Abstract
User authentication in wireless sensor networks is more difficult than in traditional networks owing to sensor network characteristics such as unreliable communication, limited resources, and unattended operation. For these reasons, various authentication schemes have been proposed to provide secure and efficient communication. In 2016, Park et al. proposed a secure biometric-based authentication scheme with smart card revocation/reissue for wireless sensor networks. However, we found that their scheme was still insecure against impersonation attack, and had a problem in the smart card revocation/reissue phase. In this paper, we show how an adversary can impersonate a legitimate user or sensor node, illegal smart card revocation/reissue and prove that Park et al.’s scheme fails to provide revocation/reissue. In addition, we propose an enhanced scheme that provides efficiency, as well as anonymity and security. Finally, we provide security and performance analysis between previous schemes and the proposed scheme, and provide formal analysis based on the random oracle model. The results prove that the proposed scheme can solve the weaknesses of impersonation attack and other security flaws in the security analysis section. Furthermore, performance analysis shows that the computational cost is lower than the previous scheme.
1. Introduction
Wireless Sensor Networks (WSNs) generally consist of gateways, users, and a large number of sensor nodes. The sensor node is tiny and can be easily deployed in various kinds of severe environments. However, each sensor node has limited resources, is lacking in memory, has low computational capabilities and short radio transmission range [1]. Data collected from sensor nodes in WSNs sometimes include valuable and classified information such as the environmental surrounding the wartime, a patient’s personal information, monitoring information of museums, and the power company’s voltage variation monitoring data. To ensure the confidentiality and reliability of deployed WSNs, only registered and legitimate users should be able to access them. In addition, establishing secure protocol actively requires a mutual authentication between the user and the sensor node. For these reasons, secure user authentication is one of the major issues in WSNs.
To support message confidentiality and secure authentication for sensor networks, various authentication schemes for WSNs have been proposed. However, a problem that occurs with respect to password-based authentication schemes is that a server must maintain a password table to legitimately verify a login user. Therefore, the server requires additional memory space to store the password table. For this reason, many researchers have proposed a new type of remote user authentication scheme whereby personal biological characteristics are used, such as a fingerprint or an iris. The main advantage biometrics is uniqueness. A smart card can be used as a tool to store biometric information. Since the smart card has its own calculation function, it can operate at more than one level. In 2004, Watro et al. [2] proposed a user authentication scheme using the RSA and DH algorithms for WSNs. After that, Wong et al. [3] proposed a hash-based dynamic user authentication scheme in 2006. However, Tseng et al. [4] found that Wong et al.’s authentication scheme was vulnerable to replay, stolen verifiers, and forgery attacks. In 2009, Das [5] proposed and claimed that his scheme can resist various real-time attacks. Unfortunately, He et al. [6] found that Das’s scheme was vulnerable to insider and impersonation attacks, and proposed an improved two factor scheme to solve these security problems. In the same year, Khan and Alghathbar [7] demonstrated that Das’s scheme did not provide mutual authentication, and was vulnerable to gateway bypassing and privileged insider attacks, and Chen et al. [8] also found that Das’s scheme did not provide mutual authentication between the gateway and the sensor, proposed a robust mutual authentication scheme for WSNs, and claimed that their scheme provides greater security than Das’s scheme. In 2010, Yuan et al. [9] proposed a biometric-based user authentication scheme. However, Yoon et al. demonstrated that Yuan et al.’s scheme was vulnerable to insiders, user impersonation, gateway node impersonation and sensor node impersonation attacks. To solve these problems, Yoon et al. [10] proposed an improved user authentication scheme. Unfortunately, He et al. [11] found that Yoon et al.’s scheme was still vulnerable to denial of service (DoS) and sensor impersonation attacks, and then proposed an improved scheme to overcome these security problems.
In 2013, Yoon and Kim [12] pointed out that He et al.’s scheme had various security vulnerabilities such as poor repairability, and was vulnerable to user and sensor node impersonation attacks. They then proposed an advanced biometrics-based user authentication scheme for WSNs. They claimed that their scheme was more effective and had stronger security than other related schemes. However, Choi et al. [13] found that Yoon and Kim’s scheme [12] had various security problems, including a biometric recognition error, a user verification problem, lack of anonymity, perfect forward secrecy, session key exposure by the gateway node, vulnerability to DoS attacks, and a revocation problem. To overcome these vulnerabilities, they proposed a biometric-based user authentication scheme using a fuzzy extractor, and claimed that their scheme is more secure than other authentication schemes. Unfortunately, Park et al. [14] demonstrated that Choi et al.’s scheme [13] was still insecure against user impersonation attacks, and had security weakness in the revocation/reissue phase. They then proposed an enhanced biometric-based authentication scheme for WSNs that has improved security functions. After careful analysis, however, we found that Park et al.’s scheme [14] was still insecure against impersonation attack, and also had a problem in the smart card revocation/reissue phase.
