Abstract
The popularity of secure cloud data sharing is on the rise, but it also comes with significant concerns about privacy violations and data tampering. While existing Proxy Re-Encryption (PRE) schemes effectively protect data in the cloud, challenges persist with certificate administration and key escrow. Moreover, the increasing number of users and prevalence of lightweight devices demand functional and cost-effective solutions. To address these issues, this paper presents a novel Pairing-free Certificate-Based Proxy Re-Encryption Plus scheme that leverages elliptic curve groups for improved effectiveness and performance. This scheme successfully resolves challenges related to certificate management and key escrow in traditional PRE schemes, while also introducing non-transferable and message-level fine-grained control characteristics. These enhancements bolster data security during sharing and minimize the risk of malicious information leakage. Our proposed scheme’s correctness, security, and effectiveness are rigorously verified and analyzed. The results demonstrate that the scheme achieves the chosen ciphertext security in the random oracle model. Compared to current PRE schemes, our approach offers greater advantages, lower computational overhead, and enhanced suitability for practical cloud computing applications.
1. Introduction
1.1. Background
With the rapid advancement and convergence of cloud computing, big data, and related technologies, public cloud storage has become immensely popular. Users increasingly depend on cloud storage solutions for online data storage and sharing. However, this convenience comes with security concerns. When users store their data in the cloud, they lose direct control, leading to potential issues such as privacy breaches and compromised data confidentiality. The semi-trustworthy nature inherent in third-party cloud service providers poses a challenge for users in conferring absolute trust. Consequently, the predominant strategy for ensuring data protection rests on the shoulders of the cloud subscribers themselves, who rightfully own and safeguard their data.
Data confidentiality is typically guaranteed via the pre-upload encryption of data to the cloud. Nevertheless, challenges arise in scenarios where data sharing among diverse users is essential. In the context of sharing data between User A and User B, User A is required to download and decrypt the data before transmitting it to User B. Upon reception, User B must re-encrypt the data before uploading it to the cloud storage platform. This method exhibits inefficiency and introduces the potential for data leakage during transmission, thereby compromising the security and convenience that public cloud storage platforms aim to provide.
Blaze et al. [1] introduced the concept of Proxy Re-Encryption (PRE) at the 1998 Euromonitor conference to address these challenges. In the PRE system, users can convert ciphertext encrypted by an authorized party into ciphertext that can be decrypted by another authorized party with the assistance of a semi-trusted third party. This process ensures that the third party cannot access the plaintext information of the data, providing an efficient and secure solution for cloud data sharing.
Utilizing a Proxy Re-Encryption (PRE) scheme empowers data owners to delegate access to their stored data, enabling designated individuals to download and access the data directly from the cloud. Proxy re-encryption serves to diminish the direct interaction between the authorizer and the authorized party, consequently elevating data-sharing security and mitigating overhead for the cloud subscriber.
1.2. Our Contribution
This paper introduces a novel scheme called Pairing-Free Certificate-Based Proxy Re-Encryption Plus (PCBPRE+), which combines the features of Pairing-free Proxy Re-Encryption (PPRE) and Certificate-Based Proxy Re-Encryption Plus (CBPRE+). The main contributions of this scheme are outlined below:
- This paper introduces the PCBPRE+ scheme, which combines the properties of PPRE and CBPRE+ schemes. The proposed scheme improves computational efficiency by eliminating the reliance on bilinear pairs, effectively addressing the issue of high computation overhead present in existing schemes. As a result, the PCBPRE+ scheme is highly suitable for deployment on computationally or power-constrained devices.
- The scheme presented in this paper effectively addresses the challenges related to certificate management and key escrow in traditional CBPRE schemes. Additionally, it incorporates non-transferable and message-level fine-grained control features. Through fine-grained data control and permission management, the scheme ensures that only authorized users can access the data, thereby preventing unauthorized information leakage and tampering.
- This paper offers a formal conceptual description of the PCBPRE+ scheme, along with a defined security model. We designed a concrete PCBPRE+ scheme and rigorously verified and analyzed its correctness, security, and performance. Detailed empirical evidence and evaluation demonstrate the feasibility and practicality of the scheme.
1.3. Organization
This paper is structured as follows: Section 2 provides a review of the relevant literature for our strategy. In Section 3, background information is presented. The security model of the system is described in Section 4. Section 5 introduces the new PCBPRE+ scheme. Its accuracy and security are confirmed in Section 6, while Section 7 contains a study of its performance.
2. Related Work
Proxy Re-Encryption (PRE) has received increased academic attention recently, leading to the development of several well-known PRE schemes [2,3,4,5,6]. However, many of these schemes rely on traditional public-key cryptosystems (PKC) [7,8,9,10] or identity-based cryptosystems [11,12,13,14], which can introduce certain limitations and challenges.
Traditional proxy re-encryption schemes based on public-key cryptosystems face challenges in certificate management, while identity-based cryptosystems have inherent key escrow issues. To address these concerns, Sur introduced the concept of certificateless proxy re-encryption (CLPRE) within the framework of certificateless public-key cryptography (CLPKC) [15]. This approach allows users to overcome key escrow problems by combining a partially trusted key generation center (KGC) with a user-selected key value, generating an independent private key. This ensures that the KGC remains unaware of any user’s private key. However, the introduction of various CLPRE schemes [16,17] has revealed that the KGC still needs to securely transmit a portion of the private key to the user, leading to a new key distribution challenge. Consequently, CLPRE still has limitations in cloud storage applications.
Sur et al. proposed a scheme known as Certificate-Based Proxy Re-Encryption (CBPRE) that addresses the limitations and shortcomings of earlier proxy Re-Encryption (PRE) schemes [18]. CBPRE leverages the implicit certificate property of the Certificate-Based Encryption (CBE) paradigm, achieving a balance between identity-based encryption and conventional public-key encryption. This approach effectively tackles the challenge of certificate revocation in conventional public-key encryption and overcomes the issues of key escrow and distribution in identity-based encryption. As a result, CBPRE has emerged as an ideal solution for achieving secure and efficient cloud storage sharing [19,20].
