Abstract
With the rapid development of technologies such as cloud computing, big data, and the Internet of Things (IoT), Software-Defined Networking (SDN) is emerging as a new network architecture for the modern Internet. SDN separates the control plane from the data plane, allowing a central controller, the SDN controller, to quickly direct the routing devices within the topology to forward data packets, thus providing flexible traffic management for communication between information sources. However, traditional Distributed Denial of Service (DDoS) attacks still significantly impact SDN systems. This paper proposes a novel dual-layer strategy capable of detecting and mitigating DDoS attacks in an SDN network environment. The first layer of the strategy enhances security by using blockchain technology to replace the SDN flow table storage container in the northbound interface of the SDN controller. Smart contracts are then used to process the stored flow table information. We employ the time window algorithm and the token bucket algorithm to construct the first layer strategy to defend against obvious DDoS attacks. To detect and mitigate less obvious DDoS attacks, we design a second-layer strategy that uses a composite data feature correlation coefficient calculation method and the Isolation Forest algorithm from unsupervised learning techniques to perform binary classification, thereby identifying abnormal traffic. We conduct experimental validation using the publicly available DDoS dataset CIC-DDoS2019. The results show that using this strategy in the SDN network reduces the average deviation of round-trip time (RTT) by approximately 38.86% compared with the original SDN network without this strategy. Furthermore, the accuracy of DDoS attack detection reaches 97.66% and an F1 score of 92.2%. Compared with other similar methods, under comparable detection accuracy, the deployment of our strategy in small-scale SDN network topologies provides faster detection speeds for DDoS attacks and exhibits less fluctuation in detection time. This indicates that implementing this strategy can effectively identify DDoS attacks without affecting the stability of data transmission in the SDN network environment.
1. Introduction
In today’s rapidly evolving landscape of internet technology, the demand for flexibility and efficiency in network architecture is becoming increasingly prominent. As a significant transformation in the field of networking, Software-Defined Networking (SDN) [1] has emerged. This network architecture is designed based on the separation of the data forwarding plane and the control plane. This separation expands the possibilities for network design and management, consolidating the myriad operations required for network control into a software component known as the SDN controller. By employing centralized control, SDN significantly simplifies the execution of new services, the selection of management policies, and the reconfiguration of networks from a software perspective. Within the SDN network topology, the control plane is connected to the SDN controller through the northbound interface. Upper-layer applications in the control plane can send commands and requests to the SDN controller. The SDN controller, in turn, communicates with the data plane via the southbound interface, sending control commands to network devices within the plane and receiving various status information from them. This network architecture, built by SDN, is a programmable network [2]. Currently, there are many mature network protocols developed based on SDN, with the OpenFlow protocol being one of the most common [3].
Distributed Denial of Service (DDoS) attacks disrupt legitimate user access by sending a large volume of malicious data packets and depleting available resources across compromised nodes [4]. Research has shown that the decoupled control model of SDN allows users and upper-layer applications greater control over the network [5], but it still faces significant threats from DDoS attacks. DDoS attacks target SDN networks by exhausting the flow table caches of switches, depleting controller resources, or blocking link bandwidth within the SDN topology. The increasing threat of DDoS attacks to network operators and internet service providers highlights its status as one of the most challenging issues in the field of network security, with no perfect solution currently available [6]. Particularly with the development of the 5G era, the exponential growth in the number of devices in the network poses a substantial threat to DDoS defense. Therefore, researching how to defend against DDoS in SDN is of great significance.
This paper builds upon our earlier work presented in [7], where we initially introduced a dual-layer DDoS defense strategy leveraging blockchain technology to enhance the security of SDN. While the paper established the feasibility of integrating blockchain and machine learning algorithms in SDN network topologies, it lacked a detailed investigation into the scalability of SDN networks, focusing solely on accuracy as a research metric, which made the evaluation somewhat limited. Furthermore, the original smart contract design exhibited efficiency bottlenecks under high-load scenarios, which affected system performance. In this paper, we further discuss the aforementioned issues, conduct a comparative analysis of our approach with similar algorithms and related strategies, and perform an in-depth study incorporating the latest developments in the field.
Existing SDN DDoS defense technologies have inherent limitations, highlighting the urgent need for new methods to combat DDoS attacks. With the development of new technologies, the widespread application of blockchain technology offers new perspectives for inter-domain collaboration in SDN network topologies [8]. Blockchain technology [9], which integrates a series of existing technologies such as cryptography, Merkle trees, and consensus mechanisms, provides a robust foundation for collaborative defense against DDoS attacks due to its decentralization, data security protection, data sharing capabilities, and distributed nature [10]. Its basic principle is as shown in Figure 1. As shown in the figure, a blockchain is composed of a series of linked blocks, each consisting of a block header and a block body. The block header includes the hash of the previous block, a timestamp, a nonce, and the Merkle root of the transactions. This structure ensures data integrity, traceability, and efficient verification of transactions through the Merkle tree. It enables the automated, distributed sharing of data, facilitating data sharing in trustless networks. Blockchain technology addresses the challenges of data sharing and trust issues among multiple domains [11]. Smart contracts [12] are used to define “protocols executed by various parties”, converting agreements among contract participants into rules written in code. They are reusable, modular, and automatically executed scripts running on the blockchain. Blockchain can leverage smart contracts and its inherent consensus mechanisms to solve cross-domain information exchange challenges and has proven effective in providing decentralized collaboration in trustless network environments. Blockchain technologies, such as Bitcoin, Ethereum, and distributed ledgers, have demonstrated high levels of security and transparency across various fields, and their application in SDN networks for DDoS defense holds significant potential for development [13].
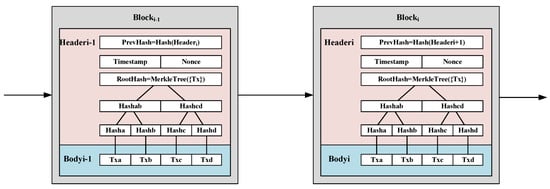
Figure 1.
The principles of basic blockchain.
In the field of DDoS defense for SDN network topologies, existing works mainly focus on two key aspects: (i) ensuring the security of network information storage, and (ii) detecting suspicious attack sources. Among these, the detection of suspicious attack sources often employs learning algorithms, including unsupervised learning and deep learning algorithms. By analyzing datasets, these methods identify suspicious attack addresses for defense, resulting in diverse approaches due to the different algorithms used. For the security of network information storage, unlike traditional information storage approaches, the recent development of blockchain technology has led to attempts to leverage its high-security attributes to address the shortcomings of conventional network information storage solutions [14]. Blockchain is often used to store blacklists and whitelists of attack source addresses. While this method can effectively prevent the forwarding of attack source data, it may still present issues of subjective settings. Therefore, this work proposes a dual-layered strategy combining blockchain and unsupervised learning algorithms. This approach not only ensures security but also proactively detects suspected attack sources. The contributions of this work are as follows:
- To address DDoS attacks, we propose utilizing the high-performance consortium blockchain FISCO BCOS as a container for storing SDN flow tables at the northbound interface of Pox-based SDN switches. We design a cross-domain data flow transmission scheme based on smart contracts, which enhances the security of flow table storage while satisfying the high-frequency access requirements of the SDN controller. This approach ensures that data storage security becomes an integral part of our DDoS attack defense strategy, under the premise of minimizing the impact on the flow table forwarding efficiency within the SDN network topology.
- We consider DDoS attack detection as a binary classification problem, categorizing data transmissions in SDN networks into two classes: benign network flows and malicious network flows. To simulate real-world scenarios as closely as possible, we use the public DDoS dataset CIC-DDoS2019 as data support for attack source data. This dataset contains 77 statistical features based on network flows from 11 different types of DDoS attacks. We propose a composite feature selection method that utilizes Recursive Feature Elimination, Random Forest, and Mutual Information to calculate correlation coefficients and perform correlation ranking on the data. This method determines seven highly correlated data features within a data flow for attack source detection.
- Malicious network flows are divided into two categories: easily detectable and difficult-to-detect. A two-tier defense method is proposed to address both types. The first tier combines time series analysis and the token bucket algorithm to monitor the frequency of network flow access, thereby defending against easily detectable attacks. The second tier employs the Isolation Forest algorithm, an unsupervised machine learning technique, to calculate anomalies based on seven highly correlated data features identified in the data flows stored on the blockchain, thus detecting difficult-to-detect attacks. Compared with similar defense strategies, the proposed method ensures high accuracy while reducing detection time.
