Abstract
With the rapid growth of Artificial Intelligence of Things (AIoT), identity management and trusted communication have become critical for system security and reliability. Continuous AI learning and large-scale device connectivity introduce challenges such as permission drift, cross-domain access, and fine-grained API calls. Traditional identity management often fails to balance privacy protection with efficiency, leading to risks of data leakage and misuse. To address these issues, this paper proposes a blockchain-based self-sovereign identity (SSI) management mechanism for AIoT. By integrating SSI with a zero-trust framework, it achieves decentralized identity storage and continuous verification, effectively preventing unauthorized access and misuse of identity data. The mechanism employs selective disclosure (SD) technology, allowing users to submit only necessary attributes, thereby ensuring user control over self-sovereign identity information and guaranteeing the privacy and integrity of undisclosed attributes. This significantly reduces verification overhead. Additionally, this paper designs a context-aware dynamic permission management that generates minimal permission sets in real time based on device requirements and environmental changes. Combined with the zero-trust principles of continuous verification and least privilege, it enhances secure interactions while maintaining flexibility. Performance experiments demonstrate that, compared with conventional approaches, the proposed zero-trust architecture-based SSI management mechanism better mitigates the risk of sensitive attribute leakage, improves identity verification efficiency under SD, and enhances the responsiveness of dynamic permission management, providing robust support for secure and efficient AIoT operations.
1. Introduction
With the deep integration of artificial intelligence (AI) and the Internet of Things (IoT), intelligent Internet of Things (AIoT) is rapidly transforming how we live and work from smart homes and intelligent transportation to industrial automation. However, the rapid development of AIoT has also led to the continuous expansion of device connectivity and increased complexity in cross-domain collaboration. Consequently, identity management and interaction trust have become core challenges for reliable system deployment [1]. Against the backdrop of continuously learning AI models and massively interconnected IoT devices, identity management demands in AIoT scenarios, such as fine-grained verification, dynamic authorization, and cross-domain data access are intensifying the risk of privacy data breaches [2]. These challenges are further compounded by the sheer volume of devices and the dynamic nature of AIoT environments, making traditional identity management mechanisms increasingly inadequate, while existing identity management mechanisms remain inadequate when confronting complex security threats. In AIoT environments, novel threats frequently emerge, including adversarial sample attacks [3] and model inversion attacks [4]. These challenges expose the limitations of existing identity management solutions.
As an emerging identity management paradigm, Self-Sovereign Identity (SSI) breaks the data monopoly of traditional identity management mechanisms [5]. The core concept of SSI is to grant entities full control over their identity data, enabling decentralized identity verification, storage, and management through blockchain technology [6]. This effectively avoids issues such as single points of failure and data breaches faced by traditional centralized identity mechanisms in IoT environments [7]. SSI achieves a dynamic equilibrium between data sovereignty and flexible authorization through distributed identity frameworks [8]. Meanwhile, the zero-trust security framework significantly mitigates potential security threats during interactions by implementing stringent identity authentication, access authorization, and real-time risk assessment [9], offering an innovative solution for identity management within AIoT environments [10,11]. By combining the zero-trust model with SSI, this framework strengthens the security and reliability of identity verification, making it suitable for complex, distributed AIoT ecosystems. In the SSI management mechanism, integrating the zero-trust continuous verification mechanism [12] into identity management enables rigorous validation of each access request and dynamic permission control [13]. This ensures a high-security match between device identities and AIoT resources, preventing unauthorized access and data leakage [14]. Simultaneously, dynamic identity attribute verification allows the system to flexibly adjust access policies based on device behavior.
However, current SSI implementations within zero-trust frameworks require the submission of complete identity information for management, lacking the capability to selectively provide partial identity attributes based on actual needs [15,16]. This creates a privacy gap, as users are required to reveal more information than necessary for identity verification. Additionally, the continuous verification mechanism advocated by the zero-trust architecture necessitates frequent identity checks, which significantly increases computational and communication overhead in AIoT scenarios involving massive device connectivity, high-frequency sensor data interactions, and real-time decision-making, thereby impacting the overall verification efficiency of the system [17]. These challenges are further amplified in AIoT environments, where the continuous learning of AI models and the dynamic data requirements of IoT devices introduce multidimensional complexities. As models iterate and data changes, permission management faces issues like permission drift, and adversarial attacks from generative AI threaten the reliability of identity verification. Meanwhile, the high cost and inefficiency of traditional PKI on edge devices require balancing trust mechanisms and resource consumption when applying zero-trust architectures in AIoT [18]. Meanwhile, as the scale of AIoT edge devices grows exponentially, the demand for real-time and lightweight identity verification mechanisms continues to rise. How to leverage blockchain to construct an identity management framework that supports massive device access, low-latency identity negotiation, and distributed reputation evaluation, while ensuring identity privacy and security, has become a core issue in the field of AIoT security [19].
To address this issue, this paper proposes a blockchain-based SSI management mechanism for AIoT. By integrating SSI with a zero-trust framework, it enables decentralized identity storage and continuous verification, effectively preventing unauthorized access and identity data misuse [20,21]. This mechanism leverages Selective Disclosure (SD) technology, allowing users to submit only necessary attributes. This ensures users retain control over their identity information while safeguarding the privacy and integrity of undisclosed attributes, significantly reducing verification overhead [22]. Additionally, this paper designs a context-aware dynamic permission management scheme that generates minimal permission sets in real-time based on device requirements and environmental changes. By integrating zero-trust continuous verification with the principle of least privilege, it enhances secure interactions while maintaining flexibility. Experimental results demonstrate that, compared to traditional identity management systems, the proposed mechanism significantly reduces the risk of sensitive data exposure while improving authentication efficiency. Performance experiments demonstrate that compared to traditional methods, the proposed zero-trust-based self-sovereign identity management mechanism more effectively mitigates the risk of sensitive attribute leakage. It enhances authentication efficiency under SD and improves the responsiveness of dynamic permission management, providing robust support for the secure and efficient operation of AIoT. The key innovations are as follows:
- (1)
- Design of a zero-trust and blockchain-based SSI integration framework. By combining the SSI with zero-trust SSI, this framework establishes trusted device identity management and real-time permission verification mechanisms within the continuous verification process, laying the foundational trust for AIoT environments.
- (2)
- The proposal of a selective disclosure SSI management mechanism. It allows users or devices to disclose only the minimum necessary identity information. Leveraging blockchain technology together with cryptographic commitments, aggregated signatures, and Zero-Knowledge Proofs (ZKP), the mechanism enables efficient attribute-based authentication while avoiding the exposure of sensitive information, thus improving both privacy protection and verification efficiency in high-concurrency AIoT scenarios.
- (3)
- The proposal of a dynamic permission management mechanism combining context awareness and SD technology. This mechanism dynamically adjusts access permissions based on device behavior, network conditions, and AI task requirements. It enforces fine-grained least-privilege control, thereby effectively preventing identity misuse and privilege escalation.
