Abstract
Unmanned Underwater Vehicles (UUVs) play an irreplaceable role in marine exploration, environmental monitoring, and national defense. The UUV depends on underwater acoustic communication (UAC) technology to enable reliable data transmission and support efficient collaboration. As the complexity of UUV missions has increased, secure UAC has become a critical element in ensuring successful mission execution. However, underwater channels are inherently characterized by high error rates, limited bandwidth, and signal interference. These problems severely limit the efficacy of traditional security methods and expose UUVs to the risk of data theft and signaling attacks. Cryptography-based security methods are important means to protect data, effectively balancing security requirements and resource constraints. They provide technical support for UUVs to build secure communication. This paper systematically reviews key advances in cryptography-based secure UAC technologies, focusing on three main areas: (1) efficient authentication protocols, (2) lightweight cryptographic algorithms, and (3) fast cryptographic synchronization algorithms. By comparing the performance boundaries and application scenarios of various technologies, we discuss the current challenges and critical issues in underwater secure communication. Finally, we explore future research directions, aiming to provide theoretical references and technical insights for the further development of secure UAC technologies for UUVs.
1. Introduction
Unmanned Underwater Vehicles (UUVs) serve as critical intelligent platforms in modern ocean technology, enabling autonomous navigation and complex task execution for applications like ocean exploration, environmental monitoring, and national security [1]. The UUV domain encompasses diverse technological configurations, with Autonomous Underwater Vehicles (AUVs) and Remotely Operated Vehicles (ROVs) representing two distinct operational paradigms. AUVs operate fully autonomously without real-time human intervention, while ROVs rely on tethered or wireless remote control [2,3]. These systems are widely applied in seabed resource exploration, marine ecological monitoring, underwater infrastructure maintenance, and military reconnaissance [4]. For example, in deep-sea mineral resource exploration, AUVs can realize seafloor topographic mapping and resource localization through high-precision sensors. In the military field, UUVs enhance combat effectiveness by supporting underwater target reconnaissance and anti-submarine warfare [5] (as shown in Figure 1).
Figure 1.
Typical application.
However, the efficient cooperative operation of UUVs relies on reliable data transmission and communication technologies. The special characteristics of underwater environments, especially the high signal attenuation, narrow bandwidth limitations, and complex multipath effects, make it difficult for traditional radio communication technologies to meet the data transmission requirements of UUVs [6]. Studies have shown that the attenuation coefficient of electromagnetic waves underwater is as high as 1.5 dB/m, resulting in an effective transmission distance usually not exceeding 100 m. Facing this technological challenge, underwater acoustic communication (UAC) has emerged as the preferred communication method for UUV collaborative operations. However, the unique challenges of UAC, such as high latency, Doppler shift caused by vehicle mobility, and time-varying multipath fading, directly impact the reliability and security of UUV coordination. Its advantages in long-distance transmission and interference resistance are critical for UUV missions, but these must be balanced against security vulnerabilities in underwater wireless sensor networks (UWSNs) [7]. Through the coded modulation technique of acoustic wave carriers, UAC not only realizes basic data exchange among UUVs but also shows significant advantages in reliability and security [8].
Although UAC technology has made significant progress, its secure transmission methods faces unique challenges rooted in underwater channel characteristics. For instance, the low data rate and high bit error rate of acoustic channels exacerbate the risk of real-time authentication failures, while the broadcast nature of acoustic waves makes UAC systems highly vulnerable to unauthorized data interception, malicious signal manipulation, and node impersonation attacks, which directly compromise mission-critical operations and sensitive marine data [9,10]. Compared to separate citations, combining them improves readability. To address these challenges, cryptography-based data security methods have become a critical solution. By combining mathematical reliability with adaptive design, they provide a balanced approach to protect communication links against attacks while operating efficiently in resource-constrained underwater environments [11]. This makes cryptographic frameworks essential for ensuring data confidentiality and mission success in UUV applications.
Cryptography-based secure communication must first address UAC-specific challenges to establish trust. For example, the dynamic topology changes in UUV swarms and the high latency of acoustic channels require authentication protocols to be lightweight yet robust against delay-induced synchronization failures, enabling secure key agreement and digital signatures under time-varying conditions [12]. Building upon this foundation, lightweight cryptographic algorithms perform dual encryption on session keys generated during authentication and core operational data, ensuring data transmission confidentiality with minimal computational overhead. To address the high bit error rates and node mobility characteristics of underwater channels, cryptographic synchronization protocols ensure reliable transmission of key states and encrypted information through complex acoustic environments, preserving real-time performance and integrity of communication links in dynamic network topologies [13]. This defense mechanism, combining mathematical reliability with environmental adaptability, provides resource-constrained UUV applications with a transmission framework that balances security and operational feasibility.
In recent years, researchers have addressed UAC security through cryptography, focusing on authentication and encryption to mitigate challenges like Doppler shift-induced key synchronization errors and multipath fading-induced data corruption [14,15]. However, most existing research focuses on a single technology path and lacks synergistic optimization and performance evaluation of multi-level security mechanisms [16,17,18]. In this paper, we systematically review advancements in secure transmission technologies for underwater communication, focusing on three core areas: authentication, encryption, and cryptographic synchronization. We analyze their technical principles, performance limits, and application scenarios in depth. By evaluating the strengths and weaknesses of existing schemes, this paper identifies current technical bottlenecks and outlines future development directions. This paper aims to provide theoretical support and technical guidance for building secure UAC for UUVs. It seeks to advance the shift from single optimization to integrated synergy in underwater communication security technologies, ensuring the reliable operation and data security of unmanned marine intelligent equipment.
The rest of the paper is organized as follows. Section 2 details the UAC communication model, analyzes channel characteristics, and compares underwater wireless communication technologies. Section 3 focuses on the key technologies of cryptography-based UAC, providing a detailed overview from three dimensions: authentication, cryptographic algorithms, and cryptographic synchronization protocols. Section 4 discusses the technical challenges and key issues facing secure UAC for UUVs. Finally, Section 5 summarizes the whole paper.
2. Structure and Characteristics of UAC
UAC serves as the primary method for information exchange in underwater environments, utilizing acoustic waves to establish robust data links between UUVs and surface control centers. The communication process involves coding, modulation, transmission, propagation, reception, and demodulation. A coding algorithm first converts raw data into formats compatible with underwater acoustic channels, such as orthogonal frequency-division multiplexing (OFDM) [19] for combating multipath fading, Quadrature Phase Shift Keying (QPSK) modulation [20] for high spectral efficiency, and Low-Density Parity-Check Code (LDPC) [21] for reducing interference. These formats are widely adopted for their robustness in noisy, bandwidth-constrained environments. During propagation, signals pass through complex underwater environments affected by temperature, salinity, and topography. These factors cause reflection, refraction, and scattering, which degrade signal integrity. At the receiver, high-precision demodulation restores encoded information, followed by decoding algorithms to extract the original data.
A typical UUV communication architecture consists of underwater sensor nodes, surface gateways, satellite base stations, and ground control centers. This forms a multi-layered network for subsea-to-terrestrial data exchange. As shown in Figure 2, the architecture uses 2D horizontal and 3D vertical communication topologies. Underwater sensor nodes, deployed at key depths, are autonomous or semi-autonomous. They use embedded sensors to collect data like hydroacoustic signals, temperature, and marine life activity. These nodes filter and extract features from the data to reduce what needs to be sent. The data is then sent via acoustic modems or optical wireless links to surface gateways, such as floating buoys or unmanned surface vehicles. These gateways aggregate data from multiple underwater nodes, convert protocols, and send information to ship/shore stations using VHF/UHF radios or satellite links. They also receive control commands and execute actuation instructions. Satellite base stations, like INMARSAT or Iridium, offer global coverage. They receive encrypted data from surface gateways, route it through satellite constellations, and send it to ground stations with high-gain antennas. This ensures connection in remote ocean areas. Ground control centers act as command hubs. They use data analytics platforms and human/machine interfaces to process data, creating products like ocean current maps or pollution forecasts. They can also issue commands to UUV swarms or start emergency protocols. The architecture’s hierarchical design and redundant paths help maintain strong coordination, fault tolerance, and fast real-time control across the UUV network.
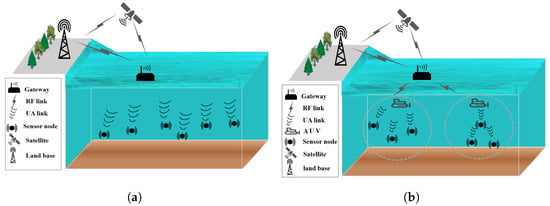
Figure 2.
System architecture. (a) Two-dimensional. (b) Three-dimensional.
Underwater acoustic communications of UUVs have the following characteristics:
Narrow bandwidth. Table 1 presents the bandwidth of underwater acoustic channels corresponding to different communication ranges [22]. As seen in Table 1, if a bandwidth greater than 100 kHz is expected, the transmission distance will be less than 100 m. When the transmission distance is to reach 1000 km, the bandwidth is less than 1 kHz [23].

Table 1.
Comparison of underwater wireless communication technologies.
High bit error rates (BERs). Underwater acoustic channels exhibit BERs between and due to three factors: (1) multipath reflections causing signal attenuation and phase distortion [24,25]; (2) intensified Doppler shifts from slow sound propagation and node movements, creating frequency distortions five times greater than in equivalent Radio Frequency (RF) systems [26]; and (3) environmental noise from ship operations and water property variations. While Magneto Inductive (MI) communication mitigates these issues via magnetic fields, its shorter range suits localized, low-BER networks [27]. Collectively, these challenges degrade underwater communication reliability [28].
Large time delay. Terrestrial radio waves propagate in air at a speed slightly lower than the speed of light. However, the propagation speed of acoustic waves in water is merely 1.5 × 103 m/s, approximately five orders of magnitude lower than that of radio signals [29]. This significant speed difference results in a substantial time delay during underwater propagation [30]. The relationship between the signal frequency and the transmission distance is presented in Figure 3. In addition, UAC has time-varying characteristics, and its propagation speed is significantly affected by physical factors such as seawater pressure, temperature, and salinity.
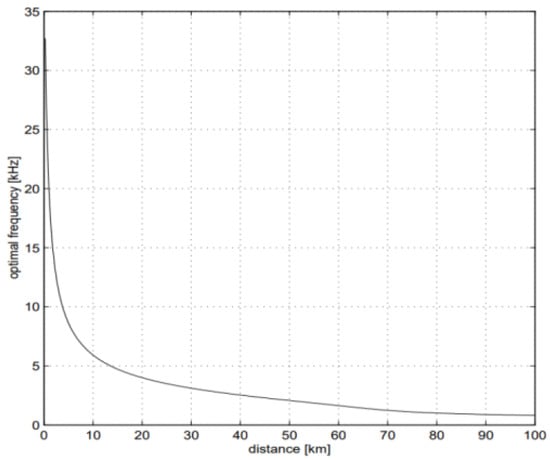
Figure 3.
Frequency–distance relationship in water medium.
and are the sound intensities at 1 m and r from the equivalent acoustic center of the sound source.
Acoustic waves have become the preferred information carrier for underwater wireless communication due to their good suitability with the water medium, long-distance propagation capability and strong penetration. Compared with electromagnetic waves, acoustic waves can effectively overcome the problem of rapid underwater attenuation. Table 2 comparatively analyzes the performance characteristics of different underwater wireless communication technologies [31].

Table 2.
Comparison of underwater wireless acoustic communication on the basis of achieved distance.