In this paper, we show how an adversary can impersonate a legitimate user or a sensor node, and perform an illegal smart card revocation/reissue. After demonstrating these problems, we propose an improved biometric authentication scheme. Finally, we analyze our proposed scheme for security properties and computational cost. The proposed scheme is more secure and efficient than other related authentication schemes.
The rest of this paper is organized as follows. In Section 2, we briefly introduce the elliptic curve cryptosystem, threat assumptions and fuzzy extractors that we adopt in our scheme. In Section 3 and Section 4, we review and analyze, respectively, Park et al.’s scheme [14]. In Section 5, we propose an improved authentication scheme for WSNs. In Section 6, we present a security analysis of the proposed scheme. Section 7 shows performance analysis comparing our scheme with previous schemes. Our conclusions are presented in Section 8.
2. Preliminaries
In this section, we briefly introduce the elliptic curve cryptosystem, threat assumptions, and fuzzy extractor.
2.1. Elliptic Curve Cryptosystem
The elliptic curve cryptosystem (ECC) was first proposed by Koblitz [15] and Miller [16] to design public key cryptosystems, and presently it is widely used in several cryptographic schemes to provide desired levels of security and performance. An elliptic curve defined over a field K of the characteristic ≠ 2 or 3 is the set of solutions , ∈ to the equation:
Cryptosystems based on GF( can be translated to systems using the group E, where E is an elliptic curve defined over a GF(q). The point multiplications = , k times) that means k times addition of point P. Given an elliptic curve E defined over a GF(q) and two points P, Q ∈ E, it finds an integer x such that if such x exists. This problem proved to be more intractable than the typically discrete logarithm problem. The details of the ECC definitions can be found in [15]. There are several computational problems based on ECC which are presented below:
Definition 1.
The elliptic curve discrete logarithm problem () is defined as: given two elements Q, , find an integer , such that .
Definition 2.
The computational Diffie–Hellman problem () is defined as: given three elements , , for any a, , , computation of is very hard to the group .
Definition 3.
The elliptic curve factorization problem ( ) is defined as: given two elements P, , where and , , , then computation of and is impossible.
Definition 4.
The decisional Diffie–Hellman problem ( ) is defined as: given four elements , , , for any , b, , , decide whether or not i.e., p or not.
Definition 5.
The weak Diffie–Hellman problem () is defined as: for and some , from the given three elements , Q, computation of is very hard.
2.2. Threat Assumptions
We introduce the Dolev–Yao [17] and some threat model [18,19], and consider the risk of side channel attack [20] to construct the threat assumptions, which are described as follows:
- An adversary can be either a user, gateway, or sensor node. Any registered user can act as an adversary.
- An adversary can eavesdrop every communication in a public channel, thereby capturing any message exchanged between a user and gateway or sensor node.
- An adversary has the ability to alter, delete or reroute the captured message.
- Information can be extracted from the smart card by examining the power consumption of the card.
2.3. Fuzzy Extractor
In this subsection, we describe the basis for a biometric-based fuzzy extractor, which converts biometric information data into a random value. Based on [21,22,23], the fuzzy extractor is given by two procedures (, ). The mechanism of a fuzzy extractor consists of two procedures (, ), which is demonstrated as:
- if is reasonably close to
The function is a probabilistic generation procedure, which on biometric input outputs an “extracted” string and an auxiliary string . is a deterministic reproduction procedure, which recovery of R from the corresponding auxiliary string P, and any vector close to . The detailed information about fuzzy extractors can be founded in the literature [24].
3. Review of Park et al.’s Authentication Scheme
In this section, we review Park et al.’s authentication scheme [14]. The notations used in the paper are listed in Table 1. The generates two master keys, x and y, and provides a long-term secret key to the sensor before the scheme is executed. Their scheme involves three parties, i.e., the user , the gateway and the sensor , to communicate with each other to perform the following three phases: registration, login/authentication, and revocation/reissue.

Table 1.
Notations used in this paper.
3.1. Registration Phase
In this phase, a user chooses an identity , imprints biometric template , and then performs the following steps:
- computes , and . then sends to the gateway .
- Upon receiving , from , computes the authentication parameters as:
- stores and the authentication parameters; , , , in the smart card . then issues to through a secure channel.
- After receiving the smart card from , stores in the smart card.
3.2. Login and Authentication Phase
If a user wants to log in to the and , performs the login phase, and then , and verify each other’s authenticities. Finally, and generate a session key in this phase as follows:
- enters and imprints biometric template . then computes , and using fuzzy extraction, and compares with as:
- generates a random number and computes and as:
- picks up and computes and as:then sends the login request message , , , , to .
- After receiving , retrieves and verifies . If this holds, computes , , and , and compares with as:If this holds, verifies the legitimacy of .
- picks up and computes , and ,then sends the authentication message , , , to .
- When receiving from , retrieves , and verifies . If this holds, verifies the validity of by comparing it with to check the legitimacy of . After that, computes , and decrypts using . then checks the validity of the received by comparing as:
- generates a random number and computes , and a session key . then picks up and computes , as:hence sends , , , to .
