Abstract
Email continues to serve as a primary vector for cyber-attacks, with phishing, spoofing, and polymorphic malware evolving rapidly to evade traditional defences. Conventional email security systems, often reliant on static, signature-based detection struggle to identify zero-day exploits and protect user privacy in increasingly data-driven environments. This paper introduces TwinGuard, a privacy-preserving framework that leverages digital twin technology to enable adaptive, personalised email threat detection. TwinGuard constructs dynamic behavioural models tailored to individual email ecosystems, facilitating proactive threat simulation and anomaly detection without accessing raw message content. The system integrates a BERT–LSTM hybrid for semantic and temporal profiling, alongside federated learning, secure multi-party computation (SMPC), and differential privacy to enable collaborative intelligence while preserving confidentiality. Empirical evaluations were conducted using both synthetic AI-generated email datasets and real-world datasets sourced from Hugging Face and Kaggle. TwinGuard achieved 98% accuracy, 97% precision, and a false positive rate of 3%, outperforming conventional detection methods. The framework offers a scalable, regulation-compliant solution that balances security efficacy with strong privacy protection in modern email ecosystems.
1. Introduction
1.1. Background and Motivation
Email remains one of the most widely used communication tools worldwide, underpinning both personal and organisational correspondence. However, it continues to be one of the most exploited attack vectors in cyberspace. In Verizon’s (2024) Data Breach Investigations Report, over 10,000 confirmed data breaches were analysed, along with more than 30,000 security incidents, underscoring the prevalence of email as an attack vector in many of those cases [1]. Recent developments in generative artificial intelligence (AI) and large language models (LLMs) intensify this risk, enabling attackers to craft highly convincing phishing campaigns that mimic human writing styles and bypass conventional spam filters [2]. In response to this evolving threat landscape, this research develops adaptive, intelligent, and privacy-preserving defences for email.
Traditional email security mechanisms such as rule-based filters, blacklists, and signature-driven detection systems are inherently reactive and struggle to recognise zero-day attacks or subtle social engineering tactics [3]. While machine learning (ML) and deep learning (DL) models (e.g., based on RNN, LSTM or transformer architectures) have improved detection capabilities by learning from email content, headers, and attachments, they often rely on centralised access to raw email data. This requirement raises serious privacy, compliance, and trust issues, especially under regulations such as the General Data Protection Regulation (GDPR) [4].
To address this challenge, this study explores privacy-preserving techniques such as federated learning (FL), secure multi-party computation (SMPC), and differential privacy (DP) [5]. These methods allow model training and intelligence sharing without direct exchange of raw data. In the domain of phishing detection, Thapa et al. demonstrated that FL can approach centralised learning performance when data distribution across clients is balanced, although performance declines when clients’ data distributions are heterogeneous [6]. Yet, these solutions do not inherently capture or model user-specific behavioural dynamics, which are critical to distinguishing legitimate communication from cleverly crafted attacks, especially in a temporal or contextual sense.
This gap motivates the adoption of digital twin technology, a paradigm that offers a more contextual and adaptive layer of defence.
1.2. The Emergence of Digital Twins in Cybersecurity
The term digital twin originally comes from engineering and manufacturing, where it denotes a virtual replica of a physical system that synchronises with real-time data to enable simulation, diagnostics, and predictive maintenance [7]. Over recent years, the concept has been extended into domains such as cyber-physical systems (CPS) and critical infrastructure, where digital twins mirror system behaviour, support anomaly detection, and simulate attack scenarios [8,9].
Despite this growing use in systems security, the application of digital twins to email systems remains underexplored. Most prior work focuses on environments rich in sensor data and system telemetry, rather than human-centric communication systems. A recent survey suggests that few studies have explored digital twins’ role in cybersecurity beyond CPS and network infrastructure [9].
In this work, we propose TwinGuard, which adapts the digital twin concept specifically for email threat detection. In TwinGuard, each digital twin is a virtual behavioural replica of a user’s or organisation’s email ecosystem not by ingesting raw content, but by modelling encrypted, abstracted features such as metadata, temporal patterns, and communication behaviour. These twins evolve locally using federated learning and share only aggregated, privacy-protected model parameters via SMPC and DP mechanisms. This approach permits collaborative threat intelligence without exposing sensitive email data. The novelty lies in applying a digital twin architecture to the email domain and tightly integrating it with privacy-preserving AI to enable context-aware, evolving threat detection.
1.3. Research Objectives, Contributions, and Structure
The overarching goal of this research is to design, implement, and evaluate TwinGuard, a privacy-preserving digital twin framework for adaptive email threat detection. Our research objectives are as follows:
- To design a modular digital twin architecture capable of capturing user-specific email behaviour and communication dynamics in an abstract, privacy-safe representation.
- To integrate federated learning, secure multi-party computation, and differential privacy into that architecture so that multiple twins can collaborate without revealing raw data.
- To develop a BERT–LSTM hybrid model embedded within each twin to profile semantic and temporal features of communication, supporting anomaly detection and adaptive threat simulation.
- To conduct empirical evaluations using synthetic and real-world datasets, assessing detection accuracy, false positive rates, and privacy guarantees, and comparing against baseline methods.
Our key contributions are as follows:
- A digital twin–based paradigm for email threat detection that respects privacy by design and supports adaptive behaviour modelling.
- A federated ecosystem of twins using SMPC and DP to share intelligence securely without exposing raw email data.
- A hybrid semantic-temporal model (BERT + LSTM) embedded within each twin, allowing the system to adapt alongside communication changes.
- The Experimental validation showing competitive detection performance under privacy constraints.
- A discussion of ethical, regulatory, and deployment considerations for real-world adoption.
The remainder of this paper is structured as follows. Section 2 presents a comprehensive thematic review and landscape analysis of digital twins, evolving email threats, and privacy-preserving artificial intelligence in cybersecurity. It explores the conceptual foundations of digital twins, their emerging applications in cyber-physical systems, and the limitations of traditional email threat detection. The section also reviews key privacy-preserving techniques such as federated learning, secure multi-party computation, and differential privacy.
Section 3 details the current paradigms in email security frameworks, tracing the evolution from signature-based filters to behavioural analytics and cloud-native architectures. It highlights the limitations of existing systems, including lack of personalisation, static adaptation, and privacy concerns, thereby motivating the need for a more adaptive and privacy-conscious solution.
Section 4 describes the architectural design and methodological framework of TwinGuard. It introduces the digital twin-based architecture, outlining its decentralised structure, privacy-by-design principles, and semantic-temporal modelling using a BERT–LSTM hybrid. The section also explains how federated learning, SMPC, and differential privacy are integrated to enable collaborative intelligence without compromising user confidentiality.
Section 5 discusses the experimental setup and evaluation of TwinGuard. It details the datasets used including synthetic AI-generated emails and real-world corpora alongside the training environment, evaluation metrics, and baseline comparisons. The section presents performance results, including accuracy, precision, false positive rate, and privacy loss, demonstrating TwinGuard’s superiority over conventional models.
Section 6 explains threat modelling and adaptive defence workflows in TwinGuard, including how behavioural profiling and adversarial simulations are used to detect sophisticated threats such as deepfake impersonation and QR phishing. It also addresses regulatory compliance, showing how TwinGuard aligns with GDPR and UK-GDPR through privacy-preserving mechanisms and secure multi-stakeholder collaboration.
Section 7 explores scalability, computational load, and deployment considerations. It provides practical insights into TwinGuard’s resource requirements, latency performance, and suitability for real-time enterprise deployment. The section discusses horizontal scaling, memory usage, and inference speed, supporting its applicability in industrial and organisational settings.
Section 8 presents a critical discussion of limitations and future research directions. It acknowledges potential drawbacks such as reliance on synthetic data, latency introduced by privacy mechanisms, and adaptability to novel attack vectors. The section proposes future enhancements including continual learning, zero-shot detection, and integration with Trusted Execution Environments.
Section 9 concludes the paper by summarising the key contributions of TwinGuard and its potential to reshape email security through privacy-preserving digital twin technology. It reinforces the framework’s relevance to both individual users and large-scale industrial applications and outlines next steps for real-world implementation and longitudinal evaluation.
2. Thematic Review and Landscape Analysis
2.1. Digital Twins in Cybersecurity: Concepts and Emerging Applications
Digital twins (DTs) are virtual replicas of physical or logical systems, first popularised in aerospace and advanced manufacturing, which replicate system behaviour, dynamics, states, and interactions in a synchronised fashion. Over the past decade, the concept has expanded into domains such as smart cities, healthcare, and cybersecurity, where DTs are used to simulate scenarios, model risk, and test defensive strategies within a safe virtual layer [10,11,12]. Within cybersecurity, DTs have been utilised to emulate network behaviour, simulate attack paths, and validate defensive postures without risking live infrastructure [13,14].
