Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking
Abstract
1. Introduction
- (1)
- A robust zero-watermarking algorithm for oblique-photography 3D models is proposed, leveraging the vertical skewness of oblique 3D models to construct zero-watermark information. This approach ensures data integrity while significantly enhancing robustness against geometric attacks, providing a reliable mechanism for copyright protection and secure transactions involving high-precision 3D models.
- (2)
- A blockchain-based trusted-transaction scheme is introduced, utilizing smart contracts to automate key processes such as identity verification and transaction record storage. By ensuring the legitimacy of transactions and preventing data tampering or duplication, this scheme enhances the efficiency and transparency of transaction management while safeguarding data security and the credibility of all parties involved.
2. Basic Ideas and Preliminaries
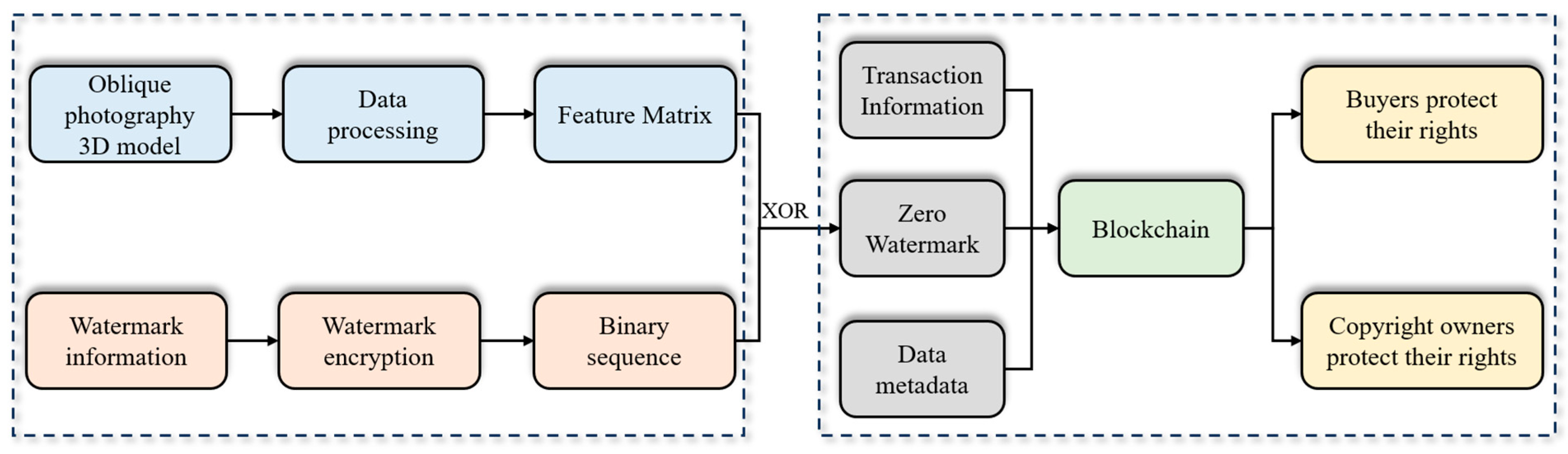
2.1. Basic Ideas
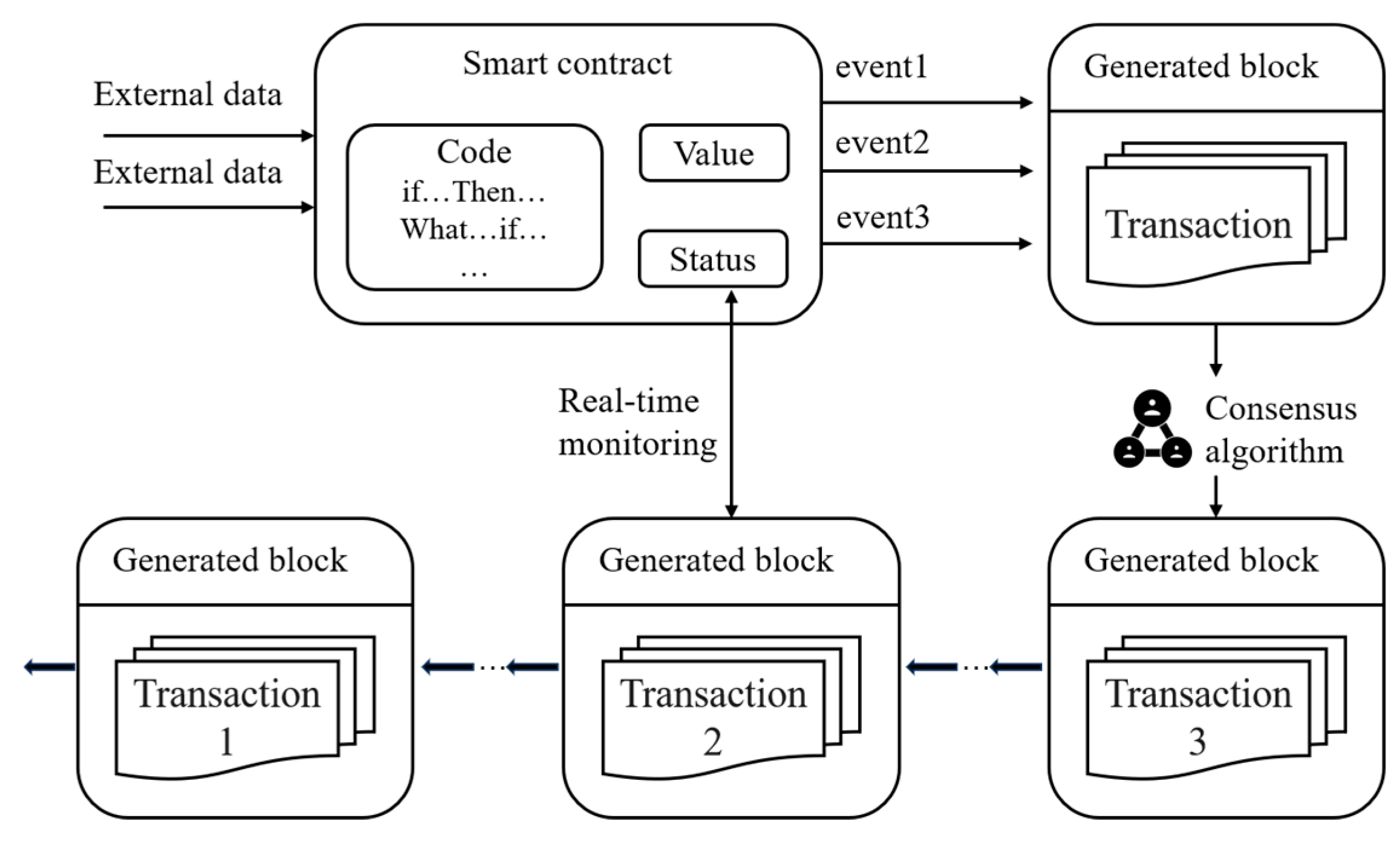
2.2. Smart Contract
2.3. IPFS
2.4. Skewness Measure