- Upon receiving , retrieves , and checks the sameness of . then computes and as:Only the legitimate can compute and . then accepts . Finally, and can communicate securely using the common .
3.3. Revocation or Reissue Phase
To make up for smart card loss or long term key disclosure, the smart card should be revoked and reissued in cycles.
- who wants to revoke and reissue a smart card inputs the previous identity and the new identity to prevent adversaries from registering with the same identity . Then, imprints biometric template and computes , and .
- computes and sends the revocation/reissue request message , , , to .
- computes , and checks the legitimacy of the user as:
- If this holds, revokes and records it on the revocation look-up table. Then, computes new authentication parameters , and as:
- stores and the new authentication parameters; , , , in the smart card . then reissues to through a secure channel.
- stores in the smart card.
4. Cryptanalysis of Park et al.’s Authentication Scheme
In this section, we analyze the security problems of Park et al.’s scheme [14]. Park et al. cryptanalyzed a scheme of Choi et al. [13] and improved it to support better security functionality. However, we found that Park et al.’s scheme [14] was still insecure against impersonation attack and had a problem with smart card revocation/reissue. The following attacks are based on the threat assumptions that a malicious adversary was completely monitored through the communication channel connecting , and in the login and authentication phases, and that the obtained the information saved in their own smart card [20]. therefore can eavesdrop, modify, insert, or delete any message transmitted over a public channel. We now reveal the details of these problems.
4.1. User Impersonation Attack
- Let be an active adversary who is he/she legal user and owns a smart card to extract information , , , , .
- then imprints one’s biometric template and computes and .
- generates a random number , and selects any identity . then computes login request message as:then sends the login request message , , , , to .
- When receiving , retrieves and verifies . If this holds, computes , , , and compares with as:If this holds and does exist in the database, the gateway continues to proceed the scheme without detected. Otherwise, selects another identity nominee and performs the same processes until he/she locates the valid identity.
- picks up and computes , and :then sends the authentication message , , , to .
- Upon receiving from , retrieves and verifies . If this holds, verifies the validity of by comparing it with to check the legitimacy of . After that, computes and decrypts using . then checks the validity of the received by comparing as
- generates a random number and computes , and a session key . then computes , as:where is current timestamp. then sends , , , to .
- After receiving , retrieves , and checks the sameness of . Then, computes and as:Lastly, and “successfully” agree on a session key . Unfortunately, the sensor mistakenly believes that he/she is communicating with the legitimate user .
4.2. Sensor Node Impersonation Attack
Park et al. [14] claimed that if wants to masquerade as the sensor node , is required to compute . This is because the symmetric key . However, if obtains the login request message , , , , of the legitimate user , then can easily impersonate the sensor node .
- After receiving from , generates a random number and computes , , , and a session key as:where is current timestamp. then sends , , , to .
- Upon receiving from , retrieves and checks the sameness of . Then, computes and as:Lastly, and “successfully” agree on a session key . Unfortunately, the user mistakenly believes that he/she is communicating with the legitimate sensor .
4.3. Illegal Smart Card Revocation/Reissue Attack
Park et al. [14] claimed that, although could get the identity in some way, checks the legitimacy of the user on the requested identity, and cannot compute and the revocation/reissue request message without the biometric information of . However, can modify the revocation/reissue request message. This is because cannot distinguish whether or not the user who wishes to revoke is the real user .
- Suppose owns a smart card to extract information , , , , and obtains the identity of the legitimate user by using a user impersonation attack.
- Next, imprints the personal biometric information at the sensor. The sensor hence sketches and extracts , from , .
- computes and and sends the revocation/reissue request message , , , to .
- computes , , and checks the legitimacy of the user as:
- If this holds, revokes and records it on the revocation look-up table. Then, computes new authentication parameters , and as:
- stores the new authentication parameters , , , in the smart card . then reissues to through a secure channel.
- stores in the smart card.
Adversary can revoke the smart card of an authenticated user who does not wish the said smart card to be revoked without permission because has no proper process for checking the legitimacy of the user on the previous identity .
5. The Proposed Scheme
In this section, we will propose a new biometric-based password authentication scheme using a smart card. In our scheme, there are also three participants, the user , the gateway and the sensor . The generates two master keys x and y, and sends a long-term secret key to the sensor before the scheme is executed. After that, computes where is the public key of the gateway. The proposed scheme consists of three phases: registration, login and authentication, and revocation/reissue.
5.1. Registration Phase
In this phase, a user chooses an identity , imprints biometric template at the sensor, and then performs the following steps:
- The sensor sketches , extracts , from , , and stores in the memory. then sends , to over a secure channel.
- When receiving the registration request message , from , the gateway computes the authentication parameters as:
- stores the authentication parameters , , , in the smart card . hence issues to via a secure channel.
- Lastly, stores in the smart card.
Figure 1 illustrates the registration phase of the proposed scheme.