In contrast, by leveraging blockchain’s immutability and the automated execution capabilities of smart contracts, we ensure that once a flow record or detection result is written to the blockchain, it cannot be arbitrarily modified, deleted, or canceled by any untrusted management party, including malicious entities or compromised system components. Smart contracts also enable automated responses—such as triggering alerts or updating access policies—based on detection outcomes without human intervention. These capabilities are critical to ensuring the reliability, traceability, and responsiveness of our proposed dual-layer DDoS defense system. Therefore, blockchain is not merely a supplementary technology in our design, but a foundational element for achieving trustworthy and verifiable network security in SDN environments.
2. Related Work
In this section, we present the existing works on DDoS attack defense in SDN networks. Amezcua Valdovinos et al. [15] summarized the SDN network architecture and provided an overview of the research work and challenges in addressing DDoS attacks within the SDN domain. From this review, it is evident that the DDoS defense strategies in SDN networks, inheriting the approaches from traditional DDoS attack defenses, also encompass multiple angles. Here, we categorize them into two main parts: the security of network information storage and the detection of suspicious attack sources.
In enhancing the security of network data storage, blockchain technology has been rapidly developed and integrated to extend traditional network information storage methods. Gao et al. [16] proposed a blockchain-based data sharing framework that combines SDN and proxy re-encryption (PRE) technology to address data security and privacy issues in DDoS attacks. Núñez-Gómez et al. [17] introduced an enhanced distributed resource allocation and access control framework called S-HIDRA, which ensures the integrity and security of data exchange processes by integrating blockchain technology, thereby improving resource management efficiency in distributed systems. Zeng et al. [18] utilized blockchain to establish global trust relationships and proposed a reputation evaluation mechanism to ensure secure routing, though the definition of reputation values may involve some subjectivity. Regarding the detection of suspicious attack sources, Ma et al. [19] proposed a DDoS attack detection algorithm that uses heterogeneous integrated feature selection and Random Forest algorithms. However, the Random Forest algorithm, as a supervised learning algorithm in machine learning, demands significant computational resources. Marvi et al. [20] proposed a method that combines feature selection and extraction using unsupervised machine learning techniques to detect various types of DDoS attacks.
Additionally, considering the attempt to integrate both aspects, Lian et al. [21] proposed FRChain, a blockchain-based SDN data forwarding security scheme that ensures the security of SDN data forwarding by storing flow rules in the blockchain. This scheme uses a voting mechanism among nodes to detect suspicious nodes in the network; however, the voting process is time-consuming and cannot respond to attacks in real time. Jian et al. [22] proposed an information-theoretic DDoS detection method that utilizes smart contracts in the blockchain, where the blockchain serves to record blacklists and whitelists, which may involve some subjective settings. Li et al. [23] introduced the blockCSDN framework for information management and intrusion detection in SDN networks, with the blockchain also playing a role in maintaining blacklists and whitelists, again involving some degree of subjective settings.
Overall, current defenses against DDoS attacks in SDN networks tend to treat data storage security and attack source detection as separate concerns. Existing approaches that attempt to integrate the two are still in preliminary stages and lack detailed explanations on how to overcome the inherent limitations of blockchain technology, such as low read-write efficiency. In light of the current research status, we directly introduce blockchain to store network flow table information in SDN networks and integrate machine learning algorithms for proactive attack source detection. A comparison of related works is given in Table 1.

Table 1.
Comprehensive comparison of DDoS defense strategies in SDN.
3. System Model and Problem Formulation
In this section, we describe the problem, introduce the system model, symbols, and concepts used in this paper, and formally define the problem. For ease of reference, the symbols used in the paper are summarized in Table 2.

Table 2.
Summary of notations.
3.1. Problem Description
The SDN network environment is susceptible to DDoS attacks, which include not only easily detectable attacks like flooding attacks but also more subtle ones. These attacks can occupy resources with malicious packets, disrupt access for legitimate users, exhaust switch flow table caches, deplete controller resources, or congest link bandwidth, posing significant threats to the network’s stability and security. Traditional defense methods still exhibit various shortcomings in addressing the complexity and variability of DDoS attacks. To overcome these challenges, it is crucial to develop a new defense mechanism capable of effectively detecting and mitigating DDoS attacks while ensuring the stability and efficiency of the SDN network. Therefore, a novel double-layered defense strategy integrating blockchain technology and unsupervised learning algorithms is proposed, leveraging the prominent security features and rapid development of blockchain technology.
3.2. System Model
Our proposed strategy for mitigating DDoS attacks is divided into two main parts: (1) the processing of flow table data using blockchain technology, and (2) the DDoS detection strategy. The detection in the second part relies on the storage and processing of data information in the first part. Together, these components form the overall double-layered defense strategy. The structure is illustrated in Figure 2. Both the blockchain and detection algorithm are implemented at the northbound interface of the SDN controller. The SDN controller invokes them to transmit data packets to the switches in the data plane.
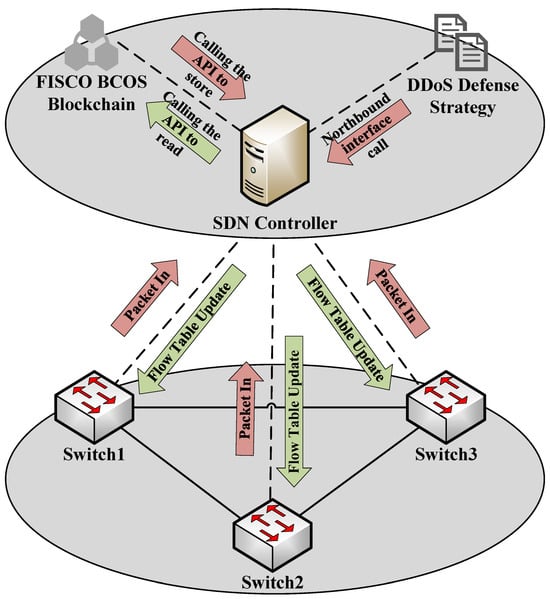
Figure 2.
SDN network architecture with the deployed defense strategy.
3.2.1. The Processing of Flow Table Data Using Blockchain Technology
The northbound interface of the SDN controller interacts with the blockchain. As shown in Figure 2, this interaction through blockchain APIs allows the SDN controller to securely store and manage flow tables. Each SDN controller’s topology is represented as a blockchain, where each node in the blockchain corresponds to a switch in the topology. Smart contracts are deployed on the blockchain to manage the flow tables, ensuring the secure and transparent storage of flow rules. These smart contracts perform several functions, including authorizing the SDN controller, updating local flow table information, and verifying participant access permissions. The decentralized nature of the blockchain provides a secure environment for flow table data, preventing unauthorized access and tampering, thereby enhancing the overall security and reliability of the SDN network. We chose the FISCO BCOS blockchain due to its efficient transaction processing, low latency, high security, and strong support for consortium-based deployments.
Furthermore, the immutability of the blockchain ensures that once flow table entries are recorded, they cannot be tampered with or deleted, effectively preventing malicious modifications or unauthorized overwrites. This property directly enhances the stability and reliability of the SDN control plane, as the controller can always retrieve consistent and verifiable flow rule data even in the event of component failures or malicious attacks.
3.2.2. The DDoS Detection Strategy
The first layer strategy utilizes time series analysis and the token bucket algorithm to detect and mitigate obvious DDoS attacks. This algorithm sets thresholds based on the frequency of certain features (such as source MAC addresses) forwarded within a specified time period, limiting the data forwarding rate from suspicious sources. By continuously reading network flow data stored in the blockchain over a period of time, the frequency of certain features is analyzed to identify potential DDoS attack sources. The token bucket algorithm is then applied to limit the data volume generated by these suspicious sources, ensuring that normal data flow remains unaffected.
Obvious DDoS attacks typically exhibit high traffic volumes and frequent repeated requests from specific sources within a short time frame, making them relatively easy to identify through threshold-based methods. These attacks often rely on overwhelming the network bandwidth or controller processing capacity, resulting in significant and abrupt changes in traffic patterns. In contrast, stealthy or subtle DDoS attacks are characterized by low-rate, distributed, and camouflaged traffic that closely resembles legitimate behavior. These attacks are harder to detect using simple statistical methods and require deeper analysis of flow features and behavioral patterns. To effectively defend against both types of threats, our system adopts a two-layer detection strategy tailored to their respective characteristics.
The second-layer strategy employs a composite feature selection approach composed of the Mutual Information algorithm, Random Forest algorithm, and Recursive Feature Elimination method to preprocess the stored flow information. This process determines the optimal number of data feature values and detection sequence. It then uses the Isolation Forest algorithm, an unsupervised machine learning technique, to detect subtle DDoS attacks. Finally, the token bucket algorithm is applied again to suppress data forwarding from the detected attack source addresses.
3.2.3. Verification System
In this subsection, the validation and evaluation of this strategy are divided into two parts: deployment stability and detection performance. The following sections will define and elaborate on each of these aspects separately.
