Abstract
Technological advancement is currently focused on the miniaturization of devices, and integrated circuits allow us to observe the increase in the number of Internet of Things (IoT) devices. Most IoT services and devices require an Internet connection, which needs to provide the minimum processing, storage and networking requirements to best serve a requested service. One of the main goals of 5G networks is to comply with the user’s various Quality of Service (QoS) requirements in different application scenarios. Fifth-generation networks use Network Function Virtualization (NFV) and Mobile Edge Computing (MEC) concepts to achieve these QoS requirements. However, the computational resource allocation mechanisms required by the services are considered very complex. Thus, in this paper, we propose an allocation and management resources mechanism for 5G networks that uses MEC and simple mathematical methods to reduce the model complexity. The mechanism decides to allocate the resource in MEC to meet the requirements requested by the user. The simulation results show that the proposed mechanism provides a larger amount of services, leading to a reduction in the service lock number and as a reduction in the blocking ratio of services due to the accuracy of the approach and its load balancing in the process of resource allocation.
1. Introduction
Fifth-generation (5G) networks have been designed to attain a 1000-fold capacity, five-fold reduced latency and 10-fold longer battery life than 4G networks [1,2]. This evolution is due to the proliferation of high-demand mobile applications and the traffic growth exchanged daily by billions of mobile wireless devices worldwide [3]. For instance, a study by Gartner Newsroom stated that around 5.5 million devices were used in 2016, and this number will be approximately 3.8 billion in 2021 [4]. Besides, AT&T states that data traffic on their mobile network has increased by about 250,000% since 2007, and they expected this growth to increase 10-fold by 2020 [5]. This behavior is especially true during the lockdowns implemented due to the COVID-19 concerns—several European Internet Exchange Points (IXPs) reached an all-time peak during this period [6]. Therefore, this rapid traffic growth brings technical challenges in terms of managing mobile devices and meeting different user demands [7].
Fifth-generation networks rely on Mobile Edge Computing (MEC) to provide computational resources at the network edge, reducing latency and improving the Quality of Service (QoS), as MEC reduces communication delay and also data traffic on the back-hall networks [8,9,10]. MEC aggregates idle resources, such as storage and processing, from mobile users sharing the same preferences. Thus, MEC provides Cloud services, such as environment monitoring services, statistical processing calculations, and other services, more closely to mobile users [11,12,13]. In this sense, some mobile users could increase their capabilities by using MEC resources, while other mobile users lend their resources to MEC [14,15]. In MEC scenario, mobile applications and services can be allocated on MEC to meet user demands [16,17]. However, each MEC has a limited resource capacity that can be used to provide services to mobile users [14]. It is therefore essential to design efficient resource management approaches to handle MEC resources to serve a higher number of requested services, minimizing the unnecessary reallocations caused by user mobility.
A resource management mechanism is implemented in two steps: (i) resource aggregation and (ii) resource allocation [18,19,20]. Specifically, the resource aggregation step creates MEC; i.e., a pool of available resources to be used by other mobile devices to meet users’ demands. This involves the announcement of the available idle computational resources, which can be shared with other devices belonging to the system, maximizing the pool of available resources that the system can use. On the other hand, the resource allocation step involves the allocation of services based on the resources available in MEC to better meet the requested services’ requirements. In this context, the choice of when and where the service will be allocated by a resource allocation mechanism greatly impacts the performance of the service provided.
However, the dynamic nature of users leads to a fluctuation in terms of the number of resources in the pool of available resources for a given MEC, where users might frequently disconnect from MEC depending on the user mobility pattern. This issue directly impacts the number of services attended/allocated. Furthermore, user mobility leads to service reallocation inside MEC to maintain service provision. Thus, user mobility highly impacts the service allocation/reallocation performance in terms of service delivery [21]. This is because the service may not be served due to a lack of resources, the service may be blocked in the search for a device to be allocated or reallocated, or it may have its quality of service impaired due to the need to relocate the service. In recent years, many works have proposed different resource allocation mechanisms to allocate services on MEC to provide better services to users [22,23,24,25,26,27,28,29,30]. However, these strategies do not take into account the service length or user mobility information. Besides, such works involve significant complexity in the decision-making process, impacting the computation expense and inference times.
In this article, we propose a resource allocation mechanism for 5G networks, considering Mobile Edge Computing to meet user demand, called RELIABLE—REsource alLocatIon mechAnism for 5G network, considering moBiLe Edge computing. We consider MEC infrastructure distributed in an urban environment by aggregating idle resources from mobile devices; e.g., vehicles, mobile users and other devices. Thus, each MEC iteration has a limited resource capacity that can be used to provide services to mobile users. In this context, RELIABLE aims to maximize the availability of resources used when requested by MEC. To this end, RELIABLE considers mobility prediction to decrease the unnecessary reallocations caused by user mobility. Service time and network consumption are also used to reduce service allocation and the impacts of reallocation. In this sense, RELIABLE considers a multi-criteria mathematical method to deal with MEC resource allocation to meet the user’s demands for Cloud services. Thus, RELIABLE decides where and when MEC services will be allocated based on the multi-criteria mathematical method. Simulation results show that RELIABLE improved the number of services to be provided compared with allocation mechanisms by 45%; i.e., for Greedy, Best, and Worst mechanisms. RELIABLE also provided a reduction of 40% in the service locks number due to its assertiveness, as well as a reduction in the blocking ratio of services about 45% due to its load balancing in resource allocation. Therefore, the contributions of this work can be summarized as follows:
- We propose a mechanism to allocate resources in MEC infrastructure as a way to maximize the availability of resources which can be used when they are requested in MEC.
- We consider the combination of mobility prediction and the resources required, as well as the service time for proper decision making.
- We perform simulation experiments to introduce the impacts and benefits of RELIABLE, where the results show that RELIABLE can effectively mitigate the challenges related to resource allocation in MEC infrastructure in terms of the number of services served, the number of services blocked and the number of services denied for a different number of users requesting different services.
