Abstract
Recently, wireless sensor networks (WSNs) have been widely used in a variety of fields, and make people’s lives more convenient and efficient. However, WSNs are usually deployed in a harsh and insecure environment. Furthermore, sensors with limited hardware resources have a low capacity for data processing and communication. For these reasons, research on efficient and secure real-time authentication and key agreement protocols based on the characteristics of WSNs has gradually attracted the attention of academics. Although many schemes have been proposed, most of them cannot achieve all known security features with satisfactory performance, among which anonymity, N-Factor security, and forward secrecy are the most vulnerable. In order to solve these shortcomings, we propose a new lightweight and anonymous three-factor authentication scheme based on symmetric cryptographic primitives for WSNs. By using the automated security verification tool ProVerif, BAN-logic verification, and an informal security analysis, we prove that our proposed scheme is secure and realizes all known security features in WSNs. Moreover, we show that our proposed scheme is practical and efficient through the comparison of security features and performance.
1. Introduction
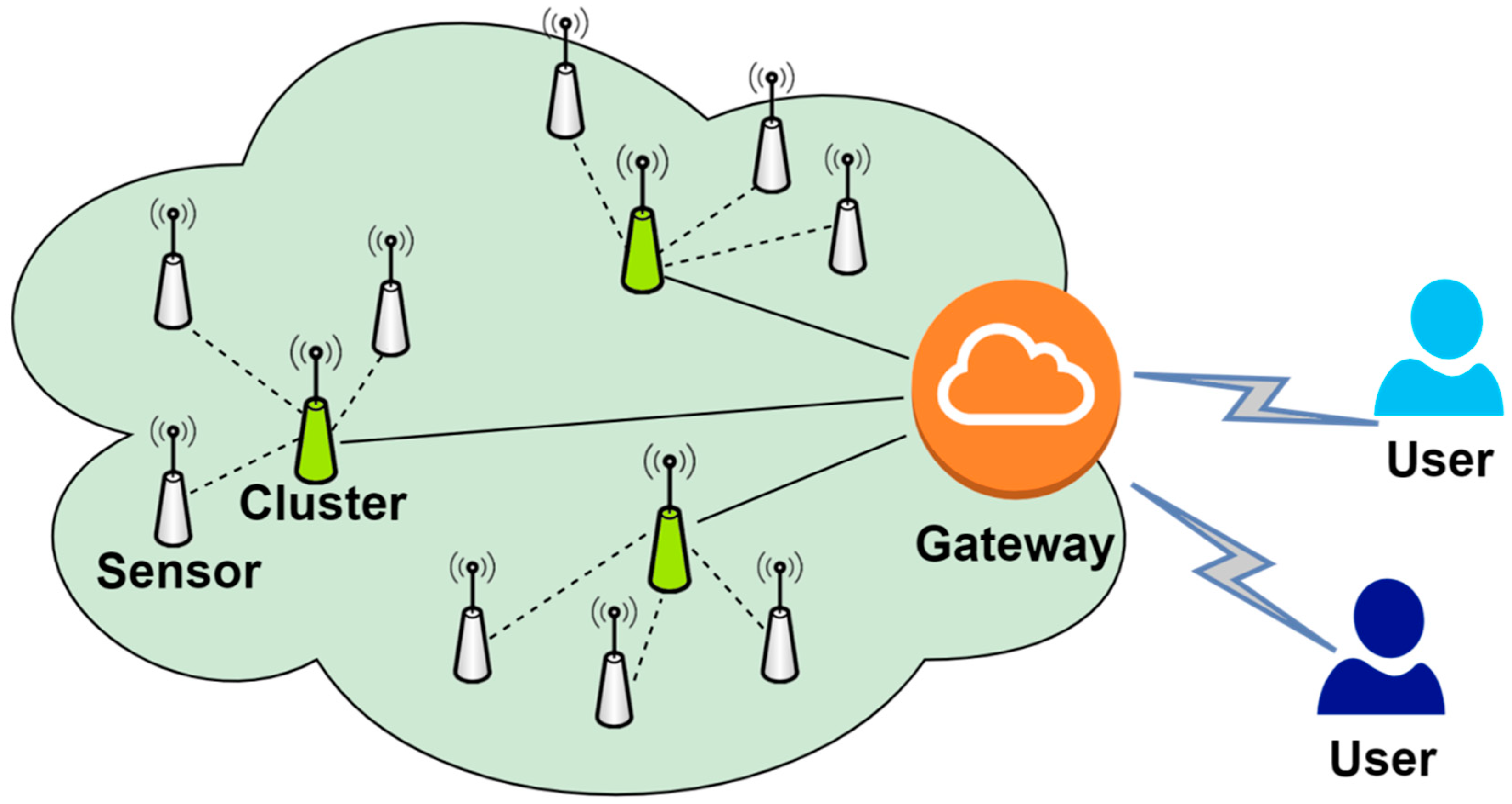
A wireless sensor network (WSN) is a distributed and self-organizing sensor network, which is composed of a large number of sensor nodes that can perceive and understand the external world. In WSNs, sensor nodes cooperate to sense, collect, and process information in the network coverage area and send it to the gateway node. In recent years, WSNs have been widely used in various practical applications in industrial and agricultural fields [1,2,3,4], such as temperature monitoring in agriculture, power consumption monitoring in smart grids, and human health monitoring in medical care. In these application environments, many scattered users, various randomly distributed sensor nodes, and one or more relatively powerful gateway nodes form a powerful network system. For example, in the field of health care, the sensors deployed on the patient’s body can monitor and obtain the patient’s body data, and the medical staff can directly and remotely obtain the patient’s current body temperature, blood pressure, pulse times, and other information in real-time through the wireless sensor network, so as to improve the health status of healthy patients. Figure 1 shows the network architecture of WSNs.
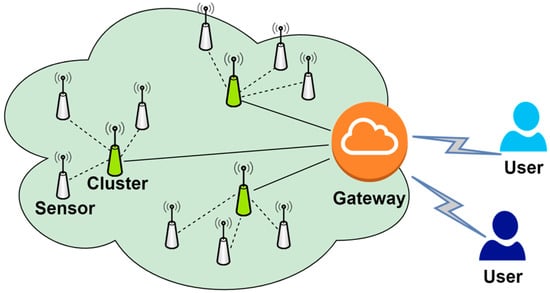
Figure 1.
Network model of wireless sensor networks.
However, when sensor nodes are active in an unattended or hostile wireless network environment, attackers can easily intercept, delete, and modify transmission messages and launch various attacks [5]. Therefore, the network security and privacy of these sensors become very critical. In order to ensure that only authorized legitimate users can access sensors and protect the communication security of real-time sensing data, it is extremely necessary for users and sensors to authenticate each other directly. Moreover, they also need to be able to establish a session key to ensure the security of future communication. Authentication and key agreement protocols are effective ways to achieve these goals. However, due to the limited resources of sensor nodes, an authentication protocol based on complex asymmetric cryptographic primitives is difficult to apply to wireless sensor networks. Therefore, the balance between security and performance is highly significant for the design of identity authentication protocols in the wireless sensor network environment.
Lamport proposed the first password-based authentication and key agreement protocol in 1980 [6], and, since then, research on authentication protocols has been a hot topic. In recent years, research on authentication and key agreement protocols in WSNs has been conducted [7,8,9,10,11,12,13,14,15,16,17,18]. In 2006, Wong et al. [19] proposed a lightweight password-based authentication scheme for WSNs. However, Das et al. point out that Wong et al.’s scheme cannot resist replay attacks and stolen-verifier attacks [20]. Furthermore, Das et al. put forward an improved scheme. Unfortunately, there are also many security flaws in Das et al.’s scheme [21,22]. Based on Farash et al.’s scheme [23], Amin et al. provided an anonymity three-factor authentication scheme [24] for WSNs in 2016. However, Jiang et al. found that the scheme could not resist smart card stolen attacks and known session-specific temporary information attacks [25]. Although many schemes have been proposed, most of them cannot achieve all known security features with satisfactory performance.