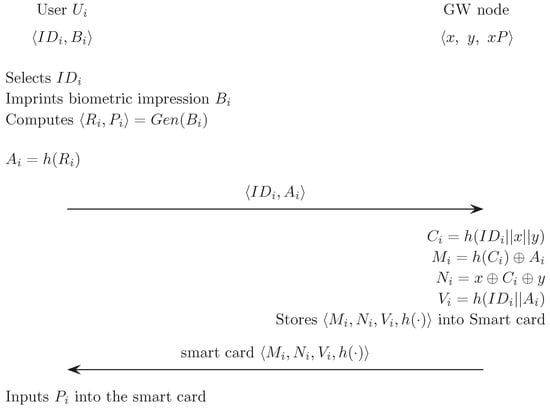
Figure 1.
Registration phase of the proposed scheme.
5.2. Login and Authentication Phase
In this phase, performs the login phase, and hence , and verify each other’s authenticity. Finally, and generates a common session key in this phase as follows:
- inserts his/her smart card into the card reader, inputs the identity , and imprints the personal biometrics at the sensor.
- The sensor then sketches and extracts from , . Then, computes and using fuzzy extraction and compares with as:
- generates random numbers and and hence computeswhere is current timestamp. Then, sends the login request message , , , , , to .
- Upon receiving a login request message from , retrieves and verifies . If this is true, computes , , and and compares with and with as:If this holds, verifies the legitimacy of .
- computes , and ,where is current timestamp. then sends the authentication message , , , to .
- When receiving the authentication message from , retrieves and verifies . If this is true, verifies the validity of by comparing it with to check the legitimacy of . After that, computes , and decrypts using . Then, checks the validity of the received by comparing the computed as
- generates a random number and computes , , , and a session key as:where is current timestamp. then sends , , , to .
- After receiving response message , , , from , computes and checks whether is equal to :The legitimate user can only compute and . and can communicate securely using the common session key .
Figure 2 illustrates the login and authentication phase of the proposed scheme.

Figure 2.
Login and authentication phase of the proposed scheme.
5.3. Revocation or Reissue Phase
To make up for smart card loss or long term key disclosure, the smart card should be revoked and reissued in cycles.
- If wants to revoke and reissue a smart card, he/she inserts his/her smart card into the card reader, inputs the previous identity and the new identity to prevent adversaries from registering with the same identity , and then imprints the personal biometrics at the sensor.
- The sensor then sketches and extracts from , . Then, computes and using fuzzy extraction,
- computes and sends the revocation/reissue request message , , , to over a secure channel.
- first checks whether is the same as or not. If they are different, computes , and checks the legitimacy of the user as:
- If this is true, revokes and records it on the revocation look-up table. Then, computes new authentication parameters , and as:
- stores and the new authentication parameters , , , in the smart card . then reissues to through a secure channel.
- stores in the smart card.
Figure 3 illustrates the revocation/reissue phase of the proposed scheme.
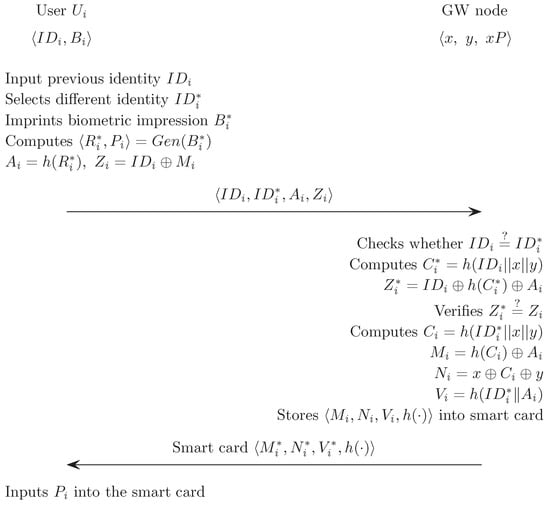
Figure 3.
Revocation/reissue phase of proposed scheme.
6. Security Analysis
In this section, we demonstrate that the proposed scheme, which retains the merits of Park et al.’s scheme [14], can withstand several types of possible attacks; and we also show that the scheme supports several security properties. The security analysis of the proposed scheme was conducted with the threat assumptions made in the Preliminaries.
6.1. Formal Security Analysis
In this subsection, we have demonstrated that the proposed scheme is secure through a formal proof using the random oracle model [18,25]. At first, we specify a collision-free one-way hash function as follows.
Definition 6.
The collision-resistance one-way hash function , , pick up an input as a binary string , that has a random length, produces a binary string , , and gratifies the following requirements:
- Given the , it is not possible to find out computationally about such that .
- Given the , it is not possible to find out computationally about another , such that .
- It is not possible to find out computationally about a pair , , with , such that .
Theorem 1.
According to the assumption that if the collision-free one-way hash function closely acts like an oracle, the proposed scheme is then distinctly secure against an adversary for the protection of the sensitive information including the identity , nearly random binary string and master secret key x, y of the gateway node .
Proof.
