Abstract
This study investigates covert communication in multi-sensor systems employing Intelligent Reflecting Surfaces (IRSs). Different from previous works, we focus on optimizing transmission amplitudes and phase angles for a 2-BPSK codebook in the presence of asymmetric noise over complex Gaussian channels. We adopt KL divergence as a covertness constraint and mutual information as a metric for transmission rate. We employ Taylor series expansion to approximate KL divergence and mutual information. Leveraging these approximations, we derive optimal phase angles through a proposed gradient descent algorithm. The numerical simulations validate the effectiveness and precision of our Taylor approximation method. Through validation in different scenarios, our algorithm demonstrates robust convergence, deriving all optimal phase angles. Comparing initial phase angles from prior works to those obtained via our algorithm, we observe a higher covert transmission rate.
1. Introduction
In the era of the Internet of Things (IoT), the surge in demand for the transmission of sensor information is witnessing exponential growth [1,2]. Addressing security concerns pertaining to information transmission in multi-sensor environments emerges as a pivotal undertaking [3,4,5]. Traditional encryption methodologies and techniques in physical layer security primarily concentrate on protecting the communication content [6,7]. Nevertheless, the mere protection of communication content no longer suffices to meet contemporary information security requisites [8,9]. To hide the communication behaviors, covert communication, also known as low probability of detection (LPD) communication, was proposed [10].
Extensive research has been conducted on covert communication techniques in military communication, with a focus on methods like spread spectrum and frequency-hopping communication [9,11,12,13]. These techniques aim to conceal the existence of communication from vigilant adversaries. However, the theoretical boundaries of covert communication were initially explored in [14], where the square root law (SRL) in additive white Gaussian noise (AWGN) channels was discovered. This seminal discovery was subsequently expanded to various channel models, encompassing binary symmetric channels [15], discrete memoryless channels [16,17,18], and multi-user channels [19,20,21,22,23], among others.
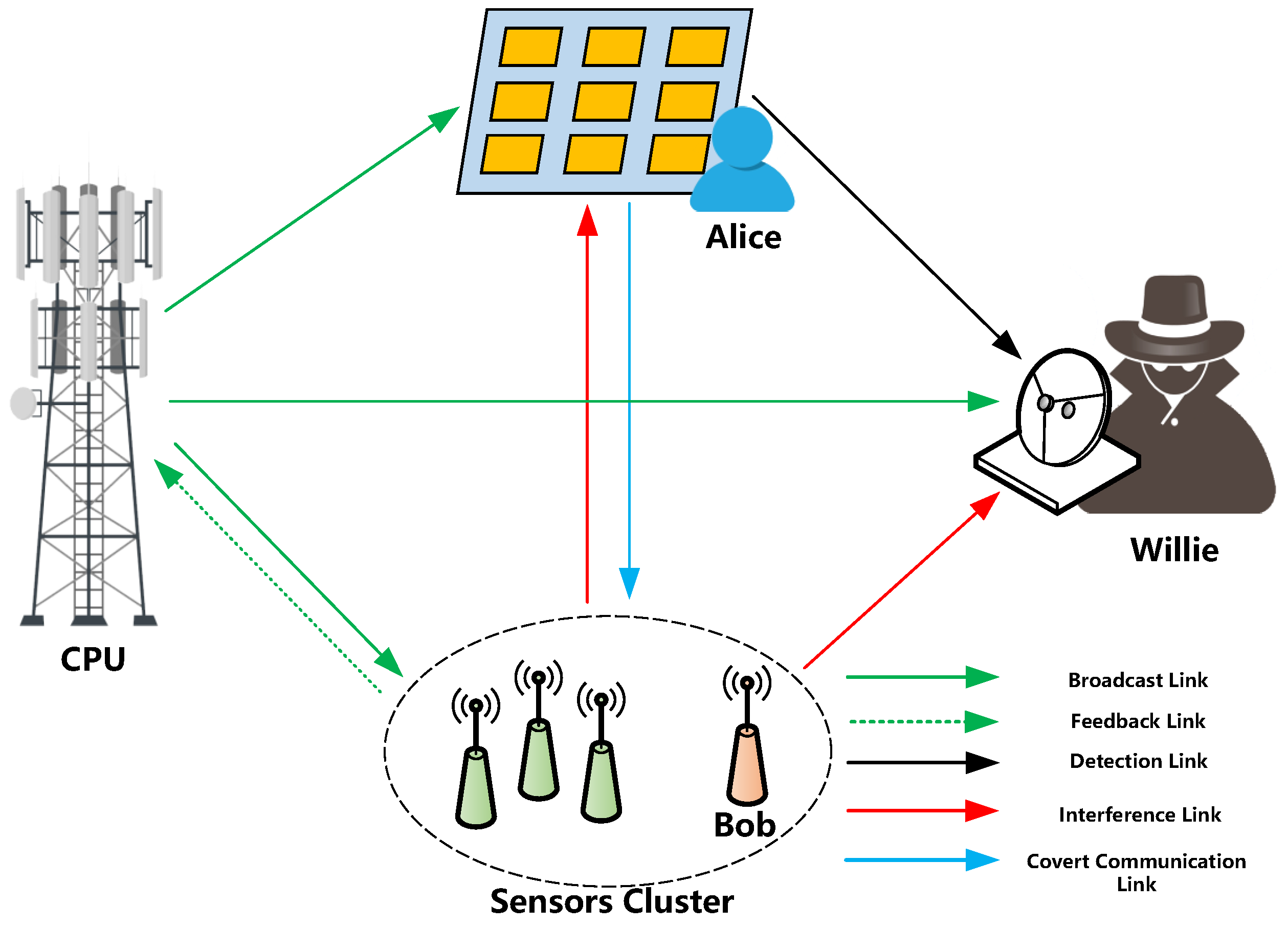
In this work, we investigate IRS-enabled covert communication in multi-sensor systems, comprising a central processing unit (CPU) and a sensor cluster with N independent sensors, as shown in Figure 1. Alice utilizes IRS-reflected signals to covertly access one of the sensors, while Willie, as the detecting entity, aims to ascertain the presence of covert access. To reduce operational complexity and communication costs, Alice employs the 2-BPSK codebook proposed in [8] for covert communication. The main contributions of this paper are summarized as follows:
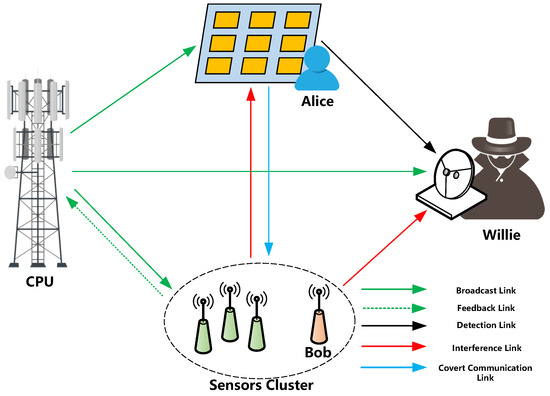
Figure 1.
IRS-enabled covert communication in multi-sensor systems.
- (1)
- We conducted the first theoretical study on IRS-enabled covert communication in multi-sensor systems with a 2-BPSK codebook. We provided closed-form solutions for the KL divergence and mutual information analysis of the target system.
- (2)
- We introduced a gradient descent algorithm, which, when employed, yields optimal initial phase angles for 2-BPSK. This algorithm both ensures covertness and maximizes the transmission rate.
- (3)
- We proposed a physical layer optimization method for IRS-enabled covert communication, transforming the multi-parameter optimization problem of transmission amplitude and phase angles into a phase-angle optimization problem. Based on the optimized phase angles, we obtained the optimal transmission amplitude.
- (4)
- Through experimental simulations, we validated the effectiveness of the proposed gradient descent algorithm. Comparative analysis with traditional phase angle parameters demonstrated that our optimization method achieves a better covert transmission rate under the same covertness constraints.