In 2019, Shin et al. proposed a lightweight three-factor authentication and key agreement protocol for WSNs [26] and claimed that the protocol can achieve all known security features with satisfactory performance. This article analyzes Shin et al.’s scheme. It is found that their scheme is vulnerable to de-synchronization attacks and cannot achieve forward secrecy and three-factor security.
Our crucial contributions are as follows:
- We review and analyze Shin et al.’s three-factor authentication scheme for WSNs. Further, we show that their scheme is vulnerable to de-synchronization attacks and cannot achieve forward secrecy and three-factor security.
- We present a new, lightweight anonymous three-factor authentication with perfect forward secrecy in WSNs. The operation of the scheme is based on a symmetric cryptosystem, so the computational overhead of the scheme is lightweight and the scheme is suitable for WSNs. The new scheme can achieve all known strong security functions with satisfactory performance, including anonymity, perfect forward secrecy, n-factor security, and so on.
- By using the automated security verification tool ProVerif and BAN-logic, we prove that our proposed scheme is secure and realizes the mutual authentication of communication participants in WSNs.
- Through the comparison of security features and performance, it can be found that our proposed scheme is practical.
The rest of this paper is organized as follows. We introduce the relevant preliminaries in Section 2 and review the scheme of Shin et al. in Section 3. In Section 4, the scheme of Shin et al. is subjected to cryptanalysis and the attack method is given. The new scheme is proposed in Section 5, and the security analysis and performance analysis of the new scheme are carried out in Section 6 and Section 7, respectively. Section 8 summarizes the paper.
2. Preliminaries
2.1. Fuzzy Extractor
At different times, there may be subtle differences in the biometrics extracted by the same user. The fuzzy extractor can eliminate these subtle differences. In other words, the fuzzy extractor can produce the same output even if the inputs are slightly different. Fuzzy logic is widely used in supply chains and healthcare logistics [27,28,29]. The fuzzy extractor consists of two parts:
- , with . as input, the probability generation mechanism outputs a random string and a random helper string .
- , with and as inputs, the deterministic mechanism can regenerate , where .
2.2. Adversary Model
In this paper, we adopt the most rigorous (but practical) adversary model proposed by Wang et al. [30] and Huang et al. [31]. Table 1 shows the capabilities of the adversary, .

Table 1.
The capabilities of the adversary.
2.3. Notations
The notations used thereinafter are listed in Table 2.

Table 2.
Notations.
3. Revisiting of Shin et al.’s Scheme
In 2019, Sooyeon Shin et al. proposed a lightweight anonymous three-factor authentication protocol for micro-sensors in wireless sensor networks [26]. Taking their protocol as an example, we analyze and point out the security defects of such authentication protocols.
Shin et al.’s protocol consists of four phases: the initialization phase, registration phase, authentication phase, and password update phase. The system completes the selection of parameters and encryption algorithm in the initialization phase. The registration phase realizes user registration and the distribution of smart cards. The authentication phase completes the mutual authentication and session key agreement between the user and the sensor. It should be noted that the communication channel in the authentication phase is public and insecure.
The specific process of the agreement is as follows:
3.1. Initialization Phase
Step 1: The GWN selects as master secrets and stores them safely.
Step 2: For sensor , the GWN chooses as the identity of and calculates .
Step 3: The sensor stores secretly.
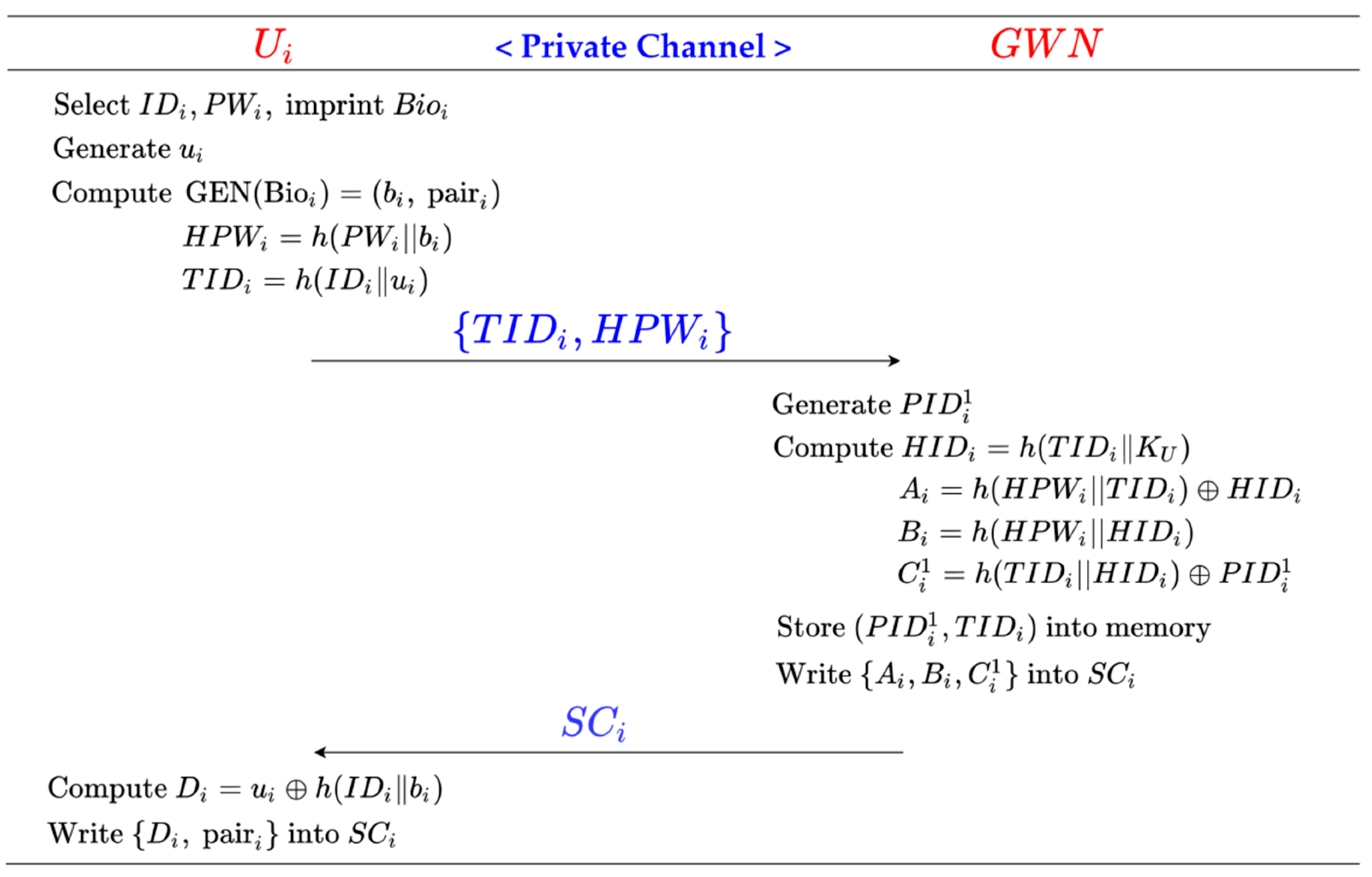
3.2. User Registration Phase
Step 1: The user . selects his identity and password and imprints . Then, chooses a random number and calculates , , and . Further, sends the registration request towards the GWN via a private secure channel.