The remainder of this article is organized as follows. Section 2 describes the most relevant related works in this area. Section 3 introduces the network scenario used in this article, as well as the RELIABLE mechanism and its operation. Section 4 shows the evaluation of the simulation of the performance of RELIABLE and its results. Finally, Section 5 presents the conclusions and directions for future works.
2. Related Works
In the literature, some papers have been produced that include MEC resource allocation mechanisms [31,32,33,34,35,36,37,38,39,40]. Song et al. [31] proposed a resource-allocation mechanism based on context-sensitive clustering technology (VNF-RACAG - virtualized network functions resource allocation) to minimize the delay in the service provisioning network. The mechanism uses a stochastic model of Network Function Virtualization (NFV), as well as geographic contexts and user transfer histories in the allocation time optimization process. Furthermore, VNF-RACAG uses individual users’ locations and characteristics to group them into clusters for more efficient functional support. The iterative gradient descent method is used to compute cluster numbers to minimize the end-to-end delay. Next, a graphical partitioning algorithm is used to reduce movement among clusters, which is executed when the user’s trend phase changes. Although the VNF-RACAG mechanism reduces communication time (delay), its complexity increases the processing load of network elements.
van Lingen et al. [32] proposed an architectural approach that addresses some of the technical challenges behind Cloud and Fog communication and resource allocation. This is a model-oriented and service-centric architecture based on OpenFog Consortium (OFC) architecture [41]. This architecture uses a two-layer abstraction model, which provides intercommunication between Cloud and Fog. Additionally, it offers features for specific IoT modules. The approach was applied in Barcelona city, focusing on a small number of use cases. Although this architecture provides intercommunication among all devices, the evaluated environment does not reflect this architecture’s performance in a larger environment with a broader set of IoT devices.
Yu et al. [33] proposed a computational and network resource allocation mechanism for mobile systems using Orthogonal Frequency Division Multiplexing/Multiple Access (OFDMA) as a means of communication. The authors performed sub-carrier allocation for task provisioning and CPU time allocation for task execution in MEC. Thus, OFDMA was proven to be efficient and almost ideal in terms of energy savings for mobile devices in this work. The authors showed that resource allocation significantly impairs system performance through extensive simulations, even though the allocation mechanism for each resource type is almost optimal. Therefore, instead of simply combining the allocation mechanism separately, the two resource types’ congestion information should be considered simultaneously. Moreover, this joint programming approach is more critical when the allocation of computational resources can provide more prominent energy savings.
Ali et al. [36] proposed a resource allocation algorithm based on the device’s power profile using the 5G communication network. This work focused on small devices such as healthcare sensors. The approach is divided into three steps: in the first step, the device’s consumed energy is compared to a selected maximum energy budget value obtained from the QoS metric based on the IoT applications’ power requirements; consequently, the number of sub-carriers is calculated. In the second step, an efficient solution is implemented by inducing a limit value. A given threshold value is selected using mapping based on a QoS metric. The threshold enhances sub-carrier selection for less highly-powered devices. Finally, a suitable threshold value is selected. The threshold value improves sub-carrier calculation for less energy-consuming devices.
Peng and Shen [37] proposed an asset assignment plan to help with distinctive vehicular applications; they considered two normal MEC designs and defined multi-dimensional asset streamlining issues, which as a rule suffered from high calculation unpredictability and an overlong critical thinking time. In this manner, they exploited reinforcement learning (RL) to change the two figured issues and explained them by utilizing Deep Deterministic Policy Gradient (DDPG) and various leveled learning models. Considering vehicles on a two-path straight national street, with one path for every heading, macro eNodeB (MeNB) and Wi-Fi Access Points (APs) were consistently sent to one roadside, with various Wi-Fi APs included in the MeNB approach. Additionally, the authors present the point-by-point range of the board techniques executed by the regulators and introduced by the MeNBand Edge Node (EN)-mounted MEC workers, including range cutting among MeNBs and Wi-Fi APs and range designation among vehicles related to a similar base station (BS).
Agarwal et al. [40] proposed a resource allocation appliance based on VNFs to support the vertical services in 5G networks. They considered that portable system administrators are responsible for planning the prerequisites of the vertical services into a framework of executive choices. This task is a part of the system coordination and involves settling on choices concerning (i) the position of the VNFs required by the verticals over the foundation; (ii) the tasks of CPU, memory and capacity assets for the VNFs; and (iii) the directing of information across organized hubs. These choices are correlated with one another in manners that are perplexing and regularly outlandish. In this paper, the center was around the distribution of computational and system assets, and such choices were considered together, representing (i) the prerequisites of each VNF and vertical service, (ii) the abilities of the system administrator’s foundation and (iii) the limit and inertness of the connections between organized hubs. A key part of this work—regularly ignored by past research on 5G and VNF arrangements—is that our methodology permits the adaptable distribution of the computational abilities of each host among the VNFs it runs.
Wang et al. [38] proposed a resource allocation mechanism based on the VNF choice technique which isolates the vehicular system into a few layers, as indicated by the request for VNFs in an SFC. In each layer, each parcel that appears should be lined first. At that point, the parcel is communicated to a next VNF layer that is chosen by the scheduler. VNFs are chosen by the traffic distinguishing proof, while also considering the system ongoing data transfer capacity and registering assets.
Kiani and Ansari [39] proposed a resource allocation mechanism called Non-Orthogonal Multiple Access - NOMAbased on Edge Computing, which aims to decrease the energy expenditure between the user and the MEC device. To this end, the authors formulated the mechanism to minimize the power consumption of MEC users, optimizing the number of user clusters and the allocation of computing and communication resources, as well as the transmission rate. In particular, similar to frequency resource blocks, the authors split the computing power available in MEC; thus, this approach uses radio-frequency allocation and computational resources for users assigned to different order indices.
Existing resource allocation mechanisms have significant complexity, meaning that MEC can be overwhelmed in the allocation process. Furthermore, most of the existing works do not consider mobility prediction as a decision parameter for carrying out resource allocation. Another important parameter for these mechanisms is the service time; i.e., when the resources will be allocated to attend the requested service, enabling the better management of available resources. Finally, it is essential to consider the computational impact of the execution of the decision mechanism. Depending on the technology used, such as artificial neural networks, the fuzzy approach or other more complex techniques, the execution of the mechanism may affect the execution of the requested services.
