Abstract
In recent years, fog-based vehicular ad hoc networks (VANETs) have become a hot research topic. Due to the inherent insecurity of open wireless channels between vehicles and fog nodes, establishing session keys through authenticated key agreement (AKA) protocols is critically important for securing communications. However, existing AKA schemes face several critical challenges: (1) When a large number of vehicles initiate AKA requests within a short time window, existing schemes that process requests one by one individually incur severe signaling congestion, resulting in significant quality of service degradation. (2) Many AKA schemes incur excessive computational and communication overheads due to the adoption of computationally intensive cryptographic primitives (e.g., bilinear pairings and scalar multiplications on elliptic curve groups) and unreasonable design choices, making them unsuitable for the low-latency requirements of VANETs. To address these issues, we propose a lightweight batch AKA scheme based on fog computing. In our scheme, when a group of vehicles requests AKA sessions with the same fog node within the set time interval, the fog node aggregates these requests and, with assistance from the traffic control center, establishes session keys for all vehicles by a round of operations. It has significantly reduced the operational complexity of the entire system. Moreover, our scheme employs Lagrange interpolation and lightweight cryptographic tools, thereby significantly reducing both computational and communication overheads. Additionally, our scheme supports conditional privacy preservation and includes a revocation mechanism for malicious vehicles. Security analysis demonstrates that the proposed scheme meets the security and privacy requirements of VANETs. Performance evaluation indicates that our scheme outperforms existing state-of-the-art solutions in terms of efficiency.
1. Introduction
With the rapid proliferation of private vehicles and increasingly complex road traffic networks, traffic management faces significant challenges, resulting in frequent accidents and substantial losses of life and property. Meanwhile, modern vehicles have transcended their traditional role as mere transportation tools, evolving into mobile intelligent spaces that integrate travel, leisure, entertainment, and work functions. These factors collectively highlight the critical importance of establishing an intelligent traffic management platform. In recent years, the swift advancement of information technology has positioned vehicular ad hoc networks (VANETs) as an emerging research focus [1,2]. By enabling wireless communication among multiple entities, VANETs provide crucial technical support for traffic control, autonomous driving, safety warnings, and vehicular services, thereby becoming a cornerstone of modern intelligent transportation systems.
The foundational architecture of conventional VANETs typically comprises three core components: a traffic control center (TCC), roadside units (RSUs), and vehicles equipped with an on-board unit (OBU) [3]. Central to this architecture, the TCC serves as both the system’s centralized control hub and primary computation component. Its responsibilities encompass identity management, secure authentication, and security policy formulation for the entire network.
However, with the rapid advancement of VANETs and the exponential growth of smart vehicles, network data traffic has surged dramatically. Due to its centralized nature, traditional vehicular network architecture struggles to meet the requirements of high concurrency and real-time communication, often resulting in communication bottlenecks and single points of failure.
To overcome these challenges, cloud computing and fog computing-based vehicular architectures have gained significant attention in recent years [4,5]. As an extension of cloud computing, fog computing deploys computing and storage resources closer to the network edge, enabling more localized data processing. This approach effectively reduces communication latency and enhances network efficiency [6]. Furthermore, given the limited coverage of RSUs, introducing fog nodes (FNs) between TCCs and RSUs can significantly improve network stability and overall communication quality in vehicular networks.
In VANET environments, information exchange primarily relies on wireless communication technologies, such as WiFi and dedicated short-range communications (DSR) [7,8]. However, the inherent security vulnerabilities in wireless technologies expose the entire system to both internal and external security threats, including man-in-the-middle attacks, replay attacks, and impersonation attacks. If VANETs suffer malicious attacks, they could result in serious casualties and substantial property damage. Therefore, ensuring communication security is a fundamental prerequisite for the widespread deployment of VANETs.
To ensure the security of VANETs, symmetric or asymmetric encryption is typically employed for secure data transmission. While asymmetric encryption offers robust security, its high computational and communication overheads make it difficult to satisfy VANETs’ requirements for high-frequency, low-latency communication. In contrast, the authenticated key agreement (AKA) mechanism enables the establishment of a secure session key between two communicating entities. This allows subsequent data transmission using symmetric encryption based on the session key, thereby reducing the computational and communication overhead while ensuring security.
At present, a variety of AKA schemes have been proposed [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26]. However, these schemes commonly face the following challenges: (1) When a large number of vehicles request key agreement from the TCC in a short period of time, each request is processed individually between the vehicle and the TCC. This paradigm incurs two critical limitations: on the one hand, the TCC has too much processing pressure in a short period of time; on the other hand, the communication overhead of the whole system increases greatly, and the processing efficiency of the whole system is relatively low. (2) Some schemes rely on complex cryptographic operations, which makes it difficult to meet the real-time requirements in the VANETs environment.
To solve the above problems, we propose an efficient batch AKA scheme based on fog computing (BAKAF), which can improve the overall efficiency of the system on the premise of ensuring security. Our key contributions are summarized as follows:
(1) For the scenario where a group of vehicles in a local area request AKA sessions within a short time frame, we propose a comprehensive AKA scheme based on the concepts of fog computing and Lagrange interpolation. In our scheme, the FN aggregates all AKA requests and, with the assistance of the TCC, establishes session keys for all vehicles by a round of operations. This approach effectively alleviates the operational complexity of the entire system. During the process of generating multiple session keys via Lagrange interpolation, a shared random point is used across the straight lines corresponding to different vehicles at the FN, thereby reducing both computational and communication overheads.
(2) Our scheme incorporates a conditional privacy-preserving mechanism and supports the revocation of malicious vehicles. The storage and computational overhead associated with tracking and revoking malicious vehicles is centralized at TCC, which is beneficial for resource-constrained vehicles.
(3) Our scheme employs cryptographic tools with low computational complexity, further reducing the overall computational overhead.
(4) Security analysis demonstrates that our scheme satisfies the security and privacy requirements of VANETs. Extensive experiments show that compared to existing advanced schemes, our approach achieves superior performance.
The remainder of this paper is organized as follows. Section 2 describes the related works. The preliminaries are presented in Section 3. Following this, the proposed scheme is detailed in Section 4. Subsequently, the security analysis and performance evaluation are presented in Section 5 and Section 6, respectively. Finally, there is the conclusion of the paper.
2. Related Works
To meet the high-security requirements for identity authentication and session key exchange, numerous AKA protocols have been proposed over the past decade.
In early schemes for foundational peer-to-peer communication scenarios, AKA mechanisms often relied on public key infrastructure (PKI). Islam et al. [9] proposed a device-to-device (D2D) AKA protocol based on elliptic curve cryptography (ECC) and self-certified public keys, which simplifies certificate management while achieving lightweight authentication. However, the lack of a complete mutual authentication mechanism makes this scheme vulnerable to typical threats such as replay and blocking attacks. To further simplify key management, Dang et al. [10] introduced a more efficient identity-based AKA protocol for VANETs, using an identity-based key generation model to reduce reliance on certificates. However, Deng et al. [11] pointed out that this scheme fails to ensure forward security in key leakage scenarios and proposed an improved version to enhance robustness under asymmetric attack models.
