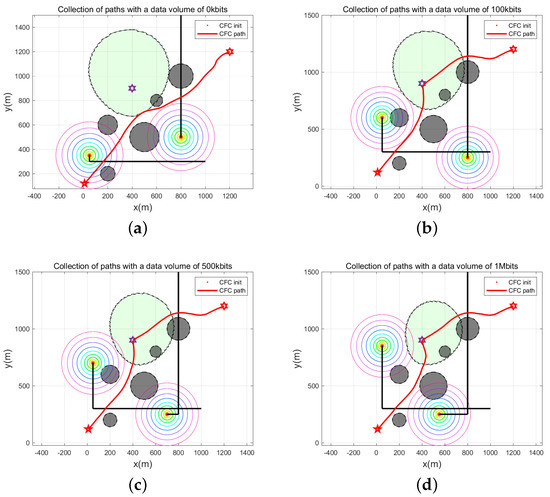
Figure 9.
UAV paths for different data collection volumes: (a) 0 bits; (b) 100 kbits; (c) 500 kbits; (d) 1 Mbits.
Figure 10 shows the variation in the amount of remaining data for different collection requirements. The larger the amount of required data, the longer the task takes to be completed, which is in line with the general rule. Figure 11 shows the variation in the in-flight energy consumption for different collection requirements. The lowest energy is consumed for zero collected data, and the highest energy is consumed for the collection of 1 Mbit.
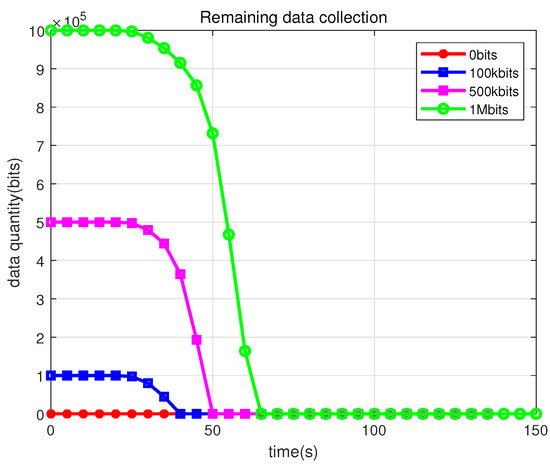
Figure 10.
Variation in the amount of data remaining for different data collection requirements.
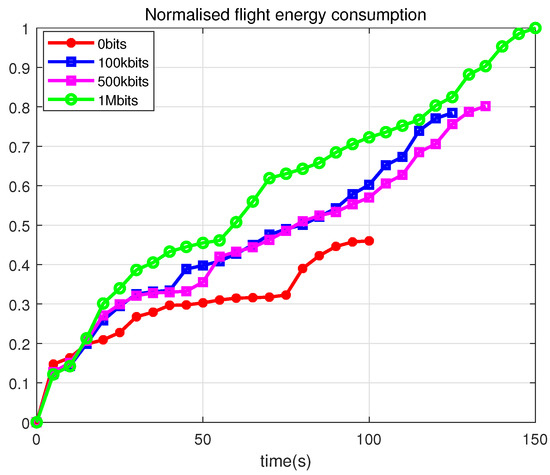
Figure 11.
Normalized flight energy consumption.
Figure 12 displays the instantaneous communication rate of the UAV for different amounts of required data. The sky-blue dashed line indicates the communication threshold. Evidently, the greater the data demand exceeds the communication threshold area; for example, the red line in the figure is the instantaneous communication rate when the data collection volume is 0, which is basically less than the communication threshold. It does not need to consider the data collection task only needs to fly with the lowest energy consumption to focus. When the data collection volume is 1 Mbit (as shown by the green curve in the diagram), it will stay above the communication threshold as much as possible until the task has been completed.
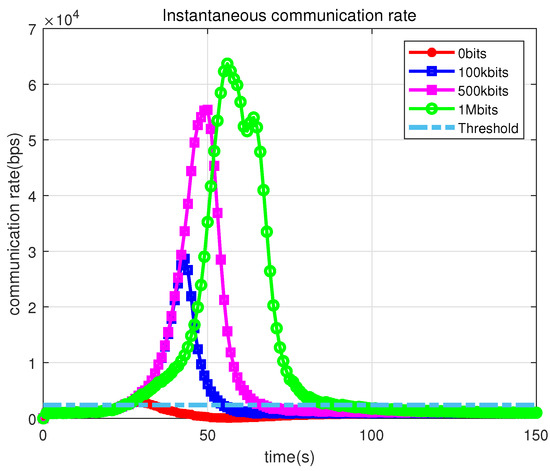
Figure 12.