Step 2: The GWN receives and freely chooses . as a pseudonym. Then, the GWN calculates , , , and . Then, the GWN writes into . and stores . Finally, the GWN transmits towards via a private, secure channel.
Step 3: receives and calculates . Finally, write into .
The process of the User registration phase is shown in Figure 2.
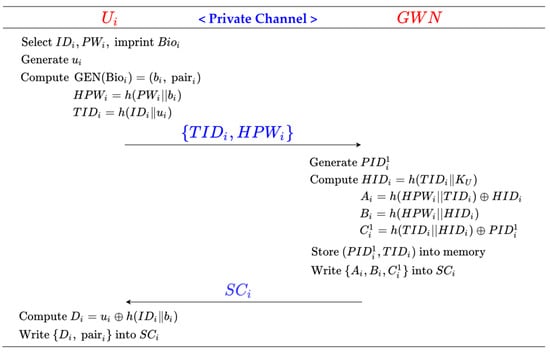
Figure 2.
User registration phase of Shin et al.’s scheme.
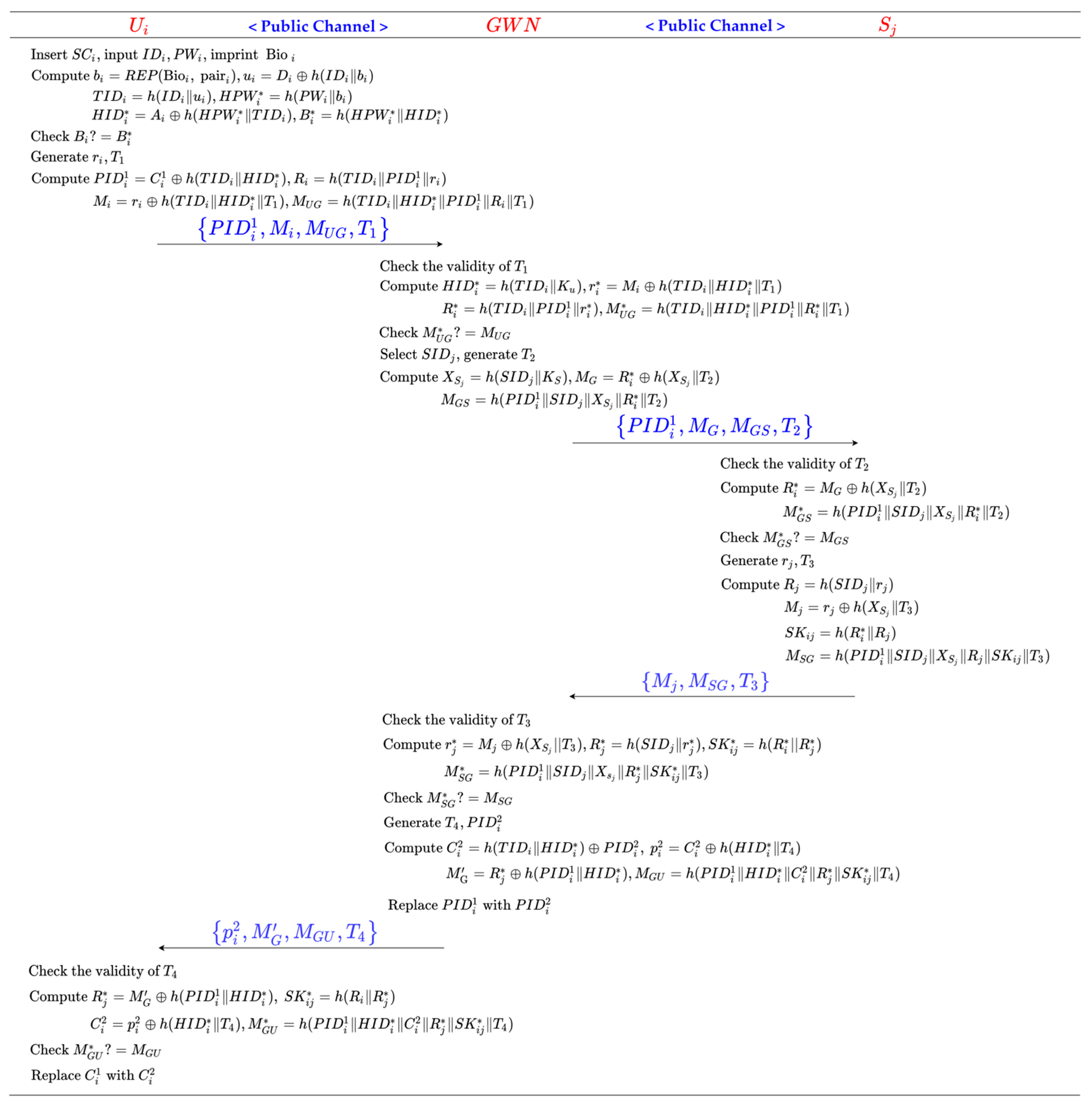
3.3. Authentication Phase
Step 1: inserts , inputs and , and imprints . calculates , , , , , and and verifies the equality check for . If it does not hold true, rejects the login request. Otherwise, generates a random number and the current timestamp , and calculates , , , and . Finally, transmits the login request towards the GWN.
Step 2: The GWN receives and checks the validity of . Then, the GWN searches in memory using and calculates , , , and . Further, the GWN checks the equality of . If it does not hold true, the GWN rejects the login request. Otherwise, the GWN selects , generates the current timestamp , and calculates , , and . Finally, the GWN transmits towards .
Step 3: Upon the reception of from the GWN, checks whether is a valid timestamp. Then, calculates and and verifies the equality check . If the verification fails, aborts the session. Otherwise, generates a random number and the current timestamp , and calculates , , , . Finally, sends back to the GWN.
Step 4: The GWN receives and checks the validity of . Then, the GWN calculates , ,, and and verifies the equality check . If the verification fails, the GWN aborts the session. Otherwise, the GWN generates the current timestamp and a new pseudonym , and calculates , , , and . Finally, the GWN sends back to . and replaces with in memory.
Step 5: receives and checks whether is a valid timestamp. Then, calculates , , , and and checks the equality of . If it holds true, replaces with in .
The process of the authentication phase is shown in Figure 3.
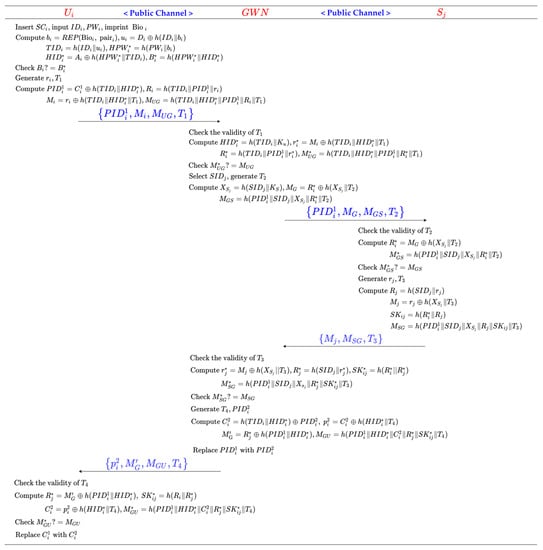
Figure 3.
Authentication phase of Shin et al.’s scheme.
3.4. Password Update Phase
Step 1: inserts to the reader, inputs and , and imprints .
Step 2: calculates , , , , , and and verifies the equality check for . If it does not hold true, rejects the request. Otherwise, inputs a new password .
Step 3: calculates , , and . At last, replaces and with and , respectively.