Table 1 summarizes the analyzed resource allocation mechanisms, in which we consider user mobility patterns, mobility prediction methods, the service time and the complexity of the method. The method will consume a significant amount of resources which some services could use; for instance, a given work is classified as high if it requires greater overheads and processing in resource management, including methods based on software-defined networks using artificial neural networks. On the other hand, a given work is classified as low if it uses the standard communication protocols and adds an allocation mechanism. Besides, user mobility means the speed at which the mobile user or device moves, where high mobility means vehicles or low mobility means a mobile user or fixed IoT device, for example. Based on our state-of-the-art analysis, we conclude that the works described do not consider the high mobility of the user or the service time and fail to perform a forecast of the mobility of the service flow in which it seeks to reduce unnecessary allocations, given the highly dynamical environment. Therefore, RELIABLE considers all these questions in its decision mechanism with low mathematical complexity. To the best of our knowledge, RELIABLE is the first technique to incorporate all of these critical features in a resource allocation mechanism.

Table 1.
Summary of resource allocation mechanisms.
3. RELIABLE
In this section, we introduce RELIABLE’s mechanism to maximize the usability of MEC resources available on a 5G network. RELIABLE is designed to handle resource management and allocation for a 5G network to serve a higher number of requested services, minimizing the unnecessary reallocations caused by user mobility. To this end, RELIABLE takes into account the bandwidth, mobility prediction, and service time as input parameters for the allocation decision mechanism. In the following, we introduce the 5G network scenario considering MEC, and we also describe the RELIABLE mechanism in detail.
3.1. Network Scenario
We consider a 5G scenario composed of a set of mobile users (e.g., vehicles, mobile users and other devices) with an individual identity , where w is the maximum number of users. At any moment, a given mobile user could need to run a service, but their computational resources would not support the processing of such a service [14]. In this sense, the device sends a request message to a controller node deployed at the 5G network infrastructure to process the service in MEC. We consider MEC (, where o is the maximum number of MEC) composed of a group of mobile devices sharing the same preferences that could lend their resources to create a pool of resources that could be made available to 5G network mobile nodes [42]. Specifically, a given mobile node might have idle computational resources, such as processing or storage, which can be aggregated and managed by a controller node [43].
In this context, a given mobile node could increase its capabilities by using the available resources of MEC , while other entities lend their resources to MEC [44,45]. Therefore, MEC could provide services ( where m is the maximum of the number of services) up to mobile users at the network edge. Figure 1 shows the scenario in which the RELIABLE can be deployed in the controller node to manage the resources coming from the urban environment composed of mobile nodes connected through the 5G network infrastructure. The controller node is a centralized entity that has a global view of each MEC iteration and all users to allow better allocation.
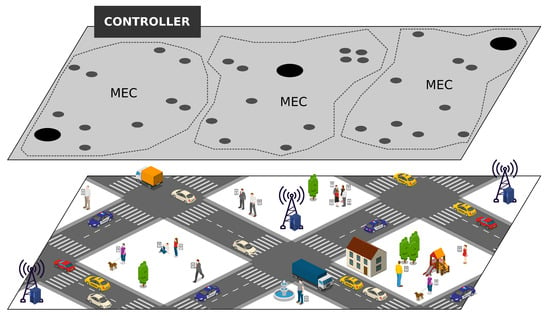
Figure 1.
Fifth-generation (5G) network environment considering Mobile Edge Computing (MEC).
In this scenario, a given mobile node that may be moving around the urban perimeter may request a given service —e.g., traffic monitoring or entertainment, among others—from the controller node . This service requires computational resources, such as processing, storage and runtime, to efficiently serve the user request. In this context, the controller node receives the request and takes all decisions regarding when and where to allocate the service on a given MEC based on the RELIABLE resource allocation mechanism. It is essential to highlight that the controller node has an overview of each service and node status to decide which MEC has the required resources to allocate a given service .
Resources made available by MEC can be used to allocate a service as requested by users. To solve the problem of resource allocation for a given service , we consider that each MEC can manage up to services, and each MEC supports up to users. Finally, the controller node may need to migrate a given service to another MEC device to continue to efficiently meet the user’s request. This is due to user mobility and resource availability, or even the need to provide load balance.
3.2. Allocation Decision
RELIABLE decides whether or not to allocate resources for a given service and which MEC such a service will be allocated to in order to meet the needs of the service. To this end, RELIABLE considers an allocation decision step, which takes the decision based on the mobility prediction , service time and bandwidth .
In this way, the controller node monitors the network traffic flows to predict mobility flow between regions; i.e., anticipating the resource utilization in a given place. According to Bui et al. [46], the user network flow follows a continuous distribution in time, and we can use a Gaussian method to predict the user flow among different MECs. This prediction method aims to anticipate the use of resources. For this purpose, Bayesian and the regression of the Gaussian process are used to perform the forecast, and it is necessary to monitor the flows in which they reflect the historical resource allocations used in MEC. Therefore, to carry out this forecasting method efficiently, a particular terminology us defined: the monitoring window, which describes a fixed workload collection period. Table 2 describes the important notations.

Table 2.
List of important notations.
Assuming the input data are a collection of locations based on a limited time slot , where is the location of the flow in the time slot t, a finite set of random variables represents the corresponding joint Gaussian distribution of historical flow monitoring statistics regarding the time order. This set, over time, forms the Gaussian process , as we can see in Equations (1)–(3), where the prediction function is composed of a kernel function [47]. This kernel function is used to define the prior underlying relationship knowledge through a positive–definite function that comprises some special parameters that specify its shape. is the mean function used to evaluate the time location x. Thus, the controller node can compute the probability that a given flow from a mobile user migrates from one location x to another based on Equation (3).