This random oracle can extract the input value x from the given hash result without fail. now executes the experimental algorithm as shown in Algorithm 1, for the proposed scheme as JHKAS, for example. Let us define the probability of success for as , where means the probability of . The advantage function for this algorithm then becomes , where the t is the execution time and is the number of queries. Discuss the algorithm as shown in Algorithm 1 for the . If has the capability to solve the hash function problem given in Definition 6, then he/she can immediately retrieve the identity , nearly random binary string and master secret key x, y of the gateway node . In that case, the will detect the complete connections between the and the ; however, the inversion of the input from a given hash value is not possible computationally, i.e., , for all . Thus, , since depends on . In conclusion, there is no way for to detect the complete connections between the and the , and the proposed scheme is distinctly secure to an adversary for retrieving (, , x, y). ☐
| Algorithm 1 |
| 1. Eavesdrop login request message , , , , , during the login phase. 2. Call the Reveal oracle. Let , , , , Reveal() 3. if ( == ) then 4. Accept , , , as the correct of user 5. Call the Reveal oracle. Let ( Reveal() 6. Call the Reveal oracle. Let ( Reveal() 7. if ( == ) then 8. Accept the as the correct of user 9. Call the Reveal oracle. Let , , Reveal() 10. Compute 11. if ( == ) then 12. Accept , as the correct secret key x, y of gateway node 13. return 1(Success) 14. else 15. return 0 16. else 17. return 0 18. end if 19. else 20. return 0 21. end if |
6.2. Simulation for Formal Security Verification Using the AVISPA Tool
In this subsection, we simulate the proposed scheme using the widely accepted AVISPA for the formal security verification. The main purpose of the simulation is to verify whether the proposed scheme is secure to replay and man-in-the middle attacks. The AVISPA tool consists of four back-ends: (i) On-the-fly Model-Checker (OFMC); (ii) Constraint-Logic-based Attack Searcher; (iii) SAT-based Model Checker; and (iv) Tree Automata based on Automatic Approximations for the Analysis of Security Protocols. In the AVISPA, the protocol is implemented in HLPSL [26], which is based on: the basic roles for representing each participant role and composition roles for representing the scenarios of the basic roles. The basic types available in the HLPSL are [27]:
- agent : The agent denotes a principal name. The intruder always has the special identifier i.
- symmetric_key : The symmetric_key is the key for a symmetric-key cryptosystem.
- text : The text values are often used as nonces. They can also be applied for messages.
- nat : The nat is used for denoting the natural numbers in non-message contexts.
- const : This type represents constants.
- hash_func : The base type hash_func represents cryptographic one-way hash functions.
The role of the initiator, the user is provided in Algorithm 2. The first receives the start signal and updates its state value from 0 to 1. The state value is maintained by the variable State. In a similar way, the roles of the gateway and sensor node of the proposed scheme are implemented and shown in Algorithm 3 and 4, respectively. The specifications in HLPSL language for the role of session, goal, and environment are specified in Algorithm 5. The simulation result for the formal security verification of the proposed scheme using CL-AtSe is shown in Algorithm 6. It is clear that the proposed scheme is secure to passive and active attacks including the replay and man-in-the middle attacks.
| Algorithm 2 Role specification for user |
