Blockchain-Enabled IoT for Rural Healthcare: Hybrid-Channel Communication with Digital Twinning
Abstract
1. Introduction
- We define an architecture and data model for HIoT data that connects rural patients’ data with healthcare providers with integrity provided by a blockchain.
- We introduce a hybrid-channel communication model, allowing HIoT devices to use two communication methods to accommodate healthcare data transmission suitable for rural areas.
- To overcome the transmission limitations on one of the two transmission channels, we incorporate a digital twin to handle data transactions from both of the communication channels and assist with blockchain transaction message reconstruction without sharing private encryption keys.
- We demonstrate the benefits of our approach over the state of the art with a performance analysis based on the real-world constraints of LoRaWAN, a widely used LPWAN technology.
2. Related Work
2.1. Rural Healthcare Monitoring
2.2. LPWAN and LoRaWAN
2.3. Blockchain Systems for Healthcare
2.4. Use Case Definition
- HIoT data must be transmissible over an LPWAN technology that can be feasibly and cost-effectively deployed into rural settings.
- Integrity of data must be preserved through the use of blockchain, allowing lifecycle stages of the data (e.g., creation, storage, and granting of access) to be recorded.
- Patient confidentiality must be maintained, ensuring that persistent data such as those stored on the blockchain do not pose a privacy risk, nor are data transmitted over LPWAN a confidentiality or integrity risk if intercepted or manipulated.
- Mechanisms to provide the above security guarantees should be achieved alongside real-time transmission, avoiding the deferral of actions, such as the creation of transactions, wherever possible.
3. Proposed Model
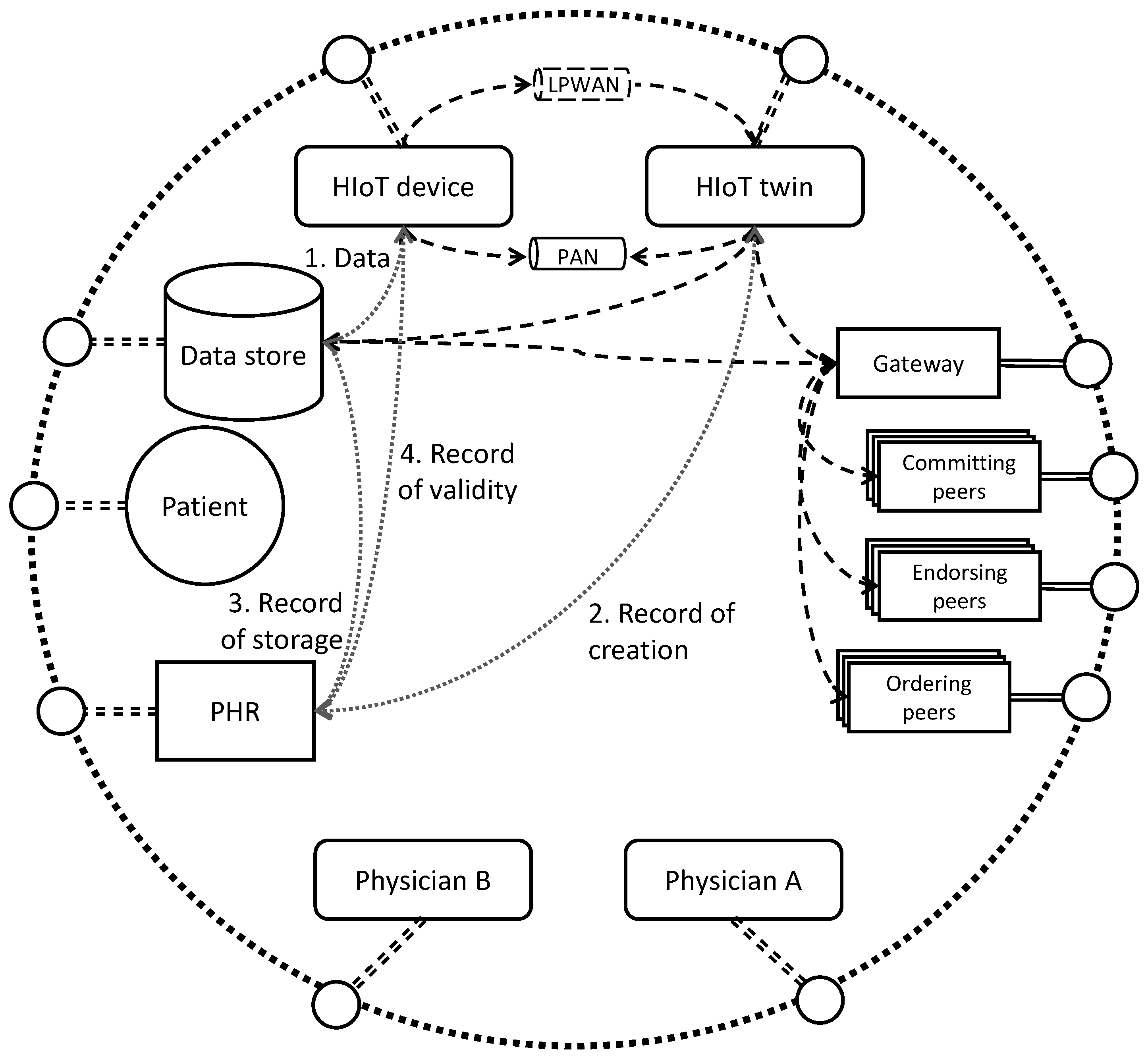
3.1. High-Level Architecture
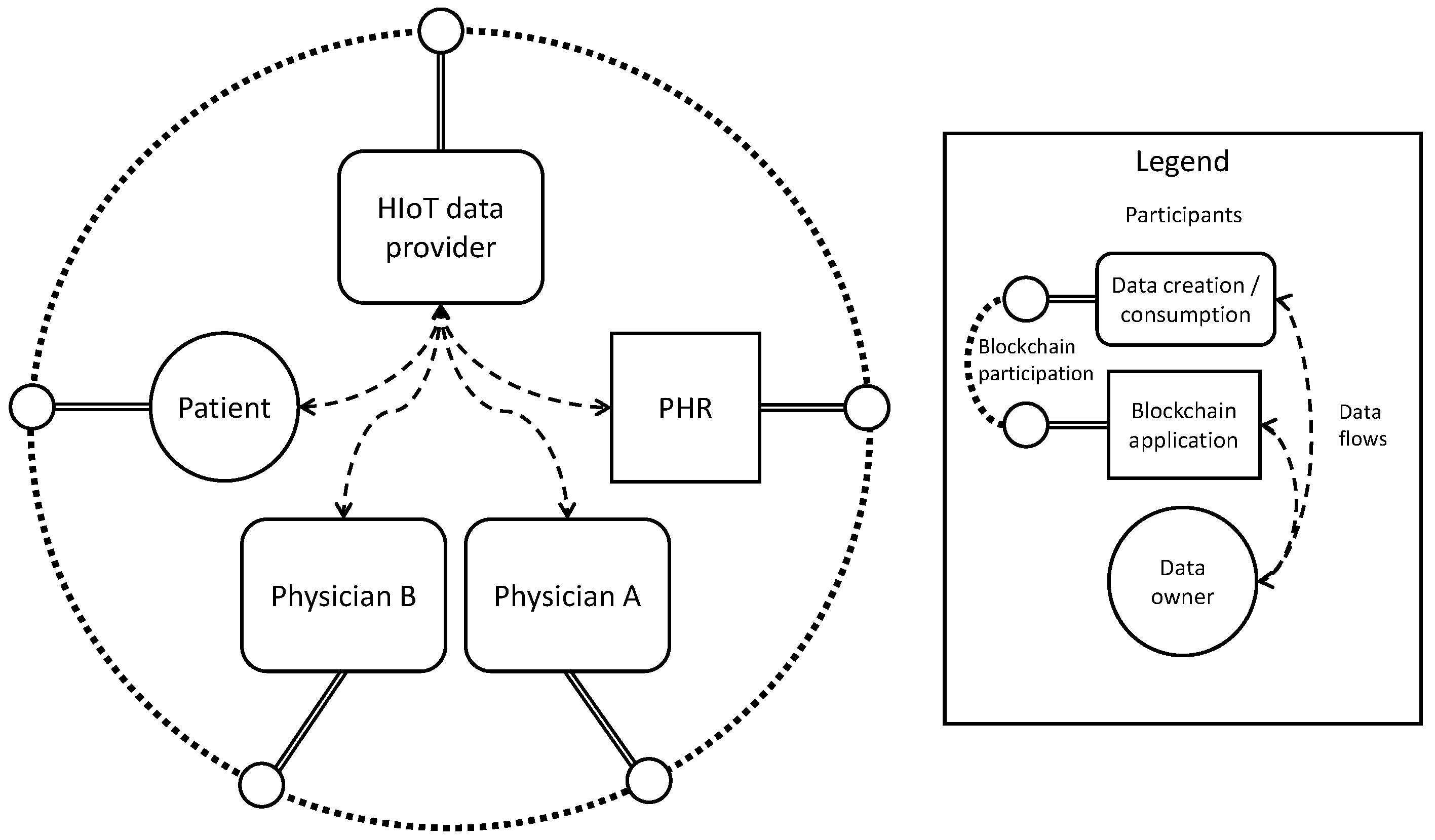
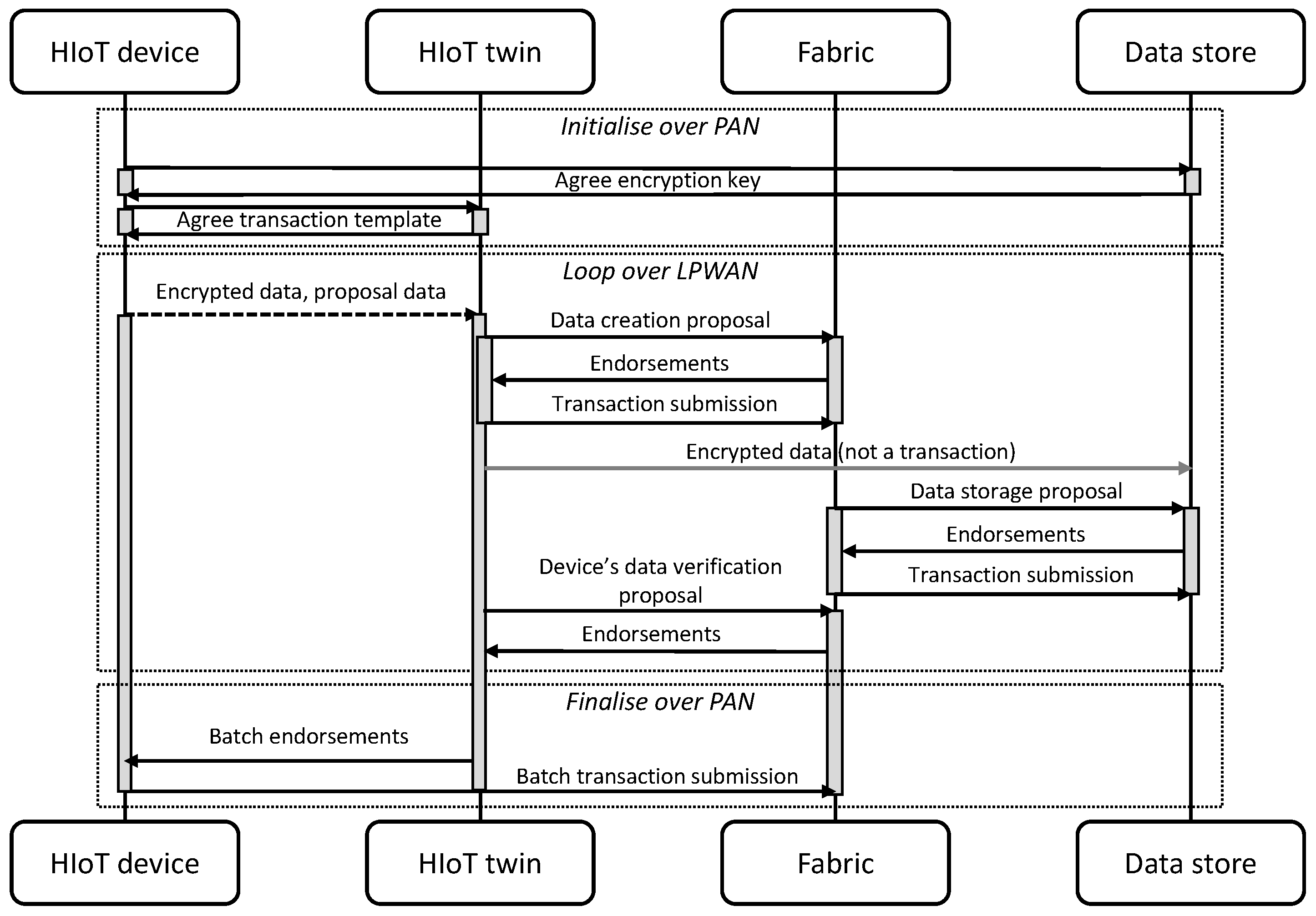
3.2. HIoT Provider Entities and Data Flow
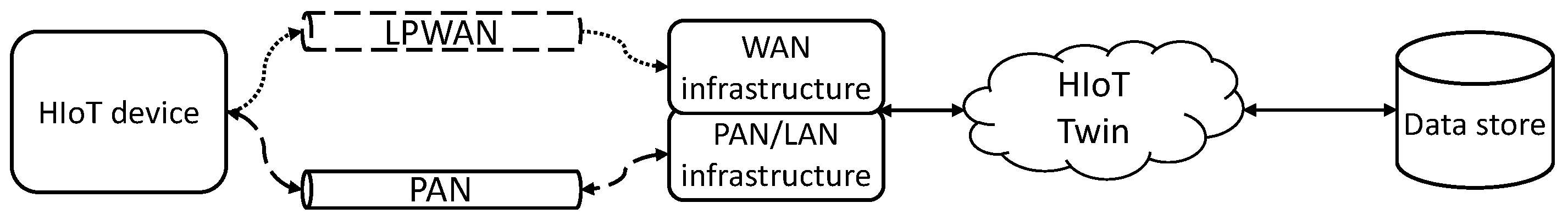
- An HIoT sensor device which is paired with and attached to a patient for a duration of time. The device is expected to be portable and battery powered, for example, a health-monitoring watch or sensor pack.
- A “twin” of the HIoT sensor device used to represent the history and most-recent known state of the sensor device, regardless of connectivity status.
- Two communication methods between the device and its twin: one an LPWAN and one a PAN, where the LPWAN is low-bandwidth and possibly one-way, while the PAN is higher-bandwidth but intermittently available, for example, only when the patient visits a clinic.
