Automated Repair of Smart Contract Vulnerabilities: A Systematic Literature Review
Abstract
1. Introduction
- The focus is on cutting-edge solutions that have been applied for vulnerability correction in SCs. In this respect, 31 journal articles and conference papers published between 2020 and 21 June 2024 will be explored.
- We classify automated repair frameworks under three different perspectives: the approaches related to APR, the rewriting strategies employed, and the detection tools utilized.
- We highlight a number of contemporary open challenges intended to tackle substantial issues that occur when different frameworks are applied to the correction of vulnerabilities.
2. Preliminaries
2.1. Blockchain
2.2. Ethereum
2.3. Smart Contract (SC)
- An on-chain execution is defined as any operation that is replicated across all participants within the blockchain network.
- Off-chain refers to the process of assigning the execution or operation that influences the ultimate state of the blockchain ledger to a specific group of nodes.
- Hybrid execution refers to a process that integrates both off-chain and on-chain operations in its execution framework.
2.4. Vulnerability
2.5. Automated Smart Contract Vulnerability Correction
3. Related Work
4. Methodology
4.1. Research Questions (RQs)
- RQ1: What recent trends automatically generate security patches for vulnerable SCs?
- RQ2: What types of vulnerabilities are fixed by novel rectification frameworks?
- RQ3: What types of vulnerability detection tools are employed by automated repair frameworks when addressing SCs?
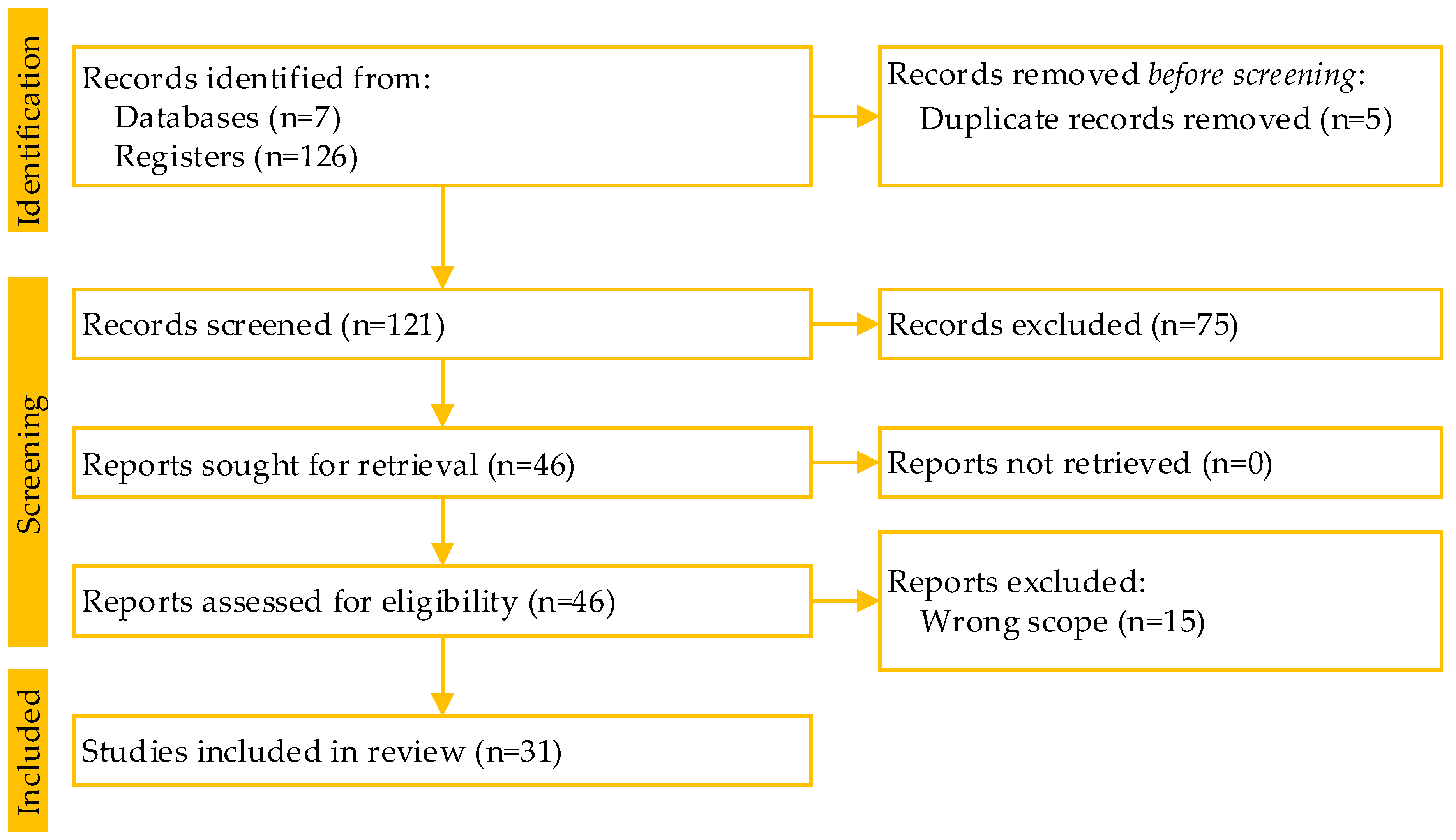
4.2. Selection of Primary Studies
4.3. Inclusion and Exclusion Criteria
4.4. Selection Results
- IEEE: 38 results.
- ScienceDirect: 13 results.
- Springer: 15 results.
- ACM: 41 results.
- Wiley: 8 results.
- Taylor and Francis: 3 results.
- Online archives: 8.