Furthermore, Sur et al. established the first provably secure CBPRE scheme and provided a formal conception of CBPRE. Following this, Li et al. [21] proposed the Certificate-Based Conditional Proxy Re-Encryption (CB-CPRE) scheme and demonstrated its chosen ciphertext security in the random oracle model. The CB-CPRE scheme allows for conditional filtering of stored data; however, the authorized party can only obtain either all plaintexts or no plaintexts after decrypting the re-encrypted ciphertexts, thus lacking the ability to achieve fine-grained sharing at the message level.
Liu et al. [22] developed the CBPRE+ technique to address fine-grained sharing at the message level. This scheme combines the advantageous features of CBPRE and Proxy Re-Encryption Plus (PRE+) [23,24,25]. PRE+ was initially proposed by Wang et al., utilizing distinct ephemeral random values chosen by the authorizer to achieve fine-grained sharing and non-transferability features at the message level, which are highly desirable characteristics for cloud storage scenarios [26,27].
Currently, certificate-based proxy re-encryption schemes typically rely on computationally intensive bilinear pairings. However, with the continuous development of cloud computing technology and the widespread adoption of Internet of Things (IoT) applications in recent years, there is a geometric growth trend in both user numbers and data volume. This trend is particularly evident in various fields such as medical IoT and vehicular IoT, where the increase in data volume is accompanied by a more urgent demand for rapid data responsiveness. Consequently, the efficiency issues of cloud storage have drawn considerable attention, as the process of data sharing often consumes significant amounts of network and computational resources. Despite some progress in the implementation of bilinear pairings, they remain the most time-consuming and least efficient part of encryption operations. Therefore, proposing a more efficient data-sharing solution has become imperative.
To address this issue, Lu et al. introduced a certificate-based proxy re-encryption scheme in their paper [28], which eliminates the reliance on bilinear pairings and adopts a non-bilinear pairing approach. This method significantly improves computational efficiency and is better suited to the data development trends in modern society. However, achieving a balance between functionality and efficiency remains a challenge under the prerequisite of meeting both aspects.
3. Preliminary
3.1. Elliptic Curve Group and Computational Assumption
To begin, a brief summary of the elliptic curve group, which serves as the foundation for the scheme, is provided.
Let be a finite field with the following operations, and let p be a prime number:
- Addition: If , then mod p, where .
- Multiplication: If , then mod p, where .
- Inversion: If a is a non-zero element in , then the inverse of a is the only element that satisfies mod p.
Let be a p element finite field and a and b be two elements of satisfying the discriminant . The elliptic curve over the finite field , denoted as , is formally defined as the set of all points on that satisfy the Weierstrass equation , along with the inclusion of point O at infinity. In other words, all the points on collectively form an exchange group denoted as .
The binary operation “+” on group G is formally defined as follows: Let , L be the line through P and L (if , then L represents the tangent line to group G at point P ), L intersects G at a third point, denoted , and reflecting on the x-axis gives a point R, defining . Quantitative multiplication in group G: (t times).
The security of this scheme relies on the underlying assumption of the Computational Diffie–Hellman (CDH) problem. This problem can be defined as follows:
Definition 1.
Let G be a large prime elliptic curve group of order q and P a generating element of group G. Then, the CDH problem on group G is as follows: Given , compute for any . Let us assume the existence of a probabilistic polynomial-time (PPT) algorithm, denoted as , that can effectively solve the Computational Diffie–Hellman (CDH) problem with a certain probability:
If the probability of success for all PPT algorithms is negligible, then the CDH problem in group G is considered computationally hard to solve.
3.2. Program Definition
This scheme involves four key roles, including the sender, receiver, semi-trusted proxy, and Certificate Authority (CA). The CA is primarily responsible for authenticating the identities of the sender and receiver and issuing certificates. The sender is tasked with key generation, message encryption, and re-encryption key generation. The semi-trusted proxy is responsible for re-encrypting the ciphertext, and upon receiving the re-encrypted ciphertext, the receiver can decrypt it using their private key. Each role plays a unique and crucial part in the scheme, collectively constituting the complete operation of the proxy re-encryption scheme. In this collaborative system, each role contributes significantly to the overall functionality.
- Setup (k): Given the security parameter k as input, the algorithm outputs the system’s public parameter and the master key .
- KeyGen (): Given the system’s public parameter as input, the algorithm generates and outputs the user’s private key and partial public key .
- Certify (): Given the system’s public parameter , master key , user identity , and partial public key as input, the algorithm generates and outputs all public keys and user certificate .
- Encrypt (): Given the ephemeral randomness , message m, user identity , public key , and the system’s public parameter as input, the algorithm creates and outputs the message’s original ciphertext .
- ReKeyGen (): Given the ephemeral randomness , the private key of user A, certificate , Identity of authorized user B, public key , and the system’s public parameter as input, the encryption key is created and output by the algorithm.
- ReEncrypt (): Given the original ciphertext , the re-encryption key , and the system’s public parameter as input, the algorithm outputs the re-encryption ciphertext .
- Decrypt1 (): Given the system’s public parameter , the private key of the authorizer, the certificate and the original ciphertext as input, the algorithm outputs either the message m or the invalid symbol ⊥.
- Decrypt2 (): Given the system’s public parameter , the private key of the authorized party, the certificate , and the original ciphertext as input, the algorithm outputs either the message m or the invalid symbol ⊥.
4. Security Model
In the PCBPRE+ scheme’s security model, the adversaries can be divided into two groups: and . Adversary simulates an unauthenticated user who lacks access to the system’s master key. However, adversary has the ability to request the certificate of any user except for the target user. On the other hand, adversary acts as a malicious Certification Authority () by simulating its behavior to gain access to the system’s master key. has the ability to request the private key of any user except for the private key of the target user.
The security of the scenario can be characterized by the interactive game --, involving adversaries and , as well as the challenger. A security model diagram is shown in Figure 1.
