A Survey of Internet of Things (IoT) Authentication Schemes †
Abstract
1. Introduction
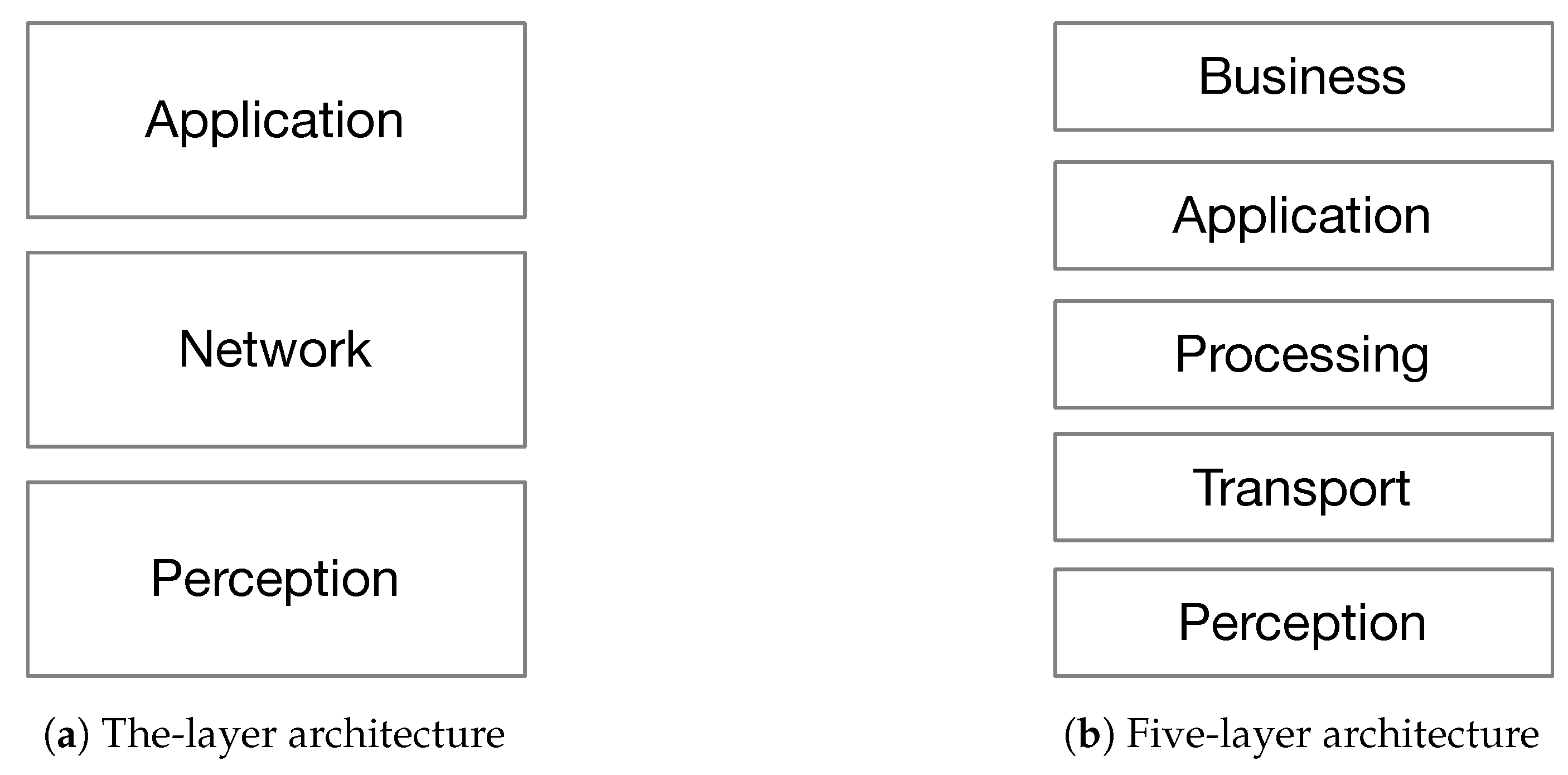
2. IoT Generic Architecture
- Perception layer: It is the physical layer that senses the environment to perceive the physical properties (e.g., temperature, humidity, speed, location, etc.) using end-nodes, through the use of different sensing technologies (e.g., RFID, GPS, NFC, etc.).
- Network Layer: It is the layer in charge of getting data from the perception layer and transmitting it to the application layer through various network technologies (e.g., 3G, 4G, 5G, Wi-Fi, Bluetooth, Zig-Bee, etc.). It is also responsible of data management from storing to processing with the help of middle-wares such as cloud computing.
- Processing layer: Also called the middle-ware layer, it is responsible of providing various types of services, mainly storing, analyzing, and processing data with respect to the computational results.
- Business layer: Its work covers the overall IoT system actions and functionality. The application layer sends the data to the business layer whose role is to build business models, graphs, and flowcharts to analyze data, in order to play a role in decision making about business strategies and road-maps.
3. Security Issues in IoT
3.1. Security Services
- Authentication: The process of confirming and insuring the identity of objects. In IoT context, each object should have the ability to identify and authenticate all other objects in the system (or in a given part of the system with which it interacts).
- The authorization: The process of giving permission to an entity to do or have something [28].
- Integrity: The way toward keeping up the consistency, precision and dependability of information over its whole life cycle. In IoT, the alteration of basic information or even the infusion of invalid information could prompt major issues, e.g., in smart health systems use cases it could lead to the death of the patient [29].
- Confidentiality: The process of ensuring that the information is only accessed by authorized people. Two main issues should be considered [27] regarding confidentiality in IoT: firstly, to ensure that the object receiving the data is not going to move/transfer these data to other objects and, secondly, to consider the data management.
- Non-repudiation: The way toward guaranteeing the ability to demonstrate that a task or event has occurred (and by whom), with the goal that this cannot be denied later. In other words, the object cannot deny the authenticity of a specific data transferred.
- Availability: The process of ensuring that the service needed is available anywhere and anytime for the intended users. This includes in IoT, the availability of the objects themselves.
- Privacy: The process of ensuring non-accessibility to private information by public or malicious objects [30].
3.2. Security Challenges in IoT Layers
3.2.1. Perception Layer Security Issues and Requirements
- Node Capture: Nodes (base node or gateway) can be easily controlled by the attackers. Catching a node empowers an adversary not only to get tightly of cryptographic keys and protocol states, but also to clone and redistribute malicious nodes in the network, which affects the security of the entire network [32,33].
- Denial of Service (DoS) Attack: A type of attacks that shuts down the system or network and prevents authorized users from accessing it. This could be achieved by overwhelming the system or network with large amount of spam requests all at the same time, thus overloading the system and preventing it from delivering the normal service [34].
- Denial of Sleep Attack: One of the essential objective of an IoT network is the capability of sensing through an extensive number of distributed nodes, each providing small data, such as temperature, humidity, vibration, etc. at a set interval and then going to sleep for another time interval in order to allow the nodes to operate for long service life. The denial of sleep attack works on the power supply of the node with a significant goal to increase the power consumption in order to reduce the service lifetime of the node by preventing the node from going asleep after sending the appropriate sensed data [35,36].
- Distributed Denial of Service (DDoS) Attack: A large scale variant of DoS attacks. The most challenging issue is the ability to use the large amount of IoT nodes to pass traffic collected toward the victim server [37,38]. There are indications that the DDoS attack called “Mirai” [5,6] occuring on October 2016 benefited from a large number of IoT nodes.
- Fake Node/Sybil Attack: A type of attacks where the attacker can deploy fake identities using fake nodes. With the presence of a sybil node, the whole system might generate wrong data or even the neighbor nodes will receive spam data and will mislay their privacy [39,40]. The fake nodes could be used to transmit data to “legitimate” nodes leading them to consume their energy, which could lead the whole service to go down.
- Routing Threats: This type of attacks is the most fundamental attack at the network layer but it could occur at the perception layer in data forwarding process. An attacker can create a routing loop causing the shortage or extension of the routing path, increasing the end-to-end delay, and increasing the error messages [43].
- Side-Channel Attack: This type of attacks occurs on encryption devices by taking advantage of the hardware information where the crypto-system is applied on (chips), such as the execution time, power consumption, power dissipation, and electromagnetic interference produced by electronic devices throughout the encryption procedure. Such information could be analyzed to discover secret keys used during the encryption process [44,45,46,47].
- Mass Node Authentication: The process of authenticating large amount of devices in an IoT system, which requires massive amount of network communication for the authentication phase to finish and this could affect the performance of the whole system.
3.2.2. Network Layer Security Issues and Requirements
- Man-in-the-Middle (MITM): According to McAfee [6], the most recurrent attacks are Denial of Service (DoS) and Man In the Browser (MITB) attacks. This latter, along with the Secure Socket Layer (SSL) attack, which enables attackers to listen to traffic, intercept it, and spoof both ends of the data, constitute the MITM attack [48,49].
- Eavesdropping/sniffing: This type of passive attacks gives the intruder the ability to listen to the private communication over the communication link [52]. The intruder might be able to extract useful information such as usernames and passwords, node identification or node configuration, which could lead to other types of attacks, e.g., fake node, replay attack, etc.
- Routing attacks: This type of attacks affects how the messages or data are routed. The intruder spoofs, redirects, misdirects or even drops packets at the network layer. The following specific attacks could be considered:
- (a)
- Black Hole: It can also be considered as a DoS attack, in which the intruder uses a fake node that welcomes all traffic by asserting that it has the shortest path. As a result, all traffic will be redirected to the fake node that has the ability to redirect them to a proxy server or even drop them [53].