4. Cryptanalysis of Shin et al.’s Scheme
We show that Shin et al.’s scheme is vulnerable to de-synchronization attacks and can not achieve forward secrecy and three-factor security in this section.
4.1. De-Synchronization Attack
Suppose that an adversary blocks , which is sent from the GWN to . On the side of the GWN, the pseudonym of is at this point. However, is unable to obtain without . Thus, the pseudonyms on the side of and the GWN become out of synchronization. When wants to access a sensor node through the GWN in the next session, the GWN will reject ’s login request. Therefore, Shin et al.’s scheme is vulnerable to de-synchronization attacks.
4.2. Forward Secrecy
Suppose that an adversary occasionally obtains , which is the long-term private key of . Furthermore, the adversary intercepted and in the previous session of and . The adversary could obtain the previous session key of and via following steps.
Step 1: The adversary calculates , , and .
Step 2: The adversary obtains the previous session key of and , .
Therefore, Shin et al.’s scheme can not achieve forward secrecy.
4.3. Three-Factor Security
For a three-factor authentication scheme, when two of the authentication factors are captured by an adversary, it is necessary to ensure that the remaining authentication factor is still secure. Suppose that an adversary captures ’s smart card and biometric simultaneously. The adversary is able to obtain the password of via the following steps.
Step 1: The adversary extracts from using side-channel technology and calculates .
Step 2: The adversary guesses a candidate identity and a candidate password from and , where and are user identity space and password space, respectively.
Step 3: The adversary calculates , , , , and .
Step 4: The adversary checks whether holds. If not, the adversary repeats Steps 2–4 until he acquires the true password. Otherwise, the adversary succeeds in obtaining the true password of .
The computational overhead of this attack is , where is the running time of the one-way hash function, is the running time of the XOR operation, and and are the spaces of user identity and password, respectively. According to the literature [20], we know that . According to the experimental data from the literature [32], , . The adversary can break the password of in 35 days. If you use a high-performance cloud computing platform, the password will be cracked within a few hours.
5. The Proposed Scheme
The proposed protocol includes the following phases: initialization phase, user registration phase, sensor node registration phase, authentication phase, password, and biometric update phase.
The detailed description of the agreement is as follows:
5.1. Initialization Phase
The gateway node GWN creates two information tables in its memory (UserInfoTable and SensorInfoTable), which is used to store relevant information of users and sensors. Then, the GWN freely chooses two master keys, and , and two secure hash functions, and .
5.2. Sensor Registration Phase
The sensor registration phase is completed by the gateway node GWN. The GWN selects a unique identity for each sensor node and calculates . Furthermore, GWN selects two random integers, and c, defines and sets . Then, the GWN inserts the into SensorInfoTable in its memory. Before is deployed, the GWN stores into .
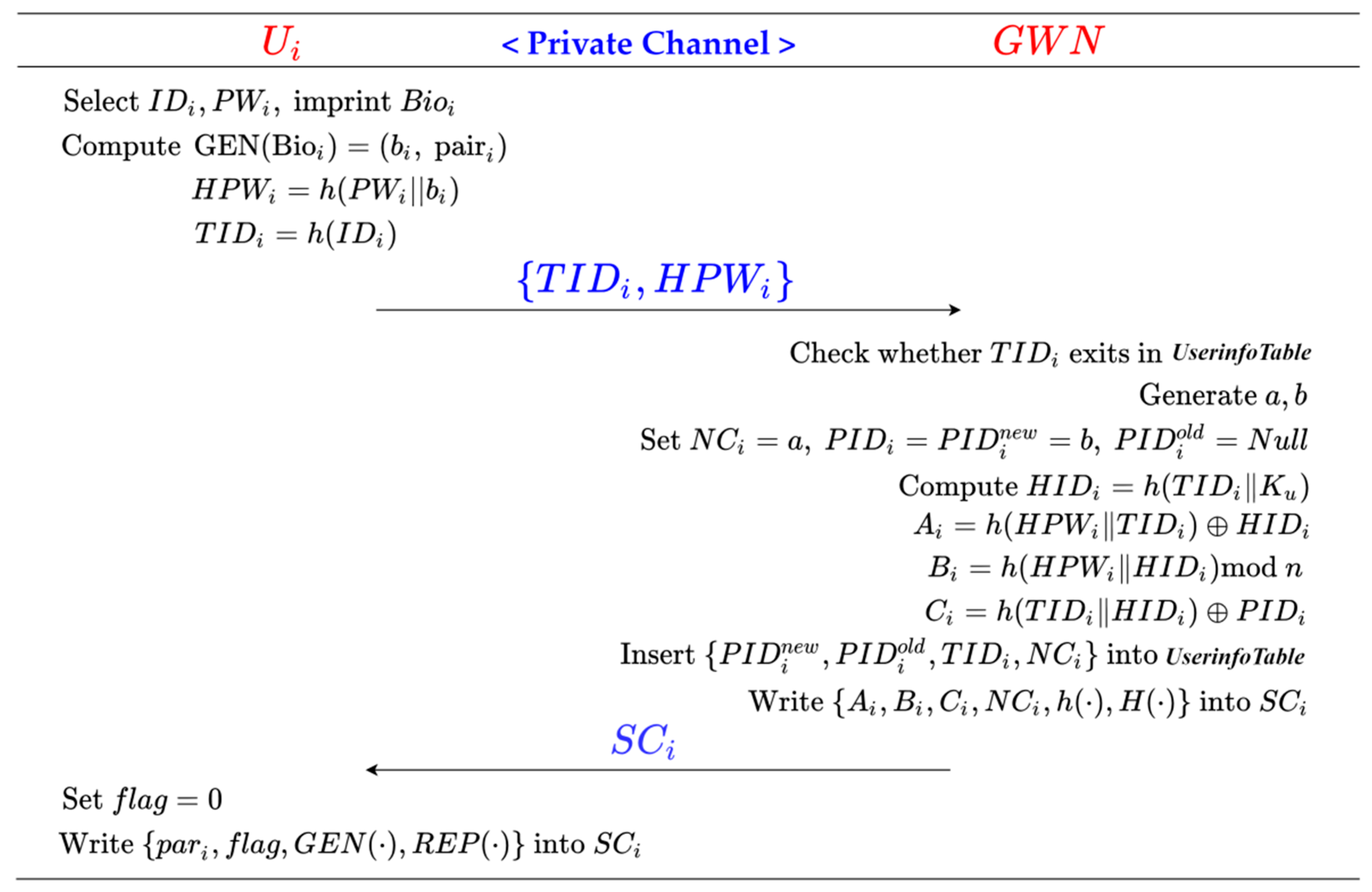
5.3. User Registration Phase
Step 1: chooses and freely, imprints . Then calculates , , and . Finally, sends the registration request towards the GWN via a private secure channel.
Step 2: The GWN receives and checks if UserInfoTable() contains the element . If yes, the GWN rejects the registration request of . Otherwise, the GWN chooses randomly, and sets , , . Then, the GWN calculates , , , and , where is an integer to determine the size of , and inserts the element into table UserInfoTable. Further, the GWN writes into , and transmits towards via a private secure channel.
Step 3: receives , and defines and sets . Finally, writes into .
The process of the user registration phase is shown in Figure 4.
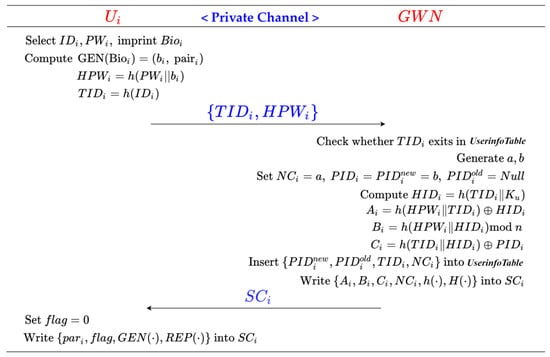
Figure 4.