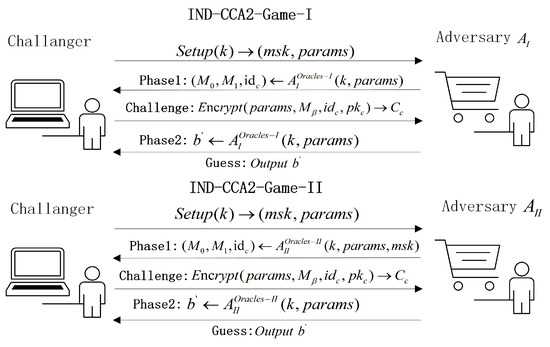
Figure 1.
Security Architecture.
4.1. Game IND-CCA2-I
- System parameter setting: The challenger executes the algorithm to generate the system’s public parameter set , with corresponding to master key . The challenger outputs the master key and outputs the system parameter set to adversary .
- Phase 1: Adversary is able to make the following inquiries in an adaptive manner.
- Users generation oracle: The challenger keeps track of the user’s private key, public key, and certificate in a table called that is initially empty. Adversary inputs the identity , and if there is already a record in table , the challenger outputs the public key to adversary ; otherwise, the challenger generates the public key , private key , and certificate corresponding to the identity , records them in , and outputs the public key to .
- Private key generation oracle: Adversary enters the identity , and the challenger extracts the private key from the table and outputs it to the .
- Certificate generation oracle: Certificate Inquiry: Adversary enters the identity , and the challenger obtains the certificate from table and outputs it to .
- Re-encryption key generation oracle: Adversary inputs the identity , randomly selects ephemeral randomness , and the challenger generates a re-encryption key , and outputs the re-encryption key to adversary .
- Re-encryption oracle: Adversary inputs an original ciphertext and the identity, and the challenger generates a re-encrypted ciphertext , and outputs the re-encrypted ciphertext to adversary .
- Decryption oracle: Adversary inputs identity and a ciphertext , and the challenger performs the decryption algorithm on and outputs the resulting value to .
- Challenge stage: After the Stage 1 inquiries, adversary produces an identity and two plaintexts of equal length, denoted as , . The restriction is that adversary has not made an inquiry about the certificate corresponding to the identity . The challenger randomly chooses , runs the algorithm to generate the original ciphertext of , and outputs it as the challenge ciphertext to , where does not interrogate the re-encryption key for .
- Phase 2: The same as the phase 1 interrogation, with the following restrictions: adversary cannot interrogate the certificate of the challenging identity ; for any , adversary cannot make an inquiry about the with the re-encryption key; adversary cannot interrogate the and the with the decryption key, and in the process, interrogates the output of the for the re-encryption.
- Guess: Adversary outputs a guess for . If , then adversary wins the game. The advantage for adversary to win is .
4.2. Game IND-CCA2-II
- System parameter setting: The challenger executes the algorithm to generate the system’s public parameter , with corresponding to the master key . The challenger outputs the master key and outputs the system parameter set to adversary .
- Phase 1: Adversary is able to make the following inquiries in an adaptive manner.
- 1.
- Users generation oracle: The challenger keeps track of the user’s private key, public key, and certificate in a table called that is initially empty. Adversary inputs the identity , and if there is already a record in table , the challenger outputs the public key to adversary ; otherwise, the challenger generates the public key , private key , and certificate corresponding to the identity , records them in , and outputs the public key to .
- 2.
- Private key generation oracle: Adversary enters the identity , and the challenger obtains the private key from the table and outputs it to .
- 3.
- Re-encryption key generation oracle: Adversary inputs the identity , randomly selects ephemeral randomness , and the challenger generates a re-encryption key , and outputs the re-encryption key to adversary .
- 4.
- Re-encryption oracle: Adversary inputs an original ciphertext , and identity , and the challenger generates a re-encrypted ciphertext , and outputs the re-encrypted ciphertext to adversary .
- 5.
- Decryption oracle: Adversary inputs identity and a ciphertext , and the challenger performs the decryption algorithm on and outputs the resulting value to .
- Challenge stage: Following the Stage 1 inquiries, adversary produces an identity along with two plaintexts of equal length, denoted as and . The restriction is that adversary has not asked for the private key corresponding to identity . The challenger randomly chooses , runs the algorithm to generate the original ciphertext of , and outputs it as the challenge ciphertext to , where does not interrogate the re-encryption key for .
- Phase 2: The same as the phase 1 interrogation, with the following restrictions: Adversary cannot ask for the private key of the challenge identity ; for any , adversary cannot inquiry the with the re-encryption key; adversary cannot interrogate the and the with the decryption key, and in the process, the interrogates the output of the for the re-encryption.
- Guess: Adversary outputs a guess for . If , then adversary wins the game. The advantage for adversary to win is .
Definition 2.
A certificate-based proxy re-encryption scheme is considered to satisfy indistinguishable security under adaptive chosen ciphertext attacks (IND-CCA2 security) if no PPT adversary can gain a significant advantage in winning the aforementioned game.
5. Pairing-Free Certificate-Based Proxy Re-Encryption Plus Scheme
The PCBPRE+ scheme consists of eight algorithms, and Figure 2 provides a concise depiction of the scheme.
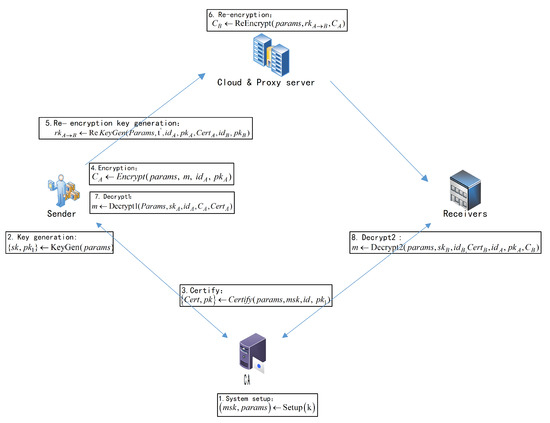
Figure 2.