- A data store for collected sensor and event data, obtained via the twin over either of the available communication methods.
- LPWAN connectivity is supported by base stations, uplinks to servers and subsequent internet connectivity to relay messages to the twin.
- PAN connectivity is achieved through short-range communication with an internet-connected bridging device, such as a phone over Bluetooth, or a physical docking station with USB or serial link.
3.3. Blockchain Integration
- Pairing between device and patient, whereby data that are generated by a device can be associated with the correct patient.
- Creation of data by the HIoT device to guarantee that a data record was produced by a legitimate, patient-paired source.
- Storage of data by an authorised data store to guarantee the retention of data that were generated by a device.
- Granting access to the data to additional entities to preserve a record of the management of permissions and, where necessary, encryption keys.
3.4. Security
4. Implementation
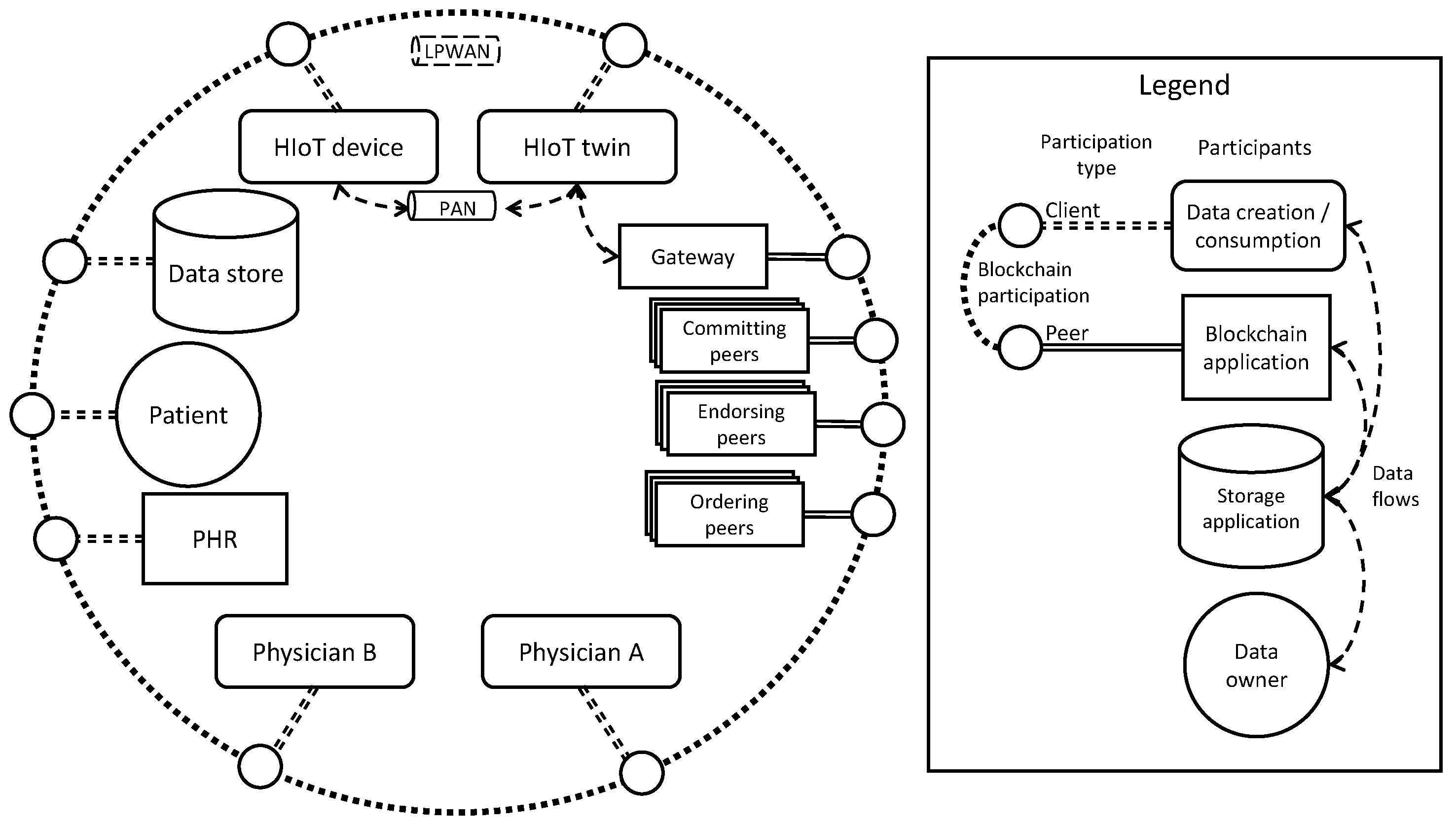
4.1. Blockchain Participation
- Committing peers are responsible for maintaining the ledger state.
