Abstract
The subject of this study is steganographic systems that are able to hide not only the content of the transmitted information but also the fact of its transmission. In this paper, we present a novel data transmission model within such systems, combining a modified Dijkstra’s algorithm with the dynamic utilization of multiple transmission routes. Consequently, this allows the simultaneous transmission of messages through parallel groups of routes with the dynamic alternation of these groups during the information exchange process between the sender and the receiver in the steganographic network. Thus, the speed, reliability, and security of message transmission are improved. Moreover, to increase the security level, the proposed model uses a route–time matrix that is available only to the sender and receiver. Additionally, the data transmission model has been tested on synthetic data and data obtained from real devices. The evaluation of the effectiveness of the proposed model on the example of various structured steganographic systems shows the significant effectiveness of our model. As a result, in comparison with existing similar methods, the secrecy index was increased five times and the violation index was decreased four times.
1. Introduction
In the current digital era, computer and communication systems are undergoing significant development worldwide. Wired, wireless, and optical communication networks have achieved remarkable data transmission rates that exceeded peoples’ expectations, unlocking continuous potential for information exchange. Particularly, with the explosion of the Internet and the pervasive diffusion of information technology, information security directly influences the lives of the majority of people across the globe. Since its inception, the Internet has been constructed on an open network architecture with non-integrated secure nodes, exposing vulnerabilities that render it susceptible to attack and breach by hackers. Within this context, ensuring the security and privacy of information transmitted over networks, particularly when it contains sensitive or confidential content, has emerged as a critical and urgent task in the present era.
To address this challenge, encryption methods based on complex problems have been extensively researched and developed over a prolonged period [1,2,3]. However, all these methods share a common drawback in that they cannot effectively hide the fact of data transmission. When employing encryption algorithms such as the Data Encryption Standard (DES) [4], Triple DES (3DES) [5], RSA [6], and similar methods to encrypt messages before transmission through networks, information may still be detected, although it is difficult for others to ascertain the precise content of that information. Therefore, in the field of information security, concealing the fact of data transmission presents a significant challenge. One of the effective methods to achieve this goal is to use information protection techniques, collectively referred to as steganographic methods [7,8,9]. Through information concealment, data can be covertly hidden within various media such as text, images, videos, and audio, making it difficult for external parties to detect or infer.
Steganographic techniques not only conceal the storage of confidential information but also have the capability to hide confidential information when transmitting it through a network environment. Currently, the method of information concealment through the utilization of multi-channel media [10,11,12] is one of the most popular techniques. These media provide diverse and flexible storage spaces for concealing confidential information. During information concealment, data files containing secret information are embedded within text, images, videos, or audio files. This diversity enhances the success and secrecy of the information concealment process.
In multi-channel systems, one approach to addressing the problem of secure data transmission is to utilize shortest path algorithms for determining transmission routes. For example, a model based on a modified of the Dijkstra algorithm is proposed in [13]. This algorithm variant not only enables the search for the shortest path but also identifies several alternative backup routes. This variation enhances the stability of the telecommunication network.
However, a drawback of concealing information within a multi-channel medium is that data are transmitted through a fixed route. This introduces the risk of interception, attacks, or potential data loss during the transmission process over the network. Such vulnerabilities can expose sensitive information and jeopardize the security of both concealed systems and concealed network infrastructure.
To overcome this drawback, this paper introduces a novel data transmission model with the main goal of enhancing the secrecy of steganographic systems. In this model, we employ a modified Dijkstra algorithm, as proposed by the authors in [13], combined with a dynamic use of multiple transmission routes, similar to the pseudo-random frequency-hopping spread spectrum (FHSS) method in radio, to enhance message transmission speed, reliability, and security within the steganographic system. Supported by time–route matrices dedicated to both the sender and receiver, the proposed scheme conceals not only the content of the transmitted information but also its transmission characteristics. The use of alternative transmission routes enhances the secrecy and safety of the information concealment process. This integration introduces flexibility and diversity in transmitting concealed information across networks, reducing the potential for the detection and blocking of confidential data. The results demonstrate the effectiveness of the proposed model in various structured steganographic systems.
The article is structured as follows: In the second section of the paper, we focus on evaluating more than 30 research works from the past 20 years that are relevant to our research topic. The evaluation results demonstrate that while there are numerous quality studies in narrow fields, there has not been any research that truly delivers outstanding outcomes regarding the proposed model for selecting optimal routes to transmit messages in steganographic network to enhance security. The third section of the paper introduces the relevant theoretical foundations for our research. In the fourth section, we provide a concise overview of the method’s concept that we propose. The fifth section concentrates on presenting the method for determining optimal routes for message transmission. We list all specific cases and propose calculation formulas to find out the most optimal model for message transmission. In the sixth section, we evaluate our method by employing hypothetical data with various different cases that we previously considered. Finally, in the conclusion section, we summarize the main research results.
2. Overview of Related Works
Due to the rapid development of the Internet, the issue of protecting information transmitted through it, especially sensitive and confidential data, has gained significant attention. Individuals and governmental and non-governmental organizations worldwide are actively researching this matter, leading to various proposed solutions. Among these solutions, cryptographic techniques have gained the most attention. Several renowned encryption methods have been introduced, such as Data Encryption Standard (DES), Advanced Encryption Standard (AES), RSA [14], and Blowfish [15]. Additionally, variations of these methods have been developed to align with practical requirements, such as CS-AES [16], AES modifications for MPEG video data streams [17], AES modifications for image encryption [18,19], modified AES-GCM [20], DESNew1, DESNew2 [21], and rapid image encryption schemes with block permutation and block diffusion [22]. Algorithms based on chaotic maps [23,24,25,26] have also been explored. Numerous other encryption algorithms have been researched and developed, yet an inherent weakness of encryption algorithms is their inability to conceal the fact of data transmission. In other words, a third party can easily detect the presence of transmitted information, even if that information has been encrypted. To address this issue, a solution utilized is the application of information hiding techniques (steganographic methods). Consequently, research and attention towards methods that protect hidden information is increasing.
One approach of steganography involves the development of algorithms to embed messages within images, videos, or audio. Many authors have utilized the Least Significant Bits (LSB) method as the basis for designing steganographic methods [27,28,29].
Authors in [30] proposed an image hiding method based on Least Significant Bits (LSB) substitution, Pixel Indicators, and the Zigzag Method. They divided the cover image into four subimages and further divided these subimages into three color planes (R, G, B). Different Pixel Indicators were then applied to each subimage using a zigzag approach. This method achieved a signal-to-noise ratio over noise PSNR > 50 dB. However, due to the use of one of the color channels (R, G, B) as an indicator for the existence of information in the other two channels, the capacity for hidden information per pixel in the cover image is reduced. Yigit, Y., and colleagues [31] employed the LZW compression algorithm to compress hidden information, then used the LSB bits of the RGB image to hide the compressed information. Although compressing the hidden information reduces the length of the embedded information, it increases the encoding and decoding time due to the added compression and decompression processes. Another method based on pixel value differencing (PVD) has also been researched for embedding confidential information into images. Gandharba Swain [32] developed an image-hiding method based on modulus function (MF) and PVD. This method utilized the difference between consecutive pixel pairs to embed confidential information. Additionally, Gandharba Swain and Aditya Kumar Sahu used pixel stacking to increase the capacity for embedding information in images [33]. Meanwhile, Z. Li and Y. He [34] proposed a combination of PVD, MF, and particle swarm optimization. Alongside LSB and PVD, there are numerous other traditional methods being developed, such as histogram shifting [35,36], multiple-bit planes [37], and palettes [38]. In addition to the aforementioned traditional methods, deep learning is emerging as an effective approach for information hiding in images. H. Shi and colleagues [39] employed generative adversarial networks (GAN) to create cover images. A GAN generator with a U-Net architecture was proposed by Yang et al. [40]. Beyond creating cover images, Rehman and colleagues demonstrated the effectiveness of deep learning in encoding and decoding (embedding and extracting) messages [41]. They trained an end-to-end pair of Convolutional Neural Networks (CNNs) for encoding and decoding to create stego images from cover images and black-and-white secret images, and to recover the secret images from the stego images. Experimental results indicated a high PSNR value (>29 dB). However, the absence of a stego key (key for the stego image) poses a risk of secret information leakage. If the decryption network is compromised or if the structure of the decryption network is revealed, the encoding and decoding pair becomes unusable, necessitating a retraining from scratch with different network structures.