Flowchart of the CBPRE+.
- Setup: On inputting security parameters k, generate the master key and the set of public parameters as follows:
- (a)
- The k-bit prime q is chosen to produce a cyclic additive group, where group G comprises elliptic curves whose order is the large prime q and P is the generating element of G.
- (b)
- Choose five hash functions, where n and l denote the length of the random bit string used by the plaintext and encryption algorithms, respectively:
- (c)
- CA randomly selects , calculates , and outputs the master key and the set of public parameters:.
- KeyGen: On inputting public parameters , this algorithm randomly selects as the user i private key and computes the partial public key . Output user i’s private keys and partial public key .
- Certify: On inputting public parameter , master key , identity , and the partial public key .
- (a)
- The algorithm randomly selects , user i’s public key .
- (b)
- The algorithm calculates user i’s certificate
- Encrypt: On inputting message , identity , the public key , and public parameter , the user does the following:
- (a)
- Choose ephemeral randomness at random.
- (b)
- Randomly select a l-bit , and calculate , .
- (c)
- Computer the ciphertext , , , , where , .
- (d)
- Randomly select , and compute the ciphertext , .
- (e)
- Output the original ciphertext .
- ReKeyGen: On inputting ephemeral randomness c, public parameter , identity , certificate , the public key of sender A, and the identity and public key of receiver B, this algorithm performs as follows:
- (a)
- Calculate , where .
- (b)
- Then, compute , , .
- (c)
- Set the proxy re-encryption key .
- ReEncrypt: On inputting a re-encryption key , ciphertext C, and public parameter , the steps that the proxy takes are as follows:
- (a)
- If , then continue; otherwise, output ⊥.
- (b)
- Compute , , , , and output a new ciphertext .
- Decrypt1: On inputting ciphertext C, identity , private keys , the certificate of sender A, and public parameter , the receiver A operates as follows:
- (a)
- If , then proceed; if not, output ⊥.
- (b)
- Compute .
- (c)
- If , where , the algorithm returns m as the message. Otherwise, it outputs ⊥, indicating a failure or invalid condition.
- Decrypt2: On inputting ciphertext , identity , the public key of sender A and identity , private keys , the certificate of receiver B, and public parameter , the receiver B operates as follows:
- (a)
- Compute .
- (b)
- Compute .
- (c)
- If , where , the algorithm returns m as the message. Otherwise, it outputs ⊥, indicating a failure or invalid condition.
6. Security Analysis
6.1. Correctness Analysis
Original ciphertext verification:
Original ciphertext decryption verification:
Re-encryption ciphertext decryption verification:
6.2. Security Analysis
Theorem 1.
Assuming that are random prophecies, if there exists a first class adversary about the security of this scheme IND-CCA2 with advantage ε, asking at most user-generated queries, private key queries, certificate queries, re-encryption key queries, re-encryption queries, decryption queries, and random prophecy queries , then the CDH problem on group G is solved by the algorithm with advantage .
Proof.
In this paper, an algorithm is constructed to mimic the challenger of IND-CCA2, a CDH problem example is given as , and the algorithm interacts with the first class adversary to solve the CDH problem:
- System parameter setting: The algorithm probabilistically selects an index value , and outputs to adversary as an open parameter set .
- Hash Oracle Queries: Adversary generates a random prophecy query, algorithm maintains table , where is initially empty, and algorithm interacts with adversary as follows:
- –
- Queries: Adversary inputs , if table already has records , algorithm outputs to adversary ; otherwise, algorithm randomly selects , records into , and outputs to adversary .
- –
- Queries: Adversary inputs , if table already has records , algorithm outputs to adversary ; otherwise, algorithm randomly selects , records into , and outputs to adversary .
- –
- Queries: Adversary inputs R, if table already has records , algorithm outputs to adversary ; otherwise, algorithm randomly selects , records into , and outputs to adversary .
- –
- Queries: Adversary inputs , if table already has records , algorithm outputs to adversary ; otherwise, algorithm randomly selects , records into , and outputs to adversary .
- –
- Queries: Adversary inputs , if table already has records , algorithm outputs to adversary ; otherwise, algorithm randomly selects , records into , and outputs to adversary .
- Phase 1: Adversary adaptively makes the following queries, and the algorithm maintains the table below as initially empty.
- User generation query: Adversary enters :
- (1)
- If there is already a record in table , algorithm outputs to adversary .
- (2)
- If is the user identity asked by adversary , that is, , the algorithm randomly selects , records into table , and outputs to adversary .
- (3)
- If , algorithm randomly select , let , add and to table and table , respectively, and output to adversary .
- Private key generation query: Adversary inputs , algorithm obtains the records from table , and outputs to adversary .
- Certificate generation query: Adversary inputs , if , Algorithm stops the game; otherwise, Algorithm obtains the records from Table and outputs to Adversary .
- Re-encryption key generation query: Adversary inputs , if , algorithm aborts the game; otherwise, algorithm obtains ephemeral randomness c, certificate , and public key , executes algorithm to produce a new re-encryption key , which is then output to adversary .
- Re-encryption query: Adversary inputs , Algorithm first verifies the equation . If the equation does not hold, Algorithm rejects the query; if it does, Algorithm executes as follows:
- (1)
- If , then algorithm searches the table for the record satisfying , where , . If there is no such record, the algorithm rejects the query; if it exists, then , , , . where . Algorithm outputs to adversary .
- (2)
- If , algorithm undergoes a re-encryption key query on to obtain , then outputs to adversary .
- Decryption query: Adversary inputs , and the algorithm is executed as follows:
- (1)
- If , is an original ciphertext, Algorithm checks , if the query is not valid, Algorithm rejects the query; otherwise, algorithm searches the table for records that satisfy , where , . If there is no such record, Algorithm rejects the query; if it exists, it outputs m to adversary as the decryption of ciphertext .