2. Related Work
2.1. Self-Sovereign Identity Management in the IoT
Blockchain, as one of the key technologies supporting SSI, provides a decentralized and tamper-proof ledger. In the IoT environment, blockchain can offer each device a unique identity and ensure the authenticity and immutability of these identities. In recent years, many studies have explored the application of blockchain and SSI in IoT, particularly in identity management, privacy protection, and security enhancement. Fedrecheski et al. [23] proposed an authentication scheme that combines decentralized identifiers (DID) and verifiable credentials (VC), allowing IoT devices to confirm their identities and exchange data without relying on centralized services. This effectively enhances privacy protection and security in the system, making it especially suitable for IoT environments that require high privacy protection. Popa et al. [24] proposed a SSI management framework combined with blockchain technology, aimed at strengthening the protection of digital identities of online users. This framework prevents unauthorized data collection and sharing through a decentralized approach, effectively preventing identity theft and fraud, making it particularly suitable for internet platforms that require high data privacy protection. Bartolomeu et al. [25] proposed an identity management solution based on the SSI paradigm. This solution allows devices to fully own and manage their digital identities through decentralization, avoiding the single point of failure and scalability issues inherent in traditional centralized identity management systems, thereby improving system security and scalability. Weingaertner et al. [26] proposed an IoT device ownership management solution based on SSI, combining blockchain, DID, and VC to achieve secure and user-centric device identity management. The solution ensures the security and effectiveness of device ownership transfer through system architecture design and protocol verification tools like ProVerif. Sakib et al. [27] proposed an identity management solution based on blockchain and DID, which stores device identities in a trusted execution environment and protects them through blockchain. This allows devices to trace their origin and prevents unauthorized ownership transfer, thereby solving the problem of reliable identification of IoT devices. These studies highlight the strong potential of SSI and blockchain for securing IoT environments, especially by decentralizing control and enabling enhanced privacy. However, most of these approaches focus on static identity verification and lack real-time, dynamic permission management, which is increasingly critical in AIoT environments.
2.2. Decentralized Identity Management in AI Environments
In the context of the rapid development of AI technologies, decentralized identity management (DIM) is becoming a key solution for ensuring data privacy and security. In this environment, AI applications not only enhance the efficiency and security of identity verification but also contribute to the creation of a more transparent and equitable identity management system. Kaul et al. [28] proposed an AI-driven decentralized authentication system that combines AI with homomorphic encryption, allowing encrypted data to be processed without decryption, thus reducing the risk of data leakage. Even in attacked environments, the system ensures secure and robust identity verification while protecting data confidentiality. Chamola et al. [29] designed a decentralized medical record management framework based on AI and blockchain, utilizing AI technologies such as optical character recognition (OCR) to process and store medical records. All data are securely stored on the blockchain network, ensuring the protection of patient personal information while enabling healthcare professionals to quickly access critical information in emergency situations. While existing AI-powered decentralized identity systems have enhanced data security, they still face issues such as efficiency bottlenecks and lack of user control. In contrast, SSI management in AI environments achieves true user control over identity data while ensuring authentication efficiency through credential protocols and verification mechanisms. Le et al. [30] introduced a blockchain-based SSI management system, which integrates AI algorithms to effectively identify and extract ID card fields, facilitating OCR and identity verification, and uses ZKP to ensure secure identity verification. Mamoshina et al. [31] proposed a decentralized personal health data ecosystem based on blockchain and deep learning, aimed at accelerating biomedical research and empowering patients with control over their personal data. This system promotes drug discovery and preventive healthcare through a secure and transparent data marketplace while addressing regulatory challenges to ensure the privacy and security of personal data. Nash [32] proposed a Decentralized Intelligence Network framework, which ensures data sovereignty through personal data storage, utilizes blockchain and federated learning protocols to achieve decentralized AI training, and ensures system fairness and security through encrypted reward mechanisms and decentralized auditing, giving participants control over their data and financial benefits. These works demonstrate the emerging role of decentralized identity management in AI environments, but they often face challenges related to scalability and the lack of a unified framework for real-time identity validation in dynamic, high-concurrency contexts like AIoT.
2.3. Zero-Trust-Based Self-Sovereign Identity Management
Although SSI management systems provide greater data control and privacy protection, combining them with the zero-trust model can further enhance the security and reliability of identity verification. The zero-trust model emphasizes always verifying every request rather than relying on traditional trust mechanisms, making DIM systems more secure and reliable in terms of identity verification and access control. Therefore, Nasrin [33] proposed a secure data retention model based on the zero-trust framework, combining SSI management and the permissioned blockchain Hyperledger Fabric to achieve digital identity verification and data sharing in a distributed environment, significantly enhancing user privacy protection and system security. Murcia et al. [14] proposed a DIM solution based on the zero-trust framework, building an identity ecosystem through blockchain and privacy protection technologies, and combining the principles of SSI to enable seamless cross-domain identity verification and authorization, enhancing security and user privacy protection. The rise of SSI under the zero-trust model marks a paradigm shift in identity management from passive defense to active control. By combining decentralized technologies with privacy protection, SSI not only ensures the security of user data but also empowers users with control over their identities. However, most of the current zero-trust-based SSI models still require complete identity disclosure, limiting the effectiveness of privacy preservation. Additionally, many of these models do not fully address the real-time and dynamic nature of AIoT environments, where access needs to be continuously monitored and permissions adjusted rapidly in response to device behavior and environmental changes.
3. Blockchain-Based Self-Sovereign Identity Management Mechanism
3.1. Mechanism Overview
This mechanism introduces a blockchain-based SSI management for AIoT environments, addressing challenges like dynamic permission drift, high-concurrency inference, and supply chain trustworthiness during collaborative AI model training, distributed inference, and continuous learning processes at the edge devices in AIoT environments. It leverages SSI management, SD technology, and dynamic permission management to construct a secure, efficient, and privacy-preserving authentication mechanism for IoT devices. The specific mechanism model is shown in Figure 1, it mainly consists of the following four entities.
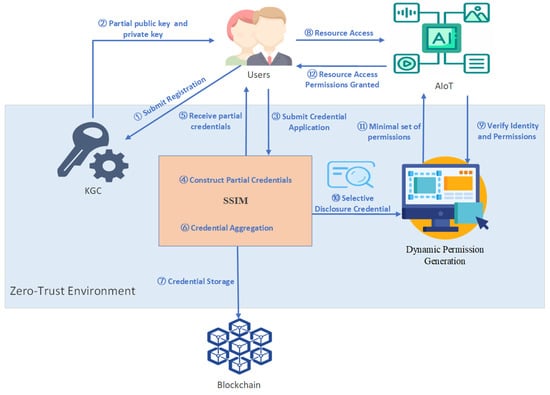
Figure 1.
Mechanism model.
- Key Generation Center (KGC) [34]: An entity responsible for assisting in the generation and management of keys within a decentralized network.
- Users: The owner and user of identity information, serving as the core of the entire mechanism. It is responsible for generating local portions of private and public keys and submitting registration requests to the KGC to complete identity initialization.
- Blockchain: Serves as the underlying technology for decentralized storage and management of credentials.
- AIoT Devices/Resources: The objects users ultimately access and interact with.
Additionally, it is composed of two key processes:
- Self-Sovereign Identity Management Mechanism (SSIM): The core logic module for handling identity credentials, responsible for constructing, aggregating, and validating credentials.
- Dynamic Permission Generation Mechanism: This module is critical for implementing zero-trust “continuous verification” and the principle of least privilege. It handles real-time decision-making and permission management while enforcing access control.
The key pair generation and registration process begins with the user. The user first generates a partial key pair locally, ensuring the core private key remains under their control. The user then submits their identity identifier and partial public key to the KGC for registration. Upon receiving the request, the KGC generates the corresponding system partial key and securely returns it, but does not store the full key. Only the user can combine the received partial key with their own to form a complete key pair, thus completing identity initialization and gaining full self-sovereign control over their digital identity. The detailed process can be found in Section 3.2.