- Endorsing peers execute chaincode or smart contracts (the state-changing code executed with a transaction’s input arguments, described in [35]) to simulate a proposed transaction to determine if it would be valid.
- Gateway peers coordinate the dissemination of proposals to endorsing peers and the collection of endorsements on behalf of the proposer.
- Orderer peers construct blocks from endorsed transactions.
- Clients run applications that need to interact with Fabric peers to make transactions.
- Admins are able to perform privileged operations that change the configuration of Fabric and its peers, for example, by adding new organisations to a channel.
4.1.1. Payload Size
4.1.2. Transaction Processing
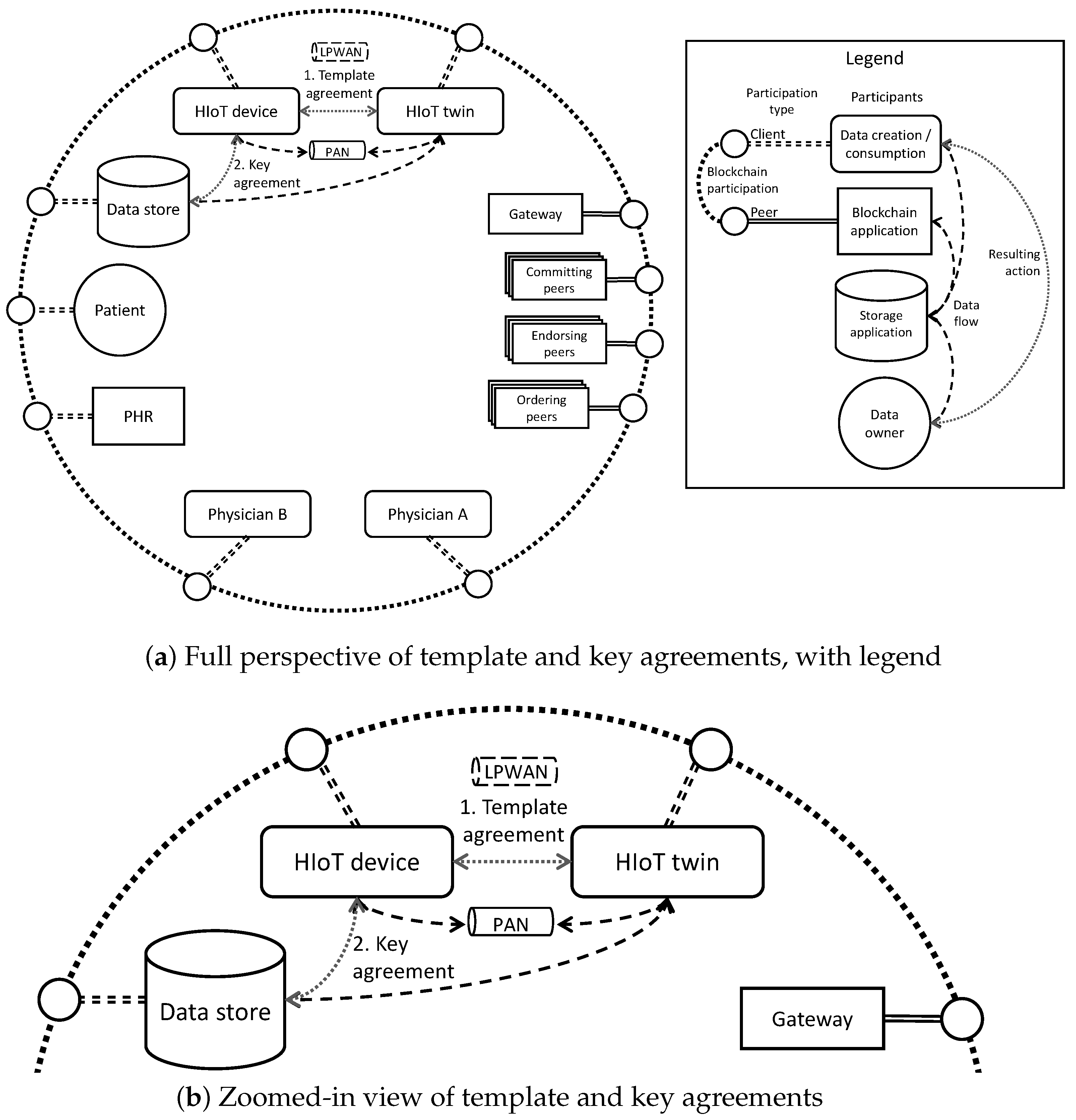
- The twin is responsible for submitting a transaction that creates the data.