3. Proposed Method
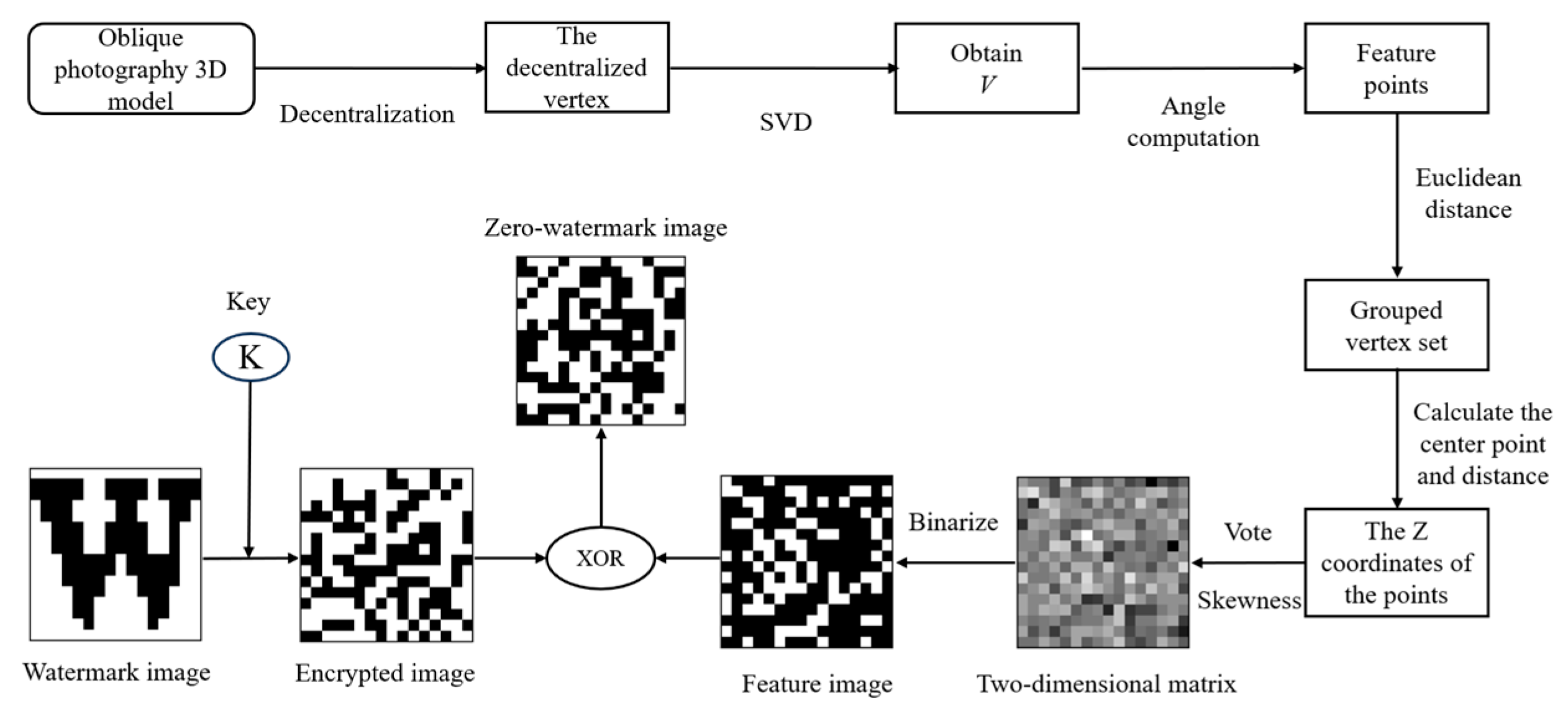
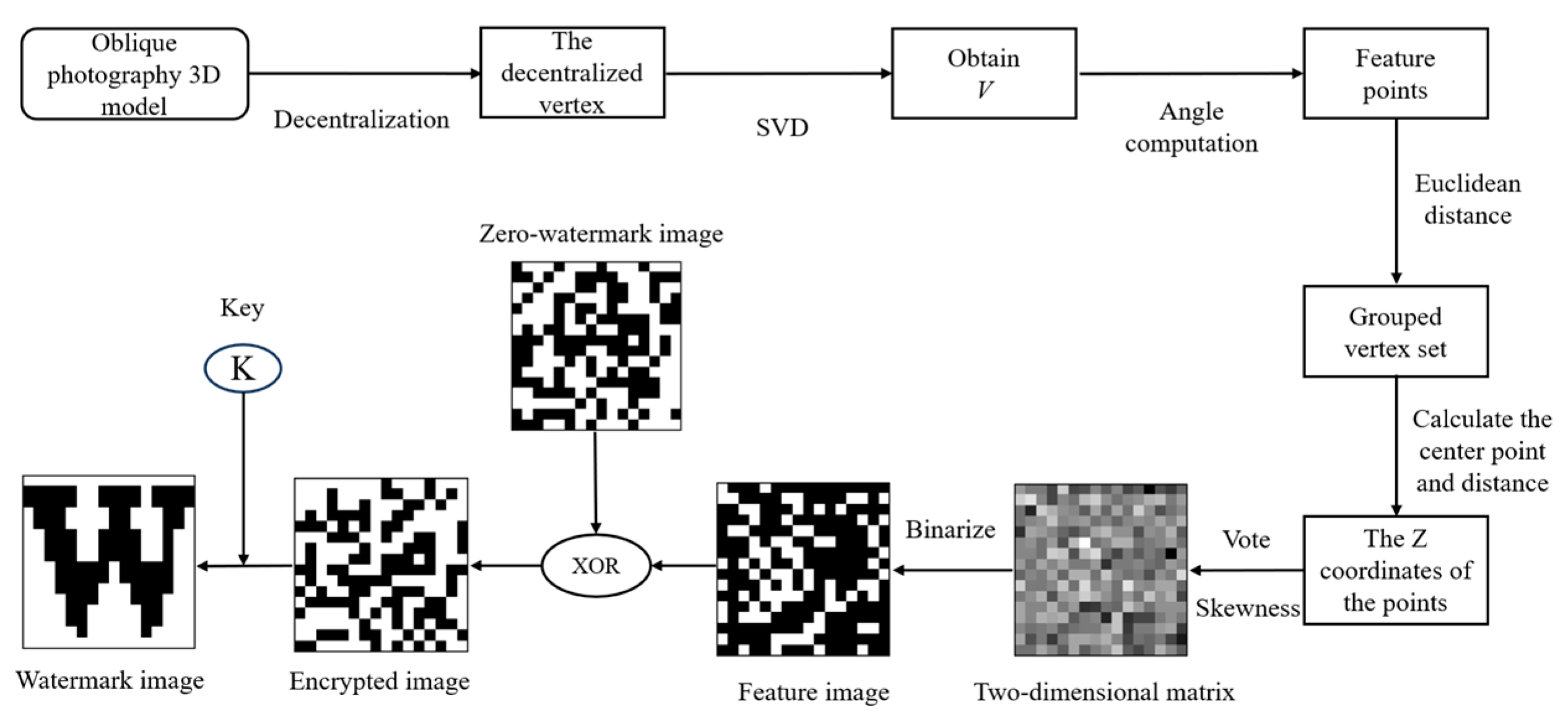
3.1. Zero-Watermark Method
3.1.1. Data Process
- (1)
- Feature point extraction
- (2)
- Grouping of vertices
- (3)
- Vertex Selection
3.1.2. Generation Process of Zero Watermark
3.1.3. Zero-Watermark Detection Process
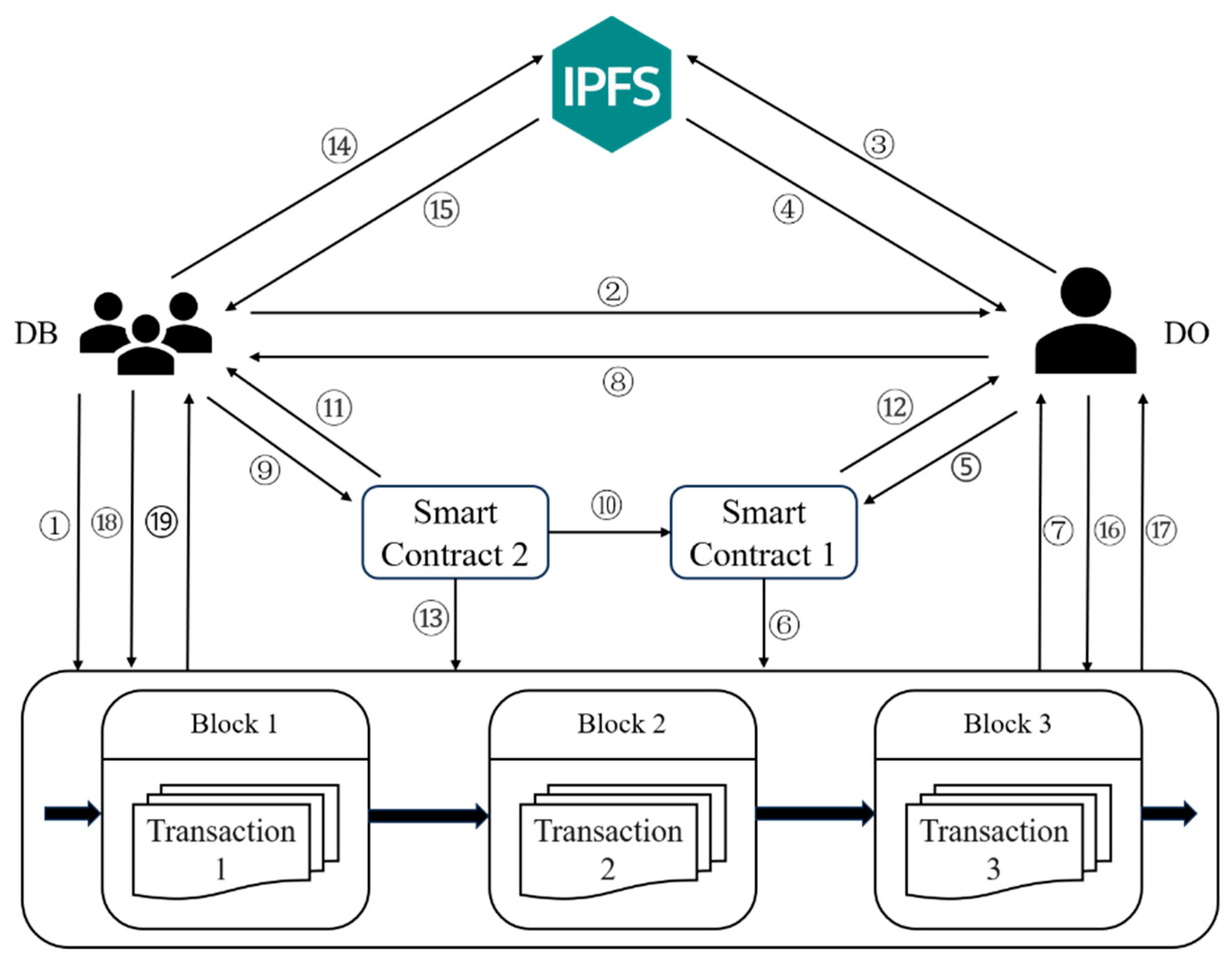
3.2. Trusted-Transaction Scheme
3.2.1. Smart-Contract Platform Selection
3.2.2. Smart-Contract Design
- (1)
- owner: An Ethereum account address representing the copyright owner’s address.