RELIABLE also considers the available bandwidth as an input parameter for the selection of the best MEC to allocate a given service . The bandwidth is used to check the impact it would have if a given MEC allocates the service ; i.e., it evaluates the impact (bandwidth consumption) on the network that the flow exchange would cause, considering that it is necessary to carry out the allocated service. In this way, the controller node captures the bandwidth , allowing the controller node to compute the network impact in case it needs to migrate or allocate a given service to another MEC .
Finally, RELIABLE considers the service length that requires resources to be allocated to fulfill the user request. In this sense, the service time enables us to estimate the start and end time of a given service requested through the sum of the services allocated execution times in MEC . Thus, the service time is used to compute the duration for which the resources used to serve a given service will be allocated.
RELIABLE calculates different importance degrees for decision making based on the Analytic Hierarchy Process (AHP) method. AHP provides the influence factor for each parameter. It assigns weights to the parameters used; that is, the parameter with the greatest importance over the others will have a greater weight at the end of AHP processing. We consider five importance levels for the comparison between each parameter pair, which indicates the importance of one parameter over the others, as shown in Table 3.

Table 3.
Pairwise importance levels.
To model the AHP, we consider a weight matrix of , in which the mobility prediction has a higher priority over the other parameters because RELIABLE minimizes the number of unnecessary exchanges caused by user mobility. We also consider that the bandwidth has a higher priority over the service time because if the service needs to be transferred, this transfer will not impact the performance of the system. Therefore, the matrix indicates what influence parameter i will have on the other parameters z. Table 4 shows the weight assignments used in our AHP. Therefore, these values will be used as a weight to establish the decision matrix, as we can see in Equation (4).

Table 4.
Influence factor. BW: bandwidth.
The influence factor of a given parameter i is computed by the sum of the current value multiplication of a metric ; i.e., , and , with the relative importance of the other metrics , as we can see in Equation (4). Therefore, each metric value and metric importance parameter is calculated by MEC through the applied computational resource monitoring, the service execution time and the bandwidth used.
In an urban environment, a given mobile user can request different services with different requirements; i.e., a service related to public or driver safety must have a higher priority than services related to advertising a restaurant close to the user. In this way, we divide services into three classes based on [48], where the safety class has priority 1 (), the comfort class has priority 2 () and the entertainment class has priority 3 (). This priority value for each service is multiplied with the influence factor to obtain the values of the decision matrix (Equation (5)). The matrix values will be used to choose the best MEC , in which the resources will be allocated depending on the service importance.
However, the values of this matrix have a high variation due to the characteristics of each parameter. In this way, we performed a simple normalization of these values to find a more accurate choice, as shown in Equation (6).
where is the matrix value for MEC K and is the all-value arithmetic average contained in column j of the matrix.
Once data are normalized, we perform a simple calculation of parameter differentiation for each MEC, and the results are stored in a vector as follows.
where represents the current MEC normalized data and the MEC device to which the resources are allocated, and represents the candidate MEC device’s normalized data to allocate the resource. Therefore, contains the values of each MEC device, where the chosen MEC device corresponds to the one with the highest final value (Equation (8)).
3.3. RELIABLE Operations
Algorithm 1 shows a decision phase overview of the RELIABLE mechanism. RELIABLE must be aware of the available resources at each MEC , which is provided by communication between MEC devices with the controller node , allowing a MEC to inform the controller node about its idle resources. In this way, these resources become available resource pool parts (lines 1–3). A given MEC allocates resources for a given service , where those resources must be reallocated in another MEC before the user disconnects from MEC . It is important to mention that the resource and service migration is beyond the scope of this work, since we focus on the choice of MEC to allocate resources for a service .
| Algorithm 1 Abstraction of RELIABLE |
|
Once a mobile user is connected to the controller node via the 5G network, it can request a particular service. At each service request, the controller node checks which is the best MEC to allocate resources to provide such a service. To do this, the controller node performs the MEC select function (lines 4–6), which uses AHP and which is also performed when a mobile user leaves one MEC device network and connects to another due to mobility. If the selected MEC does not have the necessary resources to allocate the service, the next MEC generated by the function will be selected; i.e., the service is blocked until the controller node finds a valid MEC (lines 7–11). If no MEC is selected, the requested service is discarded.
4. Performance Analysis
This section describes the performance assessment of the RELIABLE resource allocation mechanism for the 5G network based on a multi-criteria mathematical method.
4.1. Scenario Description and Methodology
We implemented RELIABLE’s mechanism using the Python language. We considered that RELIABLE would be executed in an urban environment composed of users moving following a Random Waypoint Mobility model with pause time, as this mobility model enables users to stay in a location in the city (such as a conveniences store) for a while. For RELIABLE evaluation, we considered that the user input and output and MEC followed a Pearson Type III distribution [49].
The simulation considered a variation in the number of users (i.e., 327, 499, 596, 930, and 1088) to represent different situations and to provide a comparison between the best and worst-case (the best case was the simulation with few users while the worst-case was with many users). For the representation of the urban scenario, we considered an area of Manhattan in which the coverage of the urban environment comprised four connected 5G cell towers that allowed interconnection among the MEC devices. Table 5 describes the simulation setup.

Table 5.
Simulation setup.
We considered two types of services for each MEC device based on the work presented in [48]. Specifically, the security service with the highest priority was prioritized considering the following characteristics: (i) 1 h of service execution time; (ii) 1% of bandwidth consumption for transfer over the 5G network; (iii) 0.5% of processing consumption; and (iv) 1.5% of memory consumption. On the other hand, the second service (i.e., entertainment service) had the following characteristics: (i) 2h of service execution time; (ii) 4% of bandwidth consumption for transfer considering the 5G communication; and (iii) 2.5% of processing consumption; and (iv) 2.5% of memory consumption.
In this way, we evaluated these services over three scenarios to verify the impact of allocating resources from different priority levels of services. Scenario 1 represents the case in which only security services are requested, Scenario 2 shows the case in which only entertainment services are requested, and Scenario 3 shows the case in which the choice of requesting both services is random, and the choice of which service will be requested is also random.