- The data store submits a transaction to register the storage of the data.
- The device submits a transaction that verifies the data’s origin.
4.2. Satisfying Security Requirements
4.2.1. Anonymity
4.2.2. Device Key Ownership
4.2.3. Data Keys
4.2.4. Off-Chain Data
4.2.5. Re-Encryption of Data
4.2.6. Missing Data
4.2.7. Forward Secrecy
4.2.8. Post-Quantum Encryption
5. Discussion and Limitations
5.1. Scaling and Integration Considerations
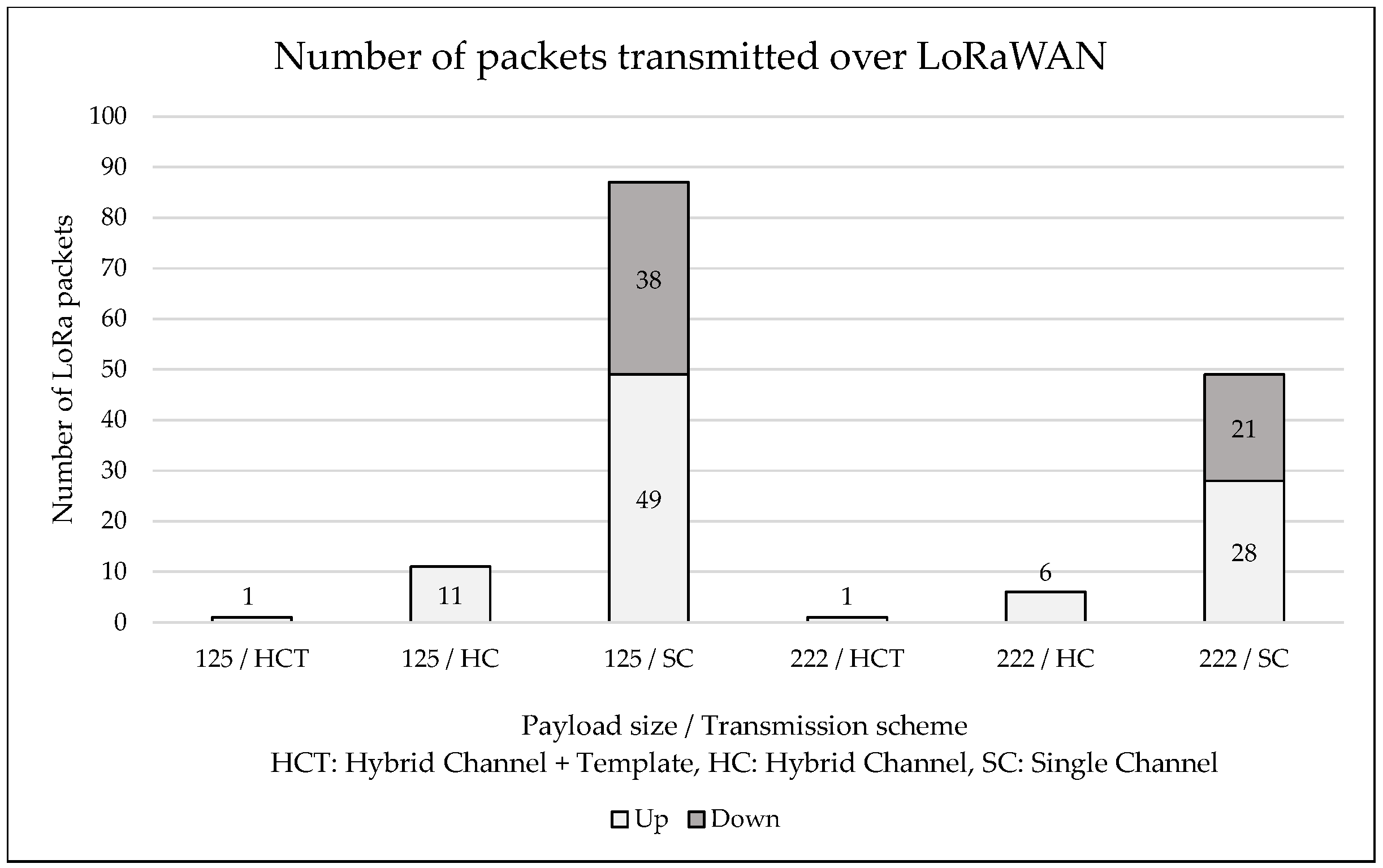
5.1.1. Data Payload Efficiency
5.1.2. Fabric Payload Efficiency
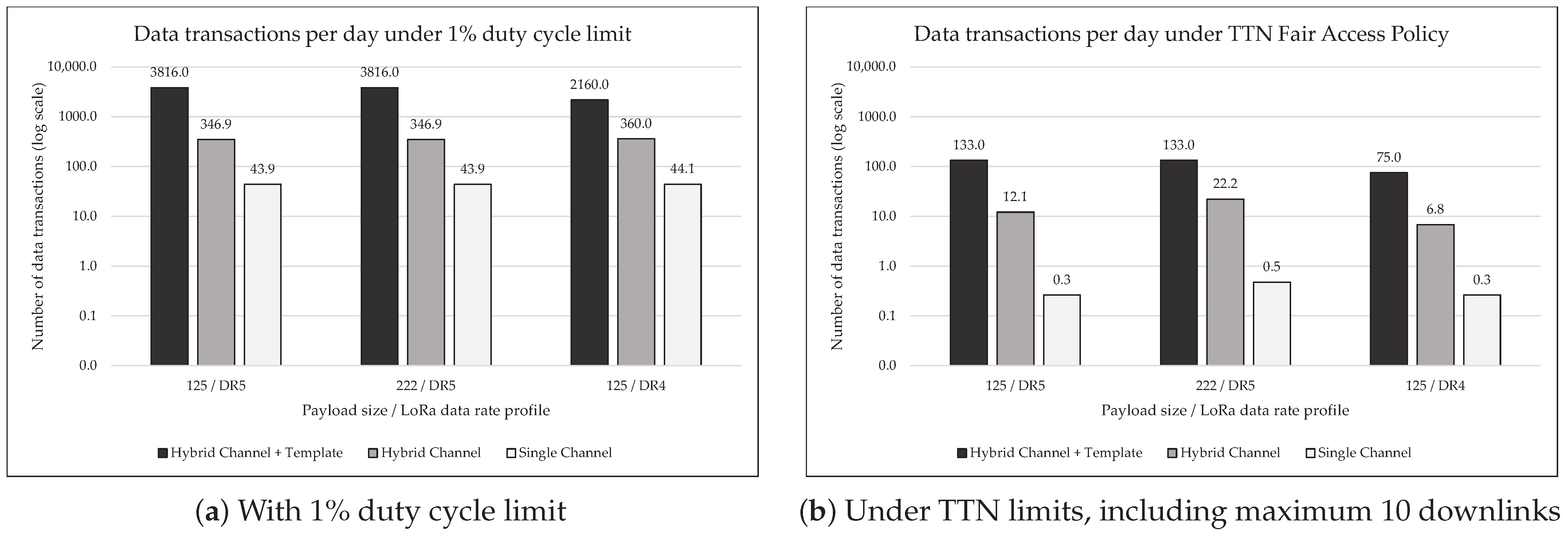
- Hybrid Channel + Template: The full HC2 implementation, where we seek to send the bare-minimum non-templated data over LoRaWAN, relying on PAN, templates and the twin for data reconstruction and interactions with the Fabric gateway.
