Abstract
This paper investigates the secure rate-splitting multiple access (RSMA) cooperation for the maritime cognitive unmanned aerial vehicle (UAV) network. Specifically, we first take into account the primary privacy information and the secondary maritime UAV’s quality of service. Then, we formulate an optimization problem to maximize UAV’s transmission rate according to the RSMA decoding principle and primary information security requirements. To solve this non-convex problem, we design a CPFS algorithm to allocate the transmit power and adjust the UAV’s location. In addition, the worst case is analyzed, which is the lower-bound secondary transmission rate. Finally, simulation results indicate that the proposed scheme improves the UAV’s transmission rate compared with the traditional schemes.
1. Introduction
The fifth generation mobile technique provides support for ultra-reliable low-latency services in order to facilitate global interconnections among space, ground, and maritime devices [1,2]. As a critical component of the global Internet of Things, maritime wireless networks can serve multiple functions, including ship navigation, unmanned underwater vehicle (UUV) control, as well as maritime real-time tracking and positioning [3,4]. As the global economy begins to recover after COVID-19, the marine wireless communication network is expected to support a significant number of devices for ocean activities. In addition to maritime satellites, shore-based maritime networks are an important approach to realize most maritime applications. Moreover, the terrestrial base state along the coastline is built to support maritime communications, which has been widely investigated in the current research [5].
Benefiting from their flexible deployment and low cost, unmanned aerial vehicles (UAVs) have been widely adopted in maritime networks. In the UAV-assisted networks, the power allocation and UAV’s position optimization have been widely discussed. In [6], the authors studied the power allocation for the transmit power and jamming power to securely transmit the privacy information. In [7], the power of the users was minimized by considering the UAV’s coverage. In addition, the downlink and uplink power allocation for the UAV networks was investigated in [8]. In addition to the power allocation, the position of a UAV will affect the network performance. In [9], the UAV’s location was optimized for the UAV relay networks. Then, this work was extended to the two-way networks with optimal UAV’s location [10]. Moreover, the joint UAV’s location and power allocation was studied in [11].
Due to the limited available spectrum, maritime wireless transmissions face considerable interference challenges [12,13]. The cognitive radio technique can alleviate the spectrum shortage situation by allowing the secondary users to utilize the primary spectrum and control the effect to the primary transmissions. In addition to cognitive radio techniques, rate-splitting multiple access (RSMA) is one of the most promising techniques with high spectral efficiency for the next generation networks. In RSMA systems, the messages are split into two or more parts and the receiver should recover all parts to successfully decode the message. Benefiting from the flexible management of each part, inter-user interference could be minimized [14]. In the cognitive radio network, the authors achieved the high ergodic rate of uplink cognitive transmissions [15]. In addition, in [16], the transmit power was optimally allocated, based on which the performance was compared with the non-orthogonal multiple access (NOMA) scheme. Considering the limited energy of the devices, the authors investigated the power allocation for the RSMA-based cognitive radio networks constrained by the energy harvesting and primary inference requirements [17].
The open transmission media of maritime wireless networks makes privacy information sensitive to eavesdropping. In addition to the encryption methods, physical-layer security techniques can protect the privacy of information by utilizing wiretap coding. Adopting a cooperative jamming scheme, the researchers in [18] designed a cooperation secure transmission strategy with considering multiple cognitive users and multiple carriers. In addition, the RSMA scheme was adopted to simultaneously communicate with the secondary user and jam the eavesdropper while controlling the inference to the primary users. Extending to the satellite networks, the authors in [19] proposed a secure and energy-efficient cognitive beamforming method for the satellite systems, where the analytical and asymptotic secrecy outage probability were derived under interfering and imperfect channel state information (CSI). Moreover, the above works were extended to the multiple eavesdropper’s scenarios, and a new secure-energy problem was formulated to optimally allocate the transmit power in cognitive satellite-terrestrial networks [20]. When the RSMA users were distrustful of each other, the outage probabilities were analyzed in [21]. Assisted by the intelligent reflecting surface, the secrecy rate was maximized in [22], where the transmit power and phase shifts were optimally designed.