When the user needs to prove a specific identity attribute, the credential generation process begins. The user selects the necessary attributes, creates encrypted commitments using zero-knowledge proof, and submits the application to the SSIM. After validating the request, partial credentials for each attribute are generated and sent to the user. The user then aggregates these partial credentials into a complete credential. To ensure immutability and decentralized management, the final credential is securely stored on the blockchain. Steps 3 to 7 in Figure 1 illustrate this process, with details provided in Section 3.3.
In the resource access process, the user initiates a request to the target AIoT device. The device then asks the dynamic permission generation module for identity verification and an access permission set. Based on the scenario, the user generates a selective disclosure credential with only the minimum required attributes and submits it. The module verifies the credential to confirm the user’s identity, then evaluates the current context to dynamically calculate a minimized permission set. Finally, the module grants the user temporary, precise permissions to interact with the AIoT device under controlled conditions, completing the zero-trust loop. Steps 8 to 12 illustrate this process, with details in Section 3.4.
Overall, the mechanism integrates zero-trust security with blockchain-based self-sovereign identity, ensuring secure dynamic access control in AIoT environments while enhancing user privacy and data autonomy. With blockchain’s decentralized trust, efficient SD, and context-aware permissions, it provides strong identity assurance for the secure development of future AIoT ecosystems.
3.2. User Identity Registration and Key Generation
3.2.1. Parameter Generation
This mechanism is initialized by a decentralized network (such as a blockchain or distributed trust network) with parameters, setting a t-bit prime number (a sufficiently large prime) and a generator P as security parameter inputs. It will return the public parameters and the confidential private key y, with the symbol list as shown in Table 1.

Table 1.
Symbol interpretation table.
- Set a t-bit prime number p and a generator P.
- Define the additive cyclic group and the elliptic curve .
- Choose the master private key denoted as , which is jointly selected by the decentralized network or generated through distributed key generation. The system’s public key is computed as .
- Choose four secure hash functions to support subsequent operations such as identity generation, encryption, and signing. Now, the system publishes the parameters and keeps y confidential.
3.2.2. User Node Registration
Each user node generates its own key pair locally. It randomly selects a private key and computes the corresponding partial public key . The node also has an identifier for registration. The user sends and to the KGC to register. The KGC then generates a temporary private key and computes the system’s partial public key, Equation (1):
Then, the KGC uses the user’s identity identifier , the system’s partial public key , and the user’s submitted local partial public key , along with the system’s master private key y, to generate the user’s partial private key, as Equation (2).
Through this process, the KGC provides the user with the system’s partial public key and the user’s partial private key. The user can subsequently use this data to complete the generation and verification of the full key, enabling identity authentication and management in a zero-trust environment.
3.2.3. Complete Key Pair Generation
Upon receiving and from the KGC, the user first verifies their correctness using the Equation (3):
If the verification is successful, the user combines the user’s partial private key with the locally generated private key to generate the complete private key . Meanwhile, the user’s complete public key is composed of the local partial public key and the received system partial public key , forming . The specific key generation process is shown in Figure 2.
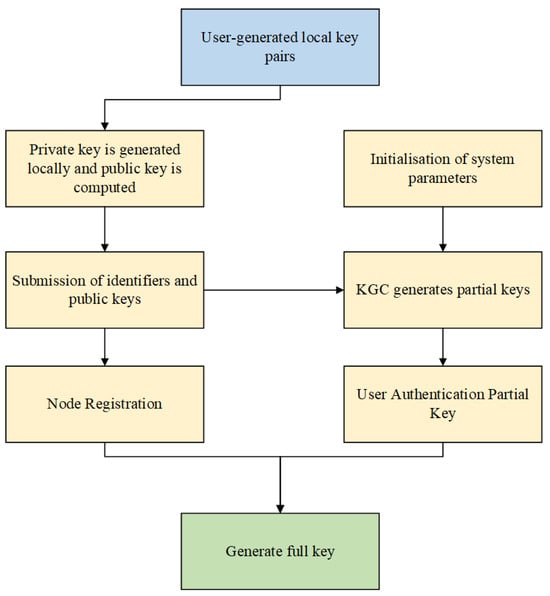
Figure 2.
Key generation process.
3.3. Construction and Aggregation of Selective Disclosure Credentials
The SD credential mechanism enables privacy preservation and efficient authentication in zero-trust settings. It allows users to choose which identity attributes to reveal in each scenario, while using cryptographic commitments and ZKP to ensure the integrity and validity of hidden data. This approach effectively meets the dynamic needs of devices. This section details the construction and aggregation of such credentials, as illustrated in Figure 3:
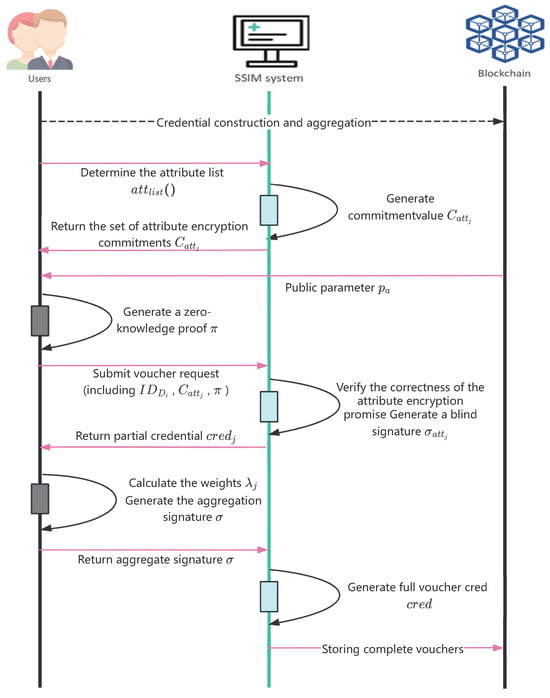
Figure 3.
Construction and aggregation of SD credentials.
3.3.1. Credential Construction
Credential construction is the initial phase of SD, generating credentials that contain only selected attributes while protecting undisclosed ones. The process involves user–system interaction, including identity submission, attribute verification, and partial credential generation.
(1) User generates attribute list
First, the user determines the attribute list to be authenticated . These attributes may include geographic location, network permission levels, and other device-related important information. To protect the privacy of these attributes, the user generates a commitment value for each attribute through a cryptographic commitment mechanism. The computation of the commitment value is shown in Equation (4):
where are system generators, usually base points in elliptic curve cryptosystems, is the attribute value, and is a random number used to ensure that each computed commitment value is non-repeatable and unpredictable.
(2) Submit credential application
After generating the identity identifier and the attribute commitment set , user needs to submit a credential application to the system. The submitted content includes the following: the identity identifier , which indicates the unique identity of the user; the attribute commitment set , used to protect user attributes under privacy; and the ZKP , used to prove the validity of the attribute values without revealing the specific values. The ZKP is generated as in Equation (5):
where is the user’s private key, generated during the key generation phase; is the system’s public parameters, published by the blockchain system. The purpose of the ZKP is that the user can prove knowledge of the attributes to the system without directly disclosing the attribute values. Specifically, this proof can ensure that belongs to the valid range of values defined by the system and is consistent with the submitted commitment value .
(3) System verifies attributes and generates partial credentials
After receiving the credential application from user , the system needs to verify the correctness of the attribute commitments and generate a blind signature, finally producing partial credentials.