- Hybrid Channel: A simpler approach that still uses a PAN and twin to minimise LoRaWAN usage but uses a signed proposal generated and sent in full by the device.
- Single Channel: No PAN is used, and therefore messages for Fabric must be sent and received over LoRaWAN, even if a twin assists in transitioning between LoRaWAN and TCP/IP communication to the gateway.
5.1.3. Blockchain Utilisation
5.2. Integration Challenges
6. Conclusions
Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Qadri, Y.A.; Nauman, A.; Zikria, Y.B.; Vasilakos, A.V.; Kim, S.W. The Future of Healthcare Internet of Things: A Survey of Emerging Technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1121–1167. [Google Scholar] [CrossRef]
- Li, J.; Carayon, P. Health Care 4.0: A vision for smart and connected health care. IISE Trans. Healthc. Syst. Eng. 2021, 11, 171–180. [Google Scholar] [CrossRef] [PubMed]
- Dimitrievski, A.; Filiposka, S.; Melero, F.J.; Zdravevski, E.; Lameski, P.; Pires, I.M.; Garcia, N.M.; Lousado, J.P.; Trajkovik, V. Rural healthcare IoT architecture based on low-energy LoRa. Int. J. Environ. Res. Public Health 2021, 18, 7660. [Google Scholar] [CrossRef] [PubMed]
- Dammak, B.; Turki, M.; Cheikhrouhou, S.; Baklouti, M.; Mars, R.; Dhahbi, A. LoRaChainCare: An IoT Architecture Integrating Blockchain and LoRa Network for Personal Health Care Data Monitoring. Sensors 2022, 22, 1497. [Google Scholar] [CrossRef] [PubMed]
- Citoni, B.; Ansari, S.; Abbasi, Q.H.; Imran, M.A.; Hussain, S. Comparative Analysis of an Urban LoRaWAN Deployment: Real World Versus Simulation. IEEE Sen. J. 2022, 22, 17216–17223. [Google Scholar] [CrossRef]
- Sun, Z.; Yang, H.; Liu, K.; Yin, Z.; Li, Z.; Xu, W. Recent Advances in LoRa: A Comprehensive Survey. ACM Trans. Sens. Netw. 2022. [Google Scholar] [CrossRef]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Chenthara, S.; Ahmed, K.; Wang, H.; Whittaker, F. Security and Privacy-Preserving Challenges of e-Health Solutions in Cloud Computing. IEEE Access 2019, 7, 74361–74382. [Google Scholar] [CrossRef]
- Sun, P. Security and privacy protection in cloud computing: Discussions and challenges. J. Netw. Comput. Appl. 2020, 160, 102642. [Google Scholar] [CrossRef]
- Pennino, D.; Pizzonia, M.; Vitaletti, A.; Zecchini, M. Blockchain as IoT Economy Enabler: A Review of Architectural Aspects. J. Sens. Actuator Netw. 2022, 11, 20. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N. BSIS: Blockchain-Based Secure Incentive Scheme for Energy Delivery in Vehicular Energy Network. IEEE Trans. Ind. Inform. 2019, 15, 3620–3631. [Google Scholar] [CrossRef]
- Farooq, M.S.; Suhail, M.; Qureshi, J.N.; Rustam, F.; de la Torre Díez, I.; Mazón, J.L.V.; Rodríguez, C.L.; Ashraf, I. Consortium Framework Using Blockchain for Asthma Healthcare in Pandemics. Sensors 2022, 22, 8582. [Google Scholar] [CrossRef]
- Marbouh, D.; Simsekler, M.C.E.; Salah, K.; Jayaraman, R.; Ellahham, S. A Blockchain-Based Regulatory Framework for mHealth. Data 2022, 7, 177. [Google Scholar] [CrossRef]
- Semwal, N.; Mukherjee, M.; Raj, C.; Arif, W. An IoT based smart e-health care system. J. Inf. Optim. Sci. 2019, 40, 1787–1800. [Google Scholar] [CrossRef]
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT Express 2019, 5, 1–7. [Google Scholar] [CrossRef]
- Xue, H.; Chen, D.; Zhang, N.; Dai, H.N.; Yu, K. Integration of blockchain and edge computing in internet of things: A survey. Future Gener. Comput. Syst. 2023, 144, 307–326. [Google Scholar] [CrossRef]
- Glaessgen, E.; Stargel, D. The digital twin paradigm for future NASA and US Air Force vehicles. In Proceedings of the 53rd AIAA/ASME/ASCE/AHS/ASC Structures, Structural Dynamics and Materials Conference 20th AIAA/ASME/AHS Adaptive Structures Conference 14th AIAA, Honolulu, HI, USA, 23–26 April 2012; p. 1818. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, L.; Yang, Y.; Zhou, L.; Ren, L.; Wang, F.; Liu, R.; Pang, Z.; Deen, M.J. A Novel Cloud-Based Framework for the Elderly Healthcare Services Using Digital Twin. IEEE Access 2019, 7, 49088–49101. [Google Scholar] [CrossRef]
- Sahal, R.; Alsamhi, S.H.; Brown, K.N.; O’Shea, D.; McCarthy, C.; Guizani, M. Blockchain-Empowered Digital Twins Collaboration: Smart Transportation Use Case. Machines 2021, 9, 193. [Google Scholar] [CrossRef]
- Sornin, N.; Yegin, A. LoRaWAN™ 1.1 Specification 2; Technical Report; LoRa Alliance, Inc.: Fremont, CA, USA, 2017. [Google Scholar]
- van Bentem, A. Airtime Calculator for LoRaWAN. Available online: https://avbentem.github.io/airtime-calculator/ttn/as923/125 (accessed on 17 March 2023).