5. Taxonomy of Fixing Techniques for SC Vulnerabilities
5.1. Search-Based Approach
5.1.1. Bytecode-Level Rewriting Strategy
5.1.2. Source Code-Level Rewriting Strategy
5.2. Constraint-Based Approach
5.3. Template-Based Approach
5.3.1. Bytecode-Level Rewriting Strategy
5.3.2. Source Code-Level Rewriting Strategy
5.4. Learning-Based Approach
5.5. Large Language Model (LLM)-Based Approach
6. Comparison
6.1. RQ1: What Recent Trends Automatically Generate Security Patches for Vulnerable SCs?
6.2. RQ2: What Types of Vulnerabilities Are Fixed by Novel Rectification Frameworks?
6.3. RQ3: What Types of Vulnerability Detection Tools Are Employed by Automated Repair Frameworks When Addressing SCs?
7. Discussion
8. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Qian, P.; Cao, R.; Liu, Z.; Li, W.; Li, M.; Zhang, L.; Xu, Y.; Chen, J.; He, Q. Empirical review of smart contract and defi security: Vulnerability detection and automated repair. arXiv 2023, arXiv:2309.02391. [Google Scholar]
- Salzano, F.; Scalabrino, S.; Oliveto, R.; Pareschi, R. Fixing Smart Contract Vulnerabilities: A Comparative Analysis of Literature and Developer’s Practices. arXiv 2024, arXiv:2403.07458. [Google Scholar]
- Kumar, N.K.; Honnungar, N.V.; Prakash, M.S.; Lohith, J. Vulnerabilities in Smart Contracts: A Detailed Survey of Detection and Mitigation Methodologies. In Proceedings of the 2024 International Conference on Emerging Technologies in Computer Science for Interdisciplinary Applications (ICETCS), Bengaluru, India, 22–23 April 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–7. [Google Scholar]
- Kiani, R.; Sheng, V.S. Ethereum Smart Contract Vulnerability Detection and Machine Learning-Driven Solutions: A Systematic Literature Review. Electronics 2024, 13, 2295. [Google Scholar] [CrossRef]
- Yu, X.L.; Al-Bataineh, O.; Lo, D.; Roychoudhury, A. Smart contract repair. ACM Trans. Softw. Eng. Methodol. (TOSEM) 2020, 29, 1–32. [Google Scholar] [CrossRef]
- Wu, C.; Xiong, J.; Xiong, H.; Zhao, Y.; Yi, W. A review on recent progress of smart contract in blockchain. IEEE Access 2022, 10, 50839–50863. [Google Scholar] [CrossRef]
- Wang, M.; Xie, Z.; Wen, X.; Li, J.; Zhou, K. Ethereum smart contract vulnerability detection model based on triplet loss and BiLSTM. Electronics 2023, 12, 2327. [Google Scholar] [CrossRef]
- Fei, J.; Chen, X.; Zhao, X. MSmart: Smart contract vulnerability analysis and improved strategies based on smartcheck. Appl. Sci. 2023, 13, 1733. [Google Scholar] [CrossRef]
- Qian, S.; Ning, H.; He, Y.; Chen, M. Multi-label vulnerability detection of smart contracts based on Bi-LSTM and attention mechanism. Electronics 2022, 11, 3260. [Google Scholar] [CrossRef]
- Sujeetha, R.; Akila, K. Improving Coverage and Vulnerability Detection in Smart Contract Testing Using Self-Adaptive Learning GA. IETE J. Res. 2024, 70, 1593–1606. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and Securing Relationships on Public Networks; First Monday: Canton, TX, USA, 1997. [Google Scholar]
- Luu, L.; Chu, D.-H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–29 October 2016; pp. 254–269. [Google Scholar]
- Liu, Y.; He, J.; Li, X.; Chen, J.; Liu, X.; Peng, S.; Cao, H.; Wang, Y. An overview of blockchain smart contract execution mechanism. J. Ind. Inf. Integr. 2024, 41, 100674. [Google Scholar] [CrossRef]
- Ali, I.M.; Abdallah, M.M. On Off-chaining Smart Contract Runtime Protection: A Queuing Model Approach. IEEE Trans. Parallel Distrib. Syst. 2024, 35, 1345–1359. [Google Scholar] [CrossRef]
- Liu, B.; Sun, S.; Szalachowski, P. Smacs: Smart contract access control service. In Proceedings of the 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Valencia, Spain, 29 June–2 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 221–232. [Google Scholar]
- Frassetto, T.; Jauernig, P.; Koisser, D.; Kretzler, D.; Schlosser, B.; Faust, S.; Sadeghi, A.-R. POSE: Practical off-chain smart contract execution. arXiv 2022, arXiv:2210.07110. [Google Scholar]
- Chen, W.; Yang, Z.; Zhang, J.; Liang, J.; Sun, Q.; Zhou, F. Enhancing Blockchain Performance via On-chain and Off-chain Collaboration. In Proceedings of the International Conference on Service-Oriented Computing, Rome, Italy, 28 November–1 December 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 393–408. [Google Scholar]
- Ali, I.M.; Lasla, N.; Abdallah, M.M.; Erbad, A. SRP: An efficient runtime protection framework for blockchain-based smart contracts. J. Netw. Comput. Appl. 2023, 216, 103658. [Google Scholar] [CrossRef]
- Reno, S.; Priya, S.H.; Al-Kafi, G.A.; Tasfia, S.; Turna, M.K. A novel approach to optimizing transaction processing rate and space requirement of blockchain via off-chain architecture. Int. J. Inf. Technol. 2024, 16, 2379–2394. [Google Scholar] [CrossRef]
- Xian, D.; Wei, X. ICOE: A Lightweight Group-Consensus-Based Off-Chain Execution Model for Smart Contract-Based Industrial Applications. IEEE Trans. Ind. Inform. 2023, 20, 1895–1906. [Google Scholar] [CrossRef]