First, the system verifies whether the submitted commitment value is consistent with the submitted ZKP and the system parameters. Verification is performed using Equation (6):
where e is a bilinear mapping function, ensuring correctness of the verification process, is the system public key, derived from the system’s master private key y, and is the public key part corresponding to the user attribute , which helps verify the integrity of the disclosed attribute, ensuring it has not been tampered with.
After successful verification, the system generates a blind signature. For the attributes selected by the user for disclosure, the system uses its private key y to generate blind signatures. The blind signature is computed as in Equation (7):
where is the hash value of attribute , used to ensure uniqueness of the signature; is the random number from the cryptographic commitment; and y is the system’s private key. The blind signature ensures the privacy of the undisclosed attributes while guaranteeing the integrity of the disclosed attributes.
Finally, the system generates partial credentials for the user, as shown in Equation (8):
(4) User receives partial credentials
User receives the partial credential set from the system. These partial credentials are generated only for the attributes chosen by the user to disclose, while the privacy of the undisclosed attributes is preserved. The partial credential set is shown in Equation (9):
where N is the number of partial credentials generated by the system. Each partial credential includes a blind signature () and a cryptographic commitment (), ensuring that only the disclosed attributes are verified, and the privacy of undisclosed attributes is preserved. These partial credentials are used in the subsequent credential aggregation phase to generate a complete credential.
3.3.2. Credential Aggregation
Credential aggregation combines multiple partial credentials, generated for user-selected attributes, into a complete credential for identity verification and authorization. In a zero-trust environment, it must maintain mathematical validity, consistency, and integrity, while prioritizing user privacy.
(1) Aggregation Background and Objectives
In the credential aggregation scenario, user receives n partial credentials from the system. These partial credentials are generated for the user’s SD attribute list . The goal of aggregation is to combine these n partial credentials into a complete credential . The entire aggregation process must ensure mathematical correctness, improve verification efficiency, and reduce the risk of privacy leakage.
(2) Weight Calculation
In credential aggregation, the user needs to weight the n partial signatures generated by the system. This requires the use of Lagrangian interpolation [35] to compute the weight for each partial signature. The weight calculation is shown in Equation (10):
where , and p is a large prime number set by the system. The role of the weight is to assign a mathematical proportion to each partial signature, ensuring consistent contribution during the aggregation process. According to the above formula, the weight corresponding to each partial signature is uniquely determined, and these weights will be used for subsequent weighted signature computation.
(3) Aggregated Signature Generation
The user combines each partial signature with its corresponding weight to generate the final aggregated signature . The computation of the aggregated signature is shown in Equation (11):
The aggregated signature simplifies handling multiple partial credentials while protecting user privacy. By performing weighted combinations of each blind signature, the aggregated signature can prove the integrity and validity of the disclosed attributes without directly revealing the attribute values. At the same time, this method guarantees the unforgeability and security of the signature.
The aggregated signature allows the user to verify with a single signature instead of multiple partial ones, simplifying verification, reducing computational overhead, and improving efficiency.
(4) Generation of Complete Credential
After generating the aggregated signature , the user combines it with the attribute commitment set and the ZKP to form the complete credential . The inclusion of the ZKP ensures that even if some attributes are undisclosed, the verifier can still validate the legitimacy of those undisclosed attributes. The structure of the complete SD credential is shown in Equation (12):
The complete credential, with the aggregated signature and ZKP, enables efficient identity authentication while ensuring the unforgeability and integrity of SD credentials. Credential aggregation combines partial signatures into one, allowing a single verification, reducing computational cost, and improving efficiency. It also enhances privacy by allowing authentication without disclosing specific attributes, with cryptographic commitments and the aggregated signature protecting undisclosed information, while the ZKP further strengthens privacy.
(5) Security and Efficiency Comparison of Aggregation Schemes
The advantages of using Lagrangian interpolation for credential aggregation are shown through a systematic comparison with mainstream schemes in Table 2. Compared with RSA batch verification, which is susceptible to common-modulus attacks [36], ECDSA + Merkle trees face second-preimage collision risks [37], and the BLS aggregation scheme in [38] suffers from a k-aggregation forgery vulnerability.

Table 2.
Signature aggregation schemes comparison.
In AI environments with complex and evolving authentication scenarios, the proposed Lagrangian interpolation–based credential aggregation exhibits key advantages: on security, the threshold mechanism enforced by the mathematical constraint requires an adversary to compromise nodes to forge a valid signature, raising the break difficulty by a factor of over traditional BLS aggregation and making it, at present, the only aggregation method that satisfies the EU-CMA security model. On efficiency, dynamically computed Lagrange weights avoid the storage overhead of Merkle trees; a fixed-size aggregated signature significantly reduces transmission load; and verification with a single bilinear pairing equation markedly improves processing throughput.
Meanwhile, the ability to add or remove signers in real time, together with online weight updates, enables rapid adjustment of authentication strategies in dynamic settings such as model training and federated learning. Its lightweight design fits the resource constraints of edge devices, and the minimized interaction complexity supports high-concurrency authentication. Finally, combining Lagrangian interpolation with blind signatures—under the mathematical guarantee that assigns a unique weight to each partial signature—not only prevents tampering and reuse but also achieves dual reinforcement of privacy protection and system security through credential aggregation, providing a scalable identity management infrastructure for AI environments.
3.3.3. Credential Verification and Tracking
In the verification and tracking phase, the user uses the aggregated complete credential to complete the identity verification. During the verification process, the user selectively discloses certain identity attribute information based on actual needs and, through ZKP, demonstrates the integrity and legality of undisclosed attributes. For example, the user can prove they possess a specific identity or attribute without disclosing all personal information. This not only enhances the protection of user privacy but also ensures that the verifier can confirm the user’s legitimacy and authenticity without knowing the full identity information.
The verifier uses the ZKP and signature in the credential to verify the user’s identity, ensuring that the credential has not been tampered with and that it meets the original issuance conditions. After successful verification, the verifier generates an interaction token for subsequent authorization operations. This token may include access rights and other information, ensuring that the user can only access the resources they are authorized to.
3.4. Dynamic Permission Management
Dynamic permission management is essential in zero-trust architectures for secure and adaptive control in the AIoT. It dynamically generates minimal permission sets based on selectively disclosed credentials and contextual data, balancing security and flexibility. By integrating credential verification, permission evaluation, policy configuration, and dynamic permission algorithms, the system enables fine-grained access control. The following sections detail these core processes and technical implementations.
3.4.1. Credential Verification
Credential verification confirms the legitimacy and integrity of the user’s disclosed attributes and device identity within a zero-trust framework. This is achieved through aggregated signature verification, attribute commitment checks, and ZKP.
The aggregated signature is the core part of the SD credential submitted by the user, representing the legality and completeness of the disclosed attributes. During the verification process, the system extracts the list of attributes disclosed by the user and their corresponding weights from the credential. Then, the system computes the hash value for each attribute and uses the system generator g and the public key to construct the verification Equation (13):
In this formula, the left side, , represents the information extracted by the system from the aggregated signature submitted by the user, along with the result of the bilinear mapping between the system generator g and the public key . The right side is the mathematical construction based on the hash value of the disclosed attribute , the system’s public key , and the Lagrange interpolation weights . If the verification passes, it indicates that is a valid signature, proving that the attributes disclosed by the user are complete and have not been tampered with.
