Abstract
High-quality luxury products cater to a specific group of consumers due to their durability and the value attached to them. Counterfeiting luxury products has resulted in economic losses for both the producers and consumers. The market for counterfeit luxury products has continued to grow due to the difficulty in authenticating genuine luxury products. The traditional system of verification largely depends on the expert use of specialized equipment for visually inspecting physical luxury products and their associated certificates. This conventional process of authenticating luxury products is expensive, slow, and not easily accessible to consumers. Hence, there is a need for a digital verification approach for luxury products. Blockchain provides the potential for providing traceable and immutable information about a given luxury product. The focus of this paper is to develop a blockchain decentralized application (DApp) for authenticating luxury products in the class of luxury accessories such as jewelry across their respective lifecycles. To achieve this, qualitative analytics is applied to identify useful features for the digital authentication of luxury products. Blockchain requirement engineering modelling is then applied to explore the use of blockchain technologies to realize the features that guarantee transparency in the ownership and use of luxury products. Furthermore, this paper explores the existing blockchain technologies for realizing and implementing the developed requirements of the authentication DApp for luxury products. The selected blockchain technology stack is applied in prototyping authentication systems for luxury products. The implemented platform is simulated to demonstrate the operations carried out in authenticating luxury products.
1. Introduction
High-quality luxury products cater for a specific group of consumers [1,2]. The former is characterized by the quality of materials used in their production and their respective lifecycles that may span several years, hence, allowing them to be reused and resold [3,4]. The market for fake and counterfeited luxury products is highly lucrative. The counterfeit market negatively impacts the purchase and resale of new and pre-owned luxury products due to poor quality materials employed during their production, rendering them less durable [5]. Experts estimate that up to 9% of global production is counterfeited, and according to the OECD report, about 7% of total imports into the European Union constitutes of counterfeited and pirated products [5,6]. The conventional system for verifying luxury product authenticity has failed to put to an end the problem of counterfeit luxury products. This is due to the current system relying on manual, expensive, and inefficient authentication verification processes for these types of products. The most common approach for verifying luxury product authenticity is thus making purchases through approved retailers of specific luxury brands. Verification experts in approved retailers use specialized equipment for authenticating pre-owned luxury products [7]. Due to the complexity of authenticity verification in luxury products, and the high number of counterfeited products in circulation, consumers are likely to purchase fake products during trade-ins and the purchase of pre-owned items [5].
The purchase and use of counterfeited products raises economic concerns for both the producers and consumers of luxury products [8]. The authors in [9], propose a novel framework to address the counterfeiting problem in luxury accessories. The framework employs deep learning neural networks to distinguish authentic luxury accessories from fake items. As a result of the complex nature of the supply chain of luxury products, [10] identifies blockchain as a potential technology for achieving traceability and transparency in the sector of luxury goods. There is also an urgent need to open the supply chain to both regulators and consumers to ensure independent authenticity verification for products [11,12]. Blockchain provides the possibility of enabling traceability and transparency in the supply chains of luxury products, thereby, enabling automated verification of luxury products. Blockchain is a peer-to-peer network where participants use a consensus mechanism to add new records to their network. The data stored on a blockchain is replicated and stored across the nodes of the network participants [13]. Blockchain provides the potential for transparent and digitized verification of the authenticity and history of luxury products. The verification potential of blockchain is due to its foundational technologies such as decentralized timestamped data storage, distributed consensus, and digital signatures [13,14]. Distributed consensus ensures that information stored on a blockchain is correct. Decentralized storage ensures that product information stored is readily available to all relevant parties. Time-stamping and digital signatures ensure the historical ownership of a product can be transparently verified. Thus, with the introduction of blockchain in the logistic processes of luxury products, the authenticity of both new and pre-owned luxury products can easily be verified autonomously.
Notwithstanding the opportunities provided by blockchain in mitigating the counterfeiting problems in luxury products, a well-aligned blockchain-based solution is absent for authenticating luxury products. Recent research [15,16], respectively, shows the conceptual design of a blockchain counterfeit prevention system for products in supply chains and the implementation of an anti-forgery system for tracking data connected to a luxury product. Still, these designs and solutions do not cover the entire lifecycle of luxury products for the consumers such as product purchase, ownership, and transfer of ownership to another consumer through product resale. The article [17], describes a mathematical model for a secure transfer of product ownership in supply chains using digital signatures. Still, the article does not consider additional meta-information changes that occur during the lifecycle of a product. Furthermore, the models developed in [17] for representing products in supply chains are not in the specific business domain of luxury products. The main research gap addressed in this paper is that existing research works that apply blockchain in authenticating luxury products do not cover the entire lifecycle of luxury product ownership. This gap is further expanded in Section 2.1 of this paper. The focus of the current paper is to apply qualitative analytics (based on the results from expert interviews) to understand the authentication problems of luxury products, and then, apply a blockchain requirement engineering method in developing and implementing a proof-of-concept blockchain-based authentication system for luxury products. Thus, the main research question of this paper is how to develop a blockchain platform for digitized authenticity verification of luxury products covering the ownership lifecycle of luxury products. For the separation of concerns, the following questions are derived, which will guide the presentation of results from this work.
- What are the important features of designing a digitized verification system for the authenticity verification of luxury accessories?
- What is the model representation for outlining the requirements of important features of blockchain applications for the verification of luxury accessories across their lifecycle?
- What are the architecture and relevant blockchain technologies for prototyping the requirements in the model representation of the proposed platform?
The rest of the paper is structured as follows. Section 2 provides the theoretical background of materials and methods adopted for the research works carried out in this paper. The first part of the theoretical background presents the foundational blockchain technologies and the second part shows the research method used in addressing the research questions. Section 3 provides the main results of this paper by answering the research questions. In Section 3.1, the first research question is answered by applying qualitative analytics methods used to identify the problems of luxury product authentication. These problems are used to derive the initial features of the LogisticsBDT platform proposed in this paper. In Section 3.2, the second research question is answered by applying the blockchain-based requirement engineering methodology in deriving the requirements of the proposed platform. In Section 3.3, the third research question is answered by outlining the architecture of the designed application and using peer debriefing to identify existing decentralized technologies for implementing the developed architecture. Section 4 provides the evaluation of the implemented platform by providing simulations of operations in luxury product authentication and discussions on the implication of the simulation results. Lastly, Section 5 provides conclusions, limitations, and future work for this research.
2. Materials and Methods
This section shows the foundational blockchain technologies and the research method used in answering the research questions generated in this work and the running case for this paper. In Section 2.1, we provide a literature review of related articles that apply blockchain technology in product authentications. In Section 2.2, we give an overview of the main elements of blockchain protocol technologies. Section 2.3 explains the research methodology adopted for this paper. Section 2.4 presents the running case on which we demonstrate the feasibility of the research results.
2.1. Related Literature Review
Many articles report about the application of blockchain and related technologies such as NFTs and RFIDs in verifying the authenticity of products to prevent counterfeiting. Recent research works have applied blockchain in the verification of products in food and drug supply chains. The research in [18] provides a conceptual multi-agent architecture for managing products across various stakeholders in a supply chain. The concept uses software agents to specify roles and actions that can be executed by various stakeholders within the supply chain. The article further envisions that managing supply chains with blockchain will help in achieving a circular economy through traceability and the recycling of products. Still, the technical descriptions of how this can be achieved are lacking. Article [19] provides a track-and-trace solution for drug items in pharmaceutical supply chains using NFTs. The paper provides an architectural representation and prototype implementation of the solution. Using NFTs, digital representations of products are minted by manufacturers and transferred through intermediaries such as retailers and hospitals. The NFTs are destroyed when drugs are consumed by the customers. Article [20] presents another blockchain-based solution for drug traceability. The article outlines the architecture, algorithms and prototype implementation of a drug for an end to end-product tracking as drugs move across various stakeholders in the healthcare supply chain. Article [21] employs RFIDs and blockchain for enabling traceability in wine industries and to prevent counterfeiting. The system gathers all activities associated with wine production as transactions on a blockchain. Some of the entities that have their activities captured as transactions and stored on a blockchain include growers, producers, distributors, and retailers. An RFID tag on the wine bottle directly maps with the on-chain transaction published by the wine producer, thereby, the authenticity of the wine is verified. Article [17] provides a mathematical model for verifying ownership of products in supply chains and transferring such ownership using digital signatures.
Unlike the products in the supply chains which are mostly one-time-use products, the lifecycle of luxury products is different. This is due to their long lifespan and resale values; hence, they require a different design of blockchain authentication. This is necessary to capture the customer’s (consumer) ownership of luxury products and historical changes that occur during the lifecycle of a luxury product. Article [15] proposed a conceptual framework for preventing the counterfeiting of luxury products with blockchain using the public key and digital signatures to identify the luxury brand and other stakeholders associated with a given product. The conceptual model is proposed for a consortium blockchain where stakeholders are pre-registered with their public keys by a centralized certificate authority. Article [16] shows the implementation of a blockchain solution for the traceability of luxury products similar to [15]. The implemented approach allows luxury brands and other stakeholders to pre-register their digital identities on a consortium blockchain and append their signature to data related to a produced luxury product.