- Wang, W.; Song, J.; Xu, G.; Li, Y.; Wang, H.; Su, C. Contractward: Automated vulnerability detection models for ethereum smart contracts. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1133–1144. [Google Scholar] [CrossRef]
- Colin, L.S.H.; Mohan, P.M.; Pan, J.; Keong, P.L.K. An Integrated Smart Contract Vulnerability Detection Tool Using Multi-layer Perceptron on Real-time Solidity Smart Contracts. IEEE Access 2024, 12, 23549–23567. [Google Scholar] [CrossRef]
- Liao, J.-W.; Tsai, T.-T.; He, C.-K.; Tien, C.-W. Soliaudit: Smart contract vulnerability assessment based on machine learning and fuzz testing. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; IEEE: New York, NY, USA, 2019; pp. 458–465. [Google Scholar]
- Momeni, P.; Wang, Y.; Samavi, R. Machine learning model for smart contracts security analysis. In Proceedings of the 2019 17th International Conference on Privacy, Security and Trust (PST), Fredericton, NB, Canada, 26–28 August 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Hwang, S.; Ryu, S. Gap between theory and practice: An empirical study of security patches in solidity. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–17 July 2020; pp. 542–553. [Google Scholar]
- Tolmach, P.; Li, Y.; Lin, S.-W.; Liu, Y.; Li, Z. A survey of smart contract formal specification and verification. ACM Comput. Surv. (CSUR) 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Garfatta, I.; Klai, K.; Gaaloul, W.; Graiet, M. A survey on formal verification for solidity smart contracts. In Proceedings of the 2021 Australasian Computer Science Week Multiconference, Dunedin, New Zealand, 1–5 February 2021; pp. 1–10. [Google Scholar]
- Zhang, Z.; Zhang, B.; Xu, W.; Lin, Z. Demystifying exploitable bugs in smart contracts. In Proceedings of the 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE), Melbourne, Australia, 14–20 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 615–627. [Google Scholar]
- Chu, H.; Zhang, P.; Dong, H.; Xiao, Y.; Ji, S.; Li, W. A survey on smart contract vulnerabilities: Data sources, detection and repair. Inf. Softw. Technol. 2023, 159, 107221. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, X.; Huang, Y.; Zhu, H.-N.; Bian, J.; Zheng, Z. An empirical study on real bug fixes from solidity smart contract projects. J. Syst. Softw. 2023, 204, 111787. [Google Scholar] [CrossRef]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G.; PRISMA Group. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. Ann. Intern. Med. 2009, 151, 264–269. [Google Scholar] [CrossRef]
- Huang, K.; Xu, Z.; Yang, S.; Sun, H.; Li, X.; Yan, Z.; Zhang, Y. A survey on automated program repair techniques. arXiv 2023, arXiv:2303.18184. [Google Scholar]
- Hou, Z.; Dong, C.; Shang, Y. HermHD: Enhancing smart contract security based on code obfuscation. In Proceedings of the 2023 11th International Conference on Information Technology: IoT and Smart City, Kyoto Japan, 14–17 December 2023; pp. 96–101. [Google Scholar]
- Nassirzadeh, B.; Sun, H.; Banescu, S.; Ganesh, V. Gas gauge: A security analysis tool for smart contract out-of-gas vulnerabilities. In Proceedings of the International Conference on Mathematical Research for Blockchain Economy, Vilamoura, Portugal, 12–14 July 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 143–167. [Google Scholar]
- Ren, M.; Ma, F.; Yin, Z.; Fu, Y.; Li, H.; Chang, W.; Jiang, Y. Making smart contract development more secure and easier. In Proceedings of the 29th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Athens, Greece, 23–28 August 2021; pp. 1360–1370. [Google Scholar]
- Liu, Y.; Mechtaev, S.; Subotić, P.; Roychoudhury, A. Program Repair Guided by Datalog-Defined Static Analysis. In Proceedings of the 31st ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering, San Francisco, CA, USA, 3–9 December 2023; pp. 1216–1228. [Google Scholar]
- Zhang, Y.; Ma, S.; Li, J.; Li, K.; Nepal, S.; Gu, D. Smartshield: Automatic smart contract protection made easy. In Proceedings of the 2020 IEEE 27th International Conference on Software Analysis, Evolution and Reengineering (SANER), London, ON, Canada, 18–21 February 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 23–34. [Google Scholar]
- Rodler, M.; Li, W.; Karame, G.O.; Davi, L. {EVMPatch}: Timely and automated patching of ethereum smart contracts. In Proceedings of the 30th Usenix Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–12 August 2021; pp. 1289–1306. [Google Scholar]
- Jin, H.; Wang, Z.; Wen, M.; Dai, W.; Zhu, Y.; Zou, D. Aroc: An automatic repair framework for on-chain smart contracts. IEEE Trans. Softw. Eng. 2021, 48, 4611–4629. [Google Scholar] [CrossRef]
- Ferreira Torres, C.; Jonker, H.; State, R. Elysium: Context-aware bytecode-level patching to automatically heal vulnerable smart contracts. In Proceedings of the 25th International Symposium on Research in Attacks, Intrusions and Defenses, Limassol, Cyprus, 26–28 October 2022; pp. 115–128. [Google Scholar]
