Systematic Review and Quantitative Comparison of Cyberattack Scenario Detection and Projection
Abstract
1. Introduction
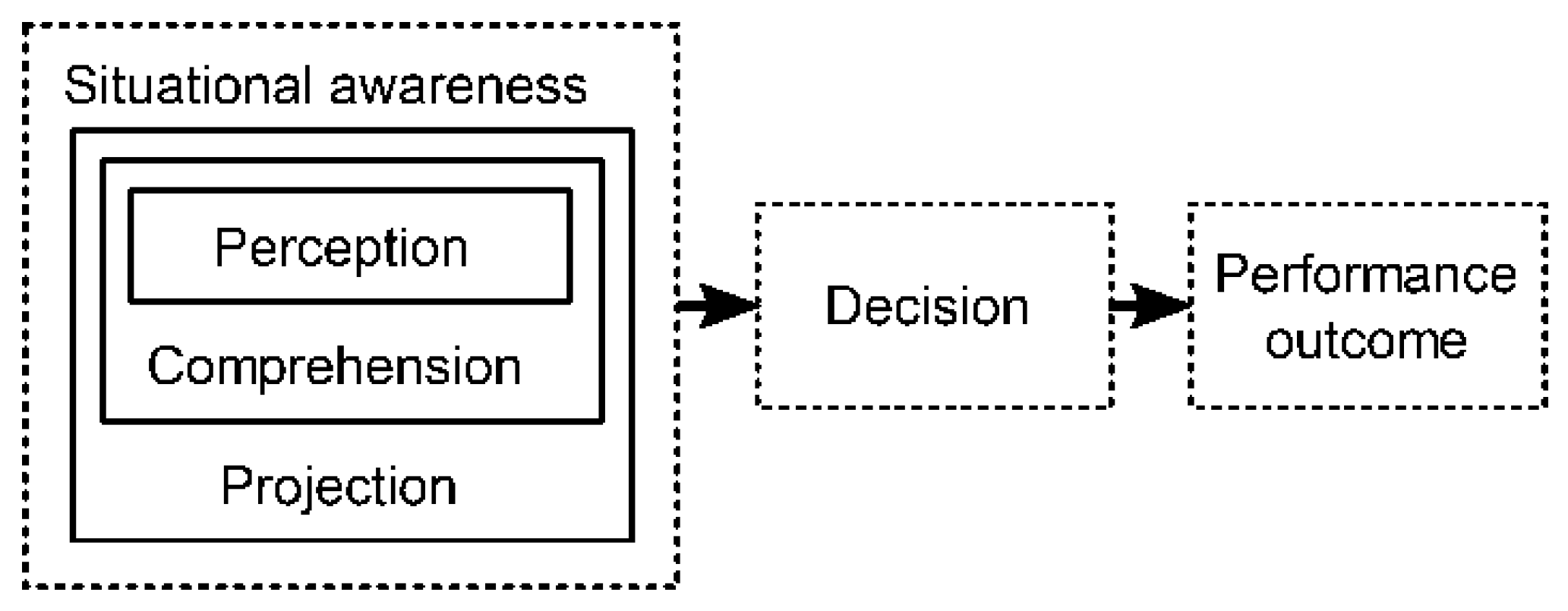
2. Preliminaries: Achieving Cyber Situational Awareness
2.1. Attack Detection
2.2. Attack Projection
2.3. The Problem of Uncertainty
3. Related Work
- alert database containing alerts from low-level sensors such as Network Intrusion Detection Systems (NIDS) or Host Intrusion Detection Systems (HIDS);
- topology information, such as hosts, connectivity, etc.;
- vulnerabilities database, e.g., Common Vulnerabilities and Exposures (CVE) database;
- trouble ticketing system information;
- ontology database, with domain semantics that can be used for automatic inference;
- cases database, containing rules for associating alerts with common and known problems; and,
- knowledge representation, rules and models either put together by experts or inferred from datasets, which are used for correlating alerts.
4. Evaluation Metrics
5. Evaluation Datasets
5.1. Darpa Intrusion Detection Evaluation Datasets
5.2. Def Con Ctf Datasets
5.3. Cyber Treasure Hunt Dataset
5.4. Unb Datasets
5.5. Other Datasets
5.6. Criticism of Existing Datasets
6. Survey of Developments in Attack Scenario Detection and Projection
6.1. Methods
- Three Google Scholar and Scopus searches were performed, using the following keywords: “attack scenario detection alert correlation”, “attack scenario reconstruction alert correlation”, and “attack scenario projection alert correlation”.
- A table containing 300 articles was populated while using the top 100 articles returned by each Google Scholar search.
- We sorted the table by four criteria, each time listing the first 25 results whose titles and abstracts fell within the scope of the survey. The first criterion was the total number of citations, in order to find the most influential papers. The second criterion was the number of citations divided by the age of the paper, in order to find more recent papers that gained traction. The third criterion was the rank that the Google Scholar search yielded, used to measure the relevance of the paper. Finally, as we noticed the lack of newer papers on the list, we added a fourth criteria, which filtered out all papers older than 2015, and sorted the remaining papers using their Google Scholar ranks. At this point, the list contained 100 article mentions.
- All 23 articles ([25,26,31,32,33,34,38,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73]) that appeared more than once on the list were considered for inclusion in the survey. Additionally, [35,36] were included, because, although each of them appeared only once on the list, they were in essence representing the same approach. Porras et al. [58] was excluded because it primarily concerns with mission impact and elimination of duplicate and false positive alerts, and not attack scenarios. Hossain et al. [59] were excluded, because they primarily focus on detecting low-level attacks on a single host. Pietraszek et al. [71] was excluded, because they primarily focused on reducing false-positive IDS alerts.
- The steps described above were repeated using Scopus searches with the same search terms. While the first search returned the target 100 results, subsequent searches only found a handful of articles. In this manner, additional 9 articles ([29,30,88,89,90,91,92,93,94]) were found and considered for inclusion in our survey. Alhaj et al. [92] was excluded because their goal is correlating alerts into individual attack steps, but they do not reconstruct the high-level attack scenarios, effectively performing alert aggregation.
- Finally, four articles were included on an individual basis. Huang et al. [95] was included, because it considers operational planning of attacks. Yu and Frincke [41] was included, because it introduced an expressive metrics, Quality of Alerts (7). GhasemiGol and Ghaemi-Bafghi [27], and Albanese et al. [96] were included due to using approaches whose types were underrepresented.
6.2. State Transition Analysis Technique
6.3. Event and/or Alert Correlation Relying on Expert Knowledge
6.3.1. Alert Correlation Based on Alert Attributes
6.3.2. Preconditions and Post-Conditions
6.3.3. Attack Graphs and Trees
6.4. Event and/or Alert Correlation Relying on Data Mining and Machine Learning
7. Results
- Model gives a basic description of the concepts which the method or tool is based on. Some of the articles propose attack description languages, such as STATL, and are therefore labeled as Language. Similarity stands for feature similarity and refers to models which compare alert features, often using pre-defined formulas for similarity. Articles relying on attack graphs and attack trees are labeled as Graph. Most papers either use a knowledge base (KB) populated by experts, or machine learning (ML) or data mining (DM) to extract attack scenarios. In some cases, names of data mining algorithms or machine learning models are provided. Hidden Markov model is abbreviated as HMM, Similarity as Sim., Decision Trees as DT, and Markov chain as MCh.
- Domain knowledge refers to the amount of domain knowledge that needs to be provided to the model to be fully functional. Since languages can be used in all sorts of systems, based on KB, AI, or hybrid models, the field is left empty. One star means that there is only minimal domain knowledge entry needed, in most cases about IP ranges in the network. Three stars signify that the system needs regular maintenance of a knowledge base to operate, while two stars are between the two extremes.
- Level of evaluation describes whether the authors validated their approaches on datasets without quantitative success measurement, denoted by V, evaluated them on datasets using quantitative success metrics, denoted by E, or validated them using examples, use-cases, and/or formal proofs, denoted by F.
- Real-time refers to the ability of the proposed system to work in a real online environment. It is important to note that empty fields do not necessarily mean that the system is not applicable, but that the question of such use was not considered in the paper. The papers which support real-time operation are marked with a plus sign in this column. Question marks denote that the paper left an impression that it should support real-time usage, but it did not contain clear evidence for it.
8. Discussion
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Verizon. 2020 Data Breach Investigations Report (DBIR). 2020. Available online: https://enterprise.verizon.com/resources/reports/dbir/2020/introduction/ (accessed on 1 September 2020).
- Bhatt, S.; Manadhata, P.K.; Zomlot, L. The operational role of security information and event management systems. IEEE Secur. Priv. 2014, 12, 35–41. [Google Scholar] [CrossRef]
- MIT Lincoln Laboratory. 2000 DARPA Intrusion Detection Scenario Specific Datasets. Available online: https://www.ll.mit.edu/r-d/datasets/2000-darpa-intrusion-detection-scenario-specific-datasets (accessed on 11 August 2020).
- Endsley, M.R. Design and evaluation for situation awareness enhancement. In Proceedings of the Human Factors Society Annual Meeting; Sage: Los Angeles, CA, USA, 1988; pp. 97–101. [Google Scholar]
- Tadda, G.P.; Salerno, J.S. Overview of cyber situation awareness. In Cyber Situational Awareness; Springer: Boston, MA, USA, 2010; pp. 15–35. [Google Scholar]
- Barford, P.; Dacier, M.; Dietterich, T.G.; Fredrikson, M.; Giffin, J.; Jajodia, S.; Jha, S.; Li, J.; Liu, P.; Ning, P.; et al. Cyber SA: Situational awareness for cyber defense. In Cyber Situational Awareness; Springer: Boston, MA, USA, 2010; pp. 3–13. [Google Scholar]
- Axelsson, S. The base-rate fallacy and the difficulty of intrusion detection. ACM Trans. Inf. Syst. Secur. (TISSEC) 2000, 3, 186–205. [Google Scholar] [CrossRef]
- Ilgun, K.; Kemmerer, R.A.; Porras, P.A. State transition analysis: A rule-based intrusion detection approach. IEEE Trans. Softw. Eng. 1995, 21, 181–199. [Google Scholar] [CrossRef]
- Bass, T. Intrusion detection systems and multisensor data fusion. Commun. ACM 2000, 43, 99–105. [Google Scholar] [CrossRef]
- Yang, S.J.; Du, H.; Holsopple, J.; Sudit, M. Attack projection. In Cyber Defense and Situational Awareness; Springer: New York, NY, USA, 2014; pp. 239–261. [Google Scholar]
- Husák, M.; Komárková, J.; Bou-Harb, E.; Čeleda, P. Survey of attack projection, prediction, and forecasting in cyber security. IEEE Commun. Surv. Tutor. 2018, 21, 640–660. [Google Scholar] [CrossRef]
- Ahmed, A.A.; Zaman, N.A.K. Attack Intention Recognition: A Review. IJ Netw. Secur. 2017, 19, 244–250. [Google Scholar]
- Abdlhamed, M.; Kifayat, K.; Shi, Q.; Hurst, W. Intrusion prediction systems. In Information Fusion for Cyber-Security Analytics; Springer International Publishing: Cham, Switzerland, 2017; pp. 155–174. [Google Scholar]
- Leau, Y.B.; Manickam, S. Network security situation prediction: A review and discussion. In International Conference on Soft Computing, Intelligence Systems, and Information Technology; Springer: Berlin/Heidelberg, Germany, 2015; pp. 424–435. [Google Scholar]
- Li, J.; Ou, X.; Rajagopalan, R. Uncertainty and risk management in cyber situational awareness. In Cyber Situational Awareness; Springer: Boston, MA, USA, 2010; pp. 51–68. [Google Scholar]
- Endsley, M.R.; Connors, E.S. Foundation and challenges. In Cyber Defense and Situational Awareness; Springer: New York, NY, USA, 2014; pp. 7–27. [Google Scholar]
- Salah, S.; Maciá-Fernández, G.; DíAz-Verdejo, J.E. A model-based survey of alert correlation techniques. Comput. Netw. 2013, 57, 1289–1317. [Google Scholar] [CrossRef]
- Hubballi, N.; Suryanarayanan, V. False alarm minimization techniques in signature-based intrusion detection systems: A survey. Comput. Commun. 2014, 49, 1–17. [Google Scholar] [CrossRef]
- Husák, M.; Kašpar, J. Towards predicting cyber attacks using information exchange and data mining. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 536–541. [Google Scholar]
- Navarro, J.; Deruyver, A.; Parrend, P. A systematic survey on multi-step attack detection. Comput. Secur. 2018, 76, 214–249. [Google Scholar] [CrossRef]
- Mirheidari, S.A.; Arshad, S.; Jalili, R. Alert correlation algorithms: A survey and taxonomy. In Cyberspace Safety and Security; Springer: New York, NY, USA, 2013; pp. 183–197. [Google Scholar]
- Zhou, C.V.; Leckie, C.; Karunasekera, S. A survey of coordinated attacks and collaborative intrusion detection. Comput. Secur. 2010, 29, 124–140. [Google Scholar] [CrossRef]
- Vasilomanolakis, E.; Karuppayah, S.; Mühlhäuser, M.; Fischer, M. Taxonomy and survey of collaborative intrusion detection. ACM Comput. Surv. (CSUR) 2015, 47, 1–33. [Google Scholar] [CrossRef]
- Salerno, J. Measuring situation assessment performance through the activities of interest score. In Proceedings of the 2008 11th International Conference on Information Fusion, Cologne, Germany, 30 June–3 July 2008; pp. 1–8. [Google Scholar]
- Valdes, A.; Skinner, K. Probabilistic alert correlation. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2001; pp. 54–68. [Google Scholar]
- Valeur, F.; Vigna, G.; Kruegel, C.; Kemmerer, R.A. Comprehensive approach to intrusion detection alert correlation. IEEE Trans. Dependable Secur. Comput. 2004, 1, 146–169. [Google Scholar] [CrossRef]
- GhasemiGol, M.; Ghaemi-Bafghi, A. E-correlator: An entropy-based alert correlation system. Secur. Commun. Netw. 2015, 8, 822–836. [Google Scholar] [CrossRef]
- Sadoddin, R.; Ghorbani, A.A. An incremental frequent structure mining framework for real-time alert correlation. Comput. Secur. 2009, 28, 153–173. [Google Scholar] [CrossRef]
- Roschke, S.; Cheng, F.; Meinel, C. A new alert correlation algorithm based on attack graph. In Computational Intelligence in Security for Information Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 58–67. [Google Scholar]
- Zhang, Y.; Zhao, S.; Zhang, J. RTMA: Real time mining algorithm for multi-step attack scenarios reconstruction. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 2103–2110. [Google Scholar]
- Ning, P.; Cui, Y.; Reeves, D.S. Constructing attack scenarios through correlation of intrusion alerts. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 245–254. [Google Scholar]
- Ning, P.; Cui, Y.; Reeves, D.S. Analyzing intensive intrusion alerts via correlation. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2002; pp. 74–94. [Google Scholar]
- Ning, P.; Xu, D. Learning attack strategies from intrusion alerts. In Proceedings of the 10th ACM Conference on Computer and Communications Security, New York, NY, USA, 27–31 October 2003; pp. 200–209. [Google Scholar]
- Ning, P.; Cui, Y.; Reeves, D.S.; Xu, D. Techniques and tools for analyzing intrusion alerts. ACM Trans. Inf. Syst. Secur. (TISSEC) 2004, 7, 274–318. [Google Scholar] [CrossRef]
- Saad, S.; Traore, I. Extracting attack scenarios using intrusion semantics. In International Symposium on Foundations and Practice of Security; Springer: Berlin/Heidelberg, Germany, 2012; pp. 278–292. [Google Scholar]
- Saad, S.; Traore, I. Semantic aware attack scenarios reconstruction. J. Inf. Secur. Appl. 2013, 18, 53–67. [Google Scholar] [CrossRef]
- Liu, Z.; Wang, C.; Chen, S. Correlating multi-step attack and constructing attack scenarios based on attack pattern modeling. In Proceedings of the 2008 International Conference on Information Security and Assurance (ISA 2008), Busan, Korea, 24–26 April 2008; pp. 214–219. [Google Scholar]
- Barzegar, M.; Shajari, M. Attack scenario reconstruction using intrusion semantics. Expert Syst. Appl. 2018, 108, 119–133. [Google Scholar] [CrossRef]
- Soleimani, M.; Ghorbani, A.A. Multi-layer episode filtering for the multi-step attack detection. Comput. Commun. 2012, 35, 1368–1379. [Google Scholar] [CrossRef]
- Ramaki, A.A.; Amini, M.; Atani, R.E. RTECA: Real time episode correlation algorithm for multi-step attack scenarios detection. Comput. Secur. 2015, 49, 206–219. [Google Scholar] [CrossRef]
- Yu, D.; Frincke, D. Improving the quality of alerts and predicting intruder’s next goal with Hidden Colored Petri-Net. Comput. Netw. 2007, 51, 632–654. [Google Scholar] [CrossRef]
- Fava, D.S.; Byers, S.R.; Yang, S.J. Projecting cyberattacks through variable-length markov models. IEEE Trans. Inf. Forensics Secur. 2008, 3, 359–369. [Google Scholar] [CrossRef]
- Farhadi, H.; AmirHaeri, M.; Khansari, M. Alert correlation and prediction using data mining and HMM. ISeCure ISC Int. J. Inf. Secur. 2011, 3, 77–101. [Google Scholar]
- Wang, L.; Liu, A.; Jajodia, S. An efficient and unified approach to correlating, hypothesizing, and predicting intrusion alerts. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2005; pp. 247–266. [Google Scholar]
- Kendall, K.K.R. A Database of Computer Attacks for the Evaluation of Intrusion Detection Systems. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 1999. [Google Scholar]
- MIT Lincoln Laboratory. 1999 DARPA Intrusion Detection Evaluation Dataset. 1999. Available online: https://www.ll.mit.edu/r-d/datasets/1999-darpa-intrusion-detection-evaluation-dataset (accessed on 11 August 2020).
- DEF CON. DEF CON. Available online: https://www.defcon.org (accessed on 26 August 2020).
- DEF CON. DEF CON CTF Archive. Available online: https://www.defcon.org/html/links/dc-ctf.html (accessed on 11 August 2020).
- Gharib, A.; Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. An evaluation framework for intrusion detection dataset. In Proceedings of the 2016 International Conference on Information Science and Security (ICISS), Pattaya, Thailand, 19–22 December 2016; pp. 1–6. [Google Scholar]
- Vigna, G. Teaching hands-on network security: Testbeds and live exercises. J. Inf. Warf. 2003, 2, 8–24. [Google Scholar]
- Vigna, G.; Eckmann, S.T.; Kemmerer, R.A. Attack languages. In Proceedings of the IEEE Information Survivability Workshop, Boston, MA, USA, 24–26 October 2000. [Google Scholar]
- McHugh, J. Testing intrusion detection systems: A critique of the 1998 and 1999 darpa intrusion detection system evaluations as performed by lincoln laboratory. ACM Trans. Inf. Syst. Secur. (TISSEC) 2000, 3, 262–294. [Google Scholar] [CrossRef]
- Brown, C.; Cowperthwaite, A.; Hijazi, A.; Somayaji, A. Analysis of the 1999 darpa/lincoln laboratory ids evaluation data with netadhict. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–7. [Google Scholar]
- Shiravi, A.; Shiravi, H.; Tavallaee, M.; Ghorbani, A.A. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur. 2012, 31, 357–374. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the 4th International Conference on Information Systems Security and Privacy (ICISSP 2018), Funchal, Portugal, 22–24 January 2018; pp. 108–116. [Google Scholar]
- Provos, N. A Virtual Honeypot Framework. In Proceedings of the USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; pp. 1–14. [Google Scholar]
- NETRESEC AB. Publicly Available PCAP Files. 2015. Available online: https://www.netresec.com/?page=PcapFiles (accessed on 13 May 2020).
- Porras, P.A.; Fong, M.W.; Valdes, A. A mission-impact-based approach to INFOSEC alarm correlation. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2002; pp. 95–114. [Google Scholar]
- Hossain, M.N.; Milajerdi, S.M.; Wang, J.; Eshete, B.; Gjomemo, R.; Sekar, R.; Stoller, S.; Venkatakrishnan, V. SLEUTH: Real-time attack scenario reconstruction from COTS audit data. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 487–504. [Google Scholar]
- Cuppens, F.; Miege, A. Alert correlation in a cooperative intrusion detection framework. In Proceedings of the 2002 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12–15 May 2002; pp. 202–215. [Google Scholar]
- Morin, B.; Debar, H. Correlation of intrusion symptoms: An application of chronicles. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2003; pp. 94–112. [Google Scholar]
- Morin, B.; Mé, L.; Debar, H.; Ducassé, M. M2D2: A formal data model for IDS alert correlation. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2002; pp. 115–137. [Google Scholar]
- Cuppens, F. Managing alerts in a multi-intrusion detection environment. In Proceedings of the Seventeenth Annual Computer Security Applications Conference, New Orleans, LA, USA, 10–14 December 2001. [Google Scholar]
- Ghafir, I.; Kyriakopoulos, K.G.; Lambotharan, S.; Aparicio-Navarro, F.J.; AsSadhan, B.; BinSalleeh, H.; Diab, D.M. Hidden Markov models and alert correlations for the prediction of advanced persistent threats. IEEE Access 2019, 7, 99508–99520. [Google Scholar] [CrossRef]
- Wang, L.; Liu, A.; Jajodia, S. Using attack graphs for correlating, hypothesizing, and predicting intrusion alerts. Comput. Commun. 2006, 29, 2917–2933. [Google Scholar] [CrossRef]
- Ning, P.; Xu, D.; Healey, C.G.; Amant, R.S. Building Attack Scenarios through Integration of Complementary Alert Correlation Method. 2004. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.60.4412 (accessed on 19 October 2020).
- Cheung, S.; Lindqvist, U.; Fong, M.W. Modeling multistep cyber attacks for scenario recognition. In Proceedings of the DARPA Information Survivability Conference and Exposition, Washington, DC, USA, 22–24 April 2003; pp. 284–292. [Google Scholar]
- Qin, X.; Lee, W. Statistical causality analysis of infosec alert data. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2003; pp. 73–93. [Google Scholar]
- Qin, X.; Lee, W. Attack plan recognition and prediction using causal networks. In Proceedings of the 20th Annual Computer Security Applications Conference, Tucson, AZ, USA, 6–10 December 2004; pp. 370–379. [Google Scholar]
- Zhu, B.; Ghorbani, A.A. Alert correlation for extracting attack strategies. IJ Netw. Secur. 2006, 3, 244–258. [Google Scholar]
- Pietraszek, T.; Tanner, A. Data mining and machine learning—Towards reducing false positives in intrusion detection. Inf. Secur. Tech. Rep. 2005, 10, 169–183. [Google Scholar] [CrossRef]
- Holgado, P.; Villagrá, V.A.; Vazquez, L. Real-time multistep attack prediction based on hidden markov models. IEEE Trans. Dependable Secur. Comput. 2017, 17, 134–147. [Google Scholar] [CrossRef]
- Milajerdi, S.M.; Gjomemo, R.; Eshete, B.; Sekar, R.; Venkatakrishnan, V. Holmes: Real-time apt detection through correlation of suspicious information flows. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 1137–1152. [Google Scholar]
- Hughes, T.; Sheyner, O. Attack scenario graphs for computer network threat analysis and prediction. Complexity 2003, 9, 15–18. [Google Scholar] [CrossRef]
- Geib, C.W.; Goldman, R.P. Plan recognition in intrusion detection systems. In Proceedings of the DARPA Information Survivability Conference and Exposition II. DISCEX’01, Anaheim, CA, USA, 12–14 June 2001; pp. 46–55. [Google Scholar]
- Ren, H.; Stakhanova, N.; Ghorbani, A.A. An online adaptive approach to alert correlation. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment; Springer: Berlin/Heidelberg, Germany, 2010; pp. 153–172. [Google Scholar]
- Dain, O.M.; Cunningham, R.K. Building scenarios from a heterogeneous alert stream. In Proceedings of the 2001 IEEE Workshop on Information Assurance and Security; United States Military Academy: West Point, NY, USA, 2001. [Google Scholar]
- Dain, O.; Cunningham, R.K. Fusing a heterogeneous alert stream into scenarios. In Applications of Data Mining in Computer Security; Springer: Boston, MA, USA, 2002; pp. 103–122. [Google Scholar]
- Noel, S.; Robertson, E.; Jajodia, S. Correlating intrusion events and building attack scenarios through attack graph distances. In Proceedings of the 20th Annual Computer Security Applications Conference, Tucson, AZ, USA, 6–10 December 2004; pp. 350–359. [Google Scholar]
- Morin, B.; Mé, L.; Debar, H.; Ducassé, M. A logic-based model to support alert correlation in intrusion detection. Inf. Fusion 2009, 10, 285–299. [Google Scholar] [CrossRef]
- Cuppens, F.; Ortalo, R. Lambda: A language to model a database for detection of attacks. In International Workshop on Recent Advances in Intrusion Detection; Springer: Berlin/Heidelberg, Germany, 2000; pp. 197–216. [Google Scholar]
- Templeton, S.J.; Levitt, K. A requires/provides model for computer attacks. In NSPW ’00: Proceedings of the 2000 Workshop on New Security Paradigms; Association for Computing Machinery: New York, NY, USA, 2001; pp. 31–38. [Google Scholar]
- Cuppens, F.; Autrel, F.; Miege, A.; Benferhat, S. Correlation in an intrusion detection process. In Proceedings of the Internet Security Communication Workshop, Tunis, Tunisia, 19–21 September 2002; pp. 153–172. [Google Scholar]
- Goldman, R.P.; Heimerdinger, W.; Harp, S.A.; Geib, C.W.; Thomas, V.; Carter, R.L. Information modeling for intrusion report aggregation. In Proceedings of the DARPA Information Survivability Conference and Exposition II. DISCEX’01, Anaheim, CA, USA, 12–14 June 2001; pp. 329–342. [Google Scholar]
- Valdes, A.D.J.; Skinner, K. Probabilistic Alert Correlation. U.S. Patent 7,917,393, 29 March 2011. [Google Scholar]
- Eckmann, S.T.; Vigna, G.; Kemmerer, R.A. STATL: An attack language for state-based intrusion detection. J. Comput. Secur. 2002, 10, 71–103. [Google Scholar] [CrossRef]
- Ghafir, I.; Hammoudeh, M.; Prenosil, V.; Han, L.; Hegarty, R.; Rabie, K.; Aparicio-Navarro, F.J. Detection of advanced persistent threat using machine-learning correlation analysis. Future Gener. Comput. Syst. 2018, 89, 349–359. [Google Scholar] [CrossRef]
- Ramaki, A.A.; Khosravi-Farmad, M.; Bafghi, A.G. Real time alert correlation and prediction using Bayesian networks. In Proceedings of the 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), Rasht, Iran, 8–10 September 2015; pp. 98–103. [Google Scholar]
- Albanese, M.; Jajodia, S.; Pugliese, A.; Subrahmanian, V. Scalable analysis of attack scenarios. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2011; pp. 416–433. [Google Scholar]
- Fredj, O.B. A realistic graph-based alert correlation system. Secur. Commun. Netw. 2015, 8, 2477–2493. [Google Scholar] [CrossRef]
- Ahmadinejad, S.H.; Jalili, S.; Abadi, M. A hybrid model for correlating alerts of known and unknown attack scenarios and updating attack graphs. Comput. Netw. 2011, 55, 2221–2240. [Google Scholar] [CrossRef]
- Alhaj, T.A.; Siraj, M.M.; Zainal, A.; Elshoush, H.T.; Elhaj, F. Feature selection using information gain for improved structural-based alert correlation. PLoS ONE 2016, 11, e0166017. [Google Scholar] [CrossRef]
- Zhang, K.; Zhao, F.; Luo, S.; Xin, Y.; Zhu, H. An intrusion action-based IDS alert correlation analysis and prediction framework. IEEE Access 2019, 7, 150540–150551. [Google Scholar] [CrossRef]
- Hu, H.; Liu, J.; Zhang, Y.; Liu, Y.; Xu, X.; Huang, J. Attack scenario reconstruction approach using attack graph and alert data mining. J. Inf. Secur. Appl. 2020, 54, 102522. [Google Scholar] [CrossRef]
- Huang, M.Y.; Jasper, R.J.; Wicks, T.M. A large scale distributed intrusion detection framework based on attack strategy analysis. Comput. Netw. 1999, 31, 2465–2475. [Google Scholar] [CrossRef]
- Albanese, M.; Erbacher, R.F.; Jajodia, S.; Molinaro, C.; Persia, F.; Picariello, A.; Sperlì, G.; Subrahmanian, V. Recognizing unexplained behavior in network traffic. In Network Science and Cybersecurity; Springer: New York, NY, USA, 2014; pp. 39–62. [Google Scholar]
- Dousson, C. Extending and unifying chronicle representation with event counters. In Proceedings of the 15th European Conference on Artificial Intelligence, Lyon, France, 21–26 July 2002; IOS Press: Amsterdam, The Netherlands, 2002; pp. 257–261. [Google Scholar]
- Lindqvist, U.; Porras, P.A. Detecting computer and network misuse through the production-based expert system toolset (P-BEST). In Proceedings of the 1999 IEEE Symposium on Security and Privacy (Cat. No. 99CB36344), Oakland, CA, USA, 14 May 1999; pp. 146–161. [Google Scholar]
- Mandiant, A. Exposing One of China’s Cyber Espionage Units. 2013. Available online: https://www.fireeye.com/content/dam/fireeye-www/services/pdfs/mandiant-apt1-report.pdf (accessed on 13 May 2020).
- Keromytis, A.D. Transparent Computing Engagement 3 Data Release. 2018. Available online: https://github.com/darpa-i2o/Transparent-Computing (accessed on 8 October 2020).
- Ester, M.; Kriegel, H.P.; Sander, J.; Xu, X. A Density-Based Algorithm for Discovering Clusters in Large Spatial Databases with Noise; Kdd: Seattle, WA, USA, 1996; pp. 226–231. [Google Scholar]
- Common Vulnerabilities and Exposures (CVE); The MITRE Corporation: McLean, VA, USA; Available online: https://cve.mitre.org/ (accessed on 1 September 2020).
- CESNET. 1998 DARPA Intrusion Detection Evaluation Dataset. 2016. Available online: https://sabu.cesnet.cz/en/start (accessed on 21 August 2020).
- Ou, X.; Govindavajhala, S.; Appel, A.W. MulVAL: A Logic-Based Network Security Analyzer. In Proceedings of the USENIX Security Symposium, Baltimore, MD, USA, 31 July–5 August 2005; pp. 113–128. [Google Scholar]
- Sommer, R.; Paxson, V. Outside the closed world: On using machine learning for network intrusion detection. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 305–316. [Google Scholar]
- Strom, B.E.; Applebaum, A.; Miller, D.P.; Nickels, K.C.; Pennington, A.G.; Thomas, C.B. Mitre Att&ck: Design and Philosophy; Technical Report; The MITRE Corporation: McLean, VA, USA, 2018; Available online: https://www.mitre.org/sites/default/files/publications/pr-18-0944-11-mitre-attack-design-and-philosophy.pdf (accessed on 1 September 2020).
| Salah et al. [17] | Hubballi and Suryanarayanan [18] | Husák et al. [11] | |
|---|---|---|---|
| Year | 2013 | 2014 | 2018 |
| Scope | Alert correlation | False alert minimization (a subset of more specific methods) | Attack projection Attack intention recognition Attack prediction Network security situation forecasting |
| Classes of models / methods / techniques | Similarity based methods Attribute based Temporal based Sequential based Pre-post conditions Graphs Codebook Markov models Bayesian networks Neural networks Others Case based methods Expert based Expert rules Pre-defined scenarios Inferred knowledge | Signature enhancement Stateful signatures Vulnerability signatures Alarm Mining Clustering Classification Neural Network Frequent pattern mining Alarm Correlation Multi-Step Knowledge based Complementary evidence based Causal relation based Fusion based Attack Graph based Rule based Alarm Verification Flow analysis Alarm Prioritization Hybrid methods | Discrete Models Graph models Attack Graphs Bayesian Networks Markov Models Game Theoretical models Continuous Models Time Series Grey Models Machine Learning and Data Mining Machine Learning Neural Networks SVM (etc.) Data Mining Other Approaches (e.g., similarity based correlation) |
| Notes regarding evaluation | - | - | Evaluation in surveyed proposals: Proof-of-concept Testbed Live data (e.g., honeynet) Public Dataset (DARPA, etc.) Custom Dataset Virtual Attacks Comparison with other algorithms |
| Identified open research problems | Lack of standard strategies for evaluating performance and effectiveness Development of scalable system architectures Improving FP reduction Development of new strategies for coping with unseen types of attacks | Evaluation on a common dataset Analysis of approach performance Standardization of formats and reports Evaluation of systems’ real time operation Adapting to changes in the environment | Methods relying on attack models require continuous model maintenance Low quality of evaluation datasets Low prediction accuracy and usability in practice Evaluation of methods on a common dataset with common and meaningful metrics Discovering novel attacks and security paradigms |
| Metric | Used in # Approaches | References |
|---|---|---|
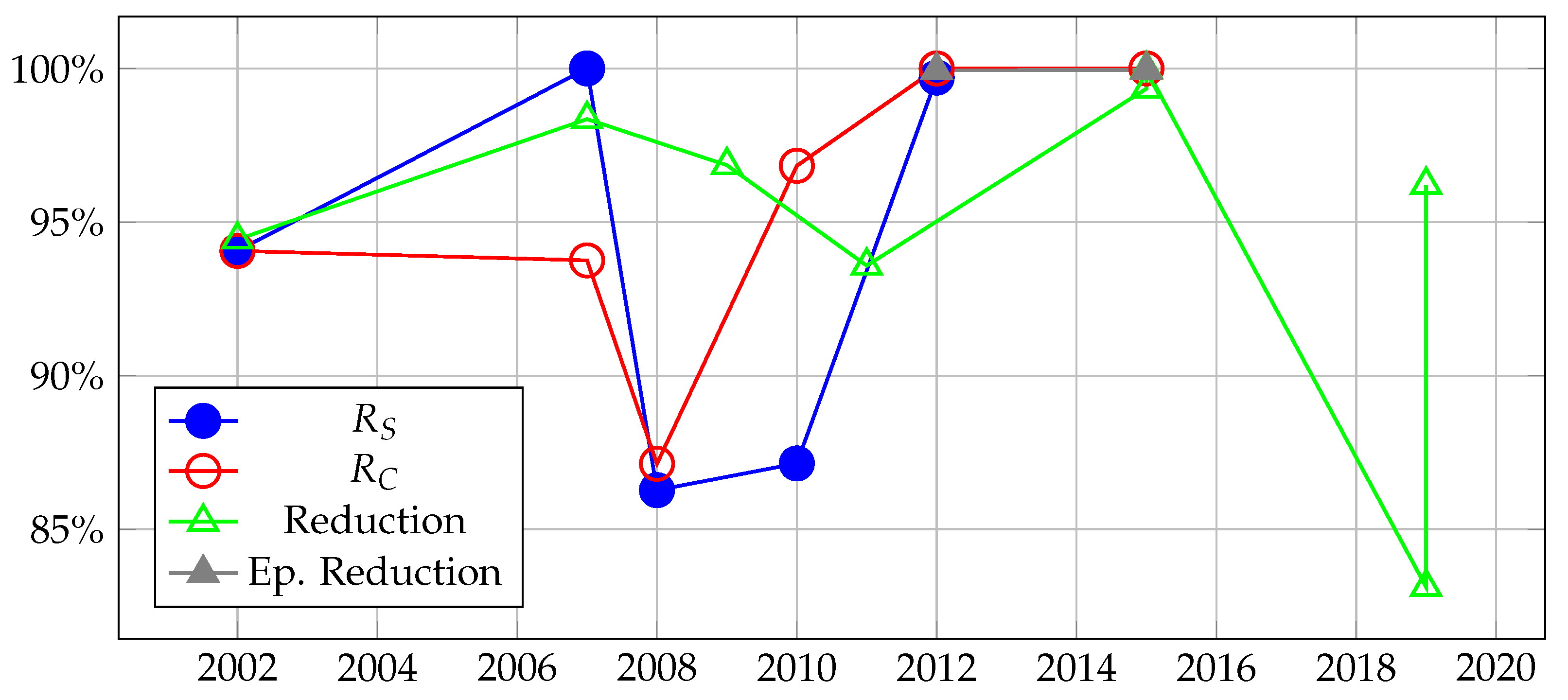
| Reduction (8) | 6 | [25,26,27,28,29,30] |
| (5) | 4 | [31,32,33,34,35,36,37,38] |
| (6) | 4 | [31,32,33,34,35,36,37,38] |
| Episode Reduction (9) | 2 | [39,40] |
| QoA (7) | 1 | [41] |
| Recall (1) | 0 | - |
| Precision (2) | 0 | - |
| Fragmentation (3) | 0 | - |
| Misassociation (4) | 0 | - |
| Details | Datasets Used | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
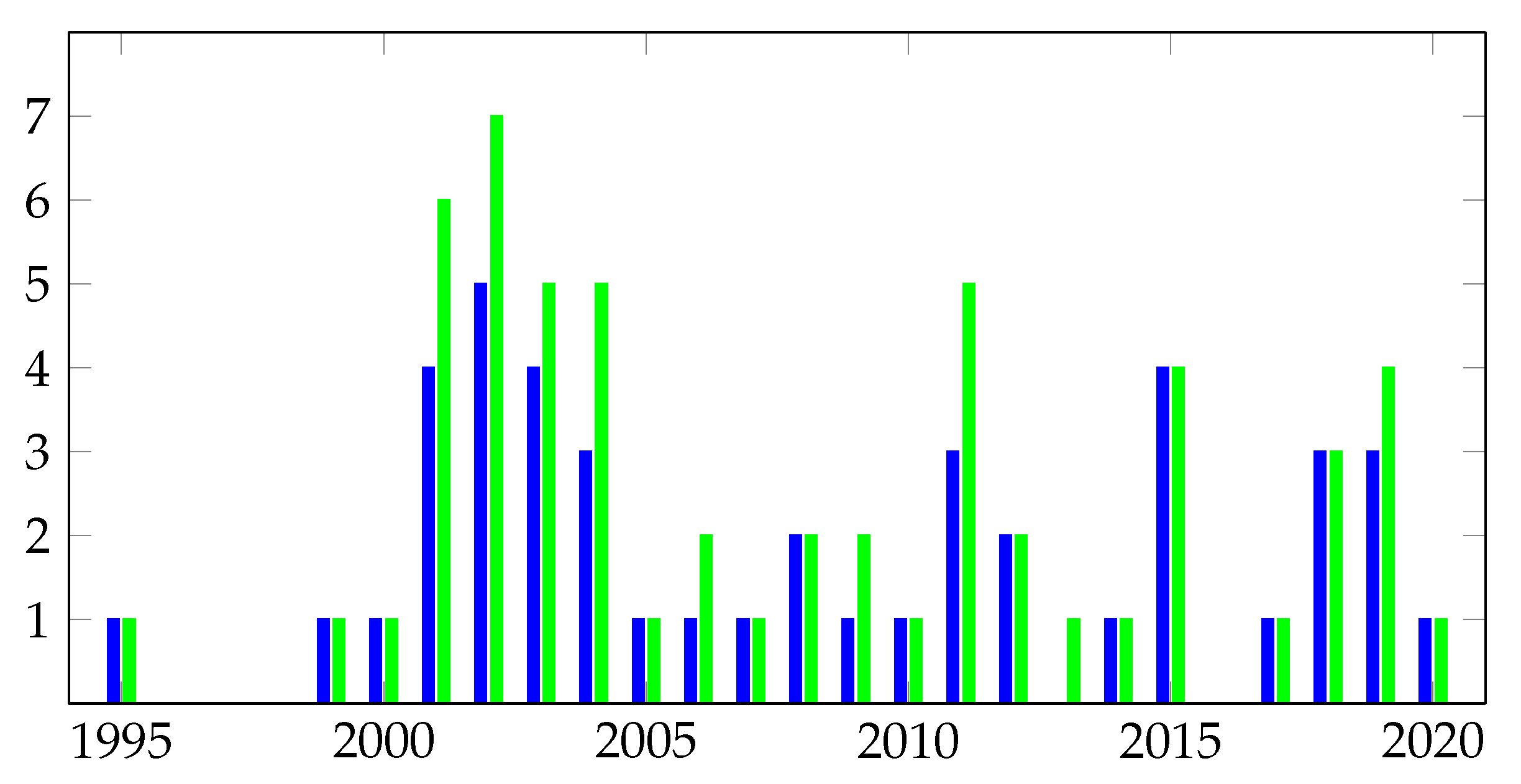
| Papers | Year | Models | Domain Knowledge | Level of Evaluation | Real-Time | Cyber Treasure Hunt | DARPA 1999 | DARPA 2000 | DARPA GCP (ver.) | DEFCON (#) | LiveD-Data | Custom/Experiment |
| Ilgun et al. [8] | 1995 | Language | V | + | ||||||||
| Huang et al. [95] | 1999 | Language | - | |||||||||
| Cuppens and Ortalo [81] | 2000 | Language | F | |||||||||
| Valdes and Skinner [25] | 2001 | Sim. | * | E | + | + | ||||||
| Templeton and Levitt [82] | 2001 | Language | F | |||||||||
| Goldman et al. [75,84] | 2001 | KB, Graph | *** | V | + | |||||||
| Dain and Cunningham [77] | 2001 | ML, DM | * | E | + | 8 | ||||||
| Ning et al. [31,32,33,34] | 2002 | KB | *** | E | + | 8 | ||||||
| Eckmann et al. [86] | 2002 | Language | V | + | ||||||||
| Morin et al. [62,80] | 2002 | KB | *** | F | ||||||||
| Morin and Debar [61] | 2003 | KB | *** | V | ? | + | ||||||
| Cuppens and Miege [60] | 2002 | KB | *** | V | + | |||||||
| Cuppens et al. [83] | 2002 | KB | *** | F | ||||||||
| Cheung et al. [67] | 2003 | KB | *** | V | + | 2.0 | ||||||
| Hughes and Sheyner [74] | 2003 | KB, Graph | *** | F | ||||||||
| Qin and Lee [68,69] | 2003 | Sim., KB | ** | E | 3.1 | 9 | ||||||
| Valeur et al. [26] | 2004 | Sim. | * | E | + | + | + | 9 | + | + | ||
| Ning et al. [66] | 2004 | Sim., KB | ** | V | + | |||||||
| Noel et al. [79] | 2004 | KB, Graph | *** | V | ? | + | ||||||
| Wang et al. [44,65] | 2005 | Sim., Graph | ** | V | + | + | + | + | ||||
| Zhu and Ghorbani [70] | 2006 | ML Ensemble | * | V | ? | + | ||||||
| Yu and Frincke [41] | 2007 | KB, HCPN | ** | E | + | + | ? | |||||
| Liu et al. [37] | 2008 | KB, Graph | ** | E | ? | + | ||||||
| Fava et al. [42] | 2008 | Markov models | * | E | + | + | ||||||
| Sadoddin and Ghorbani [28] | 2009 | DM: FSP_Growth | * | E | ? | + | + | + | ||||
| Ren et al. [76] | 2010 | Sim., ML | * | E | + | + | + | |||||
| Roschke et al. [29] | 2011 | Graph | ** | E | ? | + | ||||||
| Ahmadinejad et al. [91] | 2011 | Graph, Sim. | ** | E | + | + | + | |||||
| Albanese et al. [89] | 2011 | KB, Graph | *** | E | + | + | ||||||
| Saad and Traore [35,36] | 2012 | KB, Graph | ** | E | + | + | ||||||
| Soleimani and Ghorbani [39] | 2012 | DM, ML: DT | * | E | + | + | + | |||||
| Albanese et al. [96] | 2014 | KB, Rules | *** | - | + | |||||||
| Fredj [90] | 2015 | KB, Graph | ** | E | + | 17 | ||||||
| GhasemiGol and Ghaemi-Bafghi [27] | 2015 | ML | * | E | + | |||||||
| Ramaki et al. [40] | 2015 | DM on streams | ** | E | + | + | 3.1 | + | ||||
| Ramaki et al. [88] | 2015 | KB, Graph, ML | ** | E | + | + | ||||||
| Holgado et al. [72] | 2017 | KB, ML: HMM | ** | V | + | + | + | |||||
| Barzegar and Shajari [38] | 2018 | Sim. | * | E | + | + | ||||||
| Husák and Kašpar [11] | 2018 | DM: TopKRules | * | V | ? | + | ||||||
| Ghafir et al. [64,87] | 2018 | KB, ML: HMM | ** | E | + | + | + | |||||
| Milajerdi et al. [73] | 2019 | KB, Graph | *** | E | + | + | + | |||||
| Zhang et al. [30] | 2019 | ML: MCh | * | E | + | + | ||||||
| Zhang et al. [93] | 2019 | ML, Rules | * | E | + | + | * | |||||
| Hu et al. [94] | 2020 | ML, Graph | ** | V | 23 | + | ||||||
| Papers | Year | Scenario LLDOS 1.0 | ||
|---|---|---|---|---|
| (6) | (5) | QoA (7) | ||
| Saad and Traore [35,36] | 2012 | (P) | (P) | |
| Ramaki et al. [88] | 2015 | (P) | ||
| Ren et al. [76] | 2010 | |||
| Ning et al. [31,32,33,34] | 2002 | |||
| Yu and Frinckle [41] | 2007 | |||
| Liu et al. [37] | 2008 | |||
| Papers | Year | LLDOS 1.0 | Reduction on LLDOS 1.0 and LLDOS 2.0.2 | |
|---|---|---|---|---|
| Reduction (8) | Episode Reduction (9) | |||
| GhasemiGol and Ghaemi-Bafghi [27] | 2015 | |||
| Ramaki et al. [88] | 2015 | |||
| Yu and Frincke [41] | 2007 | |||
| Sadoddin and Ghorbani [28] | 2009 | |||
| Zhang et al. [30] | 2019 | (P) | ||
| Ning et al., Ning and Xu [31,32,33,34] | 2002 | |||
| Ahmadinejad et al. [91] | 2011 | |||
| Zhang et al. [93] | 2019 | |||
| Valeur et al. [26] | 2004 | |||
| Ramaki et al. [40] | 2015 | (P) | ||
| Soleimani and Ghorbani [39] | 2012 | (P) | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kovačević, I.; Groš, S.; Slovenec, K. Systematic Review and Quantitative Comparison of Cyberattack Scenario Detection and Projection. Electronics 2020, 9, 1722. https://doi.org/10.3390/electronics9101722
Kovačević I, Groš S, Slovenec K. Systematic Review and Quantitative Comparison of Cyberattack Scenario Detection and Projection. Electronics. 2020; 9(10):1722. https://doi.org/10.3390/electronics9101722
Chicago/Turabian StyleKovačević, Ivan, Stjepan Groš, and Karlo Slovenec. 2020. "Systematic Review and Quantitative Comparison of Cyberattack Scenario Detection and Projection" Electronics 9, no. 10: 1722. https://doi.org/10.3390/electronics9101722
APA StyleKovačević, I., Groš, S., & Slovenec, K. (2020). Systematic Review and Quantitative Comparison of Cyberattack Scenario Detection and Projection. Electronics, 9(10), 1722. https://doi.org/10.3390/electronics9101722