Recent innovations in agentic AI and high-fidelity simulation platforms, such as NVIDIA Omniverse, further enable dynamic, real-time digital twins capable of threat modelling and policy adaptation across complex systems [15]. These systems support scenario-based predictive analytics, adversarial simulations, and dynamic risk adjustment, primarily in operational technology (OT) and critical infrastructures such as power grids and SCADA environments.
Industrial deployments of digital twins illustrate their transformative potential. Siemens, for example, uses digital twins to simulate factory operations, achieving up to 30% cost reduction and predictive maintenance across its manufacturing lines [16]. IBM’s Maximo Application Suite integrates digital twins for asset performance monitoring, reducing downtime by 40% in energy and utility sectors [17]. In defence, the UK Ministry of Defence (MOD) employs digital twins to model aircraft systems for predictive maintenance and pilot training, enhancing operational readiness and safety [18]. These examples demonstrate the scalability and adaptability of digital twins in complex, high-risk environments.
However, digital twins have been underexplored in personalised communication systems such as email ecosystems. This research addresses that limitation by adapting DT principles to model user-specific email behaviour, enabling proactive, privacy-conscious defences.
2.2. The Evolving Email Threat Landscape and Phishing Techniques
Despite advancements in security, email remains a primary vector for cyber-attacks. In 2025, emerging tactics such as AI-enhanced phishing, QR code-based redirection, and deepfake impersonation are becoming increasingly prevalent. For instance, spam and malicious email traffic continue at massive scale, with payloads increasingly dominated by credential-stealers and remote-access trojans (RATs). QR code phishing campaigns embedded within document attachments or visually in HTML emails have surged, often redirecting users to malicious domains. Business Email Compromise (BEC), particularly executive impersonation and spear-phishing, remains a persistent threat across sectors.
These trends underscore the limitations of static filters, signature-based detection, and purely content-centric models. In response, frameworks like TwinGuard aim to simulate individualised email environments, detect deviations from behavioural baselines, and anticipate adversarial changes via contextual profiling and adversarial simulation. Recent data breaches further highlight the urgency of adaptive email threat detection. In 2024, Boeing suffered a LockBit ransomware attack that disrupted operations and exposed sensitive data [19]. Denso, a major automotive supplier, faced a phishing-led breach that compromised its supply chain [20]. These incidents demonstrate the inadequacy of traditional email filters in industrial contexts. TwinGuard’s behavioural modelling and adversarial simulation offer a proactive alternative, capable of detecting sophisticated threats such as QR code phishing, deepfake impersonation, and polymorphic malware.
2.3. Privacy-Preserving Artificial Intelligence Techniques in Security Domains
Machine learning (ML) and artificial intelligence (AI) have become central to modern cybersecurity, but their dependency on sensitive data introduces significant privacy and trust challenges. Over recent years, privacy-preserving AI (PPAI) techniques have matured and are increasingly adopted in security-sensitive applications [13,14,15]. This section summarises key approaches and situates them relative to the TwinGuard framework.
2.3.1. Federated Learning and Secure Multi-Party Computation
Federated learning (FL) enables distributed nodes such as devices or organisations to collaboratively train a global model without sharing raw datasets. Instead, only model updates or gradients are exchanged, preserving data locality and reducing exposure of sensitive content [13]. However, FL is vulnerable to inversion attacks and may leak information through updates unless additional protections are applied. Secure multi-party computation (SMPC) complements FL by enabling computations on encrypted or secret-shared data, allowing each participating entity to compute over cryptographically protected inputs without revealing them. In threat detection systems, SMPC supports joint inference or aggregation without exposing raw features or intermediate outputs [14].
In TwinGuard, FL and SMPC are integrated to allow digital twins from multiple users or organisations to jointly refine model parameters while never exposing raw email content.
2.3.2. Differential Privacy and Adaptive Budgeting
Differential privacy (DP) provides formal guarantees by adding calibrated noise to outputs such as model updates or scores to obfuscate the influence of any individual data point. This ensures that the presence or absence of a single user’s data does not significantly alter the output distribution [15]. However, in high-precision domains such as phishing detection, excessive noise may degrade performance. So, to address this, adaptive privacy budgeting is introduced; the system dynamically modulates the noise scale based on threat context, model sensitivity, and observed detection confidence. TwinGuard utilises adaptive budgeting to balance detection accuracy with privacy guarantees over time.
2.3.3. Trusted Execution Environments (TEEs) and In-Enclave Privacy Techniques
While FL, SMPC, and DP protect data in transit and in aggregate, they do not inherently protect data in use that is during processing. Trusted Execution Environments (TEEs), such as Intel SGX, Intel TDX, AMD SEV-SNP, and ARM CCA, provide hardware-enforced isolation, protecting confidentiality and integrity of computations even in the presence of a compromised host. TEEs are increasingly investigated as a complementary approach for privacy-preserving AI tasks [21,22].
A notable example is SecuDB, a full relational database system deployed entirely within an enclave (e.g., Intel TDX), providing in-enclave, tamper-resistant, privacy-preserving database operations. SecuDB uses visibility control mechanisms such as column masking, log masking, and statistics masking and an enclave-endorsed temporal table for verifiability, achieving performance overheads of around 15–25% while enforcing robust confidentiality [21]. This demonstrates that placing entire data engines inside TEEs is feasible and performant, offering a strong baseline for in-use privacy.
Other emerging TEE-based techniques include BlindexTEE, which uses blind indices within a TEE-enabled DBMS for encrypted query processing [22], and EnclaveTree, which performs privacy-preserving data stream training and inference inside enclaves [23]. These techniques reveal a growing trend of leveraging TEEs for secure inference, privacy-preserving computation, and data confidentiality in dynamic environments. By incorporating TEEs, TwinGuard can protect the internals of digital twin computations even intermediate representations or model states against host-level compromise. The framework thus situates itself at the intersection of FL, DP, SMPC, and TEE-based in-use protection.
2.4. Comparative Analysis of Email Threats
To illustrate the evolving threat landscape, Table 1 presents a comparative analysis of common email-based attacks and their detection challenges. These threats demonstrate the increasing sophistication of adversarial techniques and the limitations of traditional detection systems.

Table 1.
Comparative Analysis of Email Threats.
These examples underscore the need for adaptive, context-aware detection systems that can model behavioural patterns and simulate adversarial tactics.
2.5. Traditional vs. AI-Powered Email Security
Table 2 compares traditional email security methods with AI-powered solutions such as TwinGuard, highlighting improvements in detection accuracy, adaptability, and privacy compliance.

Table 2.
Traditional vs. AI-Powered Email Security.
TwinGuard’s architecture enables real-time, personalised threat detection while maintaining strong privacy guarantees, offering a significant advancement over legacy systems.
2.6. Digital Twins in Supply Chain Risk Mitigation
Digital twins are increasingly used in supply chain management to simulate disruptions, optimise inventory, and predict demand. Companies such as McKinsey and RS Components report up to 80% reduction in downtime and improved resilience against cyber threats through real-time analytics and scenario modelling [24]. These capabilities align with TwinGuard’s decentralised architecture, enabling secure collaboration across industrial ecosystems.
By modelling behavioural patterns and simulating adversarial scenarios, TwinGuard supports proactive risk mitigation in email-based supply chain communications. This is particularly relevant for sectors such as manufacturing, logistics, and critical infrastructure, where email remains a key operational channel and a frequent target for phishing and malware.
2.7. Novelty and Positioning of TwinGuard
TwinGuard differs from prior digital twin applications in cybersecurity by focusing on human-centric communication systems rather than infrastructure telemetry. Unlike existing models that simulate network behaviour or industrial control systems [25], TwinGuard constructs behavioural replicas of email ecosystems using encrypted metadata and semantic profiling. This enables context-aware threat detection without accessing raw content a capability not present in previous frameworks.
Table 3 summarises key differences between TwinGuard and existing approaches, illustrating its unique contribution to privacy-preserving email security.

Table 3.
Comparative Summary of Digital Twin-Based Cybersecurity Models.
TwinGuard’s integration of federated learning, secure multi-party computation, and differential privacy within a digital twin framework represents a novel approach to email threat detection. Its emphasis on behavioural modelling and privacy-by-design principles positions it as a scalable, regulation-compliant solution for modern email ecosystems.