User registration phase of the proposed scheme.
5.4. Authentication Phase
Step 1: inserts , inputs and , and imprints . calculates , , , , and and verifies the equality check for . If it does not hold true, rejects the login request. Otherwise, checks if holds. If yes, updates , . Then, generates the current timestamp and a random number , chooses which he wants to access and calculates , , , and . Finally, transmits the login request towards the GWN.
Step 2: The GWN receives and checks the validity of . Then, the GWN searches in UserInfoTable using and operates as below.
Case 1: If there exists an element of UserInfoTable which satisfies , then the GWN calculates , , , , , and . The GWN verifies the equality check . If the verification fails, the GWN rejects the login request. Otherwise, the GWN chooses a new randomly, and sets , , .
Case 2: If there exists an element of UserInfoTable which satisfies , then the GWN calculates , , , , and . The GWN verifies the equality check . If the verification fails, the GWN rejects the login request. Otherwise, the GWN chooses a new randomly, and sets .
Case 3: If the above two cases do not exist, the GWN rejects the login request.
Further, the GWN generates the current timestamp , searches in SensorInfoTable using , and updates , . Then, the GWN calculates and . Finally, the GWN transmits towards .
Step 3: Upon the reception of from the GWN, checks whether is a valid timestamp. Then, calculates
and checks if
holds, where is the initial threshold for preserving the computing resources of sensors. If it holds true, sets and calculates
times . Further, calculates and and verifies the equality check . If the verification fails, aborts the session. Otherwise, generates the current timestamp and a random number and calculates , , , and . updates , . Finally, sends back to the GWN.
Step 4: The GWN receives and checks the validity of . Then, the GWN searches in SensorInfoTable using and calculates , and . The GWN verifies the equality check . If the verification fails, the GWN aborts the session. Otherwise, the GWN generates the current timestamp and searches in UserInfoTable using . Further, the GWN calculates , , , and . Finally, the GWN sends to .
Step 5: Upon the reception of from the GWN, checks whether is a valid timestamp. Then, calculates , , , and . Then, verifies the equality check . If the verification fails, aborts the session. Otherwise, updates , .
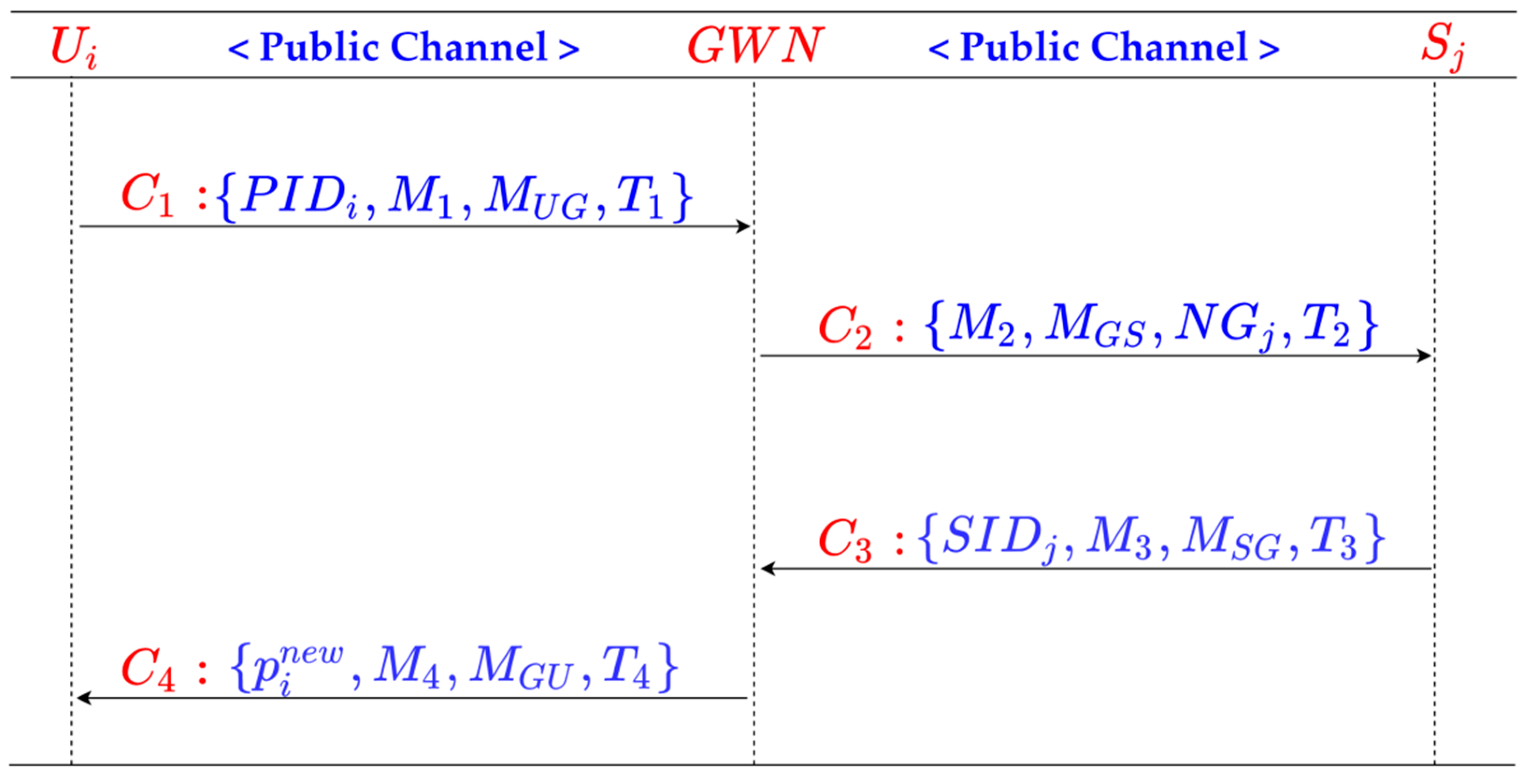
The process of the authentication phase is shown in Figure 5.
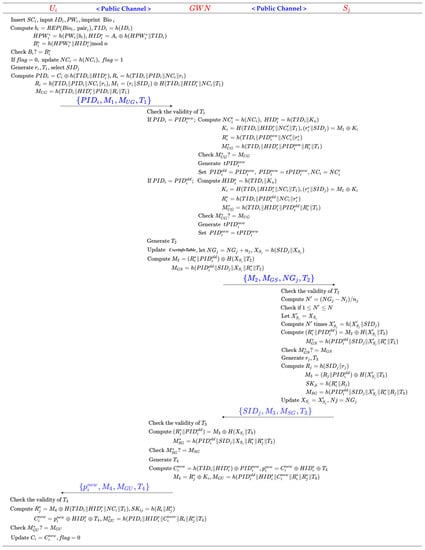
Figure 5.
Authentication phase of the proposed scheme.
5.5. Password and Biometric Update Phase
Step 1: inserts , inputs and , and imprints . calculates , , , , and and verifies the equality check for . If it does not hold true, rejects the request. Otherwise, inputs a new password and imprints a new biometric .
Step 2: calculates , , , and . At last, replaces , and , with , and , respectively.
6. Security Analysis
6.1. Security Verification Using ProVerif
ProVerif [33] is one of the widely accepted automated security verification tools for communication protocols. ProVerif supports main cryptographic primitives including hash function, encryption, digital signatures, etc. In this section, we use ProVerif to check the mutual authentication and session key secrecy of the proposed scheme.