- (b)
- (c)
- Worm Hole: In this type of attacks, the intruder creates a connection between two points in the network by either controlling at least two nodes of the network or adding new fake nodes to the network. After forming the link, the intruder collects data from one end and replays them to the other end [56,57].
- (d)
- Hello Flood: The aim of the attacker in this type of attacks is to consume the power of nodes in the system by broadcasting Hello request packets by a fake node to influence all the nodes in the system that they are in the same range, thus causing each one to send packets to its neighbor causing a huge traffic in the network [58,59,60]. (hello messages are defined in some routing protocols, so that nodes announce themselves to their neighbors.)
- (e)
- Sybil: In this attack, a fake node presents multiple identities, thus it can control a considerable part of the framework by being in different places within the network at the same time. When l many sybil nodes are within the same network, they will then send a large amount of information denying the normal nodes from using the network [61].
3.2.3. Application Layer Security Issues and Requirements
- Data Accessibility and Authentication: Each application might have many users [64]. Fake or illegal users could have a great impact on the availability of the whole system. Such great number of users means different permission and access control.
- Data privacy and identity: The fact that IoT connects different devices from different manufacturers leads to the application of different authentication schemes. The integration of these schemes is a challenging issue to ensure data privacy and identity.
- Dealing with the Availability of Big data: IoT connects a huge number of end devices, which leads to a huge amount of data to be managed. This causes an overhead on the application to analyze this data, which has a big impact on the availability of the service(s) provided by the application.
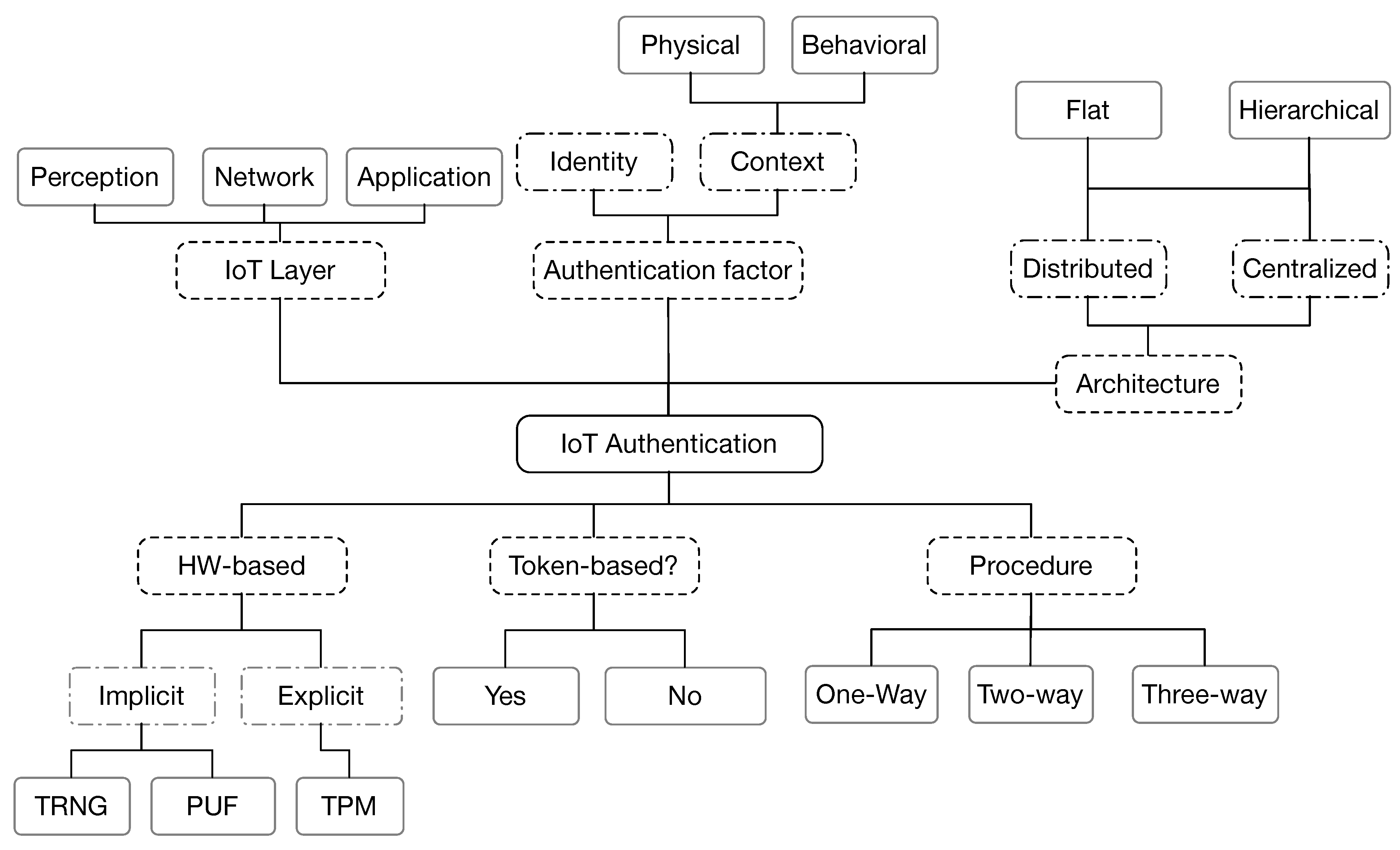
4. Taxonomy of IoT Authentication Schemes
- Authentication factor
- Identity: An information presented by one party to another to authenticate itself. Identity-based authentication schemes can use one (or a combination) of hash, symmetric or asymmetric cryptographic algorithms.
- Context: which can be:
- -
- Physical: Biometric information based on physical characteristics of an individual, e.g., fingerprints, hand geometry, retinal scans, etc.
- -
- Behavioral: Biometric based on behavioral characteristics of an individual, e.g., keystroke dynamics (pattern of rhythm and timing created when a person types), gait analysis (method used to assess the way we walk or run), voice ID (voice authentication that uses voice-print), etc.
- Use of tokens
- Authentication procedure
- One-way authentication: In a scenario of two parties wishing to communicate with each other, only one party will authenticate itself to the other, while the other one remains unauthenticated.
- Two-way authentication: It is also called mutual authentication, in which both entities authenticate each other.
- Three-way authentication: Where a central authority authenticates the two parties and helps them to mutually authenticate themselves.
- Authentication architecture
- Distributed: Using a distributed straight authentication method between the communicating parties.
- Centralized: Using a centralized server or a trusted third party to distribute and manage the credentials used for authentication.
Whether centralized or distributed, the authentication scheme architecture can be:- Hierarchical: Utilizing a multi-level architecture to handle the authentication procedure.
- Flat: No hierarchical architecture is used to deal with the authentication procedure.
- IoT layer: Indicates the layer at which the authentication procedure is applied.
- Perception layer: Responsible for collecting, processing, and digitizing information perceived data by the end nodes in IoT platform.
- Network layer: Responsible for receiving the perceived data from perception layer and processing it.
- Application layer: Responsible for receiving data from the network layer, and then providing services requested by users.
- Hardware-based: The authentication process might require the use of physical characteristics of the hardware or the hardware itself.
- Implicit hardware-based: Uses the physical characteristics of the hardware to enhance the authentication such as Physical Unclonable Function (PUF) or True Random Number Generator (TRNG).
- Explicit hardware-based: Some authentication schemes are based on the use of a Trusted Platform Module (TPM), a chip (hardware) that stores and processes the keys used for hardware authentication.
5. Analysis of IoT Authentication Schemes
5.1. Smart Grids
5.2. RFID and NFC-Based Applications
5.3. Vehicular Networks
5.4. Smart Homes
5.5. Wireless Sensor Networks
5.6. Mobile Network and Applications
5.7. Generic IoT Applications
- IoT Layer: A, Application; N, Network; P, Perception.
- Procedure: 1, One-way; 2, Two-way; 3, Three-way.
- Architecture: C, Centralized; D, Distributed; F, Flat; H, Hierarchical.
- Hardware-Based: I, Implicit; E, Explicit.
6. Related Works
7. Conclusions
- In sensor-based applications, where sensors (constrained in terms of memory, processing power, battery, etc.) are the main end-devices, the proposed protocols must be lightweight, making a trade-off between power consumption and security.
- The robustness of authentication protocols against potential attacks, e.g., sybil, node capture, replay, password guessing, message forgery, brute force, man-in-the-middle, DoS, collision, chosen-plaintext, etc. should be considered and analyzed. In particular, it is important to to consider Distributed Denial of Service attacks (second attack against IoT in 2017 as per [6]).
- There is a need to consider location and identity privacy in certain IoT applications especially smart grids and VANETs.
- The communication overhead of authentication protocols is a key factor, especially when dealing with power-limited devices; the number of messages exchanged between authentication parties should be kept as low as possible. In the same context, the size of the messages should be as small as possible due to the restricted bandwidth of the wireless communication protocols used.
- Low computation cost should be considered while designing IoT authentication schemes especially for power-constrained and processing-limited IoT environment. This emphasizes the need to adopt lightweight cryptographic algorithms and protocols while designing authentication solutions.
- IoT authentication scheme should be scalable in the sense that it should manage large number of nodes s well as have the ability to add new nodes without any further setup or configuration.
- Authentication service should be ensured for the three layers of IoT architecture (application, network and perception layer).