Next, the system verifies the attribute commitments which protect the privacy of undisclosed attributes while ensuring the integrity of disclosed ones. The commitment is defined as Equation (14):
where g and h are system generators, is the attribute, and is a random number. Verification of the commitment is performed using Equation (15):
The system first extracts from the commitment value submitted by the user and reconstructs the right-hand side of the verification expression using the disclosed attribute value . The left side, , is the result of the computation based on the user’s submitted commitment value and the system generator. If the equation holds, it indicates that the encryption commitment is consistent with the disclosed attribute and has not been tampered with, proving the legitimacy of the encryption commitment.
Finally, the system uses a ZKP verification algorithm, , to check the commitments and random numbers associated with undisclosed attributes, as in Equation (16):
The key aspect of the verification process is that the user does not need to directly expose the specific values of the undisclosed attributes but instead uses ZKPVerify to verify whether the user possesses the legitimate knowledge of these attributes. The system ensures that the undisclosed attributes meet the rules defined by the system while protecting the user’s privacy by extracting the encryption commitment and the random number , and combining them with the hash value to compute the result of the verification formula.
The integrity of credential verification guarantees the reliability of the SD credential, while the use of encryption commitments and ZKP maximizes the protection of user privacy.
3.4.2. Permission Evaluation Based on Selective Disclosure Credentials
After credential verification is completed, the system needs to evaluate the user’s permission request based on the SD credential submitted by the user. The core goal of permission evaluation is to dynamically generate the least privilege set based on the disclosed attribute set and the requested resources and operations, thereby adhering to the principle of least privilege. This process involves attribute disclosure extraction, resource matching, and operation evaluation, while dynamically adjusting user permissions using context-aware technology.
The system extracts the disclosed attribute set from the user’s credential and compares it with the resource requirements in the system’s resource permission matching table . The formula for resource permission matching is as Equation (17):
where is the set of attributes required for resource . For the resource requested by the user, if the disclosed attribute set contains , the user is granted access to that resource.
Next, the system evaluates the requested operation, , by checking if the user’s attributes meet the operation’s required permissions, , as defined in the operation permission mapping table, . The formula for operation permission evaluation is as Equation (18):
If the disclosed attribute set by the user meets the required permission set for the operation, the user is granted permission to perform the operation. Additionally, during the permission evaluation process, the system dynamically adjusts permissions by incorporating context-aware technology. The system dynamically evaluates permissions by monitoring information such as the user’s device location, network environment, and time. The formula for context-aware permission adjustment is as Equation (19):
where is the initial permission set matched for the user, and is the valid permission set under the current context. If the user’s contextual state changes, the system will automatically revoke the relevant permissions.
Finally, the system generates the user’s least privilege set based on the disclosed attributes and context-aware information. The formula for generating the least privilege set is as Equation (20):
This process ensures that the user can only access resources that match their disclosed attributes and perform legitimate operations, while avoiding over-allocation and abuse of permissions.
3.4.3. Dynamic Policy Configuration
Using selectively disclosed credentials and context-aware technologies, the system dynamically configures access policies under least privilege in zero-trust environments, ensuring resource security and operational legitimacy. Dynamic policy configuration uses real-time context monitoring to evaluate the user’s state. These parameters are compared with policy rules to adjust privileges as needed, expressed in Equation (21):
where represents the set of valid permissions under the current context, while , , , and denote the user’s geographic location, time, network environment, and device state, respectively. The function f is a predefined set of rules that maps contextual information to specific permission configurations.
When the context changes, the system dynamically adjusts the user’s permission set according to contextual rules. The specific adjustment is defined in Equation (22):
where is the context-adjusted permission set, is the initially matched permission set, and is the valid permission set derived from context-awareness rules. By continuously monitoring context, the system ensures that user permissions always comply with the current environment, preventing privilege misuse.
In dynamic policy configuration, permission lifecycle management is another critical mechanism. It is particularly important for temporary tasks, time-limited inference API trials, and access control during model update windows. Each permission granted to a user is associated with a lifecycle , which restricts the validity period of the permission. For example, when a user requests access to a resource, the system assigns a validity interval , and automatically revokes the permission once is reached. Lifecycle management is formalized as in Equation (23):
where is the set of valid permissions within their lifecycle, is the current time, and is the expiration time of permission .
Dynamic policy configuration aims to ensure flexible and secure access control using real-time context-awareness and lifecycle management. This approach enhances system adaptability and responsiveness, providing strong protection in complex AIoT environments.
3.4.4. Dynamic Permission Generation Algorithm
The dynamic permission generation algorithm generates the least privilege set in real time based on the user’s submitted SD credential and current contextual information, ensuring that the user only has the necessary permissions to fulfill the operational requirements without exceeding the required scope. The dynamic permission generation algorithm integrates credential verification, permission evaluation, and context-aware technology to dynamically compute the user’s permission set, ensuring the security and efficiency of the environment.
The core idea of dynamic permission generation is to generate the least privilege set based on the user’s disclosed attributes, requested resources, and operation types. The algorithm’s input includes the user’s disclosed attribute set , the resource permission requirement table R, the operation permission requirement table Ops, and contextual information . The output is the user’s least privilege set , which represents the operations the user can perform and the resources they can access in their current environment.
The first step of the algorithm is to initialize the user’s permission set. The system extracts all possible permission items from the resource permission requirement table R and the operation permission requirement table , and filters out the initial permission set Perm that meets the conditions based on the user’s disclosed attribute set . The specific filtering formula is as Equation (24):
where is the set of attributes required for resource , and is the set of permissions required for operation .
The system then dynamically adjusts using context-awareness, incorporating real-time environmental factors (e.g., location, time, network status). This adjustment is formalized in Equation (25), where represents the contextually valid permissions, adapting dynamically to environmental changes.
where is the valid permission set under the context rules. The context rules dynamically change based on specific environmental requirements. For example, when the user enters or leaves a particular geographic area, the permission set is updated accordingly.
After the context adjustment is complete, the system optimizes the permission set based on the principle of least privilege, generating the user’s least privilege set . The formula for optimizing the least privilege set is as Equation (26):
where n is the number of resources or operations requested by the user, and and are the permission requirements for the resources and operations, respectively. The overall process of the dynamic permission generation algorithm is as follows (Algorithm 1):
| Algorithm 1 Dynamic permission generation algorithm |
|
The Algorithm 1 ensures secure and timely privilege assignment through adaptive context-aware adjustment, enabling efficient permission management in data interactions and enhancing the security and privacy protection of IoT devices.
4. Security Analysis
Ensuring secure identity authentication and permission control in AIoT environments requires robust mechanisms for key generation, credential management, SD, and access control. Given the scale of user data, model parameters, and real-time inference requests, a highly secure framework is essential to protect privacy, enforce precise access policies, and resist attacks. This work analyzes key security properties—including the strength of key generation, the privacy of SD credentials, the validity of aggregated signatures, and the correctness of dynamic permission algorithms—to demonstrate strong resilience against threats in AIoT environments.
4.1. Security of Key Generation
Theorem 1.
Under the hardness assumption of the Elliptic Curve Discrete Logarithm Problem (ECDLP), an adversary cannot derive the master private key y or the user private key from the public system parameters .
Proof.
