Abstract
In the article, we present an ad hoc (AH) detector for two differentially encoded BPSK sources in the Hierarchical MAC (H-MAC), i.e., for the case when the receiver sees the superposition of non-orthogonal signals from individual sources. (Prefix “H-” means Hierarchical, it emphasizes that the entity is related to the many-to-one principle.) The AH detector decodes the XOR H-map of the two BPSK streams—in other words, it decides whether the transmitted symbols from the two sources are the same or opposite. The BER of the detection in H-MAC is denoted as H-BER. The H-BER is compared with the other two differential detectors, with the coherent (Coh) detector, and with an approximate coherent (ApC) detector. The exact analytical H-BER formula is derived for the ad hoc and coherent detectors. The proposed ad hoc detector is very simple for evaluation, does not require the estimation of subchannel phases, does not depend on noise variance, and it is uniformly only roughly 3.5 dB worse than the coherent one.
MSC:
94A13
1. Introduction
The two-way relay channel (TWRC) with one relay and two BPSK/PSK sources is a well-studied network. In the standard four-phase communication protocol, the first source transmits to the relay, then the relay resends the data to the second source. The same occurs in the opposite direction—the second source sends its data to the relay, and the relay again retransmits its data to the first source. The four-phase protocol can be reduced to the three-phase protocol by the application of network coding [1]—the relay collects data from both sources, computes a network function, and broadcasts the output back to the sources. Each source can then compute the data of the other source. In the most simple case, the relay computes the XOR of the source messages. Wireless networks allow further reduction of the number of phases—a two-phase protocol can be established. Both sources can transmit simultaneously to the relay. There are two main relay strategies: (1) Amplify and Forward (AF)—the relay simply retransmits the signal it receives without decoding anything; (2) Hierarchical Decode and Forward (HDF)—the relay decodes the XOR of the source symbols directly from the non-orthogonal superposition of source signals, and forwards this “XOR frame”. HDF is also called Denoise and Forward by some authors. Network coding applied in wireless networks, specifically on their physical layer, is often called Physical Layer Network Coding (PLNC) or Wireless Physical Layer Network Coding (WPNC). Details on WPNC can be found in the book [2]. The key idea is to let sources transmit at the same frequency and time, and so save communication resources. Even though the relay cannot separate the interfering signals (by linear methods), it can decode the network function—the XOR of source symbols. The critical phase, when sources transmit at the same frequency and time to the relay, is called Hierarchical MAC (H-MAC). Our work focuses on the transmission and detection in H-MAC. The performance of coherent PLNC schemes is critically dependent on precise channel estimation. We use the differential modulation to compensate for the need to know subchannel phases, i.e., to know complete channel state information (CSI) at the relay node. We consider the detector at the relay to be “differential” to emphasize the fact that the sources are differentially encoded, i.e., that it uses two subsequent channel observations.
2. Related Works
The AF relay strategy is mainly analyzed in other works. In [3], Song et al. analyze differential BPSK in TWRC with the AF relay strategy in Rayleigh fading channels. The differential method is only 3 dB worse than the coherent method. The same scenario, but with multiple relays, is analyzed by Song et al. in [4]—again, the differential method is 3 dB worse than the coherent case. In [5], Xu et al. investigate both AF and HDF with differential modulation for TWRC with multiple relays and MIMO systems. Kanthimatchi and Amutha in [6] introduce generalized differential amplitude-phase modulation for TWRC, and the AF relay strategy is assumed.
In [7], Ju and Kim derived tight upper and lower bounds for H-BER, Huang and Yuan in [8] studied the TWRC with multiple antennas, both papers studied coherent detection with the HDF relay strategy. The HDF relay strategy with differential BPSK/PSK is studied in [9] by Guan and Liu. They derived the covariance matrix of the two-point observation where the mean is over subchannel phases and noise. Subsequently, they approximated the joint distribution of the two-point observation by the joint complex normal (JCN) distribution with this covariance matrix. The detector is used with energy harvesting schemes in [10]. The work of Guan and Liu is extended by Fan et al. in [11] to 4 and 8PSK alphabets, a bitwise-XOR H-map, but the error performance is poor. Another approach is used in [12], where the authors used the product of subsequent observations, as an analogy with one-to-one transmission and reception. In [13], Hron and Sykora derived a closed-form detector that does not need the knowledge of subchannel phases. The joint pdf of observation is marginalized by the maximum over subchannel phases (joint maximum likelihood, JML). The performance is only approximately 3 dB worse than the coherent case.