First, we define two insecure channels, c1 for communication between users and the GWN and c2 for communication between the GWN and sensors.
(*--Two public channel--*)
free c1: channel. (*--The channel between users and GWN--*)
free c2: channel. (*--The channel between sensors and GWN--*)
Then, we define the parameters and constructors as follows:
(*--The basic variables--*)
free user, GWN, SN: bitstring. (*---three participants--*)
free PID: bitstring. (*---the pseudonym identity shared by user and GWN--*)
free Ku: bitstring[private]. (*---the masterkey of GWN--*)
free Ks: bitstring[private]. (*---the masterkey of GWN--*)
free XSj: bitstring[private]. (*---the shared key between GWN and sensor--*)
table Table_user_info( bitstring, bitstring, bitstring). (*---the user’s info table---*)
table Table_sensor_info(bitstring, bitstring). (*---the sensor’s info table---*)
(*--Encryption operation--*)
fun encrypt(bitstring, bitstring): bitstring.
fun decrypt(bitstring, bitstring): bitstring.
equation forall x: bitstring, y: bitstring; decrypt(encrypt(x, y), y) = x.
(*--Hash operation--*)
fun h1(bitstring): bitstring.
fun h2 (bitstring, bitstring): bitstring.
fun h4 (bitstring, bitstring, bitstring, bitstring):bitstring.
fun h5 (bitstring, bitstring, bitstring, bitstring, bitstring): bitstring.
fun h6 (bitstring, bitstring, bitstring, bitstring, bitstring, bitstring): bitstring.
(*--XOR operation--*)
fun XOR (bitstring, bitstring): bitstring.
equation forall x: bitstring, y: bitstring; XOR(XOR(x, y), y) = x.
(*--Concat and Divide operation--*)
fun Concat (bitstring, bitstring): bitstring.
fun Div1 (bitstring):bitstring.
fun Div2 (bitstring):bitstring.
equation forall x: bitstring, y: bitstring; Div1(Concat(x, y)) = x.
equation forall x: bitstring, y: bitstring; Div2(Concat(x, y)) = y.
(*--Check the Freshness of timestamp operation--*)
fun isFresh (bitstring, bool): bool
reduc forall T: bitstring; isFresh (T, true) = true.
In order to check the mutual authentication and session key secrecy, we define the following eight events and two secrets:
(*--Mutual authentication queries--*)
event beginUG(bitstring).
event endUG(bitstring).
event beginGU(bitstring).
event endGU(bitstring).
event beginGS(bitstring).
event endGS(bitstring).
event beginSG(bitstring).
event endSG(bitstring).
query x: bitstring; inj-event(endUG(x)) ==> inj-event(beginUG(x)).
query x: bitstring; inj-event(endGU(x)) ==> inj-event(beginGU(x)).
query x: bitstring; inj-event(endGS(x)) ==> inj-event(beginGS(x)).
query x: bitstring; inj-event(endSG(x)) ==> inj-event(beginSG(x)).
(*--Session key secrecy queries--*)
free secretA, secretB: bitstring [private].
query attacker(secretA);
attacker(secretB).
Three distinct processes processUser, processSensor, and processGWN are declared to model , and GWN, respectively.
(*----------------User Ui---------------------*)
let processUser(IDi: bitstring, PWi: bitstring, bi: bitstring, Ai: bitstring, Bi: bitstring, Ci: bitstring, NCi: bitstring, SIDj: bitstring) =
let TIDi = h1(IDi) in
let HPWi’ = h2(PWi, bi) in
let HIDi’ = XOR(Ai, h2(HPWi’, TIDi)) in
let Bi’ = h2(HPWi’,HIDi’) in
if Bi’=Bi then
event beginGU(GWN);
new ri: bitstring;
new T1: bitstring;
let PIDi = XOR(Ci, h2(TIDi, HIDi’)) in
let Ri = h4(TIDi, PIDi, NCi, ri) in
let M1 = XOR(Concat(ri, SIDj), h4 TIDi, HIDi’, NCi, T1)) in
let MUG = h5 (TIDi, HIDi’, PIDi, Ri, T1) in
out (c1, (PIDi, M1, MUG, T1));
in (c1, (M4:bitstring, MGU:bitstring, T4:bitstring));
if isFresh (T4, true) = true then
let Rj’ = XOR(M4,h4(TIDi, HIDi’,NCi, T1)) in
let SKij’ = h2(Ri, Rj’) in
let MGU’ = h5(PIDi, HIDi’, Ri, Rj’, T4) in
if MGU’ =MGU then
event endUG(user);
out(c1, encrypt(secretA, SKij’)).
(*----------------GWN---------------------*)
let processGWN() =
in(c1, (PIDi: bitstring, M1: bitstring, MUG: bitstring, T1:bitstring));
if isFresh(T1, true) = true then
get Table_user_info(=PIDi, TIDi, NCi) in
let HIDi’ = h2(TIDi, Ku) in
let Ki = h4(TIDi, HIDi’, NCi, T1) in
let ri’ = Div1(XOR(M1,Ki)) in
let SIDj = Div2(XOR(M1,Ki)) in
let Ri’ = h4(TIDi, PIDi, NCi, ri’) in
event beginUG(user);
let MUG’ = h5(TIDi, HIDi’, PIDi, Ri’, T1) in
if MUG’ =MUG then
event beginSG(SN);
new T2: bitstring;
get Table_sensor_info(=SIDj, XSj) in
let M2 = XOR(Concat(Ri’, PIDi),h2(XSj, T2)) in
let MGS = h5(PIDi, SIDj, XSj, Ri’, T2) in
out(c2, (M2, MGS, T2));
in(c2,(SIDj:bitstring, M3:bitstring, MSG:bitstring, T3: bitstring));
if isFresh(T3, true) = true then
let Rj’ = Div1(XOR(M3,h2(XSj, T3))) in
let PIDi = Div2(XOR(M3, h2(XSj, T3))) in
let MSG’ = h6(PIDi, SIDj, XSj, Ri’,Rj’, T3) in
if MSG’ = MSG then
new T4: bitstring;
event endGS(GWN);
let M4 = XOR(Rj’,Ki) in
let MGU = h5(PIDi, HIDi’, Ri’, Rj’, T4) in
out(c1, (M4, MGU, T4));
event endGU(GWN);
0.
(*----------------Sensor Sj---------------------*)
let processSensor(SIDj:bitstring, XSj:bitstring) =
in(c2, (MG:bitstring, MGS:bitstring, T2:bitstring));
event beginGS(GWN);
let Ri’ =Div1(XOR(MG, h2(XSj, T2))) in
let PIDi =Div2(XOR(MG, h2(XSj, T2))) in
let MGS’ = h5(PIDi, SIDj, XSj, Ri’, T2) in
if MGS’=MGS then
new T3: bitstring;
new rj: bitstring;
let Rj = h2(SIDj, rj) in
let Mj = XOR(Concat(rj, PIDi),h2(XSj, T3)) in
let SKij = h2(Ri’, Rj) in
let MSG = h6(PIDi, SIDj, XSj, Ri’, Rj, T3) in
out(c2, (SIDj, Mj, MSG, T3));
event endSG(SN);
out(c2, encrypt(secretB, SKij)).