Deployment Stability of the Strategy: Ensuring the stability of strategy deployment is crucial to prevent interference with the normal operation of the SDN network. We measure this stability using the mean deviation (mdev) of the round-trip time (RTT) of packets. A lower deviation indicates higher stability. The mdev value represents the average deviation of the packet round-trip times. This value is calculated by collecting RTT samples , computing their average, , determining the absolute deviation of each sample from the average, , and then computing the mean of all absolute deviations to obtain the mdev. The calculation formula for this metric is
In terms of scalability, we also tested the stability of strategy deployment. We incrementally increased the number of switches in the SDN network topology, as well as the number of hosts connected to each switch. After each topology change, we recorded the time taken by the SDN controller using our strategy to regulate data transmission within the topology. We used the time required for a ping_all operation as the evaluation metric. The calculation formula for this metric is
Here, represents the total time required for all hosts to ping each other, N is the total number of hosts, and is the time taken for host to successfully ping host . By measuring , we can assess the efficiency and scalability of data transmission regulation by the SDN controller under our strategy. A shorter indicates a more stable system.
In Equation (3), is precision. It represents the proportion of instances identified as positive that are actually positive. A higher precision indicates fewer normal traffic instances are misclassified as abnormal, thereby reducing unnecessary interference. Its calculation formula is
in Equation (3) is recall. It measures the proportion of positive instances that are correctly identified as positive. Recall is used to evaluate the comprehensiveness of the classification model. A higher recall indicates fewer abnormal traffic instances are missed, thereby enhancing the reliability and security of the defense system. Its calculation formula is
The aforementioned validation system clearly measures the usability of the proposed strategy. The detailed validation process is specifically described in the Experimental Results and Discussion section.
3.3. Problem Formulation
This subsection elucidates the dual-layer DDoS detection strategy involved in this paper, providing clear mathematical definitions.
3.3.1. The First-Layer Defense Strategy
The first-layer defense strategy includes the time window algorithm and the token bucket algorithm, which are used to detect and suppress easily detectable attacks. Initially, data modeling involves extracting network traffic features. Suppose we have a flow table dataset containing network traffic information, where each row represents a network flow record. We extract the following features: source MAC address () and timestamp (t).
The time window algorithm is used to analyze the frequency of specific features in network traffic. Within a time window, the algorithm calculates the occurrence frequency of each source MAC address. Define the time window length as T. For the i-th source MAC address (), the frequency of at time t is denoted as . Within the time window T, the frequency is calculated, and the frequency values are accumulated to obtain the total frequency of the time window. The calculation formula for the frequency is
In this context, represents the number of packets from at time t, and represents the total number of packets at time t. After accumulating the frequency values, the total frequency within the time window is obtained:
For any time t, calculate the occurrence frequency of the source MAC address within the time window . Set an anomaly threshold value for the network environment of the SDN topology. If , the packet is considered to originate from a DDoS attack source.
The token bucket algorithm is used to limit the data volume generated by these suspicious attack sources, ensuring that the forwarding of normal data flow is not affected. Define the number of tokens in the bucket at the current time t as , the number of tokens in the bucket at the previous time as , the token generation rate (number of tokens generated per second) as R, the time interval between the current time and the last token bucket update as , and the number of data packets to be forwarded by a certain attack source as . The number of tokens in the token bucket increases over time:
If the number of data packets that need to be forwarded by a certain attack source exceeds the current number of tokens in the token bucket , then some data packets are discarded to ensure that the forwarded data volume does not exceed the number of tokens in the token bucket, such that .
3.3.2. The Second-Layer Defense Strategy
The second-layer defense strategy combines a composite feature selection algorithm and the Isolation Forest algorithm to detect less identifiable DDoS attacks. First, the composite feature selection algorithm preprocesses the network flow information stored in the blockchain to determine the optimal number of data feature values and their detection order. Let the feature set be , where represents the i-th feature. The composite feature selection algorithm calculates the feature importance scores:
Here, represents the weight of the i-th feature selection method, and represents the importance score of feature f according to the i-th feature selection method. To avoid excessive subjectivity in the selection of , a normalization process is used for adjustment. The calculation for the normalized feature value coefficient is
where and represent the maximum and minimum scores of the feature selection methods, respectively.
The final normalized feature importance scores calculated by the composite feature selection algorithm are
The Isolation Forest algorithm is used for anomaly detection. Its basic idea is that anomalies are easier to isolate. The Isolation Forest algorithm constructs multiple random trees (Isolation Trees) to recursively partition the data and compute an isolation score for each sample.
Let the dataset be , where represents the i-th data point. The number of trees is t, the average path length of sample is , the isolation score of sample is , and the isolation score threshold is . The algorithm trains on the dataset using t trees. Each tree randomly selects features and thresholds to recursively partition the dataset. The average path length for each sample is then calculated, representing the number of steps needed to reach a leaf node from the root node. Finally, the isolation score is derived using
where is a normalization constant determined by the dataset size m:
represents the i-th harmonic number:
where is the Euler constant, approximately 0.577. If exceeds the set threshold , is considered an anomaly.
Define the classification threshold . When the isolation score exceeds the threshold , the sample is considered an anomaly; otherwise, it is considered normal:
The classification threshold is determined by calculating the F1 score. First, the Precision and Recall curves are plotted against different threshold values. Then, using the F1 score formula (Equation (3)), the F1 score is calculated for each threshold by iterating through different threshold values. The threshold that corresponds to the highest F1 score is selected as the final classification threshold .
4. Detailed Methodology
This section will provide a detailed overview of the proposed strategy for mitigating DDoS attacks, which is mainly divided into two parts: the handling of flow table data by blockchain and DDoS detection algorithms.Complete workflow of the dual-layer defense mechanism is illustrated in Figure 3.
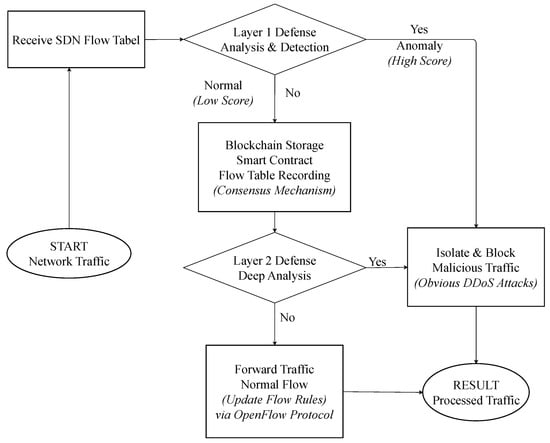
Figure 3.
Complete workflow of the dual-layer defense mechanism.
At the northbound interface of SDN, we deploy the FISCO BCOS consortium blockchain. Inter-domain smart contracts are utilized to collect relevant information about data within periodic intervals. Intra-domain, the first layer of mitigation strategy, detects obvious flood-type DDoS attacks. The second layer of mitigation strategy, incorporating the Isolation Forest algorithm, is used to detect less perceptible DDoS attacks.
4.1. Flow Table Data Processing
Similar to the traditional routing and forwarding process, in SDN network topology, when the data plane sends forwarding data requests to the SDN controller through the southbound interface, the SDN controller also needs to access the flow table to accurately control the data plane to complete a forwarding action. In this work, we deploy the FISCO BCOS [29] consortium blockchain and deploy contracts to it. Then, specific SDN controllers are authorized and authenticated within the blockchain. After successful authentication, the authorized SDN controllers interact with the FISCO BCOS client through blockchain APIs at the northbound interface to store flow table information. The utilization of blockchain in the collaboration process enables transparency and openness. In summary, smart contracts [30] should fulfill the following functions:
- The owner of the smart contract needs to possess the capability to determine whether a participant is authorized to access the blockchain.
- Authorized participants of the contract can update local flow table information.
This work proposes a specific smart contract design. Smart contracts are implemented using the Solidity programming language. Table 3 lists variables that can only be contracted and their corresponding explanations.

Table 3.
Variables in the smart contract.
IsCollaborator(user): The main role of this function takes the account of an external participant (i.e., user) as input to determine whether the external account is authorized and verified. If the participant’s account exists in the smart collaboration contract, it returns true; otherwise, it returns false. This function’s algorithm can be found in Algorithm 1.
| Algorithm 1 IsCollaborator—Collaborator Verification Function. |
Input: user—External participant’s account address Output: Boolean—true if authorized, false otherwise Function: Validates external account’s blockchain access permission
|
In the blockchain, data is stored in string format, with each storage entry represented as a string. The smart contract contains an array to store all these string values. The initial value “0,0” represents the default placeholder for various flow table entry attributes, such as the MAC address and timestamp.