- (2)
- dataIpfsAddress: The storage address of the encrypted data on the IPFS network.
- (3)
- watermarkIpfsAddress: The storage address of the zero-watermark identifier on IPFS.
- (4)
- MerkleTree: By calculating the Merkle tree root after dividing the data into blocks, this structure enables detection of the approximate location of any tampering and ensures data integrity [30].
- (5)
- dataId: The hash value of the data, generated using Hash256. This value is stored on the blockchain as the unique identifier of the data, preventing the upload of duplicate or identical data and ensuring its uniqueness [31].
- (6)
- Conditions: The transaction fee set by the copyright owner for accessing or using the data.
| Contract 1: Oblique photography 3D model information notarization contract |
| Input: string dataIpfsAddress, MerkleTree, watermarkIpfsAddres, dataId, conditions; Output: address of CopyrightDeposit; Contract CopyrightDeposit{ address public owner; string dataIpfsAddress, MerkleTree, watermarkIpfsAddres, dataId, conditions; struct ContractOwner{ string organization, name; } mapping(address => ContractOwner) public contractOwners; address constant ALLOWED_DEPLOYER =“address”; …… function setDataMessage(string memory _dataIpfsAddress, string memory _watermarkIpfsAddress, string memory _dataId, string memory _MerkleTree) public returns (address) { require(bytes(contractowner[msg.sender].name).length != 0 && bytes(contractOwners[msg.sender].tissue).length != 0, “Please execute Owner_message first to set your details.”); require(owner==msg.sender, “You do not have access.”); dataIpfsAddress = _dataIpfsAddress; watermarkIpfsAddress = _watermarkIpfsAddress; MerkleTree = _MerkleTree; dataId = _dataId; owner = msg.sender; return owner; } |
- (1)
- User: A structure type used to store the basic information of the buyer.
- (2)
- userAddress: Stores the Ethereum address of the current buyer, which is used for identity verification during subsequent transactions. Only authorized users are allowed to conduct transactions.
- (3)
- receiver: Stores the recipient’s address for the contract, enabling the withdrawal of the transaction amount after the transaction is completed.
- (4)
- copyrightDepositContract: An instantiation of the Contract 1 contract within Contract 2. This variable facilitates interaction between the two contracts, allowing access to the stored data information.
| Contract 2: Data transaction information contract |
