Evaluating the Reliability and Security of an Uplink NOMA Relay System Under Hardware Impairments
Abstract
1. Introduction
1.1. Literature Review
1.2. Motivation and Main Contributions
- A secure uplink NOMA system is proposed, where user 1 () and user 2 () transmit signals to the via an R considering the presence of a potential E and the impact of HIs on all devices.
- A comprehensive analysis of the system’s PLS and reliability is provided, with closed-form expressions derived for key performance metrics, including COP, SOP, and IP.
- To validate the accuracy of the theoretical analysis, extensive Monte Carlo simulations are conducted under various system settings. These simulations not only confirm the analytical results but also provide valuable insights into the influence of key parameters on system performance, thereby highlighting the practicality of the design.
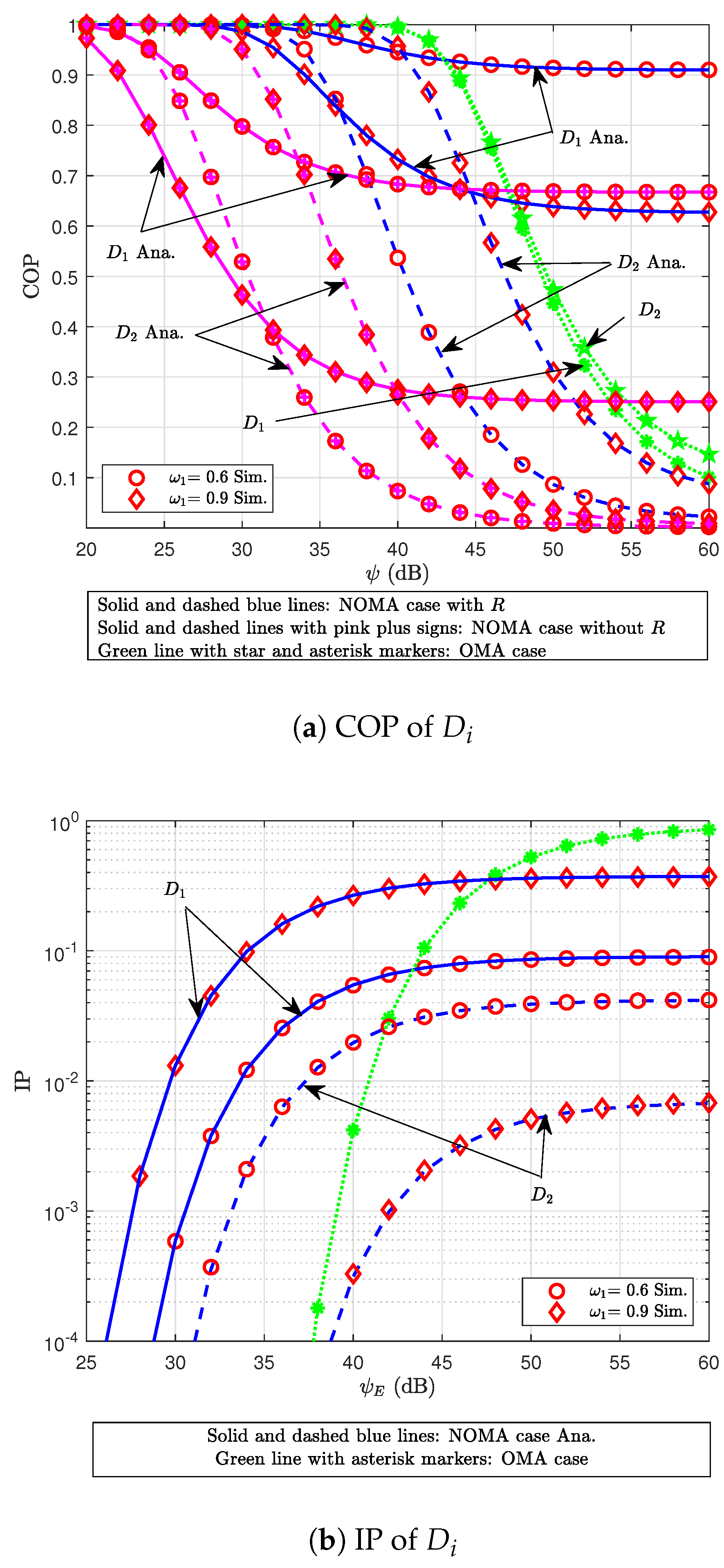
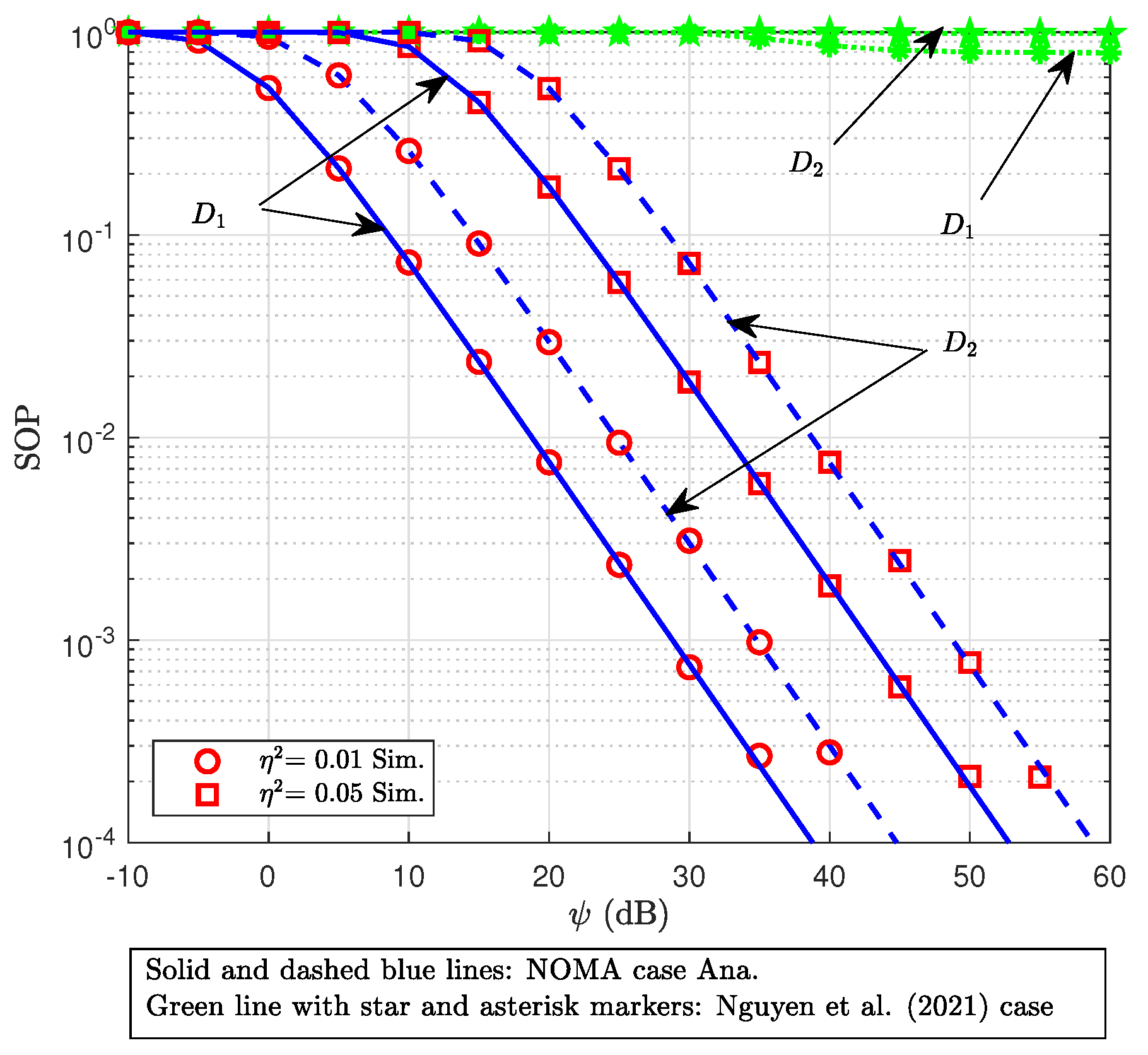
- Moreover, the proposed approach is benchmarked against conventional orthogonal multiple access (OMA)-based schemes and the related model in [19]. The results clearly demonstrate superior reliability and security, emphasizing its effectiveness and potential applicability in realistic communication scenarios.
1.3. Structure
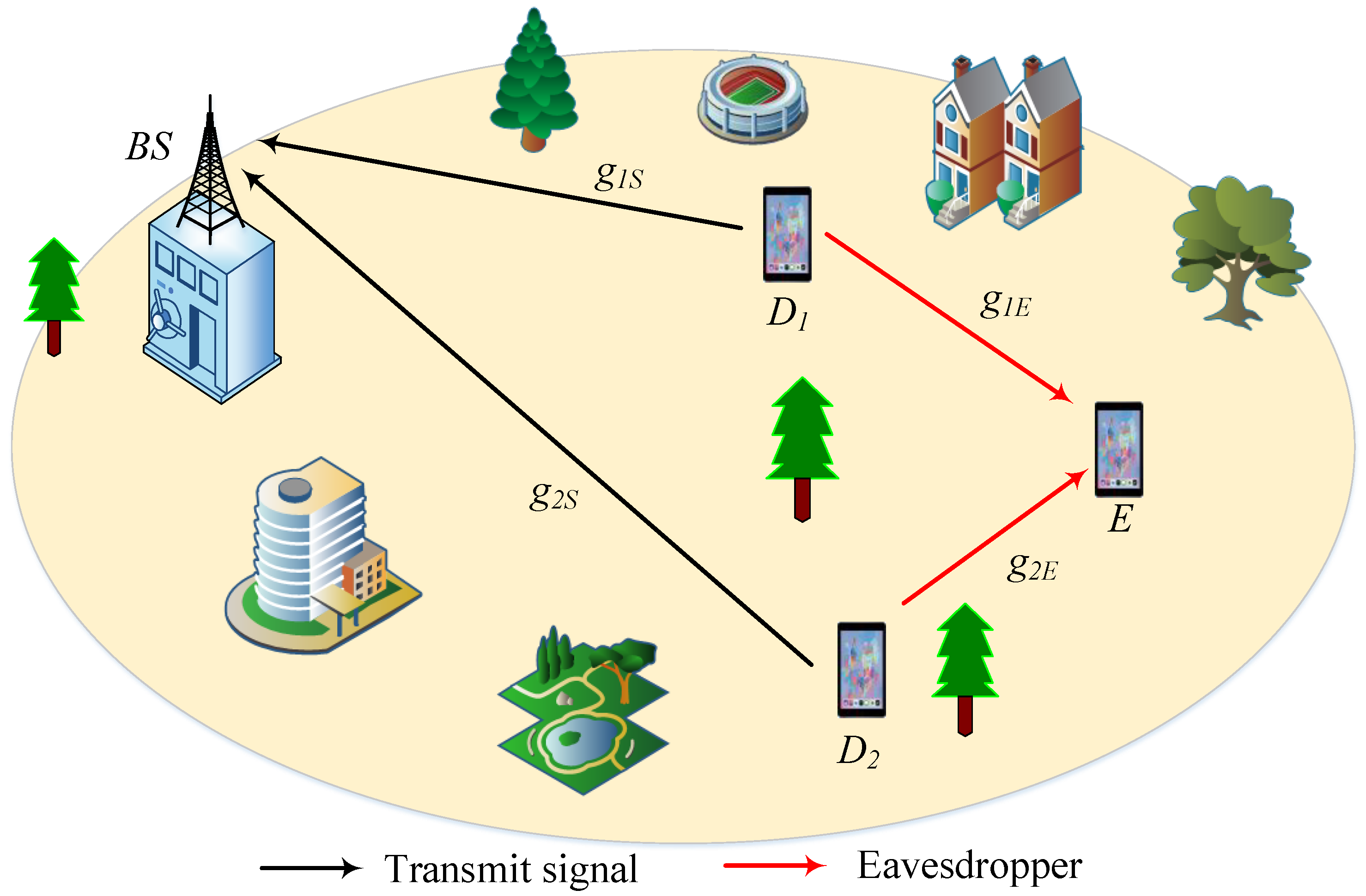
2. System Model
2.1. SIC Assumptions
- At the R, the message of is not decoded; instead, only acts as interference. The relay attempts to decode the signal of while treating the signal of as interference, as reflected in the corresponding SINR expression.