The subsequent sections of this paper are structured as follows. Section 2 introduces related works. In Section 3, the system model of IRS covert communication in multi-sensor systems is introduced. The achievability and the transmission performance analysis of covert communication are provided in Section 4 and Section 5. In Section 6, the optimization problem is reformulated and a gradient descent optimization algorithm is proposed to solve the problem. Section 7 provides numerical simulations to verify the effectiveness and superiority of our method. Finally, Section 8 provides the discussion and conclusions of this paper.
2. Related Works
In previous works, a myriad of strategies have been presented to enhance the efficacy of covert communication across diverse scenarios. These approaches span a spectrum, including the utilization of relaying networks [24,25], multiple interference networks [26,27], and multi-user networks [28]. Particularly noteworthy is the observation by Lu et al. [29], who recognized the potential of the intelligent reflecting surface, also referred to as the reconfigurable intelligent surface (RIS), in amplifying the received signal at the intended receiver while concurrently attenuating the signal at potential eavesdroppers. In their system model, Alice covertly transmits messages by either reflecting her signal to Bob or introducing additional noise to confuse potential eavesdroppers through IRS devices. Recent studies [30,31,32] have built upon this foundation, demonstrating that exploiting uncertainty about noise can effectively enhance covert performance in IRS covert communication. Furthermore, research has delved into the optimization of transmission power and reflection beamforming in IRS networks [30,33,34,35,36,37]. Additionally, covert communication within Unmanned-Aerial-Vehicle-mounted IRS (UIRS) communication systems has garnered attention in recent investigations [38,39].
In [40,41], the spectrum and time resources have been adopted to improve the performance of covert communication. Moreover, in [8], the authors have proved that phase resources can also be utilized to enhance the performance of covert communication. They extended IRS covert communication to the complex Gaussian channel and introduced a novel codebook, i.e., the N-BPSK codebook. This codebook is derived from the traditional BPSK codebook, and a simple reflect operation allows obtaining the full phase gain. This gain is crucial as traditional IRS covert communication requires biased reflection operations for each symbol, imposing high hardware demands and increased complexity on the IRS [8].
While their work and findings are significant, their analysis of IRS covert communication is limited to scenarios with symmetric noise, specifically where the noise variances on the real and imaginary axes are equal. However, in multi-sensor scenarios, channel noise is typically asymmetric due to the dispersed positions of sensors and varying signal transmission intervals. The performance boundaries of covert communication under such conditions merit further investigation.
3. System Model
3.1. Communication Scenario and Equivalent Channel
We examine a discrete-time additive white Gaussian noise channel model with complex values, as depicted in Figure 1. The central processing unit (CPU) broadcasts n complex-valued symbols to N sensors, and each sensor, denoted as the k-th sensor, transmits feedback information to the CPU in n complex-valued symbols . To optimize the transmission rate, both the broadcast and feedback signals follow Gaussian distributions, where and . The transmitter, represented by the intelligent reflecting surface (IRS) or Alice, aims to transmit n complex-valued symbols to reach the target sensor, Bob. Meanwhile, the detector, Willie, endeavors to detect any access attempts. All transmission and feedback activities occur within a single time slot. Consequently, the i-th symbol received by Bob and Willie can be expressed as:
where and represent independent and identically distributed (i.i.d.) Gaussian noise components with variances and , respectively. Specifically, and . The channel coefficients from the central processing unit (CPU) to Alice, Bob, and Willie are denoted by , , and , respectively. Additionally, the channel coefficients from Alice to Bob and from Alice to Willie are represented by and , respectively. The channel coefficients from the k-th sensor to Bob and Willie are denoted by and , respectively. For simplicity, we assume that the CPU broadcasts n symbols with a phase angle of zero, and all channel coefficients are universally known. Given the multitude of sensors, Bob and Willie face challenges in demodulating all signals. Consequently, the feedback signals from the sensors are treated as interference. Considering the composition of feedback signals from N sensors, the channel can be equivalently expressed as:
where and with and .
Based on the scenario and actual situation considerations, we assume that Bob and Willie can recover the broadcast information and perform a subtraction operation on their observations to improve transmission performance and detection performance. Then, the i-th symbol received by Bob and Willie can be equivalently rewritten as
3.2. Construction of 2-BPSK Codebook
Alice employs a covert communication strategy with Bob by manipulating the reflection coefficient of the IRS, adjusting both its amplitude and phase. Alice transmits a message W uniformly distributed in the range to Bob by encoding it into a codeword with a blocklength of n. In this work, we adopt the 2-BPSK codebook, proposed in [8], instead of the conventional Gaussian codebook or BPSK codebook. To construct the 2-BPSK codebook, we need to construct a BPSK codebook first.
In the BPSK codebook, each symbol exhibits a consistent amplitude and two potential phases, denoted as and . Specifically, the expression for each symbol can be either or . The codeword is independently and randomly generated based on the distribution , where . The 2-BPSK codebook is constructed by reflecting the BPSK codebook. By introducing a fixed phase angle to each symbol , Alice can create another BPSK codebook with varying phase angles. In other words, Alice transmits each codeword in BPSK with an additional phase angle , and each symbol can be expressed as either or . For the sake of simplicity in notation, we redefine the symbols and as and .
Assuming that Alice may optionally append an additional phase angle or choose not to perform this operation, we can obtain two independent BPSK codebooks. By combining these two codebooks, we can construct a 2-BPSK codebook. In the 2-BPSK codebook, each codeword can be represented as either and or and , where . It is assumed that the codebook is revealed to Willie, including the value of amplitude gain and the set of all possible angles, i.e., .
3.3. Transmission Scheme
By employing random coding generation of the 2-BPSK codebook, Alice encodes a message W into a codeword or , where and with . For the i-th symbol, its amplitude is independently selected from and its phase angle is independently selected from equiprobably [8,42]. The codeword is generated independently and identically distributed according to the following probability distribution:
Then, the mutual information can be expressed as
where denotes the discrete input and denotes the channel output. Combined with the construction o the 2-BPSK codebook, the mutual information in (8) can be expressed as
3.4. Hypothesis Test
In the analysis of a quasi-static flat fading channel characterized by coefficients and , the anticipated amplitude of the complex-value is denoted as A, and the expected phase angle is represented as . The determination of Alice’s communication activity involves Willie conducting a binary hypothesis test [43] based on a sequence of n observations . Specifically, the null hypothesis () and alternative hypothesis () are formulated as:
Let (resp. ) denote the probability distribution of Willie’s n observations when (resp. ) is true. Willie has knowledge of the distributions and and can conduct an optimal statistical hypothesis test such that the sum of the probability of missed detection and the probability of false alarm has a lower bound, which is given by
where represents the KL divergence between and . The objective of covert communication is to ensure the KL divergence is negligible, i.e., guaranteeing
where is an arbitrarily small value within the range (0,1).
Given the non-uniform distribution of sensors in the target scenario, the noise generated in the complex Gaussian channel is asymmetric, i.e., and . Willie possesses knowledge regarding the construction of the codebook 2-BPSK and channel coefficient from Alice to Willie. The probability distributions of under and are given by
where , and represent the variances of the Gaussian noise at Willie on the x-axis and y-axis.