As privacy protection and practicality demands rise, recent studies have incorporated multi-factor authentication, anonymous authentication, Chebyshev polynomials, and elliptic curve-based lightweight cryptographic primitives into AKA protocols. For instance, Xie et al. [12] proposed a dynamic ID-based anonymous two-factor AKA scheme combining smart cards and dynamic identities, supporting anonymity and password updates. However, Li et al. [13] revealed that the scheme [12] is vulnerable to offline guessing attacks and smart card loss scenarios. Liu et al. [14] proposed a reputation-based conditional privacy-preserving AKA scheme for VANETs, which enhances authentication credibility and supports dynamic trust management. However, it suffers from high computational overhead due to its use of bilinear pairing. Lee et al. [15] introduced an improved two-factor AKA scheme based on extended chaotic maps, constructing a timestamp verification mechanism to resist replay attacks, but the protocol still faces risks of key leakage and temporary data exposure. Jiang et al. [22] proposed a cloud-based three-factor authentication and key agreement protocol (CT-AKA) integrating passwords, biometrics, and smart cards to secure access between cloud systems and vehicles. Dua et al. [16] designed a two-tier AKA scheme based on ECC, where cluster head vehicles are authenticated by a central authority in the first tier, and ordinary vehicles are authenticated by cluster head vehicles in the second tier to achieve efficient V2V communication.
With rising device density and access demands in VANETs, traditional authentication methods struggle with communication latency and key synchronization inefficiencies. To overcome these issues, researchers have designed AKA protocols supporting batch verification and one-to-many authentication. Vijayakumar et al. [17] proposed an efficient batch AKA scheme for 6G-enabled VANETs. However, their scheme requires authentication prior to key agreement and supports only batch authentication rather than batch key agreement. Sun et al. [18] combined certificateless signatures with the Chinese Remainder Theorem to design an AKA protocol with batch processing capabilities, claiming it effectively resists man-in-the-middle, impersonation, and replay attacks. Madandi et al. [19] developed a binary-tree-based AKA protocol to share authentication loads among nodes and enhance structural scalability. It should be noted that while these one-to-many AKA protocols reduce the complexity of operations, they also introduce high-computational operations such as pairing and modular exponentiation, which impose significant computational burdens on resource-constrained VANET environments. As a result, increasing attention has been paid to designing lightweight AKA protocols tailored for VANET environments. Researchers have recognized that vehicle terminals have limited resources, while RSUs, Trusted Authorities (TAs), and FNs possess greater computational and storage capabilities, leading to fog computing-based AKA design models. Wazid et al. [24] proposed a secure AKA protocol for fog computing-based VANET deployments, offering resource-aware advantages. However, some studies pointed out potential vulnerabilities in the scheme [24] under simulated attacks [25]. Ma et al. [26] designed a fog-based AKA scheme proven to provide session key security and protect V2I communication without using bilinear pairings. Wei et al. [20] proposed a symmetric encryption-based conditional privacy-preserving AKA scheme for fog-based VANETs, significantly reducing communication and computational costs. Qiao et al. [21] proposed a lightweight anonymous three-party AKA protocol using Chebyshev chaotic map operations to generate a shared session key while preserving anonymity; however, due to its focus on healthcare IoT, it is not suitable for VANETs. Cui et al. [23] proposed a robust and scalable VANET authentication scheme enabling vehicles to register with a trusted authority (TA) once and subsequently achieve rapid and efficient authentication with cloud service providers. Considering the limited computational and storage capacities of vehicles and drones, Cui et al. [27] further introduced a lightweight and provably secure two-factor AKA scheme based on chaotic maps for UAV-assisted VANETs, featuring fuzzy verifiers and honeywords to resist offline guessing and honeypot attacks. Zhou et al. [28] designed a vehicle-attribute-based AKA scheme supporting multi-user simultaneous authentication, offering formal security under the Canetti–Krawczyk (eCK) model and enabling session key agreement and anonymous identity updates. However, its use of bilinear pairing results in significant computational overhead.
In summary, although existing AKA protocols have made significant progress in enhancing the communication security of VANETs, several key challenges remain. First, many schemes rely on complex cryptographic operations such as bilinear pairings and group signatures, resulting in high computational overhead. However, given the limited computing resources of vehicular terminals, this leads to significant communication delays, making it difficult to meet the stringent low-latency requirements of vehicular applications. Second, many current schemes have large communication overhead, further exacerbating communication delays. Moreover, most protocols do not support batch AKA operations. When a large number of AKA requests occur simultaneously within a localized area and a short time window, the system suffers from high communication complexity and degraded service quality.
Our scheme effectively addresses these issues through the following mechanisms: When a group of vehicles request AKA sessions from the TCC within a predefined time interval, the fog node aggregates these requests and establishes session keys for all vehicles in a single round of operation. This design significantly reduces the system’s operational complexity and improves efficiency under large-scale request scenarios. Additionally, by employing Lagrange interpolation and lightweight cryptographic primitives, the scheme greatly reduces both computational and communication overheads. Furthermore, the proposed scheme supports conditional privacy preservation and incorporates a revocation mechanism for malicious vehicles, thereby enhancing both security and practicality.
3. Preliminaries
In this section, we introduce some basic knowledge, including system model, security and privacy requirements.
3.1. System Model
Our BAKAF scheme is based on the new architecture with FNs, as illustrated in Figure 1. This architecture mainly comprises four entities, i.e., a traffic control center (TCC), fog node (FN), roadside unity (RSU), and vehicle. The functions and features of each entity are as follows.
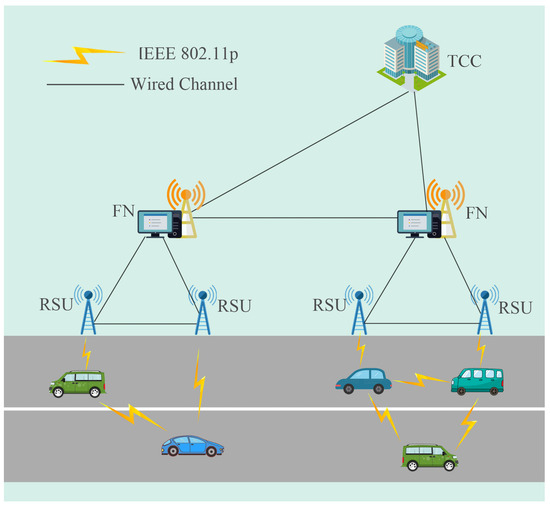
Figure 1.
System model.