GetKeyOrValue(parameter): This function serves both to retrieve data entries from the storage array at a specified index and to find the index position corresponding to a given value in the storage array of the blockchain. The method accepts a single input parameter, which can be either an unsigned integer or a string. When this method is called, it first checks the type of the input parameter. If the parameter is of type unsigned integer, it checks whether the provided index is within the valid range of the array. If the index is valid, it returns the data entry at the corresponding position in the storage array values. If the index is out of range, it returns an error message indicating that the index is out of range. If the parameter is of type string, the method traverses the storage array values and compares the prefix part of each stored value with the input value. It calculates the fixed length of the input value and then compares it with the prefix part of each stored value. If a match is found, it returns the corresponding index position. If the entire array is traversed without finding a matching value, it returns an error message indicating that the value was not found. Through this combined approach, the function ensures accurate data retrieval and localization in the blockchain, enhancing flexibility in managing data entries. This function’s algorithm can be found in Algorithm 2.
| Algorithm 2 GetKeyOrValue—Bidirectional Data Retrieval Function. |
Input: queryType (string), key (uint) or value (string) Output: Query result—corresponding value or key, error message if not found Function: Enables bidirectional lookup in blockchain storage
|
SetOrUpdateString(index, value): This function serves both to update existing data entries and to add new data entries to the storage array in the blockchain. The method accepts two input parameters: an unsigned integer index, representing the position of the data entry to be updated or where the new data entry should be added, and a string value, representing the new data value. When this method is called, it first checks whether the provided index is within the valid range of the array. If the index is valid, it updates the data entry at the corresponding position in the storage array values with the new value. If the index is out of range, the method adds the new data value to the end of the storage array values. By combining the functionalities of updating and adding data entries, this method ensures that specific data entries stored in the blockchain can be flexibly updated or expanded. This approach maintains data consistency and accuracy, while also simplifying the management of the storage array. The function’s algorithm can be found in Algorithm 3.
| Algorithm 3 SetOrUpdateString—Dynamic Storage Management Function. |
Input: operationType (string), index (uint), newValue (string) Output: Operation result—success or failure message Function: Updates existing entries or appends new data
|
DeleteStringOrClearAll(index, clearAll): This function serves both to delete a specific data entry at a given index and to clear all data entries in the storage array of the blockchain, reinitializing it with a default value. The method accepts two input parameters: an unsigned integer index, representing the position of the data entry to be deleted, and a Boolean clearAll, indicating whether to clear all entries. When this method is called, it first checks the value of clearAll. If clearAll is true, it deletes all entries in the storage array values and reinitializes it with the default value “0,0”. This ensures that the storage array is effectively reset, facilitating scenarios where data clearing and initialization are required. If clearAll is false, the method checks whether the provided index is within the valid range of the array. If the index is valid, it replaces the data entry at the corresponding position with the last element of the array and reduces the array’s length by one, thereby deleting the data entry at the specified index position. Additionally, it triggers a DeleteString event to record the deletion operation. If the index is out of range, it returns an error message indicating that the index is out of bounds. Through this combined approach, the function ensures flexible and efficient management of data entries stored in the blockchain, maintaining data integrity and supporting both targeted deletion and complete reinitialization. This function’s algorithm can be found in Algorithm 4.
| Algorithm 4 DeleteStringOrClearAll—Flexible Data Removal Function. |
Input: index (uint), clearAll (Boolean) Output: Operation result—success or failure message Function: Removes specific entries or reinitializes storage
|
4.2. Detection Strategy
The first-layer defense strategy: The first layer targets easily detectable DDoS attacks by continuously reading network flow data stored in the blockchain over a period and analyzing the frequency of certain features to determine whether to classify a source as a DDoS attack origin. In this work, the source MAC address and the timestamp stored in the blockchain are used as the data features for analysis. Using a time series algorithm, it is determined whether each data’s timestamp falls within a predefined time interval. The source MAC addresses of the data within this interval are read, and if the occurrence of a specific source MAC address within the same interval exceeds the threshold set according to the network environment of the topology, it is considered a suspected DDoS attack source.
The token bucket algorithm is then used to limit the data generated by this attack source by setting the total number of tokens in the bucket and the token issuance rate (one token allows the attack source to forward one piece of data). This ensures that the normal data flow is not affected. The updating principle for the number of tokens in the token bucket is shown in Equation (8). The number of tokens in the token bucket increases each second according to the generation rate R and decreases as data is forwarded. The current token count depends on the token count from the previous second and the number of new tokens generated during that period. When data needs to be forwarded, if the current token count is sufficient, forwarding is allowed; otherwise, forwarding is restricted to prevent DDoS attacks.
The composite feature selection method: The second-layer strategy targets difficult-to-detect DDoS attacks. To enhance the practicality of our approach, we utilize the CIC-DDoS2019 dataset [31] to support the Isolation Forest algorithm [32] used in the second layer, where binary classification is performed on network flow data. This dataset contains 77 statistical features derived from 11 types of DDoS attacks.
Due to limited computational resources, and considering that the proposed method adopts unsupervised learning to identify anomalous behavioral patterns, we focus on SYN-type attacks as a representative subset for modeling. Since different types of DDoS attacks primarily manifest as variations in the feature space, it is not necessary to design distinct detection mechanisms for each attack type. Therefore, the proposed strategy inherently possesses generalization capability across various forms of DDoS attacks, while maintaining algorithm feasibility and alignment with real-world scenarios.
To reduce the time required for binary classification using the Isolation Forest algorithm and to improve detection accuracy, it is essential to determine which data features should be selected during pre-training with the CIC-DDoS2019 dataset. Here, we propose a composite feature selection method that integrates multiple feature selection algorithms. This method aims to enhance both the robustness and the precision of feature selection by leveraging the strengths of different algorithms. We use three algorithms (see Table 4): Mutual Information (MI) [33], Random Forest (RF) [34], and Recursive Feature Elimination (RFE) [35]. The first two are employed to calculate the feature importance scores.

Table 4.
Composite feature selection strategy.
Let represent the set of features, where is the i-th feature. The importance score for each feature using MI is calculated as
where X represents the feature and Y represents the class labels, and is the joint probability distribution of X and Y. The importance score for each feature using RF is determined by the decrease in node impurity weighted by the probability of reaching that node. For a feature , the importance score is calculated as
where T is the number of trees in the forest, is the set of nodes in tree t that split on feature , is the impurity decrease at node n, and is the proportion of samples reaching node n.
The RFE method works by recursively removing the least correlated feature and applying the Isolation Forest algorithm for binary classification. Afterward, we test the accuracy of identifying whether each data flow in the training set is an attack source. Ultimately, the set of data features that yields the highest accuracy using the Isolation Forest algorithm will be selected as the detection features for real-time attack identification. The process can be described as follows:
- Calculate the importance score with MI and RF for each feature in .
- Train a model on the current set of features .
- Remove the feature with the lowest importance score: .
- Repeat steps 2 to 3 until the desired number of features is reached.
To ensure the comparability of importance scores from different algorithms, we normalize the scores using min-max normalization. The specific calculations are provided in Equations (9)–(11). We obtain the composite importance score for a feature f by combining the normalized scores from MI and RF algorithms. We assign weights to each algorithm. Let and be the weights assigned to the MI and RF algorithms, respectively. The composite importance score is calculated as follows:
Based on the composite importance scores, we use the RFE method to recursively remove the least important features, retaining the top k features that yield the highest binary classification accuracy of the Isolation Forest algorithm on the test set after training. The selected feature set is given by
where represents the top k features with the highest scores. This composite feature selection method ensures that the most relevant features are chosen for DDoS attack detection, enhancing the overall accuracy and robustness of the detection algorithm.
The second-layer defense strategy: After the feature selection algorithms have identified the specific features of a flow table entry that need to be analyzed by the Isolation Forest algorithm, during the operation of the SDN network topology, the SDN controller accesses the flow table information stored on the blockchain at specified intervals. This approach aims to minimize the impact of the flow table evaluation process on the normal forwarding efficiency. The flow table information retrieved from the blockchain at each interval is treated as a new test set, and an anomaly score is calculated for each flow table entry.
Since the Isolation Forest algorithm cannot directly perform binary classification, we need to partition the calculated anomaly scores using a threshold. To this end, during the training phase, in addition to using the composite feature selection algorithm to determine which flow data features the Isolation Forest should use for training, we also established the anomaly score threshold calculated by the Isolation Forest algorithm. Scores higher than the threshold are considered normal traffic, while those lower than the threshold are deemed abnormal traffic (since the training set contains only normal traffic). Specifically, this threshold is determined using the precision–recall (PR) curve by calculating the F1 score as a metric to balance precision and recall, thereby evaluating the classification performance under different thresholds. Finally, we select the threshold that maximizes the F1 score as the optimal threshold for dividing anomaly scores into normal and abnormal traffic.