We implemented three resource allocation mechanisms to compare the performance of RELIABLE in the same scenario. Specifically, Greedy runs through the controller until it finds the first MEC device that has the resources it needs. On the other hand, Best runs through the controller by computing the available resource numbers, creating a list of these values and sorting them to choose the most resource-intensive MEC device. Finally, Worst is similar to the previous; it also runs through the controller by computing the available resources numbers, creating a list of these values and sorting them to choose the best MEC device to attempt the service. We can consider that we perform a comparison with the market standard that makes a greedy allocation of available resources. In addition, we compare our method with two other paradigms, in which the Best and Worst scenarios are used to allocate memory. As the existing allocation methods did not consider the prediction of mobility with the time of each service, this would not represent a fair comparison with other methods.
We consider the following metrics to assess the performance of these resource allocation mechanisms:
- The number of services served means the number of services that were allocated in an MEC device.
- The number of services blocked means the number of incorrect choices for service allocation due to the lack of resources available for allocation. Therefore, the service is blocked until RELIABLE finds an MEC device that can allocate the service.
- The number of services denied means the number of requests that, due to lack of resources, were not allocated by any MEC, and thus the number of services that were not actually allocated due to lack of resources by all MEC devices.
4.2. Results for Scenario 1
Figure 2 shows the simulation results for different resource allocation mechanisms in a scenario with a different number of users requesting the security service. By analyzing the results of Figure 2a, it is possible to conclude that RELIABLE increased in the number of services served compared to other methods, especially in cases with a higher user number requesting the service; i.e., from 940 to 1094 users. This is due to RELIABLE allocating resources based on mobility prediction, as well as the time that the resources would be in execution in each MEC, allowing a better distribution of these resources and the provision of more services. When we analyze a smaller number of users requesting resources, everyone reaches their allocation limit because they can meet all demand without spending a great deal of of time finding an MEC device.
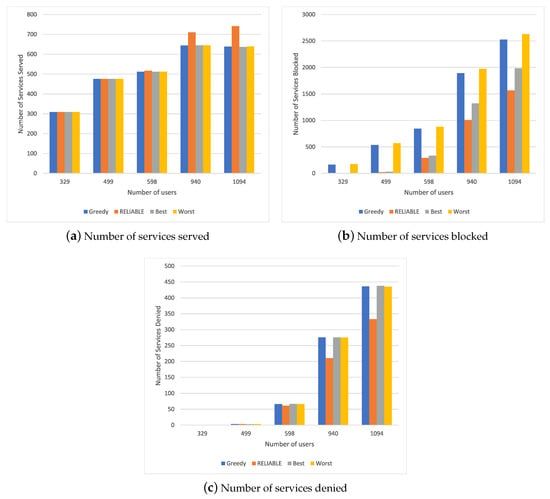
Figure 2.
Simulation results for Scenario 1.
Figure 2b describes the number of times that the service has to wait to be serviced again during a service relocation. We can observe that Best and RELIABLE obtained no blocking since they already selected the best MEC devices to carry out the allocation upon receiving the requests, unlike Greedy and Worst, which had to carry out some reallocations to serve the resources during the service’s execution. When we consider a higher number of service requests, we see that RELIABLE had a better number of blockages, as it avoided an unnecessary transfer of the service, thus obtaining a decrease of 3% compared to Best and 5% compared to the others.
This amount of blocking had an impact on the number of denied services, where RELIABLE obtained a reduction of 2% compared to the other methods, as shown in Figure 2c. When we analyzed a smaller number of requests, we were able to observe that all services were provided with 329 users requesting services, and a very similar services denied number was found 499; this was due to the number of resources available by the set of MEC devices. In this way, when considering the request for only a single service, we can see that RELIABLE can handle a greater number of requests, with a low service blocked number and resource use compared to a scenario with a higher number of requests.
4.3. Results for Scenario 2
Figure 3 shows the simulation results for different resource allocation mechanisms in a scenario with a different number of users requesting the entertainment service. Figure 3a shows the number of services served. We can see that RELIABLE could handle more requests than other methods, with a 20% increase considering a smaller number of users and an increase of 38% for a higher number of requests. This is because RELIABLE uses the service execution attributes as well as the user mobility and the resource consumption characteristics of each requested service.
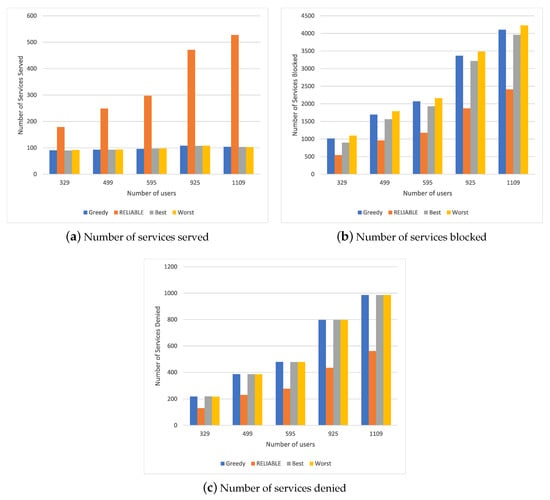
Figure 3.
Simulation lresults for Scenario 2.
RELIABLE also has a shorter blocking time for switching between one MEC device and another, both for a low and high number of requests, as we can see in Figure 3b. The other methods exhibit similar behavior as these methods provide a greater mobility of services between the MEC devices. The lack of adequate resource balance considerably affects the number of services used by the system, as we can see in Figure 3c. We can observe that the Greedy, Best and Worst methods had the same behavior since their allocation policies did not carry out load balancing among the different MECs, thus overloading only a subset of MECs. Therefore, RELIABLE achieved a 20% reduction in the number of services denied due to an efficient information flow balancing policy.