- Heterogeneity of devices in IoT networks must be taken into consideration while designing IoT authentication schemes.
- Hardware security using “PUF” is the current trend due to its advantages over software security approaches. A combination between software solutions (lower cost) and hardware solutions (more secure) should be considered.
Author Contributions
Funding
Conflicts of Interest
References
- El-hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Analysis of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–3. [Google Scholar]
- El-hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Taxonomy of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 IEEE 15th Student Conference on Research and Development (SCOReD), Putrajaya, Malaysia, 13–14 December 2017; pp. 67–71. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Maresch, D.; Gartner, J. Make disruptive technological change happen—The case of additive manufacturing. Technol. Forecast. Soc. Chang. 2018. [Google Scholar] [CrossRef]
- Ahmed, M.E.; Kim, H. DDoS Attack Mitigation in Internet of Things Using Software Defined Networking. In Proceedings of the 2017 IEEE Third International Conference on Big Data Computing Service and Applications (BigDataService), San Francisco, CA, USA, 6–9 April 2017. [Google Scholar]
- McAfee. McAfee Labs Threats Report; Technical Report; McAfee: Santa Clara, CA, USA, 2017. [Google Scholar]
- Hern, A. Hacking risk leads to recall of 500,000 pacemakers due to patient death fears. The Guardian, 31 August 2017. [Google Scholar]
- Liu, R.; Wang, J. Internet of Things: Application and Prospect. In MATEC Web of Conferences; Zhao, L., Xavior, A., Cai, J., You, L., Eds.; EDP Sciences France: Les Ulis, France, 2017; Volume 100, p. 02034. [Google Scholar]
- Taynitskiy, V.; Gubar, E.; Zhu, Q. Optimal impulse control of bi-virus SIR epidemics with application to heterogeneous Internet of Things. In Proceedings of the 2017 Constructive Nonsmooth Analysis and Related Topics (CNSA), St. Petersburg, Russia, 22–27 May 2017. [Google Scholar]
- Rajakumari, S.; Azhagumeena, S.; Devi, A.B.; Ananthi, M. Upgraded living think-IoT and big data. In Proceedings of the 2017 2nd International Conference on Computing and Communications Technologies (ICCCT), Chennai, India, 23–24 February 2017. [Google Scholar]
- Dineshkumar, P.; SenthilKumar, R.; Sujatha, K.; Ponmagal, R.; Rajavarman, V. Big data analytics of IoT based Health care monitoring system. In Proceedings of the 2016 IEEE Uttar Pradesh Section International Conference on Electrical, Computer and Electronics Engineering (UPCON), Varanasi, India, 9–11 December 2016. [Google Scholar]
- Shang, W.; Yu, Y.; Droms, R.; Zhang, L. Challenges in IoT Networking via TCP/IP Architecture. Technical Report 04, NDN, Technical Report NDN-0038; Named Data Networking. Available online: http://named-data.net/techreports.html (accessed on 10 Augest 2018).
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 2012 10th International Conference on Frontiers of Information Technology, Islamabad, India, 17–19 December 2012. [Google Scholar]
- Weyrich, M.; Ebert, C. Reference Architectures for the Internet of Things. IEEE Softw. 2016, 33, 112–116. [Google Scholar] [CrossRef]
- Bauer, M.; Boussard, M.; Bui, N.; Loof, J.D.; Magerkurth, C.; Meissner, S.; Nettsträter, A.; Stefa, J.; Thoma, M.; Walewski, J.W. IoT Reference Architecture. In Enabling Things to Talk; Springer: Berlin/Heidelberg, Germany, 2013; pp. 163–211. [Google Scholar]
- Mashal, I.; Alsaryrah, O.; Chung, T.Y.; Yang, C.Z.; Kuo, W.H.; Agrawal, D.P. Choices for interaction with things on Internet and underlying issues. Ad Hoc Netw. 2015, 28, 68–90. [Google Scholar] [CrossRef]
- Said, O.; Masud, M. Towards Internet of things: Survey and future vision. Int. J. Comput. Netw. 2013, 5, 1–17. [Google Scholar]
- Wu, M.; Lu, T.J.; Ling, F.Y.; Sun, J.; Du, H.Y. Research on the architecture of Internet of Things. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010. [Google Scholar]
- Nastase, L. Security in the Internet of Things: A Survey on Application Layer Protocols. In Proceedings of the 21st International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania, 29–31 May 2017; pp. 659–666. [Google Scholar]
- Wang, F.; Hu, L.; Zhou, J.; Zhao, K. A data processing middleware based on SOA for the Internet of things. J. Sens. 2015, 2015, 827045. [Google Scholar] [CrossRef]
- Spiess, P.; Karnouskos, S.; Guinard, D.; Savio, D.; Baecker, O.; de Souza, L.M.S.; Trifa, V. SOA-Based Integration of the Internet of Things in Enterprise Services. In Proceedings of the 2009 IEEE International Conference on Web Services, Los Angeles, CA, USA, 6–10 July 2009. [Google Scholar]
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef]
- Hernandez, G.; Arias, O.; Buentello, D.; Jin, Y. Smart Nest Thermostat: A Smart Spy in Your Home; Black Hat USA: Las Vegas, NV, USA, 2014. [Google Scholar]
- Trappe, W.; Howard, R.; Moore, R.S. Low-energy security: Limits and opportunities in the Internet of things. IEEE Secur. Privacy 2015, 13, 14–21. [Google Scholar] [CrossRef]
- Husamuddin, M.; Qayyum, M. Internet of Things: A study on security and privacy threats. In Proceedings of the 2017 2nd International Conference on Anti-Cyber Crimes (ICACC), Abha, Saudi Arabia, 26–27 March 2017. [Google Scholar]
- El Mouaatamid, O.; Lahmer, M.; Belkasmi, M. Internet of Things Security: Layered classification of attacks and possible Countermeasures. Electron. J. Inf. Technol. 2016, 9, 24–37. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015. [Google Scholar]
- Jung, S.W.; Jung, S. Personal OAuth authorization server and push OAuth for Internet of Things. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Abomhara, M.; Koien, G.M. Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things—New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Wen, Q.; Dong, X.; Zhang, R. Application of dynamic variable cipher security certificate in Internet of Things. In Proceedings of the 2012 IEEE 2nd International Conference on Cloud Computing and Intelligence Systems, Hangzhou, China, 30 October–1 November 2012. [Google Scholar]
- Zhu, B.; Addada, V.G.K.; Setia, S.; Jajodia, S.; Roy, S. Efficient Distributed Detection of Node Replication Attacks in Sensor Networks. In Proceedings of the Twenty-Third Annual Computer Security Applications Conference (ACSAC 2007), Miami Beach, FL, USA, 10–14 December 2007. [Google Scholar]
- Parno, B.; Perrig, A.; Gligor, V. Distributed detection of node replication attacks in sensor networks. In Proceedings of the 2005 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 8–11 May 2005; pp. 49–63. [Google Scholar]
- Anirudh, M.; Thileeban, S.A.; Nallathambi, D.J. Use of honeypots for mitigating DoS attacks targeted on IoT networks. In Proceedings of the 2017 International Conference on Computer, Communication and Signal Processing (ICCCSP), Chennai, India, 10–11 January 2017. [Google Scholar]
- Capossele, A.T.; Cervo, V.; Petrioli, C.; Spenza, D. Counteracting Denial-of-Sleep Attacks in Wake-Up-Radio-Based Sensing Systems. In Proceedings of the 2016 13th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), London, UK, 27–30 June 2016. [Google Scholar]
- Uher, J.; Mennecke, R.G.; Farroha, B.S. Denial of Sleep attacks in Bluetooth Low Energy wireless sensor networks. In Proceedings of the 2016 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 1–3 November 2016. [Google Scholar]
- Machaka, P.; Bagula, A.; Nelwamondo, F. Using exponentially weighted moving average algorithm to defend against DDoS attacks. In Proceedings of the 2016 Pattern Recognition Association of South Africa and Robotics and Mechatronics International Conference (PRASA-RobMech), Stellenbosch, South Africa, 30 November–2 December 2016. [Google Scholar]
- Pacheco, L.A.B.; Gondim, J.J.C.; Barreto, P.A.S.; Alchieri, E. Evaluation of Distributed Denial of Service threat in the Internet of Things. In Proceedings of the 2016 IEEE 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016. [Google Scholar]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Int. Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Evangelista, D.; Mezghani, F.; Nogueira, M.; Santos, A. Evaluation of Sybil attack detection approaches in the Internet of Things content dissemination. In Proceedings of the 2016 Wireless Days (WD), Toulouse, France, 23–25 March 2016. [Google Scholar]
- Na, S.; Hwang, D.; Shin, W.; Kim, K.H. Scenario and countermeasure for replay attack using join request messages in LoRaWAN. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017. [Google Scholar]
- Tomasin, S.; Zulian, S.; Vangelista, L. Security Analysis of LoRaWAN Join Procedure for Internet of Things Networks. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. A Lightweight Trust Design for IoT Routing. In Proceedings of the 2016 IEEE 14th Intl Conf on Dependable, Autonomic and Secure Computing, 14th Intl Conf on Pervasive Intelligence and Computing, 2nd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress(DASC/PiCom/DataCom/CyberSciTech), Auckland, New Zealand, 8–12 August 2016. [Google Scholar]