- The Things Network. LoRaWAN Duty Cycle-Fair Use Policy. Available online: https://www.thethingsnetwork.org/docs/lorawan/duty-cycle/#fair-use-policy (accessed on 17 March 2023).
- Baker, S.B.; Xiang, W.; Atkinson, I. Internet of Things for Smart Healthcare: Technologies, Challenges, and Opportunities. IEEE Access 2017, 5, 26521–26544. [Google Scholar] [CrossRef]
- YIN, Y.; Zeng, Y.; Chen, X.; Fan, Y. The internet of things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar] [CrossRef]
- Gordon, W.J.; Catalini, C. Blockchain Technology for Healthcare: Facilitating the Transition to Patient-Driven Interoperability. Comput. Struct. Biotechnol. J. 2018, 16, 224–230. [Google Scholar] [CrossRef] [PubMed]
- Haleem, A.; Javaid, M.; Singh, R.P.; Suman, R.; Rab, S. Blockchain technology applications in healthcare: An overview. Int. J. Intell. Netw. 2021, 2, 130–139. [Google Scholar] [CrossRef]
- Maftei, A.A.; Mutescu, P.M.; Popa, V.; Petrariu, A.I.; Lavric, A. Internet of Things Healthcare Application: A Blockchain and LoRa Approach. In Proceedings of the 2021 International Conference on e-Health and Bioengineering (EHB), Iasi, Romania, 18–19 November 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Ahmad, R.W.; Salah, K.; Jayaraman, R.; Yaqoob, I.; Ellahham, S.; Omar, M. The role of blockchain technology in telehealth and telemedicine. Int. J. Med. Inform. 2021, 148, 104399. [Google Scholar] [CrossRef] [PubMed]
- Adere, E.M. Blockchain in healthcare and IoT: A systematic literature review. Array 2022, 14, 100139. [Google Scholar] [CrossRef]
- Munagala, N.V.L.M.K.; Rani, A.D.; Reddy, D.V.R.K. Blockchain-Based Internet-of-Things for Secure Transmission of Medical Data in Rural Areas. Comput. J. 2022. [Google Scholar] [CrossRef]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Lee, C.C.; Wang, C.C. A Hash Based Remote User Authentication and Authenticated Key Agreement Scheme for the Integrated EPR Information System. J. Med. Syst. 2015, 39, 144. [Google Scholar] [CrossRef]
- Agencia Española de Protección de Datos. Introduction to the Hash Function as a Personal Data Pseudonymisation Technique; Technical Report; European Data Protection Supervisor: Brussels, Belgium, 2019. [Google Scholar]
- Kerrison, S. HIoT Blockchain. Available online: https://gitlab.com/hiot-blockchain (accessed on 23 March 2023).
- Hyperledger. Hyperleder Fabric: Key Concepts. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.4/key_concepts.html (accessed on 20 March 2023).
- Sykes, M.; Yellick, J.; Enyeart, D. Hyperledger Fabric gRPC Service Definitions-Proposal. Available online: https://github.com/hyperledger/fabric-protos/blob/f0d57a53cb997351d8066fd6ab24cb48da1155b2/peer/proposal.proto (accessed on 17 March 2023).
- Hyperledger. Hyperledger Fabric SDK for node.js. Available online: https://hyperledger.github.io/fabric-sdk-node/release-1.4/FabricCAClient.html#enroll__anchor (accessed on 20 March 2023).
- Bouazzouni, M.A.; Conchon, E.; Peyrard, F. Trusted mobile computing: An overview of existing solutions. Future Gener. Comput. Syst. 2018, 80, 596–612. [Google Scholar] [CrossRef]
- Dworkin, M.J. SP 800-38D. Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC; Technical Report; National Institute of Standards & Technology: Gaithersburg, MD, USA, 2007. [Google Scholar] [CrossRef]
- Rescorla, E.; Tschofenig, H.; Modadugu, N. The Datagram Transport Layer Security (DTLS) Protocol Version 1.3. Technical Report; RFC Editor. April 2022. Available online: https://datatracker.ietf.org/doc/html/draft-carpenter-rfc-citation-recs-01#section-5.2 (accessed on 27 April 2023).
- Selander, G.; Mattsson, J.P.; Palombini, F. Ephemeral Diffie-Hellman Over COSE (EDHOC); Internet-Draft draft-ietf-lake-edhoc-19; Internet Engineering Task Force: Fremont, CA, USA, 2023; Work in Progress. [Google Scholar]
- The Things Network. LoRaWAN Security. Available online: https://www.thethingsnetwork.org/docs/lorawan/security/ (accessed on 17 March 2023).