5. Experimental Results and Discussion
In this section, we set up an SDN topology and monitor the ping connectivity between hosts to evaluate the impact of our defense strategy on SDN switch performance. For DDoS attack detection, the first layer of defense can effectively identify flooding attacks that exceed predefined thresholds. To assess the effectiveness of the second-layer defense against more subtle and difficult-to-detect attacks, we simulate these using the CIC-DDoS2019 dataset. Specifically, 70% of the dataset is used for training the detection algorithm employed in the second-layer defense, while the remaining 30% serves as the test set. The test set is stored in batches on the SDN controller’s blockchain to emulate flow table entries within the network topology.
This 70/30 split, commonly adopted in machine learning, provides a balanced trade-off between sufficient training data for robust model learning and adequate testing data for objective evaluation of generalization performance. Within our framework, this setup enables the Isolation Forest algorithm to learn normal traffic patterns effectively, while the test data ensures realistic evaluation under SDN operational conditions. This methodology allows us to assess whether the controller, through the second-layer defense mechanism, can accurately detect anomalous network flows in real time.
5.1. Simulation Environment and Network Topology
This study is conducted on the Ubuntu 20.04 system, using Mininet 2.3.0 [36] as the environment simulation tool for building network topologies. We chose the Pox [37] as the controller for SDN and use Scapy as the traffic generation tool to simulate hosts in the SDN network. In Figure 4, our topology consists of 1 FISCO BCOS blockchain, one Pox controller, 3 OpenvSwitch switches, and 6 hosts. Each switch and 2 hosts form an SDN subnet. The SDN controller serves as a node of the FISCO BCOS blockchain, which is built using Python 3.8.10, deploys smart contracts through the WeBASE component, and compiles them using the Solidity languages [38] to form corresponding application ports. When the SDN topology runs for the first time, switches perform broadcast addressing, and the SDN controller records the flow data sent by switches through their ports (including their original MAC addresses, etc.). This information is stored in the blockchain as flow table information. Subsequent data forwarding prioritizes sending requests to the SDN controller to obtain flow table information in order to complete forwarding actions.
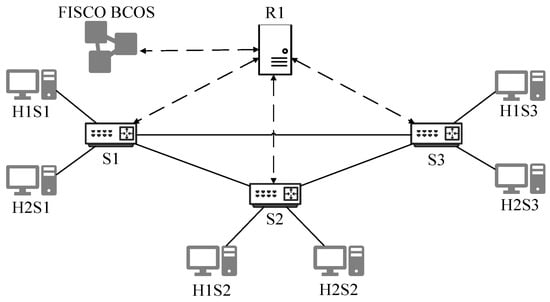
Figure 4.
Software-defined network topology.
5.2. Comparison of Flow Table Data Forwarding with the Original Controller
In this work, we propose a detection and mitigation strategy for DDoS attacks, which mainly affects the normal forwarding process of the controller in the network flow table storage. To assess the extent of this impact, we compare the stability of SDN controllers using our proposed strategy (i.e., the Pox controller integrated with FISCO BCOS blockchain-based flow table storage structure at the northbound interface of the SDN controller) with the original Pox controller that does not use our strategy.
We use the mdev value, representing the mean deviation of round-trip time (RTT) when transmitting data between hosts, as a stability indicator. In the experiments, we conduct 10 sets of comparisons by pinging between two hosts, H1S1 (the host H1 under switch S1) and H2S3 (the host H2 under switch S3), in the same network topology environment. We collect the mdev values from 10 consecutive ping connections between the hosts in each set, resulting in a total of 10 sets of comparisons, and generate a comparison line chart as shown in Figure 5. It is evident that the mdev value of the Pox controller, using blockchain as the flow table storage container, for controlling data transmission in the network topology is generally lower than that of the original Pox controller. The mean mdev value is 0.1122 ms, which is lower than the original Pox’s mean mdev value of 0.1835 ms. The former’s numerical decrease is approximately 38.86% compared with the latter. This is because the strategy employs a consortium blockchain, which is inherently suitable for handling massive data and emphasizes transaction stability. Additionally, our design smart contracts efficiently handle data processing. Therefore, when the SDN controller accesses the blockchain via northbound interfaces, stable access is consistently maintained. As a result, implementing this strategy does not affect normal data forwarding within the topology and may even enhance the stability of network flow transmission to some extent.
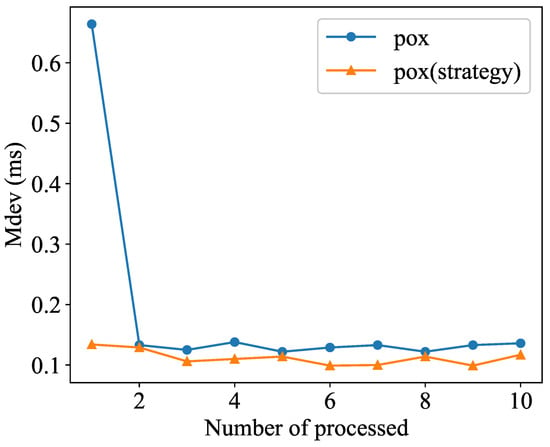
Figure 5.
Line graph of network stream transmission stability.
5.3. Scalability Testing of SDN Network Topology
In practical application scenarios, the SDN network topology often changes continuously according to user requirements. This necessitates that the defense strategies we deploy on the SDN controller maintain operational stability as much as possible. To detect whether our deployed dual-layer defense strategy affects normal flow table forwarding in network topologies of different scales, we use the time required to complete a ping_all command as the evaluation metric. We conducted experiments by incrementally increasing the number of switches and the number of hosts connected to each switch within the network topology. For each configuration change, we measured the time taken by the SDN controller, equipped with our dual-layer defense strategy, to execute the ping_all command. A shorter ping_all time suggests that the defense strategy does not significantly interfere with normal data transmission.
Our experimental setup involved creating linear topologies with varying sizes using Mininet. We systematically increased the number of switches from to and varied the number of hosts per switch from to . For each topology, we compared the ping_all execution time of our modified SDN controller against that of the original controller without any defense mechanisms.
As illustrated in Figure 6, when the number of switches increases from 1 to 3 and the number of hosts connected to each switch also grows, the time taken by the SDN controller deploying our strategy to execute a ping_all operation remains within 3% of that taken by the original Pox controller. The difference is minimal. In the experimental scenario with three switches, a slight decrease in the average one-hop Ping latency was observed when the number of hosts increased from 10 to 12, which deviates from the general trend of increasing latency with a growing number of hosts in other configurations. This anomaly can be primarily attributed to the flow table learning and caching mechanisms of the SDN controller. As the number of communicating host pairs increases, the controller incrementally installs flow entries, leading to a higher flow table hit rate and thus reducing the frequency of subsequent Packet-In requests and overall forwarding latency. Moreover, given the relatively small topology and absence of network congestion at this stage, the system may have entered a transient performance optimization state. It is worth noting that this phenomenon is likely incidental rather than universal, and further studies are needed to assess its consistency and applicability. As the primary purpose of this experiment is to compare forwarding performance with the original controller, an in-depth investigation is beyond the scope of this work.
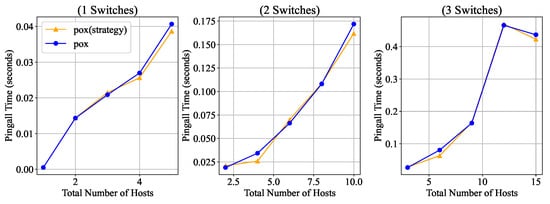
Figure 6.
Comparison of Pingall Time for SDN topologies with 1 to 3 switches.
As illustrated in Figure 7, when the number of switches increases from 4 to 6, even though the number of hosts under each switch continues to rise, the SDN controller with our strategy maintains good forwarding performance. Due to the stable read characteristics of the blockchain, it even outperforms the original POX controller to some extent, effectively managing up to 30 hosts.
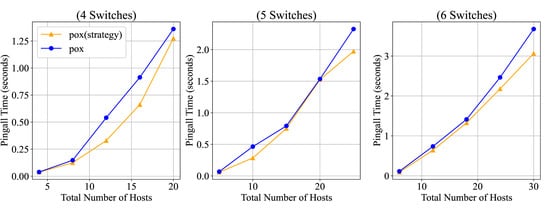
Figure 7.
Comparison of Pingall Time for SDN topologies with 4 to 6 switches.
As illustrated in Figure 8, when the number of switches increases from 7 to 9, starting from 8 switches, the time required by our strategy-deployed controller to execute the ping_all operation begins to exceed that of the original POX controller.