- (2)
- If , is a re-encrypted ciphertext, the algorithm performs the re-encryption key interrogation to obtain the re-encryption key , and computes . Algorithm searches the table for records that satisfy , where , . If there is no such record, algorithm rejects the query; if it exists, it outputs m to adversary as the decryption of ciphertext .
- (3)
- If , the algorithm obtains and , decrypts using the appropriate decryption algorithm, then outputs m to adversary .
- Challenge: After phase 1 queries, adversary outputs identity and two plaintexts of equal length . Adversary does not make a re-encryption key query for . If , the algorithm terminates the game, resulting in a failed simulation; otherwise, the algorithm probabilistically selects a value , calculates , records in table , and gives to as the challenge ciphertext. Obviously, holds.Decrypt :where .
- Phase 2: The algorithm answers the same as the phase 1 interrogation with the following constraints: adversary cannot interrogate the certificate of challenge identity ; for any , no re-encryption key interrogation can be performed on ; no decryption interrogation can be performed on and . The result of the re-encryption query is during the procedure.
- Guess: Adversary outputs a guess for . If , then wins the game.During the challenge, if adversary chooses the identity as the challenge identity, which is , then Algorithm does not abort the game. Algorithm selects a random record in table and uses as the solution to the given CDH problem.
□
Analysis: We define the following events in order to calculate the benefit of in solving the specified CDH problem:
- (1)
- : Adversary makes a random oracle query on .
- (2)
- : Adversary makes a random oracle query on .
- (3)
- : During the simulation, stops the game.
- (4)
- : rejects a legitimate re-encryption query.
- (5)
- : rejects a legitimate decryption query.
Let , obviously, , we have
The scheme of [28] in the literature specifically proves that since the advantage of adversary to win is , there is.
where , , , . Therefore
If the event occurs, the algorithm obtains a correct record in , then:
Theorem 2.
Assuming that – are random prophecies, if there exists a second class adversary about the security of this scheme IND-CCA2 with advantage ε, asking at most user-generated queries, private key queries, re-encryption key queries, re-encryption queries, decryption queries, and random prophecy queries , then the CDH problem on group G is solved by the algorithm with advantage .
Proof.
In this paper, an algorithm is constructed to mimic the challenger of IND-CCA2, given a CDH problem example , and the algorithm interacts with the first class adversary to solve the CDH problem:
- System parameter setting: The algorithm randomly selects an index value ,, master private key , and outputs public parameters and master private key to adversary .
- Phase 1: Adversary adaptively makes the following queries, and the algorithm maintains the table below as initially empty.
- User generation query: Adversary inputs :
- (1)
- If there is already a record in table , algorithm outputs to adversary .
- (2)
- If is the user identity asked by adversary , that is, , the algorithm randomly selects , Record and into table and table , respectively, and output to adversary .
- (3)
- If , algorithm randomly select , let , add and to table and table , respectively, and output to adversary .
- Private key generation query: Adversary inputs , if , algorithm aborts the game; otherwise, algorithm obtains the records from table and outputs to adversary .
- Certificate generation query: Adversary inputs , if , Algorithm stops the game; otherwise, Algorithm obtains the records from Table and outputs to Adversary .
- Re-encryption key generation query: Adversary inputs , if , algorithm aborts the game; otherwise, algorithm obtains ephemeral randomness c, certificate and public key , executes algorithm to produce a new re-encryption key , which is then output to adversary .
- Re-encryption query: Adversary inputs , Algorithm first verifies the equation . If the equation does not hold, Algorithm rejects the query; if it does, Algorithm executes as follows:
- (1)
- If , the algorithm searches the table for the record satisfying , where , . If there is no such record, the algorithm rejects the query; if it exists, then , , , . where . Algorithm output to adversary .
- (2)
- If , algorithm does re-encryption key query on to obtain , then output to adversary .
- Decryption query: Adversary inputs , and the algorithm is executed as follows:
- (1)
- If , is an original ciphertext, Algorithm checks , if the query is not valid, Algorithm rejects the query; otherwise, algorithm searches the table for records that satisfy , where , . If there is no such record, Algorithm rejects the query; if it exists, it outputs m to adversary as the decryption of ciphertext .
- (2)
- If , is a re-encrypted ciphertext, the algorithm performs the re-encryption key interrogation to obtain the re-encryption key , and computes . Algorithm searches the table for records that satisfy , where , . If there is no such record, algorithm rejects the query; if it exists, it outputs m to adversary as the decryption of ciphertext .
- (3)
- If , the algorithm obtains and , decrypts using the appropriate decryption algorithm, then outputs m to adversary .
- Challenge: After phase 1 queries, adversary outputs identity and two plaintexts of equal length . Adversary does not make re-encryption key query for . If , the algorithm terminates the game, resulting in a failed simulation; otherwise, the algorithm probabilistically selects a value , calculates , records in table , and gives to as the challenge ciphertext. Obviously, holds.Decrypt :where .
- Phase 2: The algorithm answers the same as the phase 1 interrogation with the following constraints: adversary cannot interrogate the private key of challenge identity ; for any , no re-encryption key interrogation can be performed on ; no decryption interrogation can be performed on and . The result of the re-encryption query is during the procedure.
- Guess: Adversary produces a guess for . If , then wins the game.During the challenge, if adversary chooses the identity as the challenge identity, which is , then Algorithm does not abort the game. Algorithm selects a random record in table and uses as the solution to the given CDH problem.
As proved in Theorem 1, the advantage of the algorithm to solve the CDH problem is as follow:
□
7. Performance Analysis
In this section, we conduct a comprehensive comparison between the PCBPRE+ scheme proposed in this paper and several existing PRE schemes, focusing on both functional and efficiency aspects.
For the functional analysis, we compare the properties of various existing PRE schemes used for data sharing. We consider aspects such as fine-grained sharing capabilities, non-transferability, and security, and compare them with other PRE schemes. This comparison highlights the advantages and features of the PCBPRE+ scheme in terms of functionality.