- At the E, it is assumed that SIC is feasible. In this case, E first decodes the signal of and, after cancellation, attempts to decode the signal of . This corresponds to the SINR expressions for E in both transmission phases.
- At the , decoding follows a different order due to the stronger link of . The first decodes the signal of and then performs SIC to decode the signal of .
2.2. Signal Analysis in the First Time Slot
2.3. Signal Analysis in the Second Time Slot
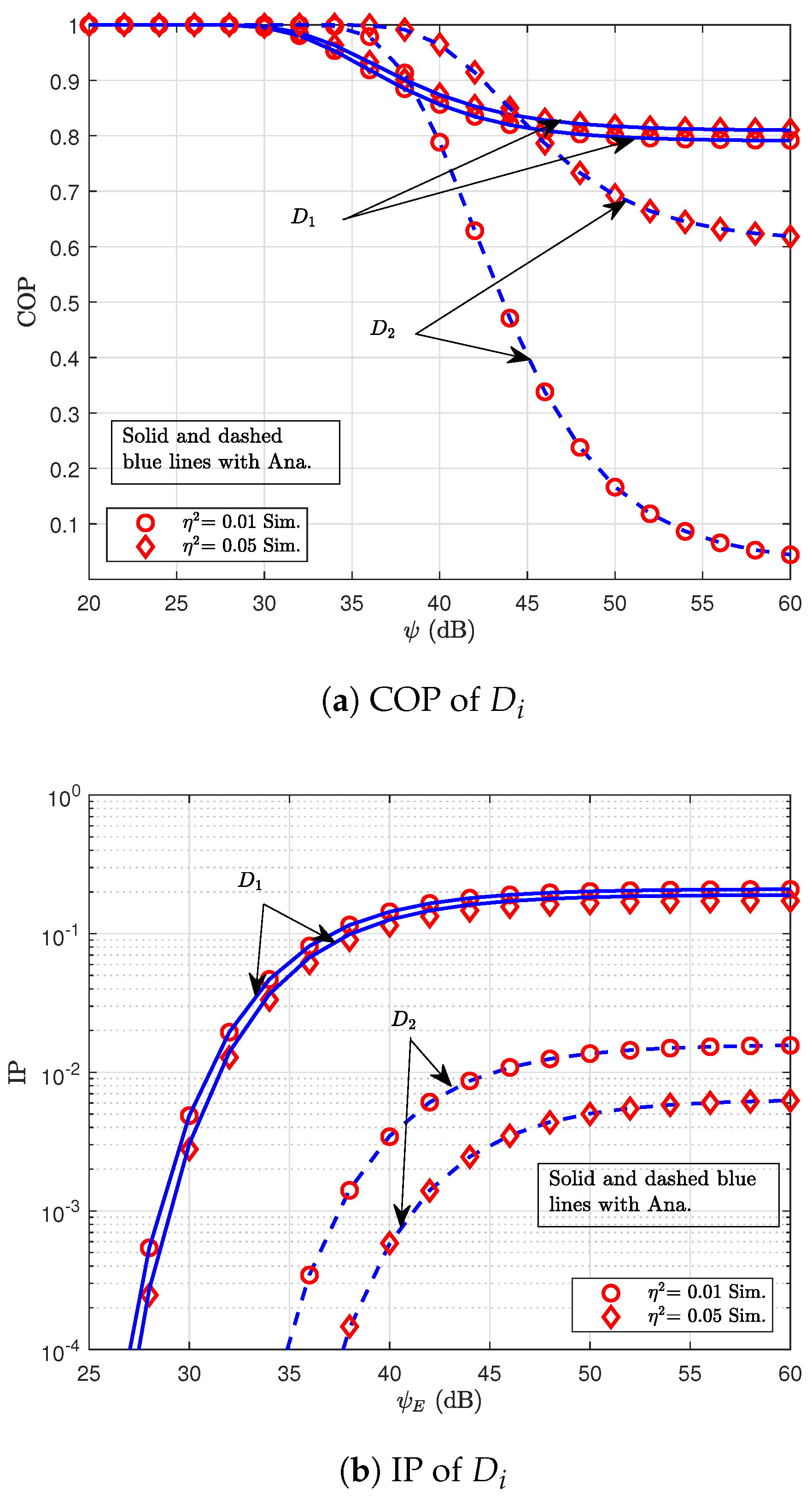
3. Examining the COP
3.1. COP for
3.2. COP for
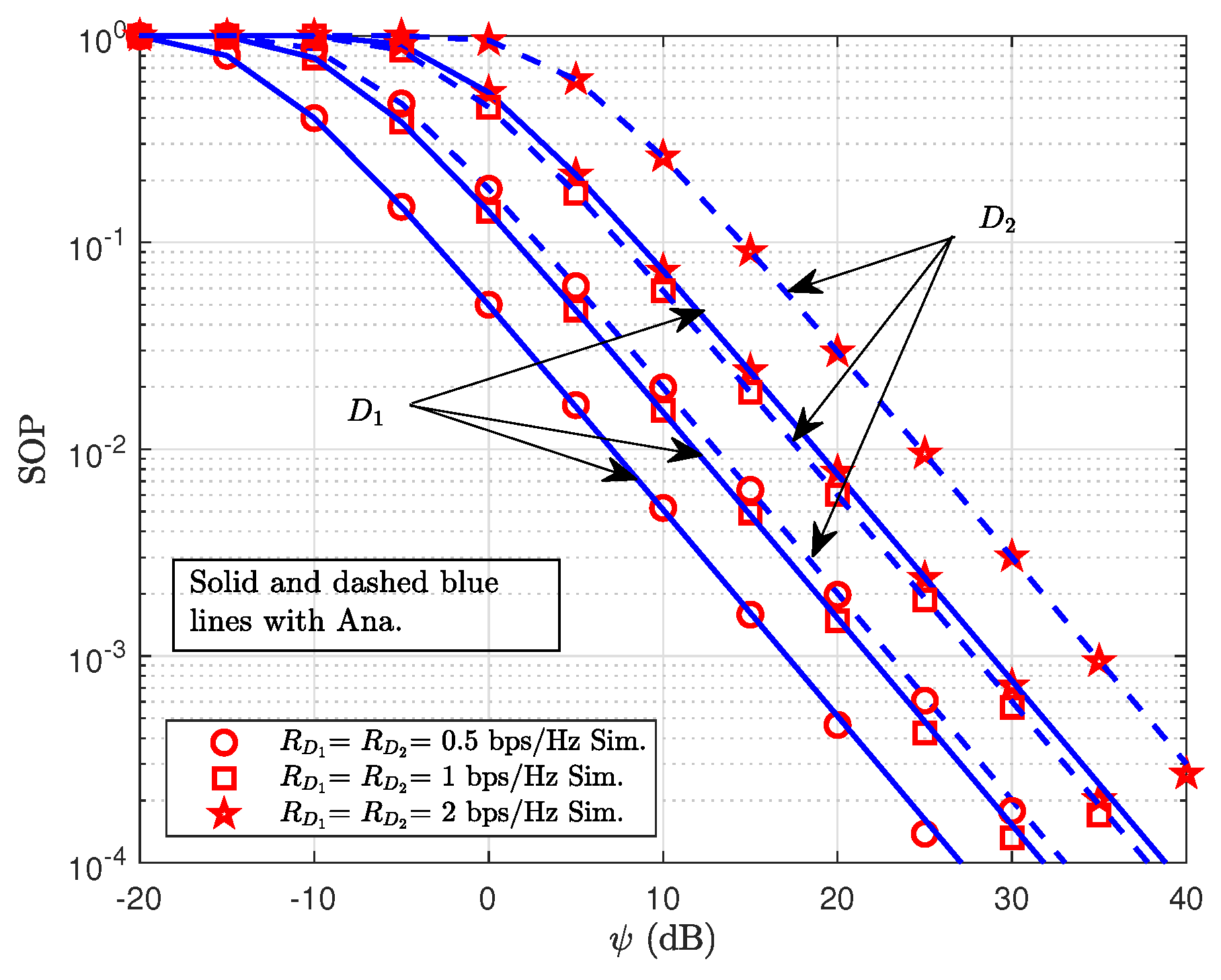
4. Examining the SOP
4.1. SOP for
4.2. SOP for