The security of key generation relies on the hardness of ECDLP. First, the system master private key y is generated through a distributed key generation protocol in a decentralized network, with the corresponding public key . If an adversary attempts to reverse-engineer y from and P, they must solve the ECDLP. Since elliptic curve parameters (e.g., NIST P-256 curve) are designed to meet computational security assumptions, no polynomial-time algorithm exists to efficiently solve the ECDLP. Therefore, the master private key y is computationally infeasible to break. □
For the user private key , its generation also depends on the hardness of ECDLP. The user locally generates and computes the public key . Even if an adversary obtains , they cannot derive in polynomial time. In addition, the partial private key generated for the user by the KGC is constructed using the temporary private key , the master private key y, and a hash function, as shown in Equation (27):
where is randomly generated and kept secret by the KGC, with the corresponding public key . Since the security of also relies on the ECDLP, an adversary cannot obtain from , and therefore cannot separate y or from . Finally, the user verifies the partial private key through the equation , which does not leak any private key information. In conclusion, the key generation mechanism possesses unforgeability under the ECDLP assumption.
Simulation of Adversarial Attack Proof: Suppose an adversary attempts to derive the master private key y or user private key from the public parameters and partial public key . obtains and , but due to the hardness of the ECDLP, cannot compute y or . Even if intercepts the partial private key , since it is a linear combination of and y, with being unknown, cannot separate y or . Therefore, the key generation mechanism effectively resists such attacks.
4.2. Privacy of Selectively Disclosed Credentials
Theorem 2.
For undisclosed attributes , the commitment computationally hides , and the ZKP π satisfies the zero-knowledge property, i.e., an adversary cannot distinguish between a real proof and a simulated proof.
Proof.
The privacy of selectively disclosed credentials rests on the Pedersen commitment scheme and ZKP. For an undisclosed attribute , its commitment is . The Pedersen commitment’s perfect hiding property, stemming from the random value , prevents an adversary from extracting from . This is because solving for would require breaking the discrete logarithm assumption. □
Furthermore, the non-interactive ZKP ensures that no information about is leaked. A simulator can produce a simulated proof that is computationally indistinguishable from a real proof without any knowledge of the actual attribute . An adversary attempting to analyze the commitment and the proof cannot differentiate between a real proof and a simulated one, and thus cannot learn the value of the undisclosed attribute. This guarantees the privacy of the selectively disclosed credentials.
4.3. Validity of Aggregate Signatures
Theorem 3.
Let be the aggregate signature, where are Lagrange coefficients. Then σ satisfies the verification Equation (28):
Proof.
The validity of aggregate signatures relies on the mathematical properties of bilinear maps and the correctness of Lagrange interpolation. Each partial signature is generated using the master private key y and the attribute hash in the form . The aggregate signature is the weighted product of these partial signatures, as shown in Equation (29):
The verification process uses the bilinear property . The left-hand side of the verification equation is computed as in Equation (30):
The right-hand side expands based on the master public key , as shown in Equation (31):
Since Lagrange interpolation requires , when satisfy the interpolation conditions, the exponent terms and remain consistent under bilinear mapping, thus ensuring the equality holds. Therefore, the aggregate signature is mathematically valid and unforgeable. □
4.4. Correctness of the Least Privilege Principle
Theorem 4.
The output of the dynamic permission generation algorithm satisfies the following:
- (1)
- Completeness: All necessary permissions are included;
- (2)
- Minimality: No redundant permissions exist.
Proof.
Dynamic permission generation achieves the least-privilege principle by combining selectively disclosed credentials and context-awareness. First, the algorithm traverses the resource permission requirement table R and the operation permission requirement table , selecting all permission items that satisfy and , forming the initial permission set . This step ensures all necessary permissions are included.
The system then dynamically adjusts permissions using contextual information (e.g., device location, time, network state). By applying the function , the algorithm retains only the permissions valid under the current environment, generating the adjusted set . This step excludes invalid permissions caused by environmental changes.
Finally, the algorithm generates the minimum permission set through the intersection . This ensures that each permission is the common intersection of multiple resource or operation requirements, eliminating redundancy. Suppose a redundant permission exists. Removing would necessarily prevent access to certain resources or operations, contradicting the definition of intersection. Therefore, the output permission set is both complete and minimal. □
5. Performance Analysis
This section evaluates the proposed mechanism for AIoT environments across four key aspects: computational efficiency of credential generation and verification; privacy protection strength measured via information entropy and simulated attacks against identity and data leakage; responsiveness and adaptability of dynamic permission management in real-time scenarios; and system overhead and scalability through stress testing. These experiments collectively demonstrate the mechanism’s practicality and robustness under realistic AIoT conditions.
5.1. Environmental Configuration
The experimental environment includes an Intel Core i7-12700 processor (Intel, Santa Clara, CA, USA) (2.10 GHz), 16 GB RAM, NVIDIA GTX 1650 (NVIDIA, Santa Clara, CA, USA), and 512 GB SSD, running Ubuntu 20.04 with the PyCryptodome cryptographic library and ZKPlib ZKP framework. The dataset simulates 10,000 users, each with 20 sensitive attributes (e.g., occupation, income, location), and dynamically manages permissions using a zero-trust system. The test dataset was synthesized manually following this workflow: first, based on public statistics for age, gender, region, occupation, and income, we constructed a five-dimensional stratified sampling framework; next, we fitted a Gaussian Copula to model the joint distribution of 20 sensitive attributes, preserving realistic relationships among variables such as occupation and income; then, with a fixed random seed, we used the Synthpop tool to draw 10,000 virtual users from this distribution, yielding a 10,000 × 20 attribute matrix; finally, we wrote the synthetic data to a database and automatically triggered the selective-disclosure and access-control processes within the zero-trust architecture.
Comparison schemes include the full disclosure method (all 20 attributes), SD (with 1, 5, or 10 attributes), and differential privacy (DP, with Laplace noise and privacy budget = 1.0). Test scenarios focus on data access in the AIoT with user scales from 1000 to 10,000, measuring credential generation and verification time, entropy of undisclosed attributes, attack success rate, and permission generation response time.
5.2. Computational Efficiency
To evaluate computational efficiency, the experiment tests varying user loads (1000 to 10,000 users) and measures credential generation and verification times. The traditional method verifies all 20 attributes, while the SD scheme uses ZKP for disclosed attributes only, and the DP method incorporates additional noise parameters. A multi-threaded stress tool simulates high-load scenarios, with results averaged over 10 runs for stability. Performance is shown in Figure 4.
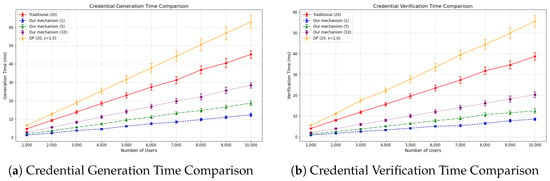
Figure 4.
Efficiency of voucher calculation.
Experimental results show that the SD scheme is highly efficient. At 10,000 users, SD credential generation (12.3 ms) and verification (8.5 ms) are over 70% faster than the traditional method (45.2 ms and 38.7 ms). Even with 10 attributes disclosed, SD remains more than twice as fast. In contrast, the DP scheme is the slowest, taking about 1.4 times longer than the traditional method due to noise-generation overhead. Crucially, the SD scheme demonstrates sub-linear computational growth with more users, unlike the nearly linear scaling of the traditional and DP methods. This efficiency stems from SD’s use of ZKPs and credential aggregation, which reduce redundant computations and combine multiple verifications into a single step.
5.3. Information Entropy and Attack Success Rate
To evaluate privacy protection, the experiment measures the uncertainty of hidden attributes using information entropy (scale 0–5, higher is better) and simulates adversary attack success rates via correlation analysis. The adversary tries to infer hidden data from disclosed attributes using association rules trained on 10,000 users. The SD scheme uses encryption commitments and ZKP to protect hidden attributes, while the DP scheme obscures values with noise. Results are shown in Table 3.

Table 3.