The paper is organized as follows. In Section 3, the system model for both coherent detection and differential detection in H-MAC is given. The ad hoc detector is presented. Moreover, the coherent detector and its high SNR approximation are given. In Section 4, we present analytical formulae for H-BER of the AH detector and coherent detectors, and we compare our differential AH detector with JML from [13] and JCN from [9]. Further, we present other numerical results such as decision regions and H-BER figures. In Section 5, we conclude the paper.
The key contribution of the paper is the proposition of the differential ad hoc (AH) detector of the XOR of source symbols. Sources use differential BPSK (DBPSK) modulation. The AH detector uses two subsequent observations together with the knowledge of the magnitudes of subchannel attenuations, i.e., the minimum of them. The loss of the proposed ad hoc (AH) detector in the error rate is 0.5 dB with regard to the JML and 3.5 dB with regard to the coherent detector. AH is slightly worse than JCN for low SNRs, where H-BER of both detectors is approximately , but AH substantially outperforms JCN for higher SNRs.
3. Materials and Methods
The section starts with stating system models of reception in H-MAC. System models for both uncoded BPSK sources and differentially modulated/encoded BPSK sources are given. For H-MAC with uncoded BPSK sources, we recall the coherent detector (Coh) of the XOR H-map. Additionally, a very good approximation of the Coh detector is given—it is denoted as the approximate coherent (ApC) detector. Further, for H-MAC with differentially modulated BPSK sources, an ad hoc detector of the XOR H-map is derived. It uses two subsequent observations. Finally, a general expression for H-BER is shown.
The system model with uncoded BPSK sources is given as
It is depicted in Figure 1.
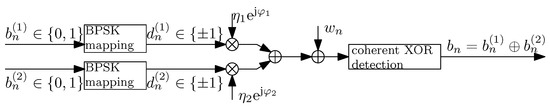
Figure 1.
The system model for coherent detection.
In Equation (1), are uncoded n-th BPSK symbols. and are magnitudes and phases of subchannel attenuations, respectively. Index 1 and 2 indicate the source. is the complex Gaussian noise with mean 0 and variance .
The H-MAC system model for the differentially encoded BPSK (DBPSK) sources is given as
The communication system is illustrated in Figure 2.
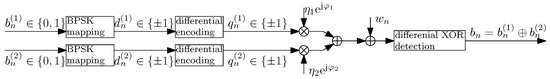
Figure 2.
The system model for differential detection.
Differential BPSK modulation is given as
are uncoded BPSK symbols; are differentially encoded BPSK symbols. Other variables in (2) are the same as in (1).
The ad hoc detector will use two subsequent observations of the H-MAC channel with DBPSK sources. The two-point observation is
In the Equations (4) and (5), we will use the following substitutions:
However, for simplicity of notation, we will omit index in , and obtain
Now, we recall the coherent detector. It uses one observation from H-MAC with uncoded BPSK (1). The channel likelihood function conditioned by the source BPSK symbols and the one conditioned by the H-symbol b is given as
where (for notation simplicity, we have omitted lower time-index n) the useful signal u is
We recall that the H-symbol b is the output of the H-map. In our case, . The coherent detector of the XOR H-map is derived from the likelihood test
We obtain the coherent detector of the form
In the Equation (15), . In addition, is the estimated H-symbol.
For the derivation of the approximate coherent detector, we use the following substitutions:
The derivation follows.
We obtain criterion (19) from (18) by applying to both sides of (18). In the expressions (18) and (19),
Finally, after resubstitution (16) and (17) to the (19), we obtain the approximate detector of the form
The approximation is based on the omission of the expression from (19). It is close to zero for higher SNR.