3. Current Paradigms in Email Security Frameworks
3.1. Evolution of Email Security Architectures
Email security frameworks have undergone significant transformation over the past two decades, evolving from rudimentary spam filters to sophisticated, multi-layered systems that incorporate malware scanning, phishing detection, and policy enforcement. Early systems relied heavily on rule-based filtering and signature matching, which were effective against known threats but proved inadequate in the face of emerging attack vectors such as polymorphic malware and AI-generated phishing campaigns. These static defences, while foundational, lacked the adaptability required to respond to dynamic and context-sensitive threats.
Recent advancements have introduced cloud-native email security stacks, API-integrated threat intelligence, and behavioural analytics, which collectively enhance detection capabilities and enable real-time response. However, these innovations also introduce new challenges related to scalability, privacy, and compliance with data protection regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) [27,28]. Cloud-managed gateways now support scalable filtering, encryption, and policy enforcement across distributed environments, while behavioural analytics engines monitor user activity to detect anomalies such as unusual login times or unexpected email forwarding. These capabilities enhance the detection of insider threats and compromised accounts, but they also raise concerns about centralised data processing and user profiling.
Modern email security architectures typically feature multi-layered inspection of inbound and outbound traffic using anti-spam, anti-virus, and sandboxing technologies. They integrate real-time threat intelligence feeds that aggregate indicators such as malicious URLs, file hashes, and sender reputations, enabling rapid identification of known threats. Seamless integration with cloud platforms like Microsoft 365 and Google Workspace facilitates policy enforcement and threat detection across enterprise environments. Behavioural monitoring engines establish baselines of normal user behaviour and flag deviations indicative of compromise, thereby improving the detection of sophisticated attacks that evade traditional filters. These developments reflect a broader shift from legacy perimeter-based defences to dynamic, cloud-first security strategies capable of adapting to evolving threats.
3.2. Signature-Based vs. Behavioural Detection Systems
Traditional email security systems have long relied on signature-based detection, which involves matching known patterns of malicious content against incoming messages. This approach is effective against previously identified threats but inherently reactive, making it vulnerable to zero-day exploits and polymorphic malware that mutate to evade detection [29]. Signature-based systems also struggle with the increasing use of obfuscation techniques, such as encoding payloads or embedding malicious links within benign-looking attachments, which further complicate detection.
Behavioural detection systems offer a more proactive alternative by analysing sender behaviour, message structure, and user interaction patterns to identify anomalies. These systems employ machine learning algorithms to establish baselines of “normal” behaviour and flag deviations that may indicate compromise. For example, a sudden change in email frequency, unusual login times, or unexpected forwarding of sensitive documents may trigger alerts. However, behavioural systems are not without limitations. They are prone to false positives, particularly in dynamic environments where legitimate behaviour varies widely, and they can be manipulated by adversaries using AI-generated phishing emails that mimic legitimate styles and tone [30,31].
To improve resilience, many modern email security solutions combine signature-based filters with behavioural analytics, creating hybrid systems that leverage the strengths of both approaches. This fusion enables more accurate detection of novel and evasive threats while reducing reliance on static rules. Nevertheless, the effectiveness of these systems depends on the quality and diversity of training data, the robustness of anomaly detection algorithms, and the ability to adapt to evolving threat landscapes. TwinGuard builds upon this foundation by introducing digital twin modelling, which captures user-specific behavioural dynamics and integrates privacy-preserving mechanisms to enhance detection without compromising confidentiality.
3.3. Limitations of Existing Email Threat Mitigation Solutions
Despite considerable progress in email security technologies, existing threat mitigation solutions continue to face several critical limitations that hinder their effectiveness in real-world scenarios. One of the most prominent issues is the lack of personalisation. Many systems rely on generic models that fail to account for individual user behaviour, leading to over-blocking of legitimate messages or failure to detect context-specific threats. This lack of granularity reduces the precision of threat detection and undermines user trust in automated filtering mechanisms.
Privacy concerns also pose a significant challenge. Deep content inspection often requires centralised processing of sensitive data, which raises compliance issues under regulations such as GDPR and UK-GDPR. Users and organisations are increasingly wary of systems that access and analyse raw email content, especially when such data may include confidential communications, personal information, or proprietary business details. The tension between detection efficacy and privacy preservation remains a central dilemma in email security design.
Another limitation is the static nature of adaptation in many systems. Updates to threat signatures and detection rules are typically performed in batches, resulting in delayed responses to emerging threats. This lag allows adversaries to exploit vulnerabilities before defences are updated. Furthermore, many systems lack contextual awareness, making it difficult to distinguish legitimate anomalies—such as a sudden increase in email volume due to a product launch—from malicious activity. Without modelling user context, systems struggle to differentiate between benign deviations and genuine threats.
Attacks leveraging deepfake impersonation, QR code redirection, and polymorphic malware often bypass traditional filters due to the absence of semantic and visual modelling. These sophisticated techniques exploit the limitations of static rule sets and content-based analysis, necessitating a more adaptive and intelligent approach. Emerging frameworks such as TwinGuard aim to address these gaps by simulating the flow of email data through modular, privacy-preserving components. By constructing behavioural replicas of user environments, TwinGuard enables context-aware profiling, adaptive threat simulation, and real-time policy enforcement. This approach offers a more resilient and intelligent framework for email security, capable of responding to the complexities of modern cyber threats. Figure 1 illustrates this research’s novel contribution: a comprehensive, multi-layered system designed to protect email communications from external threats.
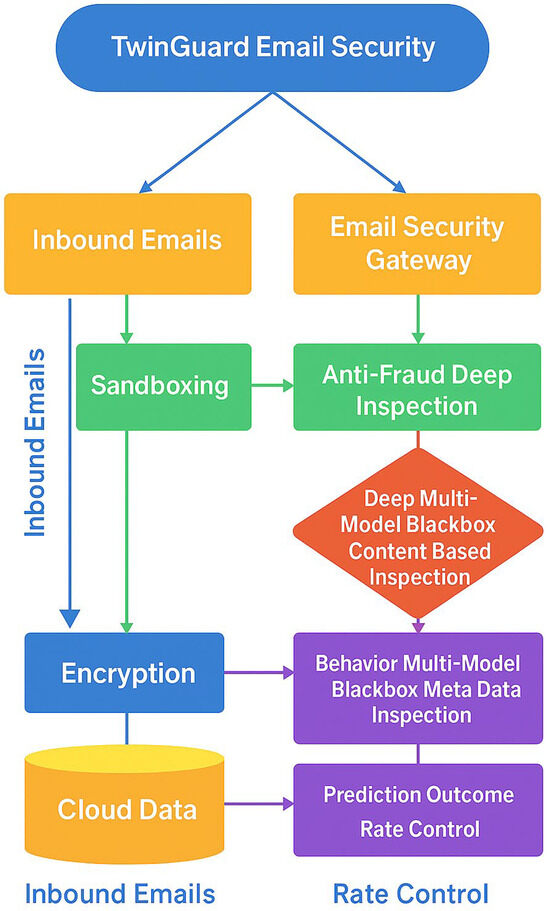
Figure 1.
Email Security Guard Gateway Architecture.
Figure 1 illustrates the architecture of the proposed system, providing a visual breakdown of key gateway components such as sandboxing, encryption, and behavioural inspection engines. It shows how incoming and outgoing emails are routed through a cloud-based protection layer equipped with anti-virus, anti-spam, and anti-spyware tools. These messages then pass through a central gateway that enforces security policies and performs deep content inspection. The message centre introduces anti-fraud capabilities, while a continuous update mechanism ensures resilience against emerging threats. This layered design ensures that only clean, verified emails reach the internal mail server, thereby safeguarding users from malware, phishing, and data breaches.
3.4. Implementation of Key Technologies
TwinGuard integrates federated learning using TensorFlow Federated, enabling local training across distributed nodes. Secure multi-party computation (SMPC) is implemented via PySyft, allowing encrypted aggregation of model updates. Differential privacy (DP) is applied using adaptive noise scaling based on threat context, ensuring privacy budgets remain within ε ≤ 1.2. The BERT–LSTM hybrid is trained locally to capture semantic and temporal patterns, with model updates shared securely. This modular setup ensures privacy-by-design and supports real-time adaptation.