The above works have enhanced the quality of services (QoS) of the RSMA-based networks. Nevertheless, there are some deficiencies to be addressed. In [14,15,16,17], the cognitive RSMA networks are investigated, based on which the power is allocated. However, the information security problem has not yet been investigated. In [18,19,20,21,22], the information security problem for the RSMA is studied, while ignoring the assistance from the secondary networks. Moreover, the above works have not considered the actual application requirements in maritime networks. For example, utilizing the UAV as a secondary transmitter (ST) is a promising approach for improving spectrum efficiency in maritime cognitive radio networks [23].
Motivated by the above discussions, this paper studied the cognitive secure RSMA transmission problem in maritime networks, where the cooperation between the primary and secondary networks is considered to support both networks’ QoS requirements. To the best of the authors’ knowledge, this is the first work that investigates the secure RSMA cooperation for the maritime cognitive networks. Specifically, in the proposed scheme, the secondary maritime UAV’s transmission can not only broadcast secondary information but also protect the primary transmission. Through the flexible allocation of the transmission resources, both users’ QoS can be provided. We formulate an optimization problem to maximize the UAV’s transmission rate under the RSMA decoding principle and primary information security requirements. We design a combined particle swarm optimization and fish swarm optimization (CPFS) algorithm to allocate the transmit power and design the UAV’s location. In addition, the worst case is analyzed, which is considered as the lower-bound to the UAV’s transmission. The main contributions are summarized as follows:
- We design a novel secure RSMA strategy for the maritime cognitive to support both primary and maritime UAV’s transmissions. In the proposed strategy, the secondary maritime UAV’s transmission can not only broadcast secondary information but also protect the primary transmission. Through the flexible allocation of the transmission resources, both users’ QoS can be provided.
- We formulate an optimization problem to maximize the UAV’s transmission rate under the RSMA decoding principle and primary information security requirements. To solve the above non-convex problem, we design a CPFS algorithm to allocate the transmit power and design the UAV’s location. In addition, the worst case is analyzed, which is considered as the lower-bound to the UAV’s transmission.
2. System Model and Problem Formulation
The maritime network is shown in Figure 1, where the primary maritime ship (PT) broadcasts the privacy signal to the base station (BS), threatened by an eavesdropper (Eve). To protect PT’s transmission, a cognitive UAV (ST) is deployed to protect PT’s secure communication, and access the spectrum for the secondary transmission. In addition, the RSMA technique is adopted to process PT’s privacy signal and the UAV’s signal, and provide the primary and secondary users’ requirements. This system can capture the application of the maritime sensor networks, where the maritime cognitive UAV collects the sensing data by occupying the limited spectrum, while the primary maritime user securely forwards it information to the BS. In order to clearly show the performance of the two systems, we assume that all users have only one antenna.
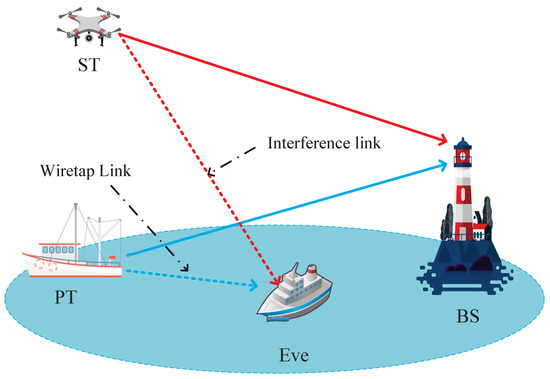
Figure 1.
The cognitive RSMA system.
In the proposed system, the locations of , , , and are denoted as , , , and , respectively. The altitude of UAV is fixed at h. The flat fading model is adopted for the links of and . We denote the channel variables of and as and , respectively. In addition, their channel power gains are denoted as and , which follow exponential distributions with parameters and , respectively. Since there are no obstacles during the transmission links and , the line-of-sight links are dominant. Therefore, the channel variables of links and are derived as
where is the path loss with distance 1 m, is the distance between the and with , is the distance between the and with , and is the path fading factor. In addition, the channel power gain of and are derived as and , respectively. The instantaneous CSI of is available. However, for practical consideration, the wiretap CSI cannot be acquired and the channel distribution information is available. PT’s transmit power and ST’s transmit power are denoted as and , respectively. In addition, we assume that all noises are cyclic white Gaussian noise with . In the following, we will illustrate the information transmission process.