Zheng Li and colleagues [42] developed the DeepKeyStego technique based on deep networks. They successfully trained and deployed DeepKeyStego for both symmetric and asymmetric steganography. In the field of wireless networks, in the context of MRC networks, Miaojiang Chen and colleagues [43] introduced a deep reinforcement learning algorithm known as GPDS. GPDS has the ability to enhance the Signal-to-Interference-plus-Noise Ratio (SINR) protection level and channel throughput for mobile devices in uncertain and dynamic communication environments. Experimental results have shown that the proposed GPDS achieves superior noise resistance effectiveness compared to state-of-the-art algorithms. Miaojiang Chen and their team [44] have also proposed a trustworthy deep reinforcement learning approach for evaluating the reliability of devices in vehicular networks. This approach includes our intelligent trustworthy system model and the DPGAQ scheme to counteract spoofing attacks from malicious vehicles. Yuxin Liu and colleagues, on the other hand, presented the Adaptive Packet Minimizing Delay (APMD) protocol [45]. APMD is designed to reduce latency and ensure reliability in industrial Wireless Sensor Networks (WSN).
Jingjing Guo and their colleagues [46] have proposed a method to evaluate the trustworthiness of associative learning in the context of Digital Twin for Mobile Networks (DTMN). The proposed framework can be employed to address the issue of selecting reliable users in the associative learning scenario, with the goal of enhancing the security of associative learning and ensuring the performance of DTMN. Zhiquan Liu and their team [47] introduced a novel Trust Layer-based Emergency Message Dissemination Model (TCEMD) within vehicular ad hoc networks (VANETs). In the proposed model, when emergency events occur, emergency messages can be disseminated among nearby vehicles through layered trust mechanisms. Within vehicular networks, Zhiquan Liu and their colleagues [48] have put forth a plan known as BTMPP to provide a viable solution for balancing trust management and privacy protection within the vehicular network. The authors utilize Privacy-preserving Set Intersection (PSI) technology based on the well-known Bloom Filter (BF).
Shumeet Baluja [49] also successfully embedded a color image (confidential information) into a color cover image. Another approach of steganography involves methods to hide confidential information within network packets. Abdullaziz and colleagues [50] proposed a hidden code technique based on the length of the user data field in packets with random sizes such as UDP, utilizing the parity of the user data field length to represent binary information. However, it is not difficult for third parties to extract the hidden information. Punam Bedi and Arti Dua [51] developed a method to embed confidential information into the overflow field of the timestamp option in an IPv4 network packet. This method does not trigger any alerts in network analysis applications like Wireshark and allows embedding 20 bits per IPv4 network packet. Sandip Babade and Rajeshawari Goudar [52] encrypted confidential information using RSA before embedding it into the flow label field in the IPv6 Header, enabling embedding 20 bits per IPv6 network packet. Drzymala and colleagues [53] utilized DNS messages to hide confidential information. As network traffic continues to increase, embedding confidential information in network packets is less likely to be detected compared to using images, videos, or audio. However, the capacity for confidential information in network packets is often significantly less than that in images, videos, or audio.
In summary, existing approaches have primarily focused on concealing how to embed confidential data within other data, without much consideration on how to reliably transmit containers from sender to receiver without loss or interception. In other words, enhancing confidentiality during container transmission has not been well-addressed. The aim of this paper is to propose a model for transmitting confidential information that enhances the confidentiality and reliability of the transmitted data.
3. Materials and Methods
Steganography is a scientific field concerned with concealing confidential messages, focusing on the efficient hiding of messages. Steganography is divided into three main approaches: classical (non-computer), computer-based (utilizing data formats in networks), and digital (hiding information in multimedia). Our research concentrates on computer-based and digital steganography.
Currently, the field of computer-based steganography is not yet complete, but it has seen numerous research proposals. Among them, the EMBSS model (Steganographic ally Systems Interconnection basic reference model—SSI model), proposed by the authors of [54], elucidates the meanings of several terms in steganography theory. This model is built upon popular concepts in steganography theory, communication system theory, and information security theory, as well as introducing new terminology.
One research approach for enhancing security in the field of steganography is the development of algorithms for finding paths for packets in a network to ensure safety and optimization. Survey results reveal that the Dijkstra algorithm [13] has been widely adopted for solving shortest path finding tasks in routing protocols.
The Dijkstra algorithm is one of the most popular algorithms for solving the shortest path problem on a directed graph. This algorithm finds the shortest path from a source vertex to all other vertices in a weighted directed graph, given that all edges in the graph have non-negative weights. The length (or weight) of a graph is the sum of the weights of its edges.
The essence of the Dijkstra algorithm is to gradually build the tree of shortest paths from the source node. In this case, the necessary factor is that after adding a communication link and a node at each stage, the newly formed shortest path is the minimum path that can serve all the untaken destination nodes into the tree. While constructing the tree of shortest paths, the weight vectors of the paths are calculated and the vectors of the initial components of the shortest paths are adjusted. The complexity of the Dijkstra method depends on how the vertex v is found, how the set of unvisited vertices is stored, and how the labels are updated. In graph G, with n and m being the number of vertices and edges, respectively, finding a vertex with the shortest path to that vertex less than or equal to v requires searching through the entire n. The Dijkstra method is widely used in networking and network programming, for example, it is employed in the OSPF (Open Shortest Path First) protocol to eliminate routing loops.
The author [55] proposes modifying the formula for calculating the metric M of steganographic communication channels to take into account the loss index in the OSPF protocol:
In this context, Mstego is the modified metric of the stego communication channel; by default, for OSPF, k1 = 1 and k2 = 0, while k3 and k4 are coefficients to determine the confidential components. Pcon is the secrecy index of the message transmitted through the covert channel, assumed to have values within the range [0, 1]. This index ensures that sensitive information is safeguarded from unauthorized disclosure during transmission, with a value of 1 corresponding to maximum secrecy and 0 indicating no secrecy.
In this study, we will employ a modified version of the Dijkstra algorithm in the steganographic network, as presented by the authors [13]. This modified version not only facilitates finding the shortest path from the source node to other nodes but also enables the identification of backup paths from the source node to other nodes.
4. Proposed Methodology
In radio communication, a method of transmitting information characterized by the frequent variation of the carrier wave frequency is known as the frequency-hopping spread spectrum technique. The frequency is changed according to a pseudo-random sequence known to both the sender and the receiver. This method enhances the channel’s resistance to noise. Building upon the concept of frequency variation, we propose a method that involves altering the communication path for each transmission session according to a predefined schedule. In our approach, instead of consistently transmitting data through a fixed route with the lowest cost, information is conveyed through various routes. This aims to introduce the difficulty in intercepting the information, thereby enhancing the confidentiality of the steganographic network system.
A general overview example of the method is illustrated in Figure 1, where at time t1, information is transmitted through routes 1 and 2, and at time t2, information is transmitted through routes 3 and 4.
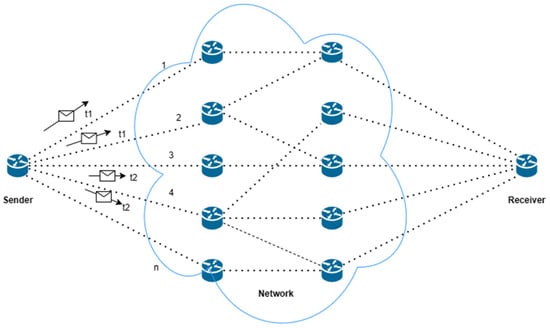
Figure 1.
Example illustrating the method’s concept.
The main steps of our proposed method include:
Step 1: Utilize the modified version of the Dijkstra algorithm to search for routes from the sender to the receiver. These routes are sequentially numbered from 1 to n, representing route names.