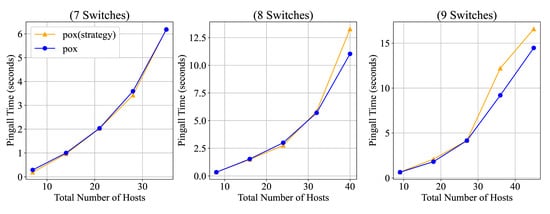
Figure 8.
Comparison of Pingall Time for SDN topologies with 7 to 9 switches.
In summary, scalability testing leads to the following conclusions: in small- to medium-scale SDN network topologies, the blockchain-based flow table protection architecture can maintain high forwarding efficiency and system stability, in some cases even outperforming traditional controller-based approaches. However, in large-scale network topologies, while blockchain storage offers enhanced data security and transparency, its performance may be affected as the topology size increases—particularly when the number of switches ranges from one to seven—due to increased access latency and storage bottlenecks. Therefore, for large-scale SDN deployments, it is necessary to further optimize the blockchain storage architecture by adopting more efficient blockchain technologies or integrating additional optimization strategies to ensure stable system performance under large-scale conditions.
5.4. DDoS Attack Detection Accuracy
Before detecting the accuracy, it is crucial to set certain parameters in our algorithm to ensure that the binary classification performed by the entire algorithm model on the dataset achieves optimal results. The primary parameters include the number of trees in the Isolation Forest algorithm and the data features required for training the algorithm. The number of trees (n_estimators) determines the number of isolation trees in the model. A higher number of trees can enhance the model’s stability and accuracy as they more comprehensively capture the anomaly patterns in the data. Data features are meaningful information extracted from network traffic, which help the model distinguish between normal and anomalous traffic. Selecting appropriate features can significantly improve the model’s performance.
Initially, we removed data with a large number of missing values that could significantly impact the training results, reducing the number of features in the dataset to 63. Then, we used a composite feature selection algorithm to calculate the correlation coefficient values for each feature in the dataset. These features were then ordered in descending order based on their coefficient values. The Isolation Forest was trained sequentially according to this order, and in each iteration, the feature with the lowest coefficient value was removed. After each round of training, the accuracy was tested using a test set. The set of feature values and the number of trees corresponding to the highest accuracy constitute the optimal parameters required for our model.
As shown in Figure 9, the X-axis represents the number of top features (i.e., the number of data features arranged in descending order of their correlation coefficients). When the number of trees is set to 184, and the top 7 features are selected, our strategy achieves optimal performance. Therefore, we choose this set of values as the parameters for our strategy model (the data in the figure only includes the portion of the chart containing the optimal data; in the actual data, the number of trees was incremented by a step size of 1, but due to the large scale of the data, a step size of 23 was used for plotting).
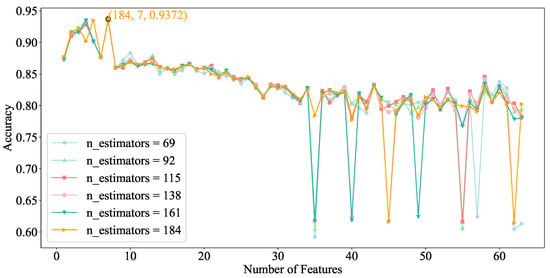
Figure 9.
Comparison of algorithm model parameters.
By applying our composite feature selection algorithm to the dataset, we obtained seven highly correlated features listed in Table 5, in sequential order. Since CIC-DDoS2019 is a publicly available dataset that closely mimics real-world scenarios, the significant features derived from this dataset will substantially aid in identifying network traffic patterns in real-world situations. The first column of the table lists the feature names, while the second column describes the role of each feature.

Table 5.
Features selected by the proposed method.
The features include the ACK Flag Count, which indicates the stability of connections by counting the number of packets with the ACK flag set; the Avg Packet Size, representing the average size of packets in a flow and helping to identify unusual patterns; the Subflow Fwd Bytes, measuring the total bytes forwarded in subflows from client to server; the Total Backward Packets, counting the number of packets sent from server to client to assess communication balance; the Idle Mean, indicating the average idle time between packets and reflecting network activity sparsity; the Flow Packets/s, measuring the number of packets transmitted per second to detect high-frequency communication; and the Packet Length Mean, representing the average length of packets and distinguishing different communication patterns. Together, these features enhance the detection and analysis of network traffic, providing a robust mechanism for identifying benign and malicious activities.
In pattern recognition and information retrieval, binary classification metrics based on true positives (TP), true negatives (TN), false positives (FP), and false negatives (FN) help measure system performance. In our study on DDoS attack detection, we utilized the SYN subset of the CIC-DDoS2019 public dataset. We trained our model on 70,336 instances of normal traffic and tested it on 907 instances of mixed normal and abnormal traffic. These metrics are crucial for evaluating our model’s performance in correctly identifying DDoS attacks. TP represents correctly identified normal traffic, while TN represents correctly identified anomalous traffic, FP represents normal traffic wrongly identified as anomalous, while FN represents anomalous traffic wrongly identified as normal. These parameters are used to calculate accuracy (ACC), a key metric for performance evaluation. The accuracy of correctly detecting attacks is defined as follows:
Based on Equation (20), we separately calculate and compare the accuracy of the final DDoS detection strategy after employing Pearson’s correlation coefficient, kernel methods, distance correlation, Spearman’s correlation coefficient, Lasso technique.
The Pearson correlation coefficient measures the linear relationship between two variables x and y. It is defined as
In this formula, and represent individual sample points, and are the mean values of the samples, and n is the number of observations. The absolute value is taken to ensure the score is non-negative.
Kernel methods, such as the Radial Basis Function (RBF) kernel, project data into a higher-dimensional space to facilitate classification. The RBF kernel is defined as
In Equation (22), and are data points, and is a parameter that determines the width of the kernel. The score is the sum of the kernel similarities across all data points.
Distance correlation measures both linear and nonlinear associations between two variables. It is given by
In Equation (23), represents the distance covariance between the variables X and Y, which captures the extent of dependency between them. The absolute value is taken to ensure that the score is non-negative.
The Spearman correlation coefficient is a measure of rank correlation, assessing how well the relationship between two variables can be described by a monotonic function. It is calculated as
In Equation (24), is the difference between the ranks of corresponding values, and n is the number of observations. The absolute value is taken to ensure the score is non-negative.
The Lasso (Least Absolute Shrinkage and Selection Operator) technique is used for regression and feature selection. The objective function for Lasso regression is
In Equation (25), is the response variable, is the vector of predictor variables, represents the coefficient vector, is the regularization parameter, and n is the number of observations. The score is obtained by minimizing the loss function, which consists of the residual sum of squares and an norm regularization term to control model complexity and prevent overfitting. The coefficients are estimated using the Lasso technique.
Our composite feature selection algorithm as data preprocessing steps, as shown in Table 6. From the table, it is evident that the composite feature selection algorithm used in this strategy achieves a final accuracy of 97.66%, significantly ensuring the accuracy of DDoS detection in the final strategy. This is attributed to the strategies proposed in this work, especially the effective feature selection of composite feature values utilized in detecting network flow data in the second-tier strategy, as well as the Isolation Forest algorithm’s effective binary classification of data.

Table 6.
Comparison of prediction accuracy under different feature selection algorithms.
In addition to accuracy, inspired by the paper in [39], we further compare the recall, precision, and F1 scores of various feature selection algorithms to comprehensively evaluate their performance in detecting DDoS attacks.
Precision: We evaluate the precision of our proposed composite feature selection method compared with other feature selection algorithms. Precision measures the proportion of true positive predictions among all positive predictions. It is an important metric in the context of DDoS attack detection, as it reflects the algorithm’s ability to accurately identify DDoS attack instances without falsely classifying normal instances as attacks.
The precision values for each method are as shown in Figure 10: our proposed method achieves a precision of 0.9766, while Lasso, Pearson, Spearman, Kernel, and Distance correlations achieve precisions of 0.892, 0.880, 0.857, 0.823, and 0.777, respectively. Our proposed method’s precision is notably higher than the other methods, demonstrating its strong ability to accurately identify DDoS attack instances while minimizing false positives.
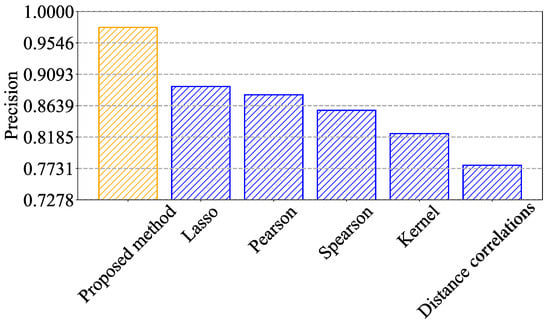
Figure 10.
Precision comparison of feature selection methods.