- Guo, S. Automatic Patch Generation System for Smart Contract. In Proceedings of the 2023 IEEE 6th Eurasian Conference on Educational Innovation (ECEI), Singapore, 3–5 February 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 59–62. [Google Scholar]
- Feng, Z.; Feng, Y.; He, H.; Zhang, W.; Zhang, Y. A bytecode-based integrated detection and repair method for reentrancy vulnerabilities in smart contracts. IET Blockchain 2023, 4, 235–251. [Google Scholar] [CrossRef]
- Shi, Y.; Zuo, H.; Zhang, Q.; Qin, Z.; Chen, L.; Jiang, X. Automatic Patching of Smart Contract Vulnerabilities Based on Comprehensive Bytecode Rewriting. In Proceedings of the 2023 8th International Conference on Signal and Image Processing (ICSIP), Wuxi, China, 8–10 July 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 763–767. [Google Scholar]
- Huang, R.; Shen, Q.; Wang, Y.; Wu, Y.; Wu, Z.; Luo, X.; Ruan, A. ReenRepair: Automatic and semantic equivalent repair of reentrancy in smart contracts. J. Syst. Softw. 2024, 216, 112107. [Google Scholar] [CrossRef]
- Li, Z.; Zhou, Y.; Guo, S.; Xiao, B. Solsaviour: A defending framework for deployed defective smart contracts. In Proceedings of the 37th Annual Computer Security Applications Conference, Virtual Event, 6–10 December 2021; pp. 748–760. [Google Scholar]
- Nguyen, T.D.; Pham, L.H.; Sun, J. SGUARD: Towards fixing vulnerable smart contracts automatically. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1215–1229. [Google Scholar]
- Thyagarajan, S.A.K.; Bhat, A.; Magri, B.; Tschudi, D.; Kate, A. Reparo: Publicly verifiable layer to repair blockchains. In Proceedings of the International Conference on Financial Cryptography and Data Security, Virtual Event, 1–5 March 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 37–56. [Google Scholar]
- Giesen, J.-R.; Andreina, S.; Rodler, M.; Karame, G.O.; Davi, L. Practical mitigation of smart contract bugs. arXiv 2022, arXiv:2203.00364. [Google Scholar]
- Beillahi, S.M.; Keilty, E.; Nelaturu, K.; Veneris, A.; Long, F. Automated auditing of price gouging TOD vulnerabilities in smart contracts. In Proceedings of the 2022 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Virtual Event, 2–5 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Antonino, P.; Ferreira, J.; Sampaio, A.; Roscoe, A. Specification is law: Safe creation and upgrade of ethereum smart contracts. In Proceedings of the International Conference on Software Engineering and Formal Methods, Berlin, Germany, 26–30 September 2022; Springer: Cham, Switzerland, 2022; pp. 227–243. [Google Scholar]
- Chen, Q.; Zhou, T.; Liu, K.; Li, L.; Ge, C.; Liu, Z.; Klein, J.; Bissyandé, T.F. Tips: Towards automating patch suggestion for vulnerable smart contracts. Autom. Softw. Eng. 2023, 30, 31. [Google Scholar] [CrossRef]
- Fang, P. CONTRACTFIX: A Framework for Automatically Fixing Vulnerabilities in Smart Contracts. arXiv 2023, arXiv:2307.08912. [Google Scholar]
- Xi, R.; Pattabiraman, K. A large-scale empirical study of low-level function use in Ethereum smart contracts and automated replacement. Softw. Pract. Exp. 2023, 53, 631–664. [Google Scholar] [CrossRef]
- Gao, C.; Yang, W.; Ye, J.; Xue, Y.; Sun, J. sGuard+: Machine learning guided rule-based automated vulnerability repair on smart contracts. ACM Trans. Softw. Eng. Methodol. 2024, 33, 1–55. [Google Scholar] [CrossRef]
- Zhou, X.; Chen, Y.; Guo, H.; Chen, X.; Huang, Y. Security code recommendations for smart contract. In Proceedings of the 2023 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER), Macao, China, 21–24 March 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 190–200. [Google Scholar]
- Guo, H.; Chen, Y.; Chen, X.; Huang, Y.; Zheng, Z. Smart contract code repair recommendation based on reinforcement learning and multi-metric optimization. ACM Trans. Softw. Eng. Methodol. 2024, 33, 1–31. [Google Scholar] [CrossRef]
- So, S.; Oh, H. Smartfix: Fixing vulnerable smart contracts by accelerating generate-and-verify repair using statistical models. In Proceedings of the 31st ACM Joint European Software Engineering Conference and Symposium on the Foundations of Software Engineering, San Francisco, CA, USA, 3–9 December 2023; pp. 185–197. [Google Scholar]
- Napoli, E.A.; Gatteschi, V. Evaluating chatgpt for smart contracts vulnerability correction. In Proceedings of the 2023 IEEE 47th Annual Computers, Software, and Applications Conference (COMPSAC), Torino, Italy, 26–30 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1828–1833. [Google Scholar]
- Ibba, G.; Ortu, M.; Tonelli, R.; Destefanis, G. Leveraging ChatGPT for Automated Smart Contract Repair: A Preliminary Exploration of GPT-3-Based Approaches. Available at SSRN 4474678. 2023. Available online: https://ssrn.com/abstract=4474678 (accessed on 21 June 2024).