Based on the results of Scenario 2, we can observe that RELIABLE reduces the number of blocks and meets a greater number of requests, with a low number of blocks and minimal service resources considering the request for only entertainment services, which requires greater computational power and greater bandwidth, as well as a longer service execution time. Comparing Scenario 1 with Scenario 2, we can observe that, with an increase in the resources requested by the service, RELIABLE maintains an increase in the number of services served, with a low amount of denied services. In other words, RELIABLE exhibits stable behavior, as it presented better behavior with an increase in requests, both in terms of meeting service needs with more computational resources and for services that need fewer resources. This is because RELIABLE considers the mobility of the flow and the time that it will be in execution, without using the parameters of the MEC device’s computational capacity in the decision policy. Thus, when we analyze the results obtained in Scenario 1 as well as Scenario 2, both showed an improvement in the increase in users. In Scenario 1 with fewer users (329, 499, 595), RELIABLE showed a behavior similar to the other solution due to the amount of available resources and the low computational quantity required by the service; however, in the transaction and the scenario with a greater number of users (925, 1109), RELIABLE performed better because it balanced its computational load by predicting mobility and the impact allocation or the change of flow. The same can be observed in Scenario 2. Nevertheless, in Scenario 2, it also performed well for a smaller number of users because the amount of resources made available by these users was also greater, which allowed RELIABLE to achieve better management of the available resources.
4.4. Results for Scenario 3
Analyzing the results obtained in Scenario 1 and Scenario 2, the behavior of RELIABLE was seen to be focused on attending to one type of service at a time. Thus, it is necessary to check whether this behavior is maintained in a scenario closer to real conditions, in which users could request one or more services at the same time, which requires more or fewer computational resources. Figure 4 shows the simulation results for different resource allocation mechanisms in a scenario with a different number of users requesting both security and entertainment services randomly. RELIABLE achieved a significant increase in the number of services served compared to other methods, as shown in Figure 4a. This is because network parameters regarding service execution are prioritized. Considering a number of users above 580, the Best, Worst and Greedy methods increased the number of services served compared to RELIABLE by 50%. It is possible to see an increase of 5% compared to Random, since it most often selected the MEC devices with sufficient resources to perform the service.
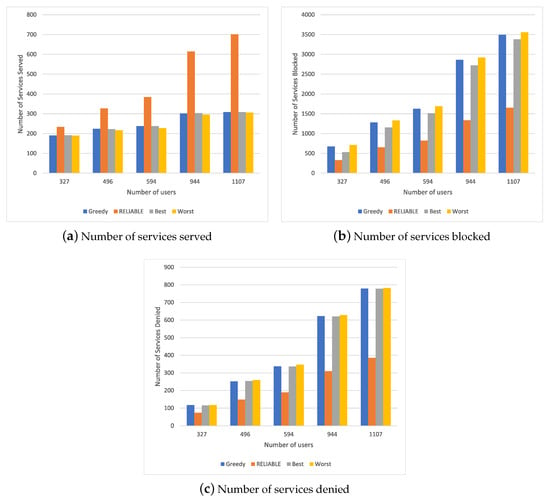
Figure 4.
Simulation results for Scenario 3.
5. Conclusions
The service must wait until the resource allocation mechanism finds an MEC device capable of meeting the requirements that the service demands, as shown in Figure 4b. When Best, Worst and Greedy methods are compared to RELIABLE, a reduction close to 47% can be observed. In the case of comparison with Random, the reduction is 7% as the proposed policy selects the first options of MEC devices with sufficient resources to perform the service.
The number of services denied due to a lack of pool resources and Cloud MEC devices can be seen in Figure 4c. When the Best, Worst and Greedy methods are compared to RELIABLE, a reduction close to 39% can be observed. In the case of comparison with Random, the reduction is 3% as the proposed policy has a better load balancing behavior between resources within the MEC; i.e., the Best, Worst and Greedy methods allow the allocation of the available resources in a disorderly manner.
The results show that RELIABLE behaves as expected. RELIABLE remains stable even with different loads of resource requests, and it can therefore serve a higher number of services and consequently block and deny a lower percentage of services. Thus, RELIABLE provides better load balancing in allocations. Analyzing the three scenarios, we can observe that under a mixture of services—that is, a mixture of demands in the network RELIABLE—there was an 18% increase in service attendance for the scenario of higher demand in Scenario 2; however, with a reduction of approximately 1% compared to a scenario with low computational demand. This is because RELIABLE manages to prioritize which services will be allocated and where resources will be allocated to meet such services. When we consider the number of blocked and the number of denied services, we could observe a reduction of approximately 13% of blocked services and 10% of denied services compared to Scenario 2 and a small increase of approximately 27% of blocked services and 25% compared to Scenario 1. This may lead to a greater demand for services close to Scenario 2. However, RELIABLE performed better than the other comparison mechanisms—Greedy, Best and Worst.
In this article, we proposed RELIABLE, which addresses the resource allocation problem in 5G networks using MEC. We consider an MEC network composed of a set of mobile devices which have available resources to be shared, increasing the number of services offered by the MEC network. To this end, we designed a multi-criteria decision-making method and AHP that considered not only the service and network parameters but also the mobility of the flow. Therefore, the decision-making method offers a balanced input with different degrees of importance, maximizing resource utilization in the Cloud. The numerical results show that RELIABLE allows a larger amount of services to be provided, providing a reduction in the number of service blocks due to its assertiveness, as well as a reduction in the number of services denied due to its load balancing in resource allocation. In future work, we will consider other parameters, such as energy consumption and mobility, to improve the mechanism.
Author Contributions
Conceptualization, R.S.P. and R.I.M.; methodology, R.S.P., D.D.L., M.A.C.d.S.; formal analysis, R.S.P., D.D.L., M.A.C.d.S.; writing—original draft preparation, R.S.P., D.D.L., M.A.C.d.S. and J.B.D.d.C.; writing—review and editing, A.H.M.P., D.R., L.V. and R.I.M. All authors have read and agreed to the published version of the manuscript.