- Sanchez-Iborra, R.; Sánchez-Gómez, J.; Pérez, S.; Fernández, P.J.; Santa, J.; Hernández-Ramos, J.L.; Skarmeta, A.F. Enhancing LoRaWAN Security through a Lightweight and Authenticated Key Management Approach. Sensors 2018, 18, 1833. [Google Scholar] [CrossRef]
- Chen, X.; Lech, M.; Wang, L. A Complete Key Management Scheme for LoRaWAN v1.1. Sensors 2021, 21, 2962. [Google Scholar] [CrossRef]
- Bernstein, D.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef]
- Boutin, C. NIST Selects ‘Lightweight Cryptography’ Algorithms to Protect Small Devices. Available online: https://www.nist.gov/news-events/news/2023/02/nist-selects-lightweight-cryptography-algorithms-protect-small-devices (accessed on 20 March 2023).
- Housley, R.; Polk, T.; Bassham, L. Algorithms and Identifiers for the Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Technical Report; RFC Editor. April 2002. Available online: https://datatracker.ietf.org/doc/html/draft-carpenter-rfc-citation-recs-01#section-5.2 (accessed on 27 April 2023). [CrossRef]
- Gorenflo, C.; Lee, S.; Golab, L.; Keshav, S. FastFabric: Scaling Hyperledger Fabric to 20,000 Transactions per Second. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 455–463. [Google Scholar] [CrossRef]
- Kim, S.; Kwon, Y.; Cho, S. A Survey of Scalability Solutions on Blockchain. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 17–19 October 2018; pp. 1204–1207. [Google Scholar] [CrossRef]
- Górski, T. UML Profile for Messaging Patterns in Service-Oriented Architecture, Microservices, and Internet of Things. Appl. Sci. 2022, 12, 12790. [Google Scholar] [CrossRef]
| Component | Choice | Justification | Limitations | Alternatives |
|---|---|---|---|---|
| Sensor device | Micro-controller | Widely used for IoT-type devices. Relatively low cost. Capable of real-time sensor data acquisition. | Small amount of RAM and flash. Low processing power. | Smartphone or SBC with sensor attachments. |
| LPWAN | LoRaWAN | Multi-km range. Ability to create own infrastructure or use third party. | Limited or no downlinking. Very small uplink payloads and low duty cycles. | Narrow band IoT (NB-IoT), Weightless, Category M1 (Cat M1). |
| PAN | UART | Simplest communication method that can also be encapsulated within appropriate wireless protocols such as Bluetooth Serial Port Profile (SPP). Multi-kilobit to megabit transfer speeds are adequate for bulk data transfer. | Requires cable connection or dock to enable connection to twin. | Wi-Fi (LAN), ZigBee, Bluetooth low energy (BLE), serial peripheral interconnect (SPI), inter-integrated circuit (I2C). |
| Twin | Online deployment | Easier integration with LPWAN and connectivity to blockchain peers. | Link to device requires additional hardware with PAN + Internet capabilities. No offline capabilities. | Deployment onto LoRa gateways. |
| Blockchain | Hyperledger Fabric | Widely used for blockchain applications centring around business logic. Private access model. Certificate-based identities. | Transactions require round-trip communication with initiator. | Ethereum, Hyperledger Iroha. |
| Data store | MQTT historian | Commonly used protocol for IoT data simplifies collection of data. Multiple receivers can be implemented. | Blockchain application logic and data security must be additionally implemented and integrated. | Timescale, InfluxDB. |
| Name | Symbol | Description |
|---|---|---|
| Header fields | Unchanging fields within the message header or headers of components within it. | |
| Sync time | Timestamp at synchronisation | |
| Period | P | Time period stepped between transmissions |
| Identity | Device’s identity (certificate) | |
| Seed | Seed value used for per-transaction nonces | |
| Args | Unchanging chaincode arguments |
| Name | Symbol | Description |
|---|---|---|
| Counter | C | Number of messages since last synchronisation |
| Data | Encrypted sensor data | |
| Signature | Signature of proposal as computed device-side |
| Name | Symbol | Computation | Description |
|---|---|---|---|
| Nonce | Proposal nonce based on seed and counter. | ||
| Timestamp | Timestamp at which data was sent based on counter value | ||
| Data hash | Hash() | A chaincode argument dependent on received encrypted data | |
| Transaction ID | Hash() | A unique ID for the proposed transaction based on nonce and creator. |
| Byte Position | 0–1 | 2–65 | 66–124 | Total |
| Length (bytes) | 2 | 64 | 59 | 125 |
| Purpose | Counter | Signature | Encrypted data | — |
| Confidentiality | Anonymity of data (Section 4.2.1), ownership of keys (Section 4.2.2), data keys (Section 4.2.3), off-chain data (Section 4.2.4), re-encryption (Section 4.2.5), forward secrecy (Section 4.2.7), post-quantum encryption (Section 4.2.8) |
| Integrity | Data keys (Section 4.2.3), post-quantum encryption (Section 4.2.8) |
| Availability | Missing data detection (Section 4.2.6) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kerrison, S.; Jusak, J.; Huang, T. Blockchain-Enabled IoT for Rural Healthcare: Hybrid-Channel Communication with Digital Twinning. Electronics 2023, 12, 2128. https://doi.org/10.3390/electronics12092128
Kerrison S, Jusak J, Huang T. Blockchain-Enabled IoT for Rural Healthcare: Hybrid-Channel Communication with Digital Twinning. Electronics. 2023; 12(9):2128. https://doi.org/10.3390/electronics12092128
Chicago/Turabian StyleKerrison, Steve, Jusak Jusak, and Tao Huang. 2023. "Blockchain-Enabled IoT for Rural Healthcare: Hybrid-Channel Communication with Digital Twinning" Electronics 12, no. 9: 2128. https://doi.org/10.3390/electronics12092128
APA StyleKerrison, S., Jusak, J., & Huang, T. (2023). Blockchain-Enabled IoT for Rural Healthcare: Hybrid-Channel Communication with Digital Twinning. Electronics, 12(9), 2128. https://doi.org/10.3390/electronics12092128