Recall: We evaluate the recall of our proposed composite feature selection method compared with other feature selection algorithms. Recall, also known as sensitivity or true positive rate, measures the proportion of actual positives that are correctly identified. It is a critical metric in the context of DDoS attack detection, as it reflects the algorithm’s ability to correctly identify DDoS attack instances among all actual attack instances.
The recall values for each method are as shown in Figure 11: our proposed method achieves a recall of 0.873, while Lasso, Pearson, Spearman, Kernel, and Distance correlations achieve recalls of 0.883, 0.875, 0.872, 0.873, and 0.909, respectively. Although our proposed method’s recall is slightly lower than some of the other methods, it demonstrates a strong ability to correctly identify a significant proportion of DDoS attack instances, reflecting its robustness in real-world scenarios. This slight decrease in recall is primarily due to the conservative nature of the Isolation Forest algorithm used in the second-layer defense strategy. Since the model is trained exclusively on normal traffic to simulate unsupervised conditions, it prioritizes minimizing false positives to maintain high precision, which can occasionally lead to a small number of false negatives. Additionally, to avoid performance overhead in real-time SDN environments, our detection threshold is calibrated to favor stability and general applicability over overly aggressive detection. This trade-off ensures that the defense system remains reliable and efficient under practical network conditions.
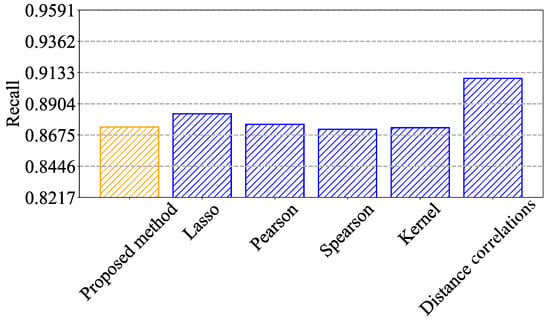
Figure 11.
Recall comparison of feature selection methods.
F1 score: The final metric we evaluate is the F1 score, which is the harmonic mean of precision and recall. The F1 score is an important measure because it balances the trade-off between precision and recall, providing a single metric that accounts for both false positives and false negatives. This is particularly crucial in DDoS attack detection, where both accurately identifying attacks (high recall) and avoiding false alarms (high precision) are important.
The F1 scores for each method are as shown in Figure 12: our proposed method achieves an F1 score of 0.922, while Lasso, Pearson, Spearman, Kernel, and Distance correlations achieve F1 scores of 0.886, 0.877, 0.865, 0.846, and 0.838, respectively. Our proposed method’s F1 score is the highest, indicating that it provides the best balance between precision and recall compared with the other methods.
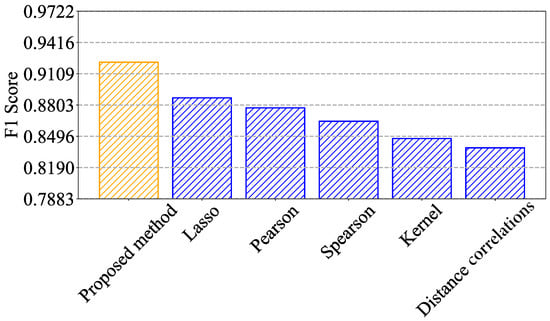
Figure 12.
F1 Score comparison of feature selection methods.
5.5. Comparison of Anomalous Network Flow Determination Time with Similar Defense Strategies
Following the preceding discussions, we have detailed the fundamental architecture of our defense strategy, the stability of its deployment, the selection of data features for anomaly detection, the determination of algorithm parameters, and the accuracy of detection. Building on this foundation, this subsection presents a comparative analysis of the analysis time for anomalous values of our dual-layer defense strategy against other similar defense strategies referenced in this paper. Specifically, we compare our approach with two DDoS defense strategies that employ machine learning or deep learning techniques: Real-time Detection [19] and an Augmented k-means Clustering Approach [20].
To ensure the fairness of the experimental results, we uniformly utilize the SDN network topology developed in this study and employ the CIC-DDoS2019 dataset as the data support for simulating real network traffic. During the data preprocessing phase, we apply our composite feature selection method to calculate the correlation coefficients of all data features. The dataset is then divided into training and testing sets, and the three strategies are trained and tested over multiple iterations. In each training round, the number of selected features is progressively reduced, starting with those having the lowest correlation coefficients. This approach minimizes potential discrepancies caused by the differing feature selection methods of the three strategies. Finally, we compare the time consumed by each strategy for determining the same test set after training with the same number of selected data features.
As illustrated in Figure 13, the Real-time Detection strategy employing the Random Forest algorithm generally incurs longer processing times than the other two strategies. In contrast, our dual-layer defense strategy exhibits processing times that are comparable to the defense strategy utilizing the k-means algorithm. However, our defense strategy demonstrates greater stability in anomaly determination times, with fewer significant fluctuations observed. Consequently, when detection accuracies are similar, our strategy requires less determination time compared with similar strategies and offers enhanced stability. This effectively highlights the superior defensive performance of our strategy within small-scale SDN network topologies.
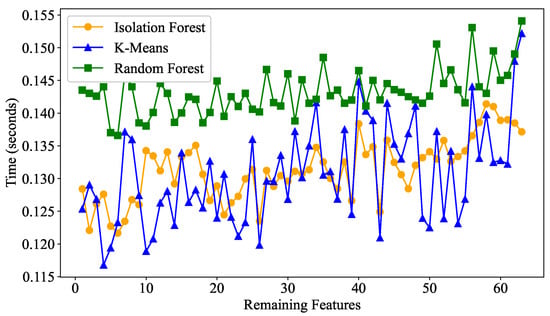
Figure 13.
Comparison of anomaly detection times for different DDoS defense strategies in small-scale SDN networks.
6. Conclusions
This research proposes a dual-layer defense mechanism that integrates blockchain technology and unsupervised learning techniques to mitigate DDoS attacks in Software-Defined Networking (SDN) environments. The strategy is designed to simultaneously address two critical aspects of SDN security: reliable flow table management and accurate anomaly detection. On one hand, blockchain and smart contracts are employed to securely manage the storage and access of flow table entries, ensuring integrity, traceability, and protection against tampering or unauthorized modifications. On the other hand, a dual-layer detection framework based on unsupervised learning—featuring composite feature selection and the Isolation Forest algorithm—enables timely and accurate identification of both obvious and subtle DDoS attack patterns. Experimental results demonstrate that the proposed strategy achieves high detection accuracy while maintaining network stability under various traffic loads and attack intensities. Future research will explore lightweight blockchain mechanisms and sharding to improve storage efficiency, as well as incorporate federated or reinforcement learning to further enhance detection performance and scalability in real-world SDN deployments. Additionally, more diverse DDoS datasets beyond CIC-DDoS2019 will be introduced to validate the robustness and generalizability of the proposed strategy across different network environments.
Author Contributions
Conceptualization, S.P. and Z.S.; methodology, S.P.; software, S.P.; validation, S.P., J.T. and X.Z.; formal analysis, S.P.; investigation, S.P.; resources, Z.S.; data curation, S.P.; writing—original draft preparation, S.P.; writing—review and editing, J.T. and S.C.; visualization, S.P.; supervision, Z.S.; project administration, Z.S. and S.C.; funding acquisition, Z.S. and S.C. All authors have read and agreed to the published version of the manuscript.
Funding
This paper was supported by Project of Software Technology Innovation Research and Industrialization in Fujian Province, Fujian Provincial Department of Industry and Information Technology Letter Software, China ([2024] No. 488), Project of Industry-University-Institute Cooperation in Colleges and Universities in Fujian Province, Fujian Provincial Department of Science and Technology, China (No. 2024H6007), Project of Industry-University-Institute Joint Innovation in Colleges and Universities in Fujian Province, Fujian Provincial Department of Science and Technology, China (No. 2024H6030), Industry-Research Project from Network Communication Company, China (No. KH230139A, NO. KH240131A).