Instantaneous communication rate.
Figure 13 and Figure 14 show the speed and flight altitude of the UAV during data collection for different required data volume, respectively. The UAV accelerates, decelerates, accelerates, and decelerates again, which is very much in line with the trapezoidal criterion we used during initialization. Therefore, the UAV should fly at full speed before entering the CFC, then decelerate appropriately to remain in the area long enough to collect the required amount of data in the CFC, and then fly at full speed to the end point. The flight altitude also increases and then decreases, which is very much in line with the dynamics of a low-energy flight.
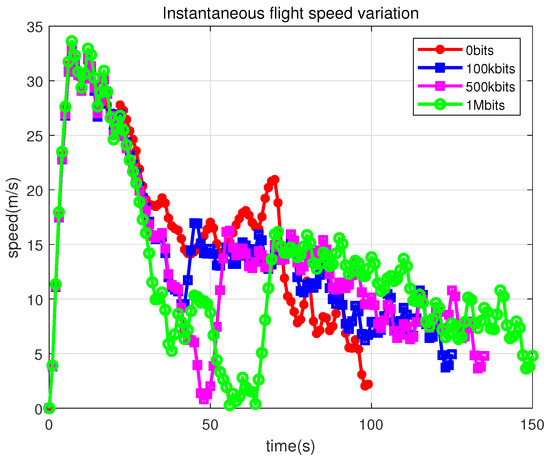
Figure 13.
Instantaneous flight speed variation.
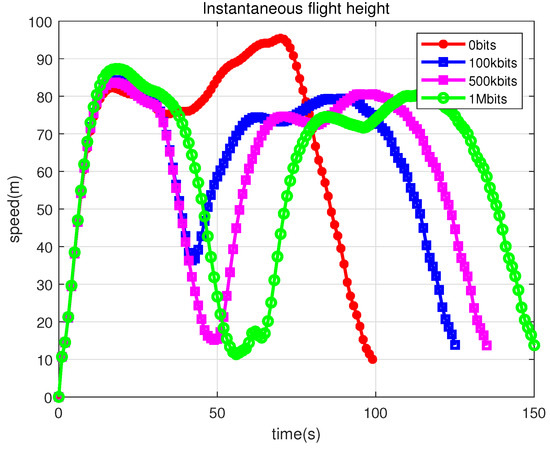
Figure 14.
Instantaneous flight height.
5. Conclusions
In this study, the motion programming of UAVs collecting data in a dynamic jamming environment was examined. Our main optimization objective was to find a safe path that consumes a minimum amount of energy and results in the required amount of collected data. As the constructed optimization problem is non-convex, we introduced auxiliary and relaxation variables to relax the original problem and used the SCA algorithm to solve the new relaxation problem. To obtain a well-localized optimal solution with the SCA algorithm, we propose a fast initialization path method that is based on a CFC for processing. We constructed the CFC and solved for the initial path of the UAV with the UAV’s perceived interference intensity and the transmission capability of the SN. Finally, we compared the simulation results with those of the AStar and DWA algorithms. The results demonstrate that the algorithm presented in the current paper is feasible and performs reliably.
Author Contributions
Methodology, D.G.; Software, C.X.; Formal analysis, B.Z.; Investigation, W.M.; Writing—original draft, B.W.; Funding acquisition, H.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A

Table A1.
Key simulation parameters.
Table A1.