3.5. Problem Formulation and Optimization Method Proposed
In this work, we aim to maximize the transmission rate in (9) while satisfying the covertness constraint in (13). To alleviate the complexity and burden associated with IRS covert communication, we employ the 2-BPSK codebook proposed in [8] instead of the Gaussian codebook or the BPSK codebook. Alice randomly selected either sub-codebook from the 2-BPSK codebook for communication. To maximize the transmission rate, optimization is performed on the transmission amplitudes and phase angles of the two sub-codebooks, i.e., and . The problem in this work can be formulated as:
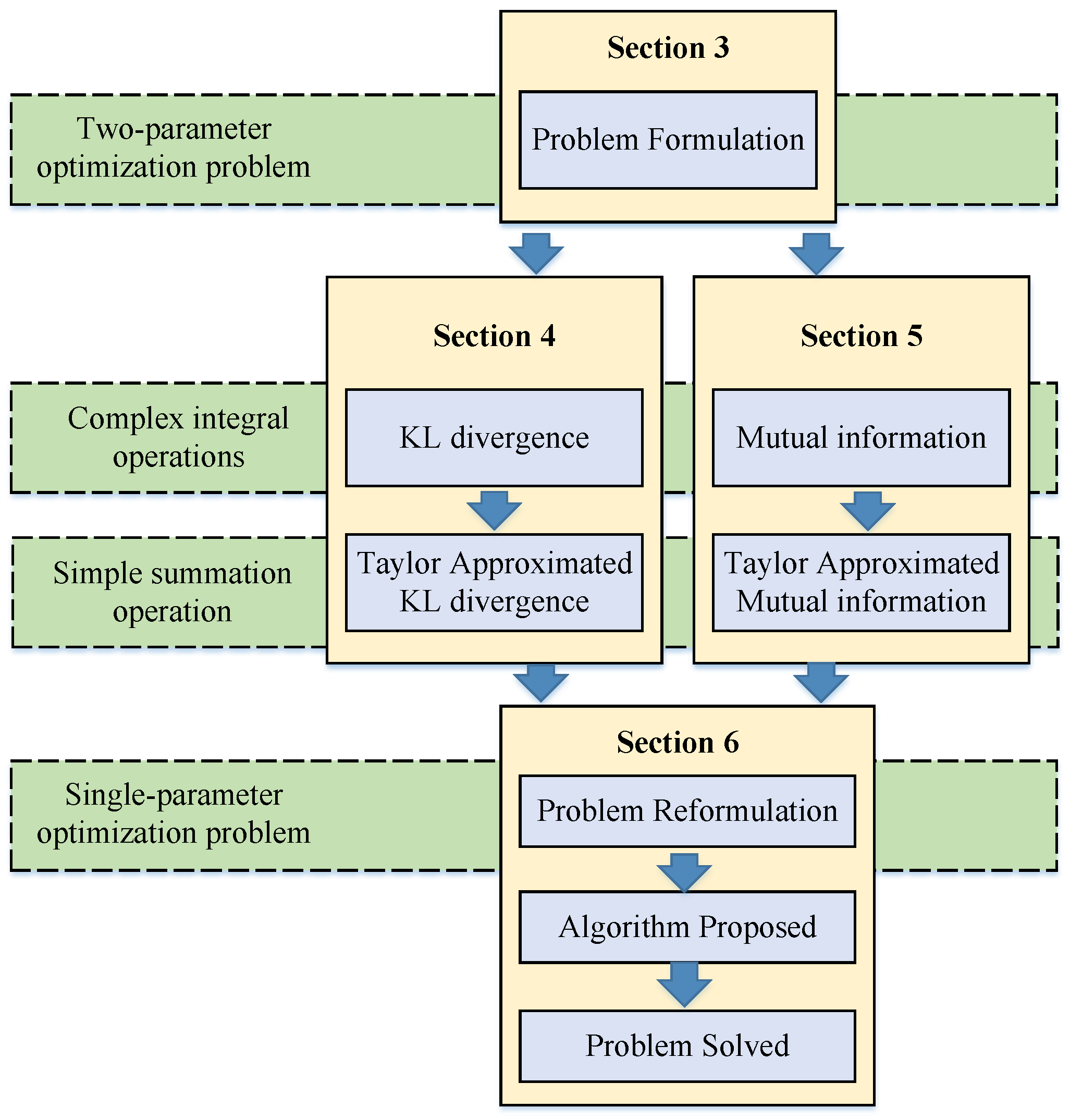
To solve the problem P1, we adopted an optimization approach different from previous works, as illustrated in Figure 2. In Section 3, we formulated this problem, which is a two-parameter optimization problem. We decomposed the problem into scaling the optimization objective (16) and constraints (17) and approximated mutual information and KL divergence in Section 4 and Section 5. In Section 4, we approximated KL divergence using a Taylor series expansion method, transforming the complex integration process for computing KL divergence into a summation. Similarly, in Section 5, we approximated mutual information using a Taylor series expansion method, converting the intricate integration process for computing mutual information into a summation. In Section 6, we integrated the approximated optimization objective mutual information and the constraint KL divergence, reformulating the problem into P2. Then, we proposed a gradient descent optimization algorithm with random initialization to solve problem P2. Finally, by combining the optimal results from P2, the original problem P1 can be completely resolved.
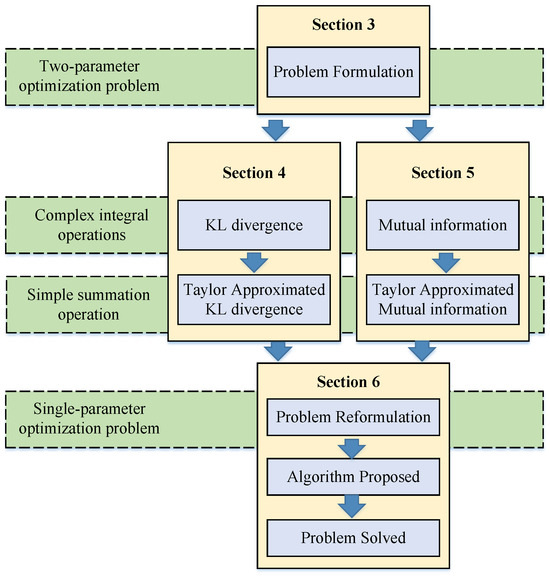
Figure 2.
Optimization methodology diagram in this work.
4. Achievability Analysis of 2-BPSK Codebook at Willie
According to the definition of the KL divergence, we have
where
It is worth noting that is the sum of two n-letter product distributions, not an n-letter product distribution. Thus, we cannot adopt the chain rule like some previous works [10,42,44,45]. We use a Taylor series expansion of to approximate it, which has been adopted in [8].
Let us define . Following from Taylor series expansion, when , we have the fact:
We can calculate the first term as
With some transformation, the term can be expressed as
Then, we can calculate the term as
Finally, we re-arrange the third term as:
With some calculation, we can obtain as follows:
5. Performance Analysis of the Covert Transmission
In (9), we have rewritten the mutual information as
Following from the chain rule, the mutual information can be expressed as
For or , we have
with
where and represent noise variances at Bob on the x-axis and y-axis, and is the phase difference value between and .
Performing Taylor expansion, we have
and
With some calculations, we can obtain
Then, we can obtain the mutual information as
6. Problem Reformulation
In Section 4 and Section 5, we derive KL divergence and mutual information in our problem. Combined with (17) and (43), the covertness constraint can be expressed as
where
Then, we can obtain the maximum amplitude gain as
Then, we define the objective function as . To solve the problem (64), we adopted a gradient descent optimization algorithm with random initialization; the details are summarized in Algorithm 1.
In Algorithm 1, the final output represents the ultimate transmission rate, while the outputs and denote the optimal values for the phase angles. Combined with the outputs and and (61), we can obtain the optimal amplitude gain as .
| Algorithm 1 Gradient Descent Optimization Algorithm with Random Initialization |
|
7. Numerical Results
In this section, we first consider scenarios characterized by noise symmetry along the x and y axes. Leveraging theoretical results from the referenced paper [8], we validate the efficacy of our proposed KL divergence and mutual information approximation methods. After establishing the accuracy of our approximation results, we proceed to validate the algorithm in two distinct scenarios utilizing our proposed approximation methods. We assess whether the gradient descent algorithm, as articulated, successfully converges to optimal angles and . Finally, through a comprehensive exploration of all angles in the target scenarios, we confirm the efficacy and superiority of our proposed algorithm.