- Pammu, A.A.; Chong, K.S.; Ho, W.G.; Gwee, B.H. Interceptive side channel attack on AES-128 wireless communications for IoT applications. In Proceedings of the 2016 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Jeju, Korea, 25–28 October 2016. [Google Scholar]
- Choi, J.; Kim, Y. An improved LEA block encryption algorithm to prevent side-channel attack in the IoT system. In Proceedings of the 2016 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA), Jeju, Korea, 13–16 December 2016. [Google Scholar]
- Shahverdi, A.; Taha, M.; Eisenbarth, T. Lightweight Side Channel Resistance: Threshold Implementations of S imon. IEEE Trans. Comput. 2017, 66, 661–671. [Google Scholar] [CrossRef]
- Tawalbeh, L.A.; Somani, T.F. More secure Internet of Things using robust encryption algorithms against side channel attacks. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016. [Google Scholar]
- Čekerevac, Z.; Dvorak, Z.; Prigoda, L.; Čekerevac, P. Man in the Middle Attacks and the Internet of Things—Security and economic risks. FBIM Trans. 2017, 5, 25–35. [Google Scholar] [CrossRef]
- Burkholder, P. SSL Man-in-the-Middle Attacks; The SANS Institute: Swansea, UK, 2002. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Securing RPL routing protocol from blackhole attacks using a trust-based mechanism. In Proceedings of the 2016 26th International Telecommunication Networks and Applications Conference (ITNAC), Dunedin, New Zealand, 7–9 December 2016. [Google Scholar]
- Glissa, G.; Rachedi, A.; Meddeb, A. A Secure Routing Protocol Based on RPL for Internet of Things. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Mukherjee, A. Physical-Layer Security in the Internet of Things: Sensing and Communication Confidentiality Under Resource Constraints. Proc. IEEE 2015, 103, 1747–1761. [Google Scholar] [CrossRef]
- Tseng, F.H.; Chou, L.D.; Chao, H.C. A survey of black hole attacks in wireless mobile ad hoc networks. Hum.-Centric Comput. Inf. Sci. 2011, 1, 4. [Google Scholar] [CrossRef]
- Gurung, S.; Chauhan, S. Performance analysis of black-hole attack mitigation protocols under gray-hole attacks in MANET. Wirel. Netw. 2017, 25, 1–14. [Google Scholar] [CrossRef]
- Xiaopeng, G.; Wei, C. A Novel Gray Hole Attack Detection Scheme for Mobile Ad-Hoc Networks. In Proceedings of the 2007 IFIP International Conference on Network and Parallel Computing Workshops (NPC 2007), Liaoning, China, 18–21 September 2007. [Google Scholar]
- Meghdadi, M.; Ozdemir, S.; Güler, I. A Survey of Wormhole-based Attacks and their Countermeasures in Wireless Sensor Networks. IETE Tech. Rev. 2011, 28, 89. [Google Scholar] [CrossRef]
- Ahmed, N.; Kanhere, S.S.; Jha, S. The holes problem in wireless sensor networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2005, 9, 4. [Google Scholar] [CrossRef]
- Diaz, A.; Sanchez, P. Simulation of Attacks for Security in Wireless Sensor Network. Sensors 2016, 16, 1932. [Google Scholar] [CrossRef] [PubMed]
- Singh, R.; Singh, J.; Singh, R. Cluster Head Authentication Technique against Hello Flood Attack in Wireless Sensor Networks. Int. J. Comput. Appl. 2016, 156, 43–49. [Google Scholar] [CrossRef]
- Pathan, A.; Lee, H.W.; Hong, C.S. Security in wireless sensor networks: Issues and challenges. In Proceedings of the 2006 8th International Conference Advanced Communication Technology, Phoenix Park, Korea, 20–22 February 2006. [Google Scholar]
- Sharma, S.; Sharma, S. A defensive timestamp approach to detect and mitigate the Sybil attack in vanet. In Proceedings of the 2016 2nd International Conference on Contemporary Computing and Informatics (IC3I), Noida, India, 14–17 December 2016. [Google Scholar]
- Hari, P.B.; Singh, S.N. Security issues in Wireless Sensor Networks: Current research and challenges. In Proceedings of the 2016 International Conference on Advances in Computing, Communication, & Automation (ICACCA) (Spring), Dehradun, India, 8–9 April 2016. [Google Scholar]
- Hedi, I.; Speh, I.; Sarabok, A. IoT network protocols comparison for the purpose of IoT constrained networks. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017. [Google Scholar]
- Manyika, J.; Chui, M.; Bisson, P.; Woetzel, J.; Dobbs, R.; Bughin, J.; Aharon, D. Unlocking the Potential of the Internet of Things; McKinsey Global Institute: New York, NY, USA, 2015. [Google Scholar]
- Chae, C.J.; Choi, K.N.; Choi, K.; Yae, Y.H.; Shin, Y. The Extended Authentication Protocol using E-mail Authentication in OAuth 2.0 Protocol for Secure Granting of User Access. J. Internet Comput. Serv. 2015, 16, 21–28. [Google Scholar] [CrossRef]
- Emerson, S.; Choi, Y.K.; Hwang, D.Y.; Kim, K.S.; Kim, K.H. An OAuth based authentication mechanism for IoT networks. In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 28–30 October 2015. [Google Scholar]
- Blazquez, A.; Tsiatsis, V.; Vandikas, K. Performance evaluation of openid connect for an iot information marketplace. In Proceedings of the 2015 IEEE 81st IEEE Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–6. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brunig, M.; Carle, G. A DTLS based end-to-end security architecture for the Internet of Things with two-way authentication. In Proceedings of the 37th Annual IEEE Conference on Local Computer Networks—Workshops, Clearwater, FL, USA, 22–25 October 2012. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. DTLS based security and two-way authentication for the Internet of Things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Li, H.; Lu, R.; Zhou, L.; Yang, B.; Shen, X. An Efficient Merkle-Tree-Based Authentication Scheme for Smart Grid. IEEE Syst. J. 2014, 8, 655–663. [Google Scholar] [CrossRef]
- Li, D.; Aung, Z.; Williams, J.R.; Sanchez, A. Efficient authentication scheme for data aggregation in smart grid with fault tolerance and fault diagnosis. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012. [Google Scholar]
- Nicanfar, H.; Jokar, P.; Leung, V.C.M. Smart grid authentication and key management for unicast and multicast communications. In Proceedings of the 2011 IEEE PES Innovative Smart Grid Technologies, Perth, WA, Australia, 13–16 November 2011. [Google Scholar]
- Chim, T.; Yiu, S.; Hui, L.C.; Li, V.O. PASS: Privacy-preserving authentication scheme for smart grid network. In Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011. [Google Scholar]
- Fouda, M.M.; Fadlullah, Z.M.; Kato, N.; Lu, R.; Shen, X. Towards a light-weight message authentication mechanism tailored for Smart Grid communications. In Proceedings of the 2011 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Shanghai, China, 10–15 April 2011. [Google Scholar]
- Nicanfar, H.; Jokar, P.; Beznosov, K.; Leung, V.C.M. Efficient Authentication and Key Management Mechanisms for Smart Grid Communications. IEEE Syst. J. 2014, 8, 629–640. [Google Scholar] [CrossRef]
- Wu, T. The Secure Remote Password Protocol. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 11–13 March 1998; Volume 98, pp. 97–111. [Google Scholar]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H.; Shon, T.; Ahmad, H.F. A lightweight message authentication scheme for Smart Grid communications in power sector. Comput. Electr. Eng. 2016, 52, 114–124. [Google Scholar] [CrossRef]
- Ji, C.; Kim, J.; Lee, J.Y.; Hong, M. Review of one-time signatures for multicast authentication in smart grid. In Proceedings of the 2015 12th International Conference & Expo on Emerging Technologies for a Smarter World (CEWIT), Melville, NY, USA, 19–20 October 2015. [Google Scholar]
- Chim, T.W.; Yiu, S.M.; Li, V.O.; Hui, L.C.; Zhong, J. PRGA: Privacy-preserving recording & gateway-assisted authentication of power usage information for smart grid. IEEE Trans. Dependable Secur. Comput. 2015, 12, 85–97. [Google Scholar]
- Li, Q.; Cao, G. Multicast Authentication in the Smart Grid With One-Time Signature. IEEE Trans. Smart Grid 2011, 2, 686–696. [Google Scholar] [CrossRef]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef] [PubMed]
- Yang, K.; Forte, D.; Tehranipoor, M.M. Protecting endpoint devices in IoT supply chain. In Proceedings of the 2015 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 2–6 November 2015. [Google Scholar]
- Lee, J.Y.; Lin, W.C.; Huang, Y.H. A lightweight authentication protocol for Internet of Things. In Proceedings of the 2014 International Symposium on Next-Generation Electronics (ISNE), Kwei-Shan, Taiwan, 7–10 May 2014. [Google Scholar]
- Tuyls, P.; Batina, L. RFID-Tags for Anti-counterfeiting. In Topics in Cryptology—CT-RSA 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 115–131. [Google Scholar]
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Brian, A.L.A.; Arockiam, L.; Malarchelvi, P. An IOT based secured smart library system with NFC based book tracking. Int. J. Emerg. Technol. Comput. Sci. Electron. 2014, 11, 18–21. [Google Scholar]
- Fan, K.; Gong, Y.; Liang, C.; Li, H.; Yang, Y. Lightweight and ultralightweight RFID mutual authentication protocol with cache in the reader for IoT in 5G. Secur. Commun. Netw. 2016, 9, 3095–3104. [Google Scholar] [CrossRef]
- Fan, K.; Song, P.; Yang, Y. ULMAP: Ultralightweight NFC mutual authentication protocol with pseudonyms in the tag for IoT in 5G. Mob. Inf. Syst. 2017, 2017, 2349149. [Google Scholar] [CrossRef]