3. Secure Transmission in UAC
Since the 20th century, multiple countries have accelerated the development of UUVs to counter asymmetric threats [32]. Beginning in the mid-20th century, the United States, Japan, and European nations initiated research on UAC. As early as the 1950s, the U.S. military pioneered the application of UAC technology for intelligence gathering and reconnaissance. In 2016, the U.S. Defense Science Board released the “Next Generation of Unmanned Underwater Systems” report, outlining strategic recommendations to maintain underwater dominance [33]. In 2022, the U.S. introduced the Manta, a next-generation UUV designed for advanced underwater missions [34]. That same year, the U.S. Navy completed shipboard integration testing of the “Knifefish” UUV, validating the critical role of secure UAC links [35]. Additionally, the Navy acquired the “SwarmDiver” UUV, emphasizing the necessity of stable communications for swarm operations. Russia’s Poseidon nuclear-powered UUV encountered UAC signal attenuation challenges during deep-diving tests in 2019, while its nuclear payload capability imposed stringent security demands [36]. In 2021, Japan prioritized high-speed, high-capacity UAC under its Multi-Domain Integrated Defense Force initiative to enable coordination between UUVs and surface vessels. In 2022, France’s Naval Group and ECA Group developed the “A18-M” UUV and “T18-M” towed sonar for Belgium and the Netherlands as part of their Anti-Mine Joint Solution, relying on robust UAC for collaborative mine countermeasures.
In recent years, China has demonstrated a remarkable technological evolution in communication security for underwater unmanned systems [37]. Researchers have advanced key technologies such as communication encryption and anti-jamming signal processing, driving simultaneous progress in theoretical frameworks and practical implementations. Updated maritime regulations now classify intelligent submersibles as standard marine equipment, establishing essential requirements for communication security standardization [38]. During deep-sea exploration trials, engineers from the Chinese Academy of Sciences (CAS) implemented a multimodal secure communication system in their UUV prototype. This system achieved real-time transmission of seafloor topography and mineral data with a 0.01% BER in complex underwater acoustic environments. In offshore trials, a university research team established a 110 km underwater communication link using adaptive modulation-coding technology, with their UUV platform maintaining 98.7% signal stability during 1000 m deep-sea operations. Northwestern engineers addressed miniaturization challenges through a 50 kg class UUV design, integrating optimized encryption protocols and adaptive authentication to enable secure 50 km range communications at 200 m depth while achieving 40% energy savings over conventional approaches.
These breakthroughs signify that China’s research in underwater communication security has transitioned from theoretical exploration to engineering verification and standardization. Multidisciplinary collaborations have yielded breakthroughs in channel modeling, encryption algorithm optimization, and system integration, laying a technical foundation for reliable underwater information networks [39,40]. Future research should be focus on cutting-edge directions such as transmedia communication and quantum secure transmission to address increasingly complex underwater operational challenges. To fully leverage secure low-power data communication, UUV systems require three core capabilities: efficient authentication protocols, lightweight encryption algorithms, and rapid cryptographic synchronization. These features ensure secure, reliable, and efficient data transmission with supervisory robustness. The interrelationships among these key technologies are illustrated in Figure 4, with their research progress detailed as follows.
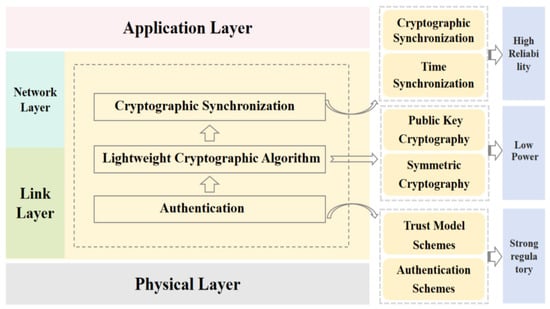
Figure 4.
Key technology internal relationships.
3.1. Authentication Protocols
UWSNs face unique operational challenges in complex marine environments: dynamic topology leads to easy counterfeiting of node identities, open transmission media exacerbate the risk of data tampering, and restricted node resources make it difficult to support traditional security mechanisms. In this context, the construction of a hierarchical security protection system has become an inevitable choice to ensure reliable network operation [41]. As the first line of defense for network security, the authentication mechanism can effectively resist penetration attacks from external malicious nodes by strictly verifying the legitimacy of UUV identities [42]. Simultaneously, the dynamic trust assessment model emphasizes internal network governance. It intelligently identifies abnormal nodes caused by environmental disturbances or hardware failures through continuous monitoring of behavioral characteristics, as illustrated in Figure 5. These two components form a complementary architecture of “boundary protection–endogenous security” [43]: authentication establishes a trusted access benchmark for the network, while the trust model implements operational risk control on this foundation. This synergistic protection mechanism not only overcomes the limitations of single security schemes but also adapts to the resource-constrained nature of underwater networks [44]. This section systematically reviews the research progress of authentication protocols, trust models, and their collaborative optimization strategies.
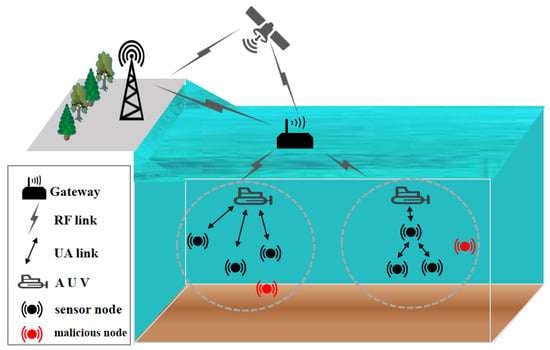
Figure 5.
Sensor nodes communicate with trusted nodes within their communication range.
3.1.1. Authentication
Authentication protocols play a crucial role in the information security system; as the first line of defense of the network, its core task is to verify the authenticity of the identity of each node in the network. Among various types of authentication protocols, cryptography-based protocols are ideal for large-scale network environments due to their inherent cryptographic properties and strong security. The following studies are organized and analyzed from different classification perspectives.
Signature and symmetric encryption-based authentication protocols are widely used in resource-constrained network environments due to their simplicity and efficiency. Prasanth et al. [45] proposed a signature-based authentication protocol for the IoT paradigm, which combines cryptographic and biometric techniques for authentication. However, the protocol is not optimized for the specific needs of UWSNs, such as communication bandwidth and processing power constraints. Porambage et al. [46] proposed a digital signature-based authentication protocol using symmetric encryption to pre-position keys with node identifiers at both the client and server side. The protocol is simple in design and suitable for sensor nodes with limited computational resources, but it is difficult to solve the problem of limited computational resources in underwater environments and the security needs to be improved. Fan et al. [47] proposed an authentication protocol based on lightweight key management, which utilizes private data carried by nodes to generate session keys. Experiments show that the protocol has good robustness against multiple attacks, but its inter-node communication and energy consumption are high. Dhillon et al. [48] proposed a lightweight three-factor remote user authentication protocol which performs authentication directly between the user and the sensor node without gateway intervention. However, the protocol has a long authentication time, high memory consumption, and does not support dynamic addition of sensor nodes. Wazid et al. [49] proposed a remote user authentication protocol for generic IoT environments. The protocol uses only one-way hash functions and XOR operations, making it unsuitable for resource-constrained environments. In addition, the authentication table based on the gateway database stored in the protocol may trigger a serious data leakage problem if it is compromised.
Multi-factor authentication enhances the security of authentication by combining multiple authentication mechanisms but is usually accompanied by high computational and communication overheads. Wu et al. [50] proposed a multi-factor authentication protocol combining fuzzy promises and mutual authentication to protect wireless sensor networks (WSNs) in IoT devices. Although its computational cost is acceptable, it has high communication overheads and suffers from offline user identity and password guessing vulnerability to attacks. He et al. [51] proposed a three-factor remote authentication scheme that fills the gap in related research but is still vulnerable to user and sensor node simulation attacks. Mo et al. [52] proposed a protocol that attempts to enhance the security by combining messages between users and sensors with session keys. However, the protocol is vulnerable to modification and denial-of-service attacks and has a high communication cost.
Elliptic curve cryptography (ECC)-based authentication protocol is one of the most widely used cryptographic schemes in WSNs due to its efficiency and security. Lu et al. [53] proposed an improved authentication protocol for WSNs, which addresses the vulnerabilities in the protocol of [54,55] such as asynchronous attacks, offline guessing attacks, and denial-of-service attacks through ECC. However, the protocol introduces a high computational burden at the user’s end and is not resistant to replay attacks. Li et al. [56] proposed a signature-based IoT authentication protocol that utilizes biometrics and cryptography and stores credentials via ECC multiplication. Although this protocol is able to withstand simulation attacks, it has a high user computational cost and is vulnerable to smart card theft attacks. Zhang et al. [57] proposed an ECC and hash-based authentication protocol that utilizes hash values and node IDs to authenticate nodes in the network. The security analysis shows that the protocol is able to withstand passive, active, and man-in-the-middle attacks, but its communication and computational overheads are not analyzed. Wang et al. [58] proposed an authentication protocol based on ECC key exchange to authenticate the nodes with the help of key distribution center method. This protocol is able to resist active attacks but is not applicable to complex network environments with limited computational resources. Porambage et al. [59] proposed an authentication protocol based on ECC and Diffie–Hellman (DH) key establishment that combines ECC and DH key exchange technologies for resource-limited network environments. The protocol is verified to be resistant to multiple types of attacks through performance evaluation and security analysis, aiming at the characteristics of UAC networks with variable environments, uncontrollable channel quality, and inconsistent security protection level requirements for different message transmissions. Maurya et al. [60] designed three levels of secure UAC schemes. The output lengths of the three hierarchical schemes are quantitatively analyzed, as shown in Table 3.

Table 3.
Quantitative analysis of output lengths for three-tier secure UAC schemes.
Table 4 summarizes the key features of the above authentication protocols, including technologies, advantages, disadvantages, and applicable environments. While ECC-based protocols strike a good balance between security and efficiency, their performance in resource-constrained UWSNs remains unproven, as most designs originate from non-underwater contexts and lack real-world validation in dynamic aquatic environments. Future research must prioritize field deployments to quantify challenges like latency degradation in turbulent waters or energy consumption under prolonged UAC operations. From this overview, it is evident that UWSN-specific authentication protocols require radical lightweight innovations, as existing solutions—developed primarily for terrestrial use—fail to address the unique constraints of underwater security, such as bandwidth scarcity and node mobility.

Table 4.
Comparison of authentication protocols.
3.1.2. Trust Model
Existing authentication protocols ensure node identity legitimacy through encryption and biometric techniques, but their static nature struggles to address dynamic underwater threats like internally compromised nodes, such as malicious packet forwarding, and behavioral drift from energy depletion or environmental fluctuations. To unify trust model evaluation, it is essential to contextualize techniques against specific attack scenarios and quantifiable metrics. Key scenarios include selective forwarding attacks, where nodes disrupt packet transmission. Hybrid attacks combine data tampering and sinkhole tactics. Environmental interference includes signal degradation from water flow or node mobility. Critical metrics for UWSNs include malicious node detection rate, such as models with ≥90% accuracy. False positive rate should ideally be under 5%. Computational overhead is measured by energy use or processing time. Environmental adaptability refers to reliability in changing conditions like channel noise. Trust evaluation provides a mathematical framework to quantify node trustworthiness via pre-interaction analysis, with higher values indicating greater reliability. As shown in Figure 6, sensor nodes are classified into evaluation, target, intermediate, and recommendation roles to form trust relationship foundations. Trust models act as dynamic security layers, continuously assessing multi-dimensional metrics like communication behavior, data consistency, and energy status to build fine-grained assessment systems.