We simulate the unbounded parallel execution of processes processUser, processSensor, and processGWN as follows:
(*--Start process--*)
process
new IDi: bitstring;
new PWi: bitstring;
new bi: bitstring;
new PIDi: bitstring;
new SIDj: bitstring;
new NCi: bitstring;
let HPWi = h2(PWi, bi) in
let TIDi = h1(IDi) in
let HIDi = h2(TIDi, Ku) in
let Ai = XOR(h2(HPWi, TIDi), HIDi) in
let Bi = h2(HPWi, HIDi) in
let Ci = XOR(h2(TIDi, HIDi),PIDi) in
let XSj = h2(SIDj, Ks) in
insert Table_user_info(PIDi, TIDi, NCi);
insert Table_sensor_info(SIDj, XSj);
(
(*-- Launch an unbounded number of sessions of the user --*)
(!processUser(IDi, PWi, bi, Ai, Bi, Ci, NCi, SIDj)) |
(*-- Launch an unbounded number of, sessions of the GWN--*)
(!processGWN()) |
(*-- Launch an unbounded number of sessions of the sensor--*)
(!processSensor(SIDj, XSj))
)
The simulation results are shown as follows:
Query inj-event(endUG(x)) ==> inj-event(beginUG(x)) is true.
Query inj-event(endGU(x)) ==> inj-event(beginGU(x)) is true.
Query inj-event(endGS(x)) ==> inj-event(beginGS(x)) is true.
Query inj-event(endSG(x)) ==> inj-event(beginSG(x)) is true.
Query not attacker(secretA[]) is true.
Query not attacker(secretB[]) is true.
The results mean that the proposed scheme is able to achieve mutual authentication. Meanwhile, the session key SKij generated by the user and the sensor is secure.
6.2. BAN-Logic
Burrows–Abadi–Needham logic (BAN-logic) [34] is a widely used tool for the formal analysis of authentication schemes which was proposed by Burrows et al. In this section, we use BAN-logic to prove the session key agreement between the user and the sensor node after the execution of the proposed scheme. Table 3 introduces the notations for the BAN-logic analysis and some basic rules for BAN-logic are described in Table 4.

Table 3.
BAN-logic notations.

Table 4.
Basic logical postulates of BAN-logic.
- (1)
- The idealized form of the proposed scheme:Message 1:Message 2:Message 3:Message 4:
- (2)
- Verification goals:Goal 1: .Goal 2: .Goal 3: .Goal 4: .
- (3)
- Assumptions about the initial state:A1: .A2: .A3: .A4: .A5: .A6: .A7: .A8: .A9:
- (4)
- Proofs:Step 1: From Message 1, we can get: .Step 2: According to Step 1, A5, and the message meaning rule, it can be inferred that: .Step 3: According to Step 2, A3, and the nonce verification rule, we obtain: .Step 4: From Message 2, we understand that: .Step 5: According to A7 and the message meaning rule, we obtain: .Step 6: According to A2, , and the freshness conjuncatenation rule, we can get: .Step 7: According to Step 5, Step 6, and the nonce verification rule, we get: .Step 8: According to Step 3, Step 7, , and , we prove: (Goal 4).Step 9: According to Step 8, A9, and the jurisdiction rule, we prove: (Goal 3).Step 10: According to Message 3, we get: .Step 11: According to Step10, A6, and the message meaning rule, it can be inferred that: .Step 12: According to Step 11, A3, , and the nonce verification rule, we obtain: .Step 13: From Message 4, we obtain: .Step 14: According to Step 13, A4, and the message meaning rule, we obtain: .Step 15 According to Step 14, A1, , and the nonce verification rule, we get: . (Goal 2).Step 16: According to Step 15, A8, and the jurisdiction rule, we prove: (Goal 1).
From the proof results obtained from the above process, Goal 1–4, , and believe that they have completed the key agreement and generated the shared session key .
6.3. Informal Security Analysis
(1) Anonymity and un-traceability
Suppose an adversary intercepted the information transmitted to a public channel from , , and . Obviously, the adversary cannot obtain the user’s actual identity , because of the security of the one-way hash function. In addition, the pseudonym identity changes after each authentication, and and are randomly generated in each session. The adversary cannot determine whether two sessions are launched by the same user.
(2) Perfect forward secrecy
Suppose an adversary accidentally captured ’s private key , ’s private key (, ), and the GWN’s master key (, ), and intercepted the information propagated in the public channel. The adversary cannot obtain the previous session key because changes after each authentication, and the adversary cannot get the in a previous session because of the security of the one-way hash function. Therefore, the proposed scheme can achieve perfect forward secrecy.
(3) Mutual authentication
In Section 6.1, we define eight events—event beginUGparam(bitstring), event endUGparam(bitstring), event beginGUparam(bitstring), event endGUparam(bitstring), event beginGSparam(bitstring), event endGSparam(bitstring), event beginSGparam(bitstring), and event endSGparam(bitstring)—to verify the mutual authentication of , , and . The results show that our proposed scheme could achieve mutual authentication.
(4) Session key agreement
The user and the sensor reach a session key for future communication after authentication. Since and are generated by and , respectively, both and have an influence on the outcome of the session key .
(5) Three-factor security
Suppose an adversary captured the smart card of and obtained the biometrics . The adversary can extract the values in . Further, the adversary guesses and calculates , , , , and . However, the adversary does not know the correctness of because . is a fuzzy verification process.
(6) Resistance of other known attacks
Insider attack: An insider adversary can obtain the user’s registration information . Because of the security of the one-way hash function and ignorance about , the adversary cannot capture . Therefore, no effective insider attack can be launched.
Stolen verifier table attack: There is no password-related or biometric-related information stored inside the GWN. Therefore, the stolen verifier table attack is infeasible in our proposed scheme.
User impersonation attack: For generating valid login request information, the adversary needs to know . While we know , , , and , where and are stored in . Therefore, the adversary cannot forge without getting , , and . Thus our proposed scheme could resist user impersonation attacks.
Sensor Spoofing Attack: An adversary cannot forge a sensor node without getting the secrets of ( and ). Therefore, no effective sensor spoofing attack can be launched.
Known session-specific temporary information attack: In our proposed scheme, the user and the micro-sensor reach a session key . Even if an adversary captured the session-specific temporary information, and , he cannot launch a known session-specific temporary information attack without . As a result, our proposed scheme can resist known session-specific temporary information attacks.
De-synchronization attack: We analyze five possible cases of de-synchronization attacks, shown in Figure 6.
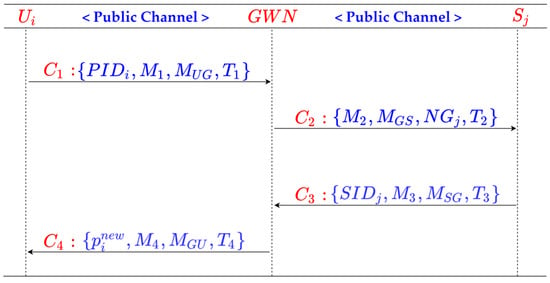
Figure 6.
Possible de-synchronization attack on our proposed protocol.
Case 1: Suppose an adversary blocked . Since none of the participants updated the information table, the attack is infeasible.
Case 2: Suppose an adversary blocked , the information stored on the GWN side and sensor side would be out of synchronization. However, by calculating
, it can be known how many times the communications between and the GWN are blocked. The information on two sides would be resynchronized by calculating times and updating , .
Case 3: If an adversary blocks . Both the GWN and have updated the and . The synchronization between and the GWN is the same as Case 4.
Case 4: If an adversary blocks . The communications between the GWN and are in synchronization, while the communications between and the GWN are out of synchronization. In this case, the GWN has completed the update of , and records the previous . Since is not received, the user does not update , and the calculated in the next session is not updated. However, when initiates the session request again, the GWN finds that the sent by is the same as the recorded in its memory. The GWN can identify the de-synchronization attack initiated by the adversary and synchronize the information according to Step 2 of the authentication phase. Therefore, the proposed new protocol can also resist the attacks of Case 3 and Case 4 of de-synchronization attacks.