Now, we derive an ad hoc differential detector. Assume the H-MAC channel with DBPSK sources, given by the channel model (2). In the derivation of the ad hoc detector, we take the two-point observation (8), and assume a no-noise case. Thus, , . We define two auxiliary sets, and . The sets are composed to correspond to H-symbols and , respectively. The detector has to decide whether or . It will choose the set ( or , i.e., the H-symbol or ) to which is closer. We use the Euclidean distance. The distance to the can be computed directly, because , and is known. Thus, the detector metric is
The decision threshold is selected to be the mid-value between the case , i.e., , and the case , i.e., , as can be seen from Table 1.

Table 1.
Values of and for all tuples of .
Thus,
In the criterion (25), we will use the shortcut .
To gain insight into what other differential detectors look like, we will proceed as in [13]. The parts of two-point observation are independent complex Gaussian distributed given , , , , , . We assign , . Single and joint likelihood of observations is, respectively,
The joint pdf (Probability Density Function) of the two-point observation given H-symbol (Hierarchical symbol) b is
The detector decides according to the ML (maximum likelihood) criterion
The criterion (31) can be simplified to the form
where and . Upper index means a complex conjugate. We can marginalize the (32) criterion by taking the maximum over , as was done in [13], or by integration. However, in all types of marginalization over phases , the resulting detector should be a function of the sum and the difference of subsequent observations. This is also true of our ad hoc case.
H-BER Formula Derivation
In this subsection, we derive a general expression for the H-BER of a detector of the XOR H-map of two BPSK sources. The detector metric will be called M—it is a function of observation(s). Denote by a the decision threshold. We assume the detector to be of the form
Next, the probability of the symbol error Pe = H-BER is derived.
where is the pdf (Probability Density Function) of M, given event . The events are defined in Table 1.
4. Results
In this section, we first show the derived H-BER formulae. The key is to derive the pdf of the detector metric, which is then submitted to Equation (34). Channel observations are taken as random variables (RVs) and detector metrics are functions of observations—functions of RVs. We use standard procedures from the book [14] to derive the pdf of the transformed RVs. Subsequently, we show H-BER of detectors in figures. Details of the derivation can be found in Appendix B. Gaussian RVs (random variables) are recalled in Appendix A. Other supplementary operations with RVs are in Appendix C.
4.1. Analytical H-BER Formula for Ad Hoc (AH) Differential Detector
can be derived to be
where and is the pdf and cdf (Cumulative Density Function) of Rice distribution, respectively,
In the expression (36), , . Then,
where is the Marcum Q-function and
Again, we have used .
4.2. Analytical H-BER Formula for Coherent Detector (Coh)
To express (pdf of M given in (14)) it is useful to define some auxiliary variables. The detector’s decision-threshold is
Define (complex valued constant)
Let a joint probability , be
In Equations (43) and (44),
and is the Dirac-delta function. Let the joint probability , be
Finally,
In (48), we can use the substitution (50). The 2D integral is then more numerically stable.
4.3. Analytical H-BER Formula for Approximate Coherent (ApC) Detector
4.4. Comparison of AH Differential Detector with Other Two Differential Detectors
In this subsection, we compare the H-BER performance of the ad hoc (AH) detector with the joint complex normal (JCN) detector from [9] and with the joint maximum likelihood (JML) detector from [13]. In the referenced figures, we use and . In Figure 3, we see the H-BER of the AH and the JCN detector. The right-hand figure zooms into the lower SNRs. It is clearly visible that for low SNRs, JCN is slightly better than AH (the error rate is of order for both detectors), but for high SNRs, AH is remarkably better. In Figure 4, we compare H-BER of the AH and JML detector. Again, the right-hand figure zooms into lower SNRs. Apparently, the loss of AH w.r.t. the JML is about 0.5 dB in H-BER.
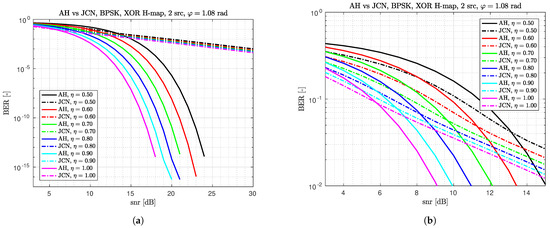
Figure 3.
H-BER of ad hoc (AH) vs. JCN detector for different ranges of SNR. (a) Ad hoc (AH) vs. JCN detector for SNR from 3 dB to 30 dB. (b) Ad hoc (AH) vs. JCN detector for SNR from 3 dB to 15 dB.