The solutions proposed and implemented in the articles above do not properly address the authentication requirements of luxury products using blockchain. The articles applied a single-signature approach to ownership and transfer of ownership of products. A multi-signature approach capturing the keys of the last owner and the current owner demonstrates a proper handshake which is needed when exchanging physical assets. This ensures that both parties agree to the physical (and digital) state of the asset at the point of transfer to the new owner. Furthermore, the blockchain-based authentication provided in the related articles do not cover the entire product lifecycle, especially the customer aspects of luxury product ownership by ensuring that historical ownership and physical changes that occur during the lifecycle are properly captured on the blockchain. In addition, there is also a need for the authenticity verification of luxury brands that that have a digital replica on the blockchain. This ensures that the first digital signature linked to a luxury product truly belongs to the brand the former is associated with. The approach to brand registration presented in the above articles can only work in permissioned networks such as private- and consortium blockchains. The objective of this current paper also involves designing and developing a different authentication approach for luxury products that addresses the gaps in the existing literature.
2.2. Blockchain Protocol Technologies
Blockchain protocols comprise several technologies that enable the development of decentralized applications operating on different blockchain networks [22,23]. The technologies that support the blockchain protocol include decentralized consensus, decentralized storage and time stamping, public key infrastructure and digital signature, smart contracts, and tokenization.
2.2.1. Decentralized Consensus
This is the mechanism of agreement between the participants of a blockchain network on how new records are added to the network [13]. Consensus mechanisms can be divided into proof-based systems and voting-based systems. In proof-based systems, a participant is selected to update the next record based on the performance of a specified proof. In proof of work (PoW), the participant is selected after solving a specified difficult mathematical task, while in proof of stake (PoS), a participant is randomly selected and the probability of selection depends on their overall stake in the network [13]. In voting-based systems, the consensus in validating the next record added to the network is achieved by a majority vote. Most voting-based consensus mechanisms are derived from byzantine fault-tolerant systems (BFTS) [13]. Proof-based consensus is commonly used in public blockchains where permission is not required to join the network, while voting-based consensus systems are largely used in private/permissioned networks.
2.2.2. Decentralized Storage and Time Stamping
Information stored on a blockchain network is replicated across all the participating nodes such that there is no single point of failure [14]. This system of data storage ensures a blockchain network has no single point of failure. The records contained in a blockchain network are organized in blocks with timestamps showing when the block was created. Each block is cryptographically linked to the respective preceding block, ensuring no modification can be recorded [13].
2.2.3. Public Key (PK) Infrastructure and Digital Signature
This system provides a unique and secure way of identification in the blockchain network. Two key pairs consisting of public- and private keys are generated for each user. The public key is generally for identification while the private key provides the possibility of signing a transaction (and decrypting data) [14]. This implies that all information stored on a blockchain can be traced to a specific account (public key) that executed a transaction resulting in such information.
2.2.4. Smart Contracts and Tokenization
The software programs that run on a blockchain are referred to as smart contracts and are an essential part of decentralized applications that execute different functions on a blockchain [14]. Thus, business logic and operations can be encoded as smart contracts that are then executed without reliance on a central authority. Furthermore, assets can be created and stored on a blockchain as tokens. With smart contracts, specific blockchain-relevant conditions are outlined on a blockchain for exchanging assets between network participants. Smart-contract enabled tokens provide utility for executing transactions on a blockchain. Additionally, a new token type, referred to as the non-fungible tokens (NFTs), provide a unique representation of digital (and physical) assets on the blockchain [24].
2.3. Research Method—Design Science Research
This paper adopts the Design Science Research (DSR) method for addressing the formulated research questions. DSR provides a rigorous framework for creating and evaluating new software artefacts represented as models and prototypes [25]. The DSR framework contains three main pillars. Namely, environment, information system research and knowledge base. The environment pillar outlines the application domain of this research. The business domain considered in this research is the luxury domain and the focus is on using blockchain to verify the authenticity of luxury products. The knowledge base provides the scientific foundations for this research. We apply qualitative analytics (QA) to understand the current authentication process of luxury products and identify problems that exist in them. We apply the trustable DApp modelling (T-DM) approach to specify the requirements and architecture of the proposed blockchain platform for authenticating luxury products. We further apply Peer debriefing (PD) for validating the chosen technology stacks for implementing the proposed platform. Lastly, the middle pillar of the DSR shows the assessment of the developed software artefact. We apply use-case simulations of various operations in the proposed authentication platform to evaluate the developed prototype.
Figure 1 shows the instantiation of the DSR methodology for this research. The details about this problem domain and classes of luxury products considered in this research are captured in the running case presentation in Section 2.3. The detailed explanations of the methodologies such as QA, T-DM, and PD applied in this research are explained in Section 2.2.1, Section 2.2.2 and Section 2.2.3, respectively. The main results of this work are presented in Section 3. The simulations used to evaluate the operations of developed prototype software is presented in Section 4.
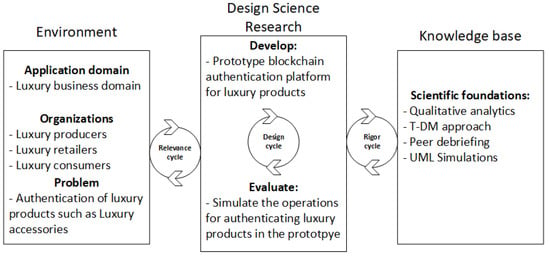
Figure 1.
Instantiation of design science research method, adapted from [25].
2.3.1. Qualitative Analytics
Qualitative data analytics involves extracting important facts and key topics such that the information content of a given dataset is dimensionalized into its core themes [26]. Eight experts from the luxury industry comprising producers and sellers of luxury products are interviewed on two topical categories: (i) awareness of luxury product authentication methods and (ii) problems associated with luxury product authentication methods. A detailed description of the case-study research used in generating the interview questions and results is presented in the previous work [27]. First, we apply thematic analyses/reduction techniques on the textual data generated from the expert interviews to the authentication process for new and pre-owned luxury products. Later, problems associated with each class of luxury product authentication are identified and mapped. The presented qualitative analytics approach is used to answer the first research question RQ1.
2.3.2. Blockchain Technologies and T-DM Methodology
The T-DM methodology provides a framework for designing and building blockchain applications [28,29]. The approach outlines a systematic approach for building blockchain DApp by providing the technique for modelling the initial requirements, static architecture and dynamic behavior of the developed application. The T-DM approach is adapted from agent-oriented modelling [30,31]. The objective is to apply the T-DM technique in digitizing and transforming the conventional technique for luxury product authentication and apply foundational blockchain technologies such as tokenization, e.g., NFTs, digital signatures, time-stamping, and decentralized storage to address the problems of luxury product authentication. The requirement diagram of the T-DM modelling framework provides the methodology for identifying the functional requirements, software properties, and stakeholders in a blockchain-based software system using agent-oriented modelling techniques. The functional requirements outline the main functions and sub-functions that can be executed in the proposed application. The software requirement identifies the software properties that outline how a given functional requirement is executed. The stakeholders include the human users and software agents that execute the listed functions in the designed application. Furthermore, the static architecture of the designed application is derived by heuristic mapping of the main requirements outlining the main component, subcomponents, and interfaces in the designed application. The dynamic behavior of the designed application is represented by sequential activities that result in a status change of information stored on the blockchain. The presented blockchain application requirement modelling approach is used to answer the second research question RQ2.
2.3.3. Peer Debriefing Mapping of Requirements to Blockchain Technologies
Peer debriefing (PD) provides a methodology for reviewing, assessing, and validating the results of research by using unbiased and experienced peers/colleagues in a particular field [32]. Hence, to assess and map existing blockchain technologies to the requirements of the designed application, first, we identify and describe the potential blockchain Layer 1 technologies to realize the different requirements depicted in the architecture model of the designed application. Later, PD is used to assess the suitability of listed blockchain Layer 1 technologies for each requirement and rank them accordingly. The presented PD validation approach, in combination with the static architecture of a designed blockchain application, is used to answer the third research question RQ3.
2.4. Running Case
In a previous study, we adopted case-study research in analyzing the problems in luxury product authentication by comparing the consumers’ and experts’ points of view [27]. Eight experts from the luxury products domain comprising producers and approved sellers of luxury products were interviewed to understand their current awareness of corresponding authentication systems, associated problems and their opinions concerning blockchain-based features for problem mitigation. The same set of questions was presented to non-experts comprising 248 owners of luxury products using a quantitative survey. The case study focused on luxury accessories as a group of luxury products that are highly impacted by counterfeiting [27]. The current research extends the previous work by using the qualitative results from the conducted expert interviews to model the current process (AS-IS process) of luxury product authentication. Hence, we present the associated problems with the conventional authentication process. Furthermore, the findings from expert interviews on blockchain-based features that can address limitations in the traditional authentication systems are used in T-DM designing a proposed authentication system for luxury products designed and implemented in this paper.