In the efficiency analysis, we perform both theoretical analysis and experimental simulations. The theoretical analysis evaluates the performance of each PRE scheme by analyzing its algorithmic complexity and computational overhead. The experimental simulation, on the other hand, assesses the performance of each scheme in a real scenario, constructing an actual test environment and data set. We thoroughly evaluate the efficiency of each PRE scheme, considering the findings from both the theoretical study and the experimental simulation.
7.1. Property Analysis
In this section, we provide a comparison between our scheme and existing PRE schemes from the literature [5,18,19,21,22], as shown in Table 1. Our scheme offers several advantages over other schemes, which are as follows:

Table 1.
Properties analysis and comparison of the schemes.
- Improved Efficiency: In contrast to the predominant proxy re-encryption schemes relying on bilinear pairings, our study introduces a bilinear pair-free approach employing elliptic curves for construction. This innovative methodology substantially diminishes the computational overhead, amplifies efficiency, and elevates the scalability of the scheme in comparison to prevailing methods. Noteworthy is the adaptability of our scheme, especially in scenarios involving power-constrained devices, rendering it highly applicable across diverse settings.
- Fine-Grained Message-Level Delegation: In our scheme, fine-grained control at the message level is attained via the utilization of ephemeral random values. This distinctive feature bestows upon the authorizer the ability to encrypt specific data intended for sharing, utilizing the same ephemeral random value, while employing distinct values for encrypting other messages. Through the strategic selection of diverse ephemeral random values, the authorizer acquires meticulous control over data access, facilitating the nuanced and selective sharing of information. This heightened level of flexibility and precision empowers users to authorize and share data with the utmost accuracy, finely tailored to their specific needs.
- Non-Transferability Guarantee: Our PCBPRE+ scheme integrates ephemeral randomness, the message, and the sender’s public key in the computation and generation of the re-encryption key. This approach guarantees complete independence among sender A, receiver B, and proxy P, preventing any collusion between P and B to deduce the ephemeral random value generated by A. Consequently, authorized users are unable to transfer their decryption privileges to others, ensuring data security and maintaining ownership control. This robust protection mechanism prevents authorized users from transferring their decryption rights to unauthorized parties, thus mitigating unauthorized data dissemination and misuse. By upholding the independence of decryption rights, our scheme enhances data protection and control, fostering secure and accountable data sharing.
- Enhanced Functionality: Our proxy re-encryption scheme, founded on certificate-based encryption (CBE), presents notable advancements compared to conventional public-key proxy re-encryption. By harnessing the advantageous properties inherent in CBE, we adeptly tackle the challenge associated with certificate revocation. Moreover, our scheme proficiently eradicates both the key escrow and distribution challenges inherent in identity-based proxy re-encryption, thereby augmenting its functionality and applicability.
- Re-encryption Control Capability: In our scheme, the cryptographer encrypts the original ciphertext by generating unique ephemeral random values for each message. This strategy guarantees the resilience of the original ciphertext decryption, even in scenarios where the encryption algorithm fails to produce a corresponding random number for the message. However, this also signifies that decrypting the re-encrypted ciphertext becomes impractical, granting the encryptor full control over the re-encryption process.
The PCBPRE+ scheme presented in this paper introduces an innovative and efficient solution for secure cloud storage sharing. It incorporates notable advantages such as fine-grained sharing, non-transferable characteristics, and computational efficiency. These advantages bear substantial implications for fostering secure cloud storage sharing and have the potential to contribute significantly to the advancement of this field.
7.2. Efficiency Analysis
The performance of the proposed scheme is assessed in the subsequent analysis. Table 2 presents a comparison of the attributes between our scheme and the scheme mentioned in the literature [18,19,21,22]. The comprehensive cost analysis of our scheme is presented in Table 3. In these tables, we use the notations P, E, M, and H to represent the bilinear pair operation, exponential operation in group , multiplicative operation in group G, and the Hash operation, respectively, along with their respective coefficients indicating the number of operations performed.

Table 2.
Efficiency analysis.

Table 3.
Computation cost in proposed scheme.
To provide a comprehensive time complexity analysis of the comparison scheme, we refer to Boyen [29], who offers estimated relative times for individual asymmetric operations when instantiating group elements in super singular curves with 80 bits of security (SS/80) and MNT curves with 80 bits of security (MNT/80).
We denote the time complexities of pairing, exponential operations in group , multiplication operations in group G, and hash operations as , , , and respectively. The relevant information can be found in Table 4. Utilizing the data from Table 4, we computed the time complexities of the comparison schemes, presented in Table 5 and Table 6. The results demonstrate that our proposed strategy outperforms the previous pairing-based PRE scheme in terms of computational efficiency.

Table 4.
Temporal overhead of cryptographic operations (Relative time: 1 unit = 1).

Table 5.
Time complexities of MNT/80.

Table 6.
Time complexities of SS/80.
Finally, we conducted simulations to implement the scheme using the MIRACL library (version 7.0.0) and the PBC library (version 0.5.14). The experiments took place on a personal computer with an AMD Ryzen 7 5800H CPU operating at a frequency of 3.20 GHz. The simulation platform ran on Windows 11.
In this study, our main focus was on time-consuming operations, including exponential operations, scalar multiplication on elliptic curves, and bilinear pairing operations. We disregarded the computational costs associated with elliptic curve addition, modular multiplication, and regular hashing, as their impact was considered negligible. For detailed information about the symbols and execution times of these operations, please refer to Table 7. The comparison of computational costs between the scheme [18,19,21,22] and our proposed scheme is presented in Table 8, Figure 3 and Figure 4.

Table 7.
Executing time.

Table 8.
Efficiency comparison (ms).