Step 2: Establish a synchronization of the message transmission schedule between the sender and the receiver across the routes. Based on the routes identified by the Dijkstra algorithm, the sender constructs a randomized pseudo-route–time matrix. Subsequently, the sender transmits this route–time matrix to the receiver through a channel with the highest secrecy index. This results in the creation of a pseudo-random route–time matrix, where only the sender and receiver know this matrix. Each column of the matrix represents a time point, and the rows correspond to route names. After a period of use, at a specified moment, if the sender wishes to change the route–time matrix, they will transmit a message containing the new route–time matrix to the receiver. Conversely, if the receiver intends to modify the route–time matrix, they must send a request a route–time matrix change from the sender. In this case, the sender will then generate a new route–time matrix and update it by retransmitting it to the receiver.
An example of a route-time matrix is illustrated in Figure 2. At time T1, routes 1 and 2 are used. At time T2, routes 4 and 5 are used.
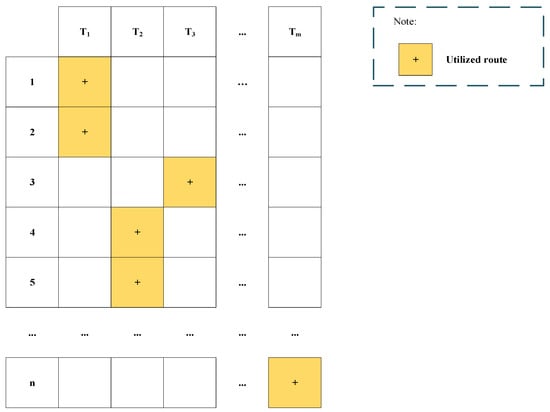
Figure 2.
Example of pseudo-random route–time matrix.
Step 3: Standardize the usage of stegocoder and stegodecoder parameters, including keys, algorithms for transmission, and the reception of information.
In Figure 3, the working model of our proposed method is depicted in detail. The sender embeds the message into a container using the stegocoder. After the message is embedded, the original container is duplicated into k copies. Each copy of the container is prepared for transmission over separate communication channels. The sender employs the route–time matrix to select k transmission routes. Once the routes are selected, each route is used to transmit a copy of the container. On the receiver’s side, containers are received by employing the route–time matrix. Upon receiving the containers, the receiver utilizes the stegodecoder to extract messages from each container.
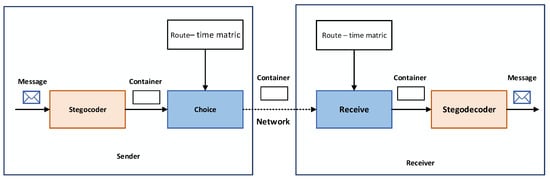
Figure 3.
Working model of the method.
5. Determining Secure Routes for Concealed Information Transmission in Steganographic Communication Channels
To assess the effectiveness of our method, we utilize a probability value that ensures the secrecy level, also referred to as the proposed secrecy index by the author [55].
—the secrecy index of the transmitted message on the i-th hidden channel of the j-th route.
—the secrecy index of the message transmitted through j-th route will be determined by the secrecy index () of the message transmitted over the hidden channels of j-th route.
An example of a route with nj hidden channels to represent the above formula is depicted in Figure 4.
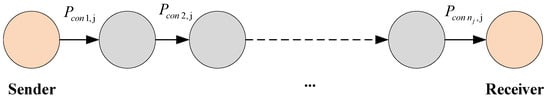
Figure 4.
Example of a route with nj hidden channels.
The authors in [55] also proposed a method to re-calculate the channel quality assessment metric, taking into account the secrecy index of steganographic communication channels. This helps identify a route with the highest secrecy index, and all messages are transmitted through this route. However, in our study, each message transmission occurs through different routes, ensuring higher anonymity. This approach avoids concentrating messages on a single route, making it more difficult for potential attackers to predict and intercept. To find the most optimal routes, we consider the following three cases:
- 1.
- Case 1: Using a single route for each transmission.
- 2.
- Case 2: Using multiple routes for each transmission.
- 3.
- Case 3: Alternating the use of route groups N out of the total M routes.
5.1. Using A Single Route for Each Transmission
The idea of this case is that each time a message is transmitted, a route will be selected from the route between the sender and the receiver.
We further propose the addition of a parameter —the probability of violating the secrecy of the message transmitted through the j-th route, which will be determined by the secrecy index of the message transmitted through the j-th route.
Here, the coefficient is the utilization rate of the j-th route for transmitting messages, . , where a is the total number of messages transmitted between the sender and the receiver, is the number of messages transmitted through j-the route. The coefficient indicates that the more j-th route is used to transmit messages, the higher the probability of violating the secrecy of the message transmitted through j-th route.
is the secrecy index of the message transmitted between the receiver and the sender.
is the probability of violating the confidentiality of the message transmitted between the sender and the receiver.
If in the study of author [49], only a single dedicated route is used for transmitting the message every time, meaning .
The probability of violating the confidentiality of the message transmitted between the sender and the receiver, using only the primary route for message transmission, i.e., employing a single fixed dedicated route (corresponding to stego channel and having ), will be determined by the expression:
An example of a steganographic system illustrating expression (2) is depicted in Figure 5.
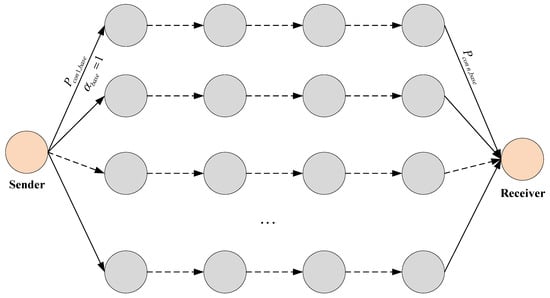
Figure 5.
Example of a steganographic system (illustrating for Equation (2)).
Equation (2) represents the probability of violating the security of the case when only a single fixed route is used.
If we consider the scenario where there is an alternation between using the main route and the backup routes, and each time a message is transmitted, a different route is utilized, the value of will change accordingly (Case 1).
The probability of violating the security of a message transmitted between the sender and receiver, considering both the main route and k backup routes (corresponding to the stego channels and , respectively, where will be determined using the following expression:
An example of a steganographic system illustrating expression (3) is depicted in Figure 6.
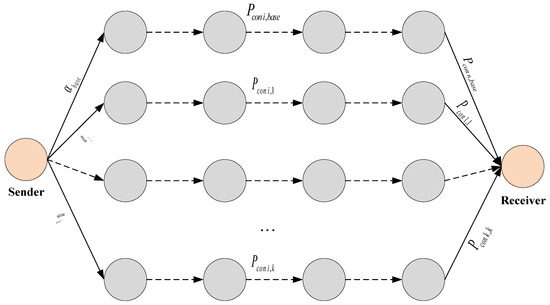
Figure 6.
Example of a steganographic system (illustration of Equation (2)).
Because for any signal transmission channel “i-th” of route “j-th”, , and for any route “j-th”, , therefore . The equal sign in this expression will occur when k = 0, meaning that no backup route is used.
From the result that , it has been demonstrated that the alternation of multiple communication routes helps decrease the probability of violating the security of transmitted messages between the sender and the receiver. This also implies an increase in the security index of the transmitted messages between the sender and the receiver.
5.2. Using Multiple Routes in Each Transmission
Figure 7 illustrates the sequentially connected steganographic communication channels:
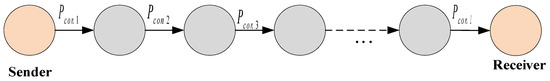
Figure 7.
An example of sequentially connected steganographic communication channels.
From the reliability formula for a serial connection, the secrecy index of the message transmitted along the pathway created through one individual consecutive channel:
where represents the secrecy index of the information transmitted through the i-th covert channel.
Figure 8 depicts the parallel-connected steganographic communication channels:
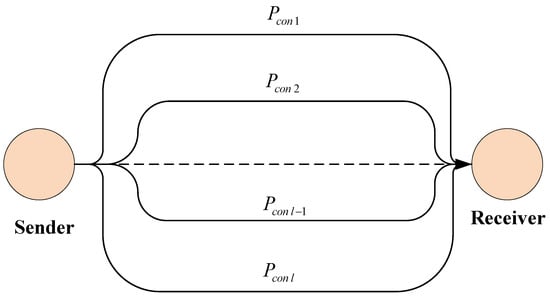
Figure 8.