Privacy comparison (fixed user size 10 K).
With just one attribute disclosed, the SD scheme achieves a high information entropy of 4.2 and a low attack success rate of 12.4%. This significantly outperforms the DP scheme (entropy 3.1, attack rate 24.7%) and the traditional full-disclosure method (entropy 0.0, attack rate 98.6%). While DP’s noise injection is vulnerable to multi-attribute correlation attacks, SD uses mathematical proofs to guarantee the integrity of hidden attributes. This prevents adversaries from extracting information from commitments, thereby preserving both data utility and privacy.
5.4. Dynamic Permission Generation Time
To evaluate the real-time performance of the dynamic permission module, the experiment simulated low- to high-load scenarios by gradually increasing policy counts from 100 to 1000. Each request generated a least-privilege permission set, and average generation time was recorded. The traditional method iterates through all policies and verifies every user attribute, the DP method adds noise to traditional verification, while the SD method pre-filters policies based on disclosed attributes, verifying only those relevant to the request. The results are shown in Figure 5.
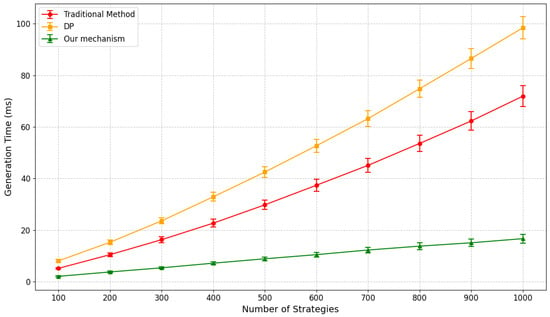
Figure 5.
Dynamic permission generation time comparison.
The experimental results demonstrate that the SD method significantly outperforms both (traditional and DP) approaches in dynamic permission generation efficiency. Under a low load of 100 policies, SD completes in 2.1 ms—59.6% faster than the traditional method (5.2 ms) and 74.1% faster than DP (8.1 ms). As policy count increases to 1000, SD requires only 16.7 ms, while traditional and DP methods rise to 71.9 ms and 98.4 ms, respectively. SD maintains millisecond-level performance even under high load, highlighting its strong advantage in dynamic permission management.
5.5. System Overhead
To comprehensively evaluate the resource efficiency of the zero-trust self-sovereign identity (SSI) management mechanism in real deployments, we designed a scalability test for system overhead. This experiment examines how key resource indicators change with different user scales, including key storage size, peak memory usage, CPU utilization, and network transmission overhead. We set 10 user-scale levels (from 1000 to 10,000 users), and for each level we performed 1000 consecutive authentication operations. Resource data were collected in real time, focusing on the memory peak during verification, the average CPU load, the key storage footprint, and the per-verification network payload. Each data point is reported as the mean ± standard deviation over 10 runs. The results are shown in Table 4.

Table 4.
System overhead under different user scales.
The results show that the proposed mechanism maintains stable overhead across user scales, with consistently low standard deviations, demonstrating the scheme’s reliability. Key storage remains within KB per user, with fluctuations of only , indicating that the distributed key generation mechanism preserves storage efficiency under varying loads. Memory usage increases from MB at 1000 users to MB at 10,000 users, with the standard deviation always below 3% of the measured value, evidencing the zero-knowledge proof framework’s highly predictable memory management.
CPU utilization exhibits a near-linear growth trend, rising from to , with the standard deviation stable at around 4%. Notably, even at the highest load (10,000 users), the utilization band (24.4–26.4%) is well below the device’s processing threshold (90%), leaving ample safety headroom. Network transmission overhead is the most stable: the per-verification payload remains within KB to KB, with a standard deviation of only 1.6%. This stability is attributed to the fixed-size output of credential aggregation. Overall, these figures are significantly better than those of traditional identity management systems, confirming the robustness of our mechanism in resource-constrained environments.
6. Conclusions
This paper presents a blockchain-based SSI management mechanism for AIoT environments, aiming to address challenges in identity management and data security during model training, inference, and continuous learning. To meet privacy requirements, the mechanism adopts SD credentials, enabling users to reveal only the necessary identity attributes. This not only reduces the risk of sensitive information exposure but also improves the efficiency and reliability of identity verification. In addition, a context-aware dynamic permission management mechanism is designed to adjust access rights in real time according to user attributes, security conditions, and task requirements. This ensures secure and adaptive data access in dynamic AIoT environments. Overall, the mechanism strengthens privacy protection, enhances authentication efficiency, and improves environment security, providing a scalable solution for AIoT applications. However, the current solution may face scalability challenges in more complex AIoT environments with high device and data variability. Future work could focus on optimizing the selective disclosure algorithm to improve its performance in large-scale scenarios. Future research should further explore more intelligent, flexible, and scalable identity management frameworks to address the evolving security requirements and promote the secure application of AIoT technologies in a broader range of fields.
Author Contributions
Study conception and design, J.R.; data collection, J.R.; analysis and interpretation of results, J.R.; draft manuscript preparation, J.R.; writing, review, and editing, J.R., J.Z., J.X. and Y.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Research Fund of the Key Lab of Education Blockchain and Intelligent Technology, Ministry of Education (EBME25-F-08).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Li, X.; Song, Z.; Yang, J. Federated adversarial learning: A framework with convergence analysis. In Proceedings of the International Conference on Machine Learning. PMLR, Honolulu, HI, USA, 23–29 July 2023; pp. 19932–19959. [Google Scholar]
- Ren, Y.; Leng, Y.; Cheng, Y.; Wang, J. Secure data storage based on blockchain and coding in edge computing. Math. Biosci. Eng. 2019, 16, 1874–1892. [Google Scholar] [CrossRef]
- Xie, G.; Hou, G.; Pei, Q.; Huang, H. Lightweight privacy protection via adversarial sample. Electronics 2024, 13, 1230. [Google Scholar] [CrossRef]
- Fredrikson, M.; Jha, S.; Ristenpart, T. Model inversion attacks that exploit confidence information and basic countermeasures. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1322–1333. [Google Scholar]
- Weigl, L.; Barbereau, T.; Fridgen, G. The construction of self-sovereign identity: Extending the interpretive flexibility of technology towards institutions. Gov. Inf. Q. 2023, 40, 101873. [Google Scholar] [CrossRef]
- Ren, Y.; Lv, Z.; Xiong, N.; Wang, J. HCNCT: A cross-chain interaction scheme for the blockchain-based metaverse. ACM Trans. Multimed. Comput. Commun. Appl. 2024, 20, 1–23. [Google Scholar] [CrossRef]