In summary, our proposed scheme can resist de-synchronization attacks. On the other hand, we have shown that our proposed scheme can achieve forward secrecy in previous part of this section. Therefore, our proposed scheme can resist offline password-guessing attacks and stolen smart card attacks.
7. Performance Analysis
This section will compare and analyze the performance of the proposed new protocol with other similar protocols, including a computing cost comparison and communication cost comparison. Since the registration phase of users and sensors occurs only once, and users do not change their passwords and biometrics frequently, this section only discusses the performance comparison between authentication phases.
7.1. Comparison of Computing Costs
According to the experimental data in the literature [35], , the computing cost comparison between our proposed scheme and other similar schemes, is shown in Table 5. From the results, the proposed protocol has a lower computation cost than the other four similar protocols.

Table 5.
Comparison of computing costs (milliseconds).
7.2. Comparison of Communication Costs
We assume that the length of identification, random number, timestamp, and other parameters involved in the proposed protocol and other similar protocols is 128 bits, and the length of the timestamp is 32 bits. Hash functions and have 128-bit and 256-bit outputs, respectively. Other related protocols use hash functions (such as MD5) with an output length of 128 bits.
In the authentication phase of the newly proposed protocol, there are four transmission messages: , , , and . The total length of the transmitted message is (128 + 256 + 128 + 32) + (256 + 128 + 128 + 32) + (128 + 256 + 128 + 32) + (128 + 128 + 128 + 32) = 2048 bits.
Table 6 shows the comparison of the communication costs between the proposed new protocol and other similar schemes. From the comparison results, our new proposed scheme is also at a good level in terms of communication costs.

Table 6.
Comparison of communication costs.
8. Conclusions
Due to the insecurity of wireless sensor networks, abundant research on authentication and key agreement protocols for WSNs has been put forward. In 2019, Shin et al. proposed a lightweight three-factor authentication and key agreement protocol based on symmetric cryptographic primitives for WSNs, which looked promising. However, we found that there are some security risks in their protocol. To solve the shortcomings, we proposed a new lightweight and anonymous three-factor authentication scheme for WSNs. Furthermore, we proved that our proposed scheme is secure using the automated security verification tool ProVerif, BAN-logic verification, and an informal security analysis. Through a performance comparison and analysis, our new scheme shows a good level of computing and communication overhead and has high practicability. In future research, we will focus on finding a lighter mathematical model to realize the strong security of identity authentication in wireless sensor networks and apply the scheme to the actual environment.
Author Contributions
Conceptualization, L.Z.; Formal analysis, H.X.; Investigation, H.X.; Methodology, L.Z.; Supervision, H.X. and K.Z.; Validation, K.Z.; Writing—original draft, L.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Project of Educational Commission of Guangdong Province (No.6019210033S), Shenzhen Fundamental Research Project (No.JCYJ20180305163701198), Shenzhen Bureau of Education (No.zdzz20002).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Gnawali, O.; Jang, K.-Y.; Paek, J.; Vieira, M.; Govindan, R.; Greenstein, B.; Joki, A.; Estrin, D.; Kohler, E. The tenet architecture for tiered sensor networks. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems ACM, Boulder, CO, USA, 31 October–3 November 2006; pp. 153–166. [Google Scholar]
- Yang, D.; Misra, S.; Fang, X.; Xue, G.; Zhang, J. Two-Tiered Constrained Relay Node Placement in Wireless Sensor Networks: Computational Complexity and Efficient Approximations. IEEE Trans. Mob. Comput. 2011, 11, 1399–1411. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J.; Yang, L.T. Security Analysis and Improvement of a Secure and Distributed Reprogramming Protocol for Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2012, 60, 5348–5354. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Guo, H.; Gao, Y.; Xu, T.; Zhang, X.; Ye, J. A secure and efficient three-factor multi-gateway authentication protocol for wireless sensor networks. Ad Hoc Networks 2019, 95, 101965. [Google Scholar] [CrossRef]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and Physically Secure Anonymous Mutual Authentication Protocol for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Ever, Y.K. Secure-anonymous user Authentication scheme for e-healthcare application using wireless medical sensor networks. IEEE Syst. J. 2018, 13, 456–467. [Google Scholar] [CrossRef]
- Adavoudi-Jolfaei, A.H.; Ashouri-Talouki, M.; Aghili, S.F. Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer-to-Peer Netw. Appl. 2019, 12, 43–59. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Mishra, D.; Vijayakumar, P.; Sureshkumar, V.; Amin, R.; Islam, S.K.H.; Gope, P. Efficient authentication protocol for secure multimedia communications in IoT-enabled wireless sensor networks. Multimed. Tools Appl. 2018, 77, 18295–18325. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Futur. Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and provably secure three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 2018, 11, 1–20. [Google Scholar] [CrossRef]
- Ramachandran, S.; Shanmugam, V. A two way authentication using bilinear mapping function for wireless sensor networks. Comput. Electr. Eng. 2017, 59, 242–249. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A Realistic Lightweight Anonymous Authentication Protocol for Securing Real-Time Application Data Access in Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Arshad, H.; Khan, M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Futur. Gener. Comput. Syst. 2016, 63, 56–75. [Google Scholar] [CrossRef]
- Xiong, L.; Peng, D.; Peng, T.; Liang, H.; Liu, Z. A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks. Sensors 2017, 17, 2681. [Google Scholar] [CrossRef] [Green Version]
- Wong, K.H.M.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC ’06), Taichung, Taiwan, 5–7 June 2006; Volume 1, p. 8. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- He, D.; Gao, Y.; Chan, S.; Chen, C.L.P. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Networks 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Networks 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T. A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes. Sensors 2019, 19, 2012. [Google Scholar] [CrossRef] [Green Version]
- Fathollahi-Fard, A.M.; Dulebenets, M.A.; Hajiaghaei–Keshteli, M.; Tavakkoli-Moghaddam, R.; Safaeian, M.; Mirzahosseinian, H. Two hybrid meta-heuristic algorithms for a dual-channel closed-loop supply chain network design problem in the tire industry under uncertainty. Adv. Eng. Inform. 2021, 50, 101418. [Google Scholar] [CrossRef]
- Fathollahi-Fard, A.M.; Ahmadi, A.; Karimi, B. Multi-Objective Optimization of Home Healthcare with Working-Time Balancing and Care Continuity. Sustainability 2021, 13, 12431. [Google Scholar] [CrossRef]
- Fallahpour, A.; Wong, K.Y.; Rajoo, S.; Fathollahi-Fard, A.M.; Antucheviciene, J.; Nayeri, S. An integrated approach for a sustainable supplier selection based on Industry 4.0 concept. Environ. Sci. Pollut. Res. 2021, 1–19. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.-H. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Huang, X.; Xiang, Y.; Chonka, A.; Zhou, J.; Deng, R. A Generic Framework for Three-Factor Authentication: Preserving Security and Privacy in Distributed Systems. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 1390–1397. [Google Scholar] [CrossRef]
- Wang, D.; Gu, Q.; Cheng, H.; Wang, P. The request for better measurement: A comparative evaluation of two-factor authentication schemes. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security ACM, Xi’an, China, 30 May–3 June 2016; pp. 475–486. [Google Scholar]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 2.00: Automatic Cryptographic Protocol Verifier, User Manual and Tutorial. 2018. Available online: https://prosecco.gforge.inria.fr/personal/bblanche/proverif (accessed on 15 October 2021).
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proceedings of the Royal Society of London. A. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- He, D.; Kumar, N.; Lee, J.-H.; Sherratt, R. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Futur. Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).