TCC: The TCC, as a fully trusted entity, is controlled by government agencies. It possesses robust storage capacity and computing power. The TCC is responsible for the registration of FNs, RSUs, and vehicles, broadcasting system parameters, and tracking and revoking malicious vehicles. By leveraging technologies such as artificial intelligence and big data, the TCC can provide data support for services like road navigation, real-time information sharing, public security investigation, traffic improvement, and urban data analysis.
FN: FNs have strong storage and processing capabilities, primarily responsible for collecting and processing data within their domains. They are generally arranged at the edges of the fogs so that the vehicles can handle various tasks nearby, thereby enhancing overall system efficiency and meeting the low-latency requirements of the VANETs. FNs are connected to the TCC and RSUs via wired links for various interactions. They are semi-trusted entities that, on the one hand, faithfully execute protocol commands, and, on the other hand, monitor and collect data from other entities.
RSU: RSUs typically feature small signal coverage areas and limited storage and computing capabilities. In our scheme, we assume that RSUs are only used for collecting and forwarding the information they receive.
Vehicle: Vehicles are equipped with wireless sensing devices and tamper-proof devices (TPDs). They are untrusted entities with weak computing and storage capabilities, making them vulnerable to various attacks. Vehicles collect surrounding information through sensing devices and transmit it to nearby vehicles or RSUs via wireless communication technology.
3.2. Security and Privacy Requirements
Mutual authentication: In order to ensure identity legitimacy of the communication entity during AKA communication, mutual authentication should be performed among vehicles, FNs, and the TCC.
Confidentiality: The session key established through the AKA process can be kept confidential from any other entity except for the participating entities.
Data integrity: If a message is maliciously forged during transmission, the receiver should be capable of detecting the forgery.
Unlinkability: Unlinkability guarantees that no observable connection exists between different messages sent by the same vehicle. This security mechanism effectively prevents any entity from deducing whether two intercepted messages were transmitted by the identical sender.
Conditional privacy preserving: During communication, the vehicle’s real identity remains hidden from all entities except the TCC, which can retrieve any vehicle’s true identity when necessary.
Revocability: Once malicious vehicles are detected, the TCC can prevent them from initiating further AKA sessions.
Forward and backward secrecy: From an adversarial perspective, session keys established across different sessions must be computationally indistinguishable. Knowledge of one session key provides no advantage in deriving another.
Resistance to various attacks: Our scheme must withstand various well-known attacks, such as impersonation attacks and replay attacks.
Remark: The Pseudo-Random Functions and Elliptic Curve Cryptography are detailed in Appendix A.
4. Proposed Scheme
In this section, we will describe our BAKAF scheme in detail, which consists of three phases, namely: the setup phase, registration phase, and authentication and key agreement phase. In the setup phase, the TCC initializes the system and selects public parameters. In the registration phase, all vehicles and fog nodes need to register with the TCC. In the authentication and key agreement phase, within the set time interval, a batch of vehicles simultaneously establishes corresponding session keys with the fog nodes. The important symbols and definitions used in subsequent sections are shown in Table 1.

Table 1.
Definitions of basic symbols.
4.1. Setup Phase
Given a 128-bit security parameter , the TCC defines as a finite field with a large prime number p as its order. The TCC then generates an elliptic curve E defined by the equation , where . Subsequently, the TCC defines an additive cyclic elliptic curve group G with order q and generator P, which includes a point at infinity denoted as O. Finally, the TCC selects a random number as the system’s master secret key and retains the corresponding system public key .
The TCC constructs a revocation list, denoted as , which is used to store the real identities of malicious vehicles. Then it chooses seven cryptographic hash functions: , , , , , , , where represents the length of the real identity or pseudonym, and represents the length of the message authentication code.
Initialize a set of global communication parameters, namely: the maximum number of AKA requests processed in a single batch, ; the maximum waiting time for request aggregation, (initially set to a fixed value of 500 ms); and the TCC status identifier, , with status information directly provided by the TCC.
The TCC publishes the system parameters and secretly saves the system’s master secret key s.
4.2. Registration Phase
4.2.1. Registration for Vehicles
Assuming vehicle requests registration, the TCC selects a specific string as the vehicle ’s real identity, calculates the certificate , and sends to vehicle through a secure channel.
4.2.2. Registration for Fog Node
Assuming fog node requests registration, the TCC selects a specific string as the fog node ’s real identity, calculates the certificate , and sends to fog node through a secure channel.
Define the following global communication parameters for fog node : the dynamic window time , initialized to and adjustable during operation; and the real-time vehicle density , monitored and updated by .
The certificate (or ) is owned exclusively by the vehicle (or fog node ) itself and the TCC, and will play a vital role in both authentication and message integrity assurance.
4.3. Authentication and Key Agreement Phase
Assume that there are n vehicles requesting key agreement with the fog node in a short period of time. For the convenience of explanation, we will take vehicle as an example to elaborate.
4.3.1. Vehicle Requests to Generate a Session Key
Vehicle selects a random number and computes to obtain a random point on the group G.
Vehicle retains its pseudonym . (The vehicle uses a different pseudonym each time it sends the requested information, helping to ensure conditional privacy preserving.)
The vehicle generates the message authentication code , where is the timestamp, and sets message .
Finally, vehicle sends the message to fog node . It notes that the subscript V denotes that the sender of the message is a vehicle, while the superscript denotes that the receiver of the message is a FN, and the superscripts and subscripts of some symbols below have similar meanings.
4.3.2. FN Aggregates the Request Data from Each Vehicle
- (1)
- Decision on Initiating the Aggregation Process
Before aggregating requests, first obtains the current status of the TCC and executes the corresponding strategy:
- (a)
- TCC congestion (): suspends the aggregation process and resumes only upon receiving a “congestion relief” signal from the TCC.
- (b)
- TCC busy (): immediately delays the aggregation process and continues collecting AKA requests until the maximum waiting time is reached.
- (c)
- TCC idle (): dynamically adjusts the window duration based on the vehicle density , with the following rules:
- High density (, where denotes the high-density threshold): If the number of accumulated AKA requests reaches , the aggregation process is immediately triggered, even if the dynamic window time has not expired. In this case, the window duration for the next batch is reset to the standard value .
- Low density (, where denotes the low-density threshold): If the dynamic window time expires and fewer than requests have been collected, the aggregation process is immediately initiated, and the window duration for the next batch is updated to , where is the minimum allowable window duration.
- Medium density (): The aggregation process is triggered immediately when either the timeout expires or the number of requests reaches . The window duration for the next batch remains unchanged.
- (2)
- Aggregation Process
Upon receiving key agreement request information from n vehicles within the predetermined time interval, initializes (a binary string of length , all bits are set to 0) and (an empty string) for storing the aggregated and message, respectively.