Example of the parallel-connected steganographic communication channels.
From the formula for calculating the reliability of parallel connections, the secrecy index of the transmitted information of the entire system, created through one individual parallel channel, is obtained.
where is the secrecy index of the information transmitted through the i-th covert channel. If we combine the sequential and parallel connection models (Figure 9) (Case 2).
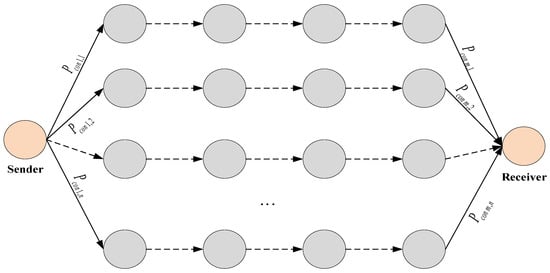
Figure 9.
Example of combined steganographic communication channels (sequential and parallel connections).
From the formula for calculating the reliability when combining sequential and parallel connections, the secrecy index of the transmitted message (when transmitted through multiple paths).
—secrecy index of the message transmitted through the j-th steganographic communication channel of the i-th path.
—secrecy index of the message transmitted along the i-th path.
n—the number of parallel paths used between the sender and the receiver.
m—the number of steganographic communication channels in each path.
Because of the probability of a breach in the confidentiality of the transmitted message between the sender and the receiver , and the probability of a breach in the confidentiality of the message transmitted through “i-th” route is , therefore , combined with . Thus, .
From the results , it has been demonstrated that combining serial and parallel connections enhances the secrecy index of the message transmitted between the sender and the receiver.
5.3. Alternating the Use of Groups of Paths N Out of the Total M Paths (Case 3—A Combination of Case 1 and Case 2)
This case is a combination of Case 1 and Case 2, and it is the proposed model. When alternating the use of N groups of paths out of the total M paths, the number of groups of paths (each consisting of N paths) is calculated as . “Alternating” here means that the proportion of using these groups of paths is equal and follows the ratio:
In the case where the secrecy index of each path is , according to Formula (4), the secrecy index of the group of N paths is:
Combining Formulas (3) and (6) and Condition (5), the secrecy index when alternating the use of N path groups out of the total of M paths will be calculated using the following formula:
where: .
Because the probability of a breach in the confidentiality of the message transmitted between the sender and the receiver and the probability of a breach in the confidentiality of the message transmitted through “i-th” route in this scenario is , therefore combined with (because ). Therefore, with , the results have shown that combining Cases 1 and 2 enhances the secrecy index of the message transmitted between the sender and the receiver.
6. Results
This section will present the performance evaluation of our proposed method through the utilization of suggested examples and data. We will conduct the assessment by sequentially considering specific scenarios to demonstrate the effectiveness of the method for transmitting messages through different routes.
We will provide examples that illustrate the formation of routes between vertices (stego nodes) within the graph (network system) and calculate the secrecy index in Case 1.
Example 1: Consider a small experimental steganographic network diagram consisting of stego nodes A, B, C, D, E, and F arranged as shown in Figure 10. Each network interface (edge) is utilized to transmit covert data from one transmitting stego node to another. Each network interface has a predefined secrecy index (Pcon). We have conducted the computation of Pcon and Pnk between node A and all other nodes (B, C, D, E, F) within the steganographic network in two distinct scenarios. In the first scenario, we employed a fixed routing approach, which utilized Dijkstra’s algorithm. In the second scenario, we adopted a modified routing model, which employed a modified of Dijkstra’s algorithm. In this context, node A serves as the sender, while nodes B, C, D, E, and F represent various recipients within the steganographic network. Table 1 contains specific parameters for each network interface.
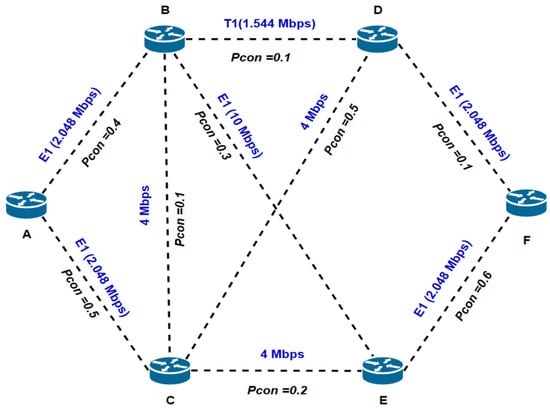
Figure 10.
Example 1 of a steganographic network system.

Table 1.
Information about network interface types.
Step 1: Calculating OSPF Metrics.
Using the proposed parameters and the provided Equation (1), we computed the OSPF metrics. With the suggested secrecy index from [55], where k1 = 1, k2 = 0, k3 = k4 = 1, we proceeded to calculate the OSPF metrics. The results are presented in Table 2.

Table 2.
OSPF metrics with secrecy index.
Based on the results obtained in Table 2, we obtained information about the metrics and secrecy indices as shown in Figure 11:
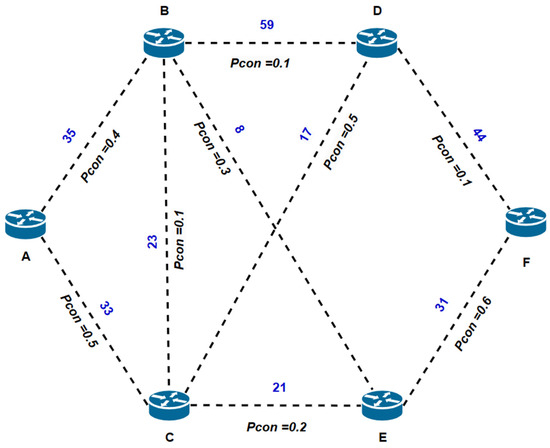
Figure 11.
Example 1 of a steganographic network system with OSPF metrics and secrecy index.
Step 2. Establishing Data Transmission Routes.
In this step, utilizing the modified version of the Dijkstra algorithm [13], we will determine sets of data transmission routes along with their associated metrics. The algorithm’s execution steps are detailed in Appendix A. Table 3 summarizes the primary routes (shortest paths) and backup routes. Here, Di represents the sets of metrics for primary routes, Li represents the sets of primary routes, Zi represents the sets of backup routes, and Si represents the sets of metrics for backup routes.

Table 3.
Summary of main paths (shortest paths) and backup paths with metrics.
Step 3: Comparing Secrecy Index and Probability of Secrecy Violation.
In this step, we assess the secrecy index and the probability of secrecy violation in the case of using fixed paths (Case 1) based on Equations (1) and (2). By employing one main path and one backup path with respective utilization rates , we obtain the results presented in Table 4.

Table 4.
Secrecy index calculation results (using one backup path ).
When using one primary path and two backup paths with respective utilization rates in Case 1, we obtain the results as shown in Table 5.

Table 5.
Secrecy index calculation results (using two backup paths ).
Example 2: Consider a small steganographic network topology consisting of stego nodes A, B, C, D, and E arranged as shown in Figure 12. Each network interface (edge) is used to transmit hidden data from one transmitting stego node to another receiving node. Each network interface has a secrecy index (Pcon) assigned to it. We undertook the computation of Pcon and Pnk between node A and all other nodes (B, C, D, E) within the steganographic network in two distinct scenarios. In the first scenario, we employed a fixed routing approach, specifically using Dijkstra’s algorithm. In the second scenario, we utilized the proposed model, which involves the application of a modified version of Dijkstra’s algorithm. In this context, node A serves as the sender, while nodes B, C, D, and E represent different receivers within the steganographic network. Table 1 contains specific parameters for each network interface.
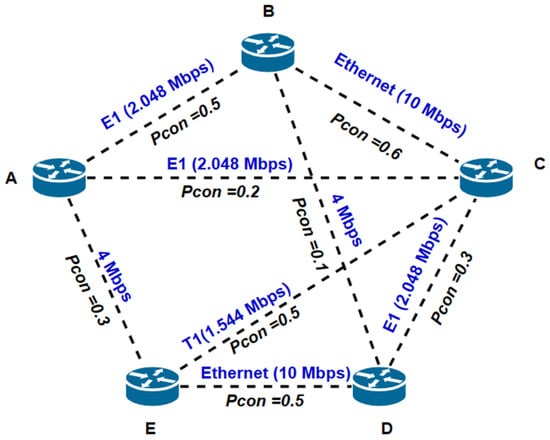
Figure 12.