- Chan, A.C.F.; Zhou, J. Cyber–physical device authentication for the smart grid electric vehicle ecosystem. IEEE J. Sel. Areas Commun. 2014, 32, 1509–1517. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Hu, C. Distributed Aggregate Privacy-Preserving Authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2017, 18, 516–526. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, C.; Wu, Q.; Domingo-Ferrer, J.; Qin, B. Privacy-preserving vehicular communication authentication with hierarchical aggregation and fast response. IEEE Trans. Comput. 2016, 65, 2562–2574. [Google Scholar] [CrossRef]
- Lyu, C.; Gu, D.; Zeng, Y.; Mohapatra, P. PBA: Prediction-Based Authentication for Vehicle-to-Vehicle Communications. IEEE Trans. Dependable Secur. Comput. 2016, 13, 71–83. [Google Scholar] [CrossRef]
- Lalli, M.; Graphy, G.S. Prediction based dual authentication model for VANET. In Proceedings of the 2017 International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 18–19 July 2017. [Google Scholar]
- Rekik, M.; Meddeb-Makhlouf, A.; Zarai, F.; Obaidat, M.S. Improved Dual Authentication and Key Management Techniques in Vehicular Ad Hoc Networks. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017. [Google Scholar]
- Roberts, B.; Akkaya, K.; Bulut, E.; Kisacikoglu, M. An Authentication Framework for Electric Vehicle-to-Electric Vehicle Charging Applications. In Proceedings of the 2017 IEEE 14th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Orlando, FL, USA, 22–25 October 2017. [Google Scholar]
- Tangade, S.; Manvi, S.S. Scalable and privacy-preserving authentication protocol for secure vehicular communications. In Proceedings of the 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bangalore, India, 6–9 November 2016. [Google Scholar]
- Waghmode, R.; Gonsalves, R.; Ambawade, D. Security enhancement in group based authentication for VANET. In Proceedings of the 2016 IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 20–21 May 2016. [Google Scholar]
- Shao, J.; Lu, R.; Lin, X.; Zuo, C. New threshold anonymous authentication for VANETs. In Proceedings of the 2015 IEEE/CIC International Conference on Communications in China (ICCC), Shenzhen, China, 2–4 November 2015. [Google Scholar]
- Shao, J.; Lin, X.; Lu, R.; Zuo, C. A Threshold Anonymous Authentication Protocol for VANETs. IEEE Trans. Veh. Technol. 2016, 65, 1711–1720. [Google Scholar] [CrossRef]
- Dolev, S.; Krzywiecki, Ł; Panwar, N.; Segal, M. Vehicle authentication via monolithically certified public key and attributes. Wirel. Netw. 2015, 22, 879–896. [Google Scholar] [CrossRef]
- Kumar, A.; Prakash, A.; Sharma, S.; Jyoti, K. Vehicle authentication and message hiding protocol for vehicle to vehicle communication. In Proceedings of the 2015 1st International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 4–5 September 2015. [Google Scholar]
- Cespedes, S.; Taha, S.; Shen, X. A Multihop-Authenticated Proxy Mobile IP Scheme for Asymmetric VANETs. IEEE Trans. Veh. Technol. 2013, 62, 3271–3286. [Google Scholar] [CrossRef]
- Huth, C.; Zibuschka, J.; Duplys, P.; Guneysu, T. Securing systems on the Internet of Things via physical properties of devices and communications. In Proceedings of the 2015 Annual IEEE Systems Conference (SysCon) Proceedings, Vancouver, BC, Canada, 13–16 April 2015. [Google Scholar]
- Sun, X.; Men, S.; Zhao, C.; Zhou, Z. A security authentication scheme in machine-to-machine home network service. Secur. Commun. Netw. 2012, 8, 2678–2686. [Google Scholar] [CrossRef]
- Zhao, M.; Yao, X.; Liu, H.; Ning, H. Physical Unclonable Function Based Authentication Protocol for Unit IoT and Ubiquitous IoT. In Proceedings of the 2016 International Conference on Identification, Information and Knowledge in the Internet of Things (IIKI), Beijing, China, 20–21 October 2016. [Google Scholar]
- Muhal, M.A.; Luo, X.; Mahmood, Z.; Ullah, A. Physical Unclonable Function Based Authentication Scheme for Smart Devices in Internet of Things. In Proceedings of the 2018 IEEE International Conference on Smart Internet of Things (SmartIoT), Xi’an, China, 17–19 August 2018; pp. 160–165. [Google Scholar]
- Jan, M.A.; Khan, F.; Alam, M.; Usman, M. A payload-based mutual authentication scheme for Internet of Things. Future Gen. Comput. Syst. 2019, 92, 1028–1039. [Google Scholar] [CrossRef]
- Hammi, M.T.; Livolant, E.; Bellot, P.; Serhrouchni, A.; Minet, P. A Lightweight Mutual Authentication Protocol for the IoT. In Mobile and Wireless Technologies 2017; Springer: Singapore, 2017; pp. 3–12. [Google Scholar]
- Du, W.; Deng, J.; Han, Y.S.; Varshney, P.K.; Katz, J.; Khalili, A. A pairwise key predistribution scheme for wireless sensor networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 228–258. [Google Scholar] [CrossRef]
- Liu, D.; Ning, P.; Li, R. Establishing pairwise keys in distributed sensor networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 41–77. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Netw. 2017, 54, 147–169. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, Y.; Moon, J.; Won, D. Security enhanced multi-factor biometric authentication scheme using bio-hash function. PLoS ONE 2017, 12, e0176250. [Google Scholar] [CrossRef] [PubMed]
- Schmitt, C.; Noack, M.; Stiller, B. TinyTO: Two-way authentication for constrained devices in the Internet of Things. In Internet of Things; Elsevier: Amsterdam, The Netherlands, 2016; pp. 239–258. [Google Scholar]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. Two-phase authentication protocol for wireless sensor networks in distributed IoT applications. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014. [Google Scholar]
- Fu, A.; Lan, S.; Huang, B.; Zhu, Z.; Zhang, Y. A Novel Group-Based Handover Authentication Scheme with Privacy Preservation for Mobile WiMAX Networks. IEEE Commun. Lett. 2012, 16, 1744–1747. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Arshad, H.; Khan, M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Future Gen. Comput. Syst. 2016, 63, 56–75. [Google Scholar] [CrossRef]
- Chung, Y.; Choi, S.; Lee, Y.; Park, N.; Won, D. An Enhanced Lightweight Anonymous Authentication Scheme for a Scalable Localization Roaming Service in Wireless Sensor Networks. Sensors 2016, 16, 1653. [Google Scholar] [CrossRef] [PubMed]
- Gope, P.; Hwang, T. A Realistic Lightweight Anonymous Authentication Protocol for Securing Real-Time Application Data Access in Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Ye, N.; Zhu, Y.; Wang, R.C.; Malekian, R.; Qiao-min, L. An Efficient Authentication and Access Control Scheme for Perception Layer of Internet of Things. Appl. Math. Inf. Sci. 2014, 8, 1617–1624. [Google Scholar] [CrossRef]
- Chu, F.; Zhang, R.; Ni, R.; Dai, W. An Improved Identity Authentication Scheme for Internet of Things in Heterogeneous Networking Environments. In Proceedings of the 2013 16th International Conference on Network-Based Information Systems, Gwangju, Korea, 4–6 September 2013. [Google Scholar]
- Kumar, P.; Lee, S.G.; Lee, H.J. E-SAP: Efficient-Strong Authentication Protocol for Healthcare Applications Using Wireless Medical Sensor Networks. Sensors 2012, 12, 1625–1647. [Google Scholar] [CrossRef] [PubMed]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Durairaj, M.; Muthuramalingam, K. A New Authentication Scheme with Elliptical Curve Cryptography for Internet of Things (IoT) Environments. Int. J. Eng. Technol. 2018, 7, 119–124. [Google Scholar] [CrossRef]
- Hamidi, H. An approach to develop the smart health using Internet of Things and authentication based on biometric technology. Future Gen. Comput. Syst. 2019, 91, 434–449. [Google Scholar] [CrossRef]
- Alotaibi, M. An Enhanced Symmetric Cryptosystem and Biometric-Based Anonymous User Authentication and Session Key Establishment Scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Computer Aided Verification; Etessami, K., Rajamani, S.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Lai, C.; Li, H.; Liang, X.; Lu, R.; Zhang, K.; Shen, X. CPAL: A Conditional Privacy-Preserving Authentication With Access Linkability for Roaming Service. IEEE Internet Things J. 2014, 1, 46–57. [Google Scholar] [CrossRef]
- Haddad, Z.J.; Taha, S.; Saroit, I.A. Anonymous authentication and location privacy preserving schemes for LTE-A networks. Egypt. Inform. J. 2017, 18, 193–203. [Google Scholar] [CrossRef]
- Lai, C.; Li, H.; Lu, R.; Shen, X.S. SE-AKA: A secure and efficient group authentication and key agreement protocol for LTE networks. Comput. Netw. 2013, 57, 3492–3510. [Google Scholar] [CrossRef]
- Lai, C.; Li, H.; Lu, R.; Jiang, R.; Shen, X. SEGR: A secure and efficient group roaming scheme for machine to machine communications between 3GPP and WiMAX networks. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014. [Google Scholar]
- Zhu, H.; Lin, X.; Zhang, Y.; Lu, R. Duth: A user-friendly dual-factor authentication for Android smartphone devices. Secur. Commun. Netw. 2014, 8, 1213–1222. [Google Scholar] [CrossRef]