The business domain of luxury products varies with several types and groups of products. For this research, the class of luxury products considered for authentication using blockchain are luxury accessories (e.g., jewelry, watches, etc.) This type of luxury product represents one of the most counterfeited. According to the recent OECD report (OECD report on Trade in Fake Products: https://www.oecd.org/newsroom/trade-in-fake-goods-is-now-33-of-world-trade-and-rising.htm (accessed on 22 December 2022)), accessories such as watches and jewelry account for 9% of the global counterfeit market. The proposed luxury product authentication platform developed in this paper addresses business needs between producers of luxury accessories and retailers for provenance documentation of information about a given luxury product. There exists also a relationship between the luxury product retailers and the consumers, such that the proposed platform provides an instant verification of product authenticity. The last relationship addressed is between consumers and consumers for instant verification of pre-owned luxury products. Hence, the business cases represented by the designed platform are business-to-business, business-to-consumer, and consumer-to-consumer (B2B2C2C).
3. Results
This section presents the results that address the three research questions providing the guidelines for this paper. Section 3.1 discusses the conventional authentication approaches for luxury products and the problems associated with them. Section 3.2 presents a proposed model for defining the requirements of blockchain-based luxury product authentication. Finally, Section 3.3 shows the architectural descriptions and implementation of the platform for authenticating luxury products in the class of luxury accessories.
3.1. Luxury Products Authentication and Associated Problems
This part of the paper presents the qualitative analytics results for understanding the conventional authentication approaches for luxury products, such as accessories and the problems associated with them. Table 1 shows the thematic results from eight experts that work in the luxury products domain, identifying conventional methods for authenticating luxury products, underlying problems, and features that can be introduced to address the identified authentication problems. A total of 11 questions are presented in Table 1. The first column shows the question ID, the second column shows the question, and the third column shows the three most repeated themes by the experts when answering the questions. The themes are ordered according to the frequency of their repetitions from 1 to 3. For the remainder, Section 3.1.1 shows the AS-IS state of the luxury product authentication process derived by analyzing the data from industry experts. Section 3.1.2 shows problems derived from examining the AS-IS process and proposes blockchain features for the authentication of luxury accessories.

Table 1.
Thematic analysis results from the expert interviews on luxury product authentication and problems, adapted from [27].
3.1.1. Derived Process of Luxury Product Authentication
Figure 1 shows a business process modelling notation (BPMN) process representing the current authentication process of both new and resold luxury items. The thematic results generated from the answers provided by experts to questions 1–5 comprised the main inputs for modelling the AS-IS process. Two BPMN process lanes are specified in the diagram, the first when purchase/authentication happens in-store and when the purchase/authentication happens between customers.
To purchase a luxury product, the customer (buyer) first chooses a brand and then decides whether to purchase a new product of a particular brand or a pre-owned product. If it is a new product, the customer finds an approved retailer of the brand, chooses a specific product, and pays. In this instance, no verification is performed since product authenticity is derived by purchasing from the approved seller brand. Still, if the purchaser decides to buy a used luxury product, then the purchaser finds a seller who is willing to sell the already used product. Then, again the buyer decides if he wants an expert to verify the authenticity of the used item or independently perform the verification. If the buyer decides to use expert verification, the buyer also must find brand-specific experts. These verification experts are usually located within the approved retailer of the brand due to the specialized equipment used in performing the product verifications. The expert visually inspects (using specialized equipment) the product as well as the brand-certified purchase certificates that come along with the product when originally purchased. Once the visual inspection is completed, the authenticity is confirmed, and the buyer can pay the seller. Still, if the buyer decides to perform independent verification, the purchaser performs a visual inspection of the product (usually without any specialized equipment), confirms the authenticity, and pays.
3.1.2. Problems in Luxury Product Authentications
The problems that affect the AS-IS method of luxury product authentication are captured by the thematic results from the answers to expert interviews on Questions 7 and 8. Furthermore, additional problems are derived (by the authors of this paper) from the generated conventional methods of luxury product authentication specified in Figure 2.
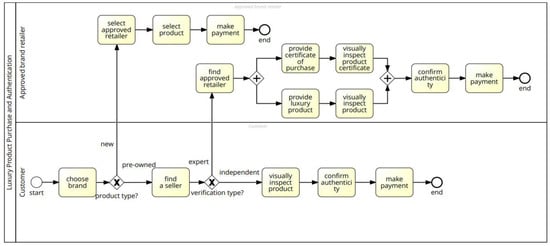
Figure 2.
The current process of luxury product purchase/authentication.
- (a)
- Experts identified problems with luxury product authentications
The findings from the expert interview identified two themes for authentication problems in luxury products. The first is traceability and document verification problems and the second is the effort and difficulty of the verification tasks. The traceability problem arises from the complex network of the supply chain in the production of luxury items. It is difficult to transparently trace the final production of a luxury item. This is because all the necessary information associated to the product during manufacturing is only available to brands that manufacture them. Hence, purchase certificates resulting from a particular luxury item cannot be independently verified due to the lack of transparent historical data for the products. Furthermore, independent verification of product certificates outside of the producing organization cannot be trusted since paper certificates can easily be faked.
A high effort is required to perform visual verification of luxury products even with specialized equipment. The verifier needs to undergo rigorous training to use the specialized equipment and also needs to have a strong understanding of the manufacturing process and specific materials used by certain brands to correctly distinguish counterfeit from authentic ones.
- (b)
- Factors that cause problems in luxury product authentication
The findings from expert interviews identified three themes of factors causing authentication problems. These factors include (i) lack of knowledge and complexity of implementation (of verification process), (ii) too expensive and (iii) authenticity cannot be guaranteed. Lack of knowledge is an important factor because of the amount of information required in understanding the production of a specific brand of luxury products. Since the production process and materials are specific to each brand, a verifier needs to have all this information at their disposal. Furthermore, implementing a verification process for luxury products is a difficult task that requires the full collaboration of organizations that produce these luxury products.
Considering the amount of knowledge and specialized equipment needed in setting up the verification process of luxury products, costs are an important factor that has caused problems for the conventional verification methods of luxury products. These verification costs are generally passed down to the customers, especially to buyers of pre-owned products. Thus, the customers will resort to independently verifying their purchased products irrespective of their limited knowledge in this domain. With the current authentication methods, regardless of who performs the verification, the authenticity of luxury products cannot be guaranteed on purchase. Since the verification process is manual, requiring a lot of specialized knowledge in brand production materials and custom equipment, the chances of false negatives and false positives occurring in the verification results are still high.
- (c) Additional derived problems from the AS-IS process of luxury authentication
In the depiction of the current authentication of luxury products, additional problems that are not pointed out by the experts can be identified. Since the verification of luxury goods performed by experts depends on the location of the approved retailers, the problem of accessibility of genuine luxury products becomes more evident, especially for customers in developing countries. In this regard, the physical location of approved retailers of different luxury brands is limited. Hence, customers are only able to authenticate luxury products using experts if they reside within the locations covered by the approved retailers. Alternatively, customers may only rely on purchasing new luxury products from the online platforms provided by different luxury brands. Due to this problem, counterfeit luxury products are most prevalent in developing economies where very few approved luxury retail brands are located [33].
- (d) Blockchain-based solution for luxury product authentication
The findings from the expert interviews show that three blockchain features can be applied to improve the current luxury product authentication process. The experts identify product ownership history verification as the most important feature that can be implemented using blockchain. The other two equally ranked features include product ownership transfer and product identification. The feature that the experts considered unimportant is the purchase of luxury products with cryptocurrency. Furthermore, the experts identify QR codes as a technology for the digital representation of luxury products. The experts also identify decentralized blockchain databases for ensuring interoperable access to digital information connected to different luxury products. Addressing these findings, the proposed blockchain application, designed to address the stated luxury product authentication problems, is referred to as the Logistics Blockchain Digital Twin (LogisticsBDT).
3.2. Model Requirements of the LogisticsBDT Application
The model requirements of the designed application, described by the T-DM metamodel [34], contain agents, software properties, and functional requirements of a designed blockchain application. In Section 3.2.1, stakeholders and agents that interact with the functions in the proposed LogisticsBDT platform are outlined and described. In Section 3.2.2, the software requirements specifying the non-functional properties of the LogisticsBDT platform are outlined and described. Lastly, in Section 3.2.3 the functional requirements showing the main value propositions, functions, and subfunctions executed by stakeholders and agents in the proposed platform are outlined. The greyed areas show the functions when executed result in a state change of the blockchain.
3.2.1. Stakeholders and Agents
The stakeholders represent human users that execute different functions in the designed application while the agents represent automated software that interacts with the application. The following classes of stakeholders are identified in the LogisticsBDT application producer, buyer, and seller. The producers are luxury brands that manufacture luxury products. The buyers represent the retailers that purchase luxury products from manufacturers or customers that purchase luxury products from retailers and fellow customers. Sellers can also represent the luxury brand that sells the product to retailers or retailers that sell the products to consumers, or consumers that sell the preowned products to fellow consumers.
The software agent identified for the proposed application is a verifier agent that performs automated checks on the data externally returned to the blockchain system. Figure 3 shows the stakeholders and software agents in the LogisticsBDT platform and the associated functions that they can execute.