| role user (Ui, GW, Sj: agent, SKug, SKus: symmetric_key, H, F: function, SND, RCV: channel (dy)) played_by Ui def= local State : nat, IDi, Ri, P, Ai, Mi, Ni, Vi: text, AIDi, R1, R2, Xi, Ci, Di, M1, M2, M3, Ti, Rs: text, RM, Yi, Vs, Ts, Gx, Gy, Kus: text init State := 0 transition 0. State = 0 ∧ RCV(start) =|> State’:= 5 ∧ Ai’ := H(Ri) ∧ secret(Ri, scrt0, Ui) ∧ secret(IDi, scrt1, {Ui, GW}) ∧ SND({IDi.Ai’}_SKug) 5. State = 2 ∧ RCV({Mi’.Ni’.Vi’}_SKug.P’) =|> State’:= 8 ∧ R1’:=new() ∧ R2’:=new() ∧ Ti’:=new() ∧ Xi’:=F(R1’.P’) ∧ Di’:=xor(Mi’, Ai’) ∧ AIDi’:=xor(IDi, H(R2’)) ∧ M1’:=xor(R2’, Di’) ∧ M2’:=H(AIDi’.Di’.Xi’.R2’.Ti’) ∧ M3’:=xor(Ni’, F(R1’.F(Gx’.P))) ∧ secret({Gx’, Gy’}, scrt2, GW) ∧ SND(AIDi’, Xi’, M1’, M2’, M3’, Ti’) ∧ witness(Ui, Sj, ui_sj_r1, R1’) 8. State = 8 ∧ RCV({RM’.Yi’.Vs’.Ts’}_SKug.P’) =|> State’:= 9 ∧ Vs’:=H(AIDi’.Xi’.Yi’.RM’.Ts’) ∧ Kus’:= F(R1’.F(Rs’.P)) ∧ SKus’:=H(AIDi’.Kus’.Ts’) ∧ witness(Ui, GW, ui_gw_r2, R2’) ∧ request(Sj, Ui, sj_ui_rs, Rs’) end role |
| Algorithm 3 Role specification for gateway |
| role gateway (Ui, GW, Sj: agent, SKug, SKgs, Kg: symmetric_key, H, F: function, SND, RCV: channel (dy)) played_by GW def= local State : nat, IDi, R1, R2, Ri, P, Ai, Mi, Ni, Vi, Rs: text, AIDi, SIDj, Ks, Xi, Ci, Di, M1, M2, M3, Ti: text, Cg, Tg, Wg, Gx, Gy: text init State := 1 transition 1. State = 1 ∧ RCV({IDi.Ai’}_SKug) =|> State’:= 6 ∧ Ci’:= H(IDi.Gx’.Gy’) ∧ P’:=new() ∧ Di’:=H(Ci’) ∧ Mi’:=xor(Di’, H(Ri)) ∧ Ni’:=xor(Gx’, Ci’, Gy’) ∧ Vi’:=H(IDi.H(Ri)) ∧ secret({Gx’, Gy’}, scrt2, GW) ∧ SND({Mi’.Ni’.Vi’}_SKug.P’) 3. State = 3 ∧ RCV({SIDj}_SKgs) =|> State’:= 6 ∧ Ks’:=H(SIDj.Gy’) ∧ SND({Ks’}_SKgs.P’) 6. State = 6 ∧ RCV(AIDi’.Xi’.M1’.M2’.M3’.Ti’) =|> State’:= 9 ∧ Tg’ = new() ∧ Di’:=H(xor(M3’, F(R1’.F(Gx’.P)), Gx’, Gy’)) ∧ R2’:=xor(M1’, Di’) ∧ IDi’:=xor(AIDi’, H(R2’)) ∧ Kg’:=H(H(SIDj’.Gy’).Tg’) ∧ Cg’:={AIDi’.R2’.Xi’}_Kg’ ∧ Wg’:=H(H(SIDj’.Gy’).AIDi’.Cg’.Tg’) ∧ secret({Gx’, Gy’}, scrt2, GW) ∧ secret(H(SIDj’.Gy’), scrt4, {GW, Sj}) ∧ SND(AIDi’.Cg’.Tg’.Wg’) ∧ request(Ui, Sj, ui_sj_r1, R1’) end role |
| Algorithm 4 Role specification for sensor |
| role sensor (Ui, GW, Sj: agent, SKgs, Kg, SKus: symmetric_key, H, F: function, SND, RCV: channel (dy)) played_by Sj def= local State : nat, IDi, Ri, P, Ai, Mi, Ni, Vi, R1, R2: text, AIDi, SIDj, Ks, Xi, Ci, M1, M2, M3, Ti: text, Cg, Tg, Wg: text, RM, Yi, Vs, Ts, Gx, Gy, Rs, Kus:text init State := 2 transition 2. State = 2 ∧ RCV(start) =|> State’:= 4 ∧ SND({SIDj}_SKgs.P’) 4. State = 4 ∧ RCV({H(SIDj.Gy’)}_SKgs.P’) =|> State’:= 7 ∧ secret({Gx’, Gy’}, scrt2, GW) 7. State = 7 ∧ RCV(AIDi’.Xi’.M1’.M2’.M3’.Ti’) =|> State’:= 10∧ Kg’:=H(H(SIDj’.Gy’).Tg’) ∧ Kus’:=F(R1’.F(Rs’.P)) ∧ Yi’:=F(Rs’.P) ∧ Ts’:=new() ∧ SKus’:=H(AIDi’.Kus’.Ts’) ∧ RM’:=new() ∧ Vs’:=H(AIDi’.Xi’.Yi’.RM’.Ts’) ∧ SND(RM’, Yi’, Vs’, Ts’) ∧ secret(H(SIDj.Gy’), scrt4, {GW, Sj}) ∧ witness(Sj, Ui, sj_ui_rs, Rs’) ∧ request(Ui, Sj, ui_sj_r1, R1’) end role |
| Algorithm 5 Role specification for session, goal and environment |
| role session(Ui, GW, Sj: agent, SKug, SKus, SKgs, Kg: symmetric_key, H, F: function) def= local Z1, Z2, Z3, S1, S2, S3: channel (dy) composition user(Ui, GW, Sj, SKug, SKus, H, F, Z1, S1) ∧ gateway(Ui, GW, Sj, SKug, SKgs, Kg, H, F, Z2, S2) ∧ sensor(Ui, GW, Sj, SKgs, Kg, SKus, H, F, Z3, S3) end role role environment() def= const ui, gw, sj : agent, skug, skgs, skus, kg : symmetric_key, h, f : function, aidi, sidj, p, xi : text, xi, m1, m2, m3, ti : text, cg, tg, wg : text, rm, yi, vs, ts : text, ui_sj_r1, ui_gw_r2, sj_ui_rs : protocol_id, scrt0, scrt1, scrt2, scrt3, scrt4 : protocol_id intruder_knowledge = {ui, gw, sj, h, f, p, aidi, sidj, xi, m1, m2, m3, ti, cg, tg, wg, rm, yi, vs, ts} composition session(ui, gw, sj, skug, skgs, kg, skus, h, f) end role goal secrecy_of scrt0 secrecy_of scrt1 secrecy_of scrt2 secrecy_of scrt3 secrecy_of scrt4 authentication_on ui_sj_r1 authentication_on ui_gw_r2 authentication_on sj_ui_rs end goal |
| Algorithm 6 Role specification for session, goal and environment |
| SUMMARY SAFE DETAILS BOUNDED_NUMBER_OF_SESSIONS PROTOCOL /home/span/span/testsuite/results/testrv.if GOAL As Specified BACKEND CL-AtSe STATISTICS Analysed : 1 states Reachable : 0 states Translations: 0.03 s Computation: 0.00 s |
6.3. Informal Security Analysis
Table 2 compares the security features provided by the proposed scheme with other related schemes.