Data Availability Statement
The data used in this study are available from the CIC-DDoS2019 dataset, which is publicly accessible.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Nisar, K.; Jimson, E.R.; Hijazi, M.H.A.; Welch, I.; Hassan, R.; Aman, A.H.M.; Sodhro, A.H.; Pirbhulal, S.; Khan, S. A survey on the architecture, application, and security of software defined networking: Challenges and open issues. Internet Things 2020, 12, 100289. [Google Scholar] [CrossRef]
- Luo, S.; Wu, J.; Li, J.; Pei, B. A defense mechanism for distributed denial of service attack in software-defined networks. In Proceedings of the 2015 Ninth International Conference on Frontier of Computer Science and Technology, Dalian, China, 26–28 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 325–329. [Google Scholar]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Kaur, P.; Kumar, M.; Bhandari, A. A review of detection approaches for distributed denial of service attacks. Syst. Sci. Control Eng. 2017, 5, 301–320. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2316–2330. [Google Scholar] [CrossRef]
- Kaur, S.; Sandhu, A.K.; Bhandari, A. Investigation of application layer DDoS attacks in legacy and software-defined networks: A comprehensive review. Int. J. Inf. Secur. 2023, 22, 1949–1988. [Google Scholar] [CrossRef]
- Tian, J.; Shu, Z.; Chen, S.; Xie, H.; Liu, X.; Qiu, C. Enhanced DDoS Defense in SDN: Double-Layered Strategy with Blockchain Integration. In Proceedings of the 2024 IEEE the 13th International Conference on Communications, Circuits, and Systems (ICCCAS 2024), Xiamen, China, 10–12 May 2024; pp. 380–384. [Google Scholar]
- Latah, M.; Kalkan, K. When SDN and blockchain shake hands. Commun. ACM 2022, 65, 68–78. [Google Scholar] [CrossRef]
- Saha, S.; Chattaraj, D.; Bera, B.; Kumar Das, A. Consortium blockchain-enabled access control mechanism in edge computing based generic Internet of Things environment. Trans. Emerg. Telecommun. Technol. 2021, 32, e3995. [Google Scholar] [CrossRef]
- Abou El Houda, Z.; Hafid, A.; Khoukhi, L. Co-IoT: A collaborative DDoS mitigation scheme in IoT environment based on blockchain using SDN. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Chattaraj, D.; Saha, S.; Bera, B.; Das, A.K. On the design of blockchain-based access control scheme for software defined networks. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 237–242. [Google Scholar]
- Abuhashim, A.; Tan, C.C. Smart contract designs on blockchain applications. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–4. [Google Scholar]
- Giotis, K.; Apostolaki, M.; Maglaris, V. A reputation-based collaborative schema for the mitigation of distributed attacks in SDN domains. In Proceedings of the NOMS 2016—2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 495–501. [Google Scholar]
- Wani, S.; Imthiyas, M.; Almohamedh, H.; Alhamed, K.M.; Almotairi, S.; Gulzar, Y. Distributed denial of service (DDoS) mitigation using blockchain—A comprehensive insight. Symmetry 2021, 13, 227. [Google Scholar] [CrossRef]
- Valdovinos, I.A.; Pérez-Díaz, J.A.; Choo, K.K.R.; Botero, J.F. Emerging DDoS attack detection and mitigation strategies in software-defined networks: Taxonomy, challenges and future directions. J. Netw. Comput. Appl. 2021, 187, 103093. [Google Scholar] [CrossRef]
- Gao, Y.; Chen, Y.; Hu, X.; Lin, H.; Liu, Y.; Nie, L. Blockchain based IIoT data sharing framework for SDN-enabled pervasive edge computing. IEEE Trans. Ind. Inform. 2020, 17, 5041–5049. [Google Scholar] [CrossRef]
- Núñez-Gómez, C.; Carrión, C.; Caminero, B.; Delicado, F.M. S-HIDRA: A blockchain and SDN domain-based architecture to orchestrate fog computing environments. Comput. Netw. 2023, 221, 109512. [Google Scholar] [CrossRef]
- Zeng, Z.; Zhang, X.; Xia, Z. Intelligent blockchain-based secure routing for multidomain SDN-enabled IoT networks. Wirel. Commun. Mob. Comput. 2022, 2022, 5693962. [Google Scholar] [CrossRef]
- Ma, R.; Wang, Q.; Bu, X.; Chen, X. Real-Time Detection of DDoS Attacks Based on Random Forest in SDN. Appl. Sci. 2023, 13, 7872. [Google Scholar] [CrossRef]
- Marvi, M.; Arfeen, A.; Uddin, R. An augmented K-means clustering approach for the detection of distributed denial-of-service attacks. Int. J. Netw. Manag. 2021, 31, e2160. [Google Scholar] [CrossRef]
- Lian, W.; Li, Z.; Guo, C.; Wei, Z.; Peng, X. FRChain: A blockchain-based flow-rules-oriented data forwarding security scheme in SDN. KSII Trans. Internet Inf. Syst. (TIIS) 2021, 15, 264–284. [Google Scholar]
- Su, J.; Jiang, M. A hybrid entropy and blockchain approach for network security defense in SDN-based IIoT. Chin. J. Electron. 2023, 32, 531–541. [Google Scholar] [CrossRef]
- Li, W.; Wang, Y.; Meng, W.; Li, J.; Su, C. BlockCSDN: Towards blockchain-based collaborative intrusion detection in software defined networking. IEICE TRANSACTIONS Inf. Syst. 2022, 105, 272–279. [Google Scholar] [CrossRef]
- Hassan, A.I.; El Reheem, E.A.; Guirguis, S.K. An entropy and machine learning based approach for DDoS attacks detection in software defined networks. Sci. Rep. 2024, 14, 18159. [Google Scholar] [CrossRef] [PubMed]
- Saiyed, M.F.; Al-Anbagi, I. A Genetic Algorithm and t-Test Based System for DDoS Attack Detection in IoT Networks. IEEE Access 2024, 12, 25623–25641. [Google Scholar] [CrossRef]
- Arvind, T.; Radhika, K. XGBoost Machine Learning Model-Based DDoS Attack Detection and Mitigation in an SDN Environment. Int. J. Eng. Trends Technol. 2023, 71, 349–361. [Google Scholar] [CrossRef]
- Hamarshe, A.; Ashqar, H.I.; Hamarsheh, M. Detection of DDoS Attacks in Software Defined Networking Using Machine Learning Models. In Proceedings of the 2023 International Conference on Advances in Computing Research (ACR’23), Orlando, FL, USA, 8–10 May 2023; Springer: Berlin/Heidelberg, Germany, 2023; Volume 700, pp. 620–636, Lecture Notes in Networks and Systems. [Google Scholar] [CrossRef]
- Butt, H.A.; Harthy, K.S.A.; Shah, M.A.; Hussain, M.; Amin, R.; Rehman, M.U. Enhanced DDoS Detection Using Advanced Machine Learning and Ensemble Techniques in Software Defined Networking. Comput. Mater. Contin. 2024, 81, 3003–3031. [Google Scholar] [CrossRef]
- Wang, R.; Ye, K.; Meng, T.; Xu, C.Z. Performance evaluation on blockchain systems: A case study on Ethereum, Fabric, Sawtooth and Fisco-Bcos. In Proceedings of the Services Computing—SCC 2020: 17th International Conference, Held as Part of the Services Conference Federation, SCF 2020, Honolulu, HI, USA, 18–20 September 2020; Proceedings 17. Springer: Berlin/Heidelberg, Germany, 2020; pp. 120–134. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Future Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing realistic distributed denial of service (DDoS) attack dataset and taxonomy. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–8. [Google Scholar]
- Hariri, S.; Kind, M.C.; Brunner, R.J. Extended isolation forest. IEEE Trans. Knowl. Data Eng. 2019, 33, 1479–1489. [Google Scholar] [CrossRef]
- Estévez, P.A.; Tesmer, M.; Perez, C.A.; Zurada, J.M. Normalized mutual information feature selection. IEEE Trans. Neural Netw. 2009, 20, 189–201. [Google Scholar] [CrossRef]
- Biau, G.; Scornet, E. A random forest guided tour. Test 2016, 25, 197–227. [Google Scholar] [CrossRef]
- Chen, X.; Jeong, J.C. Enhanced recursive feature elimination. In Proceedings of the Sixth International Conference on Machine Learning and Applications (ICMLA 2007), Cincinnati, OH, USA, 13–15 December 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 429–435. [Google Scholar]
- De Oliveira, R.L.S.; Schweitzer, C.M.; Shinoda, A.A.; Prete, L.R. Using mininet for emulation and prototyping software-defined networks. In Proceedings of the 2014 IEEE Colombian Conference on Communications and Computing (COLCOM), Bogota, Colombia, 4–6 June 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [Google Scholar]
- Tripathy, D.N.; Reed, W.M. Pox. In Diseases of Poultry; Wiley: New York, NY, USA, 2013; pp. 333–349. [Google Scholar]
- Cano-Benito, J.; Cimmino, A.; García-Castro, R. Toward the ontological modeling of smart contracts: A solidity use case. IEEE Access 2021, 9, 140156–140172. [Google Scholar] [CrossRef]
- Yacouby, R.; Axman, D. Probabilistic extension of precision, recall, and f1 score for more thorough evaluation of classification models. In Proceedings of the First Workshop on Evaluation and Comparison of NLP Systems, Online, 20 November 2020; pp. 79–91. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).