- Jain, A.; Masud, E.; Han, M.; Dhillon, R.; Rao, S.; Joshi, A.; Cheema, S.; Kumar, S. Two Timin’: Repairing Smart Contracts With A Two-Layered Approach. In Proceedings of the 2023 Second International Conference on Informatics (ICI), Noida, India, 23–25 November 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Zhang, L.; Li, K.; Sun, K.; Wu, D.; Liu, Y.; Tian, H.; Liu, Y. Acfix: Guiding llms with mined common rbac practices for context-aware repair of access control vulnerabilities in smart contracts. arXiv 2024, arXiv:2403.06838. [Google Scholar]
- Kumar, M.; Packer, B.; Koller, D. Self-paced learning for latent variable models. In Proceedings of the Advances in Neural Information Processing Systems (NIPS) 23, Vancouver, BC, Canada, 6–9 December 2010. [Google Scholar]
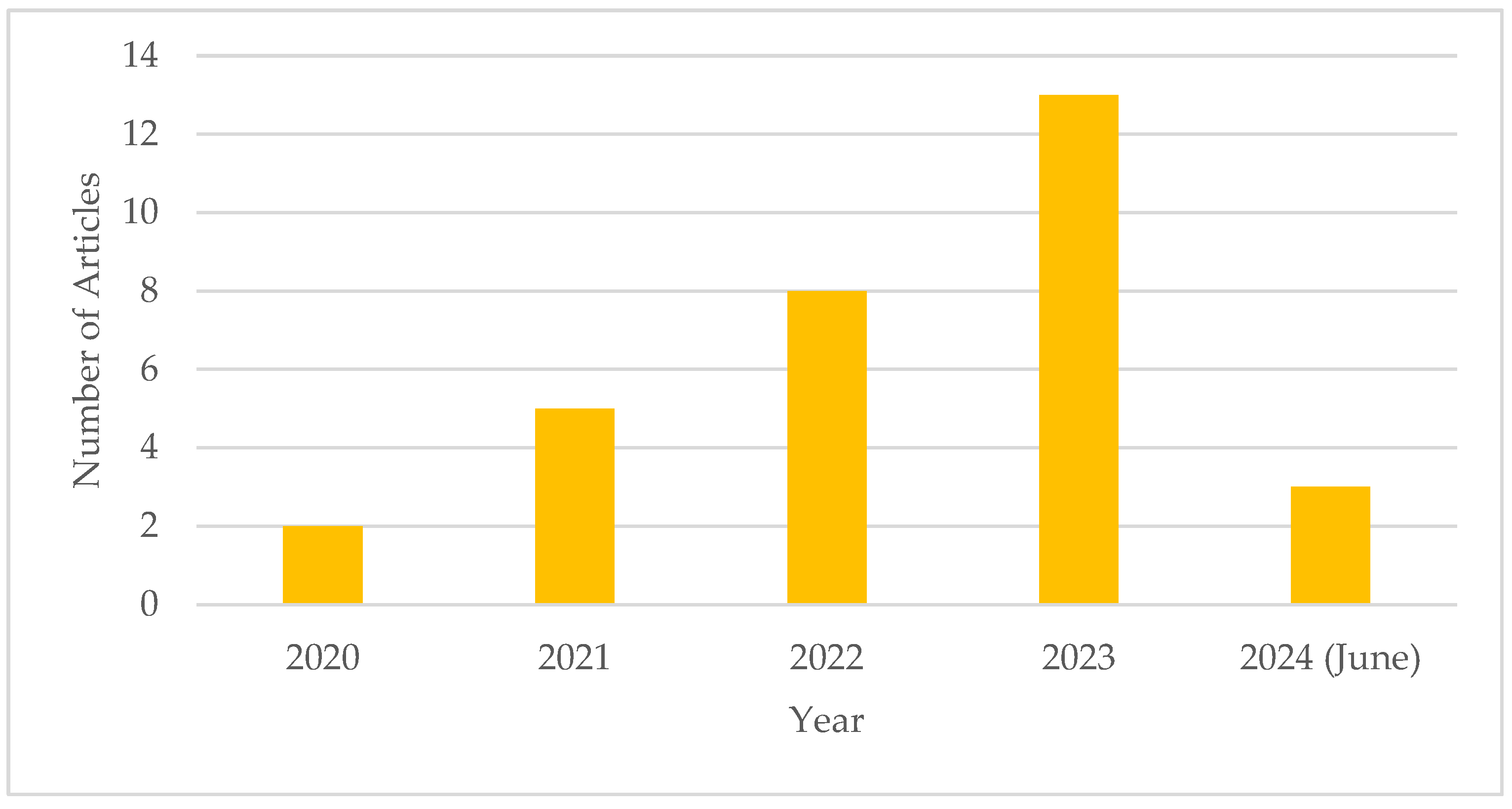

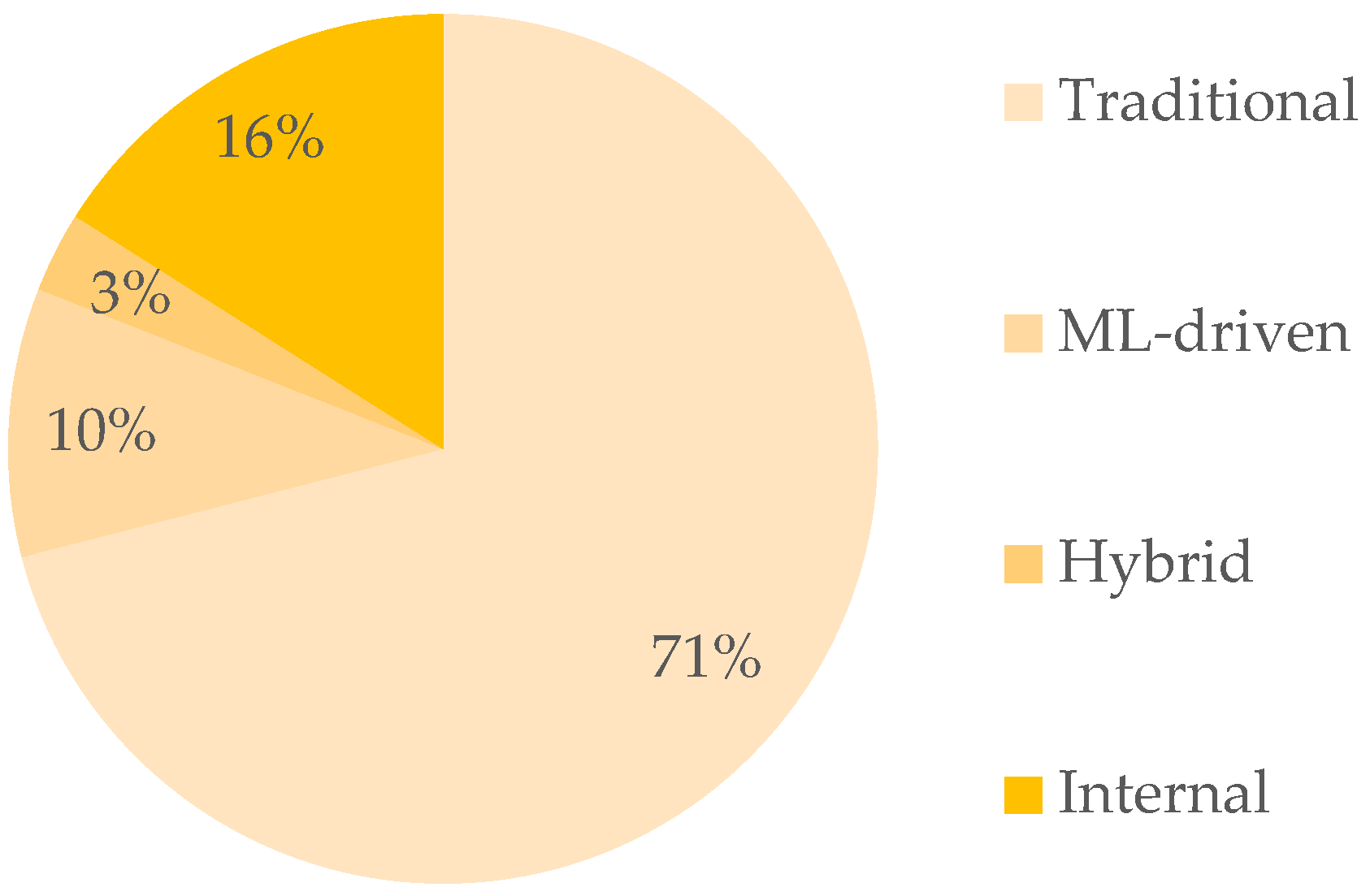
| Mechanism | Execution Type | Detail |
|---|---|---|
| SMACS [15] | off-chain | SMACS serves as an off-chain framework that delivers precise access control guidelines for SCs, characterized by its dynamic extensibility and reduced on-chain overhead. In order to activate SMACS, the owner of the SC is required to amend the contract to incorporate the verification of SMACS tokens for each method that can be accessed externally. Nonetheless, it breaches the immutability principle by allowing the contract owner to make dynamic updates to the rules. In addition, the SMACS cannot provide protection for contracts that were deployed without a pre-established upgrade mechanism. |
| POSE [16] | off-chain | POSE offers robust security assurances, even in scenarios where a significant number of participants are compromised. The purpose of POSE is to permit a collection of users to operate an intricate SC on several systems that are enabled with Trusted Execution Environments (TEEs). This framework, however, is independent of any specific TEE. This off-chain-based strategy functions by randomly choosing a group of TEEs to carry out each SC, designating one enclave as the executor while the remaining enclaves serve as watchdogs. |
| Chen et al.’s model [17] | hybrid | The research conducted by Chen et al. [17] presents a novel concurrent execution strategy that merges off-chain execution with the on-chain concurrent execution framework. This integration allows a blockchain system to boost its performance without sacrificing security and decentralization. By organizing transaction scheduling information in relation to execution-related data, this framework improves the efficiency of both information dissemination and execution among nodes. |
| SRP [18] | hybrid | SRP provides real-time protection for deployed SCs against attacks, ensuring that the performance of the underlying blockchain remains unaffected. This framework outlines a protocol tailored for interoperability in off-chain runtime verification. The SRP exhibits enhanced service time and throughput when contrasted with an on-chain-only mechanism, especially in scenarios involving escalating workloads. |
| Twin-Ledger [19] | off-chain | Twin-Ledger architecture introduces an innovative method to address the challenges of throughput without expanding block size and substantial space demands in public ledgers. This framework enables the integration of any consensus mechanism, but it particularly leverages the Proof-of-Work consensus to achieve scalability and decentralization without sacrificing security. |
| ICOE [20] | off-chain | ICOE serves as an off-chain execution paradigm aimed at addressing the scalability difficulties linked to SC-based industrial applications within blockchain environments. This framework allows the invoked SC to operate only within its specific group, ensuring that the execution result is returned solely to the invoked SC. Nevertheless, irrespective of the volume of data stored in SCs, the ICOE system transfers SCs that are initially stored on-chain to various off-chain consensus groups. This significantly alleviates the storage demands on the on-chain blockchain. Furthermore, the ICOE system is capable of supporting a wide range of applications based on smart contracts. |