Example 2 of a steganographic network system.
Step 1: Calculating OSPF Metrics.
Using the proposed parameters and the provided Equation (1), we compute the OSPF metrics. With the suggested secrecy index from [55], where k1 = 1, k2 = 0, and k3 = k4 = 1, we proceed to calculate the OSPF metrics. The results are presented in Table 6.

Table 6.
OSPF metrics with secrecy index.
Based on the results obtained in Table 6, we obtained information about the metrics and secrecy indices, as shown in Figure 13:
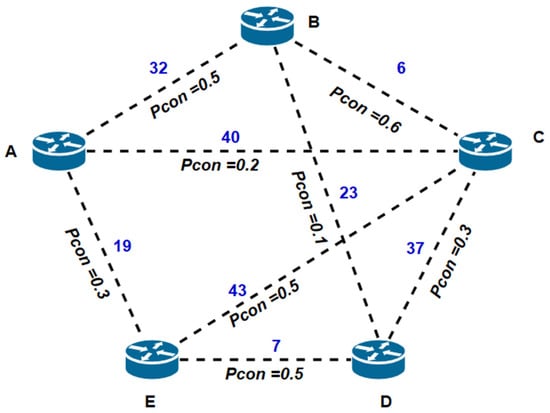
Figure 13.
Example 2 of a hidden network system with OSPF metrics and secrecy index.
Step 2: Establishing Data Transmission Routes.
In this step, utilizing the modified version of the Dijkstra algorithm [13], we will determine sets of data transmission routes along with their associated metrics. The algorithm’s execution steps are detailed in Appendix A. Table 7 summarizes the primary routes (shortest paths) and backup routes. Here, Di represents the sets of metrics for primary routes, Li represents the sets of primary routes, Zi represents the sets of backup routes, and Si represents the sets of metrics for backup routes.

Table 7.
Summary of main paths (shortest paths) and backup paths with metrics.
Comparing the Secrecy Index and Probability of Violating Secrecy in the Case of Fixed Routes and Case 1:
Based on the results from Table 4 and Table 5 in Example 1 and Table 8 in Example 2, it is evident that using a different transmission route from the set of n available routes (by alternating routes) for transmitting the message significantly increases the secrecy index of the transmitted message compared to using only a single transmission route. Additionally, the probability of violating the secrecy of the message decreases. Comparing the outcomes of Table 4 and Table 5 illustrates that as n increases, the secrecy index also increases.

Table 8.
Secrecy index calculation results (using one backup path ).
Examples Combining Sequential and Parallel Connections (Case 2):
In this scenario, for computational simplicity, we assume the existence of n parallel routes, each with an identical secrecy index of . Consequently, Equation (3) simplifies to:
Table 9 illustrates the dependency of the secrecy index on the number of parallel routes and the secrecy index of each individual route according to Equation (8).

Table 9.
Dependency of on n and .
Below is the dependency graph of the secrecy capacity on the number of parallel routes with the given secrecy capacity .
Based on Table 9 and the graphs in Figure 14, it can be observed that transmitting the message through multiple parallel routes increases the secrecy index of the message compared to using a single dedicated route. The secrecy index of the message increases as the number of parallel transmission routes (n) increases.
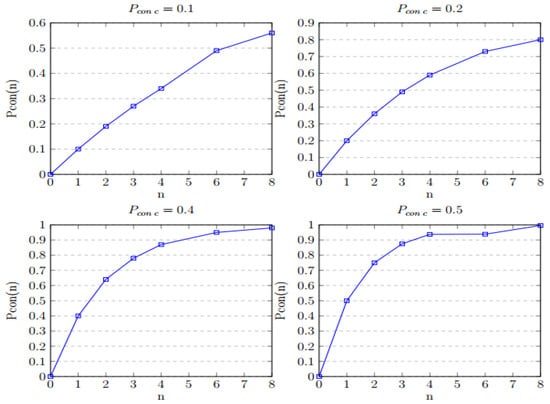
Figure 14.
Some graphs illustrating the dependence of the secrecy index of the message in the system on the number of parallel routes used in the system.
Alternating the use of groups consisting of N transmission routes out of the total M routes (Case 3).
Assuming that there are M transmission routes with the same and equal secrecy index , alternating the use of groups consisting of N transmission routes out of the total M routes implies that the frequency of using these groups of N routes is the same and equal to . Thus, we obtain Formula (7), as described in the previous section:
Table 10 shows some values of depending on the assumed values of M, N, and , according to Formula (7):

Table 10.
Dependency of on M, N, and .
The graphs in Figure 15 represent the dependency graphs of the secrecy index of the message on N, M, and the secrecy index on each channel, based on Formula (6):
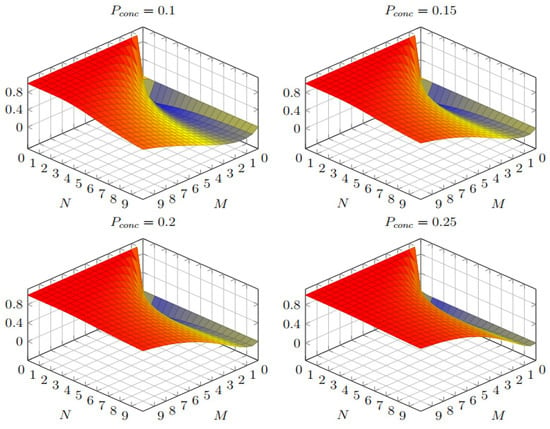
Figure 15.
Several graphs illustrating the dependency of the secrecy index of the message on N and M.
The graphs indicate that as N and M increase, the secrecy index of the message also increases. The graphs also show that the practice of alternating the use of groups of N parallel routes among the total of M routes also leads to an increase in the secrecy index of the message compared to using a single dedicated transmission route.
7. Conclusions
The paper introduces a robust data transmission model within a steganographic system, leveraging the Dijkstra algorithm to fortify the system’s security. This model facilitates the transmission of messages through parallel route groups, periodically switching between route groups during exchanges between the sender and receiver within a concealed system. This dynamic routing is accomplished through a predefined route–time matrix, known exclusively to the sender and receiver. The research underscores the substantial improvement in the secrecy index of transmitted messages achieved by employing this model, in stark contrast to the utilization of a single, static transmission route for exchanges between the sender and receiver.
Nonetheless, it is essential to acknowledge both the strengths and limitations of the applied approach. While this method substantially enhances message security and confidentiality, it introduces increased network complexity and may result in additional computational overhead, such as computing alternative routes and selecting transmission routes based on the route–time matrix. To address these challenges, our strategy involves the investigation of optimization strategies for the routing algorithm. This exploration may include the integration of load balancing techniques to more efficiently manage network traffic when establishing alternative routes. It is crucial to approach this optimization process thoughtfully, with a focus on achieving a delicate equilibrium between bolstering security measures and maintaining optimal network performance.
Furthermore, it is essential to explicitly acknowledge that the efficacy of this method can differ based on the nature of the transmitted information. Highly sensitive or classified data, for instance, may derive the greatest advantages from the enhanced security afforded by this approach. We plan to conduct additional research to categorize and identify the specific types of data that benefit the most from this method, as well as those for which it may be less effective.
Moreover, it is imperative to conduct an assessment of network load during the establishment of alternative routes to ensure seamless system operation without causing excessive congestion. This entails conducting comprehensive performance tests to gauge the method’s scalability and resource requirements, enabling us to refine its implementation accordingly. Additionally, the volume of information transmitted is influenced by the information-embedding algorithm. We are planning to design an information-embedding algorithm tailored to the model to further enhance data transmission speed.
Comparing this method with existing alternatives will provide additional valuable insights into its relative strengths and weaknesses. This comparative analysis will involve against established steganographic techniques, highlighting where our approach excels and where it may require further refinement.