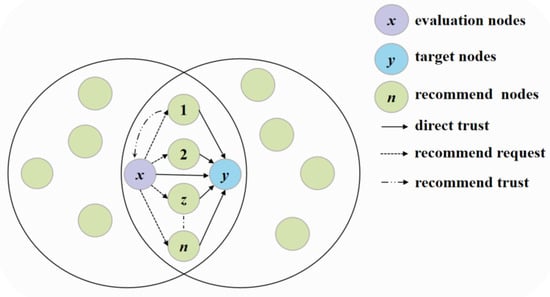
Figure 6.
Trust Relation.
Building upon this foundation, trust models are introduced as dynamic security enhancement layers, constructing a fine-grained assessment system by continuously quantifying multi-dimensional metrics such as communication behavior, data consistency, and energy status. Research on trust models for UWSNs focuses on three core steps, evidence accumulation, trust calculation, and trust update, addressing how to express, calculate, and adapt trust in real time. Han et al. [61] proposed the attack-resistant trust model for UWSNs, introducing multidimensional trust metrics for dynamic assessment. This model integrates fuzzy logic with data, link, and node trust evaluation, but its weight configuration relies on subjective experience. Jiang et al. [62] developed a cloud theory-based trust model for underwater acoustic sensor networks, leveraging cloud computing to quantify trust relationship uncertainties. While effectively capturing trust ambiguity through cloud model advantages, the approach suffers from high computational overhead that compromises energy efficiency. Aiming at the problem of insufficient evidence in sparse networks, Arifeen et al. [63] realized 91.2% malicious node detection in small samples based on an adaptive neuro-fuzzy inference system, but the environment adaptability is limited by the predefined training data.
With the penetration of machine learning technology, the trust model of UWSNs is gradually evolving towards dynamization and intelligence. Han et al. [64] proposed a SVM-based collaborative trust model for clustered UWSNs. The model implements distributed evaluation of communication, packet-sending, and energy trust through intra-cluster cooperative training, effectively addressing node sparsity issues. However, it relies on an initial assumption of zero compromised nodes and fails to quantify underwater environmental interference effects on trust prediction, limiting practical applicability. Du et al. [65] developed an isolation forest-based trust model for anomaly-resilient authentication. By unsupervised aggregation of communication, data, energy, and environmental trust metrics, this approach eliminates subjective weight assignments and achieves 92.3% accuracy in malicious node identification. However, underwater environment complexity has not been considered. Arifeen et al. [66] proposed a trust management model based on a Hidden Markov Model (HMM). The model can dynamically assess trustworthiness, but it relies on complete historical behavioral sequences and is sensitive to sudden anomalies. Muthukkumar et al. [67] proposed a trust-strategy dynamic Bayesian game model that employs Bayesian rule-based real-time trust updates. This method reduces malicious packet loss rates by 27% with minimal transmission delay but incurs high computational costs during game equilibrium resolution. Jiang et al. [68] developed a trust evaluation and update protocol for UWSNs using the C4.5 decision tree algorithm. This protocol enables fast classification and detection of multi-dimensional trust evidence and balances energy consumption with detection rates through a sliding-window update. However, it assumes no initial network attacks, which diverges from real-world deployment scenarios.
In recent years, researchers have shifted focus beyond trust calculation and node classification methods. They now emphasize the impact of complex underwater environments, flawed trust recommendations, and other factors of trust evaluation. This approach aims to achieve more accurate trust evaluation results and reduce misclassification.
Krishnan et al. [69] addressed potential selective forwarding attacks in underwater acoustic networks by proposing an improved Beta trust model. This scheme defends against selective forwarding attacks using forwarding success statistics, though it relies on a single defense dimension. Su et al. [70] proposed a trust model based on fast link quality assessment for UASNs, which quantifies link quality into equivalent distances, dynamically corrects trust values, and reduces misjudgments caused by environmental fluctuations. Han et al. [71] proposed a fault-tolerant trust model for hybrid attack patterns. The model features an integrated architecture with three phases: environment modeling, reinforcement learning, and trust redemption. It uses water flow and channel state to trigger updates, reinforcement learning to dynamically adjust parameters for distinguishing malicious behaviors from network failures, and a redemption upgrade mechanism to maintain a detection rate above 85% under hybrid attacks. Su et al. [72] proposed a method to redeem misjudged nodes by combining historical behaviors using SVM classification and D-S evidence theory. This approach reduces the misjudgment rate of normal nodes to below 5%. However, it only applies to stationary underwater nodes and does not account for node mobility. Li et al. [73] proposed a trust assessment model for nodes based on cloud theory. However, the model assumes planar deployment and immobility of UWSN nodes, limiting its applicability to most real-world UWSN scenarios. He et al. [74] proposed a reinforcement learning-based trust updating mechanism that incorporates a node criticality factor to enhance hotspot node protection. Although TUMRL improves response speed during attack mode transitions, its high communication overhead remains a limitation. Du et al. [75] developed an attention-based trust model using an edge computing architecture, deploying AUV as trust agents and employing an attention mechanism to adaptively assign indicator weights. Combined with an optimized warm-leap layer topology, ATrust enhances privacy protection and reduces anomaly identification latency. To address defective trust recommendations, Du et al. [76] proposed an LSTM-based adaptive trust model for UASNs. This model preprocesses recommendations via median/cooperative filtering, captures behavioral temporal features with LSTM, and achieves 92% anomaly detection accuracy in hybrid attack scenarios.
Trust models offer systematic approaches to evaluate node trustworthiness, gaining significant attention in security-critical applications such as secure routing. Wei et al. [77] developed a Gray Wolf Optimization (GWO)-based clustering protocol integrating trust mechanisms. While enhancing distributed decision-making, this approach suffers from limited global evidence integration and suboptimal 60% attack detection rates. To address vulnerabilities in conventional routing, Lv et al. [78] enhanced the Low-Energy Adaptive Clustering Hierarchy protocol through fuzzy logic and trust evaluation. Their method combines communication behavior trust metrics with node attributes via fuzzy inference, achieving 78% malicious cluster head rejection. However, reliance on single-dimensional trust evidence restricts defense against multi-vector attacks. Liang et al. [79] proposed a dual-phase detection framework for underwater networks, comprising the RMIS scheme for malicious node identification and a trust update mechanism. The RMIS scheme employs k-means clustering combined with SVM classification, while the trust update mechanism operates through event-time triggers. By integrating dual cluster head supervision and voting mechanisms, their solution achieves 90% malicious cluster head detection accuracy and extends network lifetime by 23%. However, sparse network conditions degrade recommendation trust reliability due to insufficient node interaction data.
In summary, as shown in Table 5, although research on trust modeling for UWSNs has achieved significant progress, critical challenges remain unresolved. First, traditional trust models often quantify trust as a fixed real number, which fails to capture trust’s subjective nature. This approach overlooks the ambiguity, randomness, and uncertainty inherent in trust, ultimately reducing the accuracy of trust assessment results. Second, most traditional trust models use fixed, unchanging parameters, making them unsuitable for dynamic underwater environments. These models cannot provide differentiated trust assessments or prioritize protection for nodes in critical areas, leading to inaccurate identification of malicious nodes. In addition, traditional trust models often rely on subjectively set parameters and thresholds, which hinder parameter optimization and reduce the model’s accuracy in identifying malicious nodes. Furthermore, the lack of datasets with malicious nodes in UWSNs makes it challenging to apply machine learning methods to trust models.

Table 5.
Comparison of trust modeling schemes.
3.2. Lightweight Cryptographic Algorithm
IoT devices in UUVs (e.g., AUVs, ROVs, etc.) are resource-constrained [80] and characterized by small memory, low computational power, limited battery power, small physical space, and vulnerability to attacks [81]. In addition, most of the IoT devices in UAC need to process data in real time and exchange data frequently between devices, resulting in data facing high information security risks [82]. In this context, cryptographic algorithms become one of the effective methods to protect the communication security of underwater IoT devices. However, as shown in Figure 7, traditional cryptographic algorithms face many challenges when deployed on resource-constrained devices. For this reason, the researchers proposed lightweight cryptographic algorithms to achieve real-time response on resource-constrained devices and meet their security requirements by optimizing storage space, reducing power consumption, and improving computational speed, among other features. For the uniqueness and limitations of underwater communication devices, it is crucial to design lightweight cryptographic algorithms. Modern cryptography is mainly categorized into symmetric cryptographic algorithms and public key cryptographic algorithms, which will be reviewed and introduced in the following.
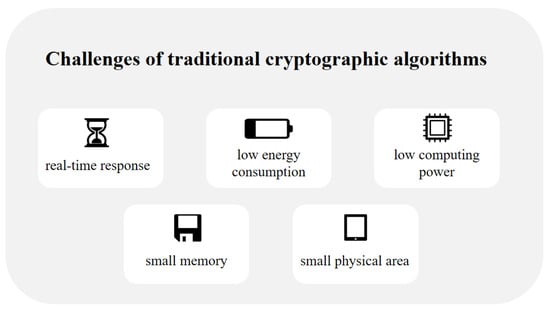
Figure 7.
Challenges of traditional cryptographic algorithms.
3.2.1. Lightweight Symmetric Cryptography
Lightweight block ciphers represent a critical branch of lightweight cryptography and a focal point in cryptanalysis research, with widespread applications in IoT devices. In recent years, researchers have proposed numerous lightweight block cipher algorithms and evaluated their hardware/software performance across diverse platforms [83,84,85].
Modern cryptography originated in the 1970s. IBM’s Data Encryption Standard (DES) [86], developed in the early 1970s, became the first federal encryption standard. Limited by embedded system constraints [87], early lightweight ciphers primarily targeted specific application scenarios. Since the 1990s, internet advancements have driven cryptographic innovation, leading to classic block ciphers like the International Data Encryption Algorithm (IDEA), Tiny Encryption Algorithm (TEA), and camellia [88]. The Advanced Encryption Standard (AES) [89], now globally adopted as the next-generation standard, offers enhanced security over DES but requires greater computational resources. To address lightweight demands, Eisenbarth et al. [90] introduced compact implementations based on the DES and AES. Block ciphers can be classified into six core architectures based on internal structures: Substitution–Permutation Network (SPN), Feistel Network (FN), Generalized Feistel Network (GFN), Add–Rotate–XOR (ARX), and hybrid structures. The following sections analyze representative block cipher algorithms through these architectural frameworks.
SPN structure. In 2003, NIST proposed the AES [89] to replace the DES algorithm. Its lightweight hardware implementation requires 2400 Gate Equivalents (GEs), establishing a benchmark for subsequent algorithm optimizations. In 2007, researchers proposed the PRESENT algorithm [91] at CHES, a hardware-oriented ultra-lightweight cipher. By adopting a single 4 × 4 S-box and 31-round iterative structure, it significantly improved hardware efficiency while ensuring security. This achievement became an ISO/IEC international standard in 2012. In 2012, researchers introduced the PRINCE algorithm [92] at ASIACRYPT. It uses a 64-bit block length, 128-bit key, and 12-round iteration. Its encryption/decryption processes share identical circuits, effectively reducing hardware costs and improving computational efficiency. The same year, Gong et al. [93] proposed the KLEIN algorithm. With a 64-bit block length, its column byte mixing design draws on AES’s column mixing transformation, achieving better software performance on classic sensor platforms. In 2015, Zhang et al. [94] developed the RECTANGLE algorithm for multi-platform compatibility. It features a 64-bit block length, 25-round iteration, and a substitution layer with 16 parallel 4 × 4 S-boxes to balance security and performance. Its permutation layer employs three cyclic shifts, lowering hardware costs. In 2016, Beierle et al. [95] proposed the SKINNY algorithm, a tunable block cipher framework offering six versions to support diverse key sizes and block lengths, ensuring low latency and high security.