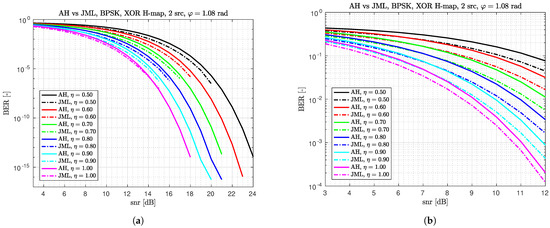
Figure 4.
H-BER of ad hoc (AH) vs. JML detector for different ranges of SNR. (a) Ad hoc (AH) vs. JML detector for SNR from 3 dB to 24 dB. (b) Ad hoc (AH) vs. JML detector for SNR from 3 dB to 12 dB.
4.5. Other Numerical Results
In this subsection, we present the following.
- 1.
- Decision regions for coherent and differential detectors.
- 2.
- Comparison of H-BER performance of coherent vs. approximate coherent detector and coherent vs. ad hoc detector.
- 3.
- H-BER performance of the ad hoc differential detector vs. the approximate coherent detector for the Rayleigh channel.
In all the figures, , , . SNR is given with regard to the first source. Rayleigh fading channel is of the form
where . is chosen to be so that E. Moreover, the channel attenuation coefficients , are assumed to be the same for two consecutive observations. The channel parameter is fixed for the whole frame and it is the only parameter known to the AH detector in the channel model (57).
Observations follow. In Figure 5a, we see that the boundaries of decision regions of the coherent and the approximate coherent detector for SNR = 0 dB are quite close to each other. For higher SNR, boundaries are closer to each other. That results in practically the same H-BER performance of the two detectors as can be seen in Figure 6a. We can notice that the boundaries of decision regions for the approximate coherent detector consist of 4 line segments.
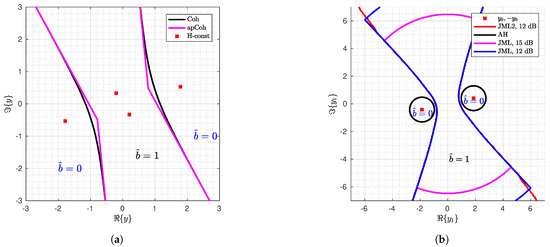
Figure 5.
Decision regions of the coherent (a) and differential detectors (b). (a) Decision regions for coherent and approximate coherent detector. For SNR = 0 dB. , rad, rad. (b) Decision regions for the differential ad hoc detector, JML detector (for two SNRs) and JML2 detector. Decision regions on for given . For .
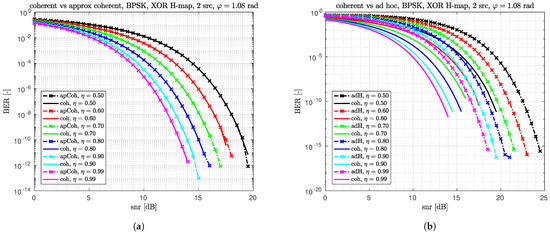
Figure 6.
H-BER of the coherent (coh) vs. the approximate coherent (apCoh) detector (a) and the coherent vs. ad hoc (adH) detector (b). (a) H-BER of coherent vs. the approximate coherent detector. (b) H-BER of coherent vs. ad hoc differential detector.
Decision regions for the ad hoc differential detector are 4-D subsets of . In Figure 5b, we have depicted decision regions for , given fixed . Decision regions of the JML detector are also shown. Here we have also shown the decision region for the detector that we get by marginalization of the criterion (32) by integration over . The differential detector is denoted as JML2.
From Figure 6b, we conclude that the H-BER loss of the ad hoc detector w.r.t. the Coh detector is about 3.5 dB.
In Figure 7, we compare the ApC and AH detector for the Rayleigh channel. The AH detector knows only the channel parameter , as given in the system model (57). We see that the knowledge of the magnitudes of subchannel attenuations for the AH detector is crucial and its absence results in very poor error performance. The ApC detector uses full knowledge of the channel parameters and .