In the considered system, the RSMA is adopted for cooperative transmissions. Specifically, ST’s signal is divided into two parts: and , with and , respectively, where denotes the expectation operation. In addition, and are transmitted with power and , respectively, where is the power allocation parameter. The primary system adopts the fixed rate to transmit PT’s information, which is denoted as with . Therefore, the received signals at the BS are derived as
where is the secondary power allocation parameter, and is the noise at the BS. Eve tries to eavesdrop the signals as
where is the received noise at Eve.
According to the RSMA strategy, the BS first decodes with rate as
Then, the BS cancels and decodes with rate as
When is successfully decoded, the BS cancels and decodes with rate as
Then, the total secondary transmission rate is derived as .
Similarly, the Eve also decodes the received signal to eavesdrop on the primary information. According to the RSMA strategy, Eve first decodes with rate as
In order to successfully decode the secondary information, should be larger than , where is the secondary target rate. Under this condition, Eve will cancel and decode with rate as
However, if , Eve will decode PT’s signal by trading the other signals as interference with the rate as
We denote as Case 1 and denote as Case 2. Therefore, the probability of Case 1 is derived as
The probability of Case 2 is .
Since the instantaneous CSI of the wiretap channel is unavailable, we will adopt the secrecy outage probability to denote the security requirement. Since the primary user will transmit with the fixed rate, the secrecy outage probability is derived as
where and is the target secrecy rate. For Case 2, the secrecy outage probability is derived as
Then, PT’s average secrecy outage probability is given by
In the next section, we will allocate ST’s power and optimize UAV’s location to maximize the UAV’s rate while satisfying the PT’s privacy requirement.
3. RSMA-Based Cognitive Maritime Transmission Strategy
In order to maximize the secondary transmission rate and protect the primary transmission rate, we formulate the optimization problem as
where (14a) is the secondary transmission rate, (14b) indicates that the signal can be successfully decoded and the secondary information is successfully transmitted, (14c) indicates that the signal can be successfully decoded and the primary information is successfully transmitted, and (14d) is the primary secure transmission requirement. For , since the optimal variables are coupled with each other and the (14d) is non-convex, it is difficult to directly derive the power allocation parameter and UAV’s location. In the following, an iterative algorithm is designed to solve P1.
3.1. Power Allocation
Lemma 1.
is a monotonically increasing function of α.
Proof.
For , its first-order derivation is derived as
Therefore, the first-order derivation of is derived as shown in (18).
Since is less than , . Therefore, is a monotonically increasing function with respect to . □
In addition, for (14b), we can derive
For (14c), we can derive
For (14d), we denote , and can be rewritten as (21). We can observe that (21) is a monotonically decreasing function of . Therefore, satisfies that when .
Therefore, the sub-optimal is derived as under the condition of .
3.2. UAV’s Location Optimization
For the UAV’s location, we adopt the CPFS algorithm to solve P1 with respect to . Particle swarm optimization (PSO) imitates the foraging behavior of birds by utilizing information exchange methods and strategies employed by birds during the process of searching for food, which is widely adopted to derive the UAV’s location [24,25]. The PSO algorithm searches the global optimum by following the currently searched optimum, which is easy to implement and fast to converge. Although the PSO algorithm has good convergence performance, it falls into the local optimum with high probability [26]. The fish swarm optimization (FSO) can achieve a global optimization algorithm [27]. Combining PSO and FSO will take advantage of both algorithms to quickly derive the optimal target. Therefore, we combine PSO and FSO to optimize UAV’s position and design a CPFS algorithm. In the CPFS algorithm, the updates of the speed and position are shown as
and
where is the weight in each iteration, is the velocity of particle i at time , is the particle i’s position at time t, is particle i’s best position experienced at time t, is all particles’ best position at time t, and and are the acceleration coefficients, which are always set to 2.
According to the above discussion, the CPFS algorithm can be shown in Algorithm 1, where
| Algorithm 1 The proposed CPFS algorithm. |
|
4. RSMA-Based Cognitive Maritime Transmission with Powerful Eve
In this section, we will study the proposed scheme of the special case where Eve always can cancel with Case 1 as
where (27d) is the security requirement. Due to the non-convex (27d), we design an iterative algorithm to solve this problem.
4.1. Power Allocation
Given the UAV’s location, according to (27e), we can derive
Since the optimal target is decrease with , the sub-optimal is derived as
where .