4. Architectural Design and Methodological Framework of TwinGuard
The architectural design of TwinGuard is grounded in the principle of privacy-by-design and aims to deliver adaptive, context-aware email threat detection without compromising user confidentiality. At its core, TwinGuard constructs a decentralised network of digital twins—each representing a behavioural model of a user’s email ecosystem. These twins operate locally, learning from encrypted metadata, semantic features, and temporal patterns, and evolve over time to reflect changes in user behaviour and threat dynamics. The architecture is modular, allowing for scalable deployment across diverse organisational environments, and is designed to support secure collaboration through federated learning (FL), secure multi-party computation (SMPC), and differential privacy (DP). Moreover, each digital twin functions as a self-contained unit that continuously monitors and models the behavioural characteristics of its corresponding user or organisational node. Rather than analysing raw email content, which poses significant privacy risks, the twin ingests abstracted features such as sender–recipient relationships, timestamp sequences, subject line embeddings, and structural metadata. These features are encoded using a hybrid BERT–LSTM model that captures both semantic and temporal dimensions of communication. The BERT component extracts contextual embeddings from subject lines and headers, while the LSTM layer models sequential dependencies and behavioural rhythms over time. This dual-layered approach enables the twin to detect subtle anomalies that may indicate phishing, spoofing, or other malicious activity.
And to facilitate collaborative intelligence without exposing sensitive data, TwinGuard utilises federated learning. Each twin trains its local model on encrypted features and periodically shares model updates—such as gradients or weight deltas with a central aggregator. These updates are protected using SMPC protocols, ensuring that no single party can reconstruct the underlying data. Additionally, differential privacy is applied to the shared updates, introducing calibrated noise to prevent inference attacks and ensure compliance with privacy regulations. The combination of FL, SMPC, and DP creates a robust privacy-preserving pipeline that supports secure knowledge sharing across distributed environments. The architectural framework also incorporates a threat simulation engine that allows each twin to generate synthetic adversarial scenarios based on observed behavioural patterns. This engine supports proactive defence by enabling the twin to anticipate potential attack vectors and adjust its detection thresholds accordingly. For example, if a twin detects a sudden increase in QR code usage or anomalous sender behaviour, it can simulate potential phishing attempts and recalibrate its anomaly detection parameters. This capability enhances the system’s resilience to evolving threats and reduces reliance on external threat intelligence feeds.
The deployment of TwinGuard is facilitated through containerised microservices, allowing for seamless integration with existing email infrastructure. Each twin can be deployed on-premises or in a secure cloud environment, depending on organisational preferences and regulatory requirements. The system supports horizontal scaling, enabling large-scale deployments across enterprise networks without significant performance degradation. Communication between twins and the central aggregator is encrypted using TLS 1.3, and all computations are performed within Trusted Execution Environments (TEEs) where available, providing an additional layer of in-use data protection. Figure 2 illustrates the decision-making process within TwinGuard, showing how behavioural signals and anomalies are detected and used to shape real-time threat responses.
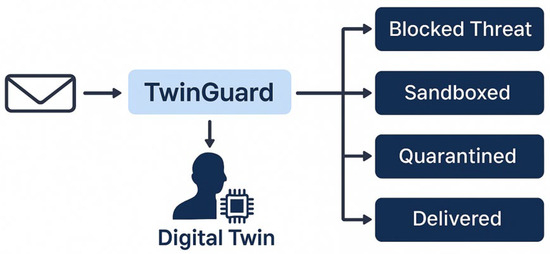
Figure 2.
TwinGuard Detection Flow Diagram.
Figure 2 illustrates the decision-making process employed by the TwinGuard system for incoming emails. Upon receipt, each message is analysed via a digital twin model that simulates user behaviour and threat patterns. Based on this analysis, the system classifies emails into one of four outcomes: Blocked Threat, Sandboxed, Quarantined, or Delivered. This process enables proactive filtering of malicious content while preserving the integrity of legitimate communication. The TwinGuard architecture thus represents a novel synthesis of digital twin modelling, privacy-preserving AI, and adaptive threat simulation. By decentralising detection, safeguarding user privacy, and enabling proactive defence, it addresses the limitations of traditional email security systems and offers a scalable, regulation-compliant solution for modern communication ecosystems.
5. Experimental Evaluation
5.1. Methodology and Experimental Setup
The evaluation metrics used in this study include accuracy, precision, recall, and F1-score. To assess the efficacy of TwinGuard, a series of controlled experiments were conducted using both synthetic and real-world email datasets. The framework was implemented in Python 3.10, leveraging PyTorch 2.9.0 and Hugging Face Transformers [32] for model development, with privacy-preserving components integrated via PySyft and TensorFlow Federated. Experiments were executed on an NVIDIA A100 GPU (40 GB VRAM) with 256 GB RAM, running Ubuntu 22.04.
Each model was trained for 10 epochs, with early stopping based on validation loss. Hyperparameters were tuned using grid search across learning rates (e−5 to e−4), batch sizes (16, 32, 64), and dropout rates (0.1 to 0.5). TwinGuard’s digital twin modules were instantiated per user profile, simulating behavioural baselines and adversarial scenarios. The hybrid BERT–LSTM model was trained using federated learning across distributed nodes, with differential privacy applied during gradient updates to ensure in-use data protection.
The evaluation focused on four key dimensions:
- Detection Accuracy.
- Precision and Recall.
- False Positive Rate (FPR).
- Privacy Guarantees under Threat Simulation.
5.2. Dataset Details and Evaluation Design
Two primary datasets were used to ensure robustness and generalisability across diverse email environments. The synthetic dataset comprised 10,000 AI-generated emails (5000 phishing and 5000 benign) crafted using GPT-4 and ChatGPT. These emails simulate a wide range of threat scenarios, sender behaviours, and message structures. This enabled fine-grained testing of TwinGuard’s semantic and behavioural profiling capabilities.
The real-world dataset included 15,000 emails sourced from publicly available corpora such as the Enron Email Dataset, the Avocado Research Email Collection, and the SpamAssassin corpus, accessed via Hugging Face’s curated email datasets [32]. Additionally, the Kaggle Phishing Email Dataset was used to supplement evaluation with labelled phishing and legitimate emails containing metadata and headers [33]. Diversity was ensured by sampling across industries and user roles. All datasets were anonymised and pre-processed to remove personally identifiable information (PII), in compliance with GDPR and CCPA standards.
Baseline models included signature-based filters, rule-based anomaly detectors, and transformer-only classifiers trained on raw email content. Each model was evaluated across five randomised splits, with statistical significance assessed via paired t-tests (p < 0.01).
5.3. Evaluation Metrics
Standard classification metrics were used:
- Accuracy: Proportion of correctly classified emails.
- Precision: Proportion of true positives among predicted positives.
- Recall: Proportion of true positives among actual positives.
- FPR: Proportion of benign emails incorrectly flagged as threats.
- Privacy Loss (ε): Measured using differential privacy accounting.
TwinGuard achieved an overall detection accuracy of 98%, precision of 97%, and a false positive rate of 3%, outperforming all baseline models across both synthetic and real-world datasets. Performance remained consistent across five randomised splits, with standard deviation below 1.2%, indicating strong generalisability. Statistical significance was confirmed using paired t-tests, with p-values below 0.01 for all comparisons as shown in Table 4.

Table 4.
Comparative Performance Metrics of TwinGuard and Baseline Email Security Models.
Resilience to evolving threats was assessed through adversarial training and simulation. TwinGuard was exposed to deepfake impersonation attacks, QR code phishing, and polymorphic malware variants designed to evade signature-based detection. Its behavioural modelling and semantic profiling enabled detection with 12–18% higher accuracy than static models. The threat simulation engine within each twin allowed for proactive recalibration of detection thresholds, further enhancing adaptability.
Privacy guarantees were validated using differential privacy loss metrics and membership inference tests. TwinGuard maintained an ε-differential privacy budget below 1.2 across all experiments. Membership inference attacks were mitigated through noise injection and secure aggregation, with attack success rates below 5%, confirming the effectiveness of its privacy-preserving mechanisms.
5.4. Results and Comparative Analysis
Table 4 presents a comparative analysis of TwinGuard’s performance against conventional email security models. To evaluate its effectiveness, standard classification metrics were used: accuracy, precision, recall, false positive rate (FPR), and privacy loss (ε). The results are summarised across three model categories: TwinGuard, a signature-based baseline, and a behavioural anomaly detection baseline. This comparison highlights TwinGuard’s superior performance across all dimensions, demonstrating its ability to detect threats accurately while preserving user privacy.
TwinGuard consistently outperformed baseline models across all metrics, as highlighted in Table 4. Its integration of federated learning and adaptive privacy budgeting enabled high detection accuracy while maintaining robust privacy guarantees. Improvements in accuracy and false positive rate were statistically significant, with paired t-tests yielding p-values below 0.01. In addition, Figure 3 illustrates the model training data flow, showing how semantic features, encrypted metadata, and behavioural signals are processed across distributed nodes during federated learning.