For each vehicle’s information , check whether the inequality holds, where and denote the current timestamp and max valid time interval, respectively. If not, discard the information. Otherwise, proceed to calculate and . In this way, the information from all vehicles is aggregated into the variables and .
selects a random number , such that , where represents the x coordinate of the point on the elliptic curve E. It calculates the verification message , where is the timestamp of . Then, sends the message to the TCC.
The operations of the FN and their logical relationships in this section are shown in Algorithm 1.
| Algorithm 1 Aggregation |
|
4.3.3. TCC Authenticates and Processes the FN’s Requests
Upon receiving the batch key agreement request message from , the TCC first checks whether the inequality holds, where denotes the current time and denotes the maximum allowable message lifetime. If this condition is not satisfied, the AKA process is terminated; the TCC then sets the response message and sends it back to .
Next, the TCC calculates and , and checks whether the equation holds. If it holds, two conclusions can be drawn: the identity legality of has been validated by the TCC, and the integrity of can be guaranteed. Otherwise, the entire AKA process will be terminated, and the TCC then sets the response message and sends it back to .
Next, the TCC initializes an auxiliary variable , which is a binary string with length equal to and each bit of which is 0, and is used to re-record the message authentication code of legitimate vehicles. Then, the TCC performs the following procedures for each vehicle to verify its identity legitimacy and information integrity.
- It retrieves the i-th tuple from and obtains the real identity of by computing .
- It calculates the vehicle ’s certificate .
- It calculates , and verifies whether vehicle is revoked by checking if its real identity exists in the revocation list .
- –
- If it is not revoked, it indicates that the vehicle is legal, then calculates .
- –
- If it is revoked, it calculates , where the message authentication code of the illegal vehicle is removed from ; at the same time, the message of the illegal vehicle should be removed from .
The TCC checks whether the equation holds. If it does not hold, it indicates that the messages from some legitimate vehicles have been tampered with, and the entire AKA process is terminated; the TCC then sets the response message and sends it back to . Otherwise, it confirms that the information from all legitimate vehicles remains intact, and the TCC proceeds with the following steps.
The TCC computes , where is the timestamp of . Then, based on the message of each legitimate vehicle , the TCC performs the following procedures.
- The TCC sets , and .
- Using the Lagrange interpolation formula, the TCC can obtain the equation of a straight line passing through points and . These straight lines corresponding to all legitimate vehicles pass through a common point , which can significantly reduce the computational and communication overheads.
- The TCC selects a random number for vehicle , such that , then substitutes into the straight line equation to compute the corresponding y coordinate, i.e., it evaluates . Therefore, in addition to the points and , the TCC has now obtained the third point on the straight line .
- The TCC obtains the verification message by computing .
Upon completing the above operations for each vehicle, the TCC computes , where l represents the number of legitimate vehicles, sets message , and transmits the to the fog node . Since the information of illegitimate vehicles has been deleted by the TCC, the pseudonyms of legitimate vehicles need to be returned to the fog node .
The operations of the TCC and their logical relationships in this section are shown in Algorithm 2.
| Algorithm 2 TCC Process |
|
4.3.4. FN Generates Session Keys
Upon receiving message , fog node checks whether is valid. If not, the entire AKA process is terminated. Then recall the aggregation algorithm in Section 4.3.2. If it is, the following process continues.
Check the type of message and take the corresponding measures. (1) If , it indicates that the entire message transmitted from the FN to the TCC has timed out. In this case, recall the aggregation algorithm in Section 4.3.2. (2) If , it indicates that there is tampering in the message transmitted from the FN to the TCC. Reuse the originally calculated and , and recall the aggregation algorithm in Section 4.3.2. (3) If , it indicates that the signatures of some vehicles are invalid or the information transmitted from the vehicle to the FN has been tampered with. Notify all vehicles to retransmit the AKA request. (4) Perform the following operations in other cases.
computes and checks whether the equation holds. If it holds, it indicates that the legality of the vehicles and the integrity of and are guaranteed. Then, performs the following steps.
- The fog node sends the messages to the corresponding vehicles , respectively.
- It computes , and performs the following operations for each legal vehicle.
- –
- It substitutes into the straight line equation to obtain the y coordinate of the intersection point between the line and the Y-axis: . The line passes through points and , where point is set by fog node and point is set by the TCC.Note: It is unnecessary to first solve the explicit expression of the linear equation here.
- –
- It obtains the session key between the vehicle and the fog node by computing .
- –
- Fog node stores the session key .
The operations of the FN and their logical relationships in this section are shown in Algorithm 3.
| Algorithm 3 FN Generates session keys |
|
4.3.5. Vehicle Generates Session Key
After receiving message , vehicle checks whether is valid. If not, the entire AKA process is terminated. If it is, the following processes continue.
The vehicle computes and checks whether the equation holds. If it holds, it indicates that the legality of the vehicles and the integrity of and are guaranteed. Then, performs the following steps.
- It sets , and computes .
- It substitutes into the linear equation to obtain the y coordinate of the intersection point between the line and the Y-axis: . The line passes through points and , where point is set by vehicle and point is set by the TCC.Note: For a specific vehicle , the three points , , and lie on the same straight line. Therefore, the line determined by any two of these points is identical, denoted as .
- It obtains the session key between the vehicle and the fog node by computing .
- Vehicle stores the session key .
Remark 1.
Within a fixed time interval, if n vehicles request AKA sessions with the same FN, the FN aggregates all AKA session requests, and the system then performs batch AKA processing. This approach offers at least three advantages: (1) it reduces the overall system complexity; (2) it lowers the communication overhead between the FN and the TCC; and (3) it decreases the computational overhead for both the FN and the TCC.
Remark 2.
On the TCC side, even if some vehicles are found to be illegal, the remaining legal vehicles can still perform the batch AKA process, which greatly enhances the flexibility of batch AKA.
5. Security Analysis
In this section, we will analyze the security performance of our scheme from both informal and formal aspects.
5.1. Informal Security Analysis
Mutual authentication: Our scheme comprises four phases of information transmission, all employing identical authentication mechanisms. We illustrate this using the TCC-to-FN message transmission as an example. The TCC first computes , where is the certificate of . Subsequently, the TCC transmits the message to . Upon receiving message , computes and checks whether the equation holds. If the equation holds, it confirms that the message must originate from the TCC, since only and the TCC possess the certificate . Therefore, the authenticity is guaranteed.
Confidentiality: In our scheme, the method for calculating the session key is . To obtain the session key between vehicle and , we first need to obtain , which represents the y coordinate of the line at . At least two points are required to determine a straight line. Even if a malicious entity intercepts a point on the straight line transmitted from the TCC, since it cannot obtain the certificates of the vehicle or the FN , it cannot obtain the other point on the required straight line. Consequently, it cannot construct the linear equation and calculate . Therefore, the session key between vehicle and remains confidential to any malicious entity.