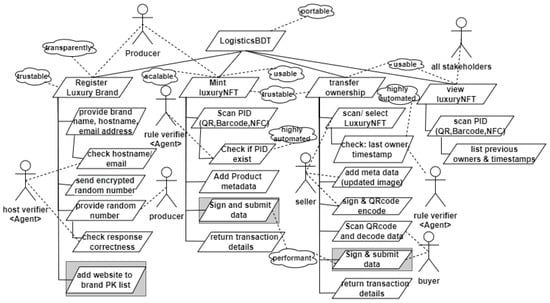
Figure 3.
Requirement model of LogisticsBDT.
3.2.2. Software Properties of the Designed Platform
The software properties of a designed DApp, also called non-functional requirements, describe how a particular function is executed in the designed DApp. The following are identified as relevant software properties of the functions in the LogisticsBDT, and they include portable, usable, scalable, transparent, trustable, and highly automated [29]. Portability implies that a particular function can be executed in different classes of devices such as mobiles and desktops. Usable implies that an executed user function is easily understandable. Scalable implies that the function can be executed by an increasing number of users without resulting in the unsuccessful completion of the function. Transparent implies that the output from the function execution is visible to the users of the application. Trustable implies that the encoded rules/conditions that determine the execution of a function and the result from such an execution are clear to the users. Lastly, highly automated implies that a function is automatically executed by a software agent.
3.2.3. Functional Requirements of the Proposed Platform
The main functional requirements of the LogisticsBDT application that describes the value propositions in authenticating and verifying luxury products include: register the brand, mint luxury NFT, transfer luxury NFT, and view luxury NFT. These main functions are refined into subfunctions as shown in Figure 3 and further described below. Software properties that describe the non-functional requirement of the system and the agents that execute the system functions are attached to the listed functions following the inheritance rule. The greyed functions represent the functions when executed, and results in a status change of the blockchain.
- (a)
- Register brand function: The platform verifies luxury brands that are allowed to mint luxury NFTs through a challenge and response system. The function provides brand details allows brands to provide their host address and email. With the function send encrypted random number, a random 2-byte token is sent to the address provided by the brand. The function add website to brand PK list links the wallet address of the user to the luxury brand on the condition that the user can provide the correct token sent. Hence, every luxury NFT minted by this user is linked to the brand host website.
- (b)
- Mint luxury NFT function: To mint a luxury NFT, the following functions are executed. The scan PID function allows the scanner to read the QR code (or RFID) information that contains the luxury product identification details (PID). The add metadata function enables the brand to provide information about the product such as name, color, image etc. The user signs the data with their wallet private key and sends it to the blockchain. On successful minting, the user is returned with the transaction details of the blockchain operation.
- (c)
- Transfer ownership function: To transfer the ownership of an existing luxury product to a new owner, the following functions are performed. The scan/select function allows the system to collect the PID information of the product and first checks if the wallet address of the current owner matches the address of the user that initiated the transfer function. The add metadata function allows the current owner of a luxury product to update the metadata (image only), thereby providing a traceable history of physical changes in the product since when it was first minted as a luxury NFT. The data is then signed by the current owner. An automated agent generates a QR code that encodes the sign data. The scan QR code and decode data allow the new owner to decode the information contained in the signed data present in the QR code and then append his/her signature to the initially signed data. This makes a complete handshake, ensuring that two parties agree to complete a transfer operation of any given luxury accessories. The new owner submits the signed data to the blockchain. If the operation is successful, transaction details of the blockchain operation are returned to the new owner.
- (d)
- View luxury NFT function: Viewing the luxury NFT function allows users to see the historic ownership of a luxury product, timestamps, and public keys linked to them. The scan PID function enables the user to locate a PID linked to the product by scanning the product QR code, barcode, or RFID. The list of previous owners, their timestamps, and other related metadata describing the luxury NFT is returned to the user.
3.3. Blockchain Technologies for Implementing the Application Model
To show the blockchain technologies that can be used in implementing the requirement model of the LogisticsBDT, first, we show the static architecture of the developed application and then identify existing blockchain technologies that can be used to realize the described architecture. The latter part of this section shows the prototype implementation of the LogisticsBDT platform and algorithms used in realizing various decision points in the luxury NFT lifecycle. Section 3.3.1 shows the proposed architecture of the platform outlining the components, interfaces, and data exchanged between them. Section 3.3.2 shows the selection of the technology stack for prototyping the developed architecture. Section 3.3.3 shows the formalized algorithms used in realizing various decision points in the luxury NFT lifecycle. Section 3.3.4 shows the sample user interface realized from the prototyped LogsiticsBDT application.
3.3.1. Architecture and Data Model of LogisticsBDT Platform
The static architecture representation of LogisticsBDT is derived by heuristic mapping of the main functions of the application specified in the requirement diagram. The architecture shows the main components, subcomponents, interfaces, and users (or agents) that interact with these components as shown in Figure 4. In addition, the data model that shows the output of interaction with these components is attached to the relevant components and interfaces. The main components of the LogisticsBDT application are brand registration, luxury NFT minting component, luxury NFT transfer component, and the viewer component. The grey part of the sub-components represents components where interactions with them results in exchange of tokens.
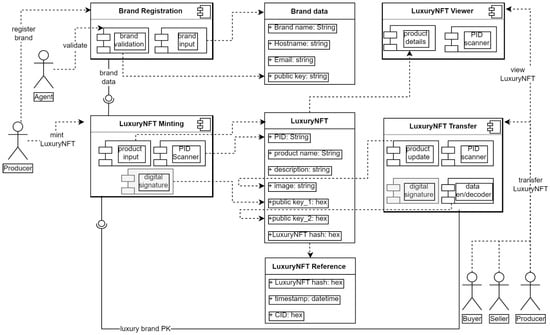
Figure 4.
Architecture and data structure of LogisticsBDT.
- (a)
- Brand registration component: Only a luxury brand represented as a producer and an automated software verification agent can interact with the brand registration component. The producer registers his brand details, while the software agent performs the challenge/response operation. The data generated from the brand registration is centrally stored in our database. In the future, we plan to decentralize the operation of brand registration using blockchain oracles and a configurable challenge–response system implemented in MFSSIA.
- (b)
- Minting component: The minting component of the application allows only verified luxury brands to mint a new luxury NFT. The PID scanner reads the product identification data from the physical product. The product input provides a form for adding metadata and
- (c)
- # an original image. The digital signature component allows the producer to assign a signature on the minted luxury NFT.
- (d)
- Transfer component: The transfer component of the application provides all users access to transferring their luxury NFTs to new owners. The product update component allows the inclusion of the current image of the luxury NFT. The PID scanner provides the reading capability of the product data, and the QR-encoder decoder provides the possibility of generating an intermediate asset that can be signed by the second party who is the new owner. The digital signature provides the signing functionality and the data generated is stored in a decentralized database with the timestamp and hash stored on a blockchain.
- (e)
- Viewer component: The viewer component of the application allows anyone with physical access to a luxury accessory already minted as an NFT to view the history of ownership of the product. The PID scanner reads the identification data, while the product details component presents the luxury NFT information to the user. To get the data, the PID read from the physical product is referenced in the data storage containing the transaction hash of the data on the blockchain. Searching the hash data on a blockchain returns the content identification details of the product metadata. This detailed information is then returned to the user showing the historical timestamps connected to the product.
3.3.2. Assessment of Selected Blockchain Technologies
This part of the paper provides a mapping showing the existing blockchain technologies that can be used to realize the requirements of the designed LogisticsBDT as specified by the components in the static architecture [28,29]. Table 2 shows the component mapping to the existing technologies. Peer debriefing is used to validate the technology mapping. The first column of the table shows the main component, the second column shows the subcomponent, the third column shows the technology used in implementing the architecture, and the last column shows the peer debriefing validation for each mapped component.

Table 2.
Component tech-stack mapping.
- (a)
- Brand registration technology stack: Brand registration is proposed to be implemented using a simple HTML form and a software agent for challenge–response verification. The challenge–response verification provides a checking method for ensuring that a particular user is part of the organization represented by the brand host address. A simple JavaScript is proposed for generating the challenge and verifying the response from the user.
- (b)
- The minting technology stack: In the LogisticsBDT minting implementation, the PID scanner is proposed to first support QR codes and barcodes. Support for RFID-attached products will be added later. Product input for adding the metadata and original image of the product is implemented using a simple HTML form. The digital signature is proposed to be implemented on Polkadot technology (Polkadot scalable, interoperable and secure blockchain technology for web: https://polkadot.network/technology/ (accessed on 22 December 2022).
- (c)
- The transferring technology stack: In LogisticsBDT transfer, the product update is proposed to be implemented using an HTML form for uploading a new image. The multi-signature that simulates a secured handshake between buyer and seller for a digital signature is implemented with the Polkadot blockchain.
- (d)
- The viewer technology stack: For the LogisticsBDT Viewer, the PID scanner works only on QR codes and barcodes. The metadata containing product details of a luxury NFT is displayed as HTML.