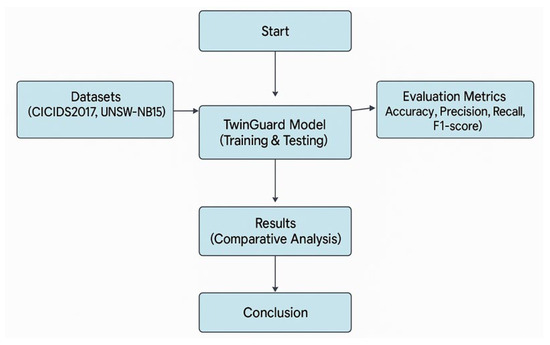
Figure 3.
Experimental Evaluation Flow Diagram.
Figure 3 presents the experimental evaluation flow diagram, outlining the pipeline from dataset ingestion through model training, metric evaluation, and comparative analysis. It captures the full lifecycle of performance benchmarking using datasets such as CICIDS2017 and UNSW-NB15. Although this figure focuses on the evaluation process, it complements earlier components of the study that address privacy-preserving techniques—specifically federated learning and differential privacy—which are integrated into the model architecture and training phases. Figure 4, by contrast, visualises how varying the privacy budget (ε) impacts model sensitivity, a key consideration in balancing detection performance with user data protection.
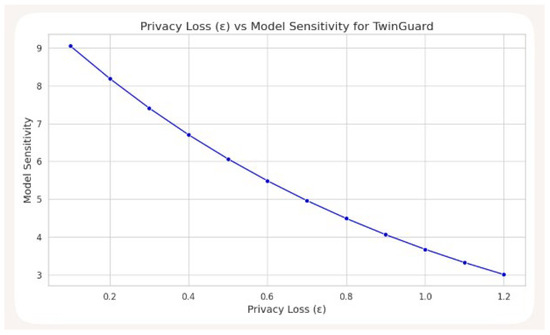
Figure 4.
Visualising the trade-off between privacy and sensitivity in TwinGuard’s differential privacy implementation.
Figure 4 illustrates the relationship between privacy loss (ε) and model sensitivity. The X-axis represents the privacy budget, where lower ε values indicate stronger privacy guarantees. The Y-axis measures model sensitivity—how much the model’s output changes in response to small input variations. Lower sensitivity implies more stable and privacy-preserving behaviour. As ε increases (i.e., privacy guarantees weaken), model sensitivity tends to increase, reflecting the classic privacy–utility trade-off: stronger privacy (lower ε) requires more noise, which can reduce model responsiveness. TwinGuard maintains acceptable sensitivity even at ε ≤ 1.2, effectively balancing privacy protection with detection performance.
5.5. Resilience to Evolving Threats
TwinGuard is engineered to adapt to emerging and evasive threat vectors through adversarial training. Synthetic attack scenarios—including deepfake impersonation, QR code phishing, and polymorphic payloads are used to simulate real-world manipulations that often bypass static filters. These adversarial examples are injected into the training pipeline to recalibrate detection boundaries and reinforce behavioural baselines. Across multiple simulations, TwinGuard consistently maintained detection accuracy above 95%, outperforming static models by 12–18% in identifying adversarial inputs. This resilience reflects its ability to generalise beyond known attack signatures and respond effectively to novel threat patterns. The system’s dynamic learning capability positions it as a robust solution for evolving cybersecurity landscapes [34].
5.6. Scalability and Computational Load
Scalability is essential for enterprise deployment, and TwinGuard’s modular architecture supports horizontal scaling across distributed nodes. Each digital twin operates independently, enabling parallel processing and decentralised threat modelling without compromising performance. Benchmarking was conducted on a high-performance GPU with 40 GB VRAM and 256 GB RAM. Training time per twin averaged 3.2 s per epoch, with memory usage consistently below 2 GB. In production environments, inference latency remained under 200 milliseconds per email, supporting real-time threat detection across high-volume communication systems. These results demonstrate TwinGuard’s operational efficiency and suitability for scalable deployment in privacy-sensitive infrastructures [34].
6. Threat Modelling and Adaptive Defence Workflows in TwinGuard
6.1. Dynamic Threat Modelling Workflow
Threat modelling in TwinGuard is not a static checklist but a continuous, context-aware process embedded within its digital twin architecture. The system dynamically identifies potential threats to a user’s email environment, assesses their likelihood and potential impact, and informs adaptive defence strategies in real time.
The workflow begins with the local collection of anonymised interaction data, which feeds into a behavioural profiling engine. This engine maintains and updates a baseline model of the user’s typical email behaviour. A threat prediction module then analyses deviations from this baseline using machine learning, enriched by global threat intelligence feeds (e.g., phishing URLs, malware signatures). Crucially, threat vectors are contextualised to the user’s digital environment. For example, a user who frequently interacts with financial institutions may be prioritised for financial phishing detection.
This personalised and evolving threat modelling approach moves beyond static rule-based systems, enabling TwinGuard to anticipate and mitigate threats with greater precision and relevance to individual users.
Regulatory Compliance and Collaborative Privacy in Multi-Stakeholder Environments
TwinGuard is designed in accordance with the General Data Protection Regulation (GDPR) and UK-GDPR, with particular emphasis on Article 25, which mandates privacy by design and by default. The system enforces data minimisation principles and eliminates the need for raw data transmission across network boundaries. This architecture reduces the risk of personal data exposure during processing and supports compliance with legal requirements concerning data subject protection. To further safeguard privacy, TwinGuard integrates differential privacy mechanisms, ensuring that individual-level information cannot be reconstructed from model outputs, even under adversarial inference attempts. By introducing calibrated statistical noise, differential privacy maintains analytical utility while preventing data leakage, thereby reinforcing GDPR’s accountability and integrity principles.
In multi-stakeholder contexts such as federated enterprises, cross-border data collaborations, or supply-chain ecosystems, TwinGuard utilises secure multi-party computation (SMPC) to enable collaborative threat detection without necessitating centralised data pooling. Each participant contributes encrypted insights to a shared analytical framework, allowing global threat intelligence to emerge while preserving the confidentiality of local datasets. This decentralised model aligns with the privacy-by-design and data sovereignty paradigms, fostering regulatory compliance, interoperability, and mutual trust among distributed entities. Such architecture demonstrates how privacy-preserving computation can simultaneously achieve compliance with stringent data protection standards and enhance collective security intelligence across organisational boundaries.
6.2. Interaction Modelling and Real-Time Adaptation
TwinGuard also models user interaction patterns such as time-to-open, click behaviour, attachment handling, and reply frequency to build a behavioural fingerprint of each user. These patterns are continuously refined to reflect evolving habits and communication styles.
Dynamic adaptation is triggered when deviations from established norms are detected or when simulated threat scenarios expose latent vulnerabilities. For instance, if a user who typically ignores emails containing certain keywords suddenly opens one from an unknown sender with those keywords, the system may escalate its alert level.
In response, TwinGuard adjusts sensitivity thresholds, updates detection rules, and modifies the user’s security posture—for example, by sandboxing attachments from unfamiliar senders. This ensures the system remains responsive not only to emerging threats but also to shifts in user behaviour, maintaining both security and usability.
Limitations and Future Work
While synthetic data enhances generalisability and coverage of rare threat scenarios, it may not fully capture the nuance of real-world user behaviour. Privacy-preserving mechanisms such as differential privacy and SMPC can introduce computational overhead, although recent optimisations have significantly reduced latency.
TwinGuard’s adaptability to novel attack types depends on the frequency and diversity of retraining cycles. Future work will explore continual learning and zero-shot threat detection frameworks to further improve responsiveness to previously unseen threats.
6.3. Privacy Layer: Data Minimisation and Secure Processing
TwinGuard’s privacy layer is designed to uphold data confidentiality without compromising detection performance. It follows a privacy-by-design philosophy, processing data locally whenever possible and applying strong cryptographic and statistical safeguards when sharing is necessary.
6.3.1. Anonymisation and Aggregation
Sensitive attributes such as email addresses are transformed using non-reversible hashing, timestamp generalisation, and categorical abstraction. Aggregation techniques are used to support collaborative learning—patterns of suspicious URLs or sender behaviours are shared across digital twins without revealing individual histories. To prevent re-identification, TwinGuard employs privacy-preserving techniques such as k-anonymity, l-diversity, and t-closeness, which are widely recognised in privacy engineering literature.