4.2. UAV’s Location Optimization
The UAV’s location will affect the channels of and , which can be rewritten as and . According to the derived , P2 can be reformulated as
We can observe that P3 is a convex problem and we can derive the sub-optimal location through the convex algorithm.
Then, the algorithm is summarized in Algorithm 2.
| Algorithm 2 The proposed iterative algorithm. |
|
5. Simulation Results
We conduct simulations to evaluate the UAV’s rate in the considered system compared with the current algorithms: the NOMA scheme [16] and the underlay scheme [28]. In the NOMA scheme, the secondary UAV adopts the NOMA scheme to protect PT’s information and broadcasts UAV’s information. For the underlay scheme, ST will broadcast its information under the interference threshold to the primary transmitter. In the simulations, we adopt the topology as shown in Figure 2. The main simulation parameters are shown in Table 1 [29,30].
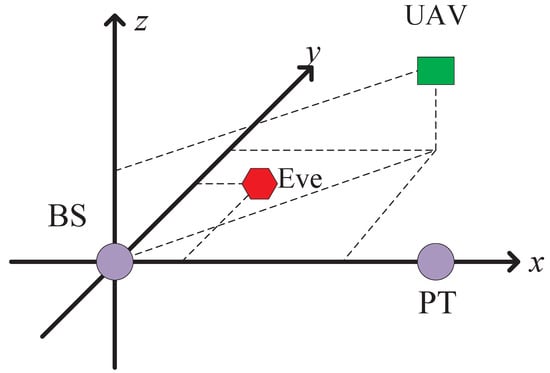
Figure 2.
The topology of the proposed system.

Table 1.
Simulation parameters.
In Figure 3, we demonstrate the secondary transmit power versus the UAV’s power . From Figure 3, we can observe that the proposed scheme achieves the best performance compared with the scheme, since the transmission resources are flexibly managed. When the power is low, more of the power is allocated for the transmission of , and the will be almost 1, which is almost equal to the NOMA scheme. When the power is high, there will be more power for the transmission of . Therefore, the transmission rate of the RSMA scheme will increase. In the worst case, the cooperation is conducted under strict security constraints, which will lead to a decrease in the UAV’s rate. In addition, the flexible power control at the UAV is ignored which leads to a secondary transmission rate decrease. Since the cooperation between the UAV and PT is ignored, the secondary transmission rate for the underlay scheme is the lowest among all the schemes.
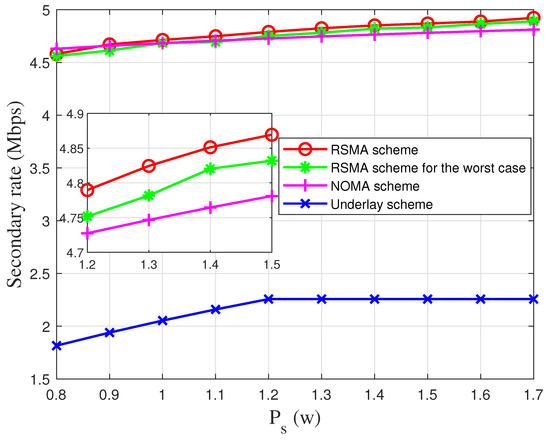
Figure 3.
The secondary transmission rate versus the secondary transmit power.
In Figure 4, we simulate UAV’s rate with respect to under different UAV’s altitudes, i.e., h with Watts. In this figure, we can observe that the UAV’s rate will increase with respect to . When is large, it is easy to satisfy the primary security requirement and there will be more transmission opportunities. Therefore, the UAV’s rate will increase. In addition, with the increase of the UAV’s altitudes, there will be more power to overcome fading, which results in less power for cooperation. Similarly, we can obverse that the transmit power of the NOMA strategy is lower than the proposed scheme.
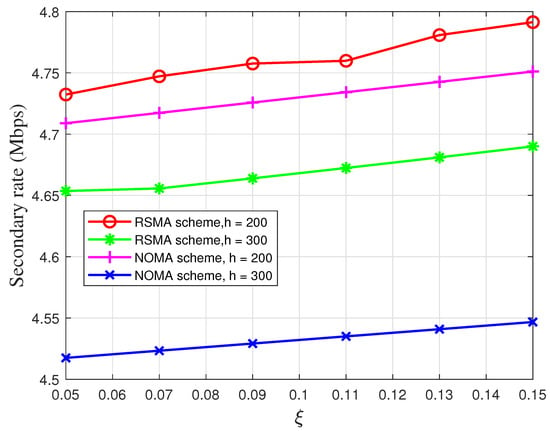
Figure 4.