| Isras et al.’s model [14] | off-chain | The research conducted by Isra et al. [14] presents a queuing model focused on off-chain runtime verification and the process of block generation. This model is capable of efficiently and flexibly representing the non-deterministic nature of blockchain systems, allowing for the estimation of both the number of transactions in the pool and their respective waiting times. |
| Reference | Environment | Review Type | Year of Pub | Selection Process | Taxonomy | Year Covered |
|---|---|---|---|---|---|---|
| [25] | Solidity | empirical review | 2020 | semi-clear 1 | - | 14 December 2018–31 March 2019 |
| [26] | SC formal specification and verification | survey | 2021 | clear 2 | ✓ | September 2014–June 2020 |
| [27] | Formal verification for Solidity SCs | survey | 2021 | semi-clear 3 | ✓ | 2008–2018 4 |
| [28] | Bugs | SLR | 2023 | not clear 5 | ✓ | 2021–2022 6 |
| [1] | DeFi 7 security | empirical review | 2023 | not clear 5 | - | 2020–2021 |
| [29] | Off-chain and on-chain repair | SLR | 2023 | clear 2 | ✓ | 2015–2023 |
| [30] | Bugs | empirical review | 2023 | clear 2 | ✓ | 2016–2021 |
| [3] | APR | survey | 2024 | not clear 5 | - | 2019–2023 4 |
| Reference | Research Questions |
|---|---|
| [25] | 1: Does the Solidity language become more secure by fixing known vulnerabilities? 2: Does the Solidity compiler get security patches for the known vulnerabilities? 3: Would Solidity developers take advantage of the repaired Solidity compilers? 4: Are the compiler patches effective enough to prevent their target vulnerabilities? 5: Do developers actually make bugs and errors due to such vulnerabilities? |
| [26] | 1: What are the formal techniques used for modeling, specification, and verification of SCs? 2: What are the common formal requirements specified and verified by these techniques? 3: What are the challenges introduced by SC and blockchain environment in formalizing and verifying SCs? 4: What are the current limitations in SC formal specification and verification and what research directions may be taken to overcome them? |
| [28] | 1: What kinds of exploitable bugs are machine auditable by existing tools? 2: How many real-world exploitable bugs are machine auditable? 3: How difficult is it to audit exploitable bugs? 4: What are the root causes, categories, and distributions of machine unauditable bugs? 5: What are the symptoms and fixes of machine unauditable bugs? |
| [1] | 1: How do traditional SC vulnerability detection tools perform when applied to DeFi protocols? 2: What is the performance of state-of-the-art tools in detecting DeFi attacks or vulnerabilities? |
| [29] | 1: What are the existing vulnerability defense methods? 2: What are the strengths and limitations of those repair methods? 3: What vulnerabilities are covered by those vulnerability repair methods? |
| [30] | 1: What types of files are involved when fixing bugs? 2: How many Solidity files are modified during a fix? 3: How many Solidity files are necessary to be added or deleted to fix bugs? 4: What is the most common fix operation during bug fixes? 5: How many element kinds are modified in a Solidity file during bug fixes? 6: How many fix actions are taken to a Solidity file during bug fixes? |
| APR Model and Rewriting Strategy | Availability |
|---|---|
| Search-based Bytecode-level | |
| HermHD [33] | https://github.com/ByteCodeMaster/HermHD (7 September 2024) |
| Search-based Source Code-level | |
| SCRepair [5] | https://SCRepair-APR.github.io (7 September 2024) |
| Gas Gauge [34] | https://gasgauge.github.io/ (7 September 2024) |