| Input: address of CopyrightDeposit, conditions; Output: dataIpfsAddress, MerkleTree, watermarkIpfsAddres, dataId; Contract DataTransaction { address public userAddress, receiver; CopyrightDeposit public copyrightDepositContract; struct User { string organization, name; } …… function tip () public payable { require (msg.value >= conditions, “you should send to use this function”); require (userAddress == msg.sender, “You do not have permission”); } function getDataAddresses () public view returns(string memory dataIpfsAddress, string memory MerkleTree, string memory dataId, string memory watermarkIpfsAddress) { require(userAddress==msg.sender, “You don’t have permission.”); return(copyrightDepositContract.dataIpfsAddress(), copyrightDeposit Contract.MerkleTree(), copyrightDepositContract.dataId(), copyright DepositContract.watermarkIpfsAddress()); } |
3.3. Trusted-Transaction Attestation System Architecture
4. Experiments and Analysis
4.1. Copyright Protection Experiment and Analysis
4.1.1. Experimental Data and Parameter Settings
4.1.2. Uniqueness Analysis
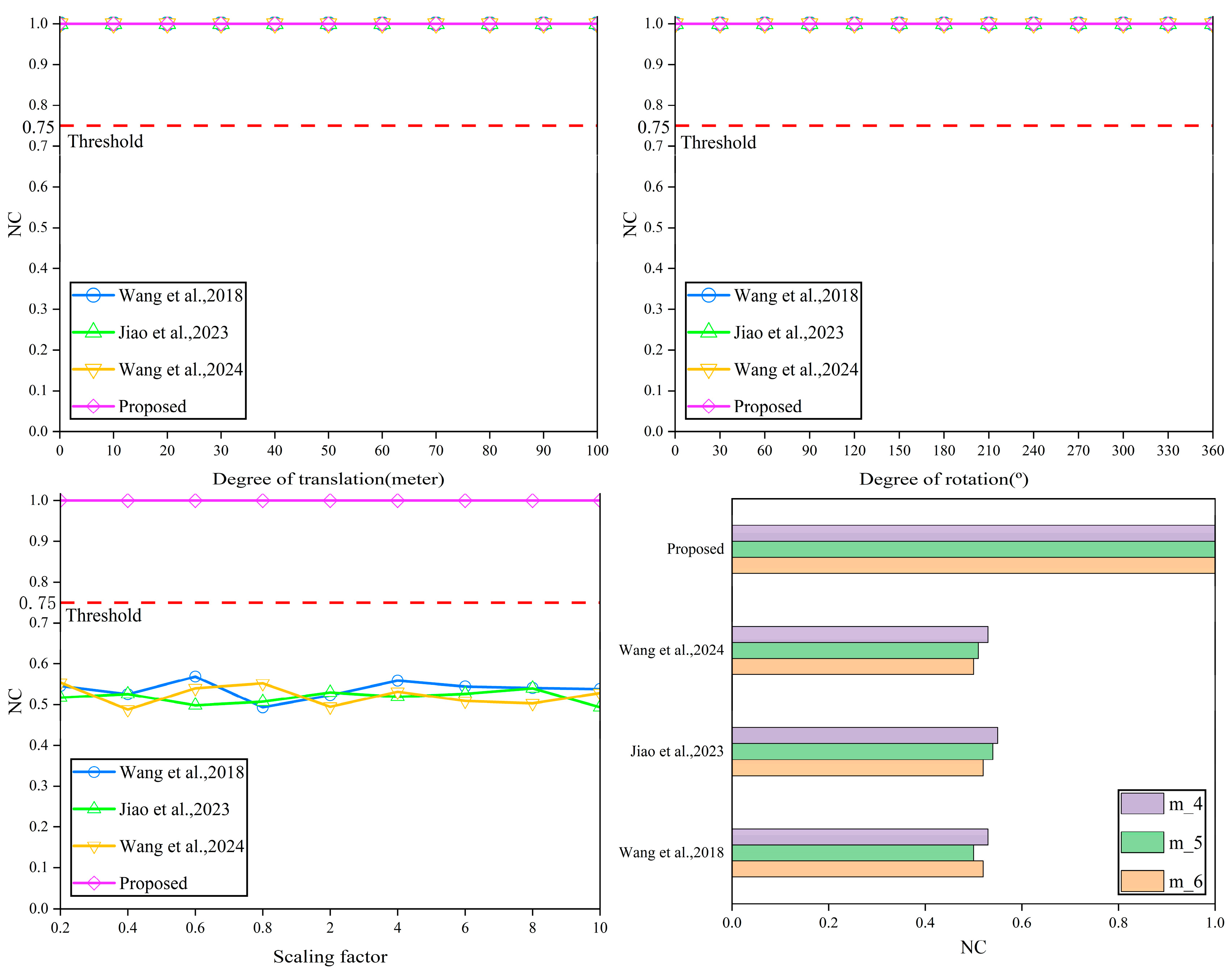
4.1.3. Robustness Analysis
- (1)
- Geometry attacks
- (2)
- Cropping attack
- (3)
- Simplified attack
- (4)
- Reordering attack
4.1.4. Efficiency Assessment
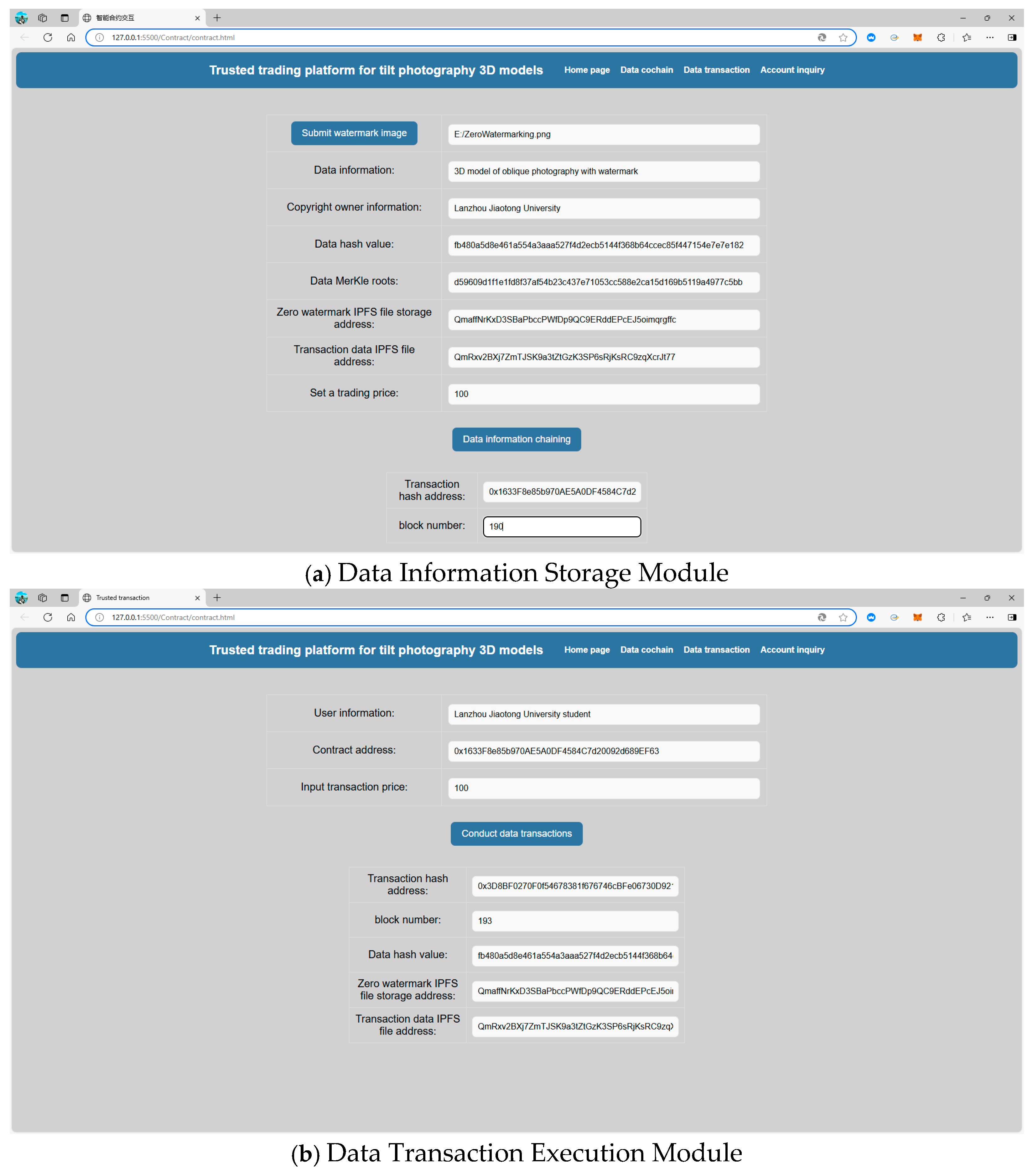
4.2. Trusted-Transaction Experiment and Results
4.2.1. System Implementation
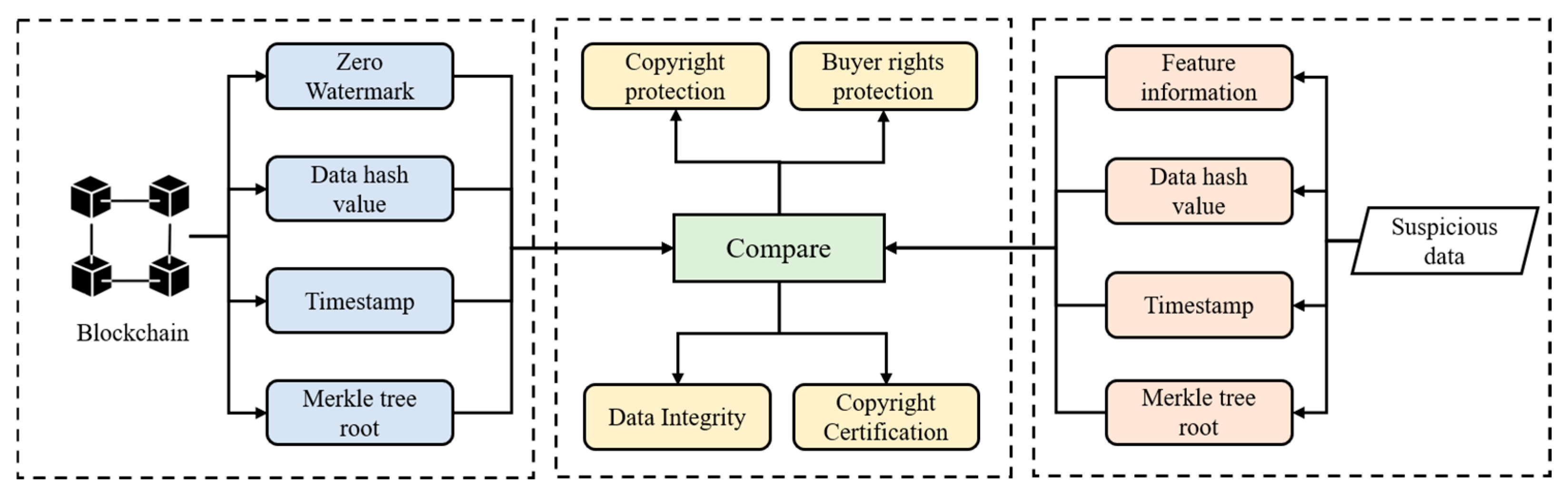
4.2.2. Security and Credibility Analysis
4.2.3. Rights Protection for Both Parties to the Transaction
4.2.4. Smart-Contract Execution Costs
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lin, M.; Li, F.-Y.; Zhou, H. A Research on the Combination of Oblique Photography and Mobile Applications Based on the Sustainable Development of Tourism. Sustainability 2020, 12, 3501. [Google Scholar] [CrossRef]
- Chen, J.; Liu, J.; Tian, H. Basic Directions and Technological Path for Building 3D Realistic Geospatial Scene in China. Geomat. Inf. Sci. Wuhan Univ. 2022, 47, 1568–1575. [Google Scholar] [CrossRef]
- Svennevig, K.; Guarnieri, P.; Stemmerik, L. From oblique photogrammetry to a 3D model-Structural modeling of Kilen, eastern North Greenland. Comput. Geosci. 2015, 83, 120–126. [Google Scholar] [CrossRef]
- Wang, J.; Wu, D.; Li, L.; Zhao, J.; Wu, H.; Tang, Y. Robust periodic blind watermarking based on sub-block mapping and block encryption. Expert Syst. Appl. 2023, 224, 119981. [Google Scholar] [CrossRef]
- Wang, P.; Zhang, L.; Wang, S.; Zhang, Z.; Zhang, Q. Reversible Watermarking Algorithm for Oblique Photogrammetry 3D Models with Controllable Accuracy. Geogr. Geo-Inf. Sci. 2024, 40, 1–7. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, C.; Wang, C.; Ma, B.; Li, Q.; Wang, M.; Zhao, T. A robust zero-watermarking algorithm for lossless copyright protection of medical images. Appl. Intell. 2022, 52, 607–621. [Google Scholar] [CrossRef]
- Jiang, Y.; Sun, G.; Feng, T. Research on Data Transaction Security Based on Blockchain. Information 2022, 13, 532. [Google Scholar] [CrossRef]
- Ying, S.; Van Oosterom, P.; Fan, H. New Techniques and Methods for Modelling, Visualization, and Analysis of a 3D City. J. Geovisualization Spat. Anal. 2023, 7, 26. [Google Scholar] [CrossRef]