Data integrity: Our scheme comprises four phases of information transmission, all employing identical message integrity protection mechanisms. We illustrate this using the FN-to-TCC message transmission as an example. first sends the message to the TCC, where , and is the certificate of , which is owned exclusively by the fog node itself and the TCC. If any field in is tampered with (e.g., altered to ), the malicious attacker must recompute the verification value . Without ’s certificate, the attacker can only arbitrarily choose , yielding: .
Upon receiving the message from , the TCC first recalculates certificate and verification value . Then, it checks whether the equation holds. Because is not equal to , the verification equation will not hold. In this way, the integrity of can be guaranteed.
Unlinkability: For each AKA session request, the vehicle generates a fresh pseudonym, timestamp, and random ECC point, where neither the timestamp nor the ECC point correlate with the vehicle’s identity or pseudonym, and no other entity except the TCC and the vehicle itself can track the true identity through the pseudonym. Therefore, this mechanism effectively prevents any malicious entity from deducing whether two intercepted messages were transmitted by the identical sender.
Conditional privacy preserving: Prior to initiating an AKA session, vehicle generates a pseudonym , then uses for all subsequent communications. Once the message is disputed, the TCC can recover the real identity via , where s is the master secret key and is a random ECC point.
To derive the real identity from , any entity must calculate either or ; s is the system’s master private key, owned only by the TCC, while is a random number, owned only by the vehicle . Solving for from or s from requires solving the difficult ECDL problem. Therefore, except for the TCC, no other entities can obtain the real identity.
Revocability: The TCC maintains a revocation list . Upon detection of a malicious vehicle , its real identity is added to . If attempts to initiate subsequent AKA sessions, the TCC will detect that its real identity is already in the revocation list and terminate the AKA procedure. All revocation operations are concentrated on the TCC, which has abundant computing and storage resources, making it relatively friendly for vehicle terminals with limited resources.
Forward and backward secrecy: In our scheme, the session key is computed as , where depends on two fresh random nonces; is a randomly generated ECC point. The single use and randomness of these parameters ensure no correlation between session keys across different sessions, thus guaranteeing both forward and backward secrecy.
Resistance to impersonation attack: In our scheme, any passed message contains a verification value, which is bound to the certificate of the entity (vehicle or FN) through a hash function. Since these certificates are exclusively held by the TCC and the originating entity itself, no other party can forge valid verification values. Consequently, any impersonation attempt by malicious attackers will be detected during the recipient’s verification process.
Resistance to replay attack: In our scheme, each transmitted message incorporates a timestamp. For instance, during the FN-to-TCC message transmission, sends the message to the TCC, where denotes the timestamp. As demonstrated in the “Data integrity” section, the timestamp is immutable. Upon receiving the message , the TCC verifies its freshness by checking whether the inequality holds, where represents the current time. If not, the TCC treats the message as expired. Therefore, this timestamp validation mechanism, combined with the immutability guarantee, ensures that our scheme can effectively defend against a replay attack.
5.2. Formal Security Proof
In this section, we formally prove that our scheme satisfies session key security under the Real-Or-Random (ROR) model [29].
5.2.1. Security Model
We first establish a security model to define the adversaries’ capabilities and the interaction rules between the challenger and the adversaries, and the model includes the following definitions:
Participants: Let , , and denote the i-th instance of a vehicle, the f-th instance of an FN, and the t-th instance of a TCC, respectively. The concrete instance of these participants can also be represented as , where indicates the instance type and represents the index. Notably, RSUs are excluded from being considered as participating entities, as they merely function as conventional base stations for message forwarding.
Partnering: Two participants are considered as partners if they (a) belong to the same session, (b) successfully exchange messages in sequence, and (c) want to mutually authenticate each other.
Freshness: If the adversary does not obtain the session key shared among , , and , then these instances are considered fresh.
Adversary: The adversary can participate in interactions of , , and by adopting the following oracle queries.
- : This query simulates the passive adversary to intercept messages exchanged among , , and .
- : The query models an active adversary sending message m to , , and . Upon receiving this query, these instances return corresponding response messages to .
- : When challenger receives this query from adversary , it randomly selects a bit ; if , sends the real session key of to ; if , sends a random key of the same length as the session key to the . If the session key of is undefined, or if a query has been made to or its partners, receives ⊥ as an invalid value.
Semantic security: Adversary first performs a query, and guesses the random value of b in the query, denoted as ; if , wins. We define our BAKAF scheme as , and the advantage of to break the ’s semantic security based on the ROR model within PPT as , where denotes the probability that the event E occurs; if is negligible, our scheme is regarded as secure under the ROR model.
5.2.2. Security Proof
In this subsection, we prove that our BAKAF scheme satisfies the semantic security of the session key.
Theorem 1.
Let , , , , , and represent the maximum number of hash () queries, the space range of hash function (), the number of oracle queries, the number of oracle queries, the number of oracle queries, and the advantage of adversary in breaking the PRF, respectively. Thus, the advantage of adversary in breaking the semantic security of the session keys in our BAKAF scheme within PPT, can be calculated as follows:
Proof.
Similar to [30,31], to prove Theorem 1, we construct a sequence of games (). These games involve interactions between adversary and challenger . We define as the event that adversary wins in .
: This game serves as the starting point of the entire proof process. It simulates a realistic environment in which adversary launches actual attacks. A random number b is predetermined before the game begins. Based on the semantic security of the session key, we have
: In this game, the adversary is permitted to eavesdrop on communications among parties , , and by executing the Execute operation. Subsequently, performs the Test operation to distinguish the real session key from a random value. And this is because of , where . Since determining the equation of a straight line requires at least two distinct points on the line, but can obtain at most one point, the actual session key cannot be computed. Consequently, the probability of winning is identical to that of winning , as shown below:
: Based on , the adversary can perform Send and hash oracle queries. In this game, launches spoofing attacks by forging and sending malicious requests to , , and . Our scheme allows to modify messages , , , and , but these messages contain random elements (, , ) and independent timestamps (, , ). Hence, must execute queries without causing collisions. By the birthday paradox, we derive the following probability bound:
: In this game, the oracle is slightly modified compared to . Specifically, when processing queries from , the challenger now substitutes the outputs with truly random numbers. Since this modification affects exactly two operations, namely and ), we can derive the following probability bound:
After that, the adversary has utilized all available oracles to challenge the semantic security of protocol . Adversary attempts to win the game solely by guessing the value of b. All session keys used to respond to Test queries in this game are independently and uniformly distributed. As a result, no information regarding the hidden bit b used by the Test oracle is leaked to the adversary. Consequently, we obtain:
Since q and are typically sufficiently large, and is small enough and infinitely close to 0, the adversary ’s advantage in breaking the semantic security of our BAKAF scheme is negligible. Thus, our scheme is semantically secure under the ROR model. □
6. Performance Evaluation
In this subsection, we evaluate the proposed scheme’s performance through two key metrics: computational overhead and communication overhead. We compare our BAKAF scheme with state-of-the-art provably secure AKA schemes [20,21,22,23]. The selection of these comparative schemes is based on two key criteria: (1) Our scheme employs three-party entity collaboration for key agreement, and all selected comparison schemes similarly adopt a three-party framework. (2) Since our scheme eliminates computationally expensive bilinear pairing operations, pairing-based AKA schemes are excluded from the comparison to ensure fairness.