Feistel structure. In 2007, Leander et al. [96] proposed a lightweight DESL algorithm that improves the DES and reduces the gate complexity of the algorithm by reusing one S-box eight times. In terms of hardware implementation, DESL and the DES have the same throughput, but the occupied area is reduced by about 20% compared with the DES. In 2011, Wu et al. [97] designed a lightweight block cipher LBlock algorithm by drawing on the PRESENT algorithm. It adopts the NLFSR structure and utilizes S-box transformation and cyclic shifting to generate round keys. In terms of hardware implementation, the throughput of LBlock and PRESENT-80 is the same, but the occupied area of LBlock is reduced by about 16% compared with PRESENT-80. In 2015, the National Security Agency (NSA) introduced the SIMON algorithm [98]. The SIMON algorithm is categorized into 10 versions, with the classification determined by different block lengths and key lengths. The round function of this algorithm comprises cyclic left shift, bitwise AND, and bitwise XOR operations. Notably, the SIMON algorithm is distinguished by its ease of implementation and its excellent performance in both hardware and software environments.
GFN structure. In 2007, Shirai et al. [99] proposed the CLEFIA algorithm using a four-branch GFN structure. Its CLEFIA-128 variant processes data through a serialized framework without requiring additional registers. ISO/IEC recognized it as a standardized lightweight block cipher in 2012. In 2011, Shibutani et al. [100] developed the ultra-lightweight PICCOLO algorithm, featuring a 64-bit block length, 80/128-bit key support, and hardware implementation requiring only 683 GE for encryption (60 GE extra for decryption). The same year, Suzaki et al. [101] introduced the TWINE algorithm with a 64-bit block length, 80/128-bit keys, and 36-round structure. While sharing design principles with LBlock, TWINE enhances security through 10 unique S-boxes and achieves superior lightweight performance across multiple modules.
ARX structure. In 2014, Hong et al. [102] proposed a software design-oriented LEA algorithm that supports 128/192/256-bit key lengths. The algorithm implements fast software encryption on general-purpose processors and has a small code size. In terms of software implementation, LEA-128 has lower ROM and RAM occupancy than AES-128. In 2015, the SPECK algorithm [98] was proposed by the NSA to provide 10 block/key length combinations. Compared with SIMON, the software implementation of SPECK has better performance, but the hardware implementation is relatively inefficient.
Hybrid structure. In 2010, Engels et al. [103] developed the ultra-lightweight HUMMINGBIRD algorithm for resource-constrained devices. This cipher uses a 16-bit block length with 256-bit keys and 20 iteration rounds. In 2022, Dobraunig et al. [104] proposed the ASCON lightweight encryption algorithm, which supports two modes: lightweight authenticated encryption and lightweight hashing. Notably, NIST adopted ASCON as a standardized encryption solution for IoT devices.
Lightweight block cipher algorithms need to balance cost and performance to minimize both software and hardware implementation overhead. Researchers categorize evaluation metrics into three groups: hardware implementation metrics, software implementation metrics, and generalized metrics. For hardware evaluation, GE measures the logic gates required to implement the algorithm. The ISO/IEC standard specifies that lightweight ciphers should maintain GE values between 1000 and 2000. Common generalized metrics include block size, key size, and number of encryption rounds. Table 6 provides a comparative analysis of the lightweight block ciphers discussed in this study, evaluating their performance across these critical parameters.

Table 6.
Comparison and evaluation of lightweight block cipher algorithms.
3.2.2. Public Key Cryptography
Since symmetric cryptographic algorithms have lower computational complexity and energy consumption compared to public key cryptographic algorithms, much of the current research and design of cryptographic authentication techniques is based on symmetric cryptographic algorithms. However, there are also many researchers who have applied asymmetric cryptographic algorithms to UAC and verified the feasibility of applying asymmetric cryptographic algorithms to unmanned systems for WSNs. The security strength of asymmetric cryptographic algorithms is mainly based on the inverse difficulty of solving a single problem, such as discrete logarithm solving, large number decomposition, and elliptic curve solving. The two most widely used asymmetric key algorithms at this stage are the RSA algorithm [105] and ECC algorithm [106]. It has been shown that ECC has more significant advantages than RSA for the same security strength. For example, there are shorter key length, faster computation speed, and less storage consumption and bandwidth consumption [107,108,109,110]. Many scholars are researching and designing cryptographic protocols which will apply asymmetric cryptographic algorithms to scenarios with corresponding security requirements.
In 2017, Yuan et al. [111] proposed a hierarchical identity-based broadcast signing and encryption scheme, but it lacks a security proof and secure model construction. In 2018, Manikandan et al. [112] introduced a certificateless encryption and authentication scheme with an optimized clustered WSN key management system. While this system enhances underwater nodes’ resistance to DDOS attacks through public–private key distribution, it falls short in ensuring special data security due to the public nature of underwater acoustic channels. In the same year, Cong et al. [113] proposed a security protection scheme for underwater communication networks that includes a reputation system and a distributed key management mechanism for the main security problems faced by underwater networks. Li et al. [114] developed a chaotic compressed sensing-based transmission scheme that strategically combines energy efficiency with security enhancements. The method alternates between encrypted and unencrypted data phases, where compressed sensing deliberately introduces controlled signal distortion during non-critical transmissions to mask communication patterns, achieving 35% energy reduction while maintaining equivalent security levels at conventional full-time encryption. In 2019, Diamant et al. [115] proposed a cooperative authentication scheme for UAC networks with the help of trusted nodes to assist the aggregation nodes in trust assessment for authentication decision making. In 2020, Kumar et al. [116] proposed a lightweight grid-signing encryption scheme for WSNs based on the grid cipher, which fully takes into consideration the characteristics of the mobile sensor nodes in order to expand the monitoring range. In the same year, Zhang et al. [117] proposed an underwater user authentication and key negotiation method based on chaotic mapping, which employs a chaotic mapping of one-way hash functions to realize lightweight key exchange and authentication for UAC networks. In 2022, Signori et al. [118] proposed a node reputation management system for aquatic acoustic communication networks. This system uses a Markov model and channel state knowledge, along with perceived noise and received signal strength, to infer state information and assess node trustworthiness based on reputation values.
The research achievements of these scholars have laid a crucial foundation for in-depth studies of lightweight cryptographic algorithms. However, it should be noted that symmetric ciphers have not been directly simulated or tested in underwater environments. Instead, only software and hardware encryption and decryption tests have been conducted, which may not fully reflect their performance and applicability in complex underwater communication scenarios. In the realm of public-key cryptography, some algorithms have been simulated in WSNs, and a few have even undergone simulations in underwater environments. Nevertheless, almost none of them have been tested in real underwater environments. As a result, in the field of lightweight cryptographic algorithms for secure transmission technologies, there remains a significant lack of real-world validation. Their work provides essential theoretical support for developing low-power, lightweight security protocols for UUVs. It also inspires new approaches to efficient encryption under low-power conditions. These contributions offer valuable theoretical guidance and practical insights for designing and optimizing related protocols.
3.3. Cryptographic Synchronization Algorithm
WSNs face significant challenges due to harsh channel conditions. These include limited bandwidth, high delays, multipath effects, and signal fading. Network operations depend on node-to-node communication, where node conditions directly impact both time and cryptographic synchronization [119,120,121]. Time synchronization supports cryptographic processes by providing precise timing data. This accuracy enables reliable cryptographic parameter configuration, such as update intervals, ensuring secure key management in critical applications. Cryptographic synchronization reciprocally strengthens time synchronization by preventing data tampering, maintaining system integrity [122]. For data transmission, bandwidth limitations require optimization strategies [123]. Joint coding techniques effectively enhance transmission efficiency within these constraints. During data processing, time synchronization triggers cryptographic operations, while cryptographic logs provide timestamped records for system audits and fault analysis. This dual method ensures robust network performance through coordinated synchronization.
In recent years, some progress has been made in the study of time synchronization protocols for UWSNs. Most of the protocols use the timestamp synchronization method to achieve time synchronization of network nodes. Syed et al. [124] proposed the TSHL time synchronization protocol for long-distance communication networks, which divides the synchronization process into two phases: timestamp acquisition and clock skew estimation. However, the protocol produces large errors when dealing with autonomous fast-moving AUV nodes and performs especially poorly when the underwater sensor nodes are relatively stationary. To address this problem, Chen et al. [125] improved the TSHL protocol and proposed a novel time synchronization protocol for long-range communication. The protocol reduces the number of message interactions to three, which significantly reduces the network overhead. However, the protocol still generates large time synchronization errors when the underwater nodes are in relative motion, and thus is only applicable to UUV scenarios where the communicating nodes are relatively stationary.
Aiming at the problem that the above time synchronization protocols are difficult to adapt to the underwater dynamic environment, researchers have proposed various improvement schemes. Feng et al. [126] proposed a Doppler-assisted time synchronization protocol for underwater acoustic sensor networks, which effectively reduces the influence of node mobility on time synchronization through the Doppler effect compensation technique. However, this technology suffers from a degradation of synchronization accuracy when the initial value of clock skew is large. To address this limitation, Ying et al. [127] developed a mobile offset time synchronization protocol. This protocol achieves accurate estimation of clock deviation by analyzing the mechanism of node mobility on clock skew. However, its application is limited by the need for two reference nodes with the same time reference, which is often difficult to realize in practical deployment. On this basis, Liu et al. [128] proposed a dynamic time synchronization scheme based on Doppler shift. The scheme utilizes the Doppler effect between dynamically moving nodes. By integrating timestamp information, velocity, acceleration, and sound speed, it estimates propagation delay and subsequently calculates clock deviation through linear regression. Although this method is theoretically more complete, its complicated parameter estimation process leads to low computational efficiency and still needs further optimization. These studies have gradually advanced the development of time synchronization techniques for underwater dynamic environments, but each of them still has certain limitations and needs to be improved in terms of accuracy, applicability, and computational efficiency in subsequent studies.
For the performance evaluation criteria of classical time synchronization protocols in UUVs, both use post-synchronization clock error [129] to describe the synchronization accuracy and energy efficiency metrics [130] to describe the node energy consumption information:
In Equation (2), is the initial value of the clock error, is the clock skew, is the noise, and clock error reflects the clock skew estimation accuracy. In Equation (3), is the network lifetime, is the number of synchronizations, and and are the number of messages required for each synchronization and the length of each message, respectively. In addition to the accuracy and energy efficiency indicators, the classical time synchronization protocols will also analyze the changing law of the own parameters, but these parameters are not universal and cannot be used as evaluation indicators.
With the deep integration between communication and cryptography, modern communication systems impose dual requirements on cryptographic modules: ensuring reliable performance and minimizing the impact on communication efficiency [131,132,133]. To this end, it is necessary to optimize the transmission involvement of the cryptographic module by transmitting only critical information during the key synchronization process to reduce the system overhead. Compared to traditional synchronization methods, this synchronization mechanism significantly reduces the amount of information transmitted by transmitting seed information to achieve link synchronization, thus reducing the overall impact on the communication system [134]. However, UAC is often difficult to directly apply traditional key transmission methods due to their unique channel characteristics. Limited by the payload of a single transmission, it is necessary to develop a dedicated synchronization scheme suitable for underwater acoustic environments, drawing on the design ideas of low-overhead cryptographic synchronization [135]. Such a scheme needs to achieve efficient cryptographic synchronization under the premise of guaranteeing security and taking into full consideration the characteristics of the underwater acoustic channel, such as high latency and low bandwidth.