- Nasr, M.; Shokri, R.; Houmansadr, A. Comprehensive privacy analysis of deep learning: Passive and active white-box inference attacks against centralized and federated learning. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–22 May 2019; pp. 739–753. [Google Scholar]
- Chen, J.; Cai, Z.; Qi, J.; Fang, B. Design of a Decentralized and Distributed Digital Identity Framework for Cross-Border Scenarios. Strateg. Study Chin. Eng. Sci. 2025, 27, 88–97. [Google Scholar]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A survey on zero trust architecture: Challenges and future trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar] [CrossRef]
- Nookala, G.; Gade, K.; Dulam, N.; Thumburu, S.K.R. Zero-Trust security frameworks: The role of data encryption in cloud infrastructure. MZ Comput. J. 2023, 4, 1–17. [Google Scholar]
- Han, C.; Chen, H.; Qiu, Z. Design and implementation of a data-flowing oriented zero-trust security situational awareness framework. In Proceedings of the International Conference on Network Simulation and Evaluation, Shenzhen, China, 22–24 November 2023; pp. 133–147. [Google Scholar]
- Gambo, M.L.; Almulhem, A. Zero trust architecture: A systematic literature review. arXiv 2025, arXiv:2503.11659. [Google Scholar]
- Ren, Y.; Leng, Y.; Qi, J.; Sharma, P.K.; Wang, J.; Almakhadmeh, Z.; Tolba, A. Multiple cloud storage mechanism based on blockchain in smart homes. Future Gener. Comput. Syst. 2021, 115, 304–313. [Google Scholar] [CrossRef]
- Murcia, J.M.B.; Cánovas, E.; García-Rodríguez, J.; Zarca, A.M.; Skarmeta, A. Decentralised identity management solution for zero-trust multi-domain computing continuum frameworks. Future Gener. Comput. Syst. 2025, 162, 107479. [Google Scholar] [CrossRef]
- Zhang, P.; Sun, H.; Zhang, Z.; Cheng, X.; Zhu, Y.; Zhang, J. Privacy-Preserving Recommendations With Mixture Model-Based Matrix Factorization Under Local Differential Privacy. IEEE Trans. Ind. Inform. 2025, 21, 5451–5459. [Google Scholar] [CrossRef]
- Feng, J.; Wu, Y.; Sun, H.; Zhang, S.; Liu, D. Panther: Practical Secure Two-Party Neural Network Inference. IEEE Trans. Inf. Forensics Secur. 2025, 20, 1149–1162. [Google Scholar] [CrossRef]
- Veeramachaneni, V. Emerging authentication technologies for zero trust in IoT systems. J. Adv. Res. Mob. Comput. 2025, 7, 7–21. [Google Scholar]
- Shahrani, A.M.; Rizwan, A.; Sánchez-Chero, M.; Cornejo, L.L.C.; Shabaz, M. Blockchain-enabled federated learning for prevention of power terminals threats in IoT environment using edge zero-trust model. J. Supercomput. 2024, 80, 7849–7875. [Google Scholar] [CrossRef]
- Dintakurthy, Y.; Innmuri, R.K.; Vanteru, A.; Thotakuri, A. Emerging applications of artificial intelligence in Edge computing: A comprehensive review. J. Mod. Technol. 2024, 1, 175–185. [Google Scholar] [CrossRef]
- Ren, Y.; Zhou, Z.; Han, Z.; Ge, C.; Huang, H. AdaptiveShard: Enhancing Throughput and Security of Sharded Blockchain with Adaptive Verifiable Coding. IEEE Trans. Inf. Forensics Secur. 2025, 20, 7927–7939. [Google Scholar] [CrossRef]
- Wang, C.; Yang, Q.; Shen, J.; Wu, Q.M.J.; He, D. BM-PDA: Blockchain Based Multifunctional Private-Preserving Data Aggregation for E-Health Systems. IEEE Trans. Dependable Secur. Comput. 2025, 1–14. [Google Scholar] [CrossRef]
- Xiao, Z.; Wang, C.; Shen, J.; Jonathan Wu, Q.M.; He, D. Less Traces Are All It Takes: Efficient Side-Channel Analysis on AES. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2025, 44, 2080–2092. [Google Scholar] [CrossRef]
- Fedrecheski, G.; Rabaey, J.M.; Costa, L.C.; Ccori, P.C.C.; Pereira, W.T.; Zuffo, M.K. Self-sovereign identity for IoT environments: A perspective. arXiv 2020, arXiv:2003.05106. [Google Scholar]
- Popa, M.; Stoklossa, S.M.; Mazumdar, S. Chaindiscipline-towards a blockchain-iot-based self-sovereign identity management framework. IEEE Trans. Serv. Comput. 2023, 16, 3238–3251. [Google Scholar] [CrossRef]
- Bartolomeu, P.C.; Vieira, E.; Hosseini, S.M.; Ferreira, J. Self-sovereign identity: Use-cases, technologies, and challenges for industrial iot. In Proceedings of the 2019 24th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Zaragoza, Spain, 10–13 September 2019; pp. 1173–1180. [Google Scholar]
- Weingaertner, T.; Camenzind, O. Identity of things: Applying concepts from self sovereign identity to IoT devices. J. Br. Blockchain Assoc. 2021, 4. [Google Scholar] [CrossRef]
- Sakib, N.; Ali, M.Y.; Momo, N.M.; Mumu, M.I.; Nahid, M.A.; Chowdhury, F.R.; Ferdous, M.S. Secure ownership management and transfer of consumer internet of things devices with self-sovereign identity. arXiv 2024, arXiv:2408.17184. [Google Scholar] [CrossRef]
- Kaul, D. AI-driven decentralized authentication system using homomorphic encryption. Int. J. Adv. Res. Eng. Technol. 2021, 12, 74–84. [Google Scholar]
- Chamola, V.; Goyal, A.; Sharma, P.; Hassija, V.; Binh, H.T.T.; Saxena, V. Artificial intelligence-assisted blockchain-based framework for smart and secure EMR management. Neural Comput. Appl. 2023, 35, 22959–22969. [Google Scholar] [CrossRef] [PubMed]
- Le, A.; Nguyen, N.; Tran, T.; Nakano, T. Securing digital futures: Exploring decentralised systems and blockchain for enhanced identity protection. In Proceedings of the International Conference on Intelligence of Things, Ho Chi Minh City, Vietnam, 25–27 October 2023; pp. 200–212. [Google Scholar]
- Mamoshina, P.; Ojomoko, L.; Yanovich, Y.; Ostrovski, A.; Botezatu, A.; Prikhodko, P.; Izumchenko, E.; Aliper, A.; Romantsov, K.; Zhebrak, A.; et al. Converging blockchain and next-generation artificial intelligence technologies to decentralize and accelerate biomedical research and healthcare. Oncotarget 2018, 9, 5665. [Google Scholar] [CrossRef] [PubMed]
- Nash, A. Decentralized intelligence network (DIN). arXiv 2024, arXiv:2407.02461. [Google Scholar] [CrossRef]
- Nasrin, S. Securing vaccination data using self-sovereign identity, hyperledger fabric and zero trust model. In Proceedings of the 2023 International Conference on Information and Communication Technology for Sustainable Development (ICICT4SD), Dhaka, Bangladesh, 21–23 September 2023; pp. 290–294. [Google Scholar]
- Verma, R.; Indra, G. ZIADA: Zero trust-based identity attestation framework for DLT verified AI-enabled industrial internet of things. In Proceedings of the 2024 IEEE Region 10 Symposium (TENSYMP), New Delhi, India, 27–29 September 2024; pp. 1–6. [Google Scholar]
- Li, S.; Doh, I.; Chae, K. A group authentication scheme based on lagrange interpolation polynomial. In Proceedings of the 2016 10th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Fukuoka, Japan, 6–8 July 2016; pp. 386–391. [Google Scholar]
- Kittur, A.S.; Pais, A.R. Batch verification of digital signatures: Approaches and challenges. J. Inf. Secur. Appl. 2017, 37, 15–27. [Google Scholar] [CrossRef]
- Bojič Burgos, J.; Pustišek, M. Decentralized iot data authentication with signature aggregation. Sensors 2024, 24, 1037. [Google Scholar] [CrossRef]
- Li, Z. A verifiable credentials system with privacy-preserving based on blockchain. J. Inf. Secur. 2022, 13, 43–65. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).