Table 2.
Comparison of security features.
6.3.1. User Anonymity
Suppose an adversary intercepts the login request message , , , , , of a legitimate user . However, cannot be derived from without the knowledge of a random number ; furthermore, the cannot be derived from without a hash value . The and can only compute ). The proposed scheme therefore provides user anonymity.
6.3.2. Mutual Authentication
The proposed scheme not only guarantees secrecy as the other authentication scheme, but also , and authenticate each other. authenticates by checking whether is valid or not because only a legitimate user can compute a valid using a biometric template. Then, authenticates by checking , which only can compute using the shared long-term key and the time stamp . Finally, the authenticates by checking the validity of because only and can compute the session key .
6.3.3. Message Confidentiality
Message confidentiality is an important security aspect that provides secrecy by limiting the adversary’s access to the message. Communication messages in the public channel do not affect the disclosure of secret values, such as , , , and . cannot compute important information from , , , , , , , and . Furthermore, , , and are basically public information, so they do not need to be protected.
6.3.4. Perfect Forward Secrecy
The perfect forward secrecy means that if one long-term key is compromised, a session key that is derived from these long-term keys will not be compromised in the future [28]. In our scheme, a session key between user and sensor is calculated as follows:
Even if the gateway ’s long-term key (x, y) is compromised, adversary cannot retrieve and to generate the session keys between and . The session key of our proposed scheme is based on a elliptic curve discrete logarithm problem (ECDLP). An adversary cannot obtain from and . Our scheme therefore provides the perfect forward secrecy.
6.3.5. User Impersonation Attack
Suppose owns a smart card to extract information , , , , and intercepts the login request message , , , , , of legitimate user . can then try modifying a login request message. Even if guesses or obtains ’s identity , verifies whether is equal to . The cannot compute and , and then fails to impersonate a legitimate user . The proposed scheme therefore can resist user impersonation attack.
6.3.6. Gateway or Sensor Node Impersonation Attack
If wants to masquerade as the gateway node or a sensor node , the hash value is needed. However, it is computationally difficult to guess or correctly. Furthermore, even if obtains the login request message , , , , , , does not know . Thus, cannot be computed. The proposed scheme therefore can resist gateway or sensor node impersonation attack.
6.3.7. Illegal Smart Card Revocation/Reissue Attack
Even if obtains the identity of a legitimate user , cannot compute without the value . Furthermore, checks the legitimacy of the user on the request identity by computing and . Therefore, even if sends the revocation/reissue request message , , , to , fails to revoke and reissue the smart card with . The proposed scheme therefore can resist an illegal smart card revocation/reissue attack.
6.3.8. Session Key Exposure by GW
The gateway can intercept communication messages and obtain both and . However, cannot derive and and therefore cannot compute the common session key . This is because our proposed scheme based on the elliptic curve discrete logarithm problem (ECDLP).
6.3.9. Denial of Service Attack
In the proposed scheme, , and basically check for freshness of timestamp in each authentication step. Each message for verification such as , and includes the current timestamp T. Furthermore, each entity checks whether the calculated value is equal to the received value. The proposed scheme can resist denial of service attack.
6.3.10. User Verification Problem
checks for the sameness in the identity to verify the status a legitimate user by computing . Furthermore, can compute constant values including as a result of the fuzzy extractor. can authenticate a legal user even if the user inputs slightly different biometric information . Our proposed scheme therefore can prevent user verification problems.
6.3.11. Stolen Verifier Attack
In the proposed scheme, and do not store any identification, password table or user biometrics. stores only the master secret key (x, y), and stores only . The proposed scheme therefore can resist stolen verifier attacks.
6.3.12. Replay Attack
Even if the adversary obtains the communication message, and sends them again with the current timestamps , , and , cannot compute , , using the current timestamps. The proposed scheme therefore can resist replay attacks.
7. Performance Analysis
In this section, we compare the computational costs of the proposed scheme with the other related schemes [13,14,29,30]. Table 3 shows a comparison of the computational costs of the proposed scheme with the other related schemes. In the comparisons, XOR operations are not considered because these also can be ignored. Compared to Park et al.’s scheme [14], the proposed scheme performs three further hash operations and two elliptic curve computations. However, we reduce three encryption/decryption operations. Additionally, the proposed scheme provides the revocation and reissue phase, and can resist well-known attacks.