5. Examining the IP
5.1. IP for
5.2. IP for
6. Expanding Research with a Model of a System Without Relay
6.1. COP of
6.2. COP of
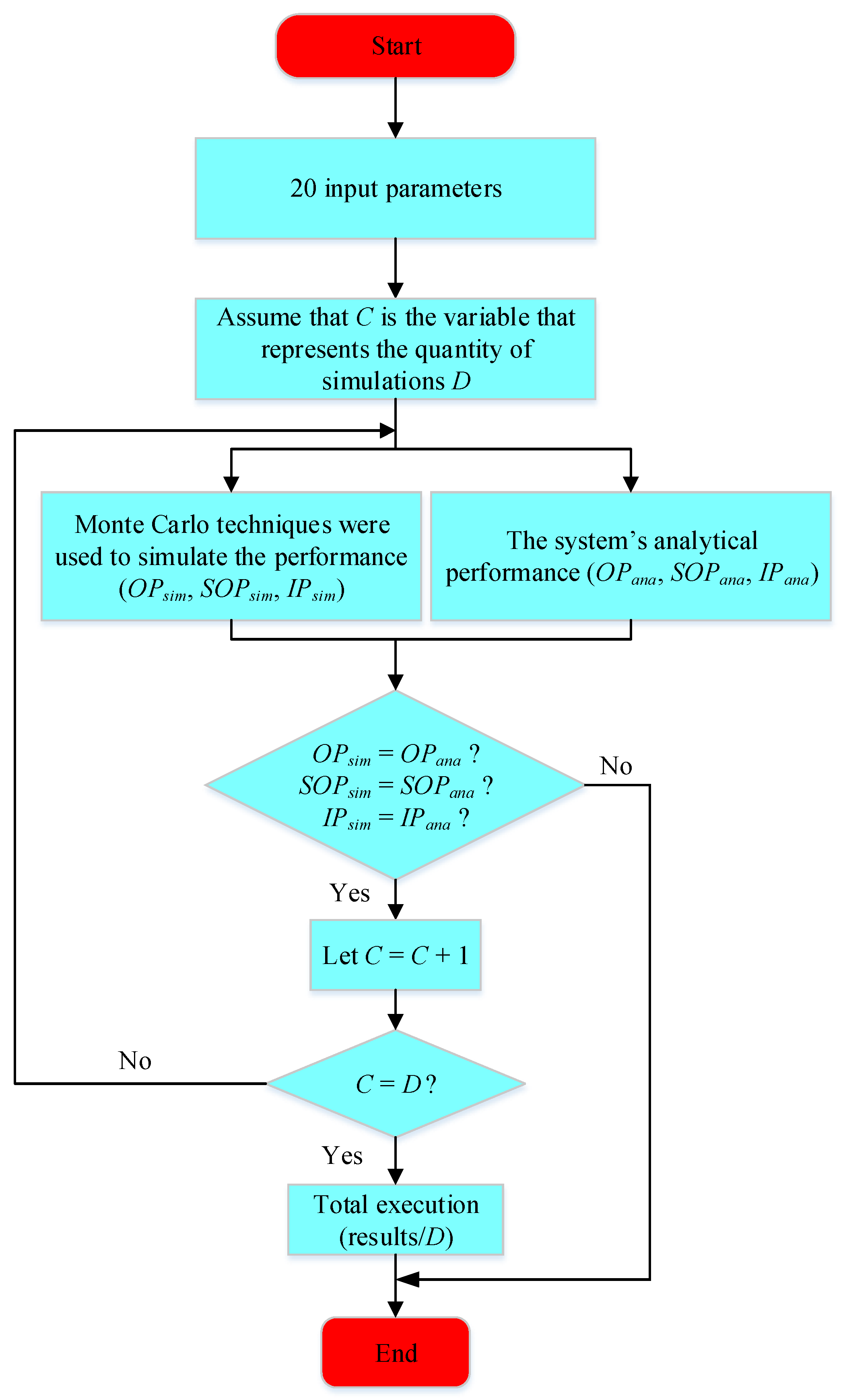
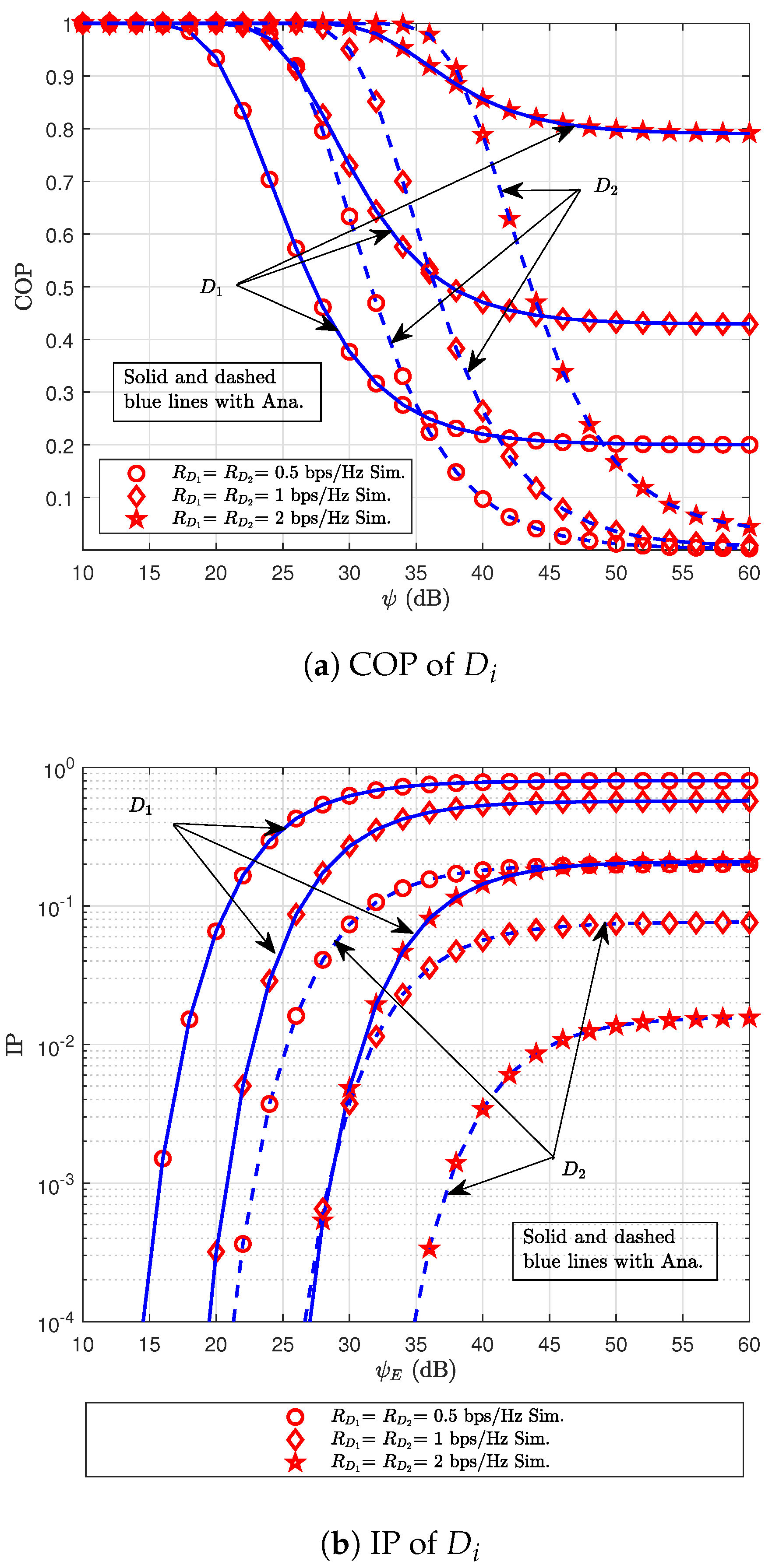
7. Simulation Results
- Slot 1: user transmits to the while the E attempts to intercept ’s transmission.