The secondary transmission rate versus the secrecy outage probability constraint.
In Figure 5, we demonstrate the UAV’s rate with respect to under different UAV altitudes. We can observe that the UAV’s rate will decrease with respect to . When is increased, the secondary system will interfere with large power and there will be fewer transmission opportunities. Therefore, the UAV’s rate will decrease. In addition, with the increase in the UAV’s altitudes, there will be more power to overcome fading, which results in less power for the secondary transmission. Similarly, we can obverse that the transmit power of the NOMA scheme is lower.
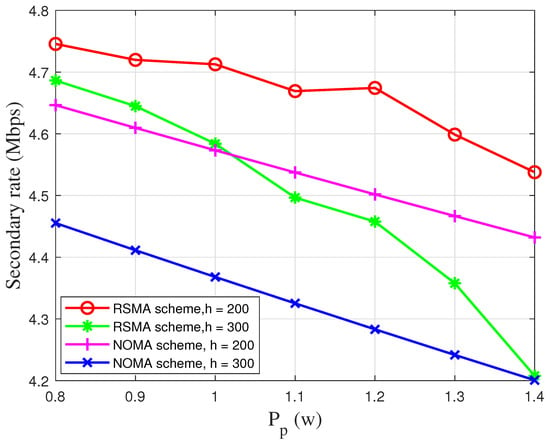
Figure 5.
The secondary transmission rate versus the primary transmit power.
Figure 6a illustrates the average running time of the three algorithms. Figure 6b shows the secondary rate comparison of the three algorithms, where Watt. From Figure 6a, we can know that the PSO algorithm has the lowest running time, and the FSO algorithm has the highest running time. By contrast, the running time of our proposed CPFS algorithm is close to that of the PSO algorithm, and much lower than that of the FSO algorithm. However, according to Figure 6b, it is observed that the CPFS algorithm is far superior to the PSO algorithm in terms of the secondary rate.
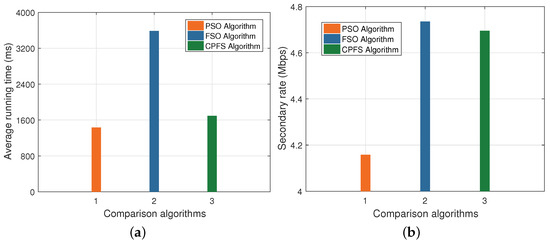
Figure 6.
The improvement archived by combining PSO and FSO. (a) Complexity comparison. (b) Secondary rate comparison.
6. Conclusions
In this paper, we proposed a novel cooperative secure RSMA scheme for cognitive maritime applications to support both primary and secondary transmissions. In this scheme, the secondary transmission could not only broadcast secondary information but also protect the primary transmission. In order to satisfy both users’ QoS, we formulated the optimization problem to maximize the UAV’s rate under the RSMA decoding principle and primary information security requirements. We designed a CPFS algorithm to allocate the transmit power and adjust the UAV’s location. In addition, the worst case was analyzed. The simulation results indicated the performance improvement in terms of the secondary transmission rate compared with the traditional schemes. Our proposed solution can not only be applied to maritime networks, but also to UAV communications, information security and other fields. Inspired by the works [31,32] on UAVs, we will further study the feasibility of using the RSMA-enhanced UAV network to provide timely information services.
Author Contributions
L.M.: Conceptualization, Methodology, Software, Writing-Original Draft Preparation, and Visualization. J.L.: Conceptualization, Resources, Methodology, Software, and Writing-Review. Y.H.: Conceptualization, Resources, Writing-Review and Editing, Supervision, Project Administration, and Funding Acquisition. W.W.: Conceptualization, Resources, Methodology, Software, and Writing-Review. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China under Grant 62206221, and in part by the Fundamental Research Funds for the Central Universities.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest for publishing in this journal.