Table 3.
Comparison of computational costs.
8. Conclusions
The various authentication schemes for WSNs have been proposed. Recently, Park et al. demonstrated the security vulnerabilities of Choi et al.’s scheme and proposed an enhanced authentication scheme. However, in this paper, we have identified vulnerabilities in Park et al.’s scheme in terms of impersonation and revocation/reissue. To overcome these vulnerabilities, we proposed a new biometric-based authentication scheme with improved security. Security and performance analysis shows that our proposed scheme is more secure and efficient than other related schemes.
Acknowledgments
This work was supported by the Institute for Information & Communications Technology Promotion(IITP) grant funded by the Korea government (Ministry of Science, ICT and Future Planning) (No. R0126-15-1111, the Development of Risk-Based Authentication·Access Control Platform and Compliance Technique for Cloud Security).
Author Contributions
J.M., D.L. and Y.L. conceived and designed the experiments; J.M. performed the experiments; J.M. and D.L. analyzed the data; and J.M. and D.W. wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Watro, R.; Kong, D.; Cuti, S.; Gardiner, C.; Lynn, C.; Kruus, P. TinyPK: Securing sensor networks with public key technology. In Proceedings of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks, Washington, DC, USA, 25 October 2004; pp. 59–64. [Google Scholar]
- Wong, K.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; Volume 1, pp. 1–8. [Google Scholar]
- Tseng, H.; Jan, R.; Yang, W. An improved dynamic user authentication scheme for wireless sensor networks. In Proceedings of the Global Telecommunications Conference, Washington, DC, USA, 26–30 November 2007; pp. 986–990. [Google Scholar]
- Das, M. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Khan, H.; Alghathbar, K. Cryptanalysis and security improvements of ‘two-factor user authentication in wireless sensor networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Chen, T.; Shih, W. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Yuan, J.; Jiang, C.; Jiang, Z. A biometric-based user authentication for wireless sensor networks. Wuhan Univ. J. Nat. Sci. 2010, 15, 272–276. [Google Scholar] [CrossRef]
- Yoon, E.; Yoo, K. A new biometric-based user authentication scheme without using password for wireless sensor networks. In Proceedings of the 20th IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative, Paris, France, 27–29 June 2011; pp. 279–284. [Google Scholar]
- He, D.; Zhang, Y.; Chen, J. Robust biometric-based user authentication scheme for wireless sensor networks. IACR Cryptol. ePrint Arch. 2012, 2012, 203–217. [Google Scholar]
- Yoon, E.; Kim, C. Advanced biometric-based user authentication scheme for wireless sensor networks. Sens. Lett. 2013, 11, 1836–1843. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, Y.; Won, D. Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction. Int. J. Distrib. Sens. Netw. 2016, 2016, 1–16. [Google Scholar] [CrossRef]
- Park, Y.; Lee, S.; Kim, C.; Park, Y. Secure biometric-based authentication scheme with smart card revocation/reissue for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2016, 12, 1–11. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V. Use of elliptic curves in cryptography. Adv. Cryptol. 1985, 218, 417–426. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Moon, J.; Choi, Y.; Jung, J.; Won, D. An improvement of robust biometrics-based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE 2015, 10, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Kocher, P.; Jaffe, J.; Jun, B.; Rohatgi, P. Introduction to differential power analysis. J. Cryptogr. Eng. 2011, 1, 1–23. [Google Scholar] [CrossRef]
- Das, A. A secure and effective biometric-based user authentication scheme for wireless sensor networks using smart card and fuzzy extractor. Int. J. Commun. Syst. 2015, 2015, 1–25. [Google Scholar] [CrossRef]
- Wang, C.; Zhang, X.; Zheng, Z. Cryptanalysis and improvement of a biometric-based multi-server authentication and key agreement scheme. PLoS ONE 2016, 11, 1–25. [Google Scholar] [CrossRef] [PubMed]
- Dodis, Y.; Kanukurthi, B.; Katz, J.; Smith, A. Robust fuzzy extractors and authenticated key agreement from close secrets. IEEE Trans. Inf. Theory 2013, 58, 6207–6222. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; pp. 523–540. [Google Scholar]
- Das, A. A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communication. Netw. Sci. 2013, 2, 12–27. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language hlpsl developed in the eu project avispa. In Proceedings of the Applied Semantics 2005 Workshop, Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- Avispa Tool Documentation. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/ (accessed on 28 March 2016).
- Zhu, H.; Hao, X. A provable authenticated key agreement protocol with privacy protection using smart card based on chaotic maps. Nonlinear Dyn. 2015, 81, 311–321. [Google Scholar] [CrossRef]
- Nam, J.; Kim, M.; Park, J.; Lee, Y.; Won, D. A provably-secure ECC-based authentication scheme for wireless sensor networks. Sensors 2014, 14, 21023–21044. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).