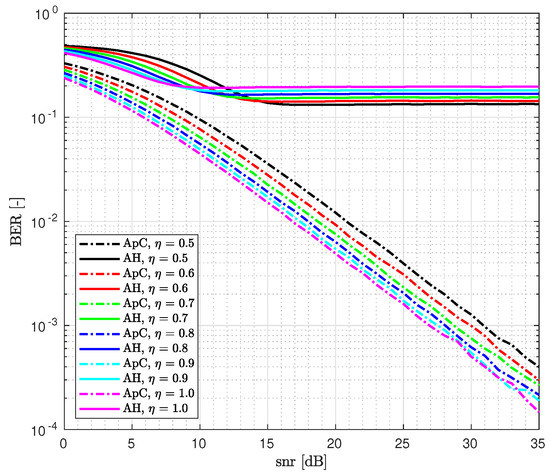
Figure 7.
H-BER of AH differential detector vs. ApC detector in Rayleigh fading channel.
5. Discussion
In this article, we have presented an AH differential detector of the XOR H-map, for two differentially encoded BPSK sources in the H-MAC. The proposed AH detector is very simple for evaluation, does not require the estimation of subchannel phases in the H-MAC channel, and the loss in its H-BER is only 3.5 dB with regard to the coherent detector. Moreover, we have derived the ApC detector, which has practically the same H-BER performance as the Coh detector. The analytical H-BER formula has been presented for the AH and coherent detectors. The AH differential detector has been compared to the other two differential detectors (JML and JCN). Additional results such as figures of H-BER and decision regions of detectors have been presented.
Author Contributions
Conceptualization, J.L. and J.S.; methodology, J.L.; software, J.L.; validation, J.L. and J.S.; formal analysis, J.S.; investigation, J.S.; resources, J.L.; data curation, J.L.; writing—original draft preparation, J.L.; writing—review and editing, J.S.; visualization, J.L.; supervision, J.S.; project administration, J.S.; funding acquisition, J.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Czech Technical University in Prague, grant number SGS21/062/OHK3/1T/13.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Matlab functions for computation of H-BER of detectors can be accessed at https://doi.org/10.17632/dn8cgnkfny.1 (accessed on 13 January 2022).
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| TWRC | Two-Way Relay Channel |
| BPSK | Binary Phase Shift Keying |
| HDF | Hierarchical Decode and Forward |
| AF | Amplify and Forward |
| PLNC/WPNC | (Wireless) Physical Layer Network Coding |
| H-MAC | Hierarchical Multiple Access Channel |
| H-BER | Hierarchical Bit Error Rate |
| CSI | Channel State Information |
| DBPSK | Differential BPSK |
| SNR | Signal to Noise Ratio |
| Probability Density Function | |
| cdf | Cumulative Density Function |
| JML | Joint Maximum Likelihood detector, maximum marginalized, from [13] |
| JML2 | Joint Maximum Likelihood detector, marginalized by integration |
| JCN | Joint Complex-Normal differential detector from [9] |
| AH/AdH | Ad Hoc Differential Detector |
| Coh | Coherent Detector |
| ApC | Approximate Coherent Detector |
| RV | Random Variable |
Appendix A. Complex Normal and Normal Distributions
Let
Then (p denotes pdf)
Some operations with complex normal and normal random variables follow:
Appendix B. Derivation of pdf of Detector Metrics
Appendix B.1. AH Differential Detector
The derivation of p follows
In the above relations, means
is the Marcum Q-function. Further,
We derive p as given in (35) using Appendix C.4.
Appendix B.2. Coherent Detector
The derivation of pCoh follows. ( are BPSK symbols, so ).
RVs and are dependent. . Constant c is defined in (42). Thus, the joint distribution of is
We obtain joint distributions of U and V by marginalization of (A21) over imaginary parts of . Here, we need to distinguish two cases: (1) and (2) . Derived is given in (43) and (44). We obtain the joint distribution of and subsequently from by applying the derivation in Appendix C.1.
Appendix B.3. Approximate Coherent Detector
Derivation of follows.
Similarly as in the coherent case, and are dependent. We define c as in (42). Then, the joint distribution of and is
The joint distribution of is computed by the marginalization of over the imaginary parts of variables x, y. is computed according to Appendix C.2. Finally, we find according to Appendix C.3.