- Lin, Z.; Peng, X.; Li, Z.; Liang, F.; Li, A. Towards Metaverse Manufacturing: A Blockchain-based Trusted Collaborative Governance System. In Proceedings of the 2022 4th International Conference on Blockchain Technology, Shanghai, China, 25–27 March 2022; pp. 171–177. [Google Scholar] [CrossRef]
- Zhang, L.; Luo, M.; Li, J.; Au, M.H.; Choo, K.-K.R.; Chen, T.; Tian, S. Blockchain based secure data sharing system for Internet of vehicles: A position paper. Veh. Commun. 2019, 16, 85–93. [Google Scholar] [CrossRef]
- Su, G.; Yang, W.; Luo, Z.; Zhang, Y.; Bai, Z.; Zhu, Y. BDTF: A Blockchain-Based Data Trading Framework with Trusted Execution Environment. In Proceedings of the 2020 16th International Conference on Mobility, Sensing and Networking, Tokyo, Japan, 17–19 December 2020; pp. 92–97. [Google Scholar] [CrossRef]
- Cheng, X.; Chen, F.; Xie, D.; Sun, H.; Huang, C. Design of a Secure Medical Data Sharing Scheme Based on Blockchain. J. Med. Syst. 2020, 44, 52. [Google Scholar] [CrossRef]
- Yang, M.; Zhu, T.; Liang, K.; Zhou, W.; Deng, R.H. A blockchain-based location privacy-preserving crowdsensing system. Future Gener. Comput. Syst. 2019, 94, 408–418. [Google Scholar] [CrossRef]
- Pincheira, M.; Donini, E.; Giaffreda, R.; Vecchio, M. A Blockchain-Based Approach to Enable Remote Sensing Trusted Data. In Proceedings of the 2020 IEEE Latin American GRSS & ISPRS Remote Sensing Conference, Santiago, Chile, 22–26 March 2020; pp. 652–657. [Google Scholar] [CrossRef]
- Xu, D.; Ren, N.; Zhu, C. High-Resolution Remote Sensing Image Zero-Watermarking Algorithm Based on Blockchain and SDAE. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2024, 17, 323–339. [Google Scholar] [CrossRef]
- Wang, B.; Jiawei, S.; Wang, W.; Zhao, P. Image Copyright Protection Based on Blockchain and Zero-Watermark. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2188–2199. [Google Scholar] [CrossRef]
- Xiang, Y.; Ren, W.; Li, T.; Zheng, X.; Zhu, T.; Choo, K.-K.R. A multi-type and decentralized data transaction scheme based on smart contracts and digital watermarks. J. Netw. Comput. Appl. 2021, 176, 102953. [Google Scholar] [CrossRef]
- Ren, N.; Wang, H.; Chen, Z.; Zhu, C.; Gu, J. A Multilevel Digital Watermarking Protocol for Vector Geographic Data Based on Blockchain. J. Geovisualization Spat. Anal. 2023, 7, 31. [Google Scholar] [CrossRef]
- Zhu, C.; Xu, D.; Ren, N.; Cui, H.; Zhao, Y. Geographic data transaction notarization and copyright protection model based on blockchain and digital watermark. Acta Geod. Et Cartogr. Sin. 2021, 50, 1694–1704. [Google Scholar] [CrossRef]
- Lee, J.S.; Chen, Y.C.; Chew, C.J.; Hung, W.C.; Fan, Y.Y.; Li, B. Constructing gene features for robust 3D mesh zero-watermarking. J. Inf. Secur. Appl. 2023, 73, 103414. [Google Scholar] [CrossRef]
- Yadav, A.S.; Agrawal, S.; Kushwaha, D.S. Distributed Ledger Technology-based land transaction system with trusted nodes consensus mechanism. J. King Saud Univ.-Comput. Inf. Sci. 2021, 34, 6414–6424. [Google Scholar] [CrossRef]
- Lu, Z.; Wei, J.; Li, C.; Zhai, J.; Tong, D. Robust copyright tracing and trusted transactions using zero-watermarking and blockchain. Multimed. Tools Appl. 2024, 84, 10687–10724. [Google Scholar] [CrossRef]
- Tan, T.M.; Saraniemi, S. Trust in blockchain-enabled exchanges: Future directions in blockchain marketing. J. Acad. Mark. Sci. 2023, 51, 914–939. [Google Scholar] [CrossRef]
- Ren, N.; Zhao, Y.; Zhu, C.; Zhou, Q.; Xu, D. Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps. ISPRS Int. J. Geo-Inf. 2021, 10, 294. [Google Scholar] [CrossRef]
- Lee, J.-S.; Liu, C.; Chen, Y.-C.; Hung, W.-C.; Li, B. Robust 3D mesh zero-watermarking based on spherical coordinate and Skewness measurement. Multimed. Tools Appl. 2021, 80, 25757–25772. [Google Scholar] [CrossRef]
- Wang, G.; Ren, N.; Zhu, C.; Jing, M. Digital Watermarking Algorithm for 3D Models from Oblique Photogrammetry. J. Geo-Inf. Sci. 2018, 20, 738–743. [Google Scholar] [CrossRef]
- Qiu, Y.; Gu, H.; Sun, J.; Duan, H.; Luo, J. Rich-information watermarking scheme for 3D models of oblique photography. Multimed. Tools Appl. 2019, 78, 31365–31386. [Google Scholar] [CrossRef]
- Ren, N.; Guo, S.; Zhu, C.; Hu, Y. A zero-watermarking scheme based on spatial topological relations for vector dataset. Expert Syst. Appl. 2023, 226, 120217. [Google Scholar] [CrossRef]
- Khandelwal, P.; Johari, R.; Gaur, V.; Vashisth, D. Blockchain Technology based Smart Contract Agreement on REMIX IDE. In Proceedings of the 2021 8th International Conference on Signal Processing and Integrated Networks, Noida, India, 26–27 August 2021; pp. 938–942. [Google Scholar] [CrossRef]
- Castellon, C.; Roy, S.; Kreidl, P.; Dutta, A.; Bölöni, L. Energy Efficient Merkle Trees for Blockchains. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications, Shenyang, China, 20–22 October 2021; pp. 1093–1099. [Google Scholar] [CrossRef]
- Gao, S.; Wu, R.; Wang, X.; Wang, J.; Li, Q.; Wang, C.; Tang, X. A 3D model encryption scheme based on a cascaded chaotic system. Signal Process. 2022, 202, 108745. [Google Scholar] [CrossRef]
- Gong, W.; Zhu, C.; Cui, H.; Ren, N. Digital Watermarking Algorithm for 3D Models from Oblique Photogrammetry Based on Feature Line Ratio. Sci. Surv. Mapp. 2022, 47, 80–86. [Google Scholar] [CrossRef]
- Jiao, Y.; Ma, C.; Luo, J.; Qiu, Y. Security Protection of 3D Models of Oblique Photography by Digital Watermarking and Data Encryption. Appl. Sci. 2023, 13, 13088. [Google Scholar] [CrossRef]


| Model | m_1 | m_2 | m_3 | m_4 | m_5 | m_6 |
|---|---|---|---|---|---|---|
| m_1 | 1 | 0.6038 | 0.5968 | 0.6044 | 0.6062 | 0.5790 |
| m_2 | 0.6038 | 1 | 0.6045 | 0.6206 | 0.6128 | 0.5963 |
| m_3 | 0.5968 | 0.6045 | 1 | 0.6110 | 0.5965 | 0.6046 |
| m_4 | 0.6044 | 0.6206 | 0.6110 | 1 | 0.5921 | 0.5829 |
| m_5 | 0.6062 | 0.6128 | 0.5965 | 0.5921 | 1 | 0.6023 |
| m_6 | 0.5790 | 0.5963 | 0.6046 | 0.5829 | 0.6023 | 1 |
| Cutting Strength | NC | |||
|---|---|---|---|---|
| Proposed | [26] | [33] | [5] | |
| 5% | 0.9823 | 0.9972 | 0.9993 | 0.9917 |
| 15% | 0.9265 | 0.9509 | 0.9814 | 0.9628 |
| 25% | 0.8321 | 0.9272 | 0.9460 | 0.9204 |
| Simplified Strength | NC | |||
|---|---|---|---|---|
| Proposed | [26] | [33] | [5] | |
| 5% | 0.9371 | 0.9043 | 0.7563 | 0.9812 |
| 15% | 0.8203 | 0.7567 | 0.5483 | 0.9640 |
| 25% | 0.7519 | 0.5312 | 0.5249 | 0.9162 |
| Model | Proposed | [26] | [33] | [5] |
|---|---|---|---|---|
| m_1 | 1.0000 | 1.0000 | 1.0000 | 0.7382 |
| m_2 | 1.0000 | 1.0000 | 1.0000 | 0.7132 |
| m_3 | 1.0000 | 1.0000 | 1.0000 | 0.6890 |
| m_4 | 1.0000 | 1.0000 | 1.0000 | 0.7804 |
| m_5 | 1.0000 | 1.0000 | 1.0000 | 0.6890 |
| m_6 | 1.0000 | 1.0000 | 1.0000 | 0.6516 |
| Smart Contract | GAS Cost | Ether Cost | USD Cost |
|---|---|---|---|
| Contract 1 | 756,893 | 0.000756893 | 2.7058 |
| Contract 2 | 886,305 | 0.000886305 | 3.1685 |
| Smart-Contract Function | GAS Cost | Ether Cost | USD Cost |
|---|---|---|---|
| Copyright information | 50,038 | 0.000050038 | 0.1788 |
| Add data address | 245,626 | 0.000245626 | 0.8781 |
| Buyer information | 69,836 | 0.000069836 | 0.2496 |
| Withdraw | 27,364 | 0.000027364 | 0.0978 |
| Acquire data information | 34,458 | 0.000034458 | 0.1231 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the International Society for Photogrammetry and Remote Sensing. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nan, R.; Zhang, L.; Xie, J.; Jin, Y.; Tan, T.; Liu, S.; Wang, H. Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking. ISPRS Int. J. Geo-Inf. 2025, 14, 317. https://doi.org/10.3390/ijgi14080317
Nan R, Zhang L, Xie J, Jin Y, Tan T, Liu S, Wang H. Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking. ISPRS International Journal of Geo-Information. 2025; 14(8):317. https://doi.org/10.3390/ijgi14080317
Chicago/Turabian StyleNan, Ruigang, Liming Zhang, Jianing Xie, Yan Jin, Tao Tan, Shuaikang Liu, and Haoran Wang. 2025. "Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking" ISPRS International Journal of Geo-Information 14, no. 8: 317. https://doi.org/10.3390/ijgi14080317
APA StyleNan, R., Zhang, L., Xie, J., Jin, Y., Tan, T., Liu, S., & Wang, H. (2025). Copyright Protection and Trusted Transactions for 3D Models Based on Smart Contracts and Zero-Watermarking. ISPRS International Journal of Geo-Information, 14(8), 317. https://doi.org/10.3390/ijgi14080317