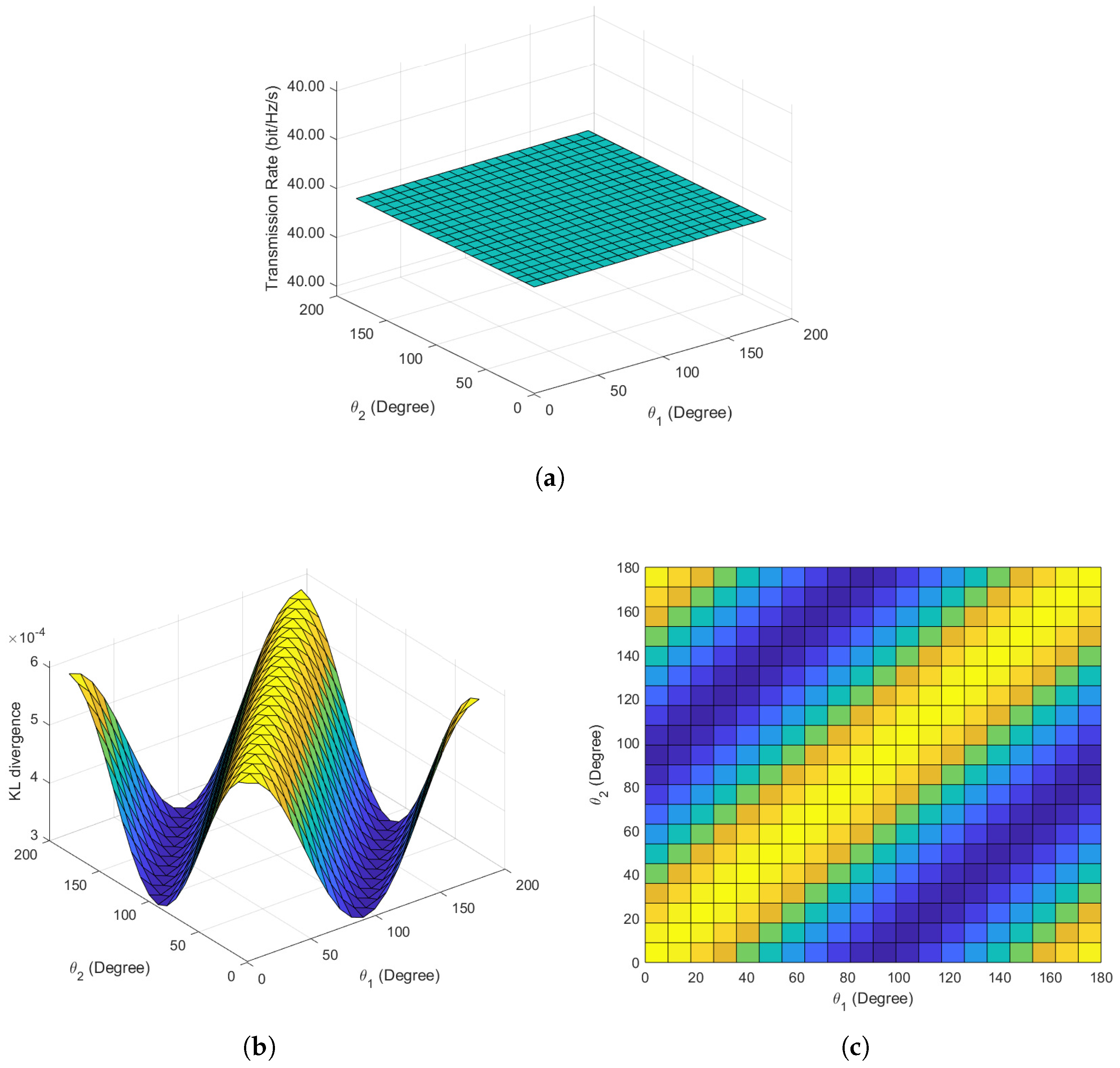
Figure 3 illustrates the simulation results for scenario 1, with specific parameters detailed in Table 1. As depicted in Figure 3a, under common conditions of noise symmetry along the x and y axes, the mutual information remains constant at 40 bit/Hz/s as the phase angles and vary. This observation aligns with the theorem in [8], indicating that altering the initial phase angles does not affect the transmission rate when the variances of noise along the x-axes and y-axes are equal. This result validates the correctness and effectiveness of our approximation for mutual information.
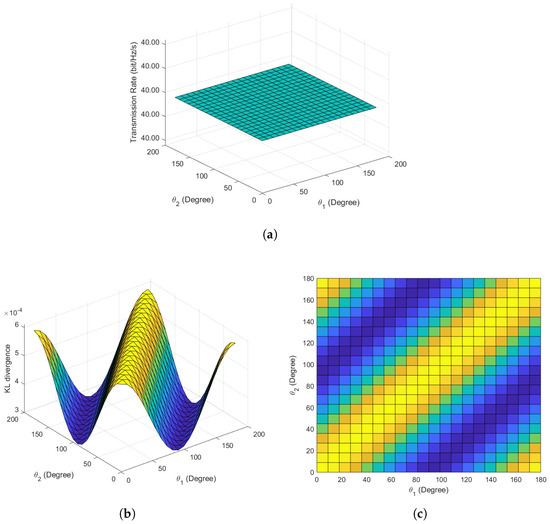
Figure 3.
Covert communication performance in scenario 1. (a) Mutual information versus phase angles. (b) Main view of KL divergence versus phase angles. (c) Top view of KL divergence versus phase angles.

Table 1.
Parameters for comparative experiments.
Figure 3b,c provide the main view and top view of the KL divergence concerning the variation of phase angles and . As illustrated, the KL divergence reaches its maximum when equals (i.e., ), indicating the poorest covertness performance. Conversely, the KL divergence achieves its minimum when and have a 90-degree separation (i.e., ), representing optimal covertness performance. For example, the simulation reveals that the minimum KL divergence occurs at and . This finding aligns with the conclusion in [8] that, under equal x-axis and y-axis noise variances, the optimal angle for 2-BPSK is 90 degrees. At , the KL divergence is , while at , the KL divergence is , showing a halving of the KL divergence, consistent with the results in [8]. Therefore, the simulation results validate the effectiveness and accuracy of our proposed approximation method, serving as a basis for further validation of our optimization strategy based on this approximation method.