- (e)
- On-chain components technology stack: The on-chain properties of the platform are proposed to be implemented on the Robonomics blockchain (Robonomics blockchain for physical internet: https://robonomics.network/ (accessed on 22 December 2022) and the Inter-planetary file system (IPFS) (Inter-planetary file system network: https://ipfs.tech/ (accessed on 22 December 2022)). The IPFS provides decentralized storage for the metadata and images associated with a given luxury NFT. The timestamping shows the historical occurrences of transactions on a given luxury NFT and is also implemented on the Robonomics platform.
- (f)
- Peer debriefing validation of proposed technology stacks: Three peers working in the field of blockchain application development research are presented with the proposed technologies described above for realizing the architecture of the LogisticsBDT application. They provide a ranking to show the suitability of each technology in the realization of a particular component. A simple average score of the results from the peers is used to generate a ranking for the suitability of the listed technologies. The PD scores for the suitability ranking of the technologies for realizing the mapped architecture of the platform are shown in the last column of Table 2.
3.3.3. Prototype Implementation of Luxury Product Authentication Platform
There are over 5000 lines of code used in implementing the LogisticsBDT DApp for luxury product authentication as shown in the Bitbucket repository (LogsiticsBDT project links: Backend: https://bitbucket.org/alexnorta/robonomics/src/master/ (accessed on 22 December 2022) and Frontend: https://bitbucket.org/alexnorta/logistic-bdt-web (accessed on 22 December 2022). We provide the formal pseudocodes of the main algorithms in the implementation of the application. These are shown in Algorithms 1, 2 and 3 below.
- (a)
- Brand verification algorithm challenge–response algorithm
The purpose of this algorithm is to provide a verification system for assigning public keys to specific brand names (and host websites) using a 16-bit challenge of randomly generated tokens sent to the email address of the brand that matches the host website. Algorithm 1 shows the formalization of the algorithm for brand registration. The first part of the algorithm shows the initialization of the variables. The algorithm begins by generating a random token (T) and sending the token to the email address provided by the user (Ez). If the root domain I of the email address and brand host address (Hz) provided by the user matches and the token returned by the user (Tz) matches with the randomly generated token, the user public key (Pz) and host URL (Hz) are added as a key–value pair in a set of the verified luxury brand list and stored on-chain. Otherwise, the brand list remains the same.
| Algorithm 1: Brand registration |
| Initialize variables: x = ∅; x is a set of verified luxury brands, initialized as empty H = f(s,r); H is host url function of subdomain(s) and root-domain(r) E = f(u,r); E is an email function of username(u) and root-domain(r) Pk = user Public key z = the user input for each user T = 16-bit Token Begin algorithm: T = randomToken(16 bit) send(T,Ez) IF: (Ezf(r) == Hzf(r)) ∧ (Tz == T) → x = x ∪ {(Pkz,Hz)} → Store(x) ESLE: x = x |
- (b)
- Luxury NFT minting algorithm
The purpose of the minting algorithm is to ensure that only registered brands can mint luxury NFTs and that the host address of the brand is listed in the luxury NFT metadata. The algorithm also checks if a luxury NFT (represented by the PID attached to the physical product) has already been minted before. Algorithm 2 shows the formalization of the NFT minting. The first part of the algorithm is the initialization of variables. A luxury NFT contains the product ID (PID) and metadata associated with the product. The variable y contains all minted luxury NFTs. The variables x, PK and H are from Algorithm 1. Lastly, z represents the user input for this algorithm.
The algorithm begins by reading the PID from the user input provided. The algorithm first checks if there is any NFT associated with the PID from the NFT list (y). If there exists an NFT with the PID, the user is returned the PID and metadata (m) associated with the product. Otherwise, a hash function is applied on the PID, the user adds the metadata of the luxury product and signs the NFT with their public key (Pk). If the public key used in signing the data is contained as a key value in the verified brand list (x), the hostname of the luxury brand and the public key of the user are added to the NFT metadata and stored on-chain.
| Algorithm 2: Minting Luxury NFT |
| Initialize variables: NFT = hash(PID) + M PID = Product ID of luxury product (in RFID, barcode or qrcode) M = Meta data of luxury product y = {(PID1 + M1), (PID2 + M2),..,(PIDn + Mn)}; y is a set of minted luxury NFTs x = {(Pk1,H1), (Pk2,H2),…(Pkn,Hn)}; x is a set of verified luxury brands Pk = user Public key H = Brand hostname z = the user input for each user Begin algorithm: Read(PIDz) IF: PIDz ∈ y → Return: PIDz + Mz ESLE: ¬ NFTz = hash(PIDz) + Mz Sign(NFTz, Pkz) IF: Pkz ∈ y → Mz = Mz + (Hz + Pkz) → Store(PIDz + Mz) Return: NFTz ELSE: ‘fail’ |
- (c)
- Luxury NFT transfer algorithm
The purpose of the transfer algorithm is to validate the signatures of the user that initiates the transfer of the user that is receiving the luxury NFT. The algorithm also checks that the user that initiates the transfer is the last owner of the NFT. Algorithm 3 shows the pseudocode for transferring a luxury NFT. The first part shows the initialization of the variables. Any transaction on a given NFT is denoted by T_N and each transaction is signed by a user public key PK. The data generated by signing an NFT transfer transaction is denoted by D. The user that initiates the transfer transaction and the user that receives the NFT are denoted by z1 and z2, respectively. Each transaction (minting and transfer transactions) is signed with a public key Pk. Only the last person that signed a transaction on an NFT can initiate the transfer transaction and Pk connected to the last transaction represents the current owner of the NFT.
The algorithm begins with the user z1 initiating a transfer action on an NFTi and the total transactions on the NFTi are represented as ΣT_Ni. The last transaction on NFTi is denoted as T_Nn and decoded to identify the public key Pkn that signed it. If the public key that signed the last transaction is the same as the public key of the user that initiated the transfer transaction Pkz1, the user is requested to sign a transfer transaction and send the signed data (Dz1) to the receiving user. The receiving user decodes the signed data and the algorithm checks if the public key Pkz1 that signed Dz1 is the same as the last public key in the transaction list of NFTi. If this condition is true, the algorithm triggers user Pkz2 to sign the transfer data Dz1 to generate Dz2. The completed transfer transaction data Dz2 is added to the list of transactions on NFTi which is ΣT_Ni and stored on-chain.
| Algorithm 3: Transferring Luxury NFT |
| Initialize variables: T_N = transaction on an NFT ΣT_N = the total transactions on an NFT T_N = Sign(NFT, Pk); transaction on NFT is signed by a user public key D = signed transfer data z1 = the user that initiates the transfer z2 = the user that receives the NFT i = a sample of an NFT Begin algorithm: Transferz1(NFTi) ΣT_Ni = count{Sign(NFT1,Pk1), Sign(NFT2,Pk2),…, Sign(NFTn,Pkn)} ΣT_N = count(T_N1, T_N2,…,T_Nn} Decode(T_Nn) IF: PKz1 == PKn → Dz1 = signTransfer(NFTi, PKz1) → Send(Dz1) → Receive(Dz1) → Decode(Dz1) IF: PKz1 ∈ Dz1 == PKn ∈ ΣT_N → Dz2 = signTransfer(Dz1) → ΣT_Ni = Dz2 ∪ count{T_N1, T_N2,… T_Nn} → Store(ΣT_Ni) ELSE: ‘fail’ ELSE: ‘fail’ |
3.3.4. User Interfaces of the LogisticsBDT DApp
Figure 5 displays sample user interfaces of the implemented application. At the top left of the figure is the first screen of the application that allows a user to register as a luxury brand, mint a luxury NFT, transfer a luxury NFT, and view the history of a luxury NFT. At the bottom left of the figure is a screenshot showing the result of a searched luxury NFT using the QR code attached to the product. The sample result shows that the luxury NFT already has three history transactions associated with it.
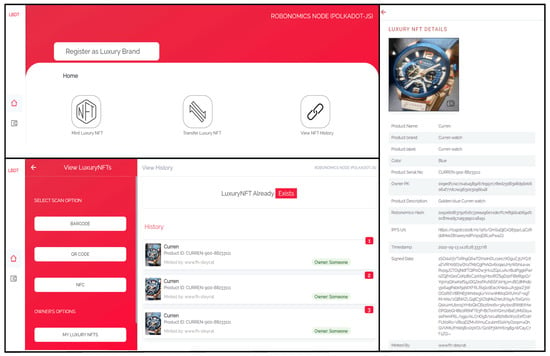
Figure 5.
App home interface, the ownership history of a luxury NFT and metadata.
The first is a minting transaction, and the other two are luxury NFT transfer operations. At the right of the figure is an expanded detail of the luxury NFT showing the metadata such as the product picture, color, brand name, etc. The blockchain-related information such as transaction hash, timestamp, and the IPFS URL. Furthermore, the signature of the transaction is also represented, such that when decoded will return the same information present in the metadata. Lastly, the minted by shows the host address of the brand organization that mints the luxury NFT.
4. Evaluation and Discussions
This section presents the evaluation of the implemented LogisticsBDT platform by simulating the user operations in authenticating luxury products. Furthermore, the results of the simulations are discussed, as well as the implications of the results of this research.