Key simulation parameters.
| The Notation | Physical Meaning | Value |
|---|---|---|
| SN transmission power | 500 mW | |
| Jammer transmission power | 5000 mW | |
| B | Total channel bandwidth | 10 kHz |
| Maximum UAV speed | 25 m/s | |
| Maximum UAV acceleration | 5 m/s | |
| Maximum UAV height | 200 m | |
| Minimum UAV height | 10 m | |
| Noise power spectral density | −169 dBm/Hz | |
| Path loss exponent | 2 | |
| Minimum collection rate | 2.4 kbps | |
| Minimum update period | 1 s | |
| Communication carrier frequency | 2 GHz |
References
- Ding, G.; Wu, Q.; Zhang, L.; Lin, Y.; Tsiftsis, T.A.; Yao, Y.-D. Anamateur drone surveillance system based on the cognitive internet of things. IEEE Commun. Mag. 2018, 56, 29–35. [Google Scholar] [CrossRef]
- Zhao, J.; Gao, F.; Wu, Q.; Jin, S.; Wu, Y.; Jia, W. Beam tracking for uav mounted satcom on-the-move with massive antenna array. IEEE J. Sel. Areas Commun. 2018, 36, 63–375. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing from the sky: A tutorial on uav communications for 5g and beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef]
- Liu, J.; Sheng, M.; Lyu, R.; Li, J. Performance analysis and optimization of uav integrated terrestrial cellular network. IEEE Internet Things J. 2019, 6, 1841–1855. [Google Scholar] [CrossRef]
- Wu, B.; Zhang, B.; Guo, D.; Wang, H.; Jiang, H. Anti-jamming trajectory design for uav-enabled wireless sensor networks using communication flight corridor. China Commun. Engl. Ed. 2022, 19, 16. [Google Scholar] [CrossRef]
- Wu, B.; Guo, D.; Zhang, B.; Zhang, X.; Wang, H.; Wang, H.; Jiang, H. Completion time minimization for uav enabled data collection with communication link constrained. IET Commun. 2022, 16, 1025–1040. [Google Scholar] [CrossRef]
- Chen, J.; Liu, T.; Shen, S. Online generation of collision-free trajectories for quadrotor flight in unknown cluttered environments. In Proceedings of the 2016 IEEE International Conference on Robotics and Automation (ICRA), Stockholm, Sweden, 16–21 May 2016; pp. 1476–1483. [Google Scholar]
- Gao, F.; Wu, W.; Lin, Y.; Shen, S. Online safe trajectory generation for quadrotors using fast marching method and bernstein basis polynomial. In Proceedings of the 2018 IEEE International Conference on Robotics and Automation (ICRA), Brisbane, Australia, 21–25 May 2018; pp. 344–351. [Google Scholar]
- Liu, J.; Jayakumar, P.; Stein, J.L.; Ersal, T. A nonlinear model predictive control formulation for obstacle avoidance in high-speed autonomous ground vehicles in unstructured environments. Veh. Syst. Dyn. Int. J. Veh. Mech. Mobil. 2018, 56, 853–882. [Google Scholar] [CrossRef]
- Liu, S.; Watterson, M.; Mohta, K.; Sun, K.; Bhattacharya, S.; Taylor, C.J.; Kumar, V. Planning dynamically feasible trajectories for quadrotors using safe flight corridors in 3-d complex environments. IEEE Robot. Autom. Lett. 2017, 2, 1688–1695. [Google Scholar] [CrossRef]
- Gao, F.; Wu, W.; Pan, J.; Zhou, B.; Shen, S. Optimal time allocation for quadrotor trajectory generation. In Proceedings of the 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Madrid, Spain, 1–5 October 2018. [Google Scholar]
- Zhou, B.; Gao, F.; Wang, L.; Liu, C.; Shen, S. Robust and efficient quadrotor trajectory generation for fast autonomous flight. IEEE Robot. Autom. Lett. 2019, 4, 3529–3536. [Google Scholar] [CrossRef]
- Wang, H.; Wang, J.; Ding, G.; Chen, J.; Gao, F.; Han, Z. Completion time minimization with path planning for fixed-wing uav communications. IEEE Trans. Wirel. Commun. 2019, 18, 3485–3499. [Google Scholar] [CrossRef]
- Zhan, C.; Zeng, Y. Completion time minimization for multi-uavenabled data collection. IEEE Trans. Wirel. Commun. 2019, 18, 4859–4872. [Google Scholar] [CrossRef]