Appendix C. Operations with Random Variables
Appendix C.1. Joint Distribution of cosh(U), cosh(V) and Their Ratio Distribution
For two RVs , the ratio distribution is given as
For given and the transformation , , we want . The Jacobian of the transformation is
For given , the solutions of , are and . For all pairs of solutions, the absolute value of the Jacobian is equal to . Thus,
For the ratio , we need to place a condition on the integration variable,
Thus,
Appendix C.2. Joint Distribution of Absolute Values of U, V
Let
The Jacobian of the transformation is
For the given , solutions of , are , . The absolute value of the Jacobian for all pairs of solutions is 1. Thus,
Appendix C.3. Difference of Two Nonnegative RVs
Let
Then
For nonnegative , we restrict to
Appendix C.4. Minimum of Two Independent RVs
Let be two independent random variables. Define . Then
References
- Ahlswede, R.; Cai, N.; Li, S.Y.R.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Sykora, J.; Burr, A. Wireless Physical Layer Network Coding; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar] [CrossRef]
- Song, L.; Li, Y.; Huang, A.; Jiao, B.; Vasilakos, A.V. Differential modulation for bidirectional relaying with analog network coding. IEEE Trans. Signal Process. 2010, 58, 3933–3938. [Google Scholar] [CrossRef]
- Song, L.; Hong, G.; Jiao, B.; Debbah, M. Joint relay selection and analog network coding using differential modulation in two-way relay channels. IEEE Trans. Veh. Technol. 2010, 59, 2932–2939. [Google Scholar] [CrossRef]
- Xu, W.; Wang, Q.; Lin, M. Distributed space-time coding scheme with differential detection and power allocation for cooperative relay network. Telecommun. Syst. 2017, 66, 431–445. [Google Scholar] [CrossRef]
- Kanthimathi, M.; Amutha, R. Performance analysis of generalized differential modulation using DAPSK for bi-directional relay networks. In Proceedings of the 2017 2nd International Conference on Computing and Communications Technologies, ICCCT 2017, Chennai, India, 23–24 February 2017; Institute of Electrical and Electronics Engineers Inc.: Chennai, India, 2017; pp. 33–36. [Google Scholar] [CrossRef]
- Ju, M.; Kim, I.M. Error Performance Analysis of BPSK Modulation in Physical-Layer Network-Coded Bidirectional Relay Networks. IEEE Trans. Commun. 2010, 58, 2770–2775. [Google Scholar] [CrossRef]
- Huang, M.; Yuan, J. Error performance of physical-layer network coding in multiple-antenna TWRC. IEEE Trans. Veh. Technol. 2014, 63, 3750–3761. [Google Scholar] [CrossRef]
- Guan, W.; Liu, K.J. Performance analysis of two-way relaying with non-coherent differential modulation. IEEE Trans. Wirel. Commun. 2011, 10, 2004–2014. [Google Scholar] [CrossRef]
- Xu, W.; Yang, Z.; Ding, Z.; Wang, L.; Fan, P. Wireless information and power transfer in two-way relaying network with non-coherent differential modulation. Eurasip J. Wirel. Commun. Netw. 2015, 2015, 131. [Google Scholar] [CrossRef][Green Version]
- Fan, J.; Li, L.; Bao, T.; Zhang, H. Two-way relaying with non-coherent differential MPSK modulation. In Proceedings of the 2015 IEEE International Conference on Signal Processing, Communications and Computing, ICSPCC 2015, Ningbo, China, 19–22 September 2015; Institute of Electrical and Electronics Engineers Inc.: Ningbo, China, 2015. [Google Scholar] [CrossRef]
- Zhu, K.; Burr, A.G. Two-way non-coherent Physical-Layer Network Coded differential distributed space-time block coding. In Proceedings of the IEEE Wireless Communications and Networking Conference, WCNC, Shanghai, China, 7–10 April 2013; pp. 2416–2421. [Google Scholar] [CrossRef]
- Hron, P.; Sykora, J. Closed-Form Differential Hierarchical Demodulator of 2-source Hierarchical-MAC Channel. IEEE Commun. Lett. 2021, 25, 3704–3708. [Google Scholar] [CrossRef]
- Papoulis, A. Probability & Statistics; Prentice Hall: Englewood Cliffs, NJ, USA, 1990; p. 454. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).