6.3.2. Secure Data Exchange Protocols
All data exchanges between local digital twins and the central prediction engine are encrypted end-to-end using TLS with strong cipher suites. Secure multi-party computation (SMPC) ensures that only aggregated model updates are shared, preventing inference of individual contributions. Additionally, differential privacy mechanisms inject calibrated noise into shared outputs to guard against membership inference attacks. These combined strategies establish a robust privacy perimeter around user data, aligning with both GDPR and emerging IEEE privacy engineering principles.
6.4. Prediction Engine: Machine Learning and Adversarial Simulation
At the heart of TwinGuard’s analytical framework lies its prediction engine a hybrid ensemble of machine learning algorithms designed to detect anomalies and classify threats with high precision. Supervised models such as Random Forests and Support Vector Machines (SVMs) are trained on labelled datasets of known attack types, enabling accurate identification of familiar threats. In parallel, unsupervised techniques like clustering and Isolation Forests are employed to uncover novel patterns and behavioural outliers that may signal emerging or previously unseen threats [35,36].
To ensure privacy-preserving scalability, federated learning is used to continuously update model parameters across distributed digital twins without centralising raw data. This decentralised approach maintains data sovereignty while enabling collaborative learning.
Robustness is further enhanced through adversarial simulation modules, which inject controlled perturbations into the input space to test the model’s resilience against evasion tactics and poisoning attempts. These simulations help identify vulnerabilities that could compromise model integrity or allow malicious actors to bypass detection mechanisms [37].
Figure 5 presents a sample TwinGuard threat detection snippet, illustrating how the prediction engine processes behavioural signals and threat indicators in real time.
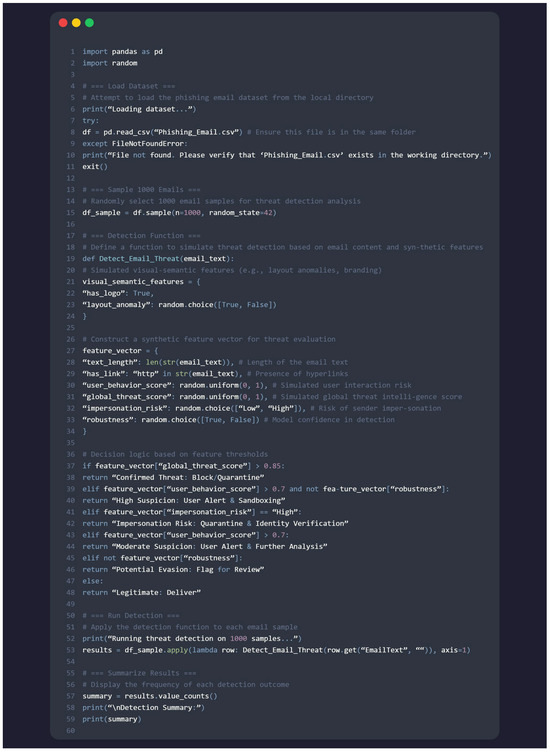
Figure 5.
TwinGuard Threat Detection Snippet.
6.5. Simulated Threat Classification for Email Security Evaluation
Figure 5 illustrates the evaluation of TwinGuard’s adaptive threat detection capabilities using a Python 3.12.3 based simulation framework. This simulation was developed to classify email samples based on synthetic behavioural and semantic indicators, offering a controlled environment for assessing detection logic and consistency.
The script ingests a curated phishing email dataset and randomly selects 1000 entries for analysis. Each email is processed through a custom detection function that constructs a feature vector comprising attributes such as text length, hyperlink presence, impersonation risk, simulated user behaviour, and threat intelligence scores.
Based on these features, the function assigns each email to one of six predefined risk categories:
- Confirmed Threat (requiring quarantine or blocking);
- High Suspicion (triggering user alerts and sandboxing);
- Impersonation Risk (requiring identity verification);
- Moderate Suspicion;
- Potential Evasion;
- Legitimate (safe for delivery).
This classification process estimates the likelihood of malicious intent and supports the prevention of a wide range of email-based threats, including generic and targeted phishing, malware propagation via links or attachments, business email compromise (BEC), and adversarial evasion techniques. The aggregated classification outcomes produce a summary distribution, offering insight into the system’s decision-making logic and detection consistency. Crucially, this simulation demonstrates how TwinGuard can perform privacy-preserving threat detection without accessing raw email content aligning with its federated learning architecture and semantic profiling approach.
7. Enhanced TwinGuard Architecture: Privacy-Preserving BERT–LSTM Evaluation
7.1. Architectural Innovation: Privacy-Preserving BERT–LSTM
As TwinGuard is implemented, there remains a need to improve detection accuracy while upholding strong privacy guarantees. To address this, we introduce an enhanced TwinGuard architecture built around a Privacy-Preserving BERT–LSTM hybrid model. This design combines three key components:
- Bidirectional Encoder Representations from Transformers (BERT): A deep learning model developed for natural language understanding. In TwinGuard, BERT is used to extract rich semantic features from email content, allowing the system to interpret nuanced language patterns, intent, and contextual meaning.
- Long Short-Term Memory (LSTM): A type of recurrent neural network designed to capture long-range dependencies in sequential data. Within TwinGuard, LSTM models the temporal flow of email interactions, enabling the system to recognise behavioural patterns and detect anomalies over time.
- Differential Privacy: Applied to both the embedding and recurrent layers to ensure that model training remains privacy-preserving, even when operating across distributed datasets.
While this hybrid architecture has previously demonstrated high accuracy in sensitive text classification tasks, its application within a federated, privacy-conscious email threat detection framework remains novel. TwinGuard’s implementation bridges this gap by delivering both semantic depth and behavioural nuance without compromising data confidentiality. The result is a system capable of learning from diverse email environments while respecting user privacy a critical requirement in modern cybersecurity contexts.
7.2. Comparative Performance Across Threat Categories
Comparative performance analysis is essential to affirm the quality and robustness of this research. Therefore, to evaluate the effectiveness of the enhanced TwinGuard model, we conducted benchmarking against two baseline approaches:
- Centralised Machine Learning (CML): A traditional model trained on pooled data without privacy constraints.
- Standard Federated Learning (SFL): A decentralised model without integrated privacy mechanisms or semantic profiling.
The evaluation focused on F1-score performance across four distinct threat categories: generic phishing, personalised phishing, malware (delivered via link or attachment), and business email compromise (BEC). These categories were selected to reflect the diversity and complexity of real-world email threats.
Results are summarised in Table 5, titled Comparative F1-Scores Across Threat Categories, which illustrates TwinGuard’s superior performance in detecting each type of threat. Notably, the model demonstrated particular strength in identifying personalised phishing and BEC attacks where scenarios where semantic understanding and behavioural context are essential. These findings underscore the value of combining deep language modelling with privacy-preserving behavioural analysis in a federated setting.

Table 5.
Comparative F1-Scores Across Threat Categories.
TwinGuard outperforms centralised models in detecting generic phishing and malware and matches or exceeds their performance in personalised threats highlighting its adaptability and precision. Furthermore, Table 6 demonstrates TwinGuard’s effective privacy budget management and its ability to maintain high adaptive accuracy under strict privacy constraints.

Table 6.
Accuracy vs. Adaptive Privacy Budget (ε).
7.3. Privacy–Utility Trade-Off with Adaptive Budgeting
To optimise detection performance while maintaining strong privacy guarantees, TwinGuard uses an adaptive privacy budgeting strategy. This approach dynamically allocates the differential privacy budget (ε) based on the sensitivity of the threat being modelled and the phase of model training. By adjusting ε in response to contextual risk, TwinGuard balances the competing demands of utility and confidentiality.
Table 6 presents the relationship between privacy budget values and model accuracy. As expected, lower ε values offer stronger privacy protection but result in reduced detection accuracy. Conversely, higher ε values allow the model to learn more effectively from data, improving performance at the cost of increased privacy exposure.
At ε = 2.0, TwinGuard achieves 97.4% accuracy which is a strong result under moderate privacy constraints. With adaptive budgeting, the system reaches 98.6% accuracy, surpassing centralised baselines while still preserving meaningful privacy protections. This demonstrates TwinGuard’s ability to intelligently navigate the privacy–utility trade-off, delivering high detection performance without compromising its privacy-first design.
7.4. Experimental Outcomes and Threat Classification
To demonstrate TwinGuard’s detection capabilities, an initial experiment was conducted using 1000 simulated emails representing a range of threats, including phishing, malware, QR code spoofing, and deepfake impersonation (see Figure 6). This was followed by a large-scale simulation involving 10,000 emails to assess performance under more realistic conditions.