As far as we know, this scheme is the first batch three-party AKA scheme in VANETs. Therefore, if other schemes perform n AKA sessions, the computational and communication overheads of those schemes are n times the respective overheads of a single AKA session.
6.1. Computational Overhead Comparison
Before comparing the computational overhead, we use the MIRACL [32] library to measure all basic operations. All experiments were conducted on a Lenovo Legion Y9000P laptop equipped with an 11th Gen Intel® Core (TM) i7-11800H processor, 16 GB of memory, and the Windows 11 operating system. The laptop was purchased from Lenovo Store, Guilin, China. We omitted normal operations (addition, multiplication) and string operations (concatenation, XOR) due to their negligible execution times. The experimental results for the average time consumption of basic operations are shown in Table 2. It is noted that each operation’s execution time was averaged across 1000 repetitions.

Table 2.
The execution time of basic operations.
In a complete AKA session process of Lu et al.’s scheme [20], the computational overheads of the vehicle and the fog node are and , respectively. A lookup operation for the real ID was performed on the Cuckoo Filter in the scheme [20]. However, since this functionality is not implemented in our scheme, we omitted it to ensure fairness, so the computational overhead of a sub-TA (corresponding to the TCC in our scheme) is . Thus, the total computational overhead of the scheme [20] for an AKA session process is .
In a complete AKA session of Qiao et al.’s scheme [21], the computational overheads of the user (corresponding to the vehicle in our scheme), the fog node, and the cloud server (corresponding to the TCC in our scheme) are , , and , respectively. Thus, the total computational overhead of scheme [21] for an AKA session process is .
In a complete AKA session process of Jiang et al.’s scheme [22], the computational overheads of the user (corresponding to the vehicle in our scheme), the autonomous vehicle (corresponding to the fog node in our scheme), and the cloud (corresponding to the TCC in our scheme) are , 4, and , respectively. Thus, the total computational overhead of scheme [22] for an AKA session process is .
In a complete AKA session process of Cui et al.’s scheme [23], the computational overheads of the vehicle, the cloud service (corresponding to the fog node in our scheme), and the TA (corresponding to the TCC in our scheme) are , , and , respectively. Thus, the total computational overhead of Scheme [23] for an AKA session process is .
In our BAKAF scheme, the AKA is executed in a batch for n vehicles; the computational overhead of n vehicles is . Moreover, the computational overheads of the fog node and the TCC are and , respectively. Thus, the total computational overhead is .
In Schemes [20,21,22,23], there are no batch handling functions. Therefore, executing n AKA sessions incurs n times the overhead of a single session. Consequently, the comparison results of computational overheads between our scheme and Schemes [20,21,22,23] are presented in Table 3.

Table 3.
Computational overheads for n AKA session (ms).
We use Figure 2 to show the comparison results for a single AKA session. According to Figure 2, our scheme maintains an identical computational overhead to Scheme [20], while demonstrating significant advantages over Schemes [21,22,23] in terms of both per-entity and total computational overhead. Meanwhile, Figure 3 compares the computational overheads (both per-entity and total) for all schemes when n AKA sessions are conducted within a fixed time interval. The results demonstrate that as the number of vehicles n increases, our scheme achieves lower computational overhead than baseline schemes.
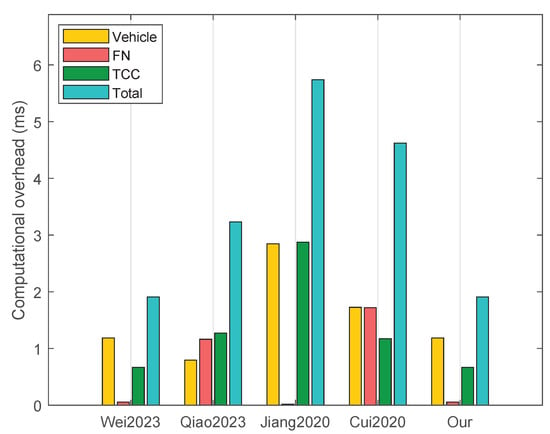
Figure 2.
Computational overhead comparison for a single AKA session [20,21,22,23].
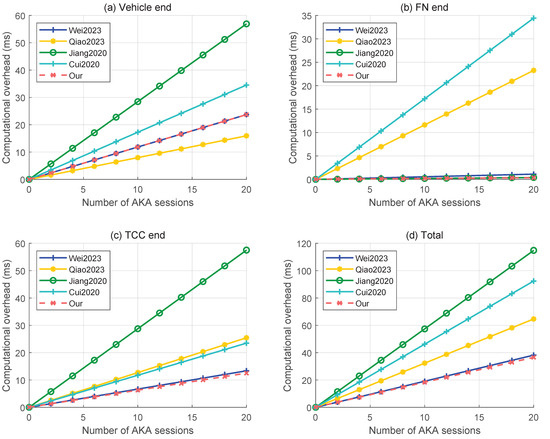
Figure 3.
Computational overhead comparison for n AKA sessions [20,21,22,23].
The low computational overhead of our scheme primarily stems from two key factors: (1) Our scheme employs lightweight cryptographic primitives, while the more computationally intensive ECC-based scalar multiplication operations are exclusively used for anonymous credential generation. (2) The batch AKA approach significantly reduces the overall computational operations. Beyond reducing per-entity computational overhead, our scheme substantially decreases the interaction between the FN and the TCC through batch AKA session processing.
6.2. Communication Overhead Comparison
Before comparing the communication overheads, we assume that the security parameters of all schemes are 128 bits in length. The element types and lengths involved in information transmission for each scheme are listed in Table 4. To ensure fairness and simplicity, we adopt AES as the symmetric encryption algorithm across all schemes, with ciphertext length identical to plaintext length.

Table 4.
The sizes of each element (byte).
In Scheme [20], a vehicle transmits to the FN in the first stage, where is the pseudonym, whose length is identical to , is the timestamp, and is an element in elliptic curve group G, , so the communication overhead in the first stage is bytes. In the second stage, the FN transmits to the TCC, where is the real identity and is the timestamp, , so the communication overhead in this stage is bytes. In the third stage, the TCC transmits to the FN, where , and is the timestamp, so the communication overhead in this stage is bytes. In the fourth stage, the FN transmits to the vehicle, so the communication overhead in this stage is bytes. Suppose there are n vehicles conducting AKA sessions during a fixed time interval, the total communication overhead is bytes.