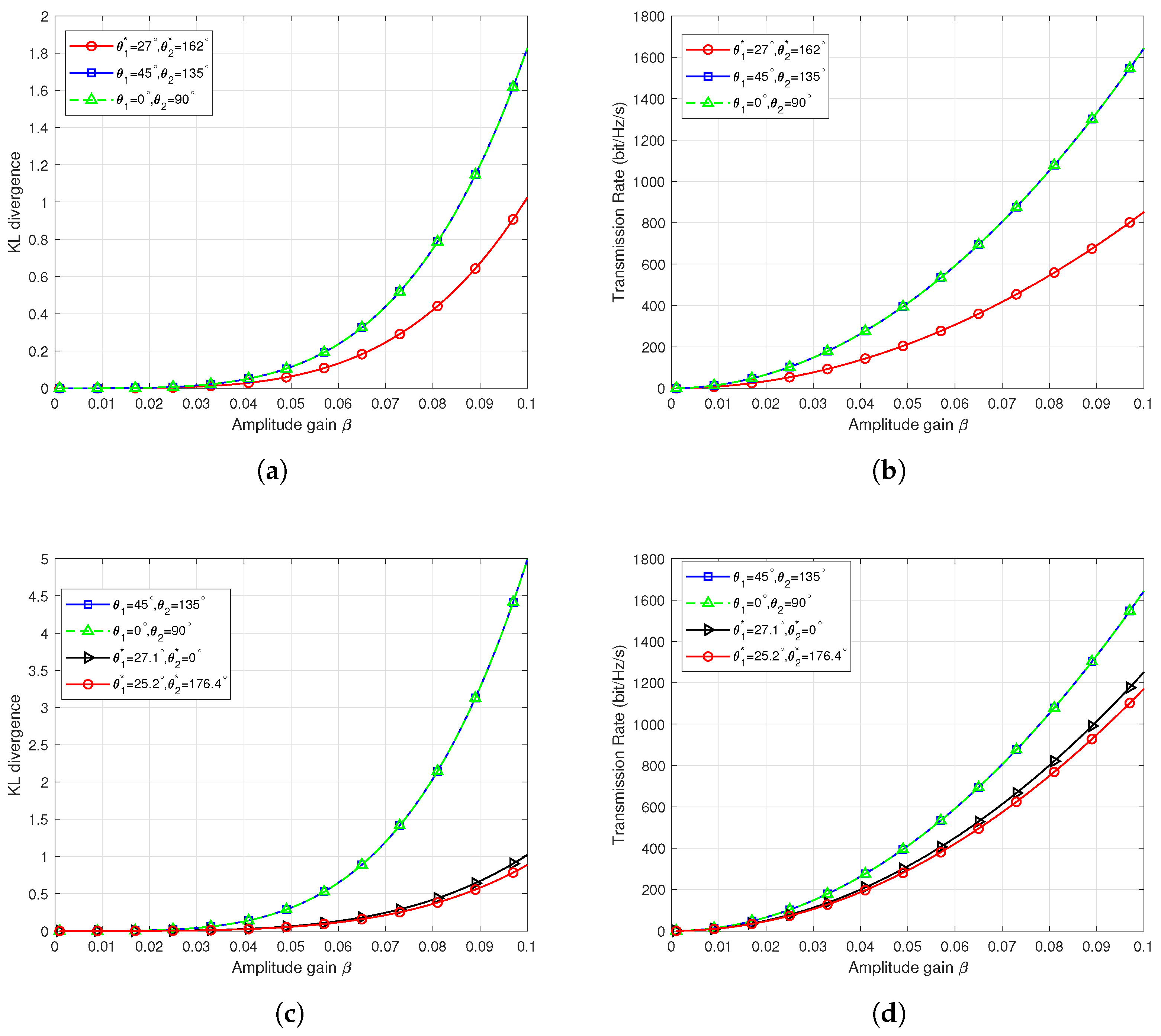
Figure 4 presents the results of covert communication performance versus amplitude gain for scenarios 2 and 3, with specific simulation parameters and optimization outcomes detailed in Table 1. For performance comparison, we conducted experiments using phase angles adopted in [8,10], specifically, , and , .
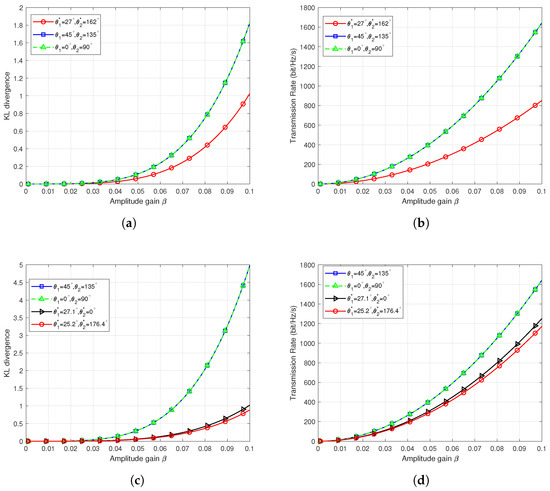
Figure 4.
Covert communication performance in different scenarios. (a) KL divergence versus amplitude gain in scenario 2. (b) Transmission rate versus amplitude gain in scenario 2. (c) KL divergence versus amplitude gain in scenario 3. (d) Transmission rate versus amplitude gain in scenario 3.
Figure 4a,b depict the KL divergence versus amplitude gain and the transmission rate versus amplitude gain in scenario 2. As shown, based on our proposed gradient descent algorithm, the optimal covertness performance can be achieved under the same amplitude at and . However, at and , the transmission rate is lower than the two comparative results. Figure 4c,d illustrate the KL divergence versus transmission amplitude and the transmission rate versus transmission amplitude in scenario 3. In scenario 3, the phase angle difference is 20 degrees, and based on our proposed gradient descent algorithm, optimal covertness performance can be achieved at and . However, at , or , , the transmission rate is lower than the two comparative results. To further compare the effectiveness of the optimization results, a re-evaluation is needed under the same covert communication constraint .
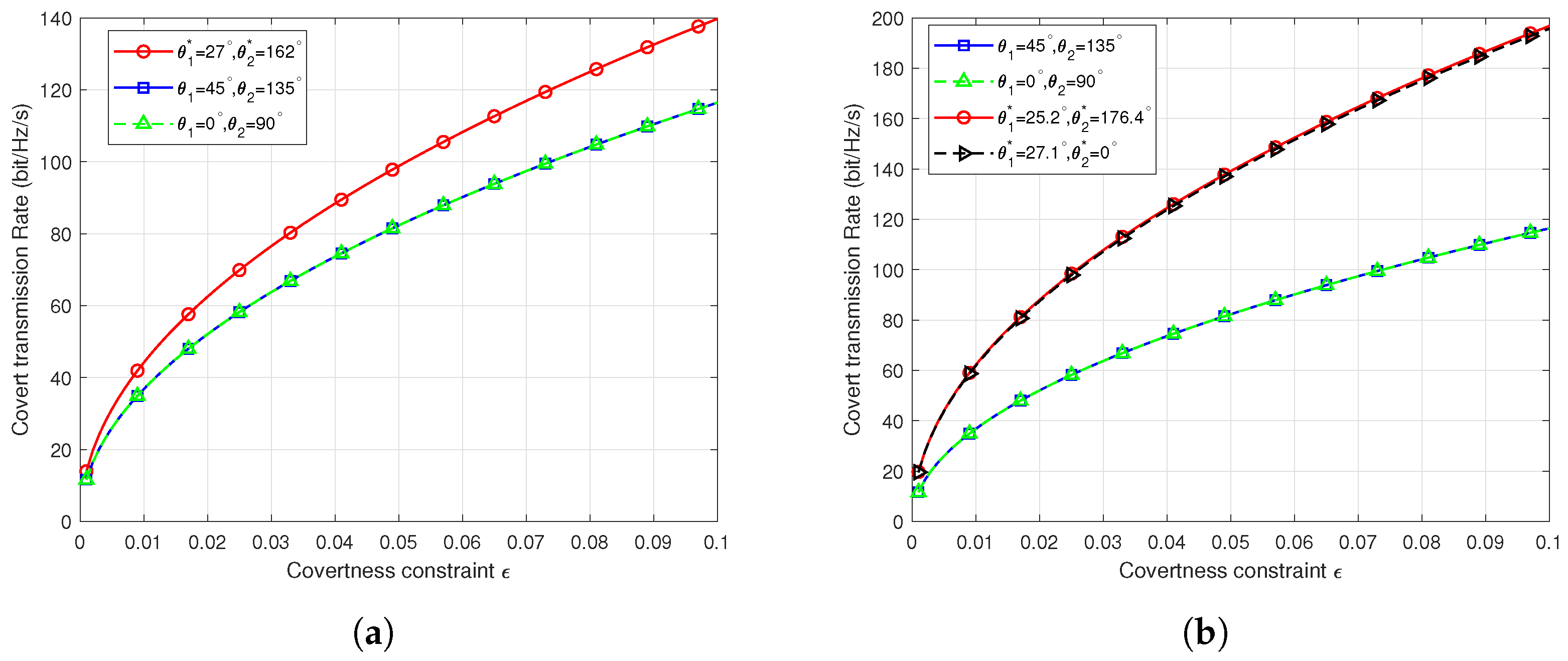
Figure 5 illustrates the covert transmission rate versus the covert constraint in scenarios 2 and 3. As depicted in Figure 5a, in scenario 1, leveraging our proposed gradient descent algorithm, the covert transmission rate is maximized at and under the same covert constraint . In scenario 2, although the transmission rate is not maximized at and for the same transmission amplitude, considering the covert constraint, this phase angle pair is optimal. For Scenario 3, our algorithm yields two optimal phase configurations: , and , . As shown in Figure 5b, both optimal configurations yield the same covert transmission rate under the same covert constraint, confirming their optimality in scenario 3. To further validate the effectiveness of the algorithm, we exhaustively traverse all phase angle options to verify if the algorithm obtains all optimal results.