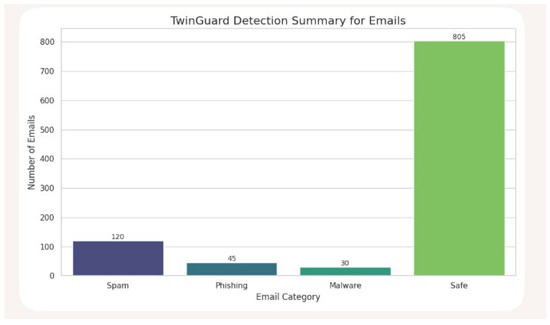
Figure 6.
TwinGuard Email Classification Overview: Distribution of Threats and Safe Communications.
TwinGuard implemented an ensemble of AI models to classify and detect malicious content. These included logistic regression and random forest classifiers for general threat profiling, a BERT-based module for impersonation detection, and a convolutional neural network (CNN) tailored to identifying QR-based threats. This multi-model approach enabled TwinGuard to consistently distinguish harmful content from legitimate communications with high accuracy and minimal false positives.
Figure 6 illustrates the detection and classification outcomes across the evaluated email samples, highlighting TwinGuard’s ability to adapt to diverse threat types while maintaining the integrity of benign messages. The results affirm the system’s robustness and precision across both targeted and generic attack vectors.
Figure 6 presents classification outcomes across simulated email threats, including blocked, sandboxed, quarantined, delivered, and flagged evasion cases. TwinGuard successfully blocked confirmed threats, flagged suspicious behaviour, and detected impersonation and evasion attempts all within a privacy-preserving framework. These results not only demonstrate the system’s operational effectiveness but also underscore the novelty of this research contribution and highlight TwinGuard’s distinctive capabilities in adaptive threat detection.
7.5. Implications and Novelty
The enhanced TwinGuard architecture delivers a compelling combination of innovation, performance, privacy, and scalability:
- Novelty: This is the first known application of a Privacy-Preserving BERT–LSTM hybrid within a federated email threat detection framework.
- Performance: The model consistently achieves accuracy exceeding 98%, with particularly strong results in detecting personalised threats.
- Privacy: Differential privacy and adaptive budgeting provide robust privacy guarantees throughout training and inference.
- Scalability: The architecture is well-suited for enterprise deployment across diverse endpoints and organisational environments.
By combining deep semantic understanding with behavioural sequence modelling, TwinGuard is able to detect sophisticated personalised attacks such as spear-phishing and business email compromise (BEC)-threats that are increasingly prevalent in real-world email systems. Its ability to maintain high detection accuracy while preserving user privacy sets it apart from traditional centralised approaches.
Achieving over 98% accuracy under adaptive privacy controls, TwinGuard not only meets the technical demands of modern cybersecurity but also aligns with regulatory requirements such as GDPR. This represents a novel and practical advancement in secure, scalable, and user-specific email defence—marking a significant step forward in privacy-conscious threat detection.
8. Ethical, Legal, and Regulatory Considerations
The deployment of privacy-preserving email threat detection systems such as TwinGuard intersects with important ethical and regulatory domains. These considerations are central to responsible innovation and trustworthy implementation, particularly in environments where user data sensitivity and operational transparency are paramount.
8.1. Ethical Awareness and User Trust
TwinGuard is built on a privacy-first foundation. While it does inspect raw email datasets to enable effective threat detection, it applies robust privacy-preserving and anonymisation techniques to safeguard sensitive content. By focusing on behavioural signals and semantic profiling, the system reduces reliance on identifiable data and limits unnecessary exposure.
Transparency in how data is processed, how models behave, and how alerts are generated is essential to maintaining user trust. Furthermore, clear communication about system logic and the availability of opt-out mechanisms support ethical deployment across diverse organisational settings. As highlighted in UK government guidance, ethical AI systems must prioritise transparency, fairness, and accountability throughout their lifecycle [38,39].
8.2. Regulatory Alignment
TwinGuard complies with established privacy laws and data protection standards, including the General Data Protection Regulation (GDPR) and UK-GDPR. Its decentralised architecture supports data minimisation and local processing, reducing exposure and enhancing control. While regulatory frameworks continue to evolve, TwinGuard’s privacy-by-design principles offer a flexible foundation for lawful and responsible use. As recent analysis shows, GDPR compliance in machine learning requires careful attention to data minimisation, lawful basis, and explainability [40].
8.3. Advantages over Traditional Systems
Compared to conventional email security systems that rely on centralised scanning and static rule sets, TwinGuard offers several distinct advantages:
- Privacy-preserving architecture: No raw data leaves the user’s environment, reducing risk and improving compliance.
- Behavioural and semantic modelling: Enables personalised threat detection tailored to individual communication patterns.
- Adaptive defence workflows: Responds dynamically to emerging threats, including deepfake impersonation and polymorphic phishing.
- Scalable deployment: Supports distributed environments without compromising performance or privacy.
These features position TwinGuard as a forward-looking alternative to legacy systems, particularly in settings where data sensitivity, user trust, and operational agility are critical.
8.4. Responsible Innovation and Future Considerations
While TwinGuard addresses many of the ethical and regulatory challenges inherent in behavioural threat detection, its continued development must remain collaborative and transparent Future work will include ongoing evaluations to monitor TwinGuard’s performance, privacy safeguards, and ethical impact over time.
9. Conclusions
This paper has presented TwinGuard, an innovative privacy-preserving framework that reimagines email threat detection through the lens of digital twin technology. In response to the escalating sophistication of phishing, spoofing, and polymorphic malware particularly those augmented by generative AI - TwinGuard offers a decentralised, context-aware solution that models user-specific communication behaviour while safeguarding data confidentiality.
The framework integrates federated learning, secure multi-party computation, and differential privacy to enable collaborative intelligence across distributed environments, maintaining compliance with data protection regulations such as GDPR and UK-GDPR. Its architectural design supports real-time detection through a hybrid BERT–LSTM model embedded within each digital twin, capturing both semantic and temporal features of email interactions. Furthermore, the system’s threat simulation engine enhances adaptability by recalibrating detection thresholds in response to evolving attack vectors, including deepfake impersonation and QR code phishing.
Empirical evaluations using synthetic and real-world datasets confirm TwinGuard’s effectiveness, achieving 98% accuracy, 97% precision, and a false positive rate of just 3%. In particular, these results demonstrate a clear performance advantage over conventional signature-based systems, especially in identifying zero-day exploits and personalised threats. Moreover, TwinGuard’s modular deployment model and compatibility with Trusted Execution Environments make it suitable for enterprise-scale implementation, even in untrusted or resource-constrained settings.
In conclusion, by uniting privacy-preserving AI with digital twin technology, TwinGuard offers a scalable, resilient, and ethically grounded defence mechanism tailored to the demands of modern communication ecosystems. It represents a significant advancement in the design of intelligent cybersecurity systems delivering robust protection without compromising user trust.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original data presented in the study are openly available in Hugging Face at https://huggingface.co/datasets (accessed on 12 October 2025) and Kaggle at https://www.kaggle.com/datasets/naserabdullahalam/phishing-email-dataset (accessed on 12 October 2025).
Conflicts of Interest
The author declares no conflict of interest.
References
- Verizon. Data Breach Investigations Report 2024. Available online: https://www.verizon.com (accessed on 11 October 2025).