4.1. Simulation and Evaluation of the Luxury Product Authentication Platform
This section shows the experimental setup and the results of the simulation for evaluating the LogisticsBDT platform as well as the simulated operations. Section 4.1.1 presents the experiment set-up outlining the purpose of the simulation and itemized requirements for the simulation. Section 4.1.2 shows the simulated user operations and their results outlining the activities that yield a state change of the blockchain.
4.1.1. Simulation Objective and Experiment Set-Up
The purpose of the simulation is to understand the tasks needed to be completed and the estimated time resources needed to complete luxury product authentication using the developed luxury product authentication platform. The simulation, thereby, represents the To-Be state of the process represented in Figure 2.
To set up the simulation experiment, the following items are required, including sample luxury products, encoded QR code of luxury products PID and a luxury producer brand. In this experiment, sample luxury products are represented by image files of a luxury product saved in a computing device. The PID of the luxury product is manually generated using a QR code encoder tool from the internet. The sample brand producer is represented by the organization of the first author of this publication. Additionally, a mobile (safari) browser with a Polkadot key imported, represents the Luxury producer, while a second mobile (chrome) browser with a second Polkadot imported key represents the buyer.
4.1.2. Simulation Results
The results of the simulation experiment of the operations in the LogisticsBDT platform are presented as follows. The simulation results are presented using the UML sequence diagram. The red numbered items in the sequence diagram figures show the transactions that results in status change of the blockchain.
Brand registration and minting luxury NFT: Figure 6 shows the sequential activities and components required for registering the luxury brand in the LogisticsBDT luxury product authentication platform and minting a luxury NFT. First, the luxury producer provides the brand details, such as brand name, host website, and email. The brand registration component checks if the email address matches the hostname, then generates a random token and sends it to the email address. If the luxury producer provides the correct token string, the public key of the luxury producer is linked to the brand data and stored on-chain. The red-numbered transaction 1 denotes the first on-chain transaction that results in the status change of the blockchain. Hence, the transaction of linking the public key with brand data results in the state of the blockchain in the brand registration operation.
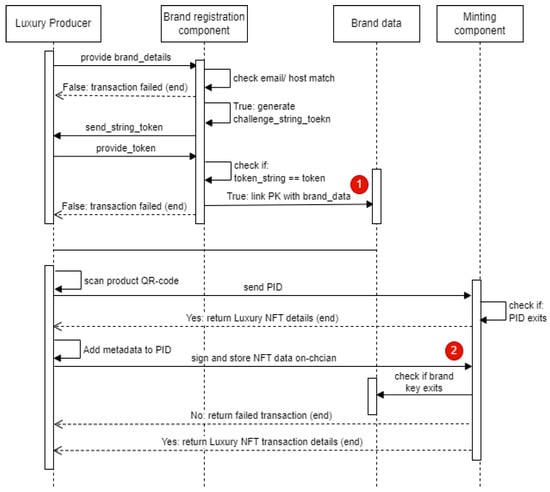
Figure 6.
Brand registration and NFT minting sequence.
To mint a luxury NFT, the luxury producer scans the QR code of a physical product to read the PID. The PID is sent to the minting component. The component verifies if an NFT already exists with the same PID. Otherwise, the luxury producer updates the PID with metadata outlining the name, description and pictural representation of the product. The data is signed and sent to the minting component. The minting component again checks if the PK of the signed minting transaction is linked to any brand data. The transaction details are returned to the luxury producer, or else the transaction fails. The red-numbered transaction 2 denotes the second on-chain transaction showing that the transaction of storing minted NFT on-chain results in the state change of the blockchain.
The brand registration requires the luxury brand to fill in a form containing three fields and to provide the correct token sent to their email. The current implementation of the LogisticsBDT stores brand data locally on the platform’s database. The luxury NFT minting requires the luxury producer to fill in a form providing the luxury NFT metadata and to take a picture representation of the physical product. Based on the recorded simulation video (LogisticsBDT NFT minting operation simulation: https://www.youtube.com/watch?v=QEWRunRNRrI (accessed on 22 December 2022) of this operation, it takes about 3 min to import registered brand account keys and mint a luxury NFT.
Viewing and Transferring a Luxury NFT: Figure 7 shows the sequential activities and components required for viewing and transferring a luxury NFT. To view a luxury NFT, the user scans the QR code associated with a product and the luxury NFT viewer component returns the NFT meta details associated with the product, if it exists. Another alternative is to read the NFTs data linked with a particular Pk from the reference data table. The second is presented in the viewing part of this simulation. A luxury producer views the NFTs connected with their PK, and the list of NFTs connected to the account is returned to the producer.
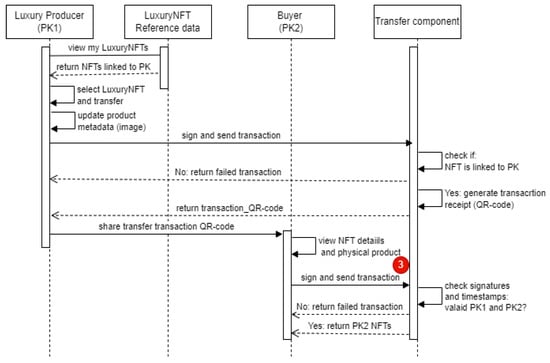
Figure 7.
Luxury NFT viewing and transfer sequence.
To transfer a luxury NFT, the producer selects an NFT from the list of returned NFTs and updates the NFT metadata by providing the current picture representation of the physical product. The updated information is signed and sent to the transfer component that checks based on the on-chain data if the Pk linked to the NFT belongs to the luxury producer, then generates a transaction receipt (embedded in a QR code) if the check is successful. The luxury producer shares the signed transaction receipt with a buyer. The buyer scans the transfer QR code and decodes the NFT information and the signature contained in the transfer receipt. The buyer checks the NFT metadata with the physical luxury product and, if satisfied, signs the transaction and sends the data to the transfer component. The transfer component finally checks the validity of the two signatures contained in the received transfer transaction, as well as the timestamp showing the correct historical ownership of the NFT. If the signatures are valid and the timestamp of the product ownership shows the last owner is Pk1 (luxury producer), the NFT is transferred to the buyer (Pk2) and the list of luxury NFTs connected to the buyer’s Pk is returned. The red-numbered transaction 3 denotes the third on-chain transaction that results in the status change of the blockchain. Hence, the transaction involving the buyer appending the signature on the initial transaction generated by the seller and storing the completed transfer transaction on-chain results in the state change of the blockchain.
The simulation results show that viewing a luxury NFT and verifying historical ownership of luxury products provides instant results within a couple of seconds. Additionally, viewing luxury NFTs requires the user to only scan the QR code of the luxury product or view NFTs linked to their public key. For transferring of luxury NFT operation, the recorded simulation video (LogisticsBDT NFT transfer operation simulation: https://www.youtube.com/watch?v=sa_91lc_1u8 (accessed on 22 December 2022) shows that it takes about 3 min to initiate the transfer operation and return the completed transfer transaction details. The transfer transaction only requires the last owner of the NFT to update the image of the product, sign the data and share the transfer receipt with the buyer. For the buyer, it requires scanning the transfer receipt, checking if NFT details match with the physical product and signing the transaction.
4.2. Discussions
The discussions resulting from this work are centered around three themes. Section 4.2.1 discusses the implication of the evaluation (simulation) results in luxury product authentication addressing the problems in luxury product authentication as represented in the AS-IS process. Section 4.2.2 discusses the implication of the developed solution in comparison with similar works that apply blockchain for luxury product authentication. Section 4.2.3 discusses the implications of the research contributions of this work for retailers and consumers of luxury products.
4.2.1. Implications of the Evaluation Results on the Problems of Luxury Products Authentication
The traditional process of luxury products authentication as depicted in Figure 2 shows that specialized equipment, specialized skills, and an enormous amount of time are required to verify luxury products. Consumers that seek to perform independent verification tasks without relying on experts yield a high number of false-positive and false-negative results due to a lack of skills and verification tools. The simulation results from the LogsiticsBDT platform demonstrate that the only item needed to verify and transfer ownership of luxury products is a standard mobile browser with a functional internet connection. Additionally, to use the application, only a minimal knowledge of blockchain is required to import wallets containing user public keys to the browser.
In terms of time requirements, the LogisticsBDT application provides instant verification results for luxury products by providing public keys and timestamps linked to the product. The user can easily verify the name of the organization that originally minted the NFT from the luxury NFT metadata. Additionally, reselling of pre-owned luxury products can be conducted between two users without using the approved brand retailer as the middleman in verifying product authenticity. The simulation results show that this type of trade can be completed between customers in about three minutes using the transfer function in the LogsiticsBDT application. Thus, consumers that are in locations not covered by the brand and their approved retailers can perform purchases of pre-owned luxury products without the risk of false-positive/false-negative verification results.
4.2.2. Implication of the Developed Blockchain-Based Luxury Product Authentication with Similar Works
Previous research has already applied blockchain in addressing counterfeiting problems in luxury products and supply chains in general. The research [15] shows a conceptual design of a blockchain solution for counterfeit prevention in supply chains. The paper [16] shows the design and implementation of anti-forgery and anti-tampering blockchain systems for transparent tracking of data associated with luxury products.