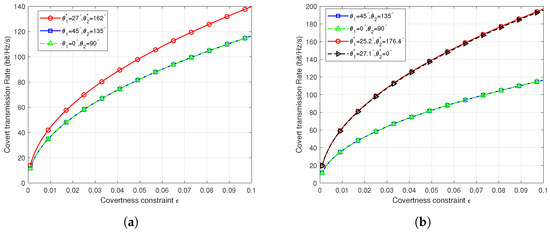
Figure 5.
Covert transmission performance in different scenarios. (a) Covert transmission rate versus covertness constraint in scenario 2. (b) Covert transmission rate versus covertness constraint in scenario 3.
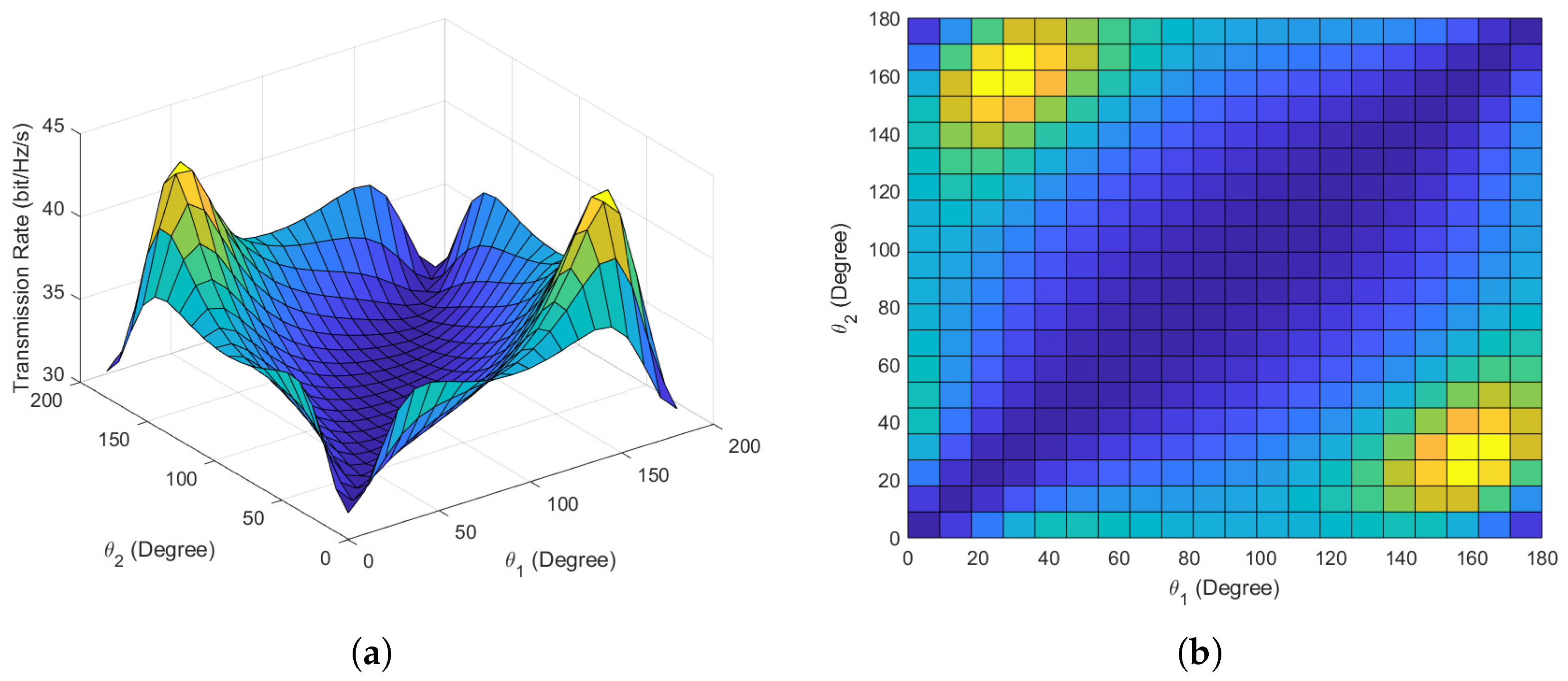
Figure 6a,b present the main and top views of the maximum covert transmission rate versus the phase angles and variations in scenario 2. In Figure 6, it is evident that there are two options for achieving the maximum covert transmission rate. Considering the symmetry of phase angles, our proposed algorithm has successfully identified all optimal phase angle options, validating the convergence and effectiveness of the algorithm. When employing conventional phase angles for covert communication, namely, at the moments when and , the covert transmission rate is 35 bits/Hz/s. However, after optimization, the maximum covert rate reaches 45 bits/Hz/s, representing a nearly increase in the transmission rate, which is a substantial improvement.
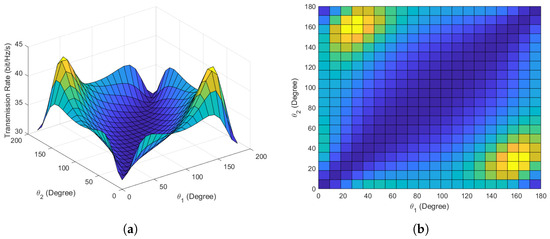
Figure 6.
Covert communication performance in scenario 2. (a) Main view of covert transmission rate versus phase angles. (b) Top view of covert transmission rate versus phase angles.