In terms of future plans, our research agenda includes delving into data fragmentation before embedding it into the container. This approach will allow us to transmit data fragments through various routes, rather than sending complete container copies as currently practiced. This innovation aims to enhance both security and efficiency in the steganographic system, making it an area ripe for exploration in our future work.
Author Contributions
Conceptualization, M.H. and D.-M.T.; methodology, M.H. and D.-M.T.; software, D.-M.T.; validation, M.H., Y.S., and D.-M.T.; formal analysis, M.H. and Y.S.; investigation, M.H. and D.-M.T.; data curation, M.H.; writing—original draft preparation, D.-M.T.; writing—review and editing, M.H. and Y.S.; visualization, Y.S.; supervision, M.H. and Y.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by supported by the Ministry of Science and Higher Education of the Russian Federation by the Agreement № 075-15-2022-291, dated 15.04.2022 on the provision of a grant in the form of subsidies from the federal budget for the implementation of state support for the establishment and development of the world-class scientific center «Pavlov center Integrative physiology for medicine, high-tech healthcare, and stress-resilience technologies».
Data Availability Statement
No associated data to be shared related to this work.
Conflicts of Interest
The authors declare that they have no known competing financial interest or personal relationship that could have appeared to influence the work reported in this paper.
Appendix A
Description of steps for executing the modified Dijkstra’s algorithm [13] to find the shortest path to the stego node in examples. Here the cells are highlighted in green with the metric of the shortest route from the starting stego node to the stego node under consideration.

Table A1.
Description of steps for executing the modified Dijkstra’s algorithm to find the shortest path and backup paths to the stego node in Example 1.
Table A1.
Description of steps for executing the modified Dijkstra’s algorithm to find the shortest path and backup paths to the stego node in Example 1.
| Step | Set | Stego Node | |||||
|---|---|---|---|---|---|---|---|
| A | B | C | D | E | F | ||
| 1 | Di | 0 | 35 | 33 | Ø | Ø | Ø |
| Li | Ø | A→B | A→C | Ø | Ø | Ø | |
| Ri | Ø | RB, A, C, D, E | RC, A, B, D, E | Ø | Ø | Ø | |
| Ci | Ø | CBA = 35, CBC = 23, CBD = 59,CBE = 8 | CCA = 33, CCB = 23, CCD = 17, CCE = 21 | Ø | Ø | Ø | |
| Zi | Ø | A→C→B | A→B→C | Ø | Ø | Ø | |
| Si | Ø | 33 + 23 = 56 | 35 + 23 = 58 | Ø | Ø | Ø | |
| 2 | Di | Ø | 35 | Ø | 33 + 17 = 50 | 33 + 21 = 54 | Ø |
| Li | Ø | A→B | A→C | A→C→D | A→C→E | Ø | |
| Ri | Ø | RB, A, C, D, E | RC, A, B, D, E | RD, B, C, F | RE, C, B, F | Ø | |
| Ci | Ø | CBA = 35, CBC = 23, CBD = 59, CBE = 8 | CCA = 33, CCB = 23, CCD = 17, CCE = 21 | CDB = 59, CDC = 17, CDF = 44 | CEC = 21, CEB = 8, CEF = 31 | Ø | |
| Zi | Ø | A→C→B A→C→E→B | A→B→C | A→B→C→D A→B→D | A→B→C→E A→B→E | Ø | |
| Si | Ø | 56, 54 + 8 = 62 | 58 | 58 + 17 = 75, 35 + 59 = 94 | 58 + 21 = 79 35 + 8 = 43 | Ø | |
| 3 | Di | Ø | Ø | Ø | 50 | 35 + 8 = 43 > 54 | Ø |
| Li | Ø | A→B | A→C | A→C→D | A→B→E | Ø | |
| Ri | Ø | RB, A, C, D, E | RC, A, B, D, E | RD, B, C, F | RE, C, B, F | Ø | |
| Ci | Ø | CBA = 35, CBC = 23, CBD = 59, CBE = 8 | CCA = 33, CCB = 23, CCD = 17, CCE = 21 | CDB = 59, CDC = 17, CDF = 44 | CEC = 21, CEB = 8, CEF = 31 | Ø | |
| Zi | Ø | A→C→B | A→B→C | A→B→C→D | A→B→C→E | Ø | |
| A→C→E→B | A→B→E→C | A→B→D | A→C→E | ||||
| Si | Ø | 56, 62 | 58 43 + 21 = 64 | 75, 94 | 79, 54 | Ø | |
| 4 | Di | Ø | Ø | Ø | 50 | Ø | 43 + 31 = 74 |
| Li | Ø | A→B | A→C | A→C→D | A→B→E | A→B→E→F | |
| Ri | Ø | RB, A, C, D, E | RC, A, B, D, E | RD, B, C, F | RE, C, B, F | RF, D, E | |
| Ci | Ø | CBA = 35, CBC = 23, CBD = 59, CBE = 8 | CCA = 33, CCB = 23, CCD = 17, CCE = 21 | CDB = 59, CDC = 17, CDF = 44 | CEC = 21, CEB = 8, CEF = 31 | CFE = 31, CFD = 44 | |
| Zi | Ø | A→C→B | A→B→C | A→B→C→D | A→B→C→E | A→C→E→F | |
| A→C→E→B | A→B→E→C | A→B→D | A→C→E | A→C→D→F | |||
| Si | Ø | 56, 62 | 58, 64 | 75, 94 | 79, 54 | 54 + 31 = 85, 50 + 44 = 94 | |
| 5 | Di | Ø | Ø | Ø | Ø | Ø | 74 |
| Li | Ø | A→B | A→C | A→C→D | A→B→E | A→B→E→F | |
| Ri | Ø | RB, A, C, D, E | RC, A, B, D, E | RD, B, C, F | RE, C, B, F | RF, D, E | |
| Ci | Ø | CBA = 35, CBC = 23, CBD = 59, CBE = 8 | CCA = 33, CCB = 23, CCD = 17, CCE = 21 | CDB = 59, CDC = 17, CDF = 44 | CEC = 21, CEB = 8, CEF = 31 | CFE = 31, CFD = 44 | |
| Zi | Ø | A→C→B | A→B→C | A→B→C→D | A→B→C→E | A→C→E→F | |
| A→C→E→B | A→B→E→C | A→B→D | A→C→E | A→C→D→F | |||
| Si | Ø | 56, 62 | 58, 64 | 75, 94 | 79, 54 | 85, 94 | |

Table A2.
Description of steps for executing the modified Dijkstra’s algorithm to find the shortest path and backup paths to the stego node in Example 2.
Table A2.
Description of steps for executing the modified Dijkstra’s algorithm to find the shortest path and backup paths to the stego node in Example 2.