Funding
R.I.M. would like to thanks CNPq (process 407248/2018-8 and 309822/2018-1) for funding the research project, the financial support granted by São Paulo Research Foundation (FAPESP), process 2020/07162-0, 2020/11951-0 and 13/07375-0 (CEPID/CeMEAI projet), in his research. J.B.D.d.C. would like to acknowledge the financial support granted by São Paulo Research Foundation (FAPESP), process 2018/16703-4, in his research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ren, H.; Pan, C.; Deng, Y.; Elkashlan, M.; Nallanathan, A. Resource Allocation for URLLC in 5G Mission-Critical IoT Networks. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Martin, A.; Egaña, J.; Flórez, J.; Montalbán, J.; Olaizola, I.G.; Quartulli, M.; Viola, R.; Zorrilla, M. Network Resource Allocation System for QoE-Aware Delivery of Media Services in 5G Networks. IEEE Trans. Broadcast. 2018, 64, 561–574. [Google Scholar] [CrossRef]
- Ji, H.; Park, S.; Yeo, J.; Kim, Y.; Lee, J.; Shim, B. Ultra-reliable and low-latency communications in 5G downlink: Physical layer aspects. IEEE Wirel. Commun. 2018, 25, 124–130. [Google Scholar] [CrossRef]
- Bankmycell. How Many Smartphones Are in the World? 2020. Available online: https://www.bankmycell.com/blog/how-many-phones-are-in-the-world (accessed on 7 July 2020).
- AT&T. Staying Connected in 2017: Our Predictions. Available online: http://about.att.com/newsroom/2017_network_predictions.html (accessed on 6 July 2020).
- Candela, M.; Luconi, V.; Vecchio, A. Impact of the COVID-19 pandemic on the Internet latency: A large-scale study. arXiv 2020, arXiv:2005.06127. [Google Scholar] [CrossRef]
- Aazam, M.; Harras, K.A.; Zeadally, S. Fog computing for 5G tactile industrial internet of things: Qoe-aware resource allocation model. IEEE Trans. Ind. Inform. 2019, 15, 3085–3092. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Rodrigues, D.O.; da Costa, J.B.D.; Rosario, D.; Villas, L.A. A Virtual Machine Migration Policy Based on Multiple Attribute Decision in Vehicular Cloud Scenario. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Byers, C.C. Architectural Imperatives for Fog Computing: Use Cases, Requirements, and Architectural Techniques for Fog-Enabled IoT Networks. IEEE Commun. Mag. 2017, 55, 14–20. [Google Scholar] [CrossRef]
- Rosário, D.; Schimuneck, M.; Camargo, J.; Nobre, J.; Both, C.; Rochol, J.; Gerla, M. Service Migration from Cloud to Multi-tier Fog Nodes for Multimedia Dissemination with QoE Support. Sensors 2018, 18, 329. [Google Scholar] [CrossRef] [PubMed]
- Shrivastava, R.; Samdanis, K.; Sciancalepore, V. Towards service-oriented soft spectrum slicing for 5G TDD networks. J. Netw. Comput. Appl. 2019, 137, 78–90. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Meneguette, R.I.; De Grande, R.; Loureiro, A.A. Intelligent Transport System in Smart Cities; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Hagenauer, F.; Higuchi, T.; Altintas, O.; Dressler, F. Efficient data handling in vehicular micro clouds. Ad Hoc Netw. 2019, 91, 101871. [Google Scholar] [CrossRef]
- Brennand, C.A.R.L.; Boukerche, A.; Meneguette, R.; Villas, L.A. A novel urban traffic management 510 mechanism based on FOG. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 377–382. [Google Scholar]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Sahay, R.; Meng, W.; Jensen, C.D. The application of Software Defined Networking on securing computer networks: A survey. J. Netw. Comput. Appl. 2019, 131, 89–108. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Boukerche, A. A cooperative and adaptive resource scheduling for Vehicular Cloud. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 398–403. [Google Scholar] [CrossRef]
- Wang, T.; Liang, Y.; Jia, W.; Arif, M.; Liu, A.; Xie, M. Coupling resource management based on fog computing in smart city systems. J. Netw. Comput. Appl. 2019, 135, 11–19. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Geraldo Filho, P.; Bittencourt, L.F.; Ueyama, J.; Krishnamachari, B.; Villas, L.A. Enhancing intelligence in inter-vehicle communications to detect and reduce congestion in urban centers. In Proceedings of the 2015 IEEE Symposium on Computers and Communication (ISCC), Larnaca, Cyprus, 6–9 July 2015; pp. 1–6. [Google Scholar]
- Rejiba, Z.; Masip-Bruin, X.; Marín-Tordera, E. A survey on mobility-induced service migration in the fog, edge, and related computing paradigms. ACM Comput. Surv. (CSUR) 2019, 52, 1–33. [Google Scholar] [CrossRef]
- Zhang, B.; Mao, X.; Yu, J.; Han, Z. Resource Allocation for 5G Heterogeneous Cloud Radio Access Networks With D2D Communication: A Matching and Coalition Approach. IEEE Trans. Veh. Technol. 2018, 67, 5883–5894. [Google Scholar] [CrossRef]
- Dighriri, M.; Alfoudi, A.S.D.; Lee, G.M.; Baker, T.; Pereira, R. Resource allocation scheme in 5G network slices. In Proceedings of the 32nd International Conference on Advanced Information Networking and Applications Workshops (WAINA), Krakow, Poland, 16–18 May 2018; pp. 275–280. [Google Scholar] [CrossRef]
- Li, W.; Wang, J.; Yang, G.; Zuo, Y.; Shao, Q.; Li, S. Energy efficiency maximization oriented resource allocation in 5G ultra-dense network: Centralized and distributed algorithms. Comput. Commun. 2018, 130, 10–19. [Google Scholar] [CrossRef]