Recent years have witnessed significant progress in cryptographic synchronization for communication security. Feng et al. [136] demonstrated deep integration of cryptographic synchronization with wireless communication through system modeling and quantitative analysis. Their work achieved microsecond-level synchronization delays, though the full information-sharing mechanism maintained over 35% synchronization redundancy, indicating potential for further optimization. To address this limitation, Zhou et al. [137] proposed a cryptographic synchronization technique leveraging system time. This method demonstrates strong efficacy in narrow band systems with network-wide synchronized time, achieving key synchronization resilient to channel quality variations through system time transformation. The method requires precise compensation for system time deviations and transmission delays. For narrowband environments lacking time synchronization, Zhang et al. [138] developed a random number synchronization scheme. Their method strategically optimizes three core parameters: cryptographic key lifespan, encryption frequency, and random number variation scope. This parametric control maintains message key reuse probability below 0.1% while preserving 98% communication throughput. Ju et al. [139] proposed an innovative self-synchronizing chaotic encryption approach. Their technique eliminates key synchronization information transmission by using preconfigured working keys and initialization vectors, significantly reducing system complexity. Guo et al. [140] designed a specialized cryptographic synchronization scheme. They validated the effectiveness of the scheme in diverse underwater environments using scenario-specific modeling and comparative simulations. Experimental results confirmed reliable performance, achieving a 0.05% bit error rate under high-noise conditions. Figure 8 illustrates the system architecture, providing implementation guidance. These advancements collectively strengthen cryptographic synchronization technology from multiple perspectives. They establish a solid foundation for UUV-specific synchronization protocols while offering valuable insights for future secure communication system design.
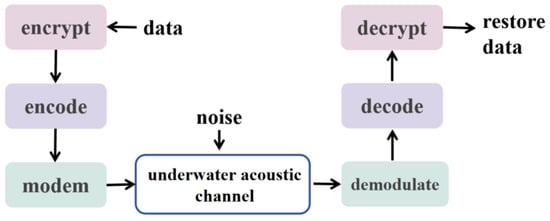
Figure 8.
Block diagram of underwater acoustic encrypted communication systems.
Time synchronization protocols face challenges in balancing dynamic accuracy with computational efficiency, while cryptographic synchronization schemes often struggle to reduce redundancy or enhance key management without compromising security. These limitations underscore the need for integrated, lightweight solutions tailored to the unique constraints of underwater wireless sensor networks, where even simulated advancements, whether in time synchronization or cryptographic mechanisms, rarely translate to operational viability without addressing the harsh realities of aquatic deployment, such as equipment corrosion, unpredictable environmental interference, and limited maintenance access.
In summary, time synchronization and cryptographic synchronization techniques exhibit distinct performance trade-offs and technical bottlenecks, as outlined in Table 7. Notably, while most fundamental time synchronization protocols have undergone simulation testing in underwater environments to evaluate their adaptability to dynamic topologies and acoustic propagation delays, very few have advanced to practical deployment in real-world scenarios. The majority remain confined to virtual testing due to challenges in scaling to large-scale networks or sustaining energy efficiency over prolonged operations. Additionally, cryptographic synchronization methods, particularly those relying on lightweight cryptographic primitives, have not been subjected to underwater simulations or real-world testing at all. This gap highlights a critical oversight, as cryptographic synchronization’s reliance on secure key exchange and low-latency coordination may behave unpredictably in high-noise, bandwidth-constrained UAC channels.

Table 7.
Comparison of synchronization protocols.
4. The Challenges and Key Issues
Due to the unique characteristics of underwater environments, UAC has become the primary communication method for UUVs. However, its limitations, such as low transmission rates and narrow bandwidth, make it difficult to directly apply traditional cryptographic algorithms and security protocols [141,142,143]. Currently, the lack of effective encryption mechanisms in UAC exposes sensitive information, including key commands, location data, and core operational parameters, to heightened security risks. Aiming at the problems of weak UAC capability and high BER of UUVs, the design of security protection protocols needs to take into account security strength and computational efficiency and minimize the consumption of resources and space [144,145,146]. The complexity of the underwater environment makes the reliability of individual nodes face challenges, which are vulnerable to attacks and may also fail due to environmental factors. Based on the above problems, the research of secure UAC for UUVs faces multi-level challenges.
4.1. UAC Authentication Encounters Difficulty Combining High Security and Dynamic Adaptability
High security demands authentication with robust anti-attack capabilities to resist eavesdropping, tampering, and replay attacks while ensuring data integrity and privacy [147]. The underwater network environment introduces complexity due to node mobility driven by water currents, causing dynamic topology changes and frequent node entry/exit events. These conditions necessitate authentication capable of real-time dynamic updates to rapidly authenticate new nodes and deactivate old ones. A critical challenge arises from the limited computational power, storage capacity, and energy resources of underwater devices, which struggle to concurrently support the computational overhead of high security protocols and real-time adaptability. High security mechanisms risk introducing latency that compromises real-time performance, whereas dynamic adaptability requires instantaneous responses to network changes. This inherent conflict imposes competing requirements on authentication design. To resolve this, research should focus on developing lightweight authentication protocols and adaptive update strategies that minimize energy consumption and computational complexity while maintaining security guarantees and enabling efficient dynamic adaptability [148].
4.2. UAC Secure Transmission Encounters Difficulty Combining High Security and Low Consumption Rate
High-security cryptosystems typically depend on complex algorithms and substantial computational resources. While traditional communication environments can meet these demands, UUVs in UAC face limitations in both computational power and energy reserves. For instance, advanced public-key cryptographic algorithms offer strong security but require significant computational resources for encryption and decryption. This places a heavy burden on underwater devices, leading to increased energy consumption and reduced operational lifespans. Conversely, using simpler encryption algorithms or reducing encryption steps to save energy significantly raises security risks [149]. UAC plays a critical role in military operations, marine resource exploration, and other vital areas. Information leaks in these contexts could have severe consequences. Attackers might exploit vulnerabilities in UAC to intercept and decrypt sensitive data, threatening national security and economic interests.
4.3. UAC Tolerates Excessively Long Cryptographic Synchronization Codes with Difficulty
Cryptographic synchronization codes play a critical role in UAC security. They ensure accurate and synchronous encryption and decryption between communicating parties. However, overly long synchronization codes create significant challenges for UAC. Long synchronization codes consume substantial bandwidth and time, reducing space for effective data transmission. This limitation proves particularly problematic in bandwidth-constrained underwater acoustic environments [150]. For example, in marine environment monitoring, extended synchronization codes can delay critical data transmission, compromising real-time environmental tracking. The receiving end must perform complex synchronization and matching operations to process long codes [151]. These operations strain underwater devices with limited computing power and energy reserves. Potential consequences include increased power consumption, slower processing speeds, and even system failures. Moreover, long synchronization codes face higher vulnerability to noise and interference during transmission. This susceptibility raises the risk of synchronization errors, directly threatening communication security and reliability [152]. These challenges collectively demonstrate why UAC systems struggle to accommodate excessively long cipher synchronization codes. The balance between security requirements and practical limitations remains a critical consideration in underwater communication design.
Based on the above challenges, the following cryptographic issues should be addressed to ensure secure UUV communication: (1) efficient authentication protocol under dynamic topology; (2) lightweight cryptographic algorithm under resource constraints; and (3) fast cryptographic synchronization protocol under channel interference. Lightweight cryptographic algorithms are essential for maintaining data security in underwater environments. To address resource limitations, these algorithms should prioritize structural optimization and minimize redundant computations while preserving security guarantees. High-efficiency authentication protocols require real-time accuracy in dynamic topologies, enabling continuous verification of mobile nodes to ensure communication safety and continuity. Fast cryptographic synchronization protocols need to support rapid multi-node synchronization in highly concurrent scenarios, ensuring reliable encrypted communication. Specially, despite some promising results so far, a notable issue is that most of the work reviewed highlighted the use of simulations to validate their work. But this does not take into account the complex nature of the water environment, nor does it allow for real-world testing. A summary of these challenges and future directions is presented in Table 8. Accordingly, we will place more emphasis on addressing these issues in the future.

Table 8.
Categorized summary of core challenges and future directions.
5. Conclusions
In this paper, a comprehensive overview of cryptography-based secure UAC key technologies is conducted. First, it introduces the background and typical application scenarios of UAC for UUVs. Then, the structures and characteristics of UAC are described, followed by a comparison of different underwater wireless communication technologies. Moreover, the research related to secure UAC is classified into three categories: authentication, lightweight cryptographic algorithms, and cryptographic synchronization algorithms. The performance boundaries and application scenarios of each technology are analyzed. Finally, we discuss the current challenges and key issues for secure underwater communication. We hope this paper can provide theoretical references and technical insights for the further development of secure UAC technology for UUVs.
To meet the specific demands of UUVs, future work in UAC security research requires multi-faceted innovation. Priorities involve developing lightweight cryptographic algorithms, adaptive authentication, and efficient key negotiation. Integrating AI and edge computing should enhance underwater adaptability. Given diverse scenarios like military and marine exploration, tailored security solutions are crucial. Since current studies mainly rely on simulations, future research must bridge theory and practice, promoting cross-domain collaborations to address emerging security challenges. This paper aims to provide theoretical references for advancing secure UAC technology for UUVs and lay a foundation for future work.
Author Contributions
Q.Z.: writing—review and editing. Q.Y.: conceptualization. C.L.: investigation. G.K.: conceptualization. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Defense Foundation Strengthening Technology Fund under Grant 2021-JCJQ-JJ-1267 and in part by the National Natural Science Foundation of China under Grant 6227072896.