In the conceptual system proposed in [15], unique IDs are generated for every single product in the supply chain, such that data about the product is updated as it moves across different stages of the supply chain using the reference ID. The product data are updated during the manufacturing, distribution and storage of the products. The proposed model also suggests a functional transfer of ownership as the product moves along the supply chain and the resulting data is stored on the blockchain. In the system described in this paper, we show the implementation of a transparent tracking system that presents the history of luxury product ownership, from its manufacturing, retailing and purchases by the consumers using digital signatures and transaction timestamps stored on the blockchain. Although [15] proposes using blockchain to show the transfer of ownership of products, the research does not show how this can be achieved. In the current paper, we show that a transparent transfer of product ownership using blockchain can be realized by updating the image metadata of the product by the last owner and using a multi-party signature for storage of the resulting transaction on the blockchain.
In implementing the authentication solution, [16] develops a consortium blockchain network on consortium blockchain comprising the major stakeholders in the supply chain of luxury products. These players include the brand, manufacturers, suppliers, distributors, and logistic providers and they also validate the transactions proving the authenticity of luxury products. All these parties are initially verified, and their public keys are linked to their respective roles. The initial product design and required materials are all specified and stored on the blockchain. The product is manufactured according to the requirements specified in the product design. The transactions connected to the product as the product moves across the major players in the supply chain are recorded on the blockchain. In comparison, the solution developed in our paper uses a public blockchain and applies an automated agent-based challenge–response system to validate and register luxury brands. The solution described in [16] does not capture transactions on luxury products once they have been sold to the customers. Thus, transactions of pre-owned luxury products cannot be verified. Still, the solution implemented in this paper uses the minting transaction by registered luxury brands as the basis of the verification of authentic luxury items. In addition, we apply a multi-signature system to transparently record the historical transactions on the entire lifecycle of the luxury product, thereby making it possible to authenticate new and pre-owned luxury products.
4.2.3. Implications of the Research Contributions of This Work for Retailers and Consumers of Luxury Products
One of the main problems of the authentication of luxury products in the future will be the sheer indistinguishability from counterfeits to original products without spending considerable amounts of time and money in the authentication process [35,36]. Thus, retailers, as well as consumers, require a reliable as well as a cost-effective method to authenticate luxury products. Investigating this issue, [27] points out that consumers mainly request a seamlessly integrated and easy-to-use authentication process and retailers require a process that reduces costs and uncertainty of the authentication process. Furthermore, the publication pointed out that the traceability of product history and ownership is one of the most requested features for retailers as well as consumers. The luxury product authentication platform presented in this paper (see Section 4) addresses all these requirements. Thus, the developed platform presents a possible starting point for retailers who want to offer their customers a seamless and cost-efficient authentication process, superior to the time-consuming and cost-intensive traditional authentication process.
5. Conclusions
The objective achieved in this paper is the development of a blockchain-based authentication system for verifying the authenticity of luxury accessories across the lifecycle of ownership of the products. This covers the purchase of luxury products by retailers from manufacturers, the purchase by consumers from retailers, and purchases by consumers from fellow consumers. Three research questions are developed to address the research needs identified for this paper. The first is to identify the important features of designing a digitized verification system for the authenticity verification of luxury accessories. By applying qualitative analytics based on expert interview data, the result shows two themes of problems in luxury product authentication. The first is product traceability and document verification problems and the second is the effort and difficulty of the verification tasks. Additionally, the factors that cause problems in luxury product authentication include a lack of knowledge and complexity of implementation of the verification process, high expense and authenticity cannot be guaranteed. Furthermore, by analyzing data from expert interviews, the AS-IS representation of luxury product authentication is developed.
The second research question seeks to develop a model representation for outlining the requirements of important features of blockchain applications for the verification of luxury accessories across their respective lifecycles. This is achieved by identifying the main blockchain-based features and technologies that can be used in addressing the weakness of conventional luxury product authentication systems represented by the AS-IS process. The features identified by the experts include product-ownership history, product identification, and product-ownership transfer. By applying blockchain-based requirement engineering prescribed by the T-DM approach, the main value propositions of a platform that enables the authentication of luxury products include, registering brands that can mint luxury NFTs, minting NFT representation of luxury products, transferring ownership of luxury products using 2-step digital signatures, and the viewing of historical ownership of a luxury product using digital timestamps. These value propositions are further refined into the functional requirements of the system. The types of users and software agents that execute these functional requirements are specified. Furthermore, the non-functional requirements that shows how the functional requirements are executed are outlined and described.
The third research question seeks to outline the architecture and existing blockchain technologies for prototyping the requirements in the model representation of the proposed platform. The architecture of the luxury product authentication platform shows the main components, subcomponents, interaction interfaces and users that interact with the components. Four main components of the platform include brand registration, minting and transfer, and the viewing components. Interacting with the brand registration component results in the brand data, the minting component produces luxury NFT and metadata, the transfer component produces updated luxury NFT metadata. Furthermore, the PD method is used to rank suggested technologies for realizing the platform architecture. The selected technologies are then applied in implementing the luxury product authentication platform.
To evaluate the implemented platform, the operations that can be carried out on the platform are simulated in a test environment. The first simulated operation is the brand registration and NFT minting operation. The second simulated operation is the viewing luxury NFT and transfer operation. The simulation result shows the user tasks completed in these operations and their estimated completion times. The brand registration requires two user tasks, and ca. 2 min to successfully register a brand. Luxury NFT minting requires two user tasks and ca. 3 min to successfully mint a luxury NFT. Viewing luxury products provides an instant result of historical ownership of an NFT and their timestamps. Transferring a luxury NFT requires four user tasks by the seller and three user tasks by the buyer and ca. 3 min to successfully complete the luxury NFT transfer operation.
The main contribution of this paper is designing and developing a PoC blockchain platform for authenticating luxury products by using NFTs to verify the entire lifecycle of ownership of luxury products. The following results were generated to form this contribution: (i) a BPMN diagram showing the conventional luxury product authentication approach. (ii) a model diagram showing the requirements of a blockchain system for authenticating luxury products. (iii) an architectural diagram and formal pseudocodes for realizing the algorithms of the developed authentication platform. (iv) behavioral diagrams showing the use case simulations of user operations when authenticating luxury products. From the academic aspect, the contribution of this paper is that it demonstrates the application of the T-DM approach in designing and developing blockchain applications for organizational use cases. The T-DM approach described and presented in the recent thesis [37], outlines software models that are used in building blockchain systems that enable trustable business collaborations. Thus, in this paper, the application of the T-DM approach establishes the business-to-business, business-to-customer and customer-to-customer relationships involved in authenticating luxury products. These collaborations are captured during the minting and transferring of luxury NFTs in the LogisticsBDT platform.
5.1. Limitations
This research comprises the following limitations. The first is the risk of generalization ability, considering that only eight experts are used in qualitatively identifying the problems in luxury product authentication and generating the corresponding AS-IS process. Due to the limited number of experts, the identified problems and depicted process may not correctly represent the current state of luxury product authentication. Another limitation is the current method used in proving the authenticity of luxury products. As presented in the paper, a luxury product is authentic if the associated NFT to the product ID is minted by the correct luxury brand. Still, the brand registration email can be exploited by hacking the brand organization’s email system. Additionally, considering that individuals who work in an organization may relocate, the current email-challenge verification system does not address these concerns. These security concerns raise questions about the authenticity of the minted NFTs.
5.2. Future Work
The future work from this research is to generate a robust set of configurable challenges that can be used to authenticate luxury brands to mint luxury NFTs using blockchain-based oracles. Previous work by MFSSIA [38] already described a flexible and secure system for authenticating organizations, individuals and devices in a digital environment using a configurable challenge–response system. Thus, integrating the MFSSIA authentication system into the brand registration and NFT minting operation of the LogisticsBDT provides a logical future work that continues this research. In addition, we will also add a manual KYC for luxury brands to further improve the robustness of the brand registration aspect of the LogisticsBDT platform. Finally, we aim to test the generalization power of this research work by applying the results to a different application domain being a novel Web3 advanced video streaming application with the goal of restoring a viable decentralized, distributed and disintermediated business model for the film industry.
Author Contributions
Conceptualization, C.U., A.N. and P.B.; methodology, C.U., A.N. and P.B.; software, C.U., A.K. and S.M.A.; validation, A.N; formal analysis, C.U. and R.Z.; investigation, C.U., A.N. and P.B; resources, C.U. and R.Z.; data curation, C.U. and R.Z.; writing—original draft preparation, C.U. and R.Z.; writing—review and editing, C.U., A.N., P.B. and R.Z.; visualization, C.U., A.K. and S.M.A.; supervision, A.N. and P.B.; project administration, A.N.; funding acquisition, C.U., A.N. and P.B. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Robonomics Grant Program, grant number Blockchain Application Development, the Government of Upper Austria as part of the Excellence Network for Logistics Log.Retail, and Estonian personal research funding “Team grant (PRG) project PRG1641”.