References
- Arienzo, L. Green RF/FSO Communications in Cognitive Relay-Based Space Information Networks for Maritime Surveillance. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 1182–1193. [Google Scholar] [CrossRef]
- Wang, D.; He, T.; Zhou, F.; Cheng, J.; Zhang, R.; Wu, Q. Outage-driven link selection for secure buffer-aided networks. Sci. China Inf. Sci. 2022, 65, 182303. [Google Scholar] [CrossRef]
- Su, X.; Meng, L.; Huang, J. Intelligent Maritime Networking With Edge Services and Computing Capability. IEEE Trans. Veh. Technol. 2020, 69, 13606–13620. [Google Scholar] [CrossRef]
- Arguedas, V.F.; Pallotta, G.; Vespe, M. Maritime traffic networks: From historical positioning data to unsupervised maritime traffic monitoring. IEEE Trans. Intell. Transp. Syst. 2017, 19, 722–732. [Google Scholar] [CrossRef]
- Tang, R.; Feng, W.; Chen, Y.; Ge, N. NOMA-based UAV communications for maritime coverage enhancement. China Commun. 2021, 18, 230–243. [Google Scholar] [CrossRef]
- Xu, K.; Zhao, M.-M.; Cai, Y.; Hanzo, L. Low-Complexity Joint Power Allocation and Trajectory Design for UAV-Enabled Secure Communications with Power Splitting. IEEE Trans. Commun. 2021, 69, 1896–1911. [Google Scholar] [CrossRef]
- Wang, D.; Wu, M.; He, Y.; Pang, L.; Xu, Q.; Zhang, R. An HAP and UAVs collaboration framework for uplink secure rate maximization in NOMA-enabled IoT networks. Remote Sens. 2022, 14, 4501. [Google Scholar] [CrossRef]
- Zhang, G.; Wu, Q.; Cui, M.; Zhang, R. Securing UAV Communications via Joint Trajectory and Power Control. IEEE Trans. Wirel. Commun. 2019, 18, 1376–1389. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, H.; Guo, S.; Yuan, D. Deployment and Association of Multiple UAVs in UAV-Assisted Cellular Networks With the Knowledge of Statistical User Position. IEEE Trans. Wirel. Commun. 2022, 21, 6553–6567. [Google Scholar] [CrossRef]
- Li, L.; Chang, T.-H.; Cai, S. UAV Positioning and Power Control for Two-Way Wireless Relaying. IEEE Trans. Wirel. Commun. 2020, 19, 1008–1024. [Google Scholar] [CrossRef]
- Jiang, M.; Li, Y.; Zhang, Q.; Qin, J. Joint Position and Time Allocation Optimization of UAV Enabled Time Allocation Optimization Networks. IEEE Trans. Commun. 2019, 67, 3806–3816. [Google Scholar] [CrossRef]
- Wang, J.-B.; Zeng, C.; Ding, C.; Zhang, H.; Lin, M.; Wang, J. Unmanned Surface Vessel Assisted Maritime Wireless Communication Toward 6G: Opportunities and Challenges. IEEE Wirel. Commun. 2022, 29, 72–79. [Google Scholar] [CrossRef]
- Zeng, C.; Wang, J.-B.; Ding, C.; Zhang, H.; Lin, M.; Cheng, J. Joint Optimization of Trajectory and Communication Resource Allocation for Unmanned Surface Vehicle Enabled Maritime Wireless Networks. IEEE Trans. Commun. 2021, 69, 8100–8115. [Google Scholar] [CrossRef]
- Clerckx, B.; Mao, Y.; Jorswieck, E.A.; Yuan, J.; Love, D.J.; Erkip, E.; Niyato, D. A Primer on Rate-Splitting Multiple Access: Tutorial, Myths, and Frequently Asked Questions. IEEE J. Sel. Areas Commun. 2023, accepted.