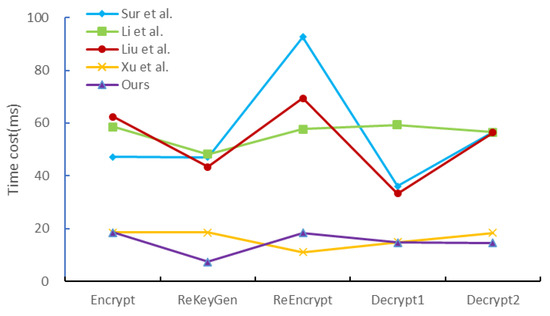
Figure 3.
Efficiency Analysis Line Chart [18,19,21,22].
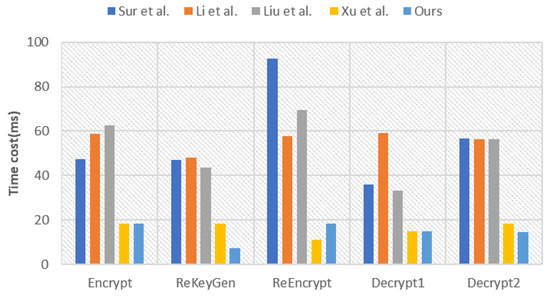
Figure 4.
Average running time of each phase [18,19,21,22].
The PCBPRE+ scheme proposed in this paper not only overcomes the limitations of existing schemes but also offers significant advantages in terms of efficiency, security, and functionality. These advancements are crucial for ensuring secure and efficient sharing of cloud storage and providing a viable solution for applications on computationally or power-constrained devices.
7.3. Application Analysis
In specific scenarios, our solution demonstrates irreplaceable advantages, especially in data transmission within the context of the Medical Internet of Things (MIoT). The emergence of MIoT has facilitated the expansion and implementation of remote medical care, allowing patients to comfortably receive real-time medical services at home. MIoT technology leverages cloud storage, thereby increasing storage capacity and computing power, driving the development of the MIoT framework. Our proposed solution offers three key advantages in this domain.
Firstly, it achieves fine-grained access control, enabling seamless data sharing at the message level. In the extensive backdrop of medical data, where some may be confidential and sensitive, and others have limited value to healthcare practitioners, this capability becomes crucial. By implementing fine-grained access control, our solution effectively regulates the sharing of medical data. This empowers the sender to exercise significant control over the data-sharing process, including the content that is re-encrypted, ensuring that only important medical data is transmitted and preventing unnecessary leakage of personal and sensitive privacy data.
Secondly, our solution possesses the non-transferable characteristic. Given the sensitivity of medical data, it is imperative to ensure that only authorized healthcare institutions have access to individuals’ health information. The non-transferability of our solution effectively prevents malicious disclosure, as only authorized recipients are allowed to transmit data within the framework.
Thirdly, the efficient implementation of our solution enables effective data sharing even in scenarios of rapid data growth or when the computational power of healthcare institutions is moderate.
Certainly, we should also consider potential limitations or conditions under which the solution may not perform as expected, such as excessive data storage, insufficient device computational power, or issues with third-party server failures. Adequate contingency plans should be prepared for such situations.
8. Conclusions
In this paper, we present a novel scheme called Pairing-free Certificate-Based Proxy Re-Encryption Plus (PCBPRE+) that facilitates the secure delegation of decryption privileges from one user to another, enabling flexible sharing of encrypted data among cloud users. Our innovative approach allows users to efficiently and securely send their encrypted data to recipients using public cloud storage, without the need for bilinear pairs. This results in improved efficiency and enhanced suitability for practical application environments. Moreover, PCBPRE+ addresses the challenges of certificate management and key distribution encountered in traditional PRE schemes. A key advantage of our scheme is the incorporation of non-transferability and message-level fine-grained delegation mechanisms, ensuring exclusive sharing of user data with authorized individuals and preventing any malicious leaks. We rigorously verify and evaluate the correctness, security, and performance of the proposed approach, demonstrating its ability to satisfy the chosen ciphertext security in the random oracle model. Overall, the PCBPRE+ scheme offers several advantages and significant application potential compared to existing PRE schemes. It provides a secure and efficient solution for data sharing in cloud environments, making it well suited for various practical scenarios.
Author Contributions
Methodology, L.Y. and H.Q.; Writing—review & editing, K.Y., H.X., X.A.W. and S.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by National Natural Science Foundation of China under Grant (NO. 62102312), Natural Science Foundation of Shaanxi Province (No. 2023-JC-YB-584), Engineering University of PAP’s Funding for Key Researcher (No. KYGG202011), and Xijing University Fund (No: XJ210206).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the Advances in Cryptology—EUROCRYPT’98: International Conference on the Theory and Application of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Kim, S.; Lee, I. IoT device security based on proxy re-encryption. J. Ambient. Intell. Humaniz. Comput. 2018, 9, 1267–1273. [Google Scholar] [CrossRef]
- Ge, C.; Susilo, W.; Baek, J.; Liu, Z.; Xia, J.; Fang, L. A verifiable and fair attribute-based proxy re-encryption scheme for data sharing in clouds. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2907–2919. [Google Scholar] [CrossRef]
- Yao, S.; Dayot, R.V.J.; Kim, H.J.; Ra, I.H. A novel revocable and identity-based conditional proxy re-encryption scheme with ciphertext evolution for secure cloud data sharing. IEEE Access 2021, 9, 42801–42816. [Google Scholar] [CrossRef]
- Kan, J.; Zhang, J.; Liu, D.; Huang, X. Proxy re-encryption scheme for decentralized storage networks. Appl. Sci. 2022, 12, 4260. [Google Scholar] [CrossRef]