Acknowledgments
The Researchers would like to thank the Naval University of Engineering for financial support.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Muller-Karger, F.E.; Gabrielle, C.; Baron, A.C. Marine Life 2030: Building global knowledge of marine life for local action in the Ocean Decade. ICES J. Mar. Sci. 2022, 80, 355–357. [Google Scholar] [CrossRef]
- Liang, Q.; Cheng, X. Underwater acoustic sensor networks: Target size detection and performance analysis. Ad Hoc Netw. 2009, 7, 803–808. [Google Scholar] [CrossRef]
- Kilfoyle, D.B.; Baggeroer, A.B. The state of the art in underwater acoustic telemetry. IEEE J. Ocean. Eng. 2000, 25, 4–27. [Google Scholar] [CrossRef]
- Preisig, J. Acoustic propagation considerations for underwater acoustic communications network development. SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 2–10. [Google Scholar] [CrossRef]
- Carlucho, I.; De Paula, M.; Wang, S.; Menna, B.V.; Petillot, Y.R.; Acosta, G.G. AUV position tracking control using end-to-end deep reinforcement learning. In Proceedings of the OCEANS MTS/IEEE Conference, Charleston, SC, USA, 20–26 October 2018; pp. 1–8. [Google Scholar]
- Gussen, C.; Diniz, P.; Campos, M.; Martins, W.; Costa, F.; Gois, J. A survey of underwater wireless communication technologies. J. Commun. Inf. Syst. 2016, 31, 242–255. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, Z.; Wang, J.; Jiang, C.; Han, Z.; Ren, Y. Design of heterogeneous multi-AUV IoUT: Architecture, key technologies and applications. IEEE Wirel. Commun. 2025, 32, 198–205. [Google Scholar] [CrossRef]
- Gohari, A.; Kramer, G. An upper bound on secret key rates for general multiterminal wiretap channels. In Proceedings of the IEEE International Symposium on Information Theory, Taipei, Taiwan, 25–30 June 2023; pp. 2320–2325. [Google Scholar]
- Almuhaideb, A.M.; Alghamdi, H.A. Design of inter-BAN authentication protocols for WBAN in a cloud-assisted environment. Big Data Cognit. Comput. 2022, 6, 124. [Google Scholar] [CrossRef]
- Huang, X.; Li, L.; Yang, J. IVLBC: An Involutive Lightweight Block Cipher for Internet of Things. IEEE Syst. J. 2023, 17, 3192–3203. [Google Scholar] [CrossRef]
- Song, Y. Underwater acoustic sensor networks with cost efficiency for Internet of underwater Things. IEEE Trans. Ind. Electron. 2021, 68, 1707–1716. [Google Scholar] [CrossRef]
- Wang, S.; He, Z.; Niu, K.; Chen, P.; Rong, Y. New results on joint channel and impulsive noise estimation and tracking in underwater acoustic OFDM systems. IEEE Trans. Wirel. Commun. 2020, 19, 2601–2612. [Google Scholar] [CrossRef]
- Abdullah; Almuhaideb, M.; Abdullah, M.; Dania, M. An Efficient Authentication and Key Agreement Scheme for the Internet of Underwater Things (IoUT) Environment. IEEE Access 2024, 12, 175773–175789. [Google Scholar]
- Xu, M.; Hao, M. Covert Secret Key Agreement Scheme Based on the Underwater Acoustic Dynamic Hypergraph. IEEE Internet Things J. 2025, 12, 15792–15806. [Google Scholar] [CrossRef]
- Sun, K.; Cui, W.; Chen, C. Review of Underwater Sensing Technologies and Applications. Sensors 2021, 21, 7849. [Google Scholar] [CrossRef]
- Adam, N.; Ali, M.; Naeem, F.; Ghazy, A.S.; Kaddoum, G. State-of-the-Art Security Schemes for the Internet of Underwater Things: A Holistic Survey. IEEE Open J. Commun. Soc. 2024, 5, 6561–6592. [Google Scholar] [CrossRef]
- Pan, P.; Su, Y.; Fan, R.; Yang, S. A Secret Key Generation Scheme Exploiting Spatiotemporal Acoustic Channel Characteristics for Underwater Sensor Networks. IEEE Sens. J. 2024, 24, 31188–31200. [Google Scholar] [CrossRef]
- Stojanovic, M. OFDM for Underwater Acoustic Communications: Adaptive Synchronization and Sparse Channel Estimation. IEEE Trans. Signal Process. 2008, 56, 5061–5075. [Google Scholar]
- Song, H.C.; Hodgkiss, W.S.; Roux, P.; Kuperman, W.A.; Akal, T.; Stevenson, M. Coherent MIMO time reversal communications in shallow water. In Proceedings of the Oceans ’04 MTS/IEEE Techno-Ocean ’04, Kobe, Japan, 9–12 November 2004; Volume 4, pp. 2225–2229. [Google Scholar]
- Guo, J.; Xiao, J.; Chen, J.; Shan, X.; Kong, D.; Wu, Y.; Ai, Y. Performance Analysis of LDPC-Coded OFDM in Underwater Wireless Optical Communications. Photonics 2023, 10, 330. [Google Scholar] [CrossRef]
- Kaushal, H.; Kaddoum, G. Underwater optical wireless communication. IEEE Access 2016, 4, 1518–1547. [Google Scholar] [CrossRef]
- Visschers, F.; Massaad, J.; Neer, P. High-Frequency Surface Dynamics at an Electroactive Polymer Producing Underwater Soundwaves. Adv. Funct. Mater. 2022, 32, 2110754. [Google Scholar] [CrossRef]
- Zhang, B. Autonomous Underwater Vehicle navigation: A review. Ocean Eng. 2023, 273, 113861. [Google Scholar] [CrossRef]
- Diamant, R.; Lampe, L.; Gamroth, E. Bounds for Low Probability of Detection for Underwater Acoustic Communication. IEEE J. Ocean. Eng. 2016, 42, 143–155. [Google Scholar] [CrossRef]
- Yan, S. Low Probability of Detection Communication: Opportunities and Challenges. IEEE Wirel. Commun. 2019, 26, 19–25. [Google Scholar] [CrossRef]
- Muzzammil, M. Full-Duplex Magnetic Induction Communication: Opportunities and Challenges. IEEE Wirel. Commun. 2024, 31, 19–25. [Google Scholar] [CrossRef]
- Khalil, R.A. Toward the Internet of Underwater Things: Recent Developments and Future Challenges. IEEE Consum. Electron. Mag. 2021, 10, 32–37. [Google Scholar] [CrossRef]
- Kong, M.; Wang, J.; Chen, Y. Security weaknesses of underwater wireless optical communication. Opt. Express 2017, 25, 21509–21518. [Google Scholar] [CrossRef] [PubMed]
- Stojanovic, M.; Medard, M.; Lucani, D. On the relationship between capacity and distance in an underwater acoustic communication channel. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 34–43. [Google Scholar] [CrossRef]
- Ling, J.; He, H.; Li, J.; Roberts, W.; Stoica, P. Covert Underwater Acoustic Communications. J. Acoust. Soc. Am. 2010, 128, 2898–2909. [Google Scholar] [CrossRef]
- Zhang, W.; Liu, X.; Han, P. Research Progress of Water Unmanned Systems and Challenges. Acta Autom. Sin. 2020, 46, 847–857. [Google Scholar]
- Wu, Y.C.; Wang, Y.A. Research on Underwater Target Recognition Neural Network for Small Samples. J. Northwestern Polytech. Univ. 2022, 40, 40–46. [Google Scholar] [CrossRef]
- Guo, K. Numerical Study on Hydrodynamic Coefficients of Autonomous Underwater Vehicles. Master’s Thesis, Harbin Institute of Technology, Harbin, China, 2009. [Google Scholar]
- Burgess, R.R. Knifefish UUV Enters Low-Rate Initial Production. Seapower Magazine, 27 August 2019. Available online: https://seapowermagazine.org/navys-knifefish-uuv-achieves-milestone-c/ (accessed on 27 August 2019).
- Wang, Z.; Qu, X.; Li, L.; Wang, L. Development Overview and Application Prospects of Advanced UUVs. In Proceedings of the 3rd International Conference on Artificial Intelligence, Robotics, and Communication(ICAIRC), Xiamen, China, 27–29 October 2023; Springer: Singapore, 2023; pp. 35–45. [Google Scholar]
- Si, G.; Miao, Y.; Li, G. Construction Technology of Underwater Three-Dimensional Offensive and Defensive System. Command Control Simul. 2018, 40, 1–8. [Google Scholar]
- Pan, Z. Prospect of Artificial Intelligence Technology in Intelligent Control of Unmanned Surface Vehicles. Digit. Ocean Underw. Warf. 2024, 7, 561–570. [Google Scholar]
- Liu, S.; Irfan, U.; Muhammad, M.; Niaz, A.; Abdul, W.; Shao, Z. Empowering Internet of Underwater Things: An Integrated Simulator for Underwater Magneto-Coupled Wireless Sensor Networks. IEEE Internet Things Mag. 2025, 8, 109–114. [Google Scholar]
- Liu, S.; Zuberi, H.H.; Lou, Y. Mary Nonlinear Sine Chirp Spread Spectrum for Underwater Acoustic Communication Based on Virtual Time-Reversal Mirror Method. J. Wirel. Com. Netw. 2021, 2021, 112. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S. A New and Secure Authentication Scheme for Wireless Sensor Networks with Formal Proof. Peer Peer Netw. Appl. 2017, 10, 16–30. [Google Scholar] [CrossRef]
- Fattah, S.; Gani, A.; Ahmedy, I.; Idris, M.Y.I.; Targio Hashem, I.A. A Survey on Underwater Wireless Sensor Networks: Requirements Taxonomy, Recent Advances, and Open Research Challenges. Sensors 2020, 20, 5393. [Google Scholar] [CrossRef]
- Rajasoundaran, S.; Kumar, S.V.N.S.; Selvi, M. Secure and Optimized Intrusion Detection Scheme Using LSTM-MAC Principles for Underwater Wireless Sensor Networks. Wirel. Netw. 2024, 30, 209–231. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Li, Y.; Sadiq, M.; Liang, J.; Khan, M.A. Recent Advances, Future Trends, Applications, and Challenges of Internet of Underwater Things (IoUT): A Comprehensive Review. J. Mar. Sci. Eng. 2023, 11, 124. [Google Scholar] [CrossRef]
- Prasanth, A.; Jayachitra, S. A Novel Multi-Objective Optimization Strategy for Enhancing Quality of Service in IoT-Enabled WSN Applications. Peer-Netw. Appl. 2020, 13, 1905–1920. [Google Scholar] [CrossRef]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-phase authentication protocol for wireless sensor networks in distributed IoT applications. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2728–2733. [Google Scholar]
- Fan, X.; Gong, G. LPKM: A Lightweight Polynomial-Based Key Management Protocol for Distributed Wireless Sensor Networks. In Ad Hoc Networks, Proceedings of the International Conference on Ad-Hoc Networks, Belgrade, Serbia, 9–11 July 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 180–195. [Google Scholar]
- Dhillon, P.K.; Kalra, S. A Lightweight Biometrics Based Remote User Authentication Scheme for IoT Services. J. Inf. Secur. Appl. 2017, 34, 255–270. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet Things J. 2017, 5, 269–282. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S. An Improved and Provably Secure Three-Factor User Authentication Scheme for Wireless Sensor Networks. Peer Peer Netw. Appl. 2018, 11, 1–20. [Google Scholar] [CrossRef]
- He, J.; Yang, Y.; Zhang, J.; Liu, W.; Liu, C. On the Security of a Provably Secure Efficient and Flexible Authentication Scheme for Ad Hoc Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2018, 14. [Google Scholar] [CrossRef]
- Mo, J.; Chen, H. A Lightweight Secure User Authentication and Key Agreement Protocol for Wireless Sensor Networks. Secur. Commun. Netw. 2019, 2019, 2136506. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, G.; Li, L. Anonymous Three-Factor Authenticated Key Agreement for Wireless Sensor Networks. Wirel. Netw. 2019, 25, 1461–1475. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security Enhanced User Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.; Kumar, N.; Goutham, R.; Yoon, E. Secure Signature-Based Authenticated Key Establishment Scheme for Future IoT Applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.; Choo, K. A Three-Factor Anonymous Authentication Scheme for Wireless Sensor Networks in Internet of Things Environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Chang, Q.; Zhang, Y.; Qin, L. A Node Authentication Protocol Based on ECC in WSN. In Proceedings of the International Conference on Computer Design and Applications, Qinhuangdao, China, 25–27 June 2010; Volume 2, pp. 606–609. [Google Scholar]