- Xiao, Y.; Tegos, S.A.; Diamantoulakis, P.D.; Ma, Z.; Karagiannidis, G.K. On the Ergodic Rate of Cognitive Radio Inspired Uplink Multiple Access. IEEE Commun. Lett. 2023, 27, 95–99. [Google Scholar] [CrossRef]
- Gamal, S.; Rihan, M.; Hussin, S.; Zaghloul, A.; Salem, A.A. Multiple Access in Cognitive Radio Networks: From Orthogonal and Non-Orthogonal to Rate-Splitting. IEEE Access 2021, 9, 95569–95584. [Google Scholar] [CrossRef]
- Acosta, M.R.C.; Moreta, C.E.G.; Koo, I. Joint Power Allocation and Power Splitting for MISO-RSMA Cognitive Radio Systems With SWIPT and Information Decoder Users. IEEE Syst. J. 2021, 15, 5289–5300. [Google Scholar] [CrossRef]
- Dizdar, O.; Clerckx, B. Rate-Splitting Multiple Access for Communications and Jamming in Multi-Antenna Multi-Carrier Cognitive Radio Systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 628–643. [Google Scholar] [CrossRef]
- Li, X.; Fan, Y.; Yao, R.; Wang, P.; Qi, N.; Miridakis, N.I.; Tsiftsis, T.A. Rate-Splitting Multiple Access-Enabled Security Analysis in Cognitive Satellite Terrestrial Networks. IEEE Trans. Veh. Tech. 2022, 71, 11756–11771. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secure and Energy Efficient Transmission for RSMA-Based Cognitive Satellite-Terrestrial Networks. IEEE Wirel. Commun. Lett. 2021, 10, 251–255. [Google Scholar] [CrossRef]
- Tong, Y.; Li, D.; Yang, Z.; Xiong, Z.; Zhao, N.; Li, Y. Outage Analysis of Rate Splitting Networks with an Untrusted User. IEEE Trans. Veh. Tech. 2023, 72, 2626–2631. [Google Scholar] [CrossRef]
- Gao, Y.; Wu, Q.; Chen, W.; Ng, D.W.K. Rate-Splitting Multiple Access for Intelligent Reflecting Surface-Aided Secure Transmission. IEEE Commun. Lett. 2023, 27, 482–486. [Google Scholar] [CrossRef]
- He, Y.; Wang, D.; Huang, F.; Zhang, R.; Gu, X.; Pan, J. A V2I and V2V collaboration framework to support emergency communications in ABS-aided Internet of Vehicles. IEEE Trans. Green Commun. Netw. 2023, to be published. [CrossRef]
- Zhang, W.; Zhang, W. An Efficient UAV Localization Technique Based on Particle Swarm Optimization. IEEE Trans. Veh. Technol. 2022, 71, 9544–9557. [Google Scholar] [CrossRef]
- Wang, D.; Zhou, F.; Lin, W.; Ding, Z.; Al-Dhahir, N. Cooperative hybrid nonorthogonal multiple access-based mobile-edge computing in cognitive radio networks. IEEE Trans. Cognit. Commun. Netw. 2022, 8, 1104–1117. [Google Scholar] [CrossRef]
- Yu, Z.; Si, Z.; Li, X.; Wang, D.; Song, H. A Novel Hybrid Particle Swarm Optimization Algorithm for Path Planning of UAVs. IEEE Internet Things J. 2022, 9, 22547–22558. [Google Scholar] [CrossRef]
- Khan, S.U.; Yang, S.; Wang, L.; Liu, L. A Modified Particle Swarm Optimization Algorithm for Global Op-timizations of Inverse Problems. IEEE Trans. Magn. 2016, 52, 1–4. [Google Scholar]
- Nobar, S.K.; Ahmed, M.H.; Morgan, Y.; Mahmoud, S.A. Resource Allocation in Cognitive Radio-Enabled UAV Communication. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 296–310. [Google Scholar] [CrossRef]
- Lu, X.; Yang, W.; Yan, S.; Li, Z.; Ng, D.W.K. Covertness and Timeliness of Data Collection in UAV-Aided Wireless-Powered IoT. IEEE Internet Things J. 2021, 9, 12573–12587. [Google Scholar] [CrossRef]
- Hadzi-Velkov, Z.; Pejoski, S.; Zlatanov, N.; Schober, R. UAV-Assisted Wireless Powered Relay Networks With Cyclical NOMA-TDMA. IEEE Wirel. Commun. Lett. 2020, 9, 2088–2092. [Google Scholar] [CrossRef]
- He, Y.; Wang, D.; Huang, F.; Zhang, R.; Pan, J. Trajectory optimization and channel allocation for delay sensitive secure transmission in UAV-relayed VANETs. IEEE Trans. Veh. Technol. 2022, 71, 4512–4517. [Google Scholar] [CrossRef]
- Liu, A.; Lau, V.K.N. Optimization of Multi-UAV-Aided Wireless Networking Over a Ray-Tracing Channel Model. IEEE Trans. Wirel. Commun. 2019, 18, 4518–4530. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).