| DeFinery [26] | https://sites.google.com/view/ase2022-definery/ (7 September 2024) |
| Constraint-based Source Code-level | |
| Ren et al.’s model [35] | https://github.com/FISCO-BCOS/SCStudio (7 September 2024) |
| SymlogRepair [36] | https://github.com/symlog/symlog (7 September 2024) |
| Template-based Bytecode-level | |
| SmartShield [37] | on request |
| EVMPatch [38] | https://github.com/uni-due-syssec/evmpatch-developer-study (7 September 2024) |
| Aroc [39] | - |
| Elysium [40] | https://github.com/christoftorres/Elysium (7 September 2024) |
| APG [41] | - |
| Feng et al.’s model [42] | on request |
| EtherEditor [43] | - |
| ReenRepair [44] | on request |
| Template-based Source Code-level | |
| SGuard [46] | https://github.com/reentrancy/sGuard (7 September 2024) |
| SolSaviour [45] | - |
| Reparo [47] | - |
| HCC [48] | - |
| TOD [49] | https://github.com/Veneris-Group/TOD-Location-Rectificatio (7 September 2024) |
| Trusted Deployer [50] | https://github.com/formalblocks/safeevolution (7 September 2024) |
| TIPS [51] | https://github.com/CVbluecat/TIPS (7 September 2024) |
| ContractFix [42] | https://github.com/research1132/ContractFix (7 September 2024) |
| GoHigh [53] | https://github.com/DependableSystemsLab/GoHigh (7 September 2024) |
| SGuard+ [54] | https://doi.org/10.5281/zenodo.8249340 (7 September 2024) |
| Learning-based Source Code-level | |
| SmartRep [55] | https://github.com/AnonymousGithub5/SmartRep (7 September 2024) |
| RLRep [56] | https://github.com/Anonymous123xx/RLRep (7 September 2024) |
| SmartFix [57] | https://doi.org/10.5281/zenodo.8256377 (7 September 2024) |
| LLM-based Source Code-level | |
| Napoli et al.’s model [58] | https://github.com/enaples/solgpt (7 September 2024) |
| Ibba et al.’s model [59] | - |
| Two Timin [60] | - |
| ACFIX [61] | https://sites.google.com/view/acfixsmartcontract (7 September 2024) |
| Framework | # Vulnerabilities | Types of Vulnerabilities |
|---|---|---|
| HermHD [33] | 1 | protect from reverse engineering |
| SCRepair [5] | 4 | transaction order dependency, reentrancy, exception disorder, and integer overflow |
| Gas Gauge [34] | 1 | out-of-gas denial of services |
| DeFinery [26] | 2 | reentrancy and unchecked send |
| Ren et al.’s model [35] | 9 | access control, arithmetic, backdoor threats, front running, locked Ether, reentrancy, timestamp dependency, unchecked low calls, and unhandled exception |
| SymlogRepair [36] | 4 | access control, unhandled exception, reentrancy, and locked Ether |
| SmartShield [37] | 3 | state changes after external calls, missing checks for out-of-bound arithmetic operations, and missing checks for failing external calls |
| EVMPatch [38] | 2 | integer over/underflows, and access control errors |
| Aroc [39] | 3 | reentrancy, arithmetic bugs, and unchecked low-level checks |
| Elysium [40] | 5 | reentrancy, access control, arithmetic, unchecked low-level call, and denial of services |
| APG [41] | 3 | malicious voting problems, the patch vulnerabilities, and DeFi unavailability issues |
| Feng et al.’s model [42] | 1 | reentrancy |
| EtherEditor [43] | 7 | tx.origin authentication, denial of service, reentrancy, unchecked external calls, delegate call to untrusted callee, unprotected SELFDESTRUCTION instruction, and arithmetic over/under flow |
| ReenRepair [44] | 1 | reentrancy |
| SGuard [46] | 4 | arithmetic (control dependency, data dependency) and reentrancy (intra-function, cross-function) |
| SolSaviour [45] | 9 | reentrancy, integer over/underflows, delegate call, denial of service, unchecked return values, front running, timestamp dependency, bad constructor, and unknown bugs |
| Reparo [47] | 2 | reentrancy, parity multisig wallet bug |
| HCC [48] | 2 | reentrancy, and integer overflows |
| TOD [49] | 1 | price gouging transaction order dependency |