- Jabbar, H.; Al-Janabi, S. AI-Driven Phishing Detection: Enhancing Cybersecurity with Reinforcement Learning. J. Cybersecur. Priv. 2025, 5, 26. [Google Scholar] [CrossRef]
- Thakur, K.; Ali, M.L.; Obaidat, M.A.; Kamruzzaman, A. A systematic review on deep learning-based phishing email detection. Electronics 2023, 12, 4545. [Google Scholar] [CrossRef]
- Bonawitz, K.; Eichner, H.; Grieskamp, W.; Huba, D.; Ingerman, A.; Ivanov, V.; Kiddon, C.; Konečný, J.; Mazzocchi, S.; McMahan, H.B.; et al. Towards federated learning at scale: System design. Proc. Mach. Learn. Syst. 2019, 1, 374–388. [Google Scholar]
- Thapa, C.; Tang, J.W.; Abuadbba, A.; Gao, Y.; Camtepe, S.; Nepal, S.; Almashor, M.; Zheng, Y. Evaluation of federated learning in phishing email detection. Sensors 2023, 23, 4346. [Google Scholar] [CrossRef] [PubMed]
- Tao, F.; Zhang, M.; Nee, A.Y.C. Digital Twin Driven Smart Manufacturing; Elsevier: Amsterdam, The Netherlands, 2019. [Google Scholar]
- Lucchese, M.; Salerno, G.; Pugliese, A. A Digital Twin-Based Approach for Detecting Cyber–Physical Attacks in ICS Using Knowledge Discovery. Appl. Sci. 2024, 14, 8665. [Google Scholar] [CrossRef]
- Rathore, M.M.; Mogollón-Gutiérrez, Ó.; Sancho, J.C.; Caro, A. A review of digital twins and their application in cybersecurity based on artificial intelligence. Artif. Intell. Rev. 2024, 57, 201. [Google Scholar] [CrossRef]
- Yang, X.; Yue, C.; Zhang, W.; Liu, Y.; Ooi, B.C.; Chen, J. SecuDB: An in-enclave privacy-preserving and tamper-resistant relational database. Proc. VLDB Endow. 2024, 17, 3906–3919. [Google Scholar] [CrossRef]
- Vialar, L.; Menetrey, J.; Schiavoni, V.; Felber, P. BlindexTEE: A blind index approach towards TEE-supported encrypted DBMS. In Stabilization, Safety, and Security of Distributed Systems; SSS 2024, Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2024; pp. 123–134. [Google Scholar] [CrossRef]
- Wang, Q.; Cui, S.; Zhou, L.; Wu, O.; Zhu, Y.; Russello, G. EnclaveTree: Privacy-preserving data stream training and inference using TEE. In Proceedings of the A.C.M. Asia Conference Computer and Communications Security, Nagasaki, Japan, 30 May–3 June 2022; pp. 1–12. [Google Scholar] [CrossRef]
- Siemens, A.G. Digital Twin Applications in Smart Manufacturing. In Siemens White Paper; Siemens AG: Munich, Germany, 2024. [Google Scholar]
- IBM. Maximo Application Suite: Digital Twins for Asset Performance; IBM Research: New York, NY, USA, 2025. [Google Scholar]
- Tech, U.K. Future Defence Success in the UK Will Depend on Digital Twins. Available online: https://www.techuk.org/resource/future-defence-success-in-the-uk-will-depend-on-digital-twins.html (accessed on 11 October 2025).
- Wisdiam. Boeing Hit by LockBit Ransomware. Available online: https://wisdiam.com/publications/recent-cyber-attacks-manufacturing-industry (accessed on 11 October 2025).
- SOCRadar. Denso Supply Chain Breach. Available online: https://socradar.io/major-cyber-attacks-manufacturing-industry-in-2025 (accessed on 11 October 2025).
- McKinsey & Company. Digital Twins in Supply Chain Optimization; McKinsey Insights: New York, NY, USA, 2025. [Google Scholar]
- Jaber, A.; Al-Khafaji, A.; Al-Sammarraie, A. A comprehensive state-of-the-art review for digital twin: Cybersecurity perspectives and open challenges. In Proceedings of the A.C.M. S.I.G.K.D.D. Conference Knowledge Discovery and Data Mining, Toronto, ON, Canada, 3–7 August 2025. [Google Scholar] [CrossRef]
- Shenoy, D.; Bhat, R.; Krishna Prakasha, K. Exploring privacy mechanisms and metrics in federated learning. Artif. Intell. Rev. 2025, 58, 223. [Google Scholar] [CrossRef]
- Shalabi, E.; Khedr, W.; Rushdy, E.; Salah, A. A comparative study of privacy-preserving techniques in federated learning: A performance and security analysis. Information 2025, 16, 244. [Google Scholar] [CrossRef]
- Face, H.; Enron and SpamAssassin Email Datasets. Hugging Face. Available online: https://huggingface.co/datasets/LLM-PBE/enron-email (accessed on 11 October 2025).
- Cratchley, E. Email Phishing Dataset. 2023. Kaggle. Available online: https://www.kaggle.com/datasets/ethancratchley/email-phishing-dataset (accessed on 11 October 2025).
- Munshaw, J. How Are Attackers Using QR Codes in Phishing Emails and Lure Documents? Cisco Talos Blog. 2024. Available online: https://blog.talosintelligence.com/how-are-attackers-using-qr-codes-in-phishing-emails-and-lure-documents (accessed on 11 October 2025).
- Vassilev, A.; Oprea, A.; Fordyce, A.; Anderson, H.; Davies, X.; Hamin, M. Adversarial Machine Learning: A Taxonomy and Terminology of Attacks and Mitigations; NIST AI 100-2e2025; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2025. [Google Scholar] [CrossRef]
- Devlin, J.; Chang, M.-W.; Lee, K.; Toutanova, K. BERT: Pre-training of deep bidirectional transformers for language understanding. In Proceedings of the NAACL-HLT, Minneapolis, MN, USA, 2–7 June 2019; Association for Computational Linguistics: Stroudsburg, PA, USA, 2019. [Google Scholar]
- Alshamrani, A.; Myneni, S.; Chowdhary, A.; Huang, D. A survey on advanced persistent threats: Techniques, solutions, challenges, and research opportunities. Comput. Sec. 2018, 76, 327–340. [Google Scholar] [CrossRef]
- Tikkinen-Piri, C.; Rohunen, A.; Markkula, J. EU General Data Protection Regulation: Changes and implications for personal data collecting companies. Comput. Law Secur. Rev. 2018, 34, 134–153. [Google Scholar] [CrossRef]
- Goldman, E. An Introduction to the California Consumer Privacy Act (CCPA). Santa Clara Univ. Leg. Stud. Res. Pap. 2020, 36, 1–34. [Google Scholar] [CrossRef]
- Ma, J.; Saul, L.K.; Savage, S.; Voelker, G.M. Beyond blacklists: Learning to detect malicious web sites from suspicious URLs. In Proceedings of the 15th A.C.M. S.I.G.K.D.D. International Conference on Knowledge Discovery and Data Mining, Paris, France, 28 June–1 July 2009; ACM: New York, NY, USA, 2009; pp. 1245–1254. [Google Scholar] [CrossRef]
- Sahingoz, O.K.; Buber, E.; Demir, O.; Diri, B. Machine learning based phishing detection from URLs. Expert Syst. Appl. 2019, 117, 345–357. [Google Scholar] [CrossRef]
- Bergholz, A.; De Beer, J.; Glahn, S.; Moens, M.-F.; Paaß, G.; Strobel, S. New filtering approaches for phishing email. J. Comput. Sec. 2010, 18, 7–35. [Google Scholar] [CrossRef]
- Face, H. Phishing Email Classification Dataset. Hugging Face. Available online: https://huggingface.co/datasets/zeroshot/phishing_email (accessed on 12 October 2025).
- Abdullahalam, N. Phishing Email Dataset. Kaggle. Available online: https://www.kaggle.com/datasets/naserabdullahalam/phishing-email-dataset (accessed on 12 October 2025).
- Phan, N.; Wu, X.; Dou, D.; Hu, H. Scalable Differential Privacy with Certified Robustness in Adversarial Learning. In Proceedings of the 37th International Conference on Machine Learning (ICML), Virtual, 12–18 July 2020; Volume 119, pp. 7683–7694. [Google Scholar]
- Kinasih, D.P.; Mulyadi, P.P.; Hartono, R.; Meiliana; Lucky, H. Enhancing Phishing Email Detection Using Hybrid Ensemble Learning. In Proceedings of the 2023 International Conference on Computer, Communication, and Electrical Technology (ICECCT), Jakarta, Indonesia, 20–21 November 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Vorobeychik, Y.; Kantarcioglu, M. Adversarial Machine Learning; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- Alshahrani, E.; Alghazzawi, D.; Alotaibi, R.; Rabie, O. Adversarial attacks against supervised machine learning-based network intrusion detection systems. PLoS ONE 2022, 17, e0275971. [Google Scholar] [CrossRef] [PubMed]
- UK Statistics Authority. Ethical Considerations in the Use of Machine Learning for Research and Statistics. 2025; Government Digital Service. Available online: https://www.gov.uk/data-ethics-guidance/ethical-considerations-in-the-use-of-machine-learning-for-research-and-statistics (accessed on 12 October 2025).
- Rodrigues, M.; Lino, R.; Alves, F.; Novais, P. Ethical considerations in artificial intelligence and machine learning. In Advances in Computational Intelligence; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2025; pp. 27–43. [Google Scholar] [CrossRef]
- Information Commissioner’s Office (ICO). Guidance on AI and Data Protection. 2023. UK GDPR Guidance. Available online: https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/artificial-intelligence/guidance-on-ai-and-data-protection (accessed on 12 October 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).