- Susilo, W.; Dutta, P.; Duong, D.H.; Roy, P.S. Lattice-based HRA-secure attribute-based proxy re-encryption in standard model. In Proceedings of the Computer Security–ESORICS 2021: 26th European Symposium on Research in Computer Security, Darmstadt, Germany, 4–8 October 2021; Proceedings, Part II 26. Springer: Berlin/Heidelberg, Germany, 2021; pp. 169–191. [Google Scholar]
- Ateniese, G.; Fu, K.; Green, M.; Hohenberger, S. Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur. (TISSEC) 2006, 9, 1–30. [Google Scholar] [CrossRef]
- Canetti, R.; Hohenberger, S. Chosen-ciphertext secure proxy re-encryption. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 2 November–31 October 2007; pp. 185–194. [Google Scholar]
- Libert, B.; Vergnaud, D. Unidirectional chosen-ciphertext secure proxy re-encryption. In Proceedings of the Public Key Cryptography—PKC 2008: 11th International Workshop on Practice and Theory in Public-Key Cryptography, Barcelona, Spain, 9–12 March 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 360–379. [Google Scholar]
- Shao, J.; Cao, Z. CCA-secure proxy re-encryption without pairings. In Proceedings of the Public Key Cryptography—PKC 2009: 12th International Conference on Practice and Theory in Public Key Cryptography, Irvine, CA, USA, 18–20 March 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 357–376. [Google Scholar]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef]
- Han, J.; Susilo, W.; Mu, Y. Identity-based data storage in cloud computing. Future Gener. Comput. Syst. 2013, 29, 673–681. [Google Scholar] [CrossRef]
- Luo, S.; Shen, Q.; Chen, Z. Fully secure unidirectional identity-based proxy re-encryption. In Proceedings of the Information Security and Cryptology-ICISC 2011: 14th International Conference, Seoul, Korea, 30 November–2 December 2011; Revised Selected Papers 14. Springer: Berlin/Heidelberg, Germany, 2012; pp. 109–126. [Google Scholar]
- Liang, K.; Chu, C.K.; Tan, X.; Wong, D.S.; Tang, C.; Zhou, J. Chosen-ciphertext secure multi-hop identity-based conditional proxy re-encryption with constant-size ciphertexts. Theor. Comput. Sci. 2014, 539, 87–105. [Google Scholar] [CrossRef]
- Sur, C.; Jung, C.D.; Park, Y.; Rhee, K.H. Chosen-ciphertext secure certificateless proxy re-encryption. In Proceedings of the Communications and Multimedia Security: 11th IFIP TC 6/TC 11 International Conference, CMS 2010, Linz, Austria, 31 May–2 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 214–232. [Google Scholar]
- Xu, L.; Wu, X.; Zhang, X. CL-PRE: A certificateless proxy re-encryption scheme for secure data sharing with public cloud. In Proceedings of the 7th ACM Symposium on Information, Computer and Communications Security, Seoul, Republic of Korea, 2–4 May 2012; pp. 87–88. [Google Scholar]
- Wang, L.L.; Chen, K.F.; Mao, X.P.; Wang, Y.T. Efficient and provably-secure certificateless proxy re-encryption scheme for secure cloud data sharing. J. Shanghai Jiaotong Univ. (Sci.) 2014, 19, 398–405. [Google Scholar] [CrossRef]
- Sur, C.; Park, Y.; Shin, S.U.; Rhee, K.H.; Seo, C. Certificate-based proxy re-encryption for public cloud storage. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, Taiwan, 3–5 July 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 159–166. [Google Scholar]
- Xu, J.; Chen, K.; Shen, Z.; Xu, X. Pairing-free certificate-based multi-domain conditional proxy re-encryption scheme. J. Cryptologic Res. 2018, 5, 55–67. [Google Scholar]
- Tian, J.; Lu, Y.; Wang, F.; Yu, X. Efficient Multi-receiver Certificate-Based Proxy Re-encryption Scheme for Secure Cloud Data Sharing. In Proceedings of the Advances in Artificial Intelligence and Security: 7th International Conference, ICAIS 2021, Dublin, Ireland, 19–23 July 2021; Proceedings, Part II 7. Springer: Berlin/Heidelberg, Germany, 2021; pp. 593–605. [Google Scholar]
- Li, J.; Zhao, X.; Zhang, Y.; Yao, W. Provably Secure Certificate-based Conditional Proxy Re-encryption. J. Inf. Sci. Eng. 2016, 32, 813. [Google Scholar]
- Liu, S.; Qin, H.; Taniar, D.; Liu, W.; Li, Y.; Zhang, J. A certificate-based proxy re-encryption plus scheme for secure medical data sharing. Internet Things 2023, 23, 100836. [Google Scholar] [CrossRef]
- Wang, X.A.; Xhafa, F.; Ma, J.; Zheng, Z. Controlled secure social cloud data sharing based on a novel identity based proxy re-encryption plus scheme. J. Parallel Distrib. Comput. 2019, 130, 153–165. [Google Scholar] [CrossRef]
- Singh, K.; Rangan, C.P.; Sheshank, S.; Agrawal, R. Lattice-based unidirectional Proxy Re-Encryption and Proxy Re-Encryption+ schemes. IET Inf. Secur. 2021, 15, 1–12. [Google Scholar] [CrossRef]
- Singh, K.; Rangan, C.P.; Agrawal, R.; Sheshank, S. Provably secure lattice based identity based unidirectional PRE and PRE+ schemes. J. Inf. Secur. Appl. 2020, 54, 102569. [Google Scholar] [CrossRef]
- Wang, X.A.; Ge, Y.; Yang, X. PRE+: Dual of proxy re-encryption and its application. Cryptol. ePrint Arch. 2013, 2013, 872. [Google Scholar]
- Wang, X.A.; Xhafa, F.; Ma, J.; Barolli, L.; Ge, Y. PRE+: Dual of proxy re-encryption for secure cloud data sharing service. Int. J. Web Grid Serv. 2018, 14, 44–69. [Google Scholar] [CrossRef]
- Lu, Y.; Li, J. A pairing-free certificate-based proxy re-encryption scheme for secure data sharing in public clouds. Future Gener. Comput. Syst. 2016, 62, 140–147. [Google Scholar] [CrossRef]
- Boyen, X. The BB1 Identity-Based Cryptosystem: A Standard for Encryption and Key Encapsulation; IEEE P1363.3; Identity-Based Public Key Cryptocraphy; IEEE: Piscataway, NJ, USA, 2006. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).