- Slot 2: user transmits to the relay R; during this slot, also transmits and thus acts as an interfering source to (this models residual simultaneous uplink activity); E listens to in this slot.
- Slot 3: transmits again to the , with E eavesdropping.
- Slot 4: R forwards the decoded signal to the , and E listens to the relay transmission.
| Algorithm 1 Methodology for Assessing the Probability of Outage for Dual Users. |
|
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
Appendix C
Appendix D
Appendix E
Appendix F
Appendix G
Appendix H
References
- Mead, J.A.; Singh, K.; Allu, R.; Biswas, S.; Ku, M.L. Hardware Impairment Aware Transmit Power Minimization for Secure RIS-Aided Full-Duplex NOMA Communications. IEEE Trans. Green Commun. Netw. 2024, 9, 1153–1166. [Google Scholar] [CrossRef]
- Ali, K.S.; Al-Dweik, A.; Hossain, E.; Chafii, M. Physical Layer Security of Partial-NOMA and NOMA in Poisson Networks. IEEE Trans. Wirel. Commun. 2024, 23, 6562–6579. [Google Scholar] [CrossRef]
- Zhang, H.; Jin, M.; Guo, Q.; Yao, J. Secure Beamforming for NOMA-ISAC with Multicast and Unicast Communications. IEEE Wirel. Commun. Lett. 2024, 13, 2927–2931. [Google Scholar] [CrossRef]
- Hao, W.; Zeng, M.; Chu, Z.; Yang, S. Energy-Efficient Power Allocation in Millimeter Wave Massive MIMO With Non-Orthogonal Multiple Access. IEEE Wirel. Commun. Lett. 2017, 6, 782–785. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-lin, I.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Van Nguyen, M.S.; Do, D.T.; Al-Rubaye, S.; Mumtaz, S.; Al-Dulaimi, A.; Dobre, O.A. Exploiting Impacts of Antenna Selection and Energy Harvesting for Massive Network Connectivity. IEEE Trans. Commun. 2021, 69, 7587–7602. [Google Scholar] [CrossRef]
- Tin, P.T.; Huy, P.V.; Thanh, L.V.; Nguyen, M.S.V. Analyzing Performance of NOMA Cooperative Networks with Reconfigurable Intelligent Surfaces in Cognitive Radio Networks. In Proceedings of the AETA 2023—Recent Advances in Electrical Engineering and Related Sciences: Theory and Application, Busan, Republic of Korea, 14–16 December 2023; Trong Dao, T., Zelinka, I., Hoang Duy, V., Wang, J.P., Dong, C.S.T., Tran, P.T., Eds.; Springer: Singapore, 2025; pp. 109–119. [Google Scholar]
- Van Nguyen, M.S.; Do, D.T.; Vahid, A.; Muhaidat, S.; Sicker, D. Enhancing NOMA Backscatter IoT Communications With RIS. IEEE Internet Things J. 2024, 11, 5604–5622. [Google Scholar] [CrossRef]
- Asif, M.; Bao, X.; Ihsan, A.; Khan, W.U.; Ahmed, M.; Li, X. Securing NOMA 6G Communications Leveraging Intelligent Omni-Surfaces Under Residual Hardware Impairments. IEEE Internet Things J. 2024, 11, 25326–25336. [Google Scholar] [CrossRef]
- Le, A.T.; Tran, D.H.; Le, C.B.; Tin, P.T.; Nguyen, T.N.; Ding, Z.; Poor, H.V.; Voznak, M. Power Beacon and NOMA-Assisted Cooperative IoT Networks With Co-Channel Interference: Performance Analysis and Deep Learning Evaluation. IEEE Trans. Mob. Comput. 2024, 23, 7270–7283. [Google Scholar] [CrossRef]
- Ju, Y.; Cao, Z.; Chen, Y.; Liu, L.; Pei, Q.; Mumtaz, S.; Dong, M.; Guizani, M. NOMA-Assisted Secure Offloading for Vehicular Edge Computing Networks With Asynchronous Deep Reinforcement Learning. IEEE Trans. Intell. Transp. Syst. 2024, 25, 2627–2640. [Google Scholar] [CrossRef]
- Zhou, T.; Fu, Y.; Qin, D.; Nie, X.; Jiang, N.; Li, C. Secure and Multistep Computation Offloading and Resource Allocation in Ultradense Multitask NOMA-Enabled IoT Networks. IEEE Internet Things J. 2024, 11, 5347–5361. [Google Scholar] [CrossRef]
- Björnson, E.; Hoydis, J.; Kountouris, M.; Debbah, M. Massive MIMO Systems With Non-Ideal Hardware: Energy Efficiency, Estimation, and Capacity Limits. IEEE Trans. Inf. Theory 2014, 60, 7112–7139. [Google Scholar] [CrossRef]
- Dang, H.P.; Van Nguyen, M.S.; Do, D.T.; Pham, H.L.; Selim, B.; Kaddoum, G. Joint Relay Selection, Full-Duplex and Device-to-Device Transmission in Wireless Powered NOMA Networks. IEEE Access 2020, 8, 82442–82460. [Google Scholar] [CrossRef]
- Li, M.; Selim, B.; Muhaidat, S.; Sofotasios, P.C.; Dianati, M.; Yoo, P.D.; Liang, J.; Wang, A. Effects of Residual Hardware Impairments on Secure NOMA-Based Cooperative Systems. IEEE Access 2020, 8, 2524–2536. [Google Scholar] [CrossRef]
- AlaaEldin, M.; Alsusa, E.; Al-Jarrah, M.; Seddik, K.G.; Matthaiou, M. Generalized BER Performance Analysis for SIC-Based Uplink NOMA. IEEE Open J. Commun. Soc. 2025, 6, 1246–1265. [Google Scholar] [CrossRef]
- Sa, S.K.; Mishra, A.K. Enhancing MEC Offloading Performance with NOMA-CDRT in the Presence of Impaired Hardware. IEEE Access 2024, 12, 98803–98815. [Google Scholar] [CrossRef]
- Al-Musawi, I.M.; Al-Hussaibi, W.A.; Ali, F.H. Efficient Secure NOMA Schemes Based on Chaotic Physical Layer Security for Wireless Networks. IEEE Open J. Commun. Soc. 2022, 3, 2425–2443. [Google Scholar] [CrossRef]
- Nguyen, M.S.V.; Do, D.T.; Afghah, F.; Islam, S.M.R.; Le, A.T. Exploiting Secrecy Performance of Uplink NOMA in Cellular Networks. IEEE Access 2021, 9, 95135–95154. [Google Scholar] [CrossRef]
- Van Nguyen, M.S.; Do, D.T. Evaluating secrecy performance of cooperative NOMA networks under existence of relay link and direct link. Int. J. Commun. Syst. 2020, 33, e4284. [Google Scholar] [CrossRef]
- Li, X.; Zhao, M.; Zeng, M.; Mumtaz, S.; Menon, V.G.; Ding, Z.; Dobre, O.A. Hardware Impaired Ambient Backscatter NOMA Systems: Reliability and Security. IEEE Trans. Commun. 2021, 69, 2723–2736. [Google Scholar] [CrossRef]
- Chen, J.; Yang, L.; Alouini, M.S. Physical Layer Security for Cooperative NOMA Systems. IEEE Trans. Veh. Technol. 2018, 67, 4645–4649. [Google Scholar] [CrossRef]
- Deng, C.; Liu, M.; Li, X.; Liu, Y. Hardware Impairments Aware Full-Duplex NOMA Networks Over Rician Fading Channels. IEEE Syst. J. 2021, 15, 2515–2518. [Google Scholar] [CrossRef]
- Tin, P.T.; Minh Nam, P.; Trung Duy, T.; Tran, P.T.; Voznak, M. Secrecy Performance of TAS/SC-Based Multi-Hop Harvest-to-Transmit Cognitive WSNs Under Joint Constraint of Interference and Hardware Imperfection. Sensors 2019, 19, 1160. [Google Scholar] [CrossRef] [PubMed]
- Wu, W.; Zhou, F.; Hu, R.Q.; Wang, B. Energy-Efficient Resource Allocation for Secure NOMA-Enabled Mobile Edge Computing Networks. IEEE Trans. Commun. 2020, 68, 493–505. [Google Scholar] [CrossRef]
- He, X.; Jin, R.; Dai, H. Physical-Layer Assisted Secure Offloading in Mobile-Edge Computing. IEEE Trans. Wirel. Commun. 2020, 19, 4054–4066. [Google Scholar] [CrossRef]
- Van Nguyen, M.S.; Do, D.T.; Tin, P.T.; Vahid, A. Secure Performance Analysis of User Pairs in Active Reconfigurable Intelligent Surface-Aided IoT Systems. IEEE Syst. J. 2025, 19, 370–381. [Google Scholar] [CrossRef]
- Ju, Y.; Zou, G.; Bai, H.; Liu, L.; Pei, Q.; Wu, C.; Otaibi, S.A. Random Beam Switching: A Physical Layer Key Generation Approach to Safeguard mmWave Electronic Devices. IEEE Trans. Consum. Electron. 2023, 69, 594–607. [Google Scholar] [CrossRef]
- Zhou, J.; Dong, X.; Cao, Z.; Vasilakos, A.V. Secure and Privacy Preserving Protocol for Cloud-Based Vehicular DTNs. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1299–1314. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless Information-Theoretic Security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Kader, M.F.; Shin, S.Y. Coordinated Direct and Relay Transmission Using Uplink NOMA. IEEE Wirel. Commun. Lett. 2018, 7, 400–403. [Google Scholar] [CrossRef]
- Tin, P.T.; Luan, N.T.; Nguyen, T.N.; Tran, M.; Duy, T.T. Throughput enhancement for multi-hop decode-and-forward protocol using interference cancellation with hardware imperfection. Alex. Eng. J. 2022, 61, 5837–5849. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, M.S.V.; Duy, T.T.; Huy, P.V.; Thanh, L.V.; Kim, B.S. Performance and Secrecy Analysis of Cooperative Full-Duplex NOMA System with Fountain Codes and Intelligent Reflective Surface. IEEE Access 2025, 13, 113089–113112. [Google Scholar] [CrossRef]
- Van Nguyen, M.S.; Do, D.T.; Phan, V.D.; Ullah Khan, W.; Imoize, A.L.; Fouda, M.M. Ergodic Performance Analysis of Double Intelligent Reflecting Surfaces-Aided NOMA–UAV Systems with Hardware Impairment. Drones 2022, 6, 408. [Google Scholar] [CrossRef]
- Nguyen, M.S.V.; Dang, H.P. Exploiting Performance of Ambient Backscatter Systems in Presence of Hardware Impairment. Adv. Electr. Electron. Eng. 2021, 19, 313–321. [Google Scholar] [CrossRef]
- Tran Tin, P.; Phan, V.D.; Si Thien Chau, D.; Nguyen, T.N.; Nguyen, P.X. Performance Analysis in DF Energy Harvesting Full-Duplex Relaying Network with MRC and SC at the Receiver under Impact of Eavesdropper. J. Electr. Comput. Eng. 2021, 2021, 5547658. [Google Scholar] [CrossRef]
- Tung, N.T.; Nam, P.M.; Tin, P.T. Performance evaluation of a two-way relay network with energy harvesting and hardware noises. Digit. Commun. Netw. 2021, 7, 45–54. [Google Scholar] [CrossRef]
- Tin, P.T.; Duy, T.T. Power allocation strategies for dual-hop relay protocols with best relay selection under constraint of intercept probability. ICT Express 2019, 5, 52–55. [Google Scholar] [CrossRef]
- Van Nguyen, M.-S.; Do, D.-T.; Tin, P.T.; Imoize, A.L.; Kumaravelu, V.B. Full duplex reconfigurable intelligent surfaces system relying on NOMA and wireless power transfer. Wirel. Netw. 2024, 30, 2127–2142. [Google Scholar] [CrossRef]
- Tin, P.T.; Dinh, B.H.; Nguyen, T.N.; Ha, D.H.; Trang, T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry 2020, 12, 106. [Google Scholar] [CrossRef]
- Tin, P.T.; Van Nguyen, M.S.; Duy, T.T.; Pham, V.H.; Kim, B.S. Combination of RIS and Fountain Codes in NOMA relay wireless networks for enhancing system performance and security. ICT Express 2025, 11, 909–913. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, M.S.V.; Bui, Q.A.; Imoize, A.L.; Kim, B.S. System Modeling and Deep Learning-Based Security Analysis of Uplink NOMA Relay Networks with IRS and Fountain Codes. Comput. Model. Eng. Sci. 2025, 144, 2521–2543. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, M.S.V.; Tran, D.H.; Nguyen, C.T.; Chatzinotas, S.; Ding, Z.; Voznak, M. Performance Analysis of User Pairing for Active RIS-Enabled Cooperative NOMA in 6G Cognitive Radio Networks. IEEE Internet Things J. 2024, 11, 37675–37692. [Google Scholar] [CrossRef]
- Yue, X.; Liu, Y.; Kang, S.; Nallanathan, A.; Ding, Z. Exploiting Full/Half-Duplex User Relaying in NOMA Systems. IEEE Trans. Commun. 2018, 66, 560–575. [Google Scholar] [CrossRef]
- Guo, K.; Zhang, B.; Huang, Y.; Guo, D. Outage Analysis of Multi-Relay Networks With Hardware Impairments Using SECps Scheduling Scheme in Shadowed-Rician Channel. IEEE Access 2017, 5, 5113–5120. [Google Scholar] [CrossRef]
- Tran Tin, P.; van Nguyen, M.S.; Trung Duy, T.; Vu Minh, B.; Kim, B.S.; Rejfek, L. Enhancing Secrecy Performance Using Fountain Codes and NOMA Under Joint Cooperative Jamming Technique and Intelligent Reflective Surface. IEEE Access 2024, 12, 117399–117417. [Google Scholar] [CrossRef]



| This Study | [1] | [2] | [20] | [9] | [15] | [19] | [21] | [22] | [23] | [24] | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| The OMA system | √ | √ | √ | √ | √ | ||||||
| The NOMA system | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | |
| Uplink | √ | √ | √ | ||||||||
| PLS | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | |
| RHI | √ | √ | √ | √ | √ | √ | √ | ||||
| The relay system | √ | √ | √ | √ | √ | √ | √ | ||||
| COP | √ | √ | √ | √ | |||||||
| SOP | √ | √ | √ | √ | √ | ||||||
| IP | √ | √ | √ |
| Parameters | Values |
|---|---|
| Monte Carlo trials | |
| AWGN | = 1 |
| The allocation of power distribution at user nodes and | = 0.8; = 0.2 [42] |
| Target rates of and | = = 2 bps/Hz [43] |
| Average channel gains | [44] |
| The levels of RHI in | = 0.01 [45] |
| The levels of RHI of the - link | = 0.01 [45] |
| The levels of RHI of -R link | = 0.01 [45] |
| The levels of RHI in the -E link | = 0.01 [45] |
| The levels of RHI at the R | = 0.01 [45] |
| The levels of RHI in the R- link | = 0.01 [45] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ha, D.-H.; Ngo, T.-A.; Tran, X.-T.; Dam, M.-L.; Le, V.-T.; Imoize, A.L.; Li, C.-T. Evaluating the Reliability and Security of an Uplink NOMA Relay System Under Hardware Impairments. Mathematics 2025, 13, 3491. https://doi.org/10.3390/math13213491
Ha D-H, Ngo T-A, Tran X-T, Dam M-L, Le V-T, Imoize AL, Li C-T. Evaluating the Reliability and Security of an Uplink NOMA Relay System Under Hardware Impairments. Mathematics. 2025; 13(21):3491. https://doi.org/10.3390/math13213491
Chicago/Turabian StyleHa, Duy-Hung, The-Anh Ngo, Xuan-Truong Tran, Minh-Linh Dam, Viet-Thanh Le, Agbotiname Lucky Imoize, and Chun-Ta Li. 2025. "Evaluating the Reliability and Security of an Uplink NOMA Relay System Under Hardware Impairments" Mathematics 13, no. 21: 3491. https://doi.org/10.3390/math13213491
APA StyleHa, D.-H., Ngo, T.-A., Tran, X.-T., Dam, M.-L., Le, V.-T., Imoize, A. L., & Li, C.-T. (2025). Evaluating the Reliability and Security of an Uplink NOMA Relay System Under Hardware Impairments. Mathematics, 13(21), 3491. https://doi.org/10.3390/math13213491