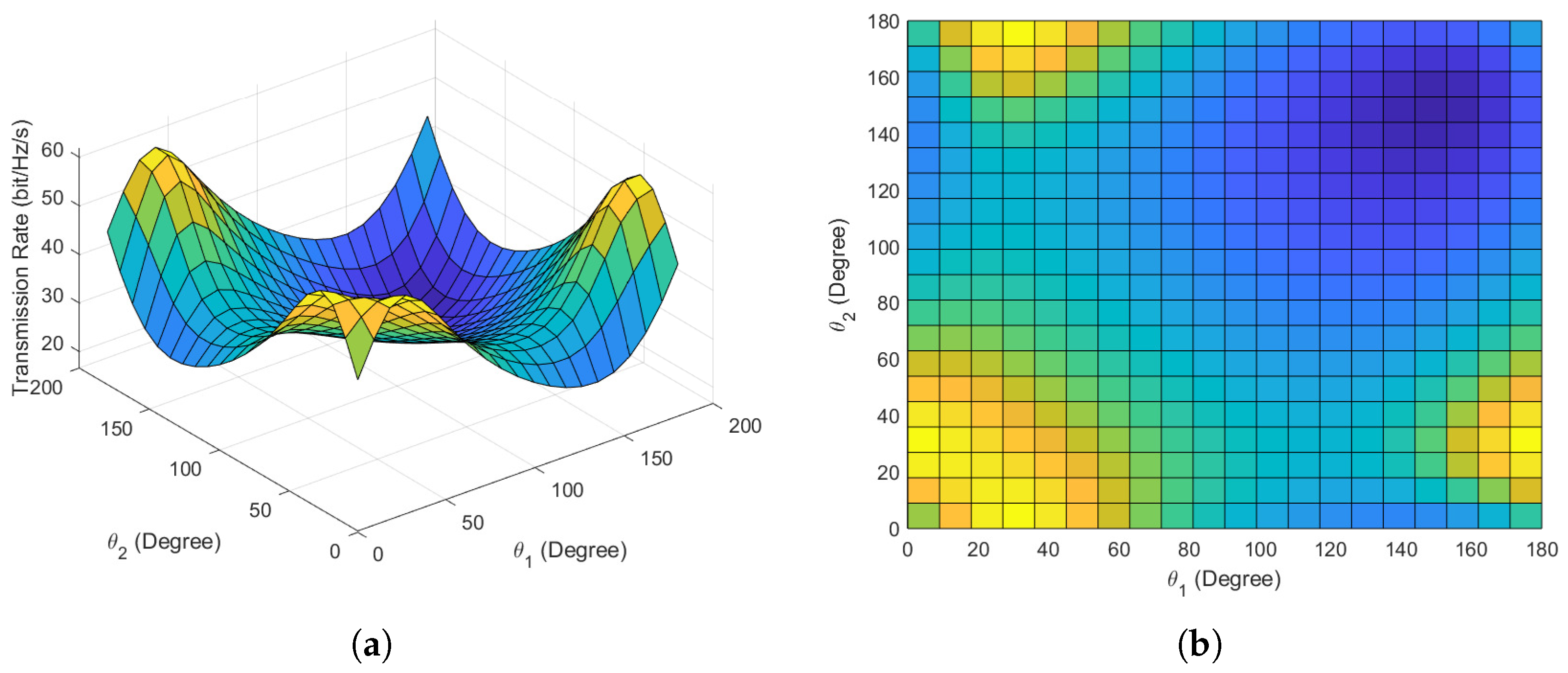
Figure 7a,b depict the main and top views of the maximum covert transmission rate versus the phase angles and variations in scenario 3. It can be observed that there are four options for achieving the maximum covert transmission rate, reduced to two when considering the symmetry of phase angles. Through multiple random initializations, the proposed algorithm effectively converges and identifies all optimal phase angle pairs. The validity and convergence of the proposed algorithm have been thoroughly validated through the numerical simulations mentioned above. When employing conventional phase angles for covert communication, i.e., and , the covert transmission rate is 40 bits/Hz/s. After optimization, the maximum covert rate achieves 60 bits/Hz/s, indicating an almost increase in the transmission rate, which is a significant enhancement.
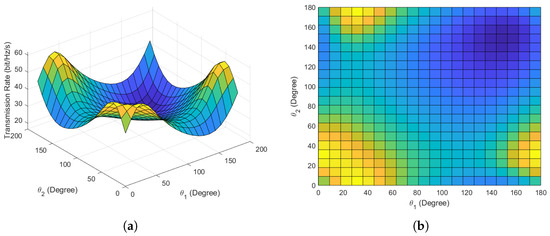
Figure 7.
Covert communication performance in scenario 3. (a) Main view of covert transmission rate versus phase angles. (b) Top view of covert transmission rate versus phase angles.
8. Discussion and Conclusions
In this work, we investigated covert communication in multi-sensor systems employing intelligent reflecting surfaces. Diverging from prior works, we examined the optimization of transmission amplitudes and optimal phase angles for a 2-BPSK codebook under the condition of asymmetric noise over complex Gaussian channels. We employed KL divergence as a metric for the covertness constraint and mutual information as a metric for the transmission rate. We approximated KL divergence and mutual information with Taylor series expansion. Leveraging the approximated KL divergence and mutual information, we solved for the optimal phase angles. Specifically, we proposed a gradient descent algorithm to obtain all optimal phase angles. Based on the optimal phase angles, we could achieve the optimal transmission amplitude gain. With numerical simulations, we verified the effectiveness and precision of our adopted Taylor approximation method. Validating our algorithm across two distinct scenarios, we demonstrated its robust convergence and capability to derive all optimal phase angles. Comparing the initial phase angles from existing works to the optimal phase angles obtained via the gradient descent algorithm, we observed a higher covert transmission rate.
In previous covert communication studies, along with the optimization of transmission power, phase angles change. However, phase angles are rarely considered as an independent optimization parameter. In this work, we employ a 2-BPSK codebook and optimize the phase angles. Simulation results demonstrate that by solely optimizing the phase angles, a significant enhancement in covert transmission rates can be achieved. In scenarios 2 and 3, the improvement in covert transmission rates is 30% and 50%, respectively. Unlike traditional IRS covert communication, the 2-BPSK codebook we utilize offers greater feasibility, requiring no intricate flipping operations to achieve substantial enhancements in IRS covert communication rates. In future work, we plan to extend the codebook to an N-BPSK codebook and optimize all initial phase angles.
Author Contributions
Conceptualization, H.F. and X.J.; methodology, H.F. and R.Z.; software, H.F. and R.Z.; validation, H.F. and X.J.; writing—original draft preparation, H.F. and R.Z.; writing—review and editing, X.H. and S.Q.; visualization, X.H. and S.Q.; supervision, S.Q. and X.J.; funding acquisition, X.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant numbers U1836104, 61801073, 61931004, 62072250; the National Key Research and Development Program of China, grant number 2021QY0700; and the Startup Foundation for Introducing Talent of NUIST, grant number 2021r039.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| IRS | Intelligent Reflecting Surface |
| UAV | Unmanned Aerial Vehicle (UAV) |
| BPSK | Binary Phase-Shift Keying |
| AWGN | Additive White Gaussian Noise |
| RIS | Reconfigurable Intelligent Surface |
| LPD | Low Probability of Detection |
References
- Liu, Z.; Liu, J.; Zeng, Y.; Ma, J. Covert wireless communication in IoT network: From AWGN channel to THz band. IEEE Internet Things J. 2020, 7, 3378–3388. [Google Scholar] [CrossRef]
- Gao, C.; Yang, B.; Jiang, X.; Inamura, H.; Fukushi, M. Covert Communication in Relay-Assisted IoT Systems. IEEE Internet Things J. 2021, 8, 6313–6323. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, L.D. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics. IEEE Internet Things J. 2019, 6, 2103–2115. [Google Scholar] [CrossRef]
- Miao, Y.; Liu, X.; Choo, K.K.R.; Deng, R.H.; Wu, H.; Li, H. Fair and Dynamic Data Sharing Framework in Cloud-Assisted Internet of Everything. IEEE Internet Things J. 2019, 6, 7201–7212. [Google Scholar] [CrossRef]
- Wu, Z.; Liu, R.; Shuai, H.; Zhu, S.; Li, C. Covert performance for integrated satellite multiple terrestrial relay networks with partial relay selection. Sensors 2022, 22, 5524. [Google Scholar] [CrossRef] [PubMed]
- Moon, J. Performance Comparison of Relay-Based Covert Communications: DF, CF and AF. Sensors 2023, 23, 8747. [Google Scholar] [CrossRef] [PubMed]
- Qiao, S.; Cao, D.; Zhang, Q.; Xu, Y.; Liu, G. Covert Communication Gains From Adversary’s Uncertainty of Phase Angles. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2899–2912. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D.; Guha, S. Hiding information in noise: Fundamental limits of covert wireless communication. IEEE Commun. Mag. 2015, 53, 26–31. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D. Limits of Reliable Communication with Low Probability of Detection on AWGN Channels. IEEE J. Sel. Areas Commun. 2013, 31, 1921–1930. [Google Scholar] [CrossRef]
- Marvin, S.; Jim, O.; Robert, S.; Barry, L. Spread Spectrum Communications Handbook, Electronic Edition, 1st ed.; McGraw-Hill Education: New York, NY, USA, 2002. [Google Scholar]
- Çek, M.E.; Savaci, F. Stable non-Gaussian noise parameter modulation in digital communication. Electron. Lett. 2009, 45, 1256–1257. [Google Scholar] [CrossRef]