- Gu, J.; Wang, H.; Ding, G.; Xu, Y.; Xue, Z.; Zhou, H. Energyconstrained completion time minimization in uav-enabled internet of things. IEEE Internet Things J. 2020, 7, 5491–5503. [Google Scholar] [CrossRef]
- Kiet, T.A.; Tuan, C.X.; Hieu, H.P.; Le Quyen, N.T.; Phuong, D.H.; Hung, V.T. Power minimization for data collection in uav-assisted iot wireless sensor networks. In Proceedings of the 2022 16th International Conference on Ubiquitous Information Management and Communication (IMCOM), Seoul, Republic of Korea, 3–5 January 2022; pp. 1–3. [Google Scholar]
- Wang, Y.; Wen, X.; Hu, Z.; Lu, Z.; Miao, J.; Sun, C.; Qi, H. Multi-uav collaborative data collection for iot devices powered by battery. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Republic of Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Jiang, H.; Zhang, Z.; Gui, G. Three-dimensional non-stationary wideband geometry-based uav channel model for a2g communication environments. IEEE Access 2019, 7, 26116–26122. [Google Scholar] [CrossRef]
- Gao, Y.; Wu, Y.; Cui, Z.; Yang, W.; Hu, G.; Xu, S. Robust trajectory and communication design for angle-constrained multi-uav communications in the presence of jammers. China Commun. 2022, 19, 131–147. [Google Scholar] [CrossRef]
- Wang, H.; Chen, J.; Ding, G.; Sun, J. Trajectory planning in uav communication with jamming. In Proceedings of the 2018 10th International Conference on Wireless Communications and Signal Processing (WCSP), Hangzhou, China, 18–20 October 2018; pp. 1–6. [Google Scholar]
- Samir, M.; Sharafeddine, S.; Assi, C.M.; Nguyen, T.M.; Ghrayeb, A. Uav trajectory planning for data collection from time-constrained iot devices. IEEE Trans. Wirel. Commun. 2020, 19, 34–46. [Google Scholar] [CrossRef]
- Nayeem, G.M.; Fan, M.; Akhter, Y. A time-varying adaptive inertia weight based modified pso algorithm for uav path planning. In Proceedings of the 2021 2nd International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 5–7 January 2021; pp. 573–576. [Google Scholar]
- Dashkevich, A.; Rosokha, S.; Vorontsova, D. Simulation tool for the drone trajectory planning based on genetic algorithm approach. In Proceedings of the 2020 IEEE KhPI Week on Advanced Technology (KhPIWeek), Kharkiv, Ukraine, 5–10 October 2020; pp. 387–390. [Google Scholar]
- Jiang, H.; Zhang, Z.; Wu, L.; Dang, J. Three-dimensional geometrybased uav-mimo channel modeling for a2g communication environments. IEEE Commun. Lett. 2018, 22, 1438–1441. [Google Scholar] [CrossRef]
- Isaacs, J.T.; Klein, D.J.; Hespanha, J.P. Algorithms for the traveling salesman problem with neighborhoods involving a dubins vehicle. In Proceedings of the 2011 American Control Conference, San Francisco, CA, USA, 29 June–1 July 2011; pp. 1704–1709. [Google Scholar]
- Chen, P.; Chen, Z.; Zheng, B.; Wang, X. Efficient doa estimation method for reconfigurable intelligent surfaces aided uav swarm. IEEE Trans. Signal Process. 2022, 70, 743–755. [Google Scholar] [CrossRef]
- Roy, R.; Kailath, T. Esprit-estimation of signal parameters via rotational invariance techniques. IEEE Trans. Acoust. Speech Signal Process. 1989, 37, 984–995. [Google Scholar] [CrossRef]
- Zhou, X.; Wang, Z.; Ye, H.; Xu, C.; Gao, F. Ego-planner: An esdffree gradient-based local planner for quadrotors. IEEE Robot. Autom. Lett. 2021, 6, 478–485. [Google Scholar] [CrossRef]
- Qin, K. General matrix representations for b-splines. In Proceedings of the Sixth Pacific Conference on Computer Graphics and Applications (Cat. No.98EX208), Singapore, 26–29 October 1998; pp. 37–43. [Google Scholar]
- Razaviyayn, M. Successive Convex Approximation: Analysis and Applications. Ph.D. Thesis, University of Minnesota, Minneapolis, MN, USA, 2014. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).