| Trusted Deployer [50] | 4 | integer overflow and underflow, Nonstandard token interface, wrong operator, and verification error |
| TIPS [51] | 8 | unchecked external calls, reentrancy, access control, arithmetic issue, strict balance equality, unmatched type assignment, Inserting a suicide function, and hard-coded address |
| ContractFix [42] | 4 | reentrancy, missing input validation, locked Ether, and unhandled exception |
| GoHigh [53] | 4 | arithmetic underflow and overflow, reentrancy, denial of service with block gas limit, and unencrypted on-chain data |
| SGuard+ [54] | 5 | integer overflow and underflow, unchecked call return value, unprotected self-destruct instruction, reentrancy, and authorization through tx-origin |
| SmartRep [55] | 11 | use of deprecated functions, unchecked return value, incorrect inheritance order, illegal coverage, transaction ordering dependence, reentrancy, erroneous visibility, arithmetic issue, missing return statement, authorization through tx.origin, and erroneous variable type |
| RLRep [56] | 5 | exception disorder, integer overflow, reentrancy, transaction order dependence, and tx.origin |
| SmartFix [57] | 5 | integer over/under-flow, ether-leak, suicidal, reentrancy, and tx.origin |
| Napoli et al.’s model [58] | - | not mentioned |
| Ibba et al.’s model [59] | 4 | reentrancy, denial of service, arithmetic overflows and underflows, and unchecked low-level calls |
| Two Timin [60] | - | not mentioned |
| ACFIX [61] | 1 | role-based access control |
| Vulnerability Detection Tools | Automated Repair Frameworks |
|---|---|
| Traditional Vulnerability Detection Tools | |
| Mythril and Octopus | HermHD [33] |
| Oyente and Slither | SCRepair [5] |
| Slither, Truffle Suite | Gas Gauge [34] |
| Oyente, Securify, SmartCheck, Pied-Piper, Mythril | Ren et al.’s model [35] |
| Securify2 | SymlogRepair [36] |
| Securify, Osiris, and Mythril | SmartShield [37] |
| Osiris, ECF teEther, Oyente, Maian, Sereum, Securify | EVMPatch [38] |
| Osiris | Aroc [39] |
| Osiris, Oyente, Mythril | Elysium [40] |
| Slither | APG [41] |
| Osiris | EtherEditor [43] |
| Securify | ReenRepair [44] |
| Securify, Ethainter | SGuard [46] |
| Slither | TOD [49] |
| Slither and Mythril | TIPS [51] |
| Securify, Slither, Smartcheck | ContractFix [52] |
| Mythril, Securify, Oyente, Slither | RLRep [56] |
| Slither | Napoli et al.’s model [58] |
| HoneyBadger, Osiris, Oyente, Mythril, Slither, and Securify | Ibba et al.’s model [59] |
| Slither and ANTLR | ACFIX [61] |
| SOLC_VERIFY | Trusted Deployer [50] |
| VeriSmart | SmartFix [57] |
| ML-driven Vulnerability Detection Tools | |
| LSTM | Feng et al.’s model [42] |
| eXtreme Gradient Boosting model | SGuard+ [54] |
| LSTM | SmartRep [55] |
| Hybrid Vulnerability Detection Tools | |
| Slither and Random Forest Classifier | Two Timin [60] |
| Internal Vulnerability Detection Tools | |
| DeFinery detection tool | DeFinery [26] |
| HCC detection tool | HCC [48] |
| GoHigh detection tool | GoHigh [53] |
| SolSaviour detection tool | SolSaviour [45] |
| Reparo detection tool | Reparo [47] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kiani, R.; Sheng, V.S. Automated Repair of Smart Contract Vulnerabilities: A Systematic Literature Review. Electronics 2024, 13, 3942. https://doi.org/10.3390/electronics13193942
Kiani R, Sheng VS. Automated Repair of Smart Contract Vulnerabilities: A Systematic Literature Review. Electronics. 2024; 13(19):3942. https://doi.org/10.3390/electronics13193942
Chicago/Turabian StyleKiani, Rasoul, and Victor S. Sheng. 2024. "Automated Repair of Smart Contract Vulnerabilities: A Systematic Literature Review" Electronics 13, no. 19: 3942. https://doi.org/10.3390/electronics13193942
APA StyleKiani, R., & Sheng, V. S. (2024). Automated Repair of Smart Contract Vulnerabilities: A Systematic Literature Review. Electronics, 13(19), 3942. https://doi.org/10.3390/electronics13193942