| Step | Set | Stego Node | ||||
|---|---|---|---|---|---|---|
| A | B | C | D | E | ||
| 1 | Di | 0 | 32 | 40 | Ø | 19 |
| Li | Ø | A→B | A→C | Ø | A→E | |
| Ri | Ø | RB, A, C, D | RB, A, B, D, E | Ø | RB, A, C, D | |
| Ci | Ø | CBA = 32, CBC = 6, CBD = 23 | CCA = 40, CCB = 6 CCD = 37, CCE = 43 | Ø | CEA = 19, CEC = 43 CED = 7 | |
| Zi | Ø | A→C→B | A→B→C A→E→C | Ø | A→B→C→E A→C→E | |
| Si | Ø | 40 + 6 = 46 | 32 + 6 = 38 19 + 43 = 62 | Ø | 38 + 43 = 81 40 + 43 = 83 | |
| 2 | Di | Ø | 32 | 40 | 26 | Ø |
| Li | Ø | A→B | A→C | A→E→D | A→E | |
| Ri | Ø | RB, A, C, D | RB, A, B, D, E | RD, B, C, E | RB, A, C, D | |
| Ci | Ø | CBA = 32, CBC = 6, CBD = 23 | CCA = 40, CCB = 6, CCD = 37, CCE = 43 | CDB = 23, CDC = 37, CDE = 7 | CEA = 19, CEC = 43, CED = 7 | |
| Zi | Ø | A→C→B | A→B→C | A→B→D | A→B→C→E | |
| A→E→C→B | A→E→C | A→C→D | A→C→E | |||
| Si | Ø | 46 | 38 | 32 + 23 = 55 | 81 | |
| 62 + 6 = 68 | 62 | 40 + 37 = 77 | 83 | |||
| 3 | Di | Ø | 32 | 40 | Ø | Ø |
| Li | Ø | A→B | A→C | A→E→D | A→E | |
| Ri | Ø | RB, A, C, D | RB, A, B, D, E | RD, B, C, E | RB, A, C, D | |
| Ci | Ø | CBA = 32, CBC = 6, CBD = 23 | CCA = 40, CCB = 6, CCD = 37, CCE = 43 | CDB = 23, CDC = 37, CDE = 7 | CEA = 19, CEC = 43, CED = 7 | |
| Zi | Ø | A→C→B | A→B→C | A→B→D | A→B→C→E | |
| A→E→C→B | A→E→C | A→C→D | A→C→E | |||
| Si | Ø | 46 | 38 | 55 | 81 | |
| 68 | 62 | 77 | 83 | |||
| 4 | Di | Ø | Ø | 32 + 6 = 38 > 40 | Ø | Ø |
| Li | Ø | A→B | A→B→C | A→E→D | A→E | |
| Ri | Ø | RB, A, C, D | RB, A, B, D, E | RD, B, C, E | RB, A, C, D | |
| Ci | Ø | CBA = 32, CBC = 6, CBD = 23 | CCA = 40, CCB = 6, CCD = 37,CCE = 43 | CDB = 23, CDC = 37, CDE = 7 | CEA = 19, CEC = 43, CED = 7 | |
| Zi | Ø | A→C→B | A→C | A→B→D | A→C→E | |
| A→E→C→B | A→E→C | A→C→D | A→B→C→E | |||
| Si | Ø | 46 | 40 | 55 | 81 | |
| 68 | 62 | 77 | 83 | |||
References
- Lin, K.T. Digital Information Encrypted in an Image Using Binary Encoding. Opt. Commun. 2008, 281, 3447–3453. [Google Scholar] [CrossRef]
- Babaei, M. A Novel Text and Image Encryption Method Based on Chaos Theory and DNA Computing. Nat. Comput. 2013, 12, 101–107. [Google Scholar] [CrossRef]
- Barrera, J.F.; Henao, R.; Torroba, R. Optical Encryption Method Using Toroidal Zone Plates. Opt. Commun. 2005, 248, 35–40. [Google Scholar] [CrossRef]
- Beletskyy, V.; Burak, D. Parallelization of the Data Encryption Standard (DES) Algorithm. In Enhanced Methods in Computer Security, Biometric and Artificial Intelligence Systems; Pejaś, J., Piegat, A., Eds.; Kluwer Academic Publishers: Boston, MA, USA, 2005; pp. 23–33. ISBN 978-1-4020-7776-0. [Google Scholar]
- Schaffer, T.; Glaser, A.; Franzon, P.D. Chip-Package Co-Implementation of a Triple DES Processor. IEEE Trans. Adv. Packag. 2004, 27, 194–202. [Google Scholar] [CrossRef]
- Genkin, D.; Shamir, A.; Tromer, E. RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis. In Advances in Cryptology—CRYPTO 2014; Garay, J.A., Gennaro, R., Eds.; Lecture Notes in Computer Science; Springer: Heidelberg/Berlin, Germany, 2014; Volume 8616, pp. 444–461. ISBN 978-3-662-44370-5. [Google Scholar]
- Bailey, K.; Curran, K. An Evaluation of Image Based Steganography Methods. Multimed Tools Appl. 2006, 30, 55–88. [Google Scholar] [CrossRef][Green Version]
- Sallee, P. Model-Based Steganography. In Digital Watermarking; Kalker, T., Cox, I., Ro, Y.M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2939, pp. 154–167. ISBN 978-3-540-21061-0. [Google Scholar]
- Cheddad, A.; Condell, J.; Curran, K.; Mc Kevitt, P. Digital Image Steganography: Survey and Analysis of Current Methods. Signal Process 2010, 90, 727–752. [Google Scholar] [CrossRef]
- Sinha, R.; Papadopoulos, C.; Kyriakakis, C. Loss Concealment for Multi-Channel Streaming Audio. In Proceedings of the Proceedings of the 13th International Workshop on Network and Operating Systems Support for Digital Audio and Video, Monterey, CA, USA, 1–3 June 2003; ACM: Monterey CA USA, 2003; pp. 100–109. [Google Scholar]
- Bei, Y.L.; Yang, D.Y.; Liu, M.X.; Zhu, L.L. A Multi-Channel Watermarking Scheme Based on HVS and DCT-DWT. In Proceedings of the 2011 IEEE International Conference on Computer Science and Automation Engineering, Shanghai, China, 10–12 June 2011; pp. 305–308. [Google Scholar]
- Al-Rawi, A.L.; Blackledge, J.; Hickson, R. Multi-Channel Audio Information Hiding. In Proceedings of the Digital Audio Effects Conference (DAFx2012), York, UK, 17–21 September 2012. [Google Scholar] [CrossRef]
- Tsvetcov, K.U.; Makarenko, S.I.; Mikhailov, R.L. Forming Reserve Paths Based on Dijkstra Algorithm in Order to Enhance Stability of Telecommunication Networks. Inf. Control Syst. 2014, 69, 71–78. [Google Scholar]
- Patil, P.; Narayankar, P.; Narayan, D.G.; Meena, S.M. A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Comput. Sci. 2016, 78, 617–624. [Google Scholar] [CrossRef]
- Singh, G. A Study of Encryption Algorithms (RSA, DES, 3DES and AES) for Information Security. Int. J. Comput. Appl. 2013, 67, 33–38. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü.; Kaçar, S.; Zengin, A.; Pehlivan, I. A Novel Hybrid Encryption Algorithm Based on Chaos and S-AES Algorithm. Nonlinear Dyn. 2018, 92, 1745–1759. [Google Scholar] [CrossRef]
- Deshmukh, P.; Kolhe, V. Modified AES Based Algorithm for MPEG Video Encryption. In Proceedings of the International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–5. [Google Scholar]
- Sharma, P.; Sabharwal, H. A New Image Encryption Using Modified Aes Algorithm and Its Comparision with AES. Int. J. Eng. Res. Technol. (IJERT) 2020, 9, 194–197. [Google Scholar]
- Hafsa, A.; Sghaier, A.; Malek, J.; Machhout, M. Image Encryption Method Based on Improved ECC and Modified AES Algorithm. Multimed. Tools Appl. 2021, 80, 19769–19801. [Google Scholar] [CrossRef]
- Bader, A.S.; Sagheer, A.M. Modification on AES-GCM to Increment Ciphertext Randomness. Trans. Int. J. Math. Sci. Comput 2018, 4, 34–40. [Google Scholar] [CrossRef]
- Yingbing, Z.; Yongzhen, L. The Design and Implementation of a Symmetric Encryption Algorithm Based on DES. In Proceedings of the 2014 IEEE 5th International Conference on Software Engineering and Service Science, Beijing, China, 27–29 June 2014; pp. 517–520. [Google Scholar]
- Chai, X.; Gan, Z.; Zhang, M. A Fast Chaos-Based Image Encryption Scheme with a Novel Plain Image-Related Swapping Block Permutation and Block Diffusion. Multimed. Tools Appl. 2017, 76, 15561–15585. [Google Scholar] [CrossRef]
- Parida, P.; Pradhan, C.; Gao, X.-Z.; Roy, D.S.; Barik, R.K. Image Encryption and Authentication with Elliptic Curve Cryptography and Multidimensional Chaotic Maps. IEEE Access 2021, 9, 76191–76204. [Google Scholar] [CrossRef]
- Elghandour, A.; Salah, A.; Karawia, A. A New Cryptographic Algorithm via a Two-Dimensional Chaotic Map. Ain Shams Eng. J. 2022, 13, 101489. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-Modulated-Sine-Coupling-Logistic Chaotic Map for Image Encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Lu, Q.; Zhu, C.; Deng, X. An Efficient Image Encryption Scheme Based on the LSS Chaotic Map and Single S-Box. IEEE Access 2020, 8, 25664–25678. [Google Scholar] [CrossRef]