In Scheme [21], a user transmits to the fog node in the first stage, where is obtained by symmetrically encrypting the concatenation of the identifier and a random number , whose length is identical to . is the timestamp, and and are derived from one-way hash functions. Since their data types are unspecified in the original paper, we adopt the 20-byte length defined therein. is the extended Chebyshev polynomial, whose length is . Thus, the communication overhead in the first stage is bytes. In the second stage, the transmits to cloud server S, where is obtained by symmetrically encrypting the concatenation of the identifier and a random number , whose length is . A and are the extended Chebyshev polynomial, is the timestamp, and is derived from one-way hash functions, so the communication overhead in this stage is bytes. In the third stage, cloud server S transmits to the fog node , where are derived from one-way hash functions, B and C are the extended Chebyshev polynomial, and is the timestamp, so the communication overhead in this stage is bytes. In the fourth stage, the fog node transmits to the user, where is the timestamp, so the communication overhead in this stage is bytes. Suppose there are n users conducting AKA sessions during a fixed time interval, the total communication overhead is bytes.
Similarly, when executing n AKA sessions within a fixed time interval, the total communication overheads for Scheme [22] and Scheme [23] are calculated as bytes and bytes, respectively.
In our scheme, suppose there are n vehicles performing AKA sessions with the same fog node within a fixed time interval; vehicle needs to transmit to the fog node , where is the pseudonym, is the timestamp, is an element in elliptic curve group G, and is the message authentication code, so the communication overhead of n vehicles in the first stage is bytes. In the second stage, the fog node transmits the message to the TCC, where is the real identity, is the time timestamp, , is formed by sequentially concatenating n messages , whose length is , and is the message authentication code, so the communication overhead in this stage is bytes. In the third stage, the TCC transmits the message to the fog node , where is the timestamp, ; here we assume , implying that all vehicles’ data are both correct and complete. Thus, the communication overhead in this stage is bytes. In the fourth stage, the fog node sends the messages to the corresponding vehicles , so the communication overhead in this stage is bytes. Thus, for n vehicles executing the AKA sessions, the total communication overhead across all four stages amounts to bytes.
Figure 4 compares the communication overheads of different schemes as the number of AKAs varies. As shown in the figure, our scheme demonstrates a clear advantage as the number of AKAs increases. This is primarily because our scheme processes multiple AKA requests in batches within a fixed time interval.
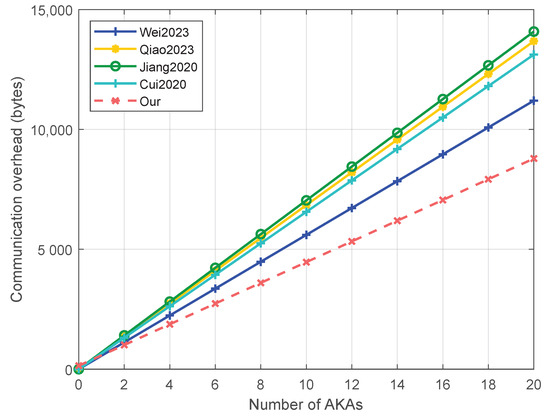
Figure 4.
The comparison of communication overheads [20,21,22,23].
7. Conclusions and Remark
In this scheme, for a batch of vehicles initiating AKA requests to the same fog node within a fixed short time interval, we combine fog computing and Lagrange interpolation to complete these AKA processes in a round of operations. The interpolation points of the straight lines corresponding to each vehicle share a common point at the fog node. These mechanisms ensure that our scheme possesses very low computational and communication overheads while simplifying the overall system operations.
The authentication component of our scheme relies on the certificates of vehicles and fog nodes, as well as the system master secret key. It is assumed that the system master secret key and the certificate values remain perpetually secure. However, existing physical attack techniques (such as side-channel attacks) can obtain such sensitive information. Since existing technologies like physically unclonable functions and fuzzy extractor can effectively resist these physical attacks, our scheme does not focus on this aspect in depth.
The batch AKA mechanism designed in our scheme requires participating vehicles to establish session keys with the same FN, which poses a certain limitation. How to perform batch AKA operations among different vehicles and different FNs within a short time interval is a key direction for our future research.
Author Contributions
Conceptualization, L.L., J.L. and C.C.; methodology, L.L. and H.Z.; validation, C.C. and H.Z.; formal analysis, L.L.; software, S.L.; writing—original draft preparation, L.L. and S.L.; writing—review and editing, L.L., C.C., S.L. and H.Z.; visualization, L.L. and H.Z.; project administration, J.L. and C.C. All authors have read and agreed to the published version of the manuscript.
Funding
National The Natural Science Foundation of China (Grant No. 62072133), and the Major Scientific and Technological Innovation Project of Wenzhou (ZG2023028, ZG2024013).
Data Availability Statement
This study is based on the MIRACL library, which is openly available at [https://github.com/miracl/MIRACL, accessed on 17 August 2025].
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
Appendix A.1. Pseudo-Random Function (PRF)
A pseudo-random function (PRF) is an important cryptographic primitive that behaves similarly to a truly random function. Specifically, given an input consisting of a key and a binary string , a PRF generates an output string via the computation . A secure PRF must ensure that its output is computationally indistinguishable from the output of a truly random function for any probabilistic polynomial time (PPT) adversary. PRFs typically have the following characteristics: (1) Given the same key and input, they will generate the same output. (2) For different keys and inputs, the output should appear random and unpredictable.
Appendix A.2. Elliptic Curve Cryptography (ECC)
Since ECC was built by Kobilitz, it has been widely applied to encryption and other safety-related areas [33].
Let denote a finite field with a large prime number p as its order. We choose an elliptic curve E defined as , where . Then, an additive cyclic elliptic curve group G on E with order q and a generator P can be generated, which contains the point at infinity O. The properties of group G are as follows:
Scalar multiplication: Let ; the scalar multiplication on E is defined as ( times).
Elliptic curve discrete logarithm (ECDL) assumption: For randomly chosen satisfying , where is unknown, there exists no efficient algorithm that can determine from Q in PPT with non-negligible advantage.