- Sbeyti, H.; El Hage, B.; Fadlallah, A. Mobile user signature extraction based on user behavioural pattern (MUSEP). Int. J. Pervasive Comput. Commun. 2016, 12, 421–446. [Google Scholar] [CrossRef]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual Authentication in IoT Systems Using Physical Unclonable Functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Li, H.; Shen, X.S. GLARM: Group-based lightweight authentication scheme for resource-constrained machine to machine communications. Comput. Netw. 2016, 99, 66–81. [Google Scholar] [CrossRef]
- Chen, D.; Zhang, N.; Qin, Z.; Mao, X.; Qin, Z.; Shen, X.; Li, X. S2M: A Lightweight Acoustic Fingerprints based Wireless Device Authentication Protocol. IEEE Internet Things J. 2016, 4, 88–100. [Google Scholar] [CrossRef]
- Mukhopadhyay, D. PUFs as Promising Tools for Security in Internet of Things. IEEE Des. Test 2016, 33, 103–115. [Google Scholar] [CrossRef]
- Wallrabenstein, J.R. Practical and Secure IoT Device Authentication Using Physical Unclonable Functions. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016. [Google Scholar]
- Barbareschi, M.; Bagnasco, P.; Mazzeo, A. Authenticating IoT Devices with Physically Unclonable Functions Models. In Proceedings of the 2015 10th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC), Krakow, Poland, 4–6 November 2015. [Google Scholar]
- Singh, A.; Chatterjee, K. A secure multi-tier authentication scheme in cloud computing environment. In Proceedings of the 2015 International Conference on Circuits, Power and Computing Technologies [ICCPCT-2015], Nagercoil, India, 19–20 March 2015. [Google Scholar]
- Moghaddam, F.F.; Moghaddam, S.G.; Rouzbeh, S.; Araghi, S.K.; Alibeigi, N.M.; Varnosfaderani, S.D. A scalable and efficient user authentication scheme for cloud computing environments. In Proceedings of the 2014 IEEE REGION 10 SYMPOSIUM, Kuala Lumpur, Malaysia, 14–16 April 2014. [Google Scholar]
- Lu, J.Z.; Chen, T.; Zhou, J.; Yang, J.; Jiang, J. An enhanced biometrics-based remote user authentication scheme using smart cards. In Proceedings of the 2013 6th International Congress on Image and Signal Processing (CISP), Hangzhou, China, 16–18 December 2013. [Google Scholar]
- Pranata, I.; Athauda, R.I.; Skinner, G. Securing and Governing Access in Ad-Hoc Networks of Internet of Things. In Proceedings of the IASTED International Conference on Engineering and Applied Science, Colombo, Sri Lanka, 27–29 December 2012; pp. 84–90. [Google Scholar]
- Hong, N. A Security Framework for the Internet of Things Based on Public Key Infrastructure. Adv. Mater. Res. 2013, 671–674, 3223–3226. [Google Scholar] [CrossRef]
- Zhao, Y.L. Research on Data Security Technology in Internet of Things. Appl. Mech. Mater. 2013, 433–435, 1752–1755. [Google Scholar] [CrossRef]
- Frikken, K.B.; Blanton, M.; Atallah, M.J. Robust Authentication Using Physically Unclonable Functions. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 262–277. [Google Scholar]
- Qi, M.; Chen, J.; Chen, Y. A secure authentication with key agreement scheme using ECC for satellite communication systems. Int. J. Satellite Commun. Netw. 2018. [Google Scholar] [CrossRef]
- Alizai, Z.A.; Tareen, N.F.; Jadoon, I. Improved IoT Device Authentication Scheme Using Device Capability and Digital Signatures. In Proceedings of the 2018 International Conference on Applied and Engineering Mathematics (ICAEM), Taxila, Pakistan, 4–5 September 2018; pp. 1–5. [Google Scholar]
- Srinivasu, B.; Vikramkumar, P.; Chattopadhyay, A.; Lam, K.Y. CoLPUF: A Novel Configurable LFSR-based PUF. In Proceedings of the 2018 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Chengdu, China, 26–30 October 2018; pp. 358–361. [Google Scholar]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gen. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Karthikeyan, S.; Patan, R.; Balamurugan, B. Enhancement of Security in the Internet of Things (IoT) by Using X. 509 Authentication Mechanism. In Recent Trends in Communication, Computing, and Electronics; Springer: Singapore, 2019; pp. 217–225. [Google Scholar]
- Wu, Z.Q.; Zhou, Y.W.; Ma, J.F. A Security Transmission Model for Internet of Things. Chin. J. Comput. 2011, 34, 1351–1364. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for Internet of Things: A comprehensive survey. Secur. Commun. Netw. 2017, 2017, 6562953. [Google Scholar] [CrossRef]
- Saadeh, M.; Sleit, A.; Qatawneh, M.; Almobaideen, W. Authentication Techniques for the Internet of Things: A Survey. In Proceedings of the 2016 Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016. [Google Scholar]
- Joshitta, R.S.M.; Arockiam, L. Authentication in IoT Environment: A Survey. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2016, 6, 140–145. [Google Scholar]
- Sey, D. A survey on authentication methods for the Internet of Things. PeerJ Prepr. 2018, 6, e26474v1. [Google Scholar]
- Atwady, Y.; Hammoudeh, M. A survey on authentication techniques for the Internet of things. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; p. 8. [Google Scholar]
- Shaikh, M.M.; Jog, V. Survey on Providing Security and Authentication for Devices to Achieve QOS in IOT. Int. J. Sci. Res. 2016, 5, 342–344. [Google Scholar]
- e Silva, E.d.O.; de Lima, W.T.S.; Ferraz, F.S.; do Nascimento Ribeiro, F.I. Authentication and the Internet of Things: A Survey Based on a Systematic Mapping. In Proceedings of the Twelfth International Conference on Software Engineering Advances, Athens, Greece, 8–12 October 2017. [Google Scholar]
- Gebrie, M.T.; Abie, H. Risk-based adaptive authentication for Internet of things in smart home eHealth. In Proceedings of the 11th European Conference on Software Architecture: Companion Proceedings, Canterbury, UK, 11–15 September 2017; pp. 102–108. [Google Scholar]
- Bamasag, O.O.; Youcef-Toumi, K. Towards continuous authentication in Internet of things based on secret sharing scheme. In Proceedings of the WESS’15: Workshop on Embedded Systems Security, Amsterdam, The Netherlands, 4–9 October 2015. [Google Scholar]
| Layer | Security Requirements |
|---|---|
| Perception | Lightweight Encryption |
| Authentication | |
| Key Agreement | |
| Data Confidentiality | |
| Network | Communication Security |
| Routing Security | |
| Authentication | |
| Key Management | |
| Intrusion Detection | |
| Application | Authentication |
| Privacy protection | |
| Information Security Management |
| Ref# | IoT Layer | Identity Context Credentials | Token Based? | Proc. | Arch. | HW. | Strength(+)/Weakness(−) |
|---|---|---|---|---|---|---|---|
| [145] | A | Encryption | x | 2 | C/H | I | +Encapsulation is used to efficiently benefit from resources. |
| [69] | A + N | Encryption/RSA | x/DTLS | 2 | C/H | I | +Low overhead regarding computation and communication and high interoperability −Unreliability due to the use of UDP over DTLS leads to |
| [108] | P | Encryption/Symmetric asynchronous One Time Password (OTP) | x/TLS | 2 | C/H | I | +Resistance to some DoS and replay attacks. −Performance analysis is not considered. |
| [109] | N | Encryption/Symmetric | ✓(NodeID, Indices of space, and Seed) | 3 | D/H | I | +Resistance to node capture attack −Energy cost is not efficient. |
| [110] | N | Encryption/Symmetric | ✓(polynomialID) | 3 | D/H | I | +Resistance to node capture attack +Efficient with respect to communication overhead −No consideration to location privacy. |
| [143] | A + N | Encryption/Asymmetric | ✓(Information) | 2 | D/H | I | +Resistance to Malicious entity by using PKI −Performance analysis is not considered |
| [144] | A + N | Encryption/Asymmetric | ✓(FormId) | 2 | C/H | I | +Compatibility problems are solved −Performance analysis is not considered. |
| [153] | A + N + P | Encryption/Symmetric | ✓(IP/EPC) | 2 | C/F | I | +Resilience to attacks, access control, client privacy and data confidentiality |
| [83] | N + P | Encryption/Symmetric using XOR | ✓(SpecificId) | 2 | C/F | I | +Authentication of RFID tags with readers −No consideration of location privacy. |
| [119] | N + P | Encryption/Symmetric + Hash + Credit card as context | ✓(Nonce) | 2 | C/H | E | +Resistance to Man-in-the-Middle, Impersonation, Replay, Privileged insider attacks, Stolen smart card, Smart card breach attacks, etc. −Communication cost is not efficient. |
| [120] | N + P | Encryption/Asymmetric using ECC | ✓(Identity, Elliptic curve function, and parameters) | 2 | C/H | I | +Resistance to Eavesdropping, DoS, Node capture, Replay and MITM attack −Attribute-based access control should be discussed in detailed manner. |
| [113] | A + N + P | Encryption/Asymmetric using RSA and ECC | x/DTLS | 2 | C/F | I | +Performance measurement is considered. +Resistance to MITM attack. −DoS and Replay attacks are not considered. |
| [114] | A + N + P | Encryption/Asymmetric using ECC | ✓(Identity) | 2 | D/F | I | +Resistance to malicious users and DoS attacks. −Not Efficient regarding the storage of the certificate. −Vulnerable to node capturing attack |
| [65,66] | A | N/A | ✓(OAuth2.0) | 1 | C/H | I | +Resistance to Impersonation and Replay attacks −No performance analysis is done. provided |