- Chen, X.; An, J.; Xiong, Z.; Xing, C.; Zhao, N.; Yu, F.R.; Nallanathan, A. Covert Communications: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2023, 25, 1173–1198. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D. Square root law for communication with low probability of detection on AWGN channels. In Proceedings of the 2012 IEEE International Symposium on Information Theory Proceedings, Cambridge, MA, USA, 1–6 July 2012; pp. 448–452. [Google Scholar]
- Che, P.H.; Bakshi, M.; Jaggi, S. Reliable deniable communication: Hiding messages in noise. In Proceedings of the 2013 IEEE International Symposium on Information Theory, Istanbul, Turkey, 7–12 July 2013; pp. 2945–2949. [Google Scholar]
- Wang, L.; Wornell, G.W.; Zheng, L. Fundamental limits of communication with low probability of detection. IEEE Trans. Inf. Theory 2016, 62, 3493–3503. [Google Scholar] [CrossRef]
- Tahmasbi, M.; Bloch, M.R. First- and Second-Order Asymptotics in Covert Communication. IEEE Trans. Inf. Theory 2019, 65, 2190–2212. [Google Scholar] [CrossRef]
- Bloch, M.R. Covert communication over noisy channels: A resolvability perspective. IEEE Trans. Inf. Theory 2016, 62, 2334–2354. [Google Scholar] [CrossRef]
- Arumugam, K.S.K.; Bloch, M.R. Covert Communication Over a K-User Multiple-Access Channel. IEEE Trans. Inf. Theory 2019, 65, 7020–7044. [Google Scholar] [CrossRef]
- Kumar Arumugam, K.S.; Bloch, M.R. Embedding Covert Information in Broadcast Communications. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2787–2801. [Google Scholar] [CrossRef]
- Cho, K.H.; Lee, S.H. Treating Interference as Noise Is Optimal for Covert Communication Over Interference Channels. IEEE Trans. Inf. Forensics Secur. 2021, 16, 322–332. [Google Scholar] [CrossRef]
- Kibloff, D.; Perlaza, S.M.; Wang, L. Embedding Covert Information on a Given Broadcast Code. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Paris, France, 7–12 July 2019; pp. 2169–2173. [Google Scholar] [CrossRef]
- Tan, V.Y.F.; Lee, S.H. Time-Division is Optimal for Covert Communication Over Some Broadcast Channels. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1377–1389. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Zhou, X.; Shu, F.; Li, J.; Wang, J. Covert Communication Achieved by a Greedy Relay in Wireless Networks. IEEE Trans. Wirel. Commun. 2018, 17, 4766–4779. [Google Scholar] [CrossRef]
- Forouzesh, M.; Azmi, P.; Kuhestani, A.; Yeoh, P.L. Covert Communication and Secure Transmission Over Untrusted Relaying Networks in the Presence of Multiple Wardens. IEEE Trans. Commun. 2020, 68, 3737–3749. [Google Scholar] [CrossRef]
- He, B.; Yan, S.; Zhou, X.; Jafarkhani, H. Covert Wireless Communication With a Poisson Field of Interferers. IEEE Trans. Wirel. Commun. 2018, 17, 6005–6017. [Google Scholar] [CrossRef]
- Zheng, T.X.; Wang, H.M.; Ng, D.W.K.; Yuan, J. Multi-Antenna Covert Communications in Random Wireless Networks. IEEE Trans. Wirel. Commun. 2019, 18, 1974–1987. [Google Scholar] [CrossRef]
- Huang, K.W.; Deng, H.; Wang, H.M. Jamming Aided Covert Communication With Multiple Receivers. IEEE Trans. Wirel. Commun. 2021, 20, 4480–4494. [Google Scholar] [CrossRef]
- Lu, X.; Hossain, E.; Shafique, T.; Feng, S.; Jiang, H.; Niyato, D. Intelligent Reflecting Surface Enabled Covert Communications in Wireless Networks. IEEE Netw. 2020, 34, 148–155. [Google Scholar] [CrossRef]
- Wang, Y.; Yan, S.; Yang, W.; Huang, Y.; Liu, C. Energy-Efficient Covert Communications for Bistatic Backscatter Systems. IEEE Trans. Veh. Commun. 2021, 70, 2906–2911. [Google Scholar] [CrossRef]
- Liu, J.; Yu, J.; Chen, X.; Zhang, R.; Wang, S.; An, J. Covert Communication in Ambient Backscatter Systems With Uncontrollable RF Source. IEEE Trans. Commun. 2022, 70, 1971–1983. [Google Scholar] [CrossRef]
- Ma, W.; Niu, Z.; Wang, W.; He, S.; Jiang, T. Covert Communication With Uninformed Backscatters in Hybrid Active/Passive Wireless Networks: Modeling and Performance Analysis. IEEE Trans. Commun. 2022, 70, 2622–2634. [Google Scholar] [CrossRef]
- Wu, C.; Yan, S.; Zhou, X.; Chen, R.; Sun, J. Intelligent Reflecting Surface (IRS)-Aided Covert Communication With Warden’s Statistical CSI. IEEE Wirel. Commun. Lett. 2021, 10, 1449–1453. [Google Scholar] [CrossRef]
- Lv, L.; Wu, Q.; Li, Z.; Ding, Z.; Al-Dhahir, N.; Chen, J. Covert Communication in Intelligent Reflecting Surface-Assisted NOMA Systems: Design, Analysis, and Optimization. IEEE Trans. Wirel. Commun. 2022, 21, 1735–1750. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network via Joint Active and Passive Beamforming. IEEE Trans. Wirel. Commun. 2019, 18, 5394–5409. [Google Scholar] [CrossRef]
- Si, J.; Li, Z.; Zhao, Y.; Cheng, J.; Guan, L.; Shi, J.; Al-Dhahir, N. Covert Transmission Assisted by Intelligent Reflecting Surface. IEEE Trans. Commun. 2021, 69, 5394–5408. [Google Scholar] [CrossRef]
- Zhou, X.; Yan, S.; Wu, Q.; Shu, F.; Kwan Ng, D.W. Joint Transmit Power and Reflection Beamforming Design for IRS-Aided Covert Communications. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Tatar Mamaghani, M.; Hong, Y. Aerial Intelligent Reflecting Surface-Enabled Terahertz Covert Communications in Beyond-5G Internet of Things. IEEE Internet Things J. 2022, 9, 19012–19033. [Google Scholar] [CrossRef]
- Wang, C.; Chen, X.; An, J.; Xiong, Z.; Xing, C.; Zhao, N.; Niyato, D. Covert Communication Assisted by UAV-IRS. IEEE Trans. Commun. 2023, 71, 357–369. [Google Scholar] [CrossRef]
- Wang, S.Y.; Bloch, M.R. Covert MIMO Communications Under Variational Distance Constraint. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4605–4620. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D. Covert communication gains from adversary’s ignorance of transmission time. IEEE Trans. Wirel. Commun. 2016, 15, 8394–8405. [Google Scholar] [CrossRef]
- Chen, W.; Ding, H.; Wang, S.; Gong, F. On the limits of covert ambient backscatter communications. IEEE Wirel. Commun. Lett. 2021, 11, 308–312. [Google Scholar] [CrossRef]
- Lehmann, E.L.; Romano, J.P.; Casella, G. Testing Statistical Hypotheses; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3. [Google Scholar]
- Yan, S.; Cong, Y.; Hanly, S.V.; Zhou, X. Gaussian Signalling for Covert Communications. IEEE Trans. Wirel. Commun. 2019, 18, 3542–3553. [Google Scholar] [CrossRef]
- Yan, S.; He, B.; Zhou, X.; Cong, Y.; Swindlehurst, A.L. Delay-Intolerant Covert Communications With Either Fixed or Random Transmit Power. IEEE Trans. Inf. Forensics Secur. 2019, 14, 129–140. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).