- Wang, G.; Ke, F.; Wang, F. A Three-Party Password-Authenticated Key Exchange Protocol Based on ECDSA. Comput. Eng. 2012, 38, 159–161. [Google Scholar]
- Porambage, P. PAuthKey: A Pervasive Authentication Protocol and Key Establishment Scheme for Wireless Sensor Networks in Distributed IoT Applications. Int. J. Distrib. Sens. Netw. 2014, 10, 357430–357435. [Google Scholar] [CrossRef]
- Maurya, A.K.; Sastry, V.N. Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things. Information 2017, 8, 136–139. [Google Scholar] [CrossRef]
- Han, G.; Jiang, J.; Shu, L.; Guizani, M. An Attack-Resistant Trust Model Based on Multidimensional Trust Metrics in Underwater Acoustic Sensor Networks. IEEE Trans. Mob. Comput. 2015, 14, 2447–2459. [Google Scholar] [CrossRef]
- Jiang, J.; Han, G.; Shu, L.; Chan, S.; Wang, K. A Trust Model Based on Cloud Theory in Underwater Acoustic Sensor Networks. IEEE Trans. Ind. Inform. 2015, 13, 342–350. [Google Scholar] [CrossRef]
- Arifeen, M.M.; Islam, A.; Rahman, M.; Taher, K.; Islam, M. ANFIS Based Trust Management Model to Enhance Location Privacy in Underwater Wireless Sensor Networks. In Proceedings of the International Conference on Electrical, Computer and Communication Engineering 2019, Cox’s Bazar, Bangladesh, 7–9 February 2019; pp. 1–6. [Google Scholar]
- Han, G.; He, Y.; Jiang, J.; Wang, N.; Guizani, M.; Ansere, J. A Synergetic Trust Model Based on SVM in Underwater Acoustic Sensor Networks. IEEE Trans. Veh. Technol. 2019, 68, 11239–11247. [Google Scholar] [CrossRef]
- Du, J.; Han, G.; Lin, C. ITrust: An Anomaly-Resilient Trust Model Based on Isolation Forest for Underwater Acoustic Sensor Networks. IEEE Trans. Mob. Comput. 2020, 21, 1684–1696. [Google Scholar] [CrossRef]
- Arifeen, M.M.; Bhakta, D.; Remu, S.; Islam, M.; Mahmud, M. Hidden Markov Model Based Trust Management Model for Underwater Wireless Sensor Networks. In Proceedings of the International Conference on Computer Advancements 2020, Dhaka, Bangladesh, 10–12 January 2020; pp. 1–5. [Google Scholar]
- Muthukkumar, R.; Manimegalai, D. Secured Transmission Using Trust Strategy-Based Dynamic Bayesian Game in Underwater Acoustic Sensor Networks. J. Ambient Intell. Humaniz. Comput. 2021, 12, 2585–2600. [Google Scholar] [CrossRef]
- Jiang, J.; Zhu, X.; Han, G.; Guizani, M.; Shu, L. A Dynamic Trust Evaluation and Update Mechanism Based on C4.5 Decision Tree in Underwater Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2020, 69, 9031–9040. [Google Scholar] [CrossRef]
- Krishnan, S.S.N. Defending Selective Forwarding Attacks in Underwater Acoustic Networks Applying Trust Model. In Proceedings of the 2nd International Conference on Electronics 2018, Kolkata, India, 4–5 May 2018; pp. 1567–1571. [Google Scholar]
- Su, Y.; Mal, S.; Jin, Z.; Fu, X.; Li, Y.; Liu, X. A Trust Model for Underwater Acoustic Sensor Networks Based on Fast Link Quality Assessment. In Proceedings of the Global Oceans Conference 2020: Singapore, Biloxi, MS, USA, 5–30 October 2020; pp. 1–6. [Google Scholar]
- Han, G.; He, Y.; Jiang, J.; Wang, H.; Peng, Y.; Fan, K. Fault-tolerant trust model for hybrid attack mode in underwater acoustic sensor networks. IEEE Netw. 2020, 34, 330–336. [Google Scholar] [CrossRef]
- Su, Y.; Ma, S.; Zhang, H.; Jin, Z.; Fu, X. A Redeemable SVM-DS Fusion-Based Trust Management Mechanism for Underwater Acoustic Sensor Networks. IEEE Sens. J. 2021, 21, 26161–26174. [Google Scholar] [CrossRef]
- Li, W. Research on Secure Communication Mechanisms Between Nodes in Underwater Acoustic Sensor Networks. Master’s Thesis, Nanjing University of Posts and Telecommunications, Nanjing, China, 2021. [Google Scholar]
- He, Y.; Han, G.; Jiang, J.; Wang, H.; Martínez-García, M. A trust update mechanism based on reinforcement learning in underwater acoustic sensor networks. IEEE Trans. Mob. Comput. 2020, 21, 811–821. [Google Scholar] [CrossRef]
- Du, J.; Han, G.; Lin, C. An edge-computing-enabled trust mechanism for underwater acoustic sensor networks. IEEE Commun. Stand. Mag. 2022, 6, 44–51. [Google Scholar] [CrossRef]
- Du, J.; Han, G.; Lin, C.; Martínez-García, M. LTrust: An adaptive trust model based on LSTM for underwater acoustic sensor networks. IEEE Trans. Wirel. Commun. 2022, 21, 7314–7328. [Google Scholar] [CrossRef]
- Cai, W. Research on Energy-Saving Algorithms and Security Management in UWSN. Ph.D. Thesis, Guilin University of Electronic Technology, Guilin, China, 2020. [Google Scholar]
- Lü, W.; Gao, D. Secure clustering routing protocol based on fuzzy control and node trustworthiness. J. Chang. Inst. Eng. 2022, 23, 94–97. [Google Scholar]
- Liang, K. Research on Malicious Node Identification Technology in Underwater Sensor Networks Based on Trust Model. Master’s Thesis, Hainan University, Haikou, China, 2022. [Google Scholar]
- Mohd, B.J.; Hayajneh, T.; Vasilakos, A.V. A survey on lightweight block ciphers for low-resource devices: Comparative study and open issues. J. Netw. Comput. Appl. 2015, 58, 73–93. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Moon, S.Y. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient Intell. Humaniz. Comput. 2017, 4, 1–18. [Google Scholar] [CrossRef]
- Banafa, A. Three major challenges facing IoT. In Introduction to Internet of Things (IoT); River Publishers: Gistrup, Denmark, 2017; pp. 29–36. [Google Scholar]
- Bhardwaj, I.; Kuma, A.; Bansal, M. A review on lightweight cryptography algorithms for data security and authentication in IoTs. In Proceedings of the 2017 4th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 21–23 September 2017; pp. 504–509. [Google Scholar]
- Diehl, W.; Farahmand, F.; Yalla, P. Comparison of hardware and software implementations of selected lightweight block ciphers. In Proceedings of the 2017 27th International Conference on Field Programmable Logic and Applications (FPL), Ghent, Belgium, 4–8 September 2017; pp. 1–4. [Google Scholar]
- Bansod, G.; Raval, N.; Pisharoty, N. Implementation of a new lightweight encryption design for embedded security. IEEE Trans. Inf. Forensics Secur. 2014, 10, 142–151. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M.E. Special feature exhaustive cryptanalysis of the NBS data encryption standard. Computer 1977, 10, 74–84. [Google Scholar] [CrossRef]
- Fysarakis, K.; Hatzivasilis, G.; Rantos, K. Embedded systems security challenges. In Proceedings of the 4th International Conference on Pervasive and Embedded Computing and Communication Systems (MeSeCCS-2014), Lisbon, Portugal, 7–9 January 2014; pp. 255–266. [Google Scholar]
- Aoki, K.; Ichikawa, T.; Kanda, M. Camellia: A 128-bit block cipher suitable for multiple platforms—Design and analysis. In Selected Areas in Cryptography, 7th Annual International Workshop, SAC 2000, Waterloo, Ontario, Canada, 14–15 August 2000; Springer: Berlin/Heidelberg, Germany, 2001; pp. 39–56. [Google Scholar]
- Bertoni, G.; Breveglieri, L.; Fragneto, P. Efficient software implementation of AES on 32-bit platforms. In Cryptographic Hardware and Embedded Systems—CHES 2002, Proceedings of the 4th International Workshop, Redwood Shores, CA, USA, 13–15 August 2002; Springer: Berlin/Heidelberg, Germany, 2003; pp. 159–171. [Google Scholar]
- Eisenbarth, T.; Gong, Z.; Guneysu, T. Compact implementation and performance evaluation of block ciphers in tiny devices. In Progress in Cryptology—AFRICACRYPT 2012, Proceedings of the 5th International Conference on Cryptology in Africa, Ifrane, Morocco, 10–12 July 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 172–187. [Google Scholar]
- Bogdanov, A.; Knudsen, L.R.; Leander, G. PRESENT: An ultra-lightweight block cipher. In Cryptographic Hardware and Embedded Systems—CHES 2007, Proceedings of the 9th International Workshop, Vienna, Austria, 10–13 September 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Borghoff, J.; Canteaut, A.; Güneysu, T.; Kavun, E.B.; Knezevic, M.; Knudsen, L.R.; Leander, G.; Nikov, V.; Paar, C.; Rechberger, C.; et al. PRINCE: A low-latency block cipher for pervasive computing applications. In Advances in Cryptology—ASIACRYPT 2012, Proceedings of the 18th International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 208–225. [Google Scholar]
- Gong, Z.; Nikova, S.; Law, Y.W. KLEIN: A new family of lightweight block ciphers. In RFID. Security and Privacy, Proceedings of the 7th International Workshop, RFIDsec 2011, Amherst, MA, USA, 26–28 June 2011; Springer: Berlin/Heidelberg, Germany, 2012; pp. 1–18. [Google Scholar]
- Zhang, W.; Bao, Z.; Lin, D. RECTANGLE: A Bit-Slice Lightweight Block Cipher Suitable for Multiple Platforms. Sci. China Inf. Sci. 2015, 58, 1–15. [Google Scholar] [CrossRef]
- Beierle, C.; Jean, J.; Kolbl, S. The SKINNY family of block ciphers and its low-latency variant MANTIS. In Advances in Cryptology—CRYPTO 2016, Proceedings of the 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 123–153. [Google Scholar]
- Leander, G.; Paar, C.; Poschmann, A. New lightweight DES variants. In Fast Software Encryption, Proceedings of the 14th International Workshop, FSE 2007, Luxembourg, 26–28 March 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 196–210. [Google Scholar]
- Wu, W.; Zhang, L. LBlock: A lightweight block cipher. In Applied Cryptography and Network Security, Proceedings of the 9th International Conference, ACNS 2011, Nerja, Spain, 7–10 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 327–344. [Google Scholar]
- Beaulieu, R.; Shors, D.; Smith, J. The SIMON and SPECK families of lightweight block ciphers. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Shirai, T.; Shibutani, K.; Akishita, T.; Moriai, S.; Iwata, T. The 128-bit blockcipher CLEFIA extended abstract. In Fast Software Encryption, Proceedings of the 14th International Workshop, FSE 2007, Luxembourg, 26–28 March 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 181–195. [Google Scholar]
- Shibutani, K.; Isobe, T.; Hiwatari, H.; Mitsuda, A.; Akishita, T.; Shirai, T. Piccolo: An ultra-lightweight blockcipher. In Cryptographic Hardware and Embedded Systems—CHES 2011, Proceedings of the 13th International Workshop, Nara, Japan, 28 September–1 October 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 342–357. [Google Scholar]
- Suzaki, T.; Minematsu, K.; Morioka, S. TWINE: A lightweight, versatile block cipher. In Proceedings of the ECRYPT Workshop Lightweight Cryptography 2011, Louvain-la-Neuve, Belgium, 28 November 2011; pp. 146–192. [Google Scholar]