- Gedkhaw, E.; Soodtoetong, N.; Ketcham, M. The Performance of Cover Image Steganography for Hidden Information within Image File Using Least Significant Bit Algorithm. In Proceedings of the 2018 18th International Symposium on Communications and Information Technologies (ISCIT), Bangkok, Thailand, 26–29 September 2018; pp. 504–508. [Google Scholar]
- Khrisat, M.S.; Alqadi, Z.A. Enhancing LSB Method Performance Using Secret Message Segmentation. IJCSNS 2022, 22, 1–6. [Google Scholar]
- Alqadi, Z.; Zahran, B.; Jaber, Q.; Ayyoub, B.; Al-Azzeh, J.; Sharadqh, A. Proposed Implementation Method to Improve LSB Efficiency. Int. J. Comput. Sci. Mob. Comput. 2019, 8, 306–319. [Google Scholar]
- Mahimah, P.; Kurinji, R. Zigzag Pixel Indicator Based Secret Data Hiding Method. In Proceedings of the 2013 IEEE International Conference on Computational Intelligence and Computing Research, Enathi, Tamilnadu, India, 26–28 December 2013; pp. 1–5. [Google Scholar]
- Yigit, Y.; Karabatak, M. A Stenography Application for Hiding Student Information into an Image. In Proceedings of the 2019 7th International Symposium on Digital Forensics and Security (ISDFS), Barcelos, Portugal, 10–12 June 2019; pp. 1–4. [Google Scholar]
- Swain, G. Adaptive Pixel Value Differencing Steganography Using Both Vertical and Horizontal Edges. Multimed Tools Appl 2016, 75, 13541–13556. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. Pixel Overlapping Image Steganography Using PVD and Modulus Function. 3D Res. 2018, 9, 40. [Google Scholar] [CrossRef]
- Li, Z.; He, Y. Steganography with Pixel-Value Differencing and Modulus Function Based on PSO. J. Inf. Secur. Appl. 2018, 43, 47–52. [Google Scholar] [CrossRef]
- Wang, W.-J.; Zhang, Y.-H.; Huang, C.-T.; Wang, S.-J. Steganography of Data Embedding in Multimedia Images Using Interpolation and Histogram Shifting. In Proceedings of the 2013 Ninth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Beijing, China, 16–18 October 2013; pp. 387–390. [Google Scholar]
- Wang, J.; Ni, J.; Zhang, X.; Shi, Y.-Q. Rate and Distortion Optimization for Reversible Data Hiding Using Multiple Histogram Shifting. IEEE Trans. Cybern. 2016, 47, 315–326. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Arch-int, S.; Arch-int, N. An Adaptive Multi Bit-Plane Image Steganography Using Block Data-Hiding. Multimed. Tools Appl. 2016, 75, 8319–8345. [Google Scholar] [CrossRef]
- Imaizumi, S.; Ozawa, K. Multibit Embedding Algorithm for Steganography of Palette-Based Images. In Image and Video Technology; Klette, R., Rivera, M., Satoh, S., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8333, pp. 99–110. ISBN 978-3-642-53841-4. [Google Scholar]
- Shi, H.; Dong, J.; Wang, W.; Qian, Y.; Zhang, X. SSGAN: Secure Steganography Based on Generative Adversarial Networks. In Advances in Multimedia Information Processing—PCM 2017; Zeng, B., Huang, Q., El Saddik, A., Li, H., Jiang, S., Fan, X., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2018; Volume 10735, pp. 534–544. ISBN 978-3-319-77379-7. [Google Scholar]
- Yang, J.; Ruan, D.; Huang, J.; Kang, X.; Shi, Y.-Q. An Embedding Cost Learning Framework Using GAN. IEEE Trans. Inform. Forensic Secur. 2020, 15, 839–851. [Google Scholar] [CrossRef]
- Ur Rehman, A.; Rahim, R.; Nadeem, S.; ul Hussain, S. End-to-End Trained CNN Encoder-Decoder Networks for Image Steganography. In Computer Vision—ECCV 2018 Workshops; Leal-Taixé, L., Roth, S., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2019; Volume 11132, pp. 723–729. ISBN 978-3-030-11017-8. [Google Scholar]
- Li, Z.; Han, G.; Guo, S.; Hu, C. DeepKeyStego: Protecting Communication by Key-Dependent Steganography with Deep Networks. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS); IEEE: Zhangjiajie, China, 10-12 August, 2019; pp. 1937–1944. [Google Scholar]
- Chen, M.; Liu, W.; Zhang, N.; Li, J.; Ren, Y.; Yi, M.; Liu, A. GPDS: A Multi-Agent Deep Reinforcement Learning Game for Anti-Jamming Secure Computing in MEC Network. Expert Syst. Appl. 2022, 210, 118394. [Google Scholar] [CrossRef]
- Chen, M.; Yi, M.; Huang, M.; Huang, G.; Ren, Y.; Liu, A. A Novel Deep Policy Gradient Action Quantization for Trusted Collaborative Computation in Intelligent Vehicle Networks. Expert Syst. Appl. 2023, 221, 119743. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Li, Y.; Li, Z.; Choi, Y.; Sekiya, H.; Li, J. APMD: A Fast Data Transmission Protocol with Reliability Guarantee for Pervasive Sensing Data Communication. Pervasive Mob. Comput. 2017, 41, 413–435. [Google Scholar] [CrossRef]
- Guo, J.; Liu, Z.; Tian, S.; Huang, F.; Li, J.; Li, X.; Igorevich, K.K.; Ma, J. TFL-DT: A Trust Evaluation Scheme for Federated Learning in Digital Twin for Mobile Networks. IEEE J. Select. Areas Commun. 2023, 1. [Google Scholar] [CrossRef]
- Liu, Z.; Weng, J.; Ma, J.; Guo, J.; Feng, B.; Jiang, Z.; Wei, K. TCEMD: A Trust Cascading-Based Emergency Message Dissemination Model in VANETs. IEEE Internet Things J. 2020, 7, 4028–4048. [Google Scholar] [CrossRef]
- Liu, Z.; Huang, F.; Weng, J.; Cao, K.; Miao, Y.; Guo, J.; Wu, Y. BTMPP: Balancing Trust Management and Privacy Preservation for Emergency Message Dissemination in Vehicular Networks. IEEE Internet Things J. 2021, 8, 5386–5407. [Google Scholar] [CrossRef]
- Baluja, S. Hiding Images within Images. IEEE Trans. Pattern Anal. Mach. Intell. 2020, 42, 1685–1697. [Google Scholar] [CrossRef] [PubMed]
- Abdullaziz, O.I.; Goh, V.T.; Ling, H.-C.; Wong, K. Network Packet Payload Parity Based Steganography. In Proceedings of the 2013 IEEE Conference on Sustainable Utilization and Development in Engineering and Technology (CSUDET), Selangor, Malaysia, 30 May–1 June 2013; pp. 56–59. [Google Scholar]
- Bedi, P.; Dua, A. Network Steganography Using the Overflow Field of Timestamp Option in an IPv4 Packet. Procedia Comput. Sci. 2020, 171, 1810–1818. [Google Scholar] [CrossRef]
- Bobade, S.; Goudar, R. Secure Data Communication Using Protocol Steganography in IPv6. In Proceedings of the 2015 International Conference on Computing Communication Control and Automation, Pune, India, 26–27 February 2015; pp. 275–279. [Google Scholar]
- Drzymała, M.; Szczypiorski, K.; Urbański, M.Ł. Network Steganography in the DNS Protocol. Int. J. Electron. Telecommun. 2016, 62, 343–346. [Google Scholar] [CrossRef]
- Makarenko, S. The steganographic system interconnection basic reference model and the justification of new areas of steganography theory’s development. Vopr. Kiberbezopasnosti 2014, 2, 24–32. [Google Scholar]
- Fan, T.K.K. Methodology for Substantiating a Stegochannel Metric That Takes into Account Privacy Indicators for a Routing Protocol in a Stegonographic Network. Specialist. Degree Thesis, St. Petersburg State Electrotechnical University, St. Petersburg, Russia, 2021. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).