Acknowledgments
Open Access Funding by University of Applied Sciences Upper Austria.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bundgaard, A.M.; Huulgaar, R.D. Luxury products for the circular economy? A case study of Bang & Olufsen. Bus. Strategy Environ. 2019, 28, 699–709. [Google Scholar]
- Hennigs, N.; Wiedmann, K.P.; Klarmann, C.; Behrens, S. Sustainability as part of the luxury essence: Delivering value through social and environmental excellence. J. Corp. Citizsh. 2013, 52, 25–35. [Google Scholar] [CrossRef]
- Abtan, O.; Ducasse, P.; Finet, L.; Gardet, C.; Gasc, M.; Salaire, S. Why Luxury Brands Should Celebrate the Preowned Boom. BCG. 2019. Available online: https://www.bcg.com/publications/2019/luxury-brands-should-celebrate-preowned-boom.aspx (accessed on 22 December 2022).
- Sun, J.J.; Bellezza, S.; Pahari, N. Buy less, buy luxury: Understanding and overcoming product durability neglect for sustainable consumption. J. Mark. 2021, 85, 28–43. [Google Scholar] [CrossRef]
- Brandão, C.; Pinto, A.M.; Gadeka, M. The Counterfeit Market and the Luxury Goods. In Fashion Industry-An Itinerary between Feelings and Technology; BoD–Books on Demand: Norderstedt, Germany, 2019. [Google Scholar]
- OECD/EUIPO. Trends in Trade in Counterfeit and Pirated Goods, Illicit Trade; OECD Publishing: Paris, France, 2019. [CrossRef]
- Ting, M.-S.; Goh, Y.-N.; Is, S.M. Determining consumer purchase intentions toward counterfeit luxury goods in Malaysia. Asia Pac. Manag. Rev. 2016, 21, 219–230. [Google Scholar] [CrossRef]
- Staake, T.; Thiesse, F.; Fleisch, E. The emergence of counterfeit trade: A literature review. Eur. J. Market. 2009, 43, 320–349. [Google Scholar] [CrossRef]
- Peng, J.; Zou, B.; Zh, C. Combining external attention GAN with deep convolutional neural networks for real–fake identification of luxury handbags. Vis. Comput. 2022, 1–12. [Google Scholar] [CrossRef]
- De Boissieu, E.; Kondrateva, G.; Baudier, P.; Ammi, C. The use of blockchain in the luxury industry: Supply chains and the traceability of goods. J. Enterp. Inf. Manag. 2021. ahead-of-print. [Google Scholar] [CrossRef]
- Kolev, G.V.; Neligan, A. Effects of a Supply Chain Regulation: Survey-Based Results on the Expected Effects of the German Supply Chains Act; No. 8/2022. IW-Report, Nr. 8; Institut der Deutschen Wirtschaft Köln: Köln, Germany, 2022. [Google Scholar]
- Felbermayr, G.; Langhammer, R.; Sandkamp, A.; Herrmann, C.; Trapp, P. Economic Evaluation of a Due Diligence Law; IfW Kiel Institute for the World Economy: Kiel, Germany, 2021. [Google Scholar]
- Swan, M. Blockchain: Blueprint for a New Econom; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Udokwu, C.; Kormiltsyn, A.; Thangalimodzi, K.; Norta, A. The state of the art for blockchain-enabled smart-contract applications in the organization. In Proceedings of the 2018 Ivannikov Ispras Open Conference (ISPRAS), Moscow, Russia, 22–23 November 2018; pp. 137–144. [Google Scholar]
- Gayialis, S.P.; Kechagias, E.; Papadopoulos, G.A.; Konstantakopoulos, G.D. Design of a blockchain-driven system for product counterfeiting restraint in the supply chain. In Proceedings of the IFIP International Conference on Advances in Production Management Systems, Austin, TX, USA, 1 September 2019; Springer: Cham, The Netherlands, 2019; pp. 474–481. [Google Scholar]
- Chen, C.L.; Guo, L.H.; Zhou, M.; Tsaur, W.J.; Sun, H.; Zhan, W.; Li, C.T. Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products. Sustainability 2022, 14, 12814. [Google Scholar] [CrossRef]
- Ugochukwu, N.A.; Goyal, S.B.; Rajawat, A.S.; Islam, S.M.; He, J.; Aslam, M. An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method. Mathematics 2022, 10, 4670. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieto, J. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Chiacchio, F.; D’Urso, D.; Oliveri, L.M.; Spitaleri, A.; Spampinato, C.; Giordano, D. A Non-Fungible Token Solution for the Track and Trace of Pharmaceutical Supply Chain. Appl. Sci. 2022, 12, 4019. [Google Scholar] [CrossRef]
- Musamih, A.; Salah, K.; Jayaraman, R.; Arshad, J.; Debe, M.; Al-Hammadi, Y.; Ellahham, S. A blockchain-based approach for drug traceability in healthcare supply chain. IEEE Access 2021, 9, 9728–9743. [Google Scholar] [CrossRef]
- Biswas, K.; Muthukkumarasamy, V.; Tan, W.L. Blockchain based wine supply chain traceability system. In Future Technologies Conference (FTC); The Science and Information Organization: New York, NY, USA, 2017; pp. 56–62. [Google Scholar]
- Rossi, M.; Mueller-Bloch, C.; Thatcher, J.B.; Beck, R. Blockchain research in information systems: Current trends and an inclusive future research agenda. J. Assoc. Inf. Syst. 2019, 20, 14. [Google Scholar] [CrossRef]
- Ullah, A.; Siddiquee, S.S.; Hossain, M.A.; Ray, S.K. thereumeum blockchain-based prototype for data security of regulated electricity market. Inventions 2020, 5, 58. [Google Scholar] [CrossRef]
- Hugo, B.; Caceres, C.; Abarzúa, L.Á. “Utility Tokens.” The Emerald Handbook on Cryptoassets: Investment Opportunities and Challenges; Emerald Publishing Limited: Bingley, UK, 2023; pp. 79–92. [Google Scholar]
- Hevner, A.R.; March, S.T.; Park, J.; Ram, S. Design science in information systems research. MIS Q. 2004, 28, 75–105. [Google Scholar] [CrossRef]
- Ritchie, J.; Spence, L. Qualitative Data Analysis for Applied Policy Research. Analyzing Qualitative Data; Routledge: Cambridge, UK, 2002; pp. 187–208. [Google Scholar]
- Zimmermann, R.; Udokwu, C.; Kompp, R.; Brandtner, P.; Norta, A. Authentication of Luxury Products–Identifying Key Requirements from a Seller and Consumer Perspective. In Proceedings of the International Conference on Future Data and Security Engineering, Ho Chi Minh City, Vietnam, 23–25 November 2022; Springer: Singapore, 2022; pp. 195–209. [Google Scholar]
- Udokwu, C.; Anyanka, H.; Nort, A. Evaluation of approaches for designing and developing decentralized applications on blockchain. In Proceedings of the 2020 4th International Conference on Algorithms, Computing and Systems, Berlin, Germany, 6–8 January 2020. [Google Scholar]
- Udokwu, C.; Nort, A. Deriving and formalizing requirements of decentralized applications for inter-organizational collaborations on blockchain. Arab. J. Sci. Eng. 2021, 46, 8397–8414. [Google Scholar] [CrossRef]
- Sterling, L.; Taveter, K. The Art of Agent-Oriented Modelling; MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Miller, T.; Pedell, S. Emotion-led modelling for people-oriented requirements engineering: The case study of emergency systems. J. Syst. Softw. 2015, 105, 54–71. [Google Scholar] [CrossRef]
- Janesick, V. Peer Debriefing. The Blackwell Encyclopedia of Sociology; Wiley Online library: Hoboken, NJ, USA, 2007; Available online: https://onlinelibrary.wiley.com/doi/abs/10.1002/9781405165518.wbeosp014.pub2 (accessed on 22 December 2022).
- Green, R.T.; Smit, T. Executive insights: Countering brand counterfeiters. J. Int. Mark. 2002, 10, 89–106. [Google Scholar] [CrossRef]
- Udokwu, C.; Brandtner, P.; Norta, A.; Kormiltsyn, A.; Matulevičius, R. Implementation and evaluation of the DAOM framework and support tool for designing blockchain decentralized applications. Int. J. Inf. Technol. 2021, 13, 2245–2263. [Google Scholar] [CrossRef]
- Randhawa, P.; Calantone, R.J.; Voorhee, C.M. The pursuit of counterfeited luxury: An examination of the negative side effects of close consumer–brand connections. J. Bus. Res. 2015, 68, 2395–2403. [Google Scholar] [CrossRef]
- Ting, S.L.; Tsan, A.H. A two-factor authentication system using radio frequency identification and watermarking technology. Comput. Ind. 2013, 64, 268–279. [Google Scholar] [CrossRef]
- Udokwu, C.J. A Modelling Approach for Building Blockchain Applications That Enables Trustable Inter-Organizational Collaborations. Doctoral Dissertation, Lappeenranta University of Technology, Lappeenranta, Finland, 2022. [Google Scholar]
- Norta, A.; Kormiltsyn, A.; Udokwu, C.; Dwivedi, V.; Aroh, S.; Nikolajev, I. A Blockchain Implementation for Configurable Multi-Factor Challenge-Set Self-Sovereign Identity Authentication. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22 August 2022; pp. 455–461. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).