| [141] | A | Encryption: registered user with AES and non-registered users using Diffie–Hellman | x (username + password) | 1 | C/F | I | +Two separate servers for storing cryptography and authentication data, +Resistance to brute force, timing, and MITM −No performance analysis is done. |
| [82] | P | Encryption/Symmetric using AES | ✓ | 2 | C/H | I | +Resistance to split attacks (i.e., swapping tags, separating tag from product, etc.) −No analysis is done for location privacy. |
| [162] | A | No Encryption/Hash | ✓ | 1 | D/F | I | +Resistance to MITM, replay, DoS, and Eavesdropping attacks. −Storage cost is not efficient |
| [140] | A | Context/multiple credentials using physical context | x (User name + password) | Multiple authentication | D/H | I | +Resistance to replay attack −DoS attack is not considered |
| [142] | A | No Encryption/Hash 256 bits + context bio-metric | ✓(User Identity) | 2 | D/F | E | +Second-tier authentication is done at client side. +Resistance to attacks from inside the system. −No ability to change credentials in both the tiers. |
| [121] | A | Encryption/Asymmetric using ECC | ✓(UserId) | 2 | D/F | I | +Resistance to MITM and DoS attacks. −User must be authenticated many times in Multi-server environment. |
| [79] | A | Encryption/RSA + Hash SHA or MD5 | x | 2 | C/H | I | +Filtering of the messages at gateway +Privacy preservation is considered +Resistance to Brute force, DoS, and Replay attacks −DDoS is not considered. |
| [77] | A + N | Encryption/RSA + AES | x | 2 | D/F | I | +Resistance to Modification, Replay, and Message analysis attacks −No analysis done for location privacy |
| [111] | A + N | Encryption/Symmetric + Hashing | ✓ + x | 2 | C/F | I | +Resistance to Replay, Impersonation, Spoofing, and Gateway attacks. −Blackhole and Wormhole attacks are not studied |
| [135] | A + N + P | Encryption/Symmetric | ✓(Identity) | 2 | C/F | I | +Resistance to MITM and DoS attack −Identity and Location privacy is not considered |
| [130] | A + N + P | Encryption/Asymmetric using ECC | ✓(Identity) | 3 | C/F | I | +Resistance to redirection, malicious, Dos, and MITM attacks. −Location and Identity privacy is not analyzed and can not authenticate group of machines at the same time |
| [129] | N + P | Encryption/Asymmetric | ✓(Identity) | 2 | C/F | I | +Location privacy is analyzed +Low communication and computational cost. |
| [131] | N + P | Encryption/Asymmetric using ECC + Hashing | ✓(Identity) | 2 | C/F | I | +Group of end devices is authenticated at the same time −Location and Identity privacy are not analyzed and resistance to attacks are not studied |
| [136] | N + P | N/A | ✓(audio samples as an identity) | 2 | D/H | I | +Low error rate and resistance to audio replay, changing distance, and same type device attacks. −Location privacy is not analyzed |
| [115] | N + P | Encryption/Symmetric + Hashing + Asymmetric using ECC | ✓(Elliptic curve function) | 2 | C/F | I | +Privacy preservation is considered −Threat and attacks are not considered |
| [104] | A + N + P | Encryption/Symmetric(AES) + Hashing | ✓(user Identity) | 2 | C/F | I | +Resistance to guessing, impersonation, and replay attacks −Privacy preservation is not considered |
| [128] | N + P | Encryption/Symmetric + Asymmetric using Hybrid Linear Combination Encryption (HLCE) | ✓(user Identity) | 2 | C/F | I | +Resistance to DoS and impersonation, considers data integrity and ensures user privacy −Location privacy is not analyzed. |
| [132] | P | N/A | ✓(writing process) | 2 | C/H | I | +Improve security without adding any extra hardware −No analysis for threats and attacks is done. |
| [102] | A + N + P | Encryption/Symmetric | ✓(user Identity) | 2 | D/H | I | +Less location update.+Uses asymmetric links in VANET. +Resistance to MITM, replay, and DoS attacks −Privacy is not analyzed |
| [98,99] | N + P | Encryption/Symmetric + Asymmetric + Hashing | x | 3 | D/H | I | +Computation cost is efficient. +Resistance to the replay attack −No analysis is done to the communication overhead |
| [92] | N + P | Encryption/Symmetric+ Hashing | x | 2 | C/F | I | +Resistance to DoS attacks and to packet loss +Computation and storage overhead are low −Privacy preservation is not considered |
| [93] | N + P | Encryption/Symmetric+ Hashing | x | 2 | C/F | I | +Resistance to DoS attacks and to packet loss +Computation and storage overhead are low. −Privacy preservation is not considered |
| [101] | N + P | Encryption/Asymmetric using ECC | ✓(cover image) | 2 | C/H | I | +Error rate is considered and analyzed −The size of the cover image should be greater than or equal the size of the text message. Otherwise, the text message will be truncated −Attack analysis is not considered. |
| [94] | N + P | Encryption/Symmetric + Asymmetric + Hashing | ✓(Spanish eID cards) | 2 | C/H | E | +Resistance to replay, DDoS attacks and improve confidentiality and non-repudiation. +Computation and communication overhead is low +Location privacy is considered −Identity privacy is not considered |
| [95] | N + P | Encryption/Symmetric(AES) + Asymmetric (DH) + Hashing | ✓(transaction ID) | 2 | C/H | I | +No rely on third parties for shared key management, instead a DH based key exchange mechanism is used. +Resistance to impersonation and MITM attacks. −Identity privacy is not considered |
| [96] | N + P | Encryption/Symmetric + Asymmetric + Hashing | ✓(pseudo-identity (PsID)) | 2 | C/H | I | +Provides a node, message authentication, and privacy protection. +Computation and communication overhead is studied. −Identity privacy is not considered |
| [97] | N + P | Encryption/Symmetric(AES) + Asymmetric(ECDSA) + Hashing | ✓(pseudo-identity (PsID)) | 2 | C/F | I | +Security and privacy analysis is considered +Computation and communication overhead is considered −Identity privacy is not considered |
| [90] | N + P | Encryption/Asymmetric + Hashing | ✓(pseudo-identity (PsID)) | 2 | C/F | I | +Resistance to DoS, Replay, Sybil, and False message attacks. +Consider privacy preservation. −Non-repudiation attack is not considered |
| [91] | N + P | Encryption/symmetric + Hashing | ✓(identity) | 2 | C/H | I | +Resistance to Movement tracking, Replay, and Message modification attacks. −Location privacy is not considered |
| [100] | N + P | Encryption/Symmetric + Asymmetric + Hashing | No/TLS | 2 | C/F | I | +Resistance to Impersonation and MITM attacks. −Privacy is not considered |
| [89] | N + P | Encryption/Symmetric + Asymmetric + Hashing | x | 2 | C/F | I | +Resistance to Substitution attack (a kind of MITM attack). −No evaluation for message delay and verification delay |
| [80] | A + N + P | Encryption/Asymmetric + Hashing | x | 2 | C/F | I | +Efficient use of one-way hash +Resistance to message forging attacks+Reduce the storage −Increase the computation overhead although it is balanced between sender and receiver −Privacy is not considered. −Integrity and Confidentiality are not considered. |
| [78] | N + P | Encryption/Asymmetric + Hashing | x | 2 | C/F | I | −Increase the computation overhead although it is balanced between sender and receiver −Storage cost is high −The distribution of the public key via secure channel is done before the complete consumption of the hash chains. |
| [70] | N + P | Encryption/Symmetric + Asymmetric + Hashing | x | 2 | C/F | I | +Resistance to Message modification attacks, Replay, Message analysis, and message injection attacks. +Efficient with respect to computation and communication overhead. −Most of the routing attacks are not considered. |
| [71] | N + P | Encryption/Asymmetric + Hashing | x | 2 | C/F | I | +Computation and communication cost is efficient +Fault tolerance Architecture. −Attacks and threats analysis is not considered. |
| [72] | N + P | Encryption/Asymmetric + Hashing | ✓(Node ID) | 3 | C/F | I | +Resistance to DoS, MITM, Brute force and Replay attacks +Secure key management. +Computation and communication cost is efficient. −Confidentiality and Integrity are not considered |
| [73] | N + P | Encryption/Asymmetric + Hashing | ✓(Identity) | 2 | C/F | I | +Efficient with respect to the success rate+Identity privacy is considered+Message overhead is low −Routing attacks are not considered −Storage cost is not considered |
| [74] | N + P | Encryption/symmetric + Asymmetric + Hashing | x | 2 | C/F | I | +Resistance to Replay, collision, and chosen-plain-text attacks. −Location and Identity privacy is not considered |
| [75] | N + P | Encryption/Asymmetric + Hashing | ✓(Entity Id and Serial number) | 2 | C/F | I | +Resistance to Impersonation, Brute force, DoS, MITM, and Replay attacks +Reducing management cost −Storage cost is not considered |
| [116] | N + P | Encryption/Asymmetric(chaotic map) + Hashing | ✓(Identity id and password) | 2 | C/H | I | +User is anonymous +Identity privacy is considered +Secure session key +Computation, communication and storage costs are considered −Data integrity is not considered |
| [117] | A + N + P | Encryption/symmetric + Asymmetric + Hashing | ✓(Identity) | 2 | D/H | I | +Resistance to Password guessing, Impersonation, Forgery, and Known session-key attacks +Computation cost is considered −Location privacy and communication cost are not considered |