References
- Cao, J.; Feng, W.; Ge, N.; Lu, J. Delay Characterization of Mobile-Edge Computing for 6G Time-Sensitive Services. IEEE Internet Things J. 2021, 8, 3758–3773. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Edge Computing in VANETs-An Efficient and Privacy-Preserving Cooperative Downloading Scheme. IEEE J. Sel. Areas Commun. 2020, 38, 1191–1204. [Google Scholar] [CrossRef]
- Saleem, M.A.; Li, X.; Mahmood, K.; Shamshad, S.; Alenazi, M.J.F.; Das, A.K. A Cost-Efficient Anonymous Authenticated and Key Agreement Scheme for V2I-Based Vehicular Ad-Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2024, 25, 12621–12630. [Google Scholar] [CrossRef]
- Lin, C.C.; Deng, D.J.; Yao, C.C. Resource Allocation in Vehicular Cloud Computing Systems with Heterogeneous Vehicles and Roadside Units. IEEE Internet Things J. 2018, 5, 3692–3700. [Google Scholar] [CrossRef]
- Awais, S.M.; Yucheng, W.; Mahmood, K.; Alenazi, M.J.F.; Bashir, A.K.; Das, A.K.; Lorenz, P. Provably Secure and Lightweight Authentication and Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2024, 25, 21107–21116. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the ACM SIGCOMM International Conference on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Kenney, J.B. Dedicated Short-Range Communications (DSRC) Standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Jiang, D.; Delgrossi, L. IEEE 802.11p: Towards an International Standard for Wireless Access in Vehicular Environments. In In Proceedings of the VTC Spring 2008—IEEE Vehicular Technology Conference, Marina Bay, Singapore, 11–14 May 2008; pp. 2036–2040. [Google Scholar] [CrossRef]
- Islam, S.H.; Biswas, G.P. Design of Two-Party Authenticated Key Agreement Protocol Based on ECC and Self-Certified Public Keys. Wirel. Pers. Commun. 2015, 82, 2727–2750. [Google Scholar] [CrossRef]
- Dang, L.; Xu, J.; Cao, X.; Li, H.; Chen, J.; Zhang, Y.; Fu, X. Efficient identity-based authenticated key agreement protocol with provable security for vehicular ad hoc networks. Int. J. Distrib. Sens. Netw. 2018, 14, 155014771877254. [Google Scholar] [CrossRef]
- Deng, L.; Shao, J.; Hu, Z. Identity based two-party authenticated key agreement scheme for vehicular ad hoc networks. Peer-To-Peer Netw. Appl. 2021, 14, 2236–2247. [Google Scholar] [CrossRef]
- Xie, Q.; Wong, D.S.; Wang, G.; Tan, X.; Chen, K.; Fang, L. Provably Secure Dynamic ID-Based Anonymous Two-Factor Authenticated Key Exchange Protocol With Extended Security Model. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1382–1392. [Google Scholar] [CrossRef]
- Li, X.; Yang, D.; Zeng, X.; Chen, B.; Zhang, Y. Comments on ‘Provably Secure Dynamic Id-Based Anonymous Two-Factor Authenticated Key Exchange Protocol With Extended Security Model’. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3344–3345. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient Privacy-Preserving Dual Authentication and Key Agreement Scheme for Secure V2V Communications in an IoV Paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Lee, T.F.; Hsiao, C.H.; Hwang, S.H.; Lin, T.H. Enhanced smartcard-based password-authenticated key agreement using extended chaotic maps. PLoS ONE 2017, 12, e0181744. [Google Scholar] [CrossRef] [PubMed]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure Message Communication Protocol Among Vehicles in Smart City. IEEE Trans. Veh. Technol. 2018, 67, 4359–4373. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kozlov, S.A.; Rodrigues, J.J.P.C. An Anonymous Batch Authentication and Key Exchange Protocols for 6G Enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2022, 23, 1630–1638. [Google Scholar] [CrossRef]
- Sun, Y.; Cao, J.; Ma, M.; Zhang, Y.; Li, H.; Niu, B. EAP-DDBA: Efficient Anonymity Proximity Device Discovery and Batch Authentication Mechanism for Massive D2D Communication Devices in 3GPP 5G HetNet. IEEE Trans. Dependable Secur. Comput. 2022, 19, 370–387. [Google Scholar] [CrossRef]
- Madanchi, M.; Abolhassani, B. Authentication and Key Agreement Based Binary Tree for D2D Group Communication. In Proceedings of the 2020 28th Iranian Conference on Electrical Engineering (ICEE), Tabriz, Iran, 4–6 August 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Bolodurina, I.; Liu, L. A Lightweight and Conditional Privacy-Preserving Authenticated Key Agreement Scheme With Multi-TA Model for Fog-Based VANETs. IEEE Trans. Dependable Secur. Comput. 2023, 20, 422–436. [Google Scholar] [CrossRef]
- Qiao, H.; Dong, X.; Jiang, Q.; Ma, S.; Liu, C.; Xi, N.; Shen, Y. Anonymous Lightweight Authenticated Key Agreement Protocol for Fog-Assisted Healthcare IoT System. IEEE Internet Things J. 2023, 10, 16715–16726. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, X.; Zhong, H.; Zhang, J.; Liu, L. Extensible Conditional Privacy Protection Authentication Scheme for Secure Vehicular Networks in a Multi-Cloud Environment. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1654–1667. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated Key Management Protocol in Fog Computing-Based Internet of Vehicles Deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Saleem, M.A.; Mahmood, K.; Kumari, S. Comments on “AKM-IoV: Authenticated Key Management Protocol in Fog Computing-Based Internet of Vehicles Deployment”. IEEE Internet Things J. 2020, 7, 4671–4675. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An Efficient and Provably Secure Authenticated Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Cui, J.; Liu, X.; Zhong, H.; Zhang, J.; Wei, L.; Bolodurina, I.; He, D. A Practical and Provably Secure Authentication and Key Agreement Scheme for UAV-Assisted VANETs for Emergency Rescue. IEEE Trans. Netw. Sci. Eng. 2024, 11, 1454–1468. [Google Scholar] [CrossRef]
- Zhou, Y.; Cao, L.; Qiao, Z.; Xu, R.; Han, Y.; Xing, J.; Yang, B.; Xia, Z.; Zhang, M. A Novel Cloud-Assisted Authentication Key Agreement Protocol for VANET. IEEE Trans. Veh. Technol. 2024, 73, 13526–13541. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-Based Authenticated Key Exchange in the Three-Party Setting. In Public Key Cryptography—PKC 2005; Vaudenay, S., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Liu, G.; Li, H.; Liang, Y.; Le, J.; Wang, N.; Mu, N.; Liu, Z.; Liu, Y.; Xiang, T. PSRAKA: Physically Secure and Robust Authenticated Key Agreement for VANETs. IEEE Trans. Veh. Technol. 2024, 74, 7953–7968. [Google Scholar] [CrossRef]
- Han, Y.; Guo, H.; Liu, J.; Ehui, B.B.; Wu, Y.; Li, S. An Enhanced Multifactor Authentication and Key Agreement Protocol in Industrial Internet of Things. IEEE Internet Things J. 2024, 11, 16243–16254. [Google Scholar] [CrossRef]
- Miracl Cryptographic SDK. 2019. Available online: https://github.com/miracl/MIRACL (accessed on 17 August 2025).
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1621–1632. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).