- Huo, L.; Jiang, D. Stackelberg game-based energy-efficient resource allocation for 5G cellular networks. Telecommun. Syst. 2019, 72, 377–388. [Google Scholar] [CrossRef]
- Hao, Y.; Tian, D.; Fortino, G.; Zhang, J.; Humar, I. Network Slicing Technology in a 5G Wearable Network. IEEE Commun. Stand. Mag. 2018, 2, 66–71. [Google Scholar] [CrossRef]
- Hao, Y.; Jiang, Y.; Hossain, M.S.; Ghoneim, A.; Yang, J.; Humar, I. Data-driven Resource Management in a 5G Wearable Network using Network Slicing Technology. IEEE Sens. J. 2019, 19, 8379–8386. [Google Scholar] [CrossRef]
- Gutierrez-Estevez, D.M.; Gramaglia, M.; De Domenico, A.; Dandachi, G.; Khatibi, S.; Tsolkas, D.; Balan, I.; Garcia-Saavedra, A.; Elzur, U.; Wang, Y. Artificial Intelligence for Elastic Management and Orchestration of 5G Networks. IEEE Wirel. Commun. 2019, 26, 134–141. [Google Scholar] [CrossRef]
- Dao, N.N.; Park, M.; Kim, J.; Paek, J.; Cho, S. Resource-aware Relay Selection for Inter-cell Interference Avoidance in 5G Heterogeneous Network for Internet of Things systems. Future Gener. Comput. Syst. 2019, 93, 877–887. [Google Scholar] [CrossRef]
- Brennand, C.A.R.L.; da Cunha, F.D.; Maia, G.; Cerqueira, E.; Loureiro, A.A.F.; Villas, L.A. FOX: A traffic management system of computer-based vehicles FOG. In Proceedings of the 2016 IEEE Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 982–987. [Google Scholar]
- Song, S.; Lee, C.; Cho, H.; Lim, G.; Chung, J. Clustered Virtualized Network Functions Resource Allocation based on Context-Aware Grouping in 5G Edge Networks. IEEE Trans. Mob. Comput. 2019, 19, 1072–1083. [Google Scholar] [CrossRef]
- van Lingen, F.; Yannuzzi, M.; Jain, A.; Irons-Mclean, R.; Lluch, O.; Carrera, D.; Perez, J.L.; Gutierrez, A.; Montero, D.; Marti, J.; et al. The Unavoidable Convergence of NFV, 5G, and Fog: A Model-Driven Approach to Bridge Cloud and Edge. IEEE Commun. Mag. 2017, 55, 28–35. [Google Scholar] [CrossRef]
- Yu, Y.; Zhang, J.; Letaief, K.B. Joint Subcarrier and CPU Time Allocation for Mobile Edge Computing. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Zhao, H.; Tao, L.; Zong, Z. Dynamic energy-aware cloudlet-based mobile cloud computing model for green computing. J. Netw. Comput. Appl. 2016, 59, 46–54. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Zhao, H. Energy-awaretask assignment for mobile cyber-enabled applications in heterogeneous cloud computing. J. Parallel Distrib. Comput. 2018, 111, 126–135. [Google Scholar] [CrossRef]
- Ali, A.; Shah, G.A.; Arshad, J. Energy Efficient Resource Allocation for M2M Devices in 5G. Sensors 2019, 19, 1830. [Google Scholar] [CrossRef]
- Peng, H.; Shen, X.S. Deep Reinforcement Learning based Resource Management for Multi-Access Edge Computing in Vehicular Networks. IEEE Trans. Netw. Sci. Eng. 2020, 1. [Google Scholar] [CrossRef]
- Wang, J.; He, B.; Wang, J.; Li, T. Intelligent VNFs Selection Based on Traffic Identification in Vehicular Cloud Networks. IEEE Trans. Veh. Technol. 2019, 68, 4140–4147. [Google Scholar] [CrossRef]
- Kiani, A.; Ansari, N. Edge Computing Aware NOMA for 5G Networks. IEEE Internet Things J. 2018, 5, 1299–1306. [Google Scholar] [CrossRef]
- Agarwal, S.; Malandrino, F.; Chiasserini, C.F.; De, S. VNF Placement and Resource Allocation for the Support of Vertical Services in 5G Networks. IEEE/ACM Trans. Netw. 2019, 27, 433–446. [Google Scholar] [CrossRef]
- Consortium, O. OpenFog Consortium. Available online: http://www.openfogconsortium.org/ (accessed on 7 July 2020).
- Boukerche, A.; Robson, E. Vehicular cloud computing: Architectures, applications, and mobility. Comput. Netw. 2018, 135, 171–189. [Google Scholar] [CrossRef]
- da Costa, J.B.D.; Meneguette, R.I.; Rosário, D.; Villas, L.A. Combinatorial Optimization-based Task Allocation Mechanism for Vehicular Clouds. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020; pp. 1–5. [Google Scholar]
- Pannu, G.S.; Hagenauer, F.; Higuchi, T.; Altintas, O.; Dressler, F. Keeping Data Alive: Communication Across Vehicular Micro Clouds. In Proceedings of the IEEE 20th International Symposium on “a World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–9. [Google Scholar]
- Thakur, A.; Malekian, R. Fog computing for detecting vehicular congestion, an Internet of Vehicles based approach: A review. IEEE Intell. Transp. Syst. Mag. 2019, 11, 8–16. [Google Scholar] [CrossRef]
- Bui, D.M.; Yoon, Y.; Huh, E.N.; Jun, S.; Lee, S. Energy efficiency for cloud computing system based on predictive optimization. J. Parallel Distrib. Comput. 2017, 102, 103–114. [Google Scholar] [CrossRef]
- Muller, K.R.; Mika, S.; Ratsch, G.; Tsuda, K.; Scholkopf, B. An introduction to kernel-based learning algorithms. IEEE Trans. Neural Netw. 2001, 12, 181–201. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Madeira, E.R.M.; Bittencourt, L.F. Multi-network packet scheduling based on vehicular ad hoc network applications. In Proceedings of the 8th International Conference on Network and Service Management (CNSM) and 2012 Workshop on Systems Virtualiztion Management (SVM), Las Vegas, NV, USA, 22–26 October 2012; pp. 214–218. [Google Scholar]
- Bobee, B.B.; Robitaille, R. The use of the Pearson type 3 and log Pearson type 3 distributions revisited. Water Resour. Res. 1977, 13, 427–443. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).