| [123] | A + N + P | Encryption/symmetric + Hashing | ✓(Identity id and password) | 2 | C/F | E | +Resistance to Stolen-Verifier, Password guessing, and Impersonation attacks −Sensor node impersonation attack is not considered −Unsafe against user who have privilege within the system attack. −No way of changing the password. |
| [122] | A + N + P | Encryption/symmetric + Hashing | ✓((smart card and password) | 2 | C/F | E | +Resistance to Replay, Masquerading user, Masquerading gateway, Gateway secret guessing, Password guessing, and Stolen-Verifier attacks +Computation and communication cost is analyzed −Unsafe against privileged insider and off-line password guessing attacks. |
| [118] | A + N + P | Encryption/symmetric + Hashing | ✓(Identity Id) | 2 | C/F | I | +Resistance to node capture and key compromise impersonation attack. +Security is achieved even if the smart card is stolen or lost. −Message delay and verification delay is not considered. |
| [137] | P | N/A | x | 2 | C/F | I | +Provided a discussion of machine learning attacks and how to deal with it. −Lack of dealing with the variation of environmental conditions |
| [103] | P | Encryption/Asymmetric(RSA or ECC) + Hashing | x | 2 | C/F | I | +Resistance to MITM and compromising a device attacks. −Lack of dealing with the variation of environmental conditions |
| [138] | P | Encryption/symmetric + Asymmetric + Hashing | x | 2 | C/F | I | +Resistance to machine-learning attacks +Deal with environmental variations by using error correction codes |
| [146] | P | Hashing | ✓(User password) | 2 | C/F | I | +Resistance to device cloning or copying −An attacker could fake the user, then asking him for his password −Authentication is done between a server and end device only. |
| [134] | P | Encryption/symmetric + Hashing | ✓(One-time alias, identity and nonce) | 2 | C/F | I | +Computation cost is low +Impersonation and Physical attacks is taken into consideration. − No consideration for machine-learning attacks. −No consideration for environmental variations |
| [139] | P | Encryption/symmetric + Hashing | x | 2 | C/F | I | +Protect against physical and side channel attacks +Avoid modeling attacks by hiding the CRP data −No consideration for environmental variations |
| [105] | P | Encryption/symmetric + Asymmetric + Hashing | ✓(Dynamic Identity) | 2 | C/H | I | +Protect against Impersonation, Physical, and Reply attacks. −No consideration for machine-learning attacks. −No consideration for environmental variations |
| [84] | P | Encryption/symmetric + Asymmetric + Hashing | ✓(Identity) | 2 | C/F | E | +Resistance to physical cloning attack. +Resistance to cloning attack based on attacking the communication protocol between the reader and the tag. −No consideration for environmental variations |
| [85] | P | Encryption/symmetric + Hashing | ✓(Identity) | 2 | C/H | I | +Deal with environmental variations(noisy system) +Resistance to Physical attacks, DoS attacks, and Forward secrecy. +Efficient in terms of computation and communication cost+Security analysis is done compared to other schemes +Authentication scheme is evaluated using AVISPA tool. −No consideration for machine-learning attacks |
| [81] | P | Encryption/symmetric + Hashing | ✓(nonce) | 2 | C/F | I | +Resistance to cloning, replay, back-tracking, and clone attacks. +Efficient in terms of computation −No consideration for environmental variations |
| [68] | A + N + P | Encryption/symmetric + Asymmetric + Hashing | ✓(Identity) | 2 | C/F | E | +Resistance to DoS −Large packet header −Large key size of RSA. |
| [124] | P | Encryption/symmetric + Asymmetric + Hashing | ✓(Identity + smart card + password) | 2 | C/H | E | +Compared with RSA regarding the encryption and decryption time −No security analysis is done |
| [106] | P | Encryption/symmetric + Hashing | ✓(smart device ID) | 2 | C/H | I | +Efficient in terms of computation and communication +Resistance to Replay attacks −No consideration for machine-learning attacks −No consideration for environmental variations |
| [147] | A + N + P | Encryption/Asymmetric + symmetric + Hashing | ✓(smart card + ID) | 2 | C/H | E | +Computation and communication +Resistance to replay, impersonation, stolen verifier, DoS, and offline guessing attacks. +Privacy preserving is considered. −Not efficient in terms of computation and communication. |
| [125] | A + N + P | Biometric | ✓(physical properties) | 1 | C/H | E | +Ease to be used in smart health environments+No ability to be stolen, borrowed, and forgotten. +Resistance to clone and fork attacks. −The uniqueness of behavioral biometric properties is low and its computation cost is high. |
| [126] | A + N + P | Encryption/+ symmetric + Hashing + Biometric | ✓(physical properties, smart card, ID and password) | 2 | C/H | E | +Uses three-factor authentication and privacy preserving is considered. +Resistance to replay, MITM, active, passive, forgery, user traceability +Resistance to clone and fork attacks. +The ability to update the biometric or password. +Scalability is high −No consideration for DoS and DDoS attacks. |
| [148] | P | Encryption/Asymmetric | ✓(Nonce) | 2 | C/H | I | +Uses two-factor authentication and +Resistance to replay attack −No security analysis is done −No comparison is done with existing authentication schemes. |
| [149] | P | Encryption/+symmetric | ✓(physical properties) | 2 | C/H | I | +New architecture using PUF +The ability to update the biometric or password. −No consideration for machine-learning attacks −Complex architecture with respect to resource-constrained devices in IoT |
| [150] | A + N + P | Encryption/+Assymmetric + Hashing | ✓(ID, token) | 2 | C/H | I | +New architecture of using Blockchain in IoT. +Security analysis is done. −The consensus protocol takes about 14 seconds to validate a transaction which considered long period for real time applications −Using a public blockchain requires a fees to be paid for each transaction, which considered inefficient. |
| [107] | A + N + P | Encryption/+symmetric | ✓(ID, token) | 2 | C/H | I | +Resistance to replay, DoS, eavesdropping, and resource exhaustion attacks. +Computation and communication cost is low. −Preshared key should be deployed at the provisioning phase −Privacy preservation is not considered. |
| [152] | A + N + P | Encryption/+ Assymmetric + symmetric + Hashing | ✓(ID) | 2 | D/H | I | +Use of Azure IoT hub cloud infrastructure. +The accuracy of generating X.509 digital certificates for device authentication is increased from 50.9% into 84.7%. −Security analysis is not considered. −No consideration for the scalability requirements of IoT systems while using PKI. |
| [151] | A + N + P | Encryption/+ symmetric + Hashing | ✓(ID, pseudo-identity pair) | 2 | D/H | I | +Computation cost is low at the device side. +Resistance to offline guessing, User tracking, forgery, and insider attacks. −Communication cost is high. −No consideration for Dos and DDoS attacks. −Computation cost at cloud is high. |
| [86] | P | physical fingerprint as context | ✓(ID) | 1 | C/F | E | +Two-factors are used for authentication +Quick search of specific book and finding the location by attaching an NFC tag on each book. −Data collected are stored as plain text in the mobile phone. −Computation and communication cost is considered. −No security analysis is done. |
| [133] | P | Behavior as context | ✓(ID) | 1 | C/H | I | +Modeling subset of the data to test the results −Restriction of the study to android platform mobile phones only −Data collected are stored as plain text in the mobile phone −No consideration for attacks. −Computation cost is high. −Achievement of positive identification of the owner is 70 out of 100. |
| [87] | P | Hashing + Xor | ✓(ID) | 2 | C/H | I | +Novel scheme and benefiting from cache concept. +Resistance to forward, replay, eavesdropping, spoofing, tracking, and DoS attacks. +Computation and storage cost is efficient with respect to other schemes in literature. −Security of data storage in IoT systems is not considered. |
| [88] | P | Shifting + Xor | ✓(ID, pseudonym (IDS)) | 2 | C/H | I | +Novel scheme and benefiting from cache concept. +Resistance to forward, replay, eavesdropping, tracking, de-synchronization, and DoS attacks. +Computation and communication cost is efficient with respect to other schemes in literature. −Storage overhead of the database is high. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
El-hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A Survey of Internet of Things (IoT) Authentication Schemes. Sensors 2019, 19, 1141. https://doi.org/10.3390/s19051141
El-hajj M, Fadlallah A, Chamoun M, Serhrouchni A. A Survey of Internet of Things (IoT) Authentication Schemes. Sensors. 2019; 19(5):1141. https://doi.org/10.3390/s19051141
Chicago/Turabian StyleEl-hajj, Mohammed, Ahmad Fadlallah, Maroun Chamoun, and Ahmed Serhrouchni. 2019. "A Survey of Internet of Things (IoT) Authentication Schemes" Sensors 19, no. 5: 1141. https://doi.org/10.3390/s19051141
APA StyleEl-hajj, M., Fadlallah, A., Chamoun, M., & Serhrouchni, A. (2019). A Survey of Internet of Things (IoT) Authentication Schemes. Sensors, 19(5), 1141. https://doi.org/10.3390/s19051141