- Hong, D.; Lee, J.-K.; Kim, D.-C.; Kwon, D.; Ryu, K.H.; Lee, D.-G. LEA: A 128-bit block cipher for fast encryption on common processors. In Information Security Applications, Proceedings of the 14th International Workshop, WISA 2013, Jeju Island, Republic of Korea, 19–21 August 2013; Springer: Cham, Switzerland, 2014; pp. 3–27. [Google Scholar]
- Engels, D.; Fan, X.; Gong, G.; Hu, H.; Smith, E.M. Hummingbird: Ultra-lightweight cryptography for resource-constrained devices. In Financial Cryptography and Data Security, Proceedings of the FC 2010 Workshops, WLC, RLCPS, and WECSR, Tenerife, Spain, 25–28 January 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 3–18. [Google Scholar]
- Dobraunig, C.; Eichlseder, M.; Mendel, F.; Schläffer, M. Ascon v1.2: Lightweight authenticated encryption and hashing. J. Cryptol. 2021, 34, 33. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Darehshoorzadeh, A.; Boukerche, A. Underwater sensor networks: A new challenge for opportunistic routing protocols. IEEE Commun. Mag. 2015, 53, 98–107. [Google Scholar] [CrossRef]
- Lal, C.; Petroccia, R.; Pelekanakis, K. Toward the development of secure underwater acoustic networks. IEEE J. Ocean. Eng. 2017, 42, 1075–1087. [Google Scholar] [CrossRef]
- Liu, J.; Shen, Z.; Han, Q. Underwater acoustic communication physical layer key generation scheme. J. Commun. 2019, 40, 111–117. [Google Scholar]
- Zhang, J.; Sha, J.; Han, G. A cooperative-control-based underwater target escorting mechanism with multiple autonomous underwater vehicles for underwater internet of things. IEEE Internet Things J. 2021, 8, 4403–4416. [Google Scholar] [CrossRef]
- Yuan, C.; Chen, W.; Li, D. A hierarchical identity-based signcryption scheme in underwater wireless sensor network. In Wireless Sensor Networks, Proceedings of the 11th China Wireless Sensor Network Conference, CWSN 2017, Tianjin, China, 12–14 October 2017; Springer: Singapore, 2017; pp. 44–54. [Google Scholar]
- Manikandan, G.; Sakthi, U. Optimal cluster based key management system using signcryption algorithm for wireless sensor networks. Neural Netw. 2018, 28, 433–455. [Google Scholar] [CrossRef]
- Cong, J.; Zhang, H. Research on key technology of underwater network security. Commun. Technol. 2018, 318, 147–151. [Google Scholar]
- Li, X.; Wang, C.; Yang, Z. Energy-efficient and secure transmission scheme based on chaotic compressive sensing in underwater wireless sensor networks. Digit. Signal Process. 2018, 81, 129–137. [Google Scholar] [CrossRef]
- Diamant, R.; Casari, P.; Tomasin, S. Cooperative authentication in underwater acoustic sensor networks. IEEE Trans. Wirel. Commun. 2019, 18, 954–968. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Rai, M.K. A lattice signcrypted secured localization in wireless sensor networks. IEEE Syst. J. 2020, 14, 3949–3956. [Google Scholar] [CrossRef]
- Zhang, S.L.; Du, X.J.; Liu, X. A secure remote mutual authentication scheme based on chaotic map for underwater acoustic networks. IEEE Access 2020, 8, 48285–48298. [Google Scholar] [CrossRef]
- Signori, A.; Campagnaro, F.; Nissen, I. Channel-based trust model for security in underwater acoustic networks. IEEE Internet Things J. 2022, 9, 20479–20491. [Google Scholar] [CrossRef]
- Guo, G.; Yu, Z. An improved clock synchronization algorithm for wireless sensor network of underground water supply pipeline. In Proceedings of the 2019 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Ajman, United Arab Emirates, 10–12 December 2019; pp. 1–6. [Google Scholar]
- Liu, F.; Chen, H.; Zhang, L. Time difference of arrival based localization methods of underwater mobile nodes using multiple surface beacons. IEEE Access 2021, 9, 31712–31724. [Google Scholar] [CrossRef]
- Gong, Z.; Li, C.; Jiang, F. AUV-aided joint localization and time synchronization for underwater acoustic sensor networks. IEEE Signal Process. Lett. 2018, 25, 477–481. [Google Scholar] [CrossRef]
- Gardner, A.; Collins, J.A. A second look at Chip Scale Atomic Clocks for long term precision timing. In Proceedings of the OCEANS 2016 MTS/IEEE Monterey, Monterey, CA, USA, 19–23 September 2016; pp. 1–9. [Google Scholar]
- Elson, J.; Girod, L.; Estrin, D. Fine-grained network time synchronization using reference broadcasts. In Proceedings of the 5th Symposium on Operating Systems Design and Implementation, Boston, MA, USA, 9–11 December 2002; pp. 1–18. [Google Scholar]
- Syed, A.; Heidemann, J. Time synchronization for high latency acoustic networks. In Proceedings of the IEEE INFOCOM 2006, Barcelona, Spain, 23–29 April 2006; pp. 1–12. [Google Scholar]
- Chen, T.; Jiang, H.; Xue, L. Tri-Message: A lightweight time synchronization protocol for high latency and resource-constrained networks. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Feng, X.; Wang, Z.; Zhu, X. Research on Doppler-assisted time synchronization mechanism for underwater sensor networks. J. Commun. 2017, 38, 9–15. [Google Scholar]
- Ying, G.; Liu, Y. Time synchronization for mobile underwater sensor networks. J. Netw. 2013, 8, 57–64. [Google Scholar]
- Liu, J.; Wang, Z.; Zuba, M. DA-Sync: A Doppler-assisted time-synchronization scheme for mobile underwater sensor networks. IEEE Trans. Mob. Comput. 2014, 13, 582–595. [Google Scholar] [CrossRef]
- Hamilton, B.R.; Ma, X.; Zhao, Q. ACES: Adaptive clock estimation and synchronization using Kalman filtering. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14–19 September 2008; pp. 1–6. [Google Scholar]
- Zhou, Z.; Peng, Z.; Cui, J. Scalable localization with mobility prediction for underwater sensor networks. IEEE Trans. Mob. Comput. 2011, 10, 335–348. [Google Scholar] [CrossRef]
- Abramson, N. The ALOHA system—Another alternative for computer communications. AFIPS Conf. Proc. 1970, 37, 281–285. [Google Scholar]
- Kleinrock, L.; Tobagi, F.A. Packet switching in radio channels: Part I—Carrier sense multiple-access modes and their throughput-delay characteristics. IEEE Trans. Commun. 1975, 23, 1400–1416. [Google Scholar] [CrossRef]
- Karn, P. MACA—A new channel access method for packet radio. In Proceedings of the 9th ARRL Computer Networking Conference 1990, London, ON, Canada, 22 September 1990; pp. 1–6. [Google Scholar]
- Bharghavan, V.; Demers, A.; Shenker, S. MACAW: A media access protocol for wireless LANs. In Proceedings of the Conference on Communications Architectures 1994, London, UK, 31 August–2 September 1994; pp. 1–10. [Google Scholar]
- Fullmer, C.L.; Garcia-Luna-Aceves, J.J. Floor acquisition multiple access (FAMA) for packet-radio networks. ACM SIGCOMM Comput. Commun. Rev. 1995, 25, 262–273. [Google Scholar] [CrossRef]
- Chien, T.; Liao, T. Design of secure digital communication systems using chaotic modulation, cryptography and chaotic synchronization. Chaos Solitons Fractals 2005, 24, 241–255. [Google Scholar] [CrossRef]
- Zhou, B.; Huang, K.; Jin, L. A key generation method based on multipath relative delay. Comput. Appl. Res. 2011, 28, 2196–2198. [Google Scholar]
- Zhang, Y.; Wen, T.; Guo, Q. Evaluation method for chaotic synchronization key stream generation algorithm. Comput. Eng. Appl. 2010, 46, 68–70. [Google Scholar]
- Ju, L.; Weng, Y.; Zhao, G. A self-synchronizing chaotic encryption method with time-varying keys. Comput. Sci. 2009, 36, 46–48. [Google Scholar]
- Zhu, H.; Zhang, Y.W. Research on Direct Spread Spectrum Sequence Synchronization Technology for Underwater Acoustic Multi-User Positioning Systems. In Proceedings of the 2025 3rd International Conference on Communication Networks and Machine Learning (CNML25), Nanjing, China, 21–23 February 2025; pp. 348–353. [Google Scholar] [CrossRef]
- Jiang, S. On securing underwater acoustic networks: A survey. IEEE Commun. Surv. Tutorials 2019, 21, 729–752. [Google Scholar] [CrossRef]
- Ardizzon, F.; Diamant, R.; Casari, P.; Tomasin, S. Machine learning-based distributed authentication of UWAN nodes with limited shared information. In Proceedings of the 2022 Sixth Underwater Communications and Networking Conference (UComms), Lerici, Italy, 30 August–1 September 2022; pp. 1–5. [Google Scholar]
- Domingo, M.C. Securing underwater wireless communication networks. IEEE Wirel. Commun. Mag. 2011, 18, 22–28. [Google Scholar] [CrossRef]
- Petrioli, C.; Saturni, G.; Spaccini, D. Feasibility study for authenticated key exchange protocols on underwater acoustic sensor networks. In Proceedings of the 14th International Conference on Underwater Networks & Systems, Atlanta, GA, USA, 23–25 October 2019; pp. 1–5. [Google Scholar]
- Gerasimov, V.; Filozhenko, A.; Komlev, A. Energy Supply of the Hybrid UUV and Information Exchange with the Onshore Control Post During the Service of Underwater Mining Complexes. In Proceedings of the 2024 International Conference on Ocean Studies (ICOS), Vladivostok, Russia, 8–11 October 2024; pp. 1–5. [Google Scholar]
- Zou, D.; Lu, L.; Zhang, W.; Guo, J. A Navigation Method for UUVs under Ocean Current Disturbance Based on Deep Reinforcement Learning. In Proceedings of the 2024 7th International Conference on Advanced Algorithms and Control Engineering (ICAACE), Shanghai, China, 1–3 March 2024; pp. 1165–1168. [Google Scholar]
- Zhao, J.; Wang, T.; Lang, F.; Niu, Y. Mine Detection Method Based on Intensity and Phase Information Using Multi-Temporal ALOS Data. In Proceedings of the IGARSS 2022—2022 IEEE International Geoscience and Remote Sensing Symposium, Kuala Lumpur, Malaysia, 17–22 July 2022; pp. 3397–3400. [Google Scholar]
- Zhang, Y.; Yan, T.; Wang, Y.; Li, Q. Marine Environment Dynamic Monitoring System under Remote Sensing Ecological Index. In Proceedings of the 2024 International Conference on Integrated Circuits and Communication Systems (ICICACS), Raichur, India, 23–24 February 2024; pp. 1–5. [Google Scholar]
- Gambardella, C.; Costa, E.; Miroglio, R.; Nugnes, R.; Giuga, M.; Castelli, F.; Piazza, V.; Garaventa, F.; Faimali, M. Early Warning Systems for Marine Monitoring. In Proceedings of the 2024 IEEE International Workshop on Metrology for the Sea; Learning to Measure Sea Health Parameters (MetroSea), Portorose, Slovenia, 14–16 October 2024; pp. 24–28. [Google Scholar]
- Kolios, A.J. Maintenance Strategy Development for Subsea Cables. In Proceedings of the 2022 Annual Reliability and Maintainability Symposium (RAMS), Tucson, AZ, USA, 24–27 January 2022; pp. 1–7. [Google Scholar]
- Zdorovenin, V. Marine Scientific Research as a New Area of Tension Between States. In Proceedings of the OCEANS ’85—Ocean Engineering and the Environment, San Diego, CA, USA, 12–14 November 1985; pp. 511–514. [Google Scholar]
- Mogeng, X. Research and Application of Key Technologies on Scientific Marine Data Integration, Submission and Credible Sharing. In Proceedings of the 2023 IEEE 14th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 17–18 October 2023; pp. 301–307. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).