Abstract
Internet of Things (IoT) is composed of various kinds of devices such as cars, electrical appliances, machines and sensors. With IoT technologies, devices can exchange information through the network, people are allowed to get information collected by devices without interacting with them, and automatic operations for devices are realized. Because of the variety of IoT devices, some of them possess limited computational capability. On the other hand, data transmission in IoT networks is usually through a public channel. To ensure efficiency and security for IoT environments, Lee et al. proposed a three-factor authentication scheme with hash function and XOR operation. They claimed their scheme possessed superior properties and could resist common attacks. After analyzing their scheme, we find that their scheme is vulnerable to five flaws. In this paper, how these found flaws threaten Lee et al.’s scheme is shown in detail. Then, we propose an improvement to overcome the found flaws and preserve the advantages by employing ECC.
1. Introduction
With the rapid development of network technologies, plenty of new applications are proposed and realized. Internet of Things is a new concept that entities can communicate with each other, and entities include various kinds of devices such as cars, electrical appliances, machines and sensors. With IoT technologies, devices can exchange information through the network, people are allowed to get information collected by devices without interacting with them, and automatic operations for devices are realized. There are many IoT applications such as Machine-to-Machine (M2M) communication, Telemedicine Information System (TMIS), Internet of Vehicles (IoV), Smart Home, Industrial of IoT (IIoT), and Smart City. Because data transmission in IoT networks is usually through a public channel, how to protect the security of transmitted data and user privacy for IoT becomes an urgent issue. On the other hand, anonymity becomes an essential issue. Anonymous communication is designed from physical layer to application layer. Various applications and technologies are designed to meet the goal [1,2,3,4,5,6].
In 2014, Turkanović et al. proposed a new IoT notion-based authentication and key agreement scheme to protect the security of heterogeneous ad hoc wireless sensor networks [7]. Their scheme uses light-weight operations, hash function and XOR operations, and provides functions including mutual authentication, key agreement, password change and dynamic node addition. They also claimed that their scheme could resist various kinds of threats while reducing cost and ensuring performance at the same time. In 2016, Farash et al. [8] found that Turkanović et al.’s scheme suffers from some security flaws such as user traceability, no sensor node anonymity, stolen smart card attack, disclosure of the session key, man-in-the-middle attack. Farash et al. also proposed a new user authentication and key agreement scheme to overcome the flaw that Turkanović et al.’s scheme suffers from and preserve the advantages of it. However, Amin et al. [9] found that Farash et al.’s scheme is still vulnerable to some weaknesses such as compromised user anonymity, known session-specific temporary information attack, offline password guessing attack using stolen smart cards, and insecure secret keys of gateway nodes. Meanwhile, Amin et al. proposed an anonymous-preserving three-factor authenticated key exchange protocol for wireless sensor networks to overcome the security flaws that Farash et al.’s scheme suffers from. In 2017, Jiang et al. [10] found that Amin et al.’s scheme suffers from loss of smart card attacks (SCLA), offline password guessing attack, lack of user untraceability, and known session-specific temporary information attack. Therefore, they proposed a lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. Jiang et al.’s scheme uses the Rabin cryptosystem to withstand tracking and smart card loss attack, uses biometric technologies to realize local password authentication to defend against offline password guessing attack, and uses time stamp mechanism to resist known session-specific temporary information attack. They claimed that their scheme could overcome the weaknesses of Amin et al.’s scheme and ensure key agreement with the higher computational load.
In 2018, Zhang et al. proposed a privacy protection mechanism for E-Health systems by means of dynamic authentication and three-factor key agreement [11]. They claimed that biometric identification on the server could be performed while the server could not get the value of biometrics. In order to protect user anonymity, dynamic authentication instead of traditional password table is adopted. Zhang et al.’s scheme uses hash function and bio-hash function to reduce computational cost and transmission cost and meet the security requirements of electronic medical systems. However, in 2019, Aghily et al. [12] found that there exist serious security vulnerabilities in Zhang et al.’s scheme, including user traceability, desynchronization attack, internal attack and denial-of-service attack. Therefore, they proposed a lightweight three-factor authentication, access control and ownership transfer scheme for E-Health systems in IoT to overcome the weaknesses that Zhang et al.’s scheme suffers from and provide an access control mechanism such that a patient’s current doctor can transfer the corresponding authority to a new doctor.
Inspired by the previous mechanisms, Lee et al. proposed a three-factor anonymous user authentication scheme for Internet of Things environments [13]. Lee et al. claimed that their scheme could resist stolen mobile device attack, user impersonation attack, replay attack, stolen-verifier attack, privileged-insider attack, sensor node impersonation attack and session-specific temporary information attack, and it could ensure user anonymity, user untraceability, mutual authentication, session key agreement, local user verification, user-friendly password change, and forward secrecy. They also claimed that their scheme could revoke users’ devices to prevent the abuse or disclosure of confidential information when devices are lost or stolen. However, after analyzing their scheme thoroughly, we find that their scheme suffers from some flaws including failure sensor node authentication, failure mobile node authentication, replay attack, denial-of-service attack, and compromised user untraceability.
2. Review of Lee et al.’s Scheme
Lee et al.’s scheme uses XOR operation, hash function and symmetric cryptography to ensure efficiency. There exist three entities in their scheme, mobile node, IoT node and gateway. At first, mobile nodes and IoT nodes need to register with the gateway. Thereupon, registered users can access services provided by IoT nodes with the smart device via the gateway’s help. Lee et al.’s scheme consists of four phases: registration phase, login and authentication phase, password change phase, and revocation phase. Notations used in Lee et al.’s scheme are listed in Table 1. The details are as follows.

Table 1.
Notations used in Lee et al.’s scheme.
2.1. Registration Phase
In Lee et al.’s scheme, registration phase is composed two phases: user registration phase and IoT node registration phase. In the following, these two parts are shown in detail.
2.1.1. User Registration Phase
When a mobile node MNi wants to access the IoT service, MNi needs to register with the gateway GW. In this phase, data is transmitted through a secure channel. This phase is depicted in Figure 1, and the details are as follows:
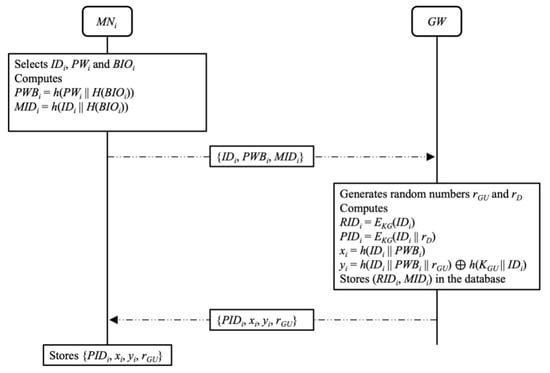
Figure 1.
User registration phase of Lee et al.’s scheme.
- Step 1.
- First, MNi chooses its identity IDi, password PWi, and biometrics BIOi. Then MNi computes PWBi = h(PWi || H(BIOi)) and MIDi = h(IDi || H(BIOi)).
- Step 2.
- MNi sends {IDi, PWBi, MIDi} to GW.
- Step 3.
- Upon receiving {IDi, PWBi, MIDi}, GW selects random numbers rGU and rD. Then GW computes RIDi = , PIDi = , xi = h(IDi || PWBi) and yi = h(IDi || PWBi || rGU) ⊕ h(KGU || IDi). GW stores (RIDi, MIDi) in its database.
- Step 4.
- GW sends {PIDi, xi, yi, rGU} to MNi.
- Step 5.
- Upon receiving {PIDi, xi, yi, rGU}, MNi stores {PIDi, xi, yi, rGU} in the mobile device.
2.1.2. IoT Node Registration
Before being added to the IoT network, a sensor node Nj needs to register with GW. In this phase, data is transmitted through a public channel. This phase is depicted in Figure 2, and the details are as follows:
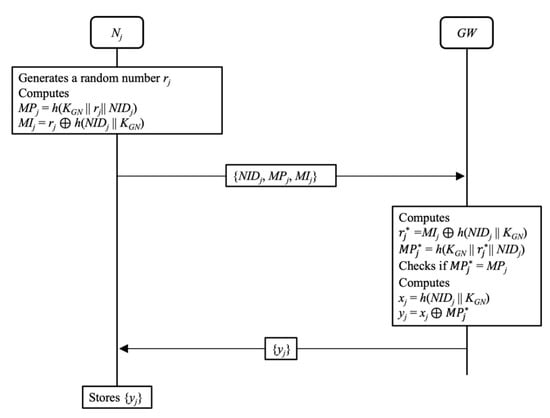
Figure 2.
IoT node registration phase of Lee et al.’s scheme.
- Step 1.
- First, Nj chooses a random number rj. Then Nj computes MPj = h(KGN || rj || NIDj) and MIj = rj ⊕ h(NIDj || KGN)
- Step 2.
- Nj sends {NIDj, MPj, MIj} to GW.
- Step 3.
- After receiving {NIDj, MPj, MIj}, GW uses the secret key KGN to compute rj* = MIj ⊕ h(NIDj || KGN) and MPj* = h(KGN || rj* || NIDj). Then GW checks whether MPj* = MPj holds or not. If it holds, GW computes xj = h(NIDj || KGN) and yj = xj ⊕ MPj*.
- Step 4.
- GW sends {yj} to Nj.
- Step 5.
- Upon receiving {yj}, Nj stores {yj} in its memory.
2.2. Login and Authentication Phase
After registration, registered MNi can access IoT services provided by registered Nj. In this phase, MNi and Nj authenticate each other, and a shared session key is negotiated for secure communication. In this phase, data is transmitted through a public channel. This phase is depicted in Figure 3, and the details are as follows:
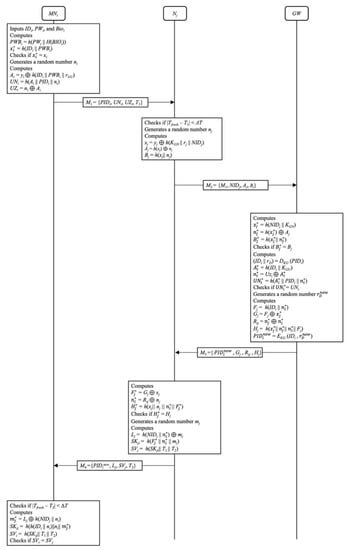
Figure 3.
Login and authentication phase of Lee et al.’s scheme.
- Step 1.
- MNi enters its identity IDi, password PWiold, and biometric BIOi. MNi computes PWBi = h(PWi || H(BIOi)) and xi* = h(IDi || PWBi). Then MNi checks whether xi* = xi holds or not. If it holds, MNi generates a random number ni and computes Ai = yi ⊕ h(IDi || PWBi || rGU), UNi = h(Ai || PIDi || ni) and UZi = ni ⊕ Ai; otherwise, MNi terminates this phase immediately.
- Step 2.
- MNi gets the current timestamp T1 and sends M1 = {PIDi, UNi, UZi, T1} to Nj.
- Step 3.
- Upon receiving M1, Nj checks whether |Tfresh - T1| ≤ ΔT holds or not. If it holds, Nj generates a random number nj and computes xj = yj ⊕ h(KGN || rj || NIDj), Aj = h(xj) ⊕ nj, and Bj = h(xj || nj).
- Step 4.
- Nj sends M2 = {M1, NIDj, Aj, Bj} to GW.
- Step 5.
- Upon receiving M2 from Nj, GW computes xj* = h(NIDj || KGN), nj* = h(xj*) ⊕ Aj, and Bj* = h(xj* || nj*). GW checks whether Bj* = Bj holds or not. If it does not hold, GW terminates this phase immediately; otherwise, this phase proceeds. GW decrypts PIDi with its private secret KG to obtain {IDi, rD} stored in the database for MNi. Then GW computes Ai* = h(IDi || KGU), ni* = UZi ⊕ Ai* and UNi* = h(Ai* || PIDi || ni*) and checks whether UNi* = UNi holds or not. If it does not hold, GW terminates this phase immediately; otherwise, this phase proceeds. GW generates a random number rDnew and computes Fj = h(IDi || ni*), Gj = Fj ⊕ xj*, Rij = nj* ⊕ ni*, Hj = h(xj* || nj* || ni* || Fj), and PIDinew = (IDi, rDnew).
- Step 6.
- GW sends M3 = {PIDinew, Gj, Rij, Hj } to Nj.
- Step 7.
- Upon receiving M3 from GW, Nj computes Fj* = Gj ⊕ xj, ni* = Rij ⊕ nj, and Hj* = h(xj || nj || ni* || Fj*) and checks if whether Hj* = Hj holds or not. If it does not hold, Nj terminates this phase immediately; otherwise, Nj generates a random number mj and computes Lj = h(NIDj || ni*) ⊕ mj, SKji = h(Fj* || ni* || mj), and SVj = h(SKji || T1 || T2).
- Step 8.
- Nj sends M4 = {PIDinew, Lj, SVj, T2} to MNi.
- Step 9.
- Upon receiving M4 from Nj, MNi checks whether |Tfresh - T2| ≤ ΔT holds or not. If it holds, Nj computes mj* = Lj ⊕ h(NIDj || ni), SKji = h(h(IDi || ni) || ni || mj*), and SVi = h(SKji || T1 || T2). If SVi is equal to SVj, MNi and Nj have successfully negotiated a session key that can be used to ensure the security of subsequent communication.
2.3. Password Change Phase
MNi’s password can be changed on its smart device, and the details of this phase are shown as follows:
- Step 1.
- MNi enters its identity IDi, original password PWiold, new password PWinew, and biometric BIOi. Then MNi computes PWBiold = h(PWiold || H(BIOi)) and xi* = h(IDi || PWBiold).
- Step 2.
- MNi checks whether xi* is equal to xi or not. If they are equal, MNi computes Ai = yi ⊕ h(IDi || PWBiold || rGU), PWBinew = h(PWinew || H(BIOi)), xinew = h(IDi || PWBinew) and yinew = h(IDi || PWBinew || rGU) ⊕ Ai ⊕ yi.
- Step 3.
- At last, MNi updates xiold and yiold with xinew and yinew, respectively. Then MNi’s password is updated with PWinew.
2.4. Revocation Phase
When MNi wants to revoke or reissue a secret parameter, revocation phase will be performed. In this phase, data is transmitted through a secure channel, and the details are as follows.
- Step 1.
- MNi inputs its original identity IDiold, new identity IDinew, new password PWinew, and biometric BIOi into the mobile device. Then MNi computes PWBinew = h(PWinew || H(BIOi)), MIDiold = h(IDiold || H(BIOi)), and MIDinew = h(IDinew || H(BIOi)).
- Step 2.
- MNi sends the revocation request {IDiold, IDinew, MIDiold, MIDinew, PWBinew} to GW.
- Step 3.
- Upon receiving the revocation request from MNi, GW computes RIDiold = (IDiold) to verify MNi’s identiy and searches (RIDi, MIDi) in the database to find the specific registered user. If (RIDi, MIDi) is equal to (RIDiold, MIDiold), the identity of MNi has been verified successfully. Then GW generates new random numbers rDnew and rGUnew and computes PIDinew = (IDi || rDnew), RIDinew = (IDinew), xinew = h(IDi || PWBinew) and yinew = h(IDi || PWBinew || rGUnew) ⊕ h(KGU || IDinew). GW stores (RIDinew, MIDinew) in the database.
- Step 4.
- GW sends {PIDinew, xinew, yinew, rGUnew} to MNi.
- Step 5.
- Upon receiving {PIDinew, xinew, yinew, rGUnew}, MNi stores {PIDinew, xinew, yinew, rGUnew} in the mobile device.
3. Security Analysis
Lee et al. claimed that their scheme could resist stolen mobile device attack, user impersonation attack, replay attack, stolen-verifier attack, privileged-insider attack, sensor node impersonation attack and session-specific temporary information attack, and it could ensure user anonymity, user untraceability, mutual authentication, session key agreement, local user verification, user-friendly password change, and forward secrecy. They also claimed that their scheme could revoke users’ devices to prevent the abuse or disclosure of confidential information when devices are lost or stolen. However, after analyzing their scheme thoroughly, we find that their scheme suffers from five flaws. First, when an IoT node Nj registers with the gateway GW, Nj stores yj sent from GW without checking the integrity of yj. This approach may make Nj authenticated by GW unsuccessfully. Secondly, in login and authentication phase, Ai = yi ⊕ h(IDi || PWBi || rGU) computed by MNi is different from Ai* = h(IDi || KGU) computed by GW. This may result in mobile node authentication failure. Thirdly, in login and authentication phase, only Nj checks the freshness of T1, and T1 is not verified by GW at all. This makes an attacker mount replay attack. Fourth, similar to the third flaw, an attacker can impersonate a mobile node by sending a request to Nj to consume GW and Nj’s computational resources. That is, denial of service attack may damage their scheme. Fifthly, user untraceability cannot be ensured as claimed. The details of how these flaws threaten Lee et al.’s scheme and our findings are shown as follows.
3.1. Failure Sensor Node Authentication
In IoT node registration phase, Nj chooses a random number rj. Then Nj computes MPj = h(KGN || rj || NIDj) and MIj = rj ⊕ h(NIDj || KGN) and sends {NIDj, MPj, MIj} to GW over a public channel. After receiving {NIDj, MPj, MIj}, GW uses the secret key KGN shared between Nj and GW to compute rj* = MIj ⊕ h(NIDj || KGN), MPj* = h(KGN || rj* || NIDj). Then GW checks whether MPj* = MPj holds or not. If it holds, the legitimacy of Nj and the integrity of {NIDj, MPj, MIj} are both ensured, and GW computes xj = h(NIDj || KGN) and yj = xj ⊕ MPj* and sends {yj} to Nj. After receiving {yj}, Nj stores {yj} in its memory. Because messages are transmitted over a public channel, anyone can eavesdrop or interrupt. If an attacker interrupts the transmission of yj sent by GW and sends the forged yj′ to Nj, Nj will store yj′ immediately with no integrity check, where yj′ ≠ yj.
Thereupon, in login and authentication phase, Nj computes xj′ = yj′ ⊕ h(KGN || rj || NIDj) ≠ xj, Aj = h(xj′) ⊕ nj, and Bj = h(xj′|| nj), where yj = xj ⊕ MPj and MPj = h(KGN || rj* || NIDj). Then Nj sends M2 = {M1, NIDj, Aj, Bj} to GW. After receiving M2, GW computes xj* = h(NIDj || KGN), nj* = h(xj*) ⊕ Aj, and Bj* = h(xj* || nj*). GW checks whether Bj* = Bj holds or not. Unfortunately, it will never hold because xj* ≠ xj′, and GW will regard that Nj is illegal and terminate login and authentication phase immediately.
3.2. Failure Mobile Node Authentication
In user registration phase, GW computes RIDi = , PIDi = , xi = h(IDi || PWBi) and yi = h(IDi || PWBi || rGU) ⊕ h(KGU || IDi). GW stores (RIDi, MIDi) in its database. GW sends {PIDi, xi, yi, rGU} to MNi through a secure channel. Upon receiving {PIDi, xi, yi, rGU}, MNi stores {PIDi, xi, yi, rGU} in the mobile device.
In login and authentication phase, MNi computes Ai = yi ⊕ h(IDi || PWBi || rGU) = h(IDi || PWBi || rGU) ⊕ h(KGU || IDi) ⊕ h(IDi || PWBi || rGU) = h(KGU || IDi), UNi = h(Ai || PIDi || ni) = h(h(KGU || IDi) || PIDi || ni) and UZi = ni ⊕ Ai= ni ⊕ h(KGU || IDi). GW computes Ai* = h(IDi || KGU), ni* = UZi ⊕ Ai* = ni ⊕ h(KGU || IDi) ⊕ h(IDi || KGU) ≠ ni, and UNi* = h(Ai* || PIDi || ni*) = h(h(IDi || KGU) || PIDi || ni*). Then GW checks whether UNi* = UNi holds or not. Unfortunately, it will never hold because UNi* = h(Ai* || PIDi || ni*) = h(h(IDi || KGU) || PIDi || ni*) ≠ UNi, where UNi = h(h(KGU || IDi) || PIDi || ni). GW will regard that MNi is illegal and terminate login and authentication phase immediately.
3.3. Vulnerability to Replay Attack
In login and authentication phase, MNi computes Ai = yi ⊕ h(IDi || PWBi || rGU), UNi = h(Ai || PIDi || ni) and UZi = ni ⊕ Ai and sends M1 = {PIDi, UNi, UZi, T1} to Nj, where T1 is the current timestamp. After receiving M1, Nj checks the freshness of T1, computes xj = yj ⊕ h(KGN || rj || NIDj), Aj = h(xj) ⊕ nj, and Bj = h(xj || nj), and sends M2 = {M1, NIDj, Aj, Bj} to GW. Upon receiving M2, GW computes xj* = h(NIDj || KGN), nj* = h(xj*) ⊕ Aj, and Bj* = h(xj* || nj*) and checks whether Bj* = Bj holds or not to verify nj* and authenticate Nj. Then GW decrypts PIDi with KG to retrieve {IDi, rD}, computes Ai* = h(IDi || KGU), ni* = UZi ⊕ Ai* and UNi* = h(Ai* || PIDi || ni*) and checks whether UNi* = UNi holds or not to verify ni* and authenticate MNi.
From the above, it is found that T1 is included in none of all parameters computes by GW. And only Nj checks the freshness of T1. Because messages are transmitted through a public channel, anyone can eavesdrop. That is, an attacker can get M1 = {PIDi, UNi, UZi, T1} easily. Thereupon, the attacker can send M1′ = {PIDi, UNi, UZi, T1′}, where T1′ is the current timestamp when the attacker mount replay attack. In the following, login and authentication phase will proceed as usual, GW will regard this request is indeed sent by MNi, and no entity can detect replay attack.
According to above analysis, it is shown that Lee et al.’s scheme cannot replay attack as claimed.
3.4. Vulnerability to Denial-of-Service Attack
Denial-of-service attack is an attack that an attacker tries to prevent legitimate users from accessing services. In order to launch this attack, an attacker usually consumes as much transmission or computational resources as possible. In login and authentication phase, MNi computes Ai = yi ⊕ h(IDi || PWBi || rGU), UNi = h(Ai || PIDi || ni) and UZi = ni ⊕ Ai and sends M1 = {PIDi, UNi, UZi, T1} to Nj, where T1 is the current timestamp. After receiving M1, Nj checks the freshness of T1, computes xj = yj ⊕ h(KGN || rj || NIDj), Aj = h(xj) ⊕ nj, and Bj = h(xj || nj), and sends M2 = {M1, NIDj, Aj, Bj} to GW. Upon receiving M2, GW computes xj* = h(NIDj || KGN), nj* = h(xj*) ⊕ Aj, and Bj* = h(xj* || nj*) and checks whether Bj* = Bj holds or not to verify nj* and authenticate Nj. Then GW decrypts PIDi with KG to retrieve {IDi, rD}, computes Ai* = h(IDi || KGU), ni* = UZi ⊕ Ai* and UNi* = h(Ai* || PIDi || ni*) and checks whether UNi* = UNi holds or not to verify ni* and authenticate MNi.
Suppose an attacker impersonates MNi to send forged M1 to Nj with fresh T1. After receiving forged M1, Nj checks the freshness of T1. However, T1 is fresh such that Nj will compute xj, Aj, and Bj and send M2 = {M1, NIDj, Aj, Bj} to GW. Upon receiving M2, GW computes xj*, nj*, and Bj* and checks whether Bj* = Bj holds or not to verify nj* and authenticate Nj. Because Bj is indeed computed by legal Nj, it must hold. Then GW decrypts PIDi with KG to retrieve {IDi, rD}, computes Ai*, ni* and UNi* and checks whether UNi* = UNi holds or not to verify ni* and authenticate MNi. Because M1 is forged, it will not hold. However, this approach has already consumed Nj and GW’s computational resources.
That is, if plenty of forged login requests are sent, GW’s resources will be exhausted, and legitimate users will be unable to access services. As a result, Lee et al.’s scheme cannot resist denial-of-service attack.
3.5. Compromised User Untraceability
In login and authentication phase, messages are transmitted through a public channel. MNi sends M1 = {PIDi, UNi, UZi, T1} to Nj, and GW sends M3 = {PIDinew, Gj, Rij, Hj} to Nj, where PIDi = and PIDinew = (IDi, rDnew). Because whether MNi replaces PIDi with PIDinew is not explicitly indicated, there are two possible cases for this issue:
Case 1: PIDi is not replaced with PIDinew.
Case 2: PIDi is replaced with PIDinew.
In Case 1, PIDi’s transmitted in different sessions are the same. This makes tracing a MNi with PIDi easy. In Case 2, PIDi’s transmitted in different sessions differ from each other. Unfortunately, PIDi and PIDinew are transmitted through a public channel such that it is easy to obtain the correlation between PIDi and PIDinew. As a result, Lee et al.s.’s scheme cannot ensure user untraceability as claimed.
3.6. Our Findings
Lee et al.’s authentication scheme is designed to ensure the security of IoT communications. In their scheme, parameters are generated, computed, or transmitted to achieve the goal with designated processes. However, improper designs result in the found flaws. In this paper, we analyze Lee et al.’s scheme by investigating the processes in detail in Section 3. According to the analyses, we obtain the following. First, the integrity of the transmitted data needs to be ensured. Secondly, because the same input parameters of hash function with different orders obtain different hash values, only rigorous designs can lead to successful verification and authentication. Thirdly, the freshness of a received message needs to be verified explicitly such that the timestamp should be one of the input parameters of hash function to resist replay attack. Fourthly, the gateway is responsible for helping a mobile node and a sensor node to authenticate each other. The gateway should authenticate the mobile node and the sensor node as early as possible to resist denial-of-service attack that may consume the gateway’s computational resources. Lastly, user anonymity can be ensured only when the identities PIDi’s transmitted in different sessions differ from each other and the correlation cannot be found.
4. The Proposed Authentication Scheme
After analyzing Lee et al.’s three-factor anonymous user authentication scheme for IoT environments, we find that their scheme cannot ensure security as claimed. To overcome the flaws and preserve the advantages, an improvement is proposed. The notations used in the proposed scheme are listed in Table 2.

Table 2.
Notations used in the proposed scheme.
Different from Lee et al.’s scheme, ECC is employed in our scheme to ensure efficiency. To initialize the scheme, an addition group G over a finite field Fp on the elliptic curve E of prime order n and the generator P of G are selected by GWN. GWN selects its private key x ∈ Zn* randomly, computes its public key X = xP, and chooses its master key KGWN. GWN publishes {E(Fp), G, P, X} while keeping x and KGWN secretly. The proposed scheme is composed of four phases: sensor registration phase, user registration phase, login and authentication phase, and password change phase. The details are as follows.
4.1. Sensor Registration Phase
Before deployment, for each sensor Sj, GWN selects an identity SIDj, computes the secret key = h(SIDj ‖ KGWN), and stores {SIDj, } in its memory. After initialization, these initialized sensors are deployed in a particular area to form a wireless sensor network.
4.2. User Registration Phase
When a new user Ui wants to access the services provided by the wireless sensor network such as acquiring sensory data from sensor nodes, Ui has to register with GWN. In this phase, data is transmitted via secure channels. User registration phase is depicted in Figure 4, and the details are as follows:
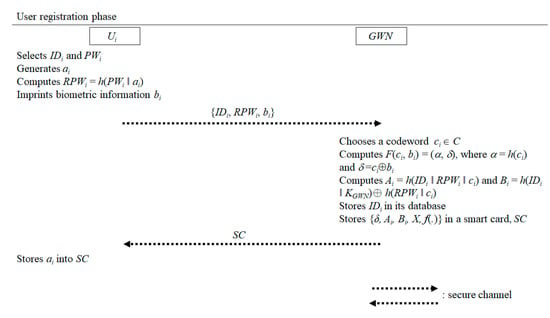
Figure 4.
User registration phase of the proposed scheme.
- Step 1.
- Ui chooses his/her identity IDi and password PWi.
- Step 2.
- Ui generates a nonce ai and computes RPWi = h(PWi ‖ ai).
- Step 3.
- Ui imprints his/her biometric on a special device to get the biometric bi.
- Step 4.
- Ui sends the registration request {IDi, RPWi, bi} to GWN via a secure channel.
- Step 5.
- After receiving Ui’s registration request {IDi, RPWi, bi}, GWN randomly chooses a codeword ci ∈ C for Ui.
- Step 6.
- GWN computes F(ci, bi) = (α, δ), Ai = h(IDi ‖ RPWi ‖ ci) and Bi = h(IDi ‖ KGWN) ⊕ h(RPWi ‖ ci), where α = h(ci) and δ = ci ⊕ bi.
- Step 7.
- GWN stores {δ, Ai, Bi, X, f(.)} into a smart card SC and issues it to Ui via a secure channel.
- Step 8.
- GWN stores IDi in its database and deletes other information.
- Step 9.
- After obtaining the smart card issued by GWN, Ui stores ai into SC. Then, SC contains {δ, Ai, Bi, X, f(.), ai}.
4.3. Login and Authentication Phase
When Ui wants to acquire Sj’s sensory data, this phase will be executed. Because only GWN shares secrets with Ui and Sj, only GWN can authenticate Ui and Sj. In this phase, Ui and Sj are authenticated by GWN, and a session key among GWN, Ui and Sj will be generated via GWN’s help. This phase is depicted in Figure 5, and the details are as follows:

Figure 5.
Login and authentication phase of the proposed scheme.
- Step 1.
- Ui inserts his/her smart card SC into a card reader and imprints his/her biometric bi′ on a special device, where SC contains {δ, Ai, Bi, X, f(.), ai}.
- Step 2.
- Ui inputs IDi and PWi.
- Step 3.
- SC computes ci′ = f(δ ⊕ bi′) = f((ci ⊕ bi) ⊕ bi′) and Ai′ = h(IDi ‖ h(PWi ‖ ai) ‖ci′).
- Step 4.
- SC checks whether Ai′ = Ai holds or not. If it does not hold, this session is terminated by SC; otherwise, Ui’s identity IDi, password PWi and biometric bi′ are verified successfully by SC, and this phase proceeds.
- Step 5.
- SC randomly chooses numbers ri and s ∈ Zn*.
- Step 6.
- SC computes M1 = Bi ⊕ h(h(PWi ‖ ai) ‖ ci′) = h(IDi ‖ KGWN), M2 = sP, M3 = sX = sxP, M4 = IDi ⊕ M3, M5 = h(M1 ‖ M3) ⊕ ri, M6 = h(IDi ‖ ri) ⊕ SIDj and M7 = h(M1 ‖ SIDj ‖ M3 ‖ ri).
- Step 7.
- Ui sends the login request {M2, M4, M5, M6, M7} to GWN.
- Step 8.
- After receiving the login request {M2, M4, M5, M6, M7} from Ui, GWN computes M3′ = xM2 = xsP and IDi′ = M4 ⊕ M3′.
- Step 9.
- GWN checks whether IDi′ exists in the database or not. If IDi′ does not exist, this login request is rejected by GWN; otherwise, this phase proceeds.
- Step 10.
- GWN computes M1′ = h(IDi′ ‖ KGWN), ri′ = M5 ⊕ h(M1′ ‖ M3′), SIDj′ = M6 ⊕ h(IDi′ ‖ ri′) and M7′ = h(M1′ ‖ SIDj′ ‖ M3′ ‖ ri′).
- Step 11.
- GWN checks whether M7′ = M7 holds or not. If it does not hold, this session is terminated by GWN; otherwise, this phase proceeds.
- Step 12.
- GWN generates a random number rg.
- Step 13.
- GWN computes ′ = h(SIDj′ ‖ KGWN), M8 = IDi′ ⊕ h(rg ‖ ′), M9 = h(M8 ‖ SIDj′ ‖ ′) ⊕ rg, M10 = h(IDi′ ‖ rg) ⊕ ri′ and M11 = h(IDi′ ‖ SIDj′ ‖ ′ ‖ ri′ ‖ rg).
- Step 14.
- GWN sends {M8, M9, M10, M11} to Sj.
- Step 15.
- After receiving {M8, M9, M10, M11}, Sj computes IDi″ = M8 ⊕ h(IDi″ ‖ ), rg′ = M9 ⊕ h(M8 ‖ SIDj ‖ ), ri″ = M10 ⊕ h(IDi′ ‖ rg), and M11′ = h(IDi″ ‖ SIDj ‖ ‖ ri″ ‖ rg′).
- Step 16.
- Sj checks whether M11′ = M11 holds or not. If it does not hold, this session is terminated by Sj; otherwise, this phase proceeds.
- Step 17.
- Sj generates a random number rj.
- Step 18.
- Sj computes M12 = h(rg′ ‖ ri″ ‖ ) ⊕ rj, SKj = h(IDi″ ‖ SIDj ‖ ri″ ‖ rg′ ‖ rj) and M13 = h( ‖ SKj ‖ rj).
- Step 19.
- Sj sends the response {M12, M13} to GWN.
- Step 20.
- After getting the response {M12, M13}, GWN computes rj′ = M12 ⊕ h(rg ‖ri′ ‖ ′), SKGWN = h(IDi′ ‖ SIDj′ ‖ ri′ ‖ rg ‖ rj′) and M13′ = h(′ ‖ SKGWN ‖ rj′).
- Step 21.
- GWN checks whether M13′ = M13 holds or not. If it does not hold, this session is terminated; otherwise, this phase proceeds.
- Step 22.
- GWN computes M14 = h(ri′ ‖ M1′) ⊕ rg, M15 = h(IDi′ ‖ ri′) ⊕ rj′ and M16 = h(IDi′ ‖ SKGWN ‖ rg ‖ rj′).
- Step 23.
- GWN sends {M14, M15, M16} to Ui.
- Step 24.
- Ui computes rg″ = M14 ⊕ h(ri′ ‖ M1′), rj″ = M15 ⊕ h(IDi′ ‖ ri′), SKi = h(IDi ‖ SIDj ‖ ri ‖ rg″ ‖ rj″) and M16′ = h(IDi ‖ SKi ‖ rg″ ‖ rj″).
- Step 25.
- Ui checks whether M16′ = M16 holds or not. If it does not hold, this session is terminated; otherwise, the process is completed.
After the above process, Ui can acquire Sj’s sensory data via GWN while a session key is shared among Ui, Sj and GWN, where SKi = SKj = SKGWN.
4.4. Password Change Phase
In the proposed scheme, a user can update his password without GWN involved. This phase is depicted is Figure 6, and the details are as follows:
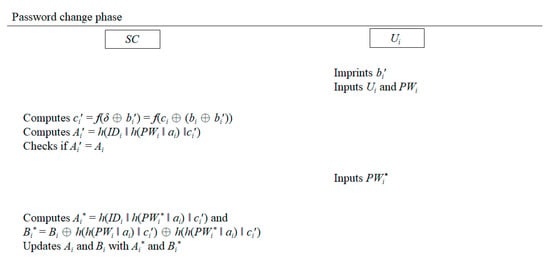
Figure 6.
Password change phase of the proposed protocol.
- Step 1.
- Ui inserts his/her smart card SC into a card reader and imprints his/her biometric bi′ on a special device.
- Step 2.
- Ui inputs IDi and PWi.
- Step 3.
- SC computes ci′ = f(δ ⊕ bi′) = f((ci ⊕ bi) ⊕ bi′) and Ai′ = h(IDi ‖ h(PWi ‖ ai) ‖ ci′).
- Step 4.
- SC checks whether Ai′ = Ai or not. If it does not hold, this request is declined by SC; otherwise, Ui inputs a new password PWi*.
- Step 5.
- SC computes Ai* = h(IDi ‖ h(PWi* ‖ ai) ‖ ci′) and Bi* = Bi ⊕ h(h(PWi ‖ ai) ‖ ci′) ⊕ h(h(PWi* ‖ ai) ‖ ci′).
- Step 6.
- SC updates Ai and Bi with Ai* and Bi*.
5. Security Analysis and Further Discussions
In this section, security analysis is first made to show that the proposed scheme can not only overcome the drawbacks that Lee et al.’s scheme suffers from but also resist common attack. The further discussions are made to demonstrate the properties that the proposed scheme possesses. The details are as follows.
5.1. Resistance against Leakage of the Secret Key Shared between GWN and Sj
In login and authentication phase, GWN sends {M8, M9, M10, M11} to where ′ = h(SIDj′ ‖ KGWN), M8 = IDi′ ⊕ h(rg ‖ ′), M9 = h(M8 ‖ SIDj′ ‖ ′) ⊕ rg, M10 = h(IDi′ ‖ rg) ⊕ ri′ and M11 = h(IDi′ ‖ SIDj′ ‖ ′ ‖ ri′ ‖ rg). After getting {M8, M9, M10, M11}, Sj computes IDi″ = M8 ⊕ h(IDi″ ‖ ), rg′ = M9 ⊕ h(M8 ‖ SIDj ‖ ), ri″ = M10 ⊕ h(IDi′ ‖ rg), and M11′ = h(IDi″ ‖ SIDj ‖ ‖ ri″ ‖ rg′). Then Sj checks if M11′ = M11 to determine whether the communication party is GWN and to ensure the correctness of the obtained ri″, rg′, and IDi″. Thereupon, Sj generates a random number rj, computes M12 = h(rg′ ‖ ri″ ‖ ) ⊕ rj, SKj = h(IDi″ ‖ SIDj ‖ ri″ ‖ rg′ ‖ rj) and M13 = h( ‖ SKj ‖ rj), and sends the response {M12, M13} to GWN.
The secret key = h(SIDj ‖ KGWN) shared between GWN and Sj is contained in M8 = IDi′ ⊕ h(rg ‖ ′), M9 = h(M8 ‖ SIDj′ ‖ ′) ⊕ rg, M11 = h(IDi′ ‖ SIDj′ ‖ ′ ‖ ri′ ‖ rg), M12 = h(rg′ ‖ ri″ ‖ ) ⊕ rj, and M13 = h( ‖ SKj ‖ rj). A legal user Ui knows IDi, SIDj, ri, rg, rj, and SKi. From M8, M9, M11, M12, and M13, Ui can retrieve h(rg ‖ ′), h(M8 ‖ SIDj′ ‖ ′), and h(rg′ ‖ ri″ ‖ ). However, is concealed by the secure one-way hash function. According to the properties of one-way hash function, it is infeasible to retrieve the input from a hash value. It denotes that cannot be retrieved from h(rg ‖ ′), h(M8 ‖ SIDj′ ‖ ′), and h(rg′ ‖ ri″ ‖ ). According to the above, it is ensured that no one even a legal user can retrieve the secret key = h(SIDj ‖ KGWN) shared between GWN and Sj.
5.2. Resistance against Sensor Node Impersonation Attack
We have explained why the proposed scheme can protect the secret key = h(SIDj ‖ KGWN) shared between GWN and Sj from being revealed. If an adversary wants to impersonate Sj, he needs to send M12 = h(rg′ ‖ ri″ ‖ ) ⊕ rj, and M13 = h( ‖ SKj ‖ rj) to GWN. In each session, random numbers ri, rg, and rj will be generated. It denotes that ri, rg, rj and SKj differ from those in other sessions, where SKj = h(IDi″ ‖ SIDj ‖ ri″ ‖ rg′ ‖ rj). Because is unknown, the adversary cannot retrieve correct IDi′ and rg′ from M8 and M9, where M8 = IDi′ ⊕ h(rg ‖ ′) and M9 = h(M8 ‖ SIDj′ ‖ ′) ⊕ rg. As a result, ri′ cannot be retrieved as well. Because the adversary is not aware of IDi′, rg′, ri″ and , he cannot compute correct M12 and M13 to cheat GWN. If the adversary retransmits M12 and M13 in a previous session, GWN will detect that M12 and M13 are not correct. It is because ri, rg, rj and SKj in one session differ from those in other sessions. According to the above, it is ensured that no one can impersonate Sj.
5.3. Resistance against Gateway Node Impersonation Attack
After sensor registration phase, GWN and Sj, GWN share the secret key = h(SIDj ‖ KGWN). After user registration phase, Ui gets a smart card SC containing {δ, Ai, Bi, X, f(.), ai}, where F(ci, bi) = (α, δ), α = h(ci), δ = ci ⊕ bi, Ai = h(IDi ‖ RPWi ‖ ci) and Bi = h(IDi ‖ KGWN) ⊕ h(RPWi ‖ ci). In login and authentication phase, GWN sends {M8, M9, M10, M11} to Sj. After receiving {M8, M9, M10, M11}, Sj computes IDi″ = M8 ⊕ h(IDi″ ‖ ), rg′ = M9 ⊕ h(M8 ‖ SIDj ‖ ), ri″ = M10 ⊕ h(IDi′ ‖ rg), and M11′ = h(IDi″ ‖ SIDj ‖ ‖ ri″ ‖ rg′) and checks if M11′ = M11. If it holds, it denotes that the computed IDi″, rg′ and ri″ and the shared secret key are correct. If an adversary retransmits {M8, M9, M10, M11} of a previous session, M11′ = M11 must hold. However, because and M1 = h(IDi ‖ KGWN) are unknown, the adversary cannot obtain rg, ri′ and rj′. That is, the adversary cannot obtain SKGWN = h(IDi′ ‖ SIDj′ ‖ ri′ ‖ rg ‖ rj′) such that no sensory data collected by Sj will be revealed.
On the other hand, in login and authentication phase, Ui sends the login request {M2, M4, M5, M6, M7} to GWN. After receiving the login request {M2, M4, M5, M6, M7} from Ui, GWN computes M3′ = xM2 = xsP and IDi′ = M4 ⊕ M3′ and checks if IDi′ exists in the database. Then, GWN computes M1′ = h(IDi′ ‖ KGWN), ri′ = M5 ⊕ h(M1′ ‖ M3′), SIDj′ = M6 ⊕ h(IDi′ ‖ ri′) and M7′ = h(M1′ ‖ SIDj′ ‖ M3′ ‖ ri′) and checks if M7′ = M7. Then the phase proceeds. After getting {M14, M15, M16} from GWN, Ui computes rg″ = M14 ⊕ h(ri′ ‖ M1′), rj″ = M15 ⊕ h(IDi′ ‖ ri′), SKi = h(IDi ‖ SIDj ‖ ri ‖ rg″ ‖ rj″) and M16′ = h(IDi ‖ SKi ‖ rg″ ‖ rj″) and checks if M16′ = M16. If it holds, it denotes that GWN is legal and the session key SKi is negotiated successfully. Because only GWN knows KGWN, only GWN can compute M1′ = h(IDi′ ‖ KGWN) to retrieve ri′ and IDi′. That is, only GWN can compute M14, M15, and M16 to have itself authenticated by Ui.
According to the above, the proposed scheme can resist gateway node impersonation attack.
5.4. Resistance against User Impersonation Attack
After user registration phase, Ui gets a smart card SC containing {δ, Ai, Bi, X, f(.), ai}, where F(ci, bi) = (α, δ), α = h(ci), δ = ci ⊕ bi, Ai = h(IDi ‖ RPWi ‖ ci) and Bi = h(IDi ‖ KGWN) ⊕ h(RPWi ‖ ci). In login and authentication phase, Ui sends the login request {M2, M4, M5, M6, M7} to GWN. After receiving the login request {M2, M4, M5, M6, M7} from Ui, GWN computes M3′ = xM2 = xsP and IDi′ = M4 ⊕ M3′ and checks if IDi′ exists in the database. Then, GWN computes M1′ = h(IDi′ ‖ KGWN), ri′ = M5 ⊕ h(M1′ ‖ M3′), SIDj′ = M6 ⊕ h(IDi′ ‖ ri′) and M7′ = h(M1′ ‖ SIDj′ ‖ M3′ ‖ ri′) and checks if M7′ = M7. If it holds, it denotes that the computed M1′, ri′ and SIDj′ are correct. If an adversary retransmits the login request {M2, M4, M5, M6, M7} of a previous session to GWN, M7′ = M7 must hold. The phase will proceed. Then GWN sends {M14, M15, M16} to Ui.
Although {M2, M4, M5, M6, M7} and {M14, M15, M16} are transmitted via public channels, the adversary cannot retrieve M1 =h(IDi ‖ KGWN) because of the properties of one-way hash function, where M1 = h(IDi ‖ KGWN), M2 = sP, M3 = sX = sxP, M4 = IDi ⊕ M3, M5 = h(M1 ‖ M3) ⊕ ri, M6 = h(IDi ‖ ri) ⊕ SIDj, M7 = h(M1 ‖ SIDj ‖ M3 ‖ ri), M14 = h(ri′ ‖ M1′) ⊕ rg, M15 = h(IDi′ ‖ ri′) ⊕ rj′ and M16 = h(IDi′ ‖ SKGWN ‖ rg ‖ rj′). After getting {M14, M15, M16} from GWN, the adversary cannot obtain rg″, rj″, and SKi. As a result, the adversary cannot obtain the sensory data from Sj. From the above, the proposed scheme can defend against user impersonation attack.
5.5. Resistance against Replay Attack
Sensory data collected by Sj will be concealed by the session key. Ui, Sj and GWN obtain SKi, SKj and SKGWN, respectively. SKi = SKj = SKGWN = h(IDi ‖ SIDj ‖ ri ‖ rg ‖ rj). ri, rg, and rj are random numbers generated by Ui, GWN and Sj, respectively. In each session, ri, rg, and rj are fresh. If an adversary wants to mount replay attack, he cannot obtain the fresh session key to obtain Sj’s sensory data.
5.6. Resistance against Stolen Smart Card Attack
{δ, Ai, Bi, X, f(.), ai} are stored in SC, where RPWi = h(PWi ‖ ai), F(ci, bi) = (α, δ), Ai = h(IDi ‖ RPWi ‖ ci), Bi = h(IDi ‖ KGWN) ⊕ h(RPWi ‖ ci), α = h(ci) and δ = ci ⊕ bi. If an attacker gets Ui’s smart card SC and has the ability to reveal the stored parameters, the attacker gets δ, Ai, Bi, X, f(.) and ai. However, only the one who has bi can obtain ci, and only the one who has ci and knows PWi can get h(IDi ‖ KGWN). Moreover, in login and authentication phase, only the one who knows h(IDi ‖ KGWN) and IDi can be authenticated by GWN. As a result, even if an attacker steals a smart card and reveals the stored data, he still cannot get essential authentication information.
5.7. User Anonymity and Untraceability
In login and authentication phase, data is transmitted via public channels such that a malicious user can eavesdrop. It denotes that the malicious user can get M4 = IDi ⊕ M3 and M8 = IDi′ ⊕ h(rg ‖ ′). SC randomly chooses numbers ri and s ∈ Zn* and computes M3 = sX = sxP. Only GWN can obtain M3 because only GWN knows its private key x. As a result, only GWN can retrieve IDi from M4. Moreover, only GWN and Sj know such that only Sj can retrieve IDi′ from M8.
On the other hand, all transmitted parameters are computed with fresh random numbers such that no constant parameter is transmitted. This makes tracing a specific user is impossible. According to the above, the proposed scheme can ensure user anonymity and untraceability.
5.8. Further Assessment
In our scheme, parameters are generated, computed, or transmitted to achieve the goal with designated processes. Only proper designs result in secure mechanisms. We analyze our scheme thoroughly by investigating the processes with various attack scenarios and assessing user anonymity and untraceability in Section 5. According to the analyses, we obtain the following. Firstly, our scheme can resist leakage of the secret key shared between GWN and Sj because the secret key = h(SIDj ‖ KGWN) shared between GWN and Sj is concealed by hash function. No one can retrieve it from the transmitted parameters because of the properties of one-way hash function. Secondly