Abstract
The dynamic confrontation between medical image-encryption technology and cryptanalysis enhances the security of sensitive healthcare information. Recently, Lai et al. proposed a color medical image-encryption scheme (LG-IES) based on a 2D Logistic-Gaussian hyperchaotic map (Applied Mathematics and Computation, 2023). This paper identifies that the LG-IES suffers from vulnerabilities stemming from the existence of equivalent keys and the linear solvability of the diffusion equation, enabling successful attacks through crafted chosen-plaintext attacks and known-plaintext attacks. For an image, a system of linear equations with rank r can be constructed, resulting in a reduction of the key space from to . To address these security flaws, the improved ILG-IES integrates the SHA-3 Edge-Pixel Filling Algorithm (SHA-3-EPFA), which includes plaintext-related SHA-3 hashing for parameter generation, a chaos-driven 3 × 3 × 3 Unit Rubik’s Cube rotation to achieve cross-channel fusion, and edge-pixel filling rules for diffusion encryption. ILG-IES outperforms LG-IES in attack resistance (resists CPA/KPA/differential attacks) while maintaining comparable security indicators (e.g., NPCR 99.6%, UACI 33.5%) to reference schemes. In future work, SHA-3-EPFA can be embedded as an independent module into most permutation-diffusion-based image-encryption systems, offering new perspectives for securing sensitive color images.
1. Introduction
Medical imaging techniques such as computed tomography (CT), magnetic resonance imaging (MRI), X-rays, and ultrasound are essential tools in modern healthcare [1]. However, the increasing demand for digital medical images has also raised significant concerns about data privacy and security [2]. The potential for leaks and tampering of medical images poses serious risks to patient privacy due to the sensitive personal information and health data typically contained within these images [3]. Therefore, in the context of digital healthcare [4,5], the complex medical image encryption and effective cryptographic analysis techniques are crucial for protecting patient data and maintaining trust in medical imaging practices.
With the increasing demands for efficiency, traditional image encryption techniques [6,7] struggle to provide both the computational speed and robust security needed for modern digital image transmission. In response to these challenges, various advanced encryption methods have been introduced, including chaos-based encryption, DNA encoding [2,8,9], and compressive sensing [10,11,12]. These innovative approaches offer better adaptability and higher performance compared to traditional methods. Among these, chaotic systems have gained attention for their pseudorandomness and sensitivity to initial conditions and parameters, making them suitable for cryptographic applications [13,14]. To strengthen security further, chaos-based encryption methods often incorporate multiple chaotic cascades or high-dimensional chaotic mappings [15,16,17], which increase key complexity and scramble pixel positions more effectively. Among high-dimensional chaotic mappings, 2D Logistic-Gaussian hyperchaotic maps (2D-LGHM) stand out for better dynamic performance than traditional low-dimensional chaotic systems: it fuses the nonlinearity of Logistic maps with the statistical randomness of Gaussian distribution, producing hyperchaotic sequences with two or more positive Lyapunov exponents—this property enables more complex and unpredictable behavior, which is critical for enhancing the randomness of encryption keys and pixel scrambling [18,19]. Additionally, chaos theory is frequently combined with other techniques.
However, while chaotic-based image encryption has significantly enhanced the security and efficiency of digital image transmission, it also faces new and evolving threats. In this regard, the field of image cryptanalysis, which combines chaotic systems with mathematical techniques, has made significant progress in identifying and addressing these vulnerabilities. Chen et al. [20] proposed an image-encryption scheme based on the cryptographic properties of Latin squares [21], utilizing chaos to construct a Latin equation lookup table (LUT). However, Hu [22], Li [23], and Wu [24], among others, have successively exploited vulnerabilities through cryptanalysis algorithms such as CPA. To enhance the security of the original scheme, several modifications have been suggested, including using different Latin equations for each module in each round and employing high-dimensional chaotic maps to replace the diffusion equations. Despite these improvements, however, the diffusion equations still exhibit periodicity, which may allow attackers to identify patterns in the encryption process. Modifications such as using different Latin equations for each module in each round and adopting high-dimensional chaotic maps to replace diffusion equations have been proposed, yet the diffusion equations still exhibit periodicity. Chen et al. [25] proposed constructing linear XOR equations of the original equations and applying Gaussian elimination to recover the encrypted image in the context of high-speed scrambling and pixel-adaptive diffusion encryption algorithms. Gaur et al. [26] used an improved amplitude-phase retrieval algorithm combined with cubic and cube root operations to obtain the decryption key. It is important to recognize that, despite claims of high robustness and effectiveness by the authors when constructing such algorithms using algebraic knowledge, they may still be susceptible to targeted password attacks.
This paper performs a cryptanalysis on the LG-IES scheme proposed by Lai et al. [27], and identifies the weaknesses of algebraic structure in the system. On one hand, all Pseudorandom Number Generators (PRNGs) generated by chaos are independent of plaintext, leading to the existence of equivalent keys. On the other hand, the reversibility of the permutation process and the high correlation with edge pixels of the diffusion process result in the arrangement pixel being generalized into nine specific states, which makes the key leaked by the edge pixels. Furthermore, the single-channel encryption scheme fails to meet the requirements for protecting sensitive information in color medical images.
The main contributions of this work are as follows:
- (1)
- The cryptographic analysis of the color medical image-encryption scheme proposed by Lai et al. [27] is carried out, and some security defects are found. Furthermore, we propose a cryptanalysis method incorporating differential analysis, CPA, and KPA. Consequently, the LG-IES based on Shannon’s principle [28] is cracked.
- (2)
- An improved security enhancement scheme is proposed, which uses Secure Hash Algorithm 3 (SHA-3) to establish plaintext-related Rubik’s Cube rotation rules to realize edge-pixel perturbation between channels. The experimental results show that the improved diffusion structure has better chaotic performance and has passed the security analysis.
2. The Image-Encryption Scheme of Lai et al.
This section reviews an image-encryption scheme (LG-IES) proposed by Lai et al. [27]. The encryption steps include the chaotic map and the encryption process of LG-IES.
2.1. 2D Logistic-Gaussian Hyperchaotic Map
Lai et al. [27] construct a two-dimensional Logistic-Gaussian hyperchaotic map (2D-LGHM) with a wide range of hyperchaos, and the dynamical equation is as follows:
where x, y are the state variables, and , , a, b are the control parameters, respectively. It shall be established that this system exhibits hyperchaos when the parameters , , a, b are chosen as
2.2. Description of LG-IES
2.2.1. The Secret Key
The secret parameter K is composed of several elements:
- -
- : Two different original initial value for the chaotic sequence.
- -
- : The correlation coefficients for and , respectively.
- -
- : The original control parameter.
- -
- d: A perturbation coefficient.
The length of the key K is 256 bits, with , , and d each occupying 48 bits, and and each occupying 32 bits.
Convert the 48-bit binary numbers , , and d into floating-point numbers in the range , and and into integers. The parameter K is then updated with the following equation:
where . Using and as initial chaotic parameters, substitute them into Equation (1), then iterate times to generate the y-sequence. Assign the generated values in row-major order to populate the matrix S. Similarly, with and as initial parameters, one can generate another y-sequence for the matrix R. This produces the chaotic matrices S and R.
2.2.2. One-Round Permutation
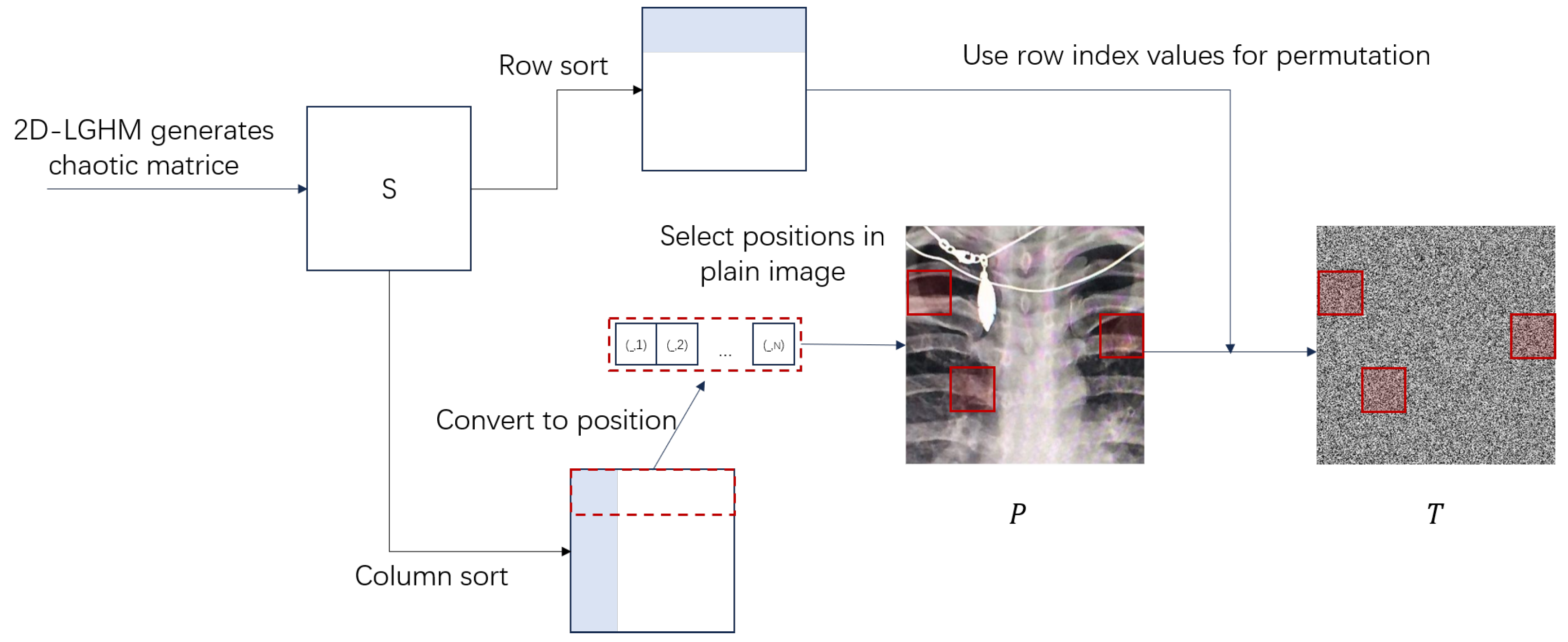
Sort each row (column) of S in ascending order to obtain the ordering matrices (). Then, encode the matrices () to obtain the position matrices ().
Next, the LG-IES scheme performs the permutation operation on the input image P to obtain the permutation image T, using position matrices and ordering matrices . Firstly, the positions of pixels of the original image P are represented by values from 1 to M × N. The new image is denoted as . Secondly, we will use the elements of the position matrix as indices to mark the position in the matrix . The rule is as follows: The intersection of the row and the j column of the matrix is taken as the position marked by the position matrix . Thirdly, we use the ordering matrix O1 to complete the permutation of positions. The specific rules are as follows: Each row i of the ordering matrix O1 is regarded as a permutation mapping from the set to itself. The elements of matrix marked by are permuted to the position . As shown in Figure 1, the positions and rules of the permutation are determined by the chaotic matrix, effectively disrupting the row and column pixels of the plain image in a single round of permutations.
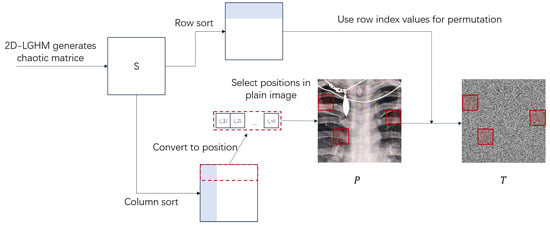
Figure 1.
High-efficiency one (Pixel Scrambling Positions Marked by Red Squares) round permutation.
2.2.3. Two Round Diffusions
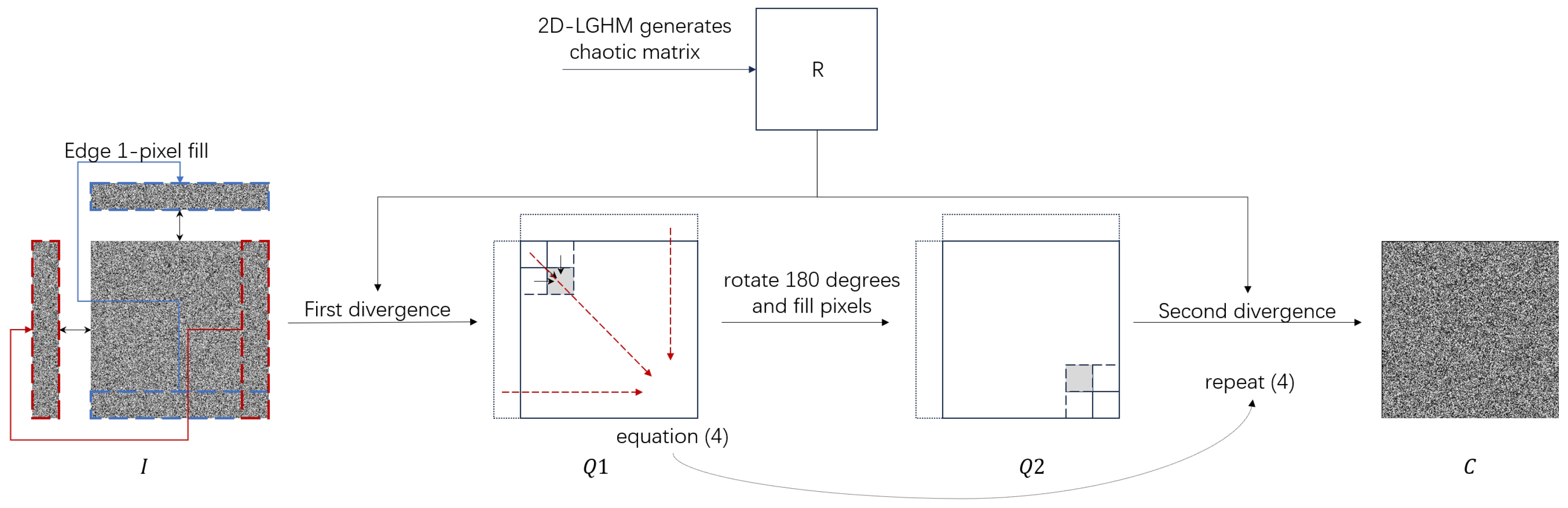
The multi-directional pixel substitution constructs a diffusion model. In this model, the pixel value at the current position is influenced by both the surrounding pixel values and its own state, resulting in a new pixel value that further affects pixels at other positions. The multi-directional diffusion method consists of two-round diffusion, each round contains two divergence equations. The divergence equation is as follows:
I represents the input image, and denotes the output image after the divergence process. Here, refers to the floor operation, represents the modulo function, and specifies the color level of the image. The matrix R is a chaotic matrix generated as described in Section 2.2.1.
The input image I utilizes Equation (4) for the first divergence, resulting in . The second divergence is then performed as follows: is rotated by 180 degrees to obtain the image , and Equation (4) is applied again to produce the final password image C. Since then, from I to C, multi-directional pixel diffusion is realized. The whole diffusion process is shown in Figure 2.
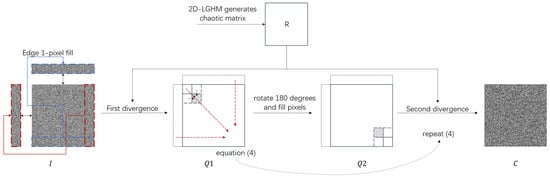
Figure 2.
Multi-directional pixels substitution.
2.2.4. Encryption Algorithm of LG-IES
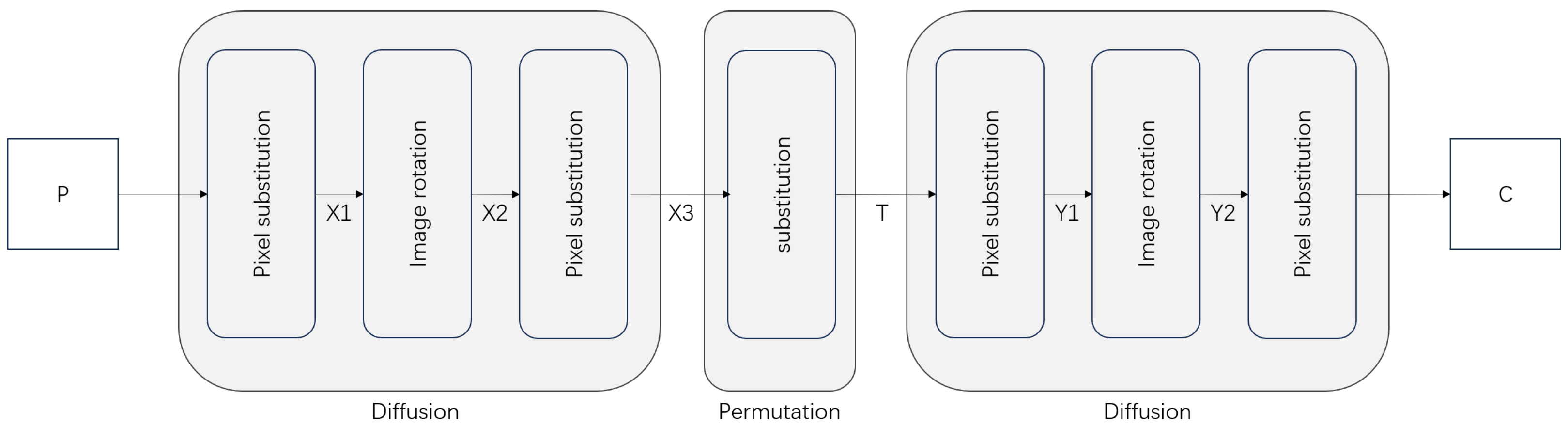
LG-IES consists of one-round permutation and two-round same diffusion; the overall block diagram of encryption is shown in Figure 3. To encrypt the plain image P, the first round of diffusion is applied (as described in Section 2.2.3), producing the intermediate results , , and . Following this, a permutation (Section 2.2.2) transforms into T. A second round of diffusion (Section 2.2.3) is then applied, resulting in , , and the ciphertext C. This sequence of operations, implemented through LG-IES, completes the encryption of P into C.
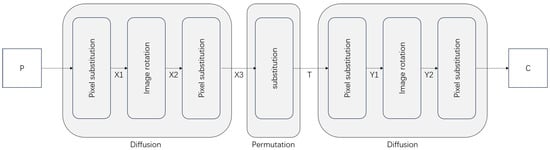
Figure 3.
Block diagram of LG-IES.
In this paper, the decryption algorithm does not impact the security analysis and will not be elaborated on in detail (please refer to the original work [27]).
3. Cryptanalysis
This section analyzes the security of the image-encryption scheme presented by Lai et al. [27]. The relevant properties are listed in Section 3.1. Then the defects of the model are analyzed in Section 3.2, and the encryption algorithm can be finally cracked by cryptanalysis of each encryption process in Section 3.3.
3.1. Relevant Properties
Construct two plain images, denoted as and . It can define the difference image as . Similarly, the other differential images are defined such as , , , , , , and .
Proposition 1.
After one-round diffusion, the differential image depends only on the differences between the original images and without any terms involving R.
Proof.
There are three steps from the plain image P to image , which consists of two divergence equations and an image flipping. Next, they are analyzed as follows.
- The first divergence:According to Equation (4) and the definition of difference image, can be written as:Here, due to the characteristics of the differential, the term is eliminated, so the difference equation for the first divergence of the first-round result does not include the chaotic matrix R.
- Rotation operation:The rotation operation does not change the difference relationship between the matrix elements. Therefore, the difference matrix retains the same difference structure as and still does not contain the terms of the chaotic matrix R.
- The second divergence:The difference equation for isSimilarly, in this differential analysis, the influence of the chaotic matrix R is eliminated. So it holds.
□
Proposition 2.
When satisfies the condition that all pixel values are zero except at a single position where , with and , there exists some certain relationships between the differential image and the differential ciphertext :
(1) When ,
- If , satisfies
- Else if , satisfies
- Else if , satisfies
(2) When ,
- If , satisfies Equation (9).
- Else if , satisfies
- Else if , satisfieswhere and .
(3) When ,
- If , satisfies
- Else if , satisfies
- Else if , satisfies Equation (11).
(4) When ,
(5) In addition to the above, when , satisfies
where and .
Proof.
Assume that and are two input images satisfying . In Equation (13), if the image satisfies where . Then image is defined as shown in Equation (16),
The diffusion process in the LG-IES scheme is as follows. The elements and are directly calculated according to Equation (5). Then rotate () by 180 degrees to obtain (). Finally, it can directly compute to obtain from Equation (6). The matrix form of the ciphertext difference is as follows:
Therefore, the relationship between and is established, and Equation (13) is proved. The proof process for other equations is similar and will not be repeated here (see Appendix A). □
Note: Table 1 provides a detailed example of the evolution for a matrix. When , corresponding to , it satisfies Equation (13) (with and ). This table reflects the change process from to .

Table 1.
The proof of Equation (13).
Proposition 3.
Assume that , , …, belongs to the set , i.e., , , …, , and . If , then it has
3.2. Model Analysis
(1) In LG-IES, the authors only utilize a secret parameter K (in Section 2.2.1) to generate chaotic matrices used for encryption, which exhibit low correlation with the plain image, leading to the existence of equivalent keys. This approach produces the same PRNGs across different plaintext images of equal size, allowing the encryption to be deciphered without knowledge of the actual secret key.
(2) We observe that there is a potential risk of differential attack through the Proposition 1. The reason for this is that the influence of the chaotic matrix R is canceled out by differential analysis during the diffusion process. This enables the attacker to design a differential input combination such that the output matches the expected pattern, allowing them to obtain feature information of the original image.
(3) In the multi-directional diffusion process of Section 2.2.3, the image T is supplemented using the rightmost and bottommost edge pixels. During the first round of diffusion, it acts on the leftmost and topmost pixels. After rotation, the leftmost and topmost pixels move to the rightmost and bottommost edge pixels. During the second round of diffusion, the new rightmost and bottommost pixels act on the new leftmost and topmost pixels.
The way the edge pixels are complemented and diffused carries a certain regularity. Thus, the leftmost and topmost pixels of the cipher image C are influenced by the edge pixels of the input image T. This allows an attacker to predict the corresponding positions in the cipher image from the known edge pixels, which reduces the randomness and security of the encryption and leads to vulnerabilities.
(4) In LG-IES, the scheme applies the same encryption process to each channel, resulting in a lack of correlation between the channels. This might lead to a lack of cohesion in the encryption scheme, thereby reducing its security.
3.3. Chosen-Plaintext and Known-Plaintext Attacks
Step 1: Identification of Permutation Patterns
(1) sets of special input pairs are constructed.
(2) Assuming satisfies , after first round of diffusion, intermediate ciphertext images are obtained.
(3) According to Proposition 1 and Equation (4), each differential image satisfies for an unique pixel , with all other pixels set to 0, where and .
(4) The differential image set is obtained by applying a permutation operation to . Each differential image corresponds to a single non-zero pixel, , with all other pixels set to 0, where and .
(5) After LG-IES encryption, the ciphertext is obtained.
(6) According to Property 2, eve infers the positional mapping from to in the final ciphertext , and she can obtain an equivalent substitution transformation.
The image set , obtained based on , ensures that every position in the matrix obtained after one diffusion has exactly one occurrence of the value 1 across the set of differential images. Example 1 gives a example to demonstrate the construction of a special image .
Example 1.
Given two matrices and as follows:
The difference between and , denoted as , is computed element-wise:
According to Proposition 1, it generates the differential images. The images , , and are derived as follows:
Here, is a special differential image where the pixel at position is set to 1, and all other pixels are 0. This corresponds to one of its differential images in our set of differential images.
Step 2: Extraction of Diffused Chaotic Matrix R
Any known-plaintext image P is processed through LG-IES to generate the corresponding ciphertext image C. By establishing a system of linear equations based on the relationships between each element of P and C, the chaotic matrix R can be solved.
Example 2.
The plain image P can be arbitrary, and for ease of demonstration, a specially constructed all-zero matrix P is defined as follows:
P is then processed through the LG-IES encryption system, resulting in the corresponding ciphertext image C, given by:
Let the intermediate cipher image be defined as:
Substitute Equation (26) into Equation (4) to obtain Equation (25). Solve the simultaneous equations to derive Equation (27).
For example, .
According to the chaotic matrix (27) and the one-to-one mapping permutation from to T obtained in Step 2, we can subsequently obtain (see Equation (A1a) in the Appendix B), (A1b), (A1c), T (A1d), (A1e), and (A1f).
This forms a linear self-consistent loop of the encryption system LG-IES, allowing us to solve the system by establishing the relevant equations between Equation (26) and Equation (A1f) in the Appendix B, i.e., , as follows:
Resulting in:
The chaotic matrix is then obtained
The complexity analysis is as follows:
Each element of chaos in Equation (30) has possible values. In the example above, by reducing the unknowns in the chaotic matrix R to a single parameter h, the entire matrix can be expressed as a function of h. Consequently, the key space shrinks from to , losing 256 bits of security.
For the image, the initial key space is given by . Referring to Example 2 in this section, an system of linear equations (as shown in Equation (28)) can be derived, with the rank (r) defined as the maximum number of linearly independent rows or columns in the coefficient matrix of the system. The key space reduction based on the rank (r) of the equation system is as follows:
- (1)
- When , the key space shrinks by , reducing from to 1.
- (2)
- When , the key space shrinks by a factor of , and the security (in terms of bits) is reduced by bits.
This significant reduction makes the encryption scheme highly vulnerable to brute-force attacks, with the time complexity of this process presented in Table 2. This feasibility is enabled by modern computing technologies, which can practically exhaust the smaller search space.

Table 2.
Reduced Key Space and Time to Solve for Matrix R Across Image Sizes and Types.
4. Proposed SHA-3-EPFA
Based on the LG-IES proposed by Lai et al. [27], this paper presents an enhanced scheme for the medical image encryption, and provides simulation as well as security analysis.
4.1. Encryption Scheme
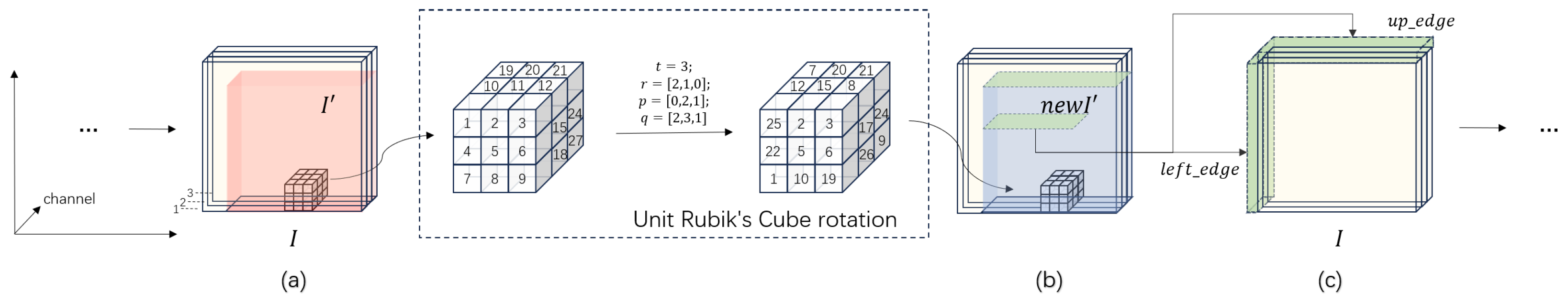
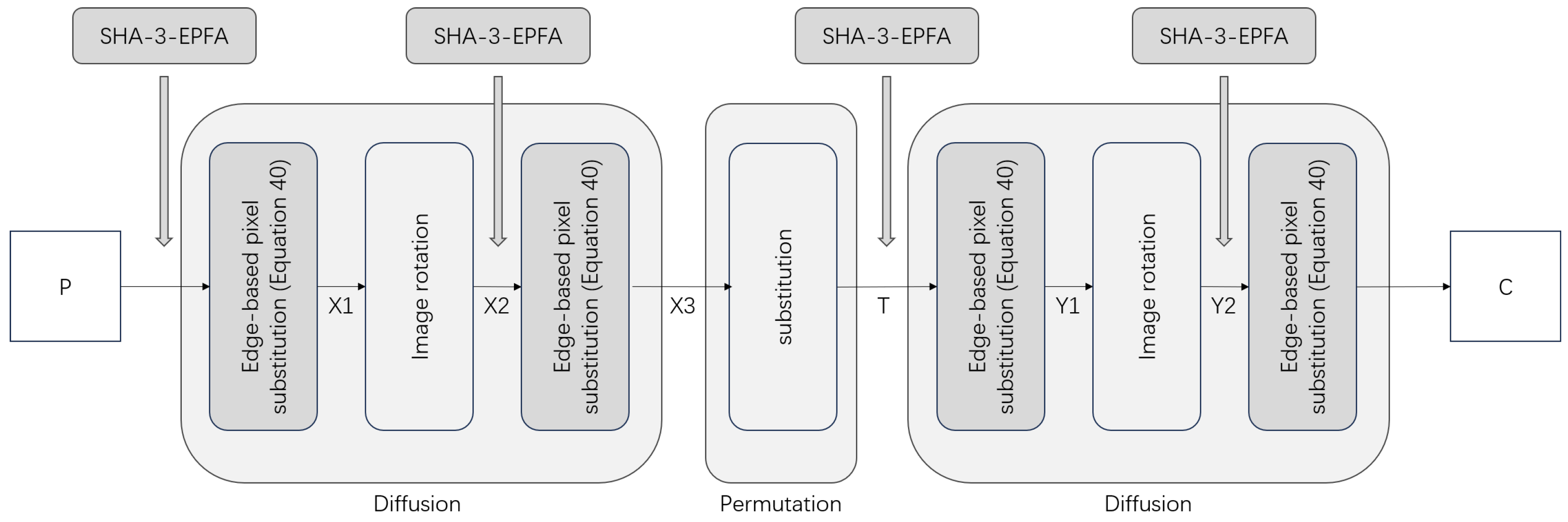
The LG-IES suffers from vulnerabilities stemming from the existence of equivalent keys and the linear solvability of the diffusion equation, enabling successful attacks through crafted chosen-plaintext attacks and known-plaintext attacks. To address these vulnerabilities and overcome the limitation of 2D planar image encryption in the original scheme, we introduce a color medical image-encryption scheme based on the SHA-3 Edge-Pixel Filling Algorithm (SHA-3-EPFA), referred to as ILG-IES. This encryption scheme comprises two main components: an auxiliary algorithm, SHA-3-EPFA (Steps 1 to 6), and the primary encryption scheme (described in Step 7). Before each round of divergence (Equation (4)), the SHA-3-EPFA component is responsible for generating edge-filled pixel values by leveraging the principles of rotation and displacement within a Rubik’s Cube in three-dimensional space, thereby introducing pixel-level channel fusion and enhancing randomness. Meanwhile, the primary encryption scheme performs the actual encryption operations. Assuming the input image size is , the structure of SHA-3-EPFA is illustrated in Figure 4, while the overall block diagram of ILG-IES is shown in Figure 5. The steps of ILG-IES in detail are as follows:

Figure 4.
SHA-3-EPFA (Only Key Steps Shown). (a) Divide the rotation area, (b) rotate Rubik’s Cube, and (c) obtain new pixels to fill.
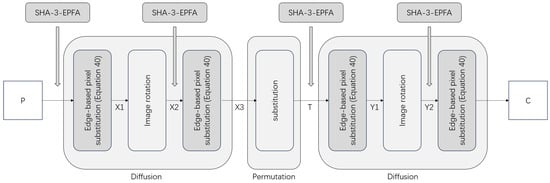
Figure 5.
Block diagram of ILG-IES.
Step 1: Partitioning of the Rubik’s Cube rotation area (Figure 4a)
(1) Given a color input image I of , a subset is obtained by excluding the elements of the first row and the first column from I.
(2) The color image with dimensions , where and , is sequentially divided into unit Rubik’s Cubes, each of size .
Step 2: Generating the Plaintext-Related Matrix
(1) Calculate the sum of all elements across the three subimages of to obtain s.
(2) Calculate according to Equation (31), where .
(3) Fill the row-wise into a matrix to obtain V.
Step 3: Generating the Chaos-Related Matrices
(1) Using and in Section 2.2.1 as initial chaotic parameters, substitute them into Equation (1), then iterate times to generate the y-sequence.
(2) Extract the elements from the to the positions of the y-sequence, and arrange them in rows to obtain a new chaotic matrix A.
(3) Using and as initial chaotic parameters, substitute them into Equation (1), then iterate times to generate another -sequence.
(4) Extract the elements from the to the positions of the sequence, and obtain the chaotic sequence w.
Step 4: Obtaining Rubik’s Cube Parameters
(1) The matrices V and A are concatenated along the first dimension to obtain a three-dimensional matrix B with size .
(2) Applying the SHA-3 hash function to this matrix B generates a 256-bit hash value.
(3) The first 16 digits of this hash value are designated as a group labeled , and each subsequent set of 16 digits is labeled as , , and , respectively.
(4) Calculate the parameters controlling the rotation of the Rubik’s Cube using Equation (32).
where t denotes the number of rotations, r denotes the dimension of the rotation, p denotes the specific layer or index of the rotation operation, q denotes the angle of the rotation, and .
The equation below outlines a detailed rotation strategy:
Step 5: Rotating the Image (Figure 4b)
Rotate each unit Rubik’s Cube in the image based on t, r, p and q to realize pixels scrambling in the selected area. The new image is denoted as . Algorithm 1 describes the rotation process of the unit Rubik’s Cube.
| Algorithm 1: Unit Rubik’s Cube Rotation. |
| Input: cube (The Rubik’s Cube before rotation) Output: newcube (The Rubik’s Cube after rotation) for i in range : if : elif : elif : update |
Step 6: Filling the Edges of the Image (Figure 4c)
(1) Using Equation (34), obtain the padded pixel values ,
where .
(2) When , select the corresponding pixels from to be used for column-wise and dimension-wise filling of .
(3) When , select the corresponding pixels from to be used for row-wise and dimension-wise filling of .
Step 7: Obtaining the Improved Scheme: ILG-IES
(1) The plain image P undergoes Steps 1 to 6 to obtain the padded pixels, and using Equation (35), the diffused image is obtained.
Here, denotes the color channel index, and is shared identically across all channels, i.e., for all .
(2) Rotate by 180 degrees to obtain .
(3) undergoes Steps 1 to 6, and then, using Equation (35), is obtained.
(4) Perform the permutation of Section 2.2.2 to obtain T.
(5) T undergoes Steps 1 to 6, and then, using Equation (35), is obtained.
(6) Rotate by 180 degrees to obtain .
(7) undergoes Steps 1 to 6, and then, using Equation (35), the cipher image C is obtained.
4.2. Decryption Process
The overall decryption process of ILG-IES is as follows.
Step 1: Using Equation (36), the encrypted image C is decrypted to recover the partial image , which represents the section of image before the multi-directional pixel substitution. That is, .
where , , and .
Step 2: Calculate the sum of , matrix V is obtained by referring to Step 2 in Section 4.1.
Step 3: Generate chaos through 2D-LGHM. Referring to the above encryption process, we obtain the matrices S and R, and the SHA-3-EPFA related matrix A and sequence w.
Step 4: Refer to Step 4, 5 and 6 in Section 4.1, obtain the relevant parameters t, r, p and q for the Rubik’s Cube rotation. Apply these parameters to rotate the region , and then derive the pixel matrices and for edge filling.
Step 5: Using and , restore the pixels in the upmost and leftmost columns, as in Equation (37). Thus, the entire is restored.
Step 6: Rotate by 180 degrees to obtain .
Step 7: Repeat the steps from Step 1 to Step 5 to restore T.
Step 8: Referring to Section 2.2.2, the index matrix O and Q are obtained according to matrix S, and then Equation (38) is used to recover the permuted image .
Step 9: Repeat the steps from Step 1 to Step 8 to sequentially recover , , and the plain image P.
5. Simulation Results and Security Analysis
The comparative experimental evaluation is conducted to quantify the resilience enhancement of the proposed scheme against adversarial attacks relative to the baseline approach. Furthermore, its cryptographic security is benchmarked against contemporary encryption paradigms, including DNA-based cryptography, differential cryptanalysis, and deep learning-driven encryption frameworks.
5.1. Simulation Results
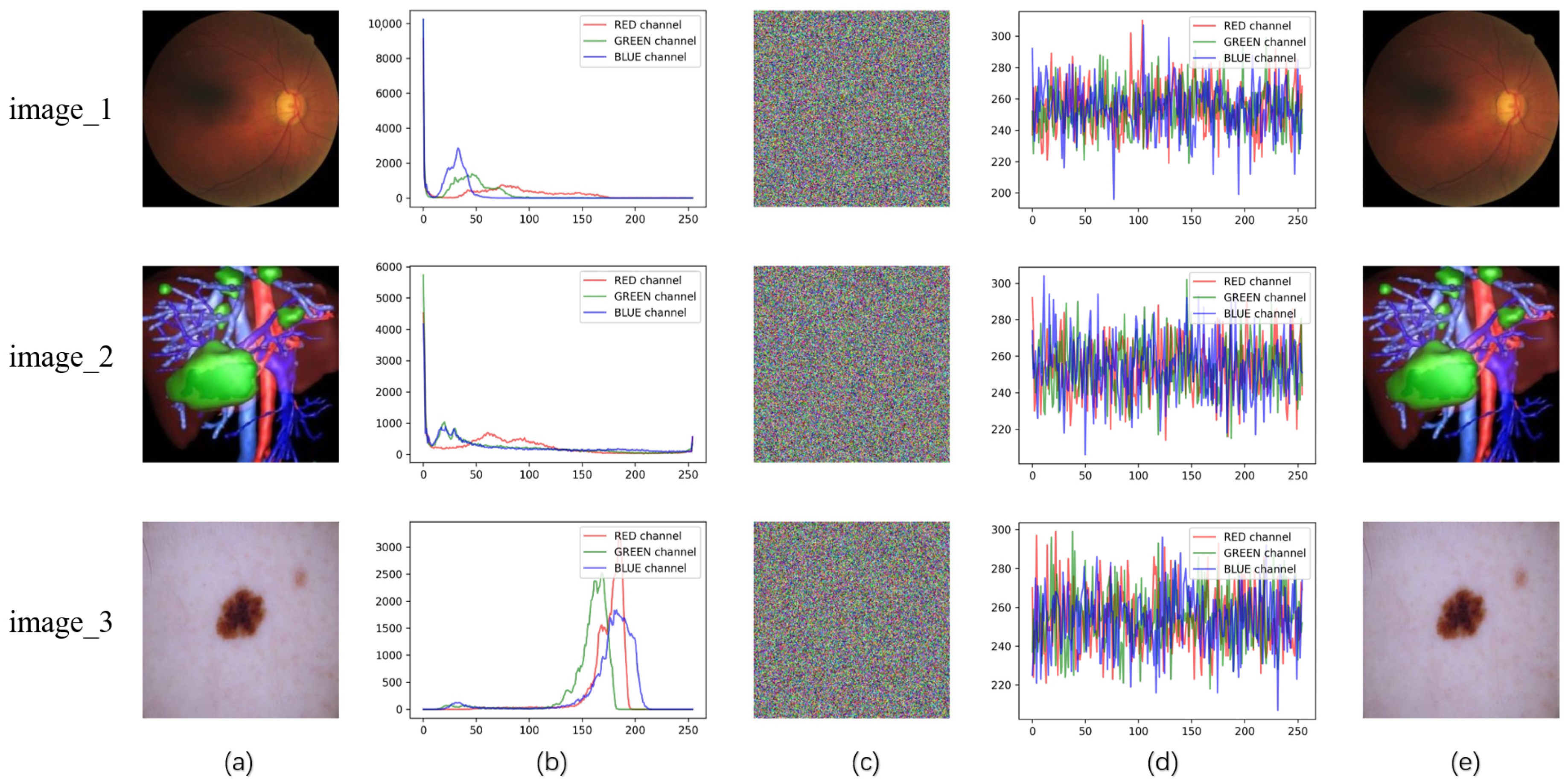
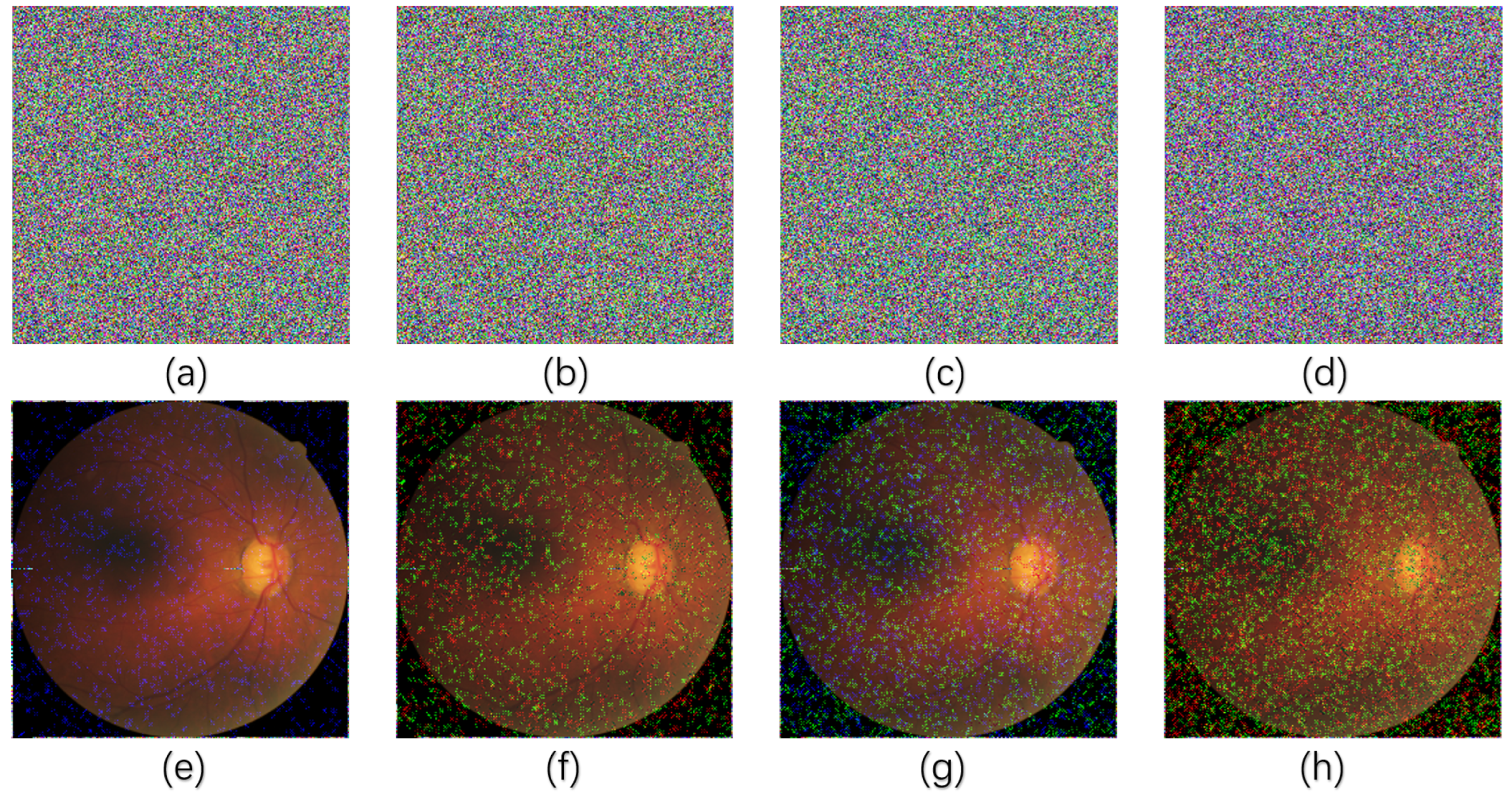
Three images are randomly downloaded from color medical image datasets and preprocessed to a size of . The images are named “image_1” [29], “image_2” [30], and “image_3” [31]—with their original sources accessible via the following URLs: “image_1” from the Glaucoma Dataset (https://doi.org/10.1145/3603765.3603779 (accessed on 21 September 2025)), “image_2” from the 3D Medical Image Reconstruction Dataset (https://www.ircad.fr/research/data-sets/ (accessed on 21 September 2025)), and “image_3” from the ISIC 2024 Skin Image Archive (https://www.isic-archive.com/(accessed on 21 September 2025))—as shown in Figure 6a. These images are then processed using ILG-IES with SHA-3-EPFA added. The simulation results of Figure 6c are obtained through encryption, visually obscuring the medical information. The images after direct decryption are shown in Figure 6e, which is not significantly different from the original images. The time cost of the encryption and decryption process is shown in Table 3.
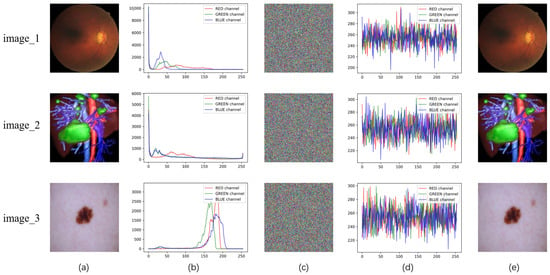
Figure 6.
(a) plain images, (b) histogram of (a), (c) cipher images, (d) histogram of (c), (e) recovered images.

Table 3.
Time Overhead Comparison Between LG-IES and ILG-IES.
5.2. Key Sensitivity
According to Section 2.2.1, the key is defined as the initial input of the parameters for the 2D Logistic-Gaussian hyperchaotic map. In the improved scheme, the key is represented as . Given that the key space in this context is , the probability of an adversary successfully cracking the key through probabilistic means is exceedingly low.
To analyze the impact of minor changes in the key on the differences between two encrypted images of the same plaintext, we randomly select 1 bit from the key space of K and invert it. This process introduces a slight modification to the key parameters, leading to different chaotic sequences being generated. These modified sequences are then used to encrypt the plaintext image. We conduct 1000 independent experiments, computing the number of pixel change rate (NPCR), uniform average change intensity (UACI), and blocked average changing intensity (BACI) to measure the differences between the resulting pairs of cipher images. The average values of these metrics are presented in Table 4. NPCR, UACI, and BACI are quantitative indicators used to assess the differences between two images, and the calculation formula is shown below.
where
The calculated average values of NPCR, UACI, and BACI are very close to their theoretical values. This indicates that the differences among the ciphertext images obtained by encrypting “image_1”, “image_2”, and “image_3” with slightly altered keys are significant. Therefore, it can be concluded that each randomly selected key from the key space is effective.

Table 4.
Key sensitivity analysis results.
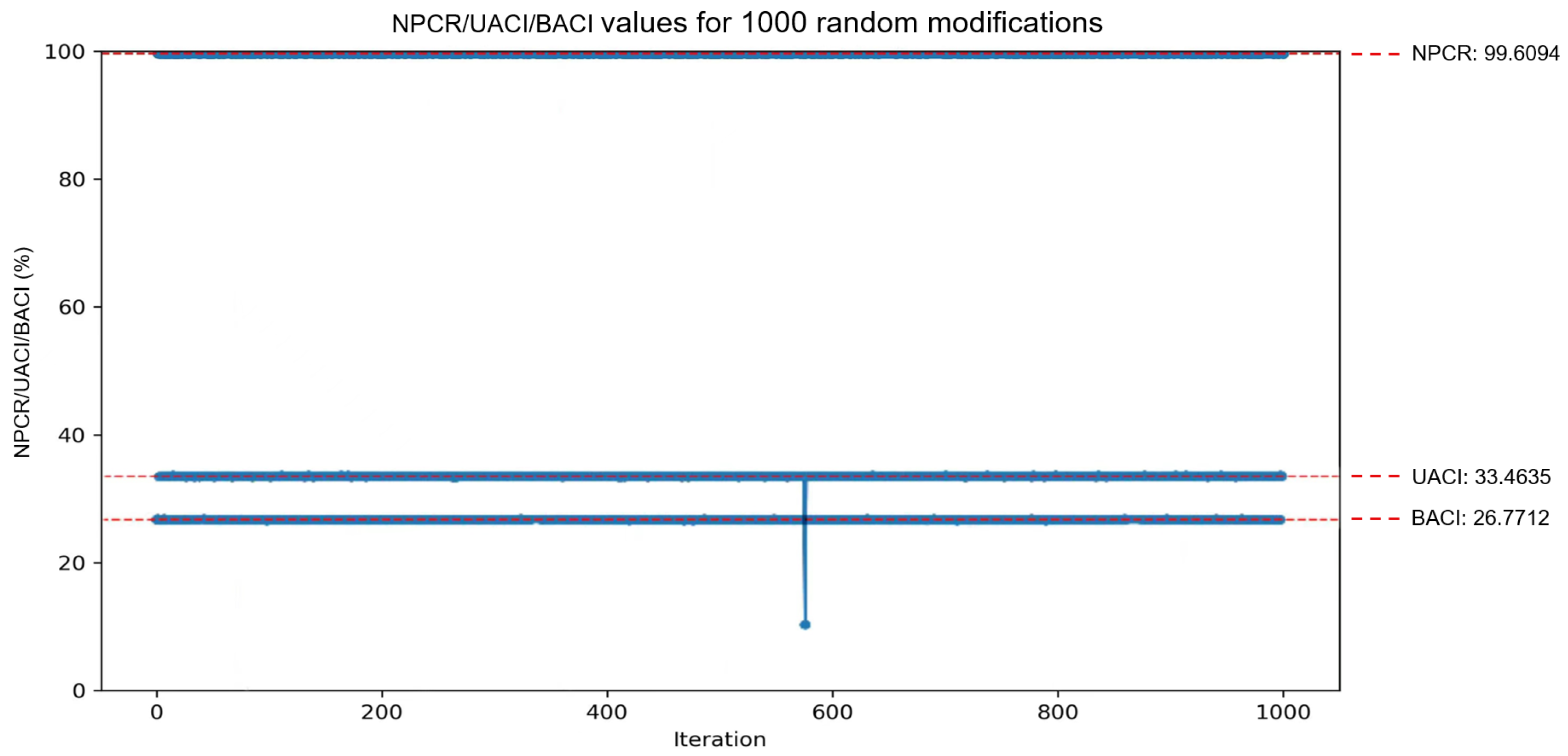
5.3. Plaintext Sensitivity Analysis
Plaintext sensitivity refers to the difference between two ciphertexts obtained by encrypting two plain images with slight differences using the same key. For medical images, certain details such as lesions or abnormal areas may occupy only a small portion of the image. These minor differences are often the critical information in medical images. Therefore, high plaintext sensitivity ensures that these key details are sufficiently obscured during the encryption process, preventing attackers from extracting sensitive data by analyzing local information in the encrypted images.
In this analysis, we randomly select an image from “image_1”, “image_2”, and “image_3” and denote it as P. A pixel point within P is then randomly chosen, and its value is modified to , resulting in a slightly adjusted plain image . This process is repeated 1000 times, encrypting separately. Each time, the NPCR between the cipher images C and is calculated. The final results of the improved scheme are plotted as shown in Figure 7. where it can be observed that the calculated values closely approach the ideal values , , . In LG-IES, the average NPCR value obtained was , whereas in the improved scheme with SHA-3-EPFA added, the NPCR value reached . This demonstrates that when encrypting with LG-IES enhanced by SHA-3—EPFA, two plaintext images differing by only one bit will produce significantly different ciphertext images. In addition, compared with the original scheme, the algorithm exhibits higher sensitivity to plaintext, possessing excellent differential resistance, which ensures sufficient confidentiality and privacy for color medical images.

Figure 7.
Plaintext sensitivity analysis.
5.4. Histogram Analysis
When the histogram of a ciphertext image displays a uniform distribution of pixel values or a high degree of mixing, it indicates that the encryption algorithm possesses enhanced security, making statistical attacks more challenging. As shown in Figure 6, the histograms of each channel in the images encrypted using the improved scheme exhibit a uniform distribution. This demonstrates that the enhanced encryption algorithm effectively conceals the image information.
The distribution is defined as follows:
where , is the observed pixel proportion of each gray level.
We further compare the balance of the ciphertext histograms between the original and improved schemes. A smaller indicates a more balanced histogram, and for grayscale images with a grayscale level of 256, the chi-square is 293 at the common significance level . Table 5 lists the chi-square results of different channels and the same type of scheme. The chi-square values of the improved scheme are slightly lower than those of the original scheme and are generally below the threshold. This implies that the null hypothesis of histogram uniformity cannot be rejected at a significance level of 0.05. The addition of SHA-3-EPFA encryption results in more balanced histograms.

Table 5.
Each channel chi-square test for histogram analysis.
5.5. Correlation Analysis
Ordinary image pixels are usually highly correlated, and one pixel will often reveal the information of surrounding pixels, which can be used by the opponent to predict the plain image. Therefore, the goal of the encryption algorithm is to reduce this correlation as much as possible. To quantify the linear correlation between pixels, Pearson correlation coefficients [36] are calculated using 5000 randomly selected pixels from each channel. The equation for correlation is as follows:
where
and denote the gray value of the pixel pair, is the number of selected pixel pairs.
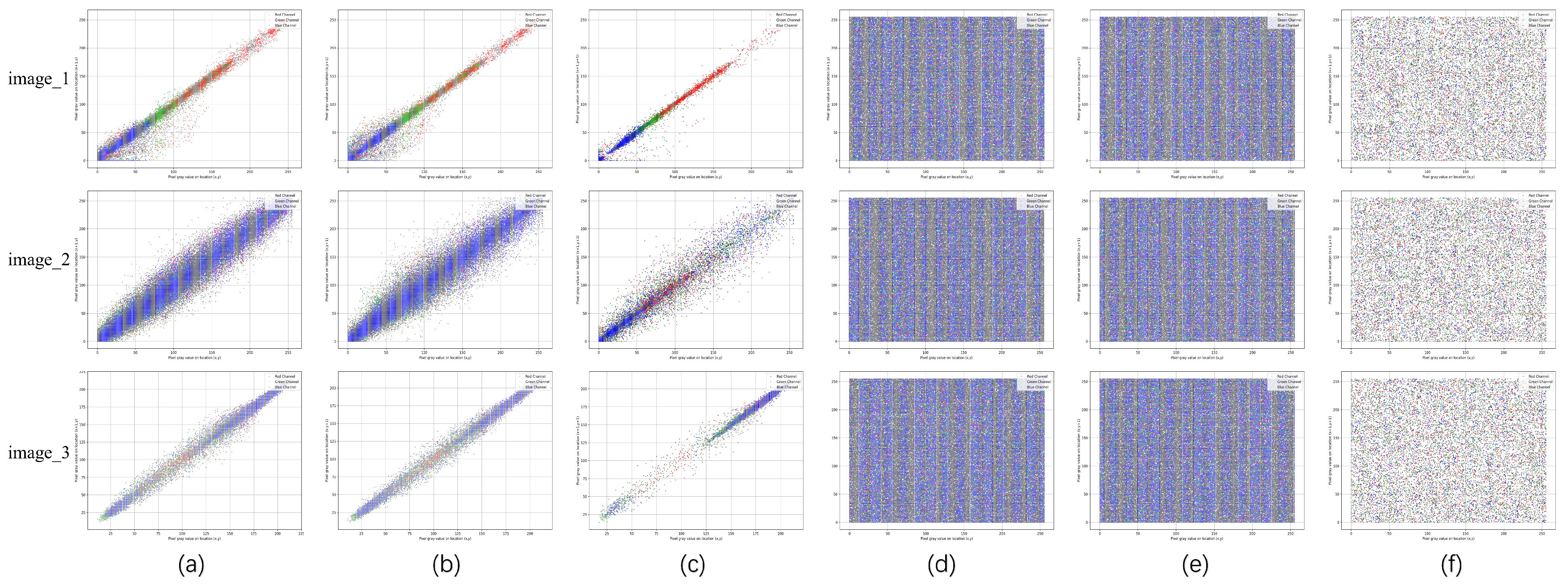
Figure 8a–c present scatter plots of the three plain images in horizontal, vertical, and diagonal directions, while Figure 8d–f illustrate the correlation in their corresponding encrypted images. Table 6 is the correlation calculation result of “image_1”, where H, V, and D represent horizontal, vertical, and diagonal directions, respectively. In the ciphertext image, the adjacent pixels in various directions are dispersed across the matrix area, with their correlation approaching 0 and outperforming the original scheme. This indicates that the proposed cryptosystem can effectively remove the strong correlation between adjacent pixels of the plain image.
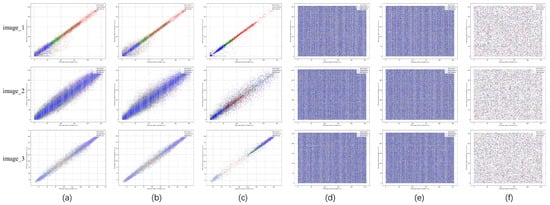
Figure 8.
Correlation of plain images and cipher images in horizontal, vertical, and diagonal directions, respectively.

Table 6.
Correlation analysis.
5.6. Entropy Analysis
The information entropy of an image reflects the uncertainty of the image information, and the calculation formula is as follows:
where L is the number of grayscale levels of the image, and represents the probability of occurrence of grayscale value i.
Calculate the gray entropy of the plaintext “image_1”, “image_2”, “image_3” and the cipher images before and after the improved cryptosystem. The results are shown in Table 7. The entropy value of the encrypted images is very close to the entropy value of a randomly generated color image of the same size, which is measured to be . The improved encryption scheme can make the information entropy of the image close to the ideal value; therefore, the algorithm maintains high security and confidentiality.

Table 7.
Entropy analysis.
5.7. Noise and Cropping Attacks
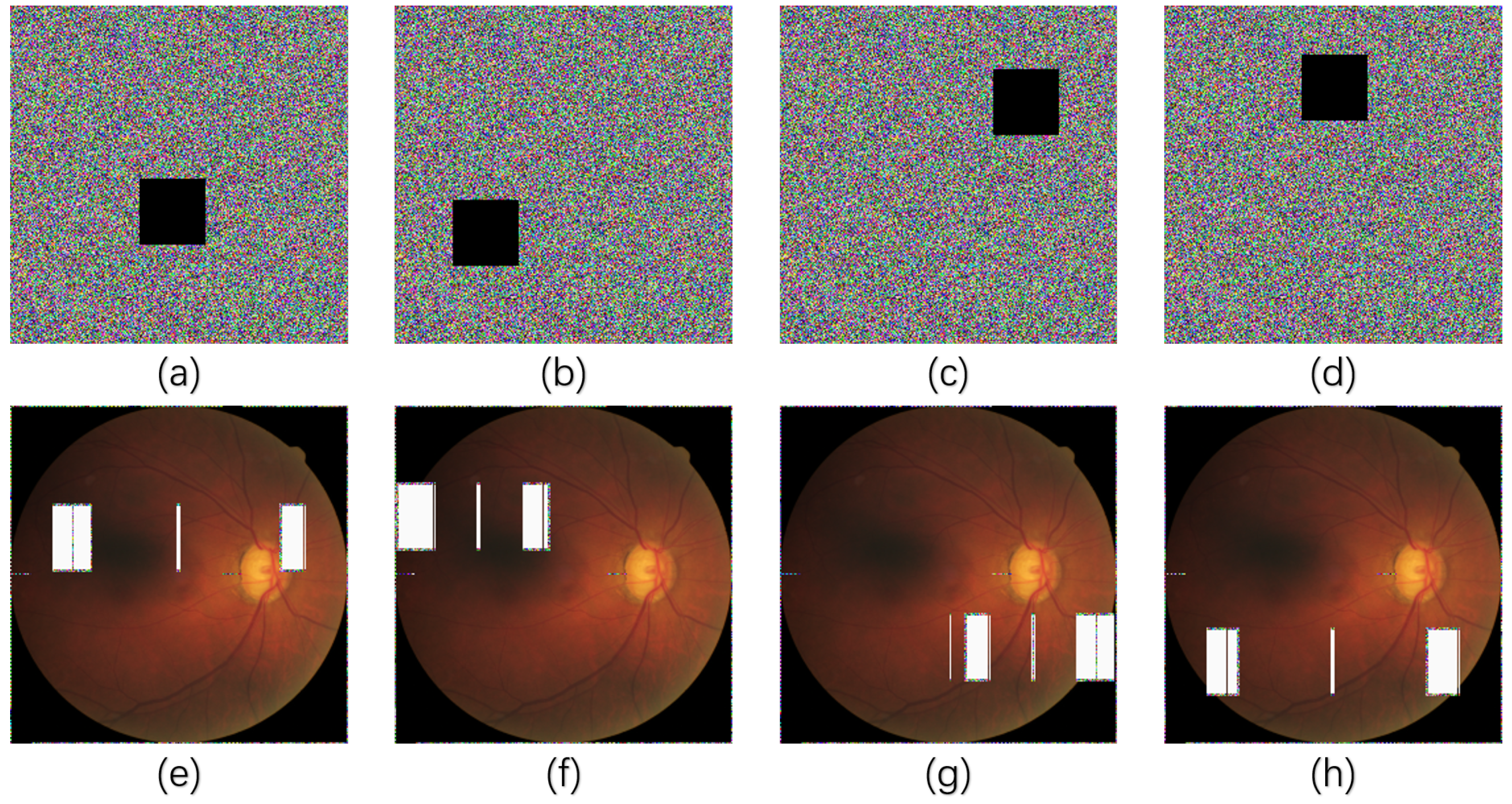
Color medical images often contain important diagnostic information, such as the color and edge details of the lesion. The addition of noise may interfere with these details and thus affect the doctor’s diagnosis. If the encryption algorithm cannot maintain the key features of the decrypted image under noise attack, the application of the algorithm in the medical field may not be robust enough. The experiment introduces 1%, 3%, 5%, and 10% salt and pepper noise to the encrypted “image_1”, creating noisy versions as illustrated in Figure 9a–d. These noisy images are then decrypted, producing four corresponding distorted images shown in Figure 9e–h.
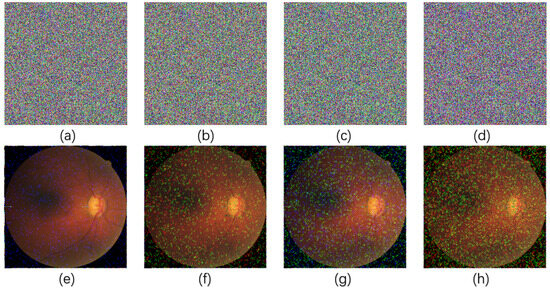
Figure 9.
Simulation results of noise attacks. (a–d) encrypted “image_1”, respectively, add 1%, 2%, 3%, and 5% of salt and pepper noise; (e–h) the corresponding decrypted images.
Cropping attacks destroy parts of these areas, causing the decrypted image to lose important information. Evaluating the performance of the encryption algorithm under cropping attacks can ensure that even if part of the image information is lost, as much diagnostic information as possible is retained after decryption, or the missing part of the information is clearly marked. The experiment randomly selects any positions of the encrypted “image_1” for cropping attacks, as shown in Figure 10a–d, and decrypts them to obtain the distorted images as shown in Figure 10e–h.
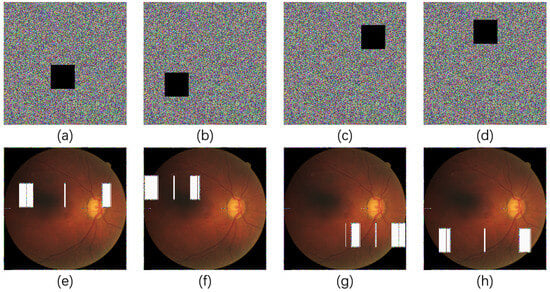
Figure 10.
Simulation results of cropping attacks. (a–d) randomly crop size of the encrypted “image_1”, (e–h) the corresponding decrypted images.
Apparently, after noise and cropping attacks, despite some loss of information or anomalies, the scheme can still decrypt the cryptographic images affected by partial (important) data destruction into globally visible images. Color images show better robustness when subjected to external interference, and can well prevent critical medical information from being recovered and leaked by unauthorized visitors.
5.8. Attacks Resistance Analysis
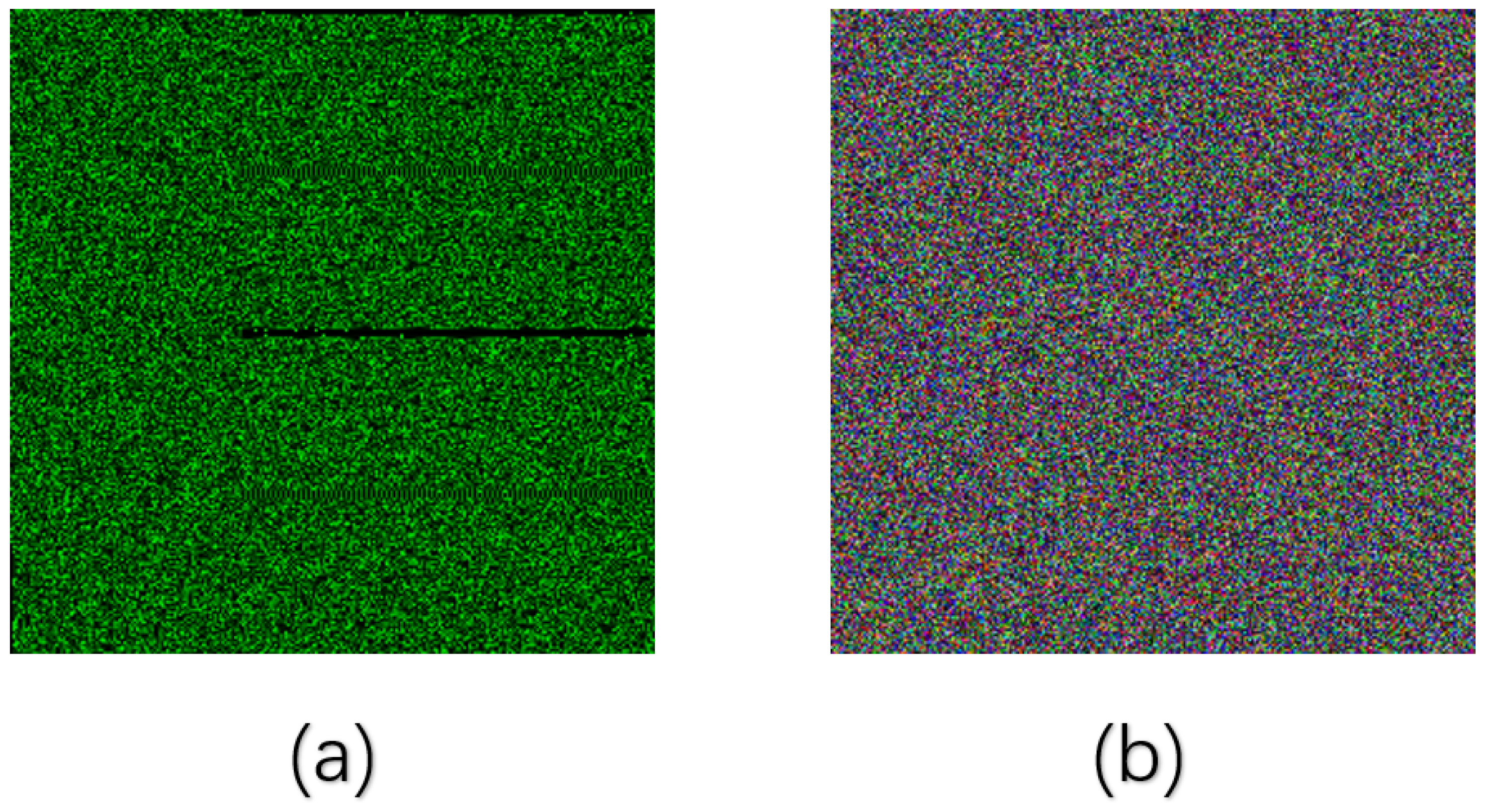
To evaluate the security of the proposed scheme, the same CPA and differential analysis methods as the original scheme were employed. We constructed two specific images: an all-zero image and an image where only one pixel is set to 1 while all others are set to 0. These images were encrypted separately, and then the difference between them was calculated. Figure 11a shows the difference image obtained using the original scheme, while Figure 11b shows the difference image obtained using our scheme. Our scheme not only overcomes the occurrence of a large number of zero pixels at the edges, eliminating discernible patterns, but also further achieves inter-channel fusion, thereby increasing the ciphertext complexity. Based on this, the complexity of attacks on the cipher image is , equivalent to a brute-force attack. Thus, it can effectively resist the attacks proposed in the cryptanalysis of this paper. Table 8 compares the resistance of the proposed scheme and other schemes to various attacks. It can be seen that SHA-3-EPFA can resist a variety of attacks and has good robustness in the same type of advanced schemes.

Figure 11.
Contrast resistance attacks.

Table 8.
Attacks on various schemes.
6. Conclusions
In this paper, a chaotic image cipher based on algebraic operations is analyzed. We prove that there are some vulnerabilities in this cryptosystem, and we can partially crack the chaotic matrices by constructing special images and establishing linear equations to reduce the secret key space. In addition, in view of the reversibility of the permutation process and the edge correlation and linear features of diffusion, we also propose a three-dimensional image rotation based on SHA-3 that implements an edge-pixel filling algorithm. The experimental results and security analysis show that the improved cryptosystem has good robustness and security while resisting the chosen-plaintext attack.
The proposed SHA-3-EPFA not only enhances the security performance of the original scheme, resisting CPA, KPA, and DC attacks, but it can also be embedded as an independent module into most permutation-diffusion-based encryption models for pixel position perturbation in future work. This is particularly effective for multi-channel images, such as color images, breaking the limitation of traditional encryption methods that only confuse pixels within individual channels. It enables pixel interaction between channels, allowing the encryption algorithm to achieve overall integrity and transferability with relatively low computational overhead.
Author Contributions
Conceptualization, data curation, formal analysis, funding acquisition, resources, software, and supervision were carried out by W.W., while S.W. focused on investigation, methodology, project administration, validation, visualization, and writing the original draft. Both authors collaboratively reviewed, edited, and approved the final manuscript. This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors. During the preparation of this work, the authors used artificial intelligence (AI) and AI-assisted technologies in order to enhance the readability and language quality of the text. After using this tool/service, the authors reviewed and edited the content as needed and take full responsibility for the content of the published article. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data presented in this study are openly available from these sources: One is from the Glaucoma Dataset (https://doi.org/10.1145/3603765.3603779, accessed on 21 September 2025). Another is from the 3D Medical Image Reconstruction Dataset (https://www.ircad.fr/research/data-sets/, accessed on 21 September 2025). The third is from the ISIC 2024 Skin Image Archive (https://www.isic-archive.com/, accessed on 21 September 2025). The fourth is from Chest X-ray Pneumonia Dataset (https://www.kaggle.com/datasets/paultimothymooney/chest-xray-pneumonia, accessed on 21 September 2025).
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A. Specific Multi-Directional Diffusion Demonstration
In this appendix, we present a table demonstrating the specific multi-directional diffusion coefficients measured in our experiment.

Table A1.
Specific multi-directional diffusion demonstration.
Appendix B. Intermediate Ciphertext Representation of Example 2
In this appendix, we give some matrices calculated during the encryption process.

Figure A1.
Matrices , , , T, and showing intermediate transformations of Example 2.
Figure A1.
Matrices , , , T, and showing intermediate transformations of Example 2.
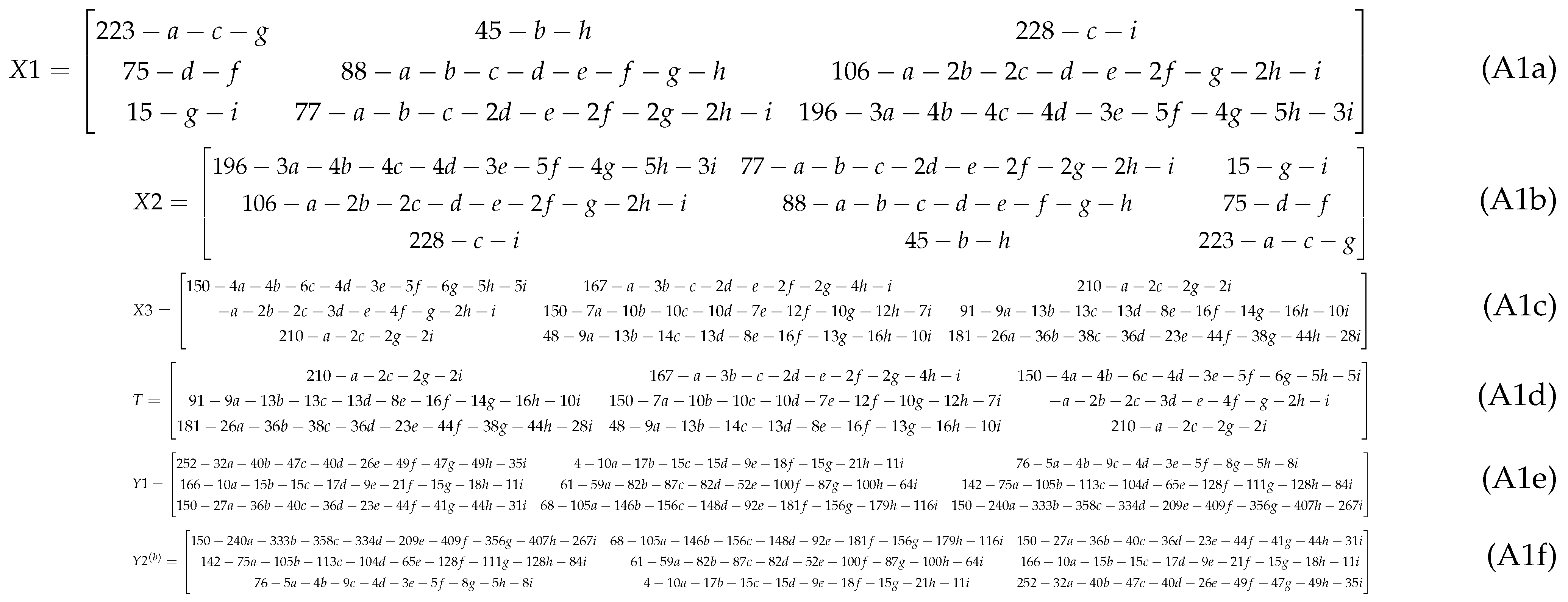
References
- Zinger, S.; Ruijters, D.; Do, L.; de With, P.H. View interpolation for medical images on autostereoscopic displays. IEEE Trans. Circuits Syst. Video Technol. 2011, 22, 128–137. [Google Scholar] [CrossRef]
- Liu, H.; Teng, L.; Zhang, Y.; Si, R.; Liu, P. Mutil-medical image encryption by a new spatiotemporal chaos model and DNA new computing for information security. Expert Syst. Appl. 2024, 235, 121090. [Google Scholar] [CrossRef]
- Kaissis, G.A.; Makowski, M.R.; Rückert, D.; Braren, R.F. Secure, privacy-preserving and federated machine learning in medical imaging. Nat. Mach. Intell. 2020, 2, 305–311. [Google Scholar] [CrossRef]
- Kaissis, G.; Ziller, A.; Passerat-Palmbach, J.; Ryffel, T.; Usynin, D.; Trask, A.; Lima, I., Jr.; Mancuso, J.; Jungmann, F.; Steinborn, M.M.; et al. End-to-end privacy preserving deep learning on multi-institutional medical imaging. Nat. Mach. Intell. 2021, 3, 473–484. [Google Scholar] [CrossRef]
- Ziller, A.; Mueller, T.T.; Stieger, S.; Feiner, L.F.; Brandt, J.; Braren, R.; Rueckert, D.; Kaissis, G. Reconciling privacy and accuracy in AI for medical imaging. Nat. Mach. Intell. 2024, 6, 764–774. [Google Scholar] [CrossRef]
- Data Encryption Standard. Data Encryption standard. Fed. Inf. Process. Stand. Publ. 1999, 112, 3. [Google Scholar]
- Paar, C.; Pelzl, J.; Paar, C.; Pelzl, J. The advanced encryption standard (AES). Understanding Cryptography: A Textbook for Students and Practitioners; Springer: Berlin/Heidelberg, Germany, 2010; pp. 87–121. [Google Scholar]
- Wang, X.; Zhao, M. An image encryption algorithm based on hyperchaotic system and DNA coding. Opt. Laser Technol. 2021, 143, 107316. [Google Scholar] [CrossRef]
- Yildirim, M. Optical color image encryption scheme with a novel DNA encoding algorithm based on a chaotic circuit. Chaos Solitons Fractals 2022, 155, 111631. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; Jiang, D. A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Inf. Sci. 2021, 574, 505–527. [Google Scholar] [CrossRef]
- Wang, C.; Song, L. An image encryption scheme based on chaotic system and compressed sensing for multiple application scenarios. Inf. Sci. 2023, 642, 119166. [Google Scholar] [CrossRef]
- Brahim, A.H.; Pacha, A.A.; Said, N.H. Image encryption based on compressive sensing and chaos systems. Opt. Laser Technol. 2020, 132, 106489. [Google Scholar] [CrossRef]
- Teh, J.S.; Alawida, M.; Sii, Y.C. Implementation and practical problems of chaos-based cryptography revisited. J. Inf. Secur. Appl. 2020, 50, 102421. [Google Scholar] [CrossRef]
- Upadhyay, D.; Gaikwad, N.; Zaman, M.; Sampalli, S. Investigating the avalanche effect of various cryptographically secure Hash functions and Hash-based applications. IEEE Access 2022, 10, 112472–112486. [Google Scholar] [CrossRef]
- Yuan, F.; Deng, Y.; Li, Y.; Chen, G. A cascading method for constructing new discrete chaotic systems with better randomness. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 053120. [Google Scholar] [CrossRef]
- Hamza, R.; Yan, Z.; Muhammad, K.; Bellavista, P.; Titouna, F. A privacy-preserving cryptosystem for IoT E-healthcare. Inf. Sci. 2020, 527, 493–510. [Google Scholar] [CrossRef]
- Mehdi, S.A.; Ali, Z.L. Image encryption algorithm based on a novel six-dimensional hyper-chaotic system. Al-Mustansiriyah J. Sci. 2020, 31, 54–63. [Google Scholar] [CrossRef]
- Liu, X.l.; Xu, K.s.; Kang, Z.c.; Xu, M.t.; Wang, M.m. New 2D inserting-log-logistic-sine chaotic map with applications in highly robust image encryption algorithm. Nonlinear Dyn. 2025, 113, 17227–17256. [Google Scholar] [CrossRef]
- Masood, F.; Boulila, W.; Alsaeedi, A.; Khan, J.S.; Ahmad, J.; Khan, M.A.; Rehman, S.U. A novel image encryption scheme based on Arnold cat map, Newton-Leipnik system and Logistic Gaussian map. Multimed. Tools Appl. 2022, 81, 30931–30959. [Google Scholar] [CrossRef]
- Chen, J.x.; Zhu, Z.l.; Fu, C.; Zhang, L.b.; Zhang, Y. An efficient image encryption scheme using lookup table-based confusion and diffusion. Nonlinear Dyn. 2015, 81, 1151–1166. [Google Scholar] [CrossRef]
- Grošek, O.; Sỳs, M. Isotopy of Latin squares in cryptography. Tatra Mt. Math. Publ. 2010, 45, 27–36. [Google Scholar] [CrossRef]
- Hu, G.; Xiao, D.; Wang, Y.; Li, X. Cryptanalysis of a chaotic image cipher using Latin square-based confusion and diffusion. Nonlinear Dyn. 2017, 88, 1305–1316. [Google Scholar] [CrossRef]
- Li, M.; Lu, D.; Xiang, Y.; Zhang, Y.; Ren, H. Cryptanalysis and improvement in a chaotic image cipher using two-round permutation and diffusion. Nonlinear Dyn. 2019, 96, 31–47. [Google Scholar] [CrossRef]
- Wu, W.; Wang, Q. Cryptanalysis and improvement of an image encryption algorithm based on chaotic and Latin square. Nonlinear Dyn. 2023, 111, 3831–3850. [Google Scholar] [CrossRef]
- Chen, Y.; Tang, C.; Ye, R. Cryptanalysis and improvement of medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process. 2020, 167, 107286. [Google Scholar] [CrossRef]
- Gaur, K.S.; Singh, H.; Thakran, S. Cryptanalysis of the optical cryptosystem titled “an asymmetric image encryption based on phase truncated hybrid transform”. J. Opt. 2024, 53, 605–609. [Google Scholar] [CrossRef]
- Lai, Q.; Hu, G.; Erkan, U.; Toktas, A. High-efficiency medical image encryption method based on 2D Logistic-Gaussian hyperchaotic map. Appl. Math. Comput. 2023, 442, 127738. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Kiefer, R.; Abid, M.; Steen, J.; Ardali, M.R.; Amjadian, E. A Catalog of Public Glaucoma Datasets for Machine Learning Applications: A detailed description and analysis of public glaucoma datasets available to machine learning engineers tackling glaucoma-related problems using retinal fundus images and OCT images. In Proceedings of the 2023 7th International Conference on Information System and Data Mining, Atlanta, GA, USA, 10–12 May 2023; pp. 24–31. [Google Scholar]
- Soler, L.; Hostettler, A.; Agnus, V.; Charnoz, A.; Fasquel, J.; Moreau, J.; Osswald, A.; Bouhadjar, M.; Marescaux, J. 3D Image Reconstruction for Comparison of Algorithm Database: A Patient Specific Anatomical and Medical Image Database; Technical Report; IRCAD: Strasbourg, France, 2010. [Google Scholar]
- International Skin Imaging Collaboration. ISIC Image Archive. 2024. Available online: https://www.isic-archive.com/ (accessed on 23 July 2024).
- Feng, W.; Zhang, J. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Zhang, D.; Chen, L.; Li, T. Hyper-chaotic color image encryption based on 3D orthogonal Latin cubes and RNA diffusion. Multimed. Tools Appl. 2024, 83, 22571–22594. [Google Scholar] [CrossRef]
- Mohamed, H.G.; ElKamchouchi, D.H.; Moussa, K.H. A novel color image encryption algorithm based on hyperchaotic maps and mitochondrial DNA sequences. Entropy 2024, 22, 158. [Google Scholar] [CrossRef]
- Raghuvanshi, K.K.; Kumar, S.; Kumar, S.; Kumar, S. Image encryption algorithm based on DNA encoding and CNN. Expert Syst. Appl. 2024, 252, 124287. [Google Scholar] [CrossRef]
- Cohen, I.; Huang, Y.; Chen, J.; Benesty, J.; Benesty, J.; Chen, J.; Huang, Y.; Cohen, I. Pearson correlation coefficient. In Noise Reduction in Speech Processing; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–4. [Google Scholar]
- Tan, R.C.; Lei, T.; Zhao, Q.M.; Gong, L.H.; Zhou, Z.H. Quantum Color Image Encryption Algorithm Based on A Hyper-Chaotic System and Quantum Fourier Transform. Int. J. Theor. Phys. 2016, 55, 5368–5384. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).