Abstract
As a new generation of mobile communication networks, 6G security faces many new security challenges. Vehicle to Everything (V2X) will be an important part of 6G. In V2X, connected and automated vehicles (CAVs) need to frequently share data with other vehicles and infrastructures. Therefore, identity revocation technology in the authentication is an important way to secure CAVs and other 6G scenario applications. This paper proposes an efficient credential revocation scheme with a four-layer architecture. First, a rapid pre-filtration layer is constructed based on the cuckoo filter, responsible for the initial screening of credentials. Secondly, a directed routing layer and the precision judgement layer are designed based on the consistency hash and the dynamic RSA accumulator. By proposing the dynamic expansion of the RSA accumulator and load-balancing algorithm, a smaller and more stable revocation delay can be achieved when many users and terminal devices access 6G. Finally, a trusted storage layer is built based on the blockchain, and the key revocation parameters are uploaded to the blockchain to achieve a tamper-proof revocation mechanism and trusted data traceability. Based on this architecture, this paper also proposes a detailed identity credential revocation and verification process. Compared to existing solutions, this paper’s solution has a combined average improvement of 59.14% in the performance of the latency of the cancellation of the inspection, and the system has excellent load balancing, with a standard deviation of only 11.62, and the maximum deviation is controlled within the range of ±4%.
1. Introduction
With the release of the 6G standard schedule, the research and development of 6G has entered a critical period. 6G networks will incorporate multiple heterogeneous networks, typified by Vehicle to Everything (V2X) []. In recent years, there has been an influx of new research in the V2X research direction regarding better control of intelligent vehicles. The authors in [] propose a novel predictive battery thermal and energy management (p-BTEM) strategy for connected and automated electric vehicles. The study effectively reduces energy consumption in dynamic traffic scenarios by integrating forward-looking constant and time-varying factors, such as vehicle, road, and traffic information, through a cloud-based predictive control framework. The authors in [] focus on the dynamic characteristics of the V2X environment, which pose significant challenges to ensuring the robustness of intrusion detection systems (IDS). This study examines the adversarial robustness of machine learning-based IDS, analyzes AI-based evasion techniques, data poisoning threats, and challenges in detecting abnormal behavior. The authors in [] focus on the electromagnetic interference (EMI) effects in V2X and study a harmonic suppression multi-input multi-output (MIMO) antenna, which is expected to help alleviate EMI in congested areas with dense IoT devices. As can be seen, there are currently many research directions for V2X. However, research on identity revocation in 6G V2X scenarios is still relatively lacking.
As an important part of network authentication, identity revocation has a key role in authentication in 6G []. Firstly, it is reflected in the aspect of security: identity revocation is an essential line of defense to ensure network security when the user’s identity information is stolen or there are other security risks. Timely identity revocation can prevent illegal users from continuing to use the identity to access the resources in 6G, and to protect the security of 6G and data []. Secondly, the criticality of identity revocation is also reflected in privilege management []. Identity authentication is usually closely related to privilege management, and identity revocation can accurately control the user’s access to 6G resources []. When users and end devices no longer need certain privileges or are no longer qualified to access specific resources in 6G, their corresponding privileges can be canceled immediately through identity revocation [].
The contributions of this paper are as follows:
- Firstly, we discuss a reasonable identity revocation state update mechanism in 6G scenarios and analyze the defects of a single RSA accumulator scheme. Subsequently, based on the analysis results, we propose an identity credential revocation and revocation checking scheme in 6G scenarios. The architecture of this scheme consists of four layers: a rapid pre-filtration layer, a directed routing layer, a precision judgement layer, and a trustworthy storage layer.
- Secondly, we elaborate, in detail, on the core responsibilities and implementation scheme of each layer in the four-layer architecture. In the first rapid pre-filtration layer, we adopt the cuckoo filter technology, which takes the credentials as the elements in the cuckoo filter and can achieve rapid judgment regarding whether a credential has not completed revocation, which cuts down a part of the revocation checking request and effectively reduces the pressure on the system. In the second and third layers of the directed routing layer and precision judgment layer, we propose a dynamic expansion and load-balancing algorithm based on the consistency hash and RSA accumulator, which dynamically adds or deletes the RSA accumulator according to the actual number of revocation credentials, which can achieve smaller and more stable revocation checking delay. In the fourth trusted storage layer, we adopt blockchain technology as the trusted storage medium for the revocation of important parameters in 6G scenarios to achieve a tamper-proof revocation mechanism and trusted data traceability.
- Finally, based on the above-proposed scheme, we further propose the Identity Credential Revocation and Verification Process, which divides credential revocation into active credential revocation and passive credential revocation, and propose corresponding revocation processes for different mechanisms.
This paper is organized as follows: In the Review of Related Work section, we review the development history of identity revocation techniques, list representative kinds of studies at various stages, and focus on analyzing the feasibility of combining cryptographic accumulator-based identity revocation techniques with blockchain technology. In the BCMRA Scheme Architecture section, we propose a four-layer architecture scheme for credential revocation and revocation checking. In the BCMRA Scheme-Specific Implementation section, we detail the specific implementation of the BCMRA program based on this scheme. In Identity Credential Revocation and Verification Process Based on the BCMRA Scheme section, we propose a specific process for credential revocation and a specific process for checking whether it has been revoked in 6G scenarios. In the Experimental Results section, we simulate and test the load-balancing effect, checking the latency of the schemes and analyzing their advantages. Finally, in the Conclusion, we briefly summarize this paper’s findings.
2. Review of Related Work
The authors in [] classified identity revocation methods based on the state of use of identity revocation (online or offline), type of revocation list (blacklist or whitelist), and type of evidence (direct or indirect evidence). The authors in [] classified identity revocation methods into four main types: list-based, tree-based, Online Certificate Status Protocol (OCSP)-based, and cryptographic accumulator-based. The research related to these four types of identity revocation is presented below in turn.
Certificate Revocation List (CRL) is a list-based verification system introduced by the Telecommunication Standardization Sector of the International Telecommunication Union (ITU-T) in 1988. Certificate Authorities (CAs) verify the revocation status of a certificate by constructing a CRL signature data structure for the client []. Revoked certificates are identified using a sequence number in the CRL. The CRL is updated periodically by the CAs. The main drawbacks of this identity revocation method are high system communication overhead and low system availability, and the size of the CRL increases gradually over time. To reduce the amount of data necessary to be transmitted in successive CRL queries. The authors in [] proposed a sliding-window delta-CRL based approach, where the authenticator receives only the most recent changes in the data, reducing the system communication overhead.
Tree-based identity revocation methods use a sorted tree structure to store revoked identity credentials. CAs and Verification Authorities (VAs) speed up the process of querying for revoked identity credentials by using this tree structure []. The authors in [] proposed a distributed key revocation scheme based on a shared binary tree-based distributed key revocation scheme, which solves the problem of key revocation and updating in an open environment with the help of decentralized management of binary trees; however, the average query time shows a gradual increase with the number of nodes, and the increase is more significant. The authors in [] proposed a partition-based hash tree structure to improve the search of revoked ID books; this research proposal has high query latency in large-scale revocation of ID books.
OCSP is a certificate revocation system in which a user sends a request to a responder to obtain the revocation status of the current certificate. The responder checks the status of the target certificate from a revocation list it maintains, and then returns the status to the requested user []. The OCSP system, in which the user must be connected to the Internet to validate the revocation status, has a high latency, which comes from the response time the responder’s server spends on transmitting the revocation status to the requesting user.
Compared to the above three identity revocation methods, the advantages of the encrypted accumulator-based identity revocation scheme are significant. It can not only efficiently process identity revocation transactions while keeping the overhead at a low level, but also protect the identity revocation data by encryption, effectively avoiding the risk of privacy leakage, which fundamentally enhances the security of the authentication system. The authors in [] proposed an accumulator based on the RSA (Rivest–Shamir–Adleman) algorithm for anonymous revocation of identity certificates. The authors in [] argued that, in the cryptographic accumulator-based identity revocation scheme, the user’s proof-of-membership or proof-of-non-membership could not undermine the system’s anonymity, and that an RSA-based anonymous authentication system designed a new zero-knowledge non-membership protocol and proved the security of the protocol.
Blockchain technology, with its unique advantages, opens up a new way to achieve the distributed characteristics and high availability of identity revocation. In this context, many researchers have focused on exploring the in-depth integration of blockchain technology and identity revocation mechanisms, expecting to bring innovation and change in the field of identity management with the help of blockchain’s technological features. The authors in [] proposed a system that uses blockchain to publish CA-signed certificates and revocation information, an asymmetric cryptographic accumulator-based system is proposed for identity revocation. Reference [] proposes an ID certificate revocation scheme based on asymmetric cryptographic accumulators, which distributes cryptographic accumulators via blockchain. The research is still in progress, and the corresponding test simulation data has not been published yet. The authors in [] propose a blockchain-based certificate revocation management and status verification system, which describes the node to which the certificate revocation belongs and the Bloom filter information through the extended fields of the X.509 certificate structure. The query revocation process of this research scheme is cumbersome, and the required query latency increases as the number of revoked certificates increases. The authors in [] propose an ID certificate revocation scheme based on federated blockchain and chameleon hash, which constructs an editable blockchain through chameleon hash and achieves identity revocation by deleting ID certificates, which replaces the original append revocation scheme. The original append revocation scheme. Although this research scheme has better performance in terms of revocation retrieval delay and storage space-saving, it brings problems such as impaired data integrity and tampering, untraceable history records, and difficulty in consistency maintenance.
The Table 1 compares related research in the field, where Offline indicates whether offline authentication is supported or not, Anonymity indicates whether privacy preservation is supported, i.e., the revoked data is transmitted in a non-plaintext manner, and Distributed indicates whether the scheme has distributed features to withstand a single point of failure. In summary, the blockchain-based cryptographic accumulator identity revocation scheme has the best performance in terms of query overhead and security. However, the existing related research has all proposed identity revocation schemes for single-structured networks without fully considering the compatibility and interoperability problems that may arise in 6G scenarios, which makes it difficult to maintain the consistency of the revocation information among the 6G and fails to adapt to 6G scenarios with large number of users accessing the 6G with high query overhead or 6G scenarios with massive numbers of users and terminal device access. Therefore, how to achieve a secure, efficient, and compatible identity revocation scheme in 6G scenarios is still valuable for further research.

Table 1.
Comparative analysis of identity revocation methods.
3. BCMRA Scheme Architecture
Identity revocation is an important part of authentication in 6G. According to the research status study analysis in Section 2, it can be seen that the existing identity revocation research schemes do not fully take into account the compatibility and interoperability problems that may arise in 6G scenarios. Also, it is difficult to maintain the consistency of the identity revocation information between between different trust domains in 6G, and it cannot be adapted to the 6G scenarios with massive accesses in terms of the revocation and verification time delay. In this paper, we propose a credential revocation and verification scheme executed by a trust management committee to solve the compatibility and interoperability problems between different trust domains in 6G scenarios and to achieve lower and more stable revocation verification latency through a dynamic RSA multi-accumulator and load-balancing algorithm.
In this paper, the RSA accumulator is adopted as the minimum verification unit of credential revocation and verification scheme. In the initialization phase of a system, the RSA accumulator needs to generate initialization parameters on which operations such as adding elements, deleting elements, generating proofs of membership, and verifying membership depend. A is randomly chosen as the modulus of the RSA accumulator, where p and q are large prime numbers. A base g mutually prime with N is chosen as the generating element, usually at random in the cyclic group of modulus N; initial cumulative value is .
Knowing that all members within the set of elements have been added to the RSA accumulator, the latest cumulative value can be defined as follows:
Adding a new element to the above accumulator, the latest accumulated value is updated as follows:
Further removing an element from the above accumulator, the latest accumulated value is updated as follows:
where is the multiplicative inverse of in mod , and is the Euler function, denoted by .
For an element in a set, a membership proof can be generated to show that belongs to the set X. The formula for the membership proof is
After generating the proof of membership, check whether the equation holds, and if the equation holds, prove that belongs to the set X.
When verifying the existence of a member with the traditional RSA accumulator, the precondition to reach time complexity is that the membership proof of an element is known []. When a member joins or exits the RSA accumulator, the proof of membership of an element needs to be updated to , with a time complexity of , which is linearly related to the number of members in the accumulator []. When a member joins or exits the accumulator, the proofs of other members in the accumulator are triggered by the following two updates:
- Immediate update: When a member is added or removed from the RSA accumulator, the system immediately computes and generates new member proofs for the other members in the RSA accumulator, with a time complexity of . The time complexity of other member proofs is .
- Update on verification: when members are added or removed from the RSA accumulator, the system does not update the membership proofs of other members in real-time. When other members perform authentication operations, they need to check the revocation information, and the system updates the member’s proof separately under this moment, with a time complexity of .
The above two accumulator-member proof-updating methods have their own advantages and disadvantages, of which the immediate updating mechanism is more real-time, to ensure that all the member proofs in the system are always in the latest valid state. However, the accompanying cost is the exponential growth of time complexity, and the consumption of computational and time resources on the system is large. The real-time nature of the update mechanism during verification is relatively weak, the amount of computation for each update is linearly related to the number of members, and the overall resource consumption is relatively low.
In the 6G scenario, the number of users and terminal devices is huge, and the member proves that the update-on-verification mechanism is more suitable for the 6G scenario from the three perspectives of real-time demand, resource consumption, and network communication burden. Secondly, a single simple accumulator structure cannot satisfy fast credential revocation and revocation checking, and scheme improvement and optimization are needed.
Therefore, this section proposes a credential revocation and revocation checking scheme BCMRA (Blockchain, Cuckoo Filter, Multi-RSA Accumulator) based on blockchain, cuckoo filter, consistent hash routing technique, and RSA multi-accumulator, and the following describes in detail the BCMRA scheme architecture, the identity credential revocation scheme, and the revocation credential checking scheme.
The BCMRA scheme, as shown in Figure 1, is divided into a four-layer architecture according to different functions, with the fast pre-filtering layer, the directed routing layer, the precise judgement layer, and the trusted storage layer in descending order from the top layer. The four different layers are differentiated by different colours. To better understand the meaning of this architecture diagram, one can look at it from the top down, with the data to be withdrawn flowing from the top of the diagram into the first layer of the diagram, and in turn completing all the processes of the BCMRA scheme from top to bottom. The core responsibilities and key technologies of the four-layer architecture are described in detail below.
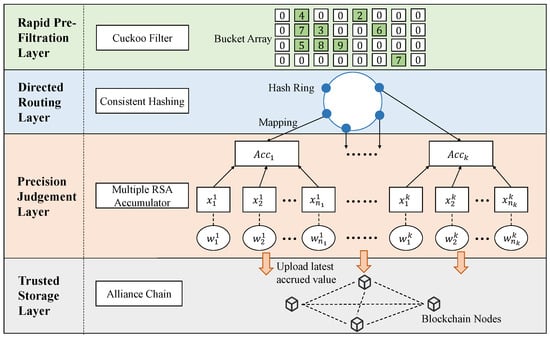
Figure 1.
BCMRA scheme architecture schematic.
4. BCMRA Scheme-Specific Implementation
4.1. Rapid Pre-Filtration Layer Based on Cuckoo Filter
The fast pre-filtering layer uses a cuckoo filter to store the identifier of revoked user credentials and intercept authentication requests for unrevoked credentials. Since there are cases of false positives, the BCMRA scheme cannot determine that a user’s credentials have been revoked by the output of only one cuckoo filter. On the contrary, the cuckoo filter can quickly determine that the credentials of a certain user have not been revoked, and can effectively intercept the checking requests for unrevoked credentials.
4.2. Directed Routing Layer Based on Consistent Hashing
The directed routing layer is responsible for mapping the identifier of a revoked user credential to the corresponding RSA accumulator number. The number of RSA accumulators in the BCMRA scheme changes dynamically according to the number of elements, so the mapping algorithm of the directed routing layer needs to reduce the number of elements that need to be re-mapped when the number of RSA accumulators changes, in addition, to satisfy the one-to-one relationship. The number of elements is to be mapped when the number of RSA accumulators changes. The simple modulo hash algorithm is expressed as , where k is the number of RSA accumulators when the number of RSA accumulators decreases or increases to , and almost all RSA accumulator elements need to re-calculate hash values and migrate. The consistent hash algorithm maps individual RSA accumulators onto a virtual ring space so that when an RSA accumulator is added or removed, only the elements adjacent to it in the ring space need to be remapped. Therefore, the directional routing layer uses the consistent hash algorithm as a method for routing RSA accumulators. The flow of the RSA accumulator mapping mechanism based on a consistent hash algorithm is as follows:
- Define the hash space: The length of the hash value is 256 bits, and the corresponding hash space ranges from , forming a logical closed-loop space.
- Deploying virtual nodes: Each RSA accumulator corresponds to V virtual nodes ; the virtual node hash value is calculated as , where is the virtual node replica serial number, with a range of .
- Build the hash ring: Sort the hash values of all virtual nodes to form a consistent hash ring; each virtual node corresponds to the interval on the ring, where is the virtual node’s own hash value and is the hash of the next virtual node after sorting.
- Locating a virtual node: Calculate the hash value of the identifier of the credential to be revoked, get the position of in the consistency hash ring, and, from that position, start to look up along the consistency hash ring in the clockwise direction and find the first virtual node where a hash value greater than . is satisfied:
- Mapping the RSA accumulator: Locate the virtual node ; the physical node corresponding to this virtual node is the target RSA accumulator. The physical node, represented by an RSA accumulator, corresponds to multiple virtual nodes. By increasing the number of virtual nodes, the virtual nodes can be distributed more evenly over the consistency hash ring, thus allowing for the credential identifier to be revoked to be distributed more evenly across the RSA accumulators. However, the greater the number of virtual nodes, the greater the burden on the system, so the number of virtual nodes should be selected according to the actual situation.
4.3. Precision Judgment Layer Based on a Multiple-RSA Accumulator
The precision judgment layer is responsible for storing the identifier of the revoked user credentials and handling the authentication requests for the revoked user credentials. The core of the BCMRA scheme is the Multi-Accumulator Mechanism based on the Dynamic Scaling and Load-Balancing algorithms, which are described below in terms of the Multi-Accumulator Mechanism and the Dynamic Scaling and Load-Balancing, respectively.
The precision judgment layer contains a set of k RSA accumulators , initialized with uniform parameters , with the same initial accumulation value , where p and q are large prime numbers, , and g is the generating element. The ith RSA accumulator contains a collection of elements with number , where each element corresponds to an identifier of a revoked user credential. The accumulated value of the ith RSA accumulator is denoted as
The BCMRA scheme proposed in this section adopts the mechanism of updating the proof of membership at the time of verification; when the RSA accumulator changes due to the addition or deletion of an element, the element that still exists in the RSA accumulator does not need to update the proof of membership immediately; instead, it will re-generate the newest proof of membership at the time of the application of verification:
The static RSA accumulator scheme has limitations: When the number of revoked users is still small, the number of elements in the RSA accumulator is small, and there may even be RSA accumulators in an idle state, resulting in a waste of space resources in the system. 6G scenarios have a notable feature that the upper limit of the number of accessed users is high, and when the number of revoked users reaches a large scale, the number of elements in the individual RSA accumulator is too large, and the number of elements in the single RSA accumulator is too high, and the number of users and terminal devices in the system is too large. When the number of revoked users reaches a large scale, the number of elements in a single RSA accumulator is too large, and it takes a lot of time to generate new membership certificates during the revocation checking. Therefore, the dynamic expansion and load-balancing algorithm is proposed to dynamically adjust the number of RSA accumulators and reduce the number of user revocation credentials that need to be transferred.
- Add a new RSA accumulator: As shown in Algorithm 1, when the number of revocation credentials stored in any one RSA accumulator exceeds the load maximum threshold , trigger the operation of adding a new RSA accumulator, add a new RSA accumulator with the same initialization parameters, generate the corresponding virtual node, and insert it into the consistency hash ring. Starting from the position of the added RSA accumulator on the hash ring, the next RSA accumulator is found in a clockwise direction, and the revocation credentials between these two RSA accumulators are migrated to the added RSA accumulator.
- Reduce RSA accumulators: As shown in Algorithm 1, when the number of revocation credentials stored in any of the RSA accumulators falls below the load minimum threshold , trigger a reduced RSA accumulator operation. Remove all virtual nodes of that RSA accumulator from the consistency hash ring; subsequently, find all credentials originally mapped to that RSA accumulator, recalculate the hash values of those credentials, and map them to the new RSA accumulator.
| Algorithm 1 Dynamic Expansion and Load-Balancing |
|
4.4. Trusted Storage Layer Based on Blockchain
The BCMRA scheme, as an important part of the authentication scheme, needs to satisfy 6G scheme interoperability with its output credential revocation parameters and results. Therefore, the trusted storage layer is responsible for storing the latest accumulated value of each RSA accumulator in the precision judgment layer, and is automatically uploaded by the authenticator in the trust domain in the form of transactions through smart contracts to the blockchain network maintained by the nodes in the trust domain. The authenticator can obtain the relevant parameters from the blockchain when performing the authentication and revocation of credential checking.
5. Identity Credential Revocation and Verification Process Based on BCMRA Scheme
5.1. Identity Credential Revocation Process
Identity credential revocation can be divided into two types, according to the different ways of triggering revocation:
- Active credential revocation: The user submits an application for identity credential revocation independently.
- Passive credential revocation: The user’s identity credentials expire or the user commits a malicious act resulting in a decrease in the integrated trust value, and the system detects that the user’s integrated trust value is lower than the minimum tolerance limit of the trust domain.
Take the example of user A in trust domain X actively applying for the revocation of credentials: the active revocation of credentials process is shown in Figure 2, and the specific steps are as follows:
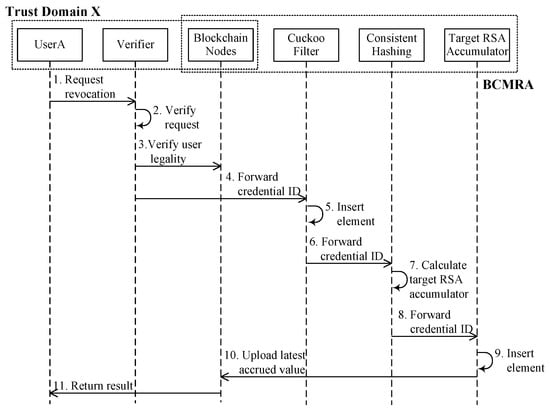
Figure 2.
User active revocation of credentials flowchart.
- User A initiates an unsolicited revocation of credential request to an authenticator within the same trust domain containing the user’s identifier and the credential identifier , encrypted by the authenticator’s public key.
- The authenticator receives the unsolicited revocation of credential request from user A and verifies the legitimacy of the request using the private key.
- The authenticator parses the user’s identity and credential information from the request and verifies the legitimacy of user A in the blockchain within the same trust domain.
- After the request of user A in step 1, the identity information in step 2, and the credential information in step 3 are verified, the verifier sends the credential identifier of user A to the cuckoo filter in the fast pre-filtering layer.
- The cuckoo filter performs an insert element operation to calculate the fingerprint and candidate bucket position of and insert it into the corresponding slot.
- In order to avoid a revocation credential validation misjudgment, , is further sent to the directed routing layer.
- The target RSA accumulator number is computed in the directed routing layer by means of a consistent hash algorithm.
- Based on the calculated target RSA accumulator number, the is further sent to the precision judgement layer.
- An insert element operation is performed by the RSA accumulator in the precision judgement layer to generate the latest accumulated value.
- The blockchain node in the trusted storage layer writes the latest cumulative value of the RSA accumulator into the blockchain network in the form of a smart contract transaction to complete the credential revocation operation of user A.
- The blockchain node returns the credential revocation result to the client of user A.
The user credential passive revocation process differs from the user active revocation process in the trigger judgement phase, as shown in Figure 3, where Steps 5–12 in the passive revocation process are the same as Steps 4–11 in the user active revocation process in Figure 2, both of which use the BCMRA scheme proposed in this section. The following therefore addresses Steps 1–4 of the user credential passive revocation process.
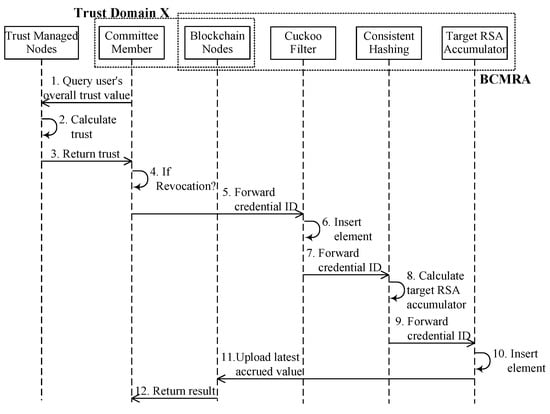
Figure 3.
User credential passive revocation flowchart.
- After user B within trust domain X commits a malicious act, a member of the trust management committee from trust domain X checks whether the composite trust value of user B is lower than the minimum trust threshold of trust domain X, and then applies to the trust management blockchain node to query and calculate the composite trust value of user B.
- The trust management blockchain node calculates the composite trust value by means of a node trust assessment scheme based on the identity identifier of user B and the trust domain identifier in which user B is located.
- The trust management blockchain node sends the integrated trust value of user B to the members of the trust management committee.
- The member of the trust management committee determines whether the credentials of user B need to be revoked based on the returned composite trust value, and if the result of the determination is that passive revocation of the credentials needs to be performed on user B, it continues to execute the BCMRA scheme of Steps 5–12 and completes the process of revoking the credentials of the user B.
5.2. Verification Process for Revoked Credentials
Revocation of credential verification is an important part of the 6G authentication scheme. When verifying the legitimacy of the user’s identity and the validity of the user’s credentials, the verifier first needs to verify whether the user’s credentials have been revoked, and only if it is confirmed that the user’s credentials have not been revoked can the verifier further perform the subsequent operations. The process of the verifier checking whether the user credentials have been revoked is shown in Figure 4.
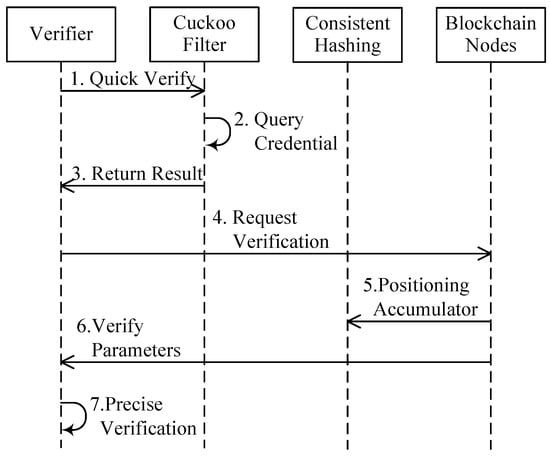
Figure 4.
Verifying user’s revoked credentials flowchart.
- The validator first performs a quick validation operation, calling the query element interface of the cuckoo filter.
- The cuckoo filter performs a query element operation with input parameter to be verified and outputs the query result as either exists or does not exist.
- If the validator receives a validation result of does not exist, the validation process ends with the result that the credential to be validated has not been revoked. If the validation result received is that exists, the subsequent steps continue.
- The validator sends a request for exact validation to the blockchain node within the same trust domain with and is encrypted by the validator’s private key.
- The blockchain node verifies the legitimacy of the request via the authenticator’s public key and subsequently computes the number of the target RSA accumulator via a consistent hash algorithm.
- The blockchain node queries the latest accumulation value of the target RSA accumulator via the number of the accumulator, generates the latest proof of membership , and sends the latest accumulation value and the proof of membership to the verifier.
- The validator verifies the validity of the latest membership proof through the validation parameters returned by the blockchain node and finally completes the entire process of verifying whether the user credentials have been revoked.
The BCMRA scheme can complete the validation with only one query element operation in the most ideal case, and even if a second precise validation is required, the validation latency can still be reduced by adopting the BCMRA scheme proposed in this section.
6. Experimental Results
In this paper, we propose a credential revocation and revocation checking scheme, BCMRA. This subsection tests the load-balancing effect of the BCMRA scheme and compares the revocation credential checking latency of the BCMRA scheme with that of the traditional single-RSA accumulator scheme. The hardware environment in which the experiments were carried out was an Intel i7-11700 CPU, 16GB of RAM, and a 512GB SSD. The system used is Ubuntu 18.04. In terms of experimental parameter settings, since the query latency of a single most basic RSA accumulator unit is linear, the size of needs to be controlled not to be too high, and it is usually set to a few hundred, which is more appropriate. Meanwhile, the number of virtual nodes also affects the latency. The load maximum threshold of the BCMRA scheme is set to 550, and the number of virtual nodes corresponding to each RSA accumulator is set to 5000. Firstly, the special case of revocation credential checking is introduced, i.e., the user credentials have not been revoked yet, and the judgment in the BCMRA scheme can be completed only by a fast pre-filtering layer. The test results show that when the cuckoo filter stores elements of the order of magnitude , the latency of checking is only single-digit milliseconds. Therefore, to ensure the fairness and reasonableness of the experiment, this subsection will test the latency of the complete execution of the whole BCMRA scheme.
The core of the BCMRA scheme is to dynamically adjust the mapping between the number of RSA accumulators in the precision judgment layer and the mapping in the directional routing layer by means of a load-balancing algorithm. As shown in Figure 5, the curve represents the total time spent on load-balancing as the number of revoked credentials increases, corresponding to the vertical axis on the left side. The bar graph represents the total number of credentials to be migrated, corresponding to the vertical axis on the right side. The time spent on load-balancing is the time spent on migrating credentials. When the number of revoked credentials is 1000, there are two RSA accumulators in the precision judgment layer, and load-balancing is not required; as the number of revoked credentials increases to 1500, the number of elements stored in the RSA accumulators exceeds the load maximum threshold of , and BCMRA starts load-balancing and dynamically increases the number of RSA accumulators to three and transfers a portion of the credentials. The time required to perform load-balancing when the number of revoked credentials grows from 1000 to 1500 in Figure 5 is expressed as the value of the curve at 1500 minus the value of the curve at 1000. It can be seen that as the number of revoked credentials increases, the time taken by the BCMRA scheme to perform load-balancing each time remains more-or-less the same.
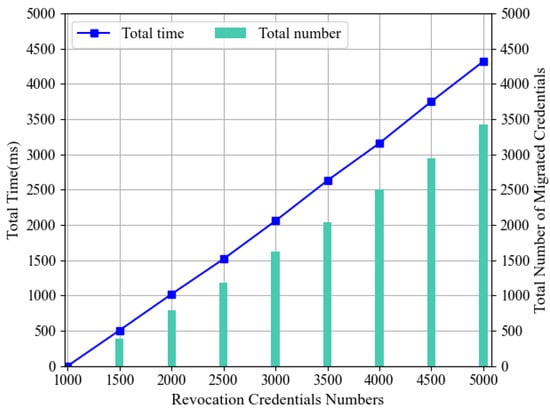
Figure 5.
BCMRA scheme load-balancing time consumption results chart.
When the number of revoked credentials reaches 5000, as shown in Figure 6, the number of RSA accumulators in the precision judgment layer is 10, and the maximum difference in the number of revoked credentials stored in each RSA accumulator is only 40. The experimental results show that the BCMRA scheme proposed in this paper is able to ensure a more uniform load-balancing.
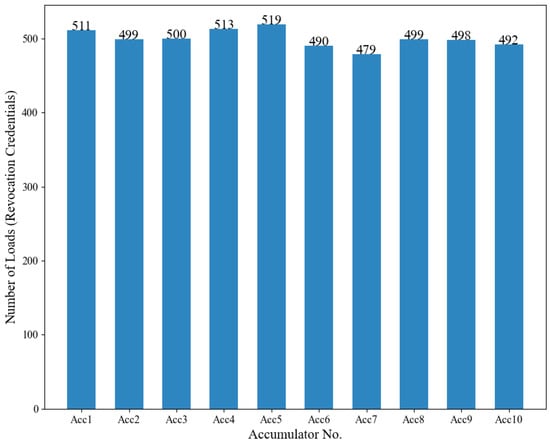
Figure 6.
Revocation credential load-balancing effect.
Figure 7 shows the time required for revocation credential checking. The blue curve in the figure shows the test results of the single RSA accumulator scheme proposed in [], where the checking latency increases linearly with the number of stored credentials when only a single RSA accumulator is used for the revocation of credential storage. The purple curve in the figure is the blockchain-based revocation management scheme proposed in []. As the number of stored credentials increases, the chain formed by the blocks grows longer, and the checking latency increases linearly. The green curve in the figure represents the checking latency of BCMRA, which also remains relatively stable when the number of revoked credentials increases with the BCMRA load-balancing algorithm. In general, most of the revocation of verification requests will not be initiated at the same time as the load-balancing; the system can complete the load-balancing in the absence of requests or low request volume, but does not rule out the case of simultaneous load-balancing and verification revocation during peak periods. The red curve in the figure shows the latency of simultaneous load-balancing and verification cancellation, and it can be seen that even if verification cancellation is performed immediately after load-balancing, the total latency is still lower than the original scheme and can be controlled within 1 s, which does not cause obvious system lag in 6G scenarios with large-scale users and terminal devices.
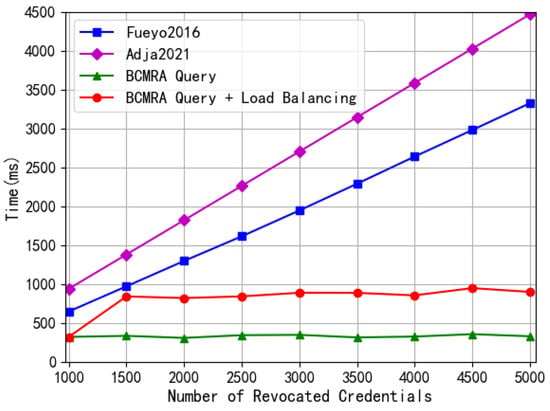
Figure 7.
Comparison of revocation certificate verification delays between BCMRA, [,].
In terms of security, the revocation system needs to be analyzed for a single point of failure. A single point of failure is due to server failure or downtime, resulting in the inability to carry out identity revocation and verification normally. The BCMRA scheme in this paper deploys blockchain nodes using a distributed architecture, and analyses the anti-single point of failure characteristics of blockchain nodes.
Let be the system steady-state availability parameter, which indicates the probability that the system is in an available state in long-term operation, and its value range is ; if , it means that the system is available 99.99% of the time, and the annual unavailability time is about 52 min. The single-node availability model is first given, assuming that the failure and repair of a single node obeys a continuous time Markov chain, introducing a failure rate and a repair rate , where denotes the probability of a node failing per unit of time, and denotes the probability of a faulty node being recovered per unit of time, and the steady-state availability of a single node is .
For a blockchain system consisting of N independent nodes, assuming that the node failure events are independent of each other and the system adopts a redundancy strategy, at least k nodes are normal to keep the system running normally, the system availability formula is as follows:
where the probability of each node being normal is , the probability of a failure is , and the probability that exactly i nodes are normal is calculated, and a summation operation is performed. Assume that the blockchain network adopts a PBFT consensus mechanism with nodes and requires at least nodes to survive to reach consensus. If the annual failure rate of a single node /year and the repair time is 4 h, the corresponding repair rate /year. Calculation based on the above parameters gives , which corresponds to an annual unavailability time of about 0.39 s. Therefore, it can be concluded that the blockchain-based BCMRA scheme does not have a single point of failure in its underlying design, and the system can still maintain normal operation when some nodes fail.
7. Conclusions
In this paper, we propose a BCMRA scheme with a four-layer architecture to address the challenges of 6G access by a large number of users and terminal devices, put forward the dynamic expansion of the RSA accumulator and load-balancing algorithm, and elaborate the detailed credential revocation process and revocation of the credential checking process. Test results show that the BCMRA scheme can achieve dynamic load-balancing, and has smaller and more stable credential revocation and revocation verification latency in 6G scenarios with a large number of users. In conclusion, the experimental results show that in 6G scenarios with massive access, a single architecture is not effective in providing smaller and stable delays, and the use of a layered architecture incorporating multiple techniques can achieve results. In future research, cryptographic enhancement designs against quantum computing attacks need to be considered. Existing schemes rely on traditional cryptographic algorithms, but the rapid development of quantum computing poses a potential threat to long-term security. Future research is needed to investigate the fusion mechanism between post-quantum cryptographic algorithms and blockchain architectures to ensure the quantum resistance of identity revocation systems.
Author Contributions
Conceptualization, G.W. and Y.Z.; methodology, Y.Z.; validation, G.W., Y.Z. and Y.J.; formal analysis, Y.Z.; investigation, H.C. and J.Z.; resources, G.W.; data curation, Y.Z.; writing—original draft preparation, G.W. and Y.Z.; writing—review and editing, Y.J. and Y.Z.; visualization, Y.Z.; supervision, Y.J. All authors have read and agreed to the published version of the manuscript.
Funding
This paper was supported by the Young Elite Scientists Sponsorship Program by CAST under grant 2023QNRC001.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Acknowledgments
We would like to express our sincere gratitude to the the Young Elite Scientists Sponsorship Program by CAST under grant 2023QNRC001 for its support of this paper.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| V2X | Vehicle to Everything |
| CAVs | connected and automated vehicles |
| 6G | 6th Generation Mobile Networks |
| IDS | Intrusion Detection Systems |
| EMI | Electromagnetic Interference |
| MIMO | Multi-input Multi-output |
| OCSP | Online Certificate Status Protocol |
| CRL | Certificate Revocation List |
| CA | Certificate Authorities |
| VA | Verification Authorities |
| RSA | Rivest-Shamir-Adleman |
| BCMRA | Blockchain, Cuckoo Filter, Multi-RSA Accumulator |
References
- Ju, Y.; Gao, Z.; Wang, H.; Liu, L.; Pei, Q.; Dong, M.; Mumtaz, S.; Leung, V.C. Energy-efficient cooperative secure communications in mmwave vehicular networks using deep recurrent reinforcement learning. IEEE Trans. Intell. Transp. Syst. 2024, 25, 14460–14475. [Google Scholar] [CrossRef]
- Dong, H.; Hu, Q.; Li, D.; Li, Z.; Song, Z. Predictive battery thermal and energy management for connected and automated electric vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 26, 2144–2156. [Google Scholar] [CrossRef]
- Hakeem, S.A.A.; Kim, H. Advancing Intrusion Detection in V2X Networks: A Comprehensive Survey on Machine Learning, Federated Learning, and Edge AI for V2X Security. IEEE Trans. Intell. Transp. Syst. 2025. [Google Scholar] [CrossRef]
- Gangwar, D.; Malik, J.; Patnaik, A. Harmonic suppressed MIMO antenna for highly integrated V2X communication system. IEEE Lett. Electromagn. Compat. Pract. Appl. 2024, 7, 19–24. [Google Scholar] [CrossRef]
- Alhashimi, H.F.; Hindia, M.N.; Dimyati, K.; Hanafi, E.B.; Safie, N.; Qamar, F.; Azrin, K.; Nguyen, Q.N. A survey on resource management for 6G heterogeneous networks: Current research, future trends, and challenges. Electronics 2023, 12, 647. [Google Scholar] [CrossRef]
- Ju, Y.; Cao, Z.; Chen, Y.; Liu, L.; Pei, Q.; Mumtaz, S.; Dong, M.; Guizani, M. NOMA-Assisted Secure Offloading for Vehicular Edge Computing Networks with Asynchronous Deep Reinforcement Learning. IEEE Trans. Intell. Transp. Syst. 2023, 25, 2627–2640. [Google Scholar] [CrossRef]
- George, A.; Murthy, G.R. (Eds.) Towards Wireless Heterogeneity in 6G Networks; CRC Press: Boca Raton, FL, USA, 2024. [Google Scholar]
- Ju, Y.; Song, J.; Li, W.; Zhang, Y.; He, C.; Dong, F.; Chen, C. Dynamic Load-Balancing Routing Strategy for LEO Satellite Networks Based on Spatio-Temporal Traffic Prediction. IEEE Trans. Aerosp. Electron. Syst. 2025. [Google Scholar] [CrossRef]
- Kazmi, S.H.A.; Hassan, R.; Qamar, F.; Nisar, K.; Ibrahim, A.A.A. Security concepts in emerging 6G communication: Threats, countermeasures, authentication techniques and research directions. Symmetry 2023, 15, 1147. [Google Scholar] [CrossRef]
- Jain, G. Certificate Revocation: A Survey. Citeseer. 2000. Available online: https://www.researchgate.net/publication/2498488_Certificate_Revocation_A_Survey (accessed on 27 July 2025).
- Ozcelik, I.; Skjellum, A. Cryptorevocate: A cryptographic accumulator based distributed certificate revocation list. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 27–30 January 2021; pp. 561–570. [Google Scholar]
- Naor, M.; Nissim, K. Certificate revocation and certificate update. IEEE J. Sel. Areas Commun. 2000, 18, 561–570. [Google Scholar] [CrossRef]
- Cooper, D.A. A More Efficient Use of Delta-CRLs. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000. [Google Scholar]
- Kikuchi, H.; Abe, K.; Nakanishi, S. Performance evaluation of public-key certificate revocation system with balanced hash tree. In Proceedings of the 1999 ICPP Workshops on Collaboration and Mobile Computing (CMC’99). Group Communications (IWGC). Internet’99 (IWI’99). Industrial Applications on Network Computing (INDAP), Aizu-Wakamatsu, Japan, 24 September 1999; pp. 204–209. [Google Scholar]
- Wang, S.; Du, X.; Yang, Z. Distributed key revocation scheme based on shared binary tree. In Proceedings of the 2015 IEEE International Conference on Progress in Informatics and Computing (PIC), Nanjing, China, 18–20 December 2015; pp. 338–342. [Google Scholar]
- Annavajjala, R.M.; Anand, V. Partition based hash tree—An efficient certificate revocation system. In Proceedings of the 2017 IEEE International Conference on Electro Information Technology (EIT), Lincoln, NE, USA, 14–17 May 2017; pp. 551–556. [Google Scholar]
- Berbecaru, D.; Lioy, A.; Marian, M. Security aspects in standard certificate revocation mechanisms: A case study for OCSP. In Proceedings of the ISCC 2002 Seventh International Symposium on Computers and Communications, Taormina-Giardini Naxos, Italy, 1–4 July 2002; pp. 484–489. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. Dynamic Accumulators and Application to Efficient Revocation of Anonymous Credentials. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Fueyo, M.; Herranz, J. On the efficiency of revocation in RSA-based anonymous systems. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1771–1779. [Google Scholar] [CrossRef]
- Wang, Z.; Lin, J.; Cai, Q.; Wang, Q.; Zha, D.; Jing, J. Blockchain-based Certificate Transparency and Revocation Transparency. IEEE Trans. Dependable Secur. Comput. 2020, 19, 681–697. [Google Scholar] [CrossRef]
- Adja, Y.C.E.; Hammi, B.; Serhrouchni, A.; Zeadally, S. A Blockchain-based Certificate Revocation Management and Status Verification System. Comput. Secur. 2021, 104, 102209. [Google Scholar] [CrossRef]
- Zhang, H.; Chen, Y.; Ren, W.; Li, T. CertRV: An Efficient Certificate Revocation Scheme via Consortium Blockchain, Chameleon Hash and Cuckoo Filter. In Proceedings of the 2024 IEEE International Conference on Web Services (ICWS), Shenzhen, China, 7–13 July 2024; Volume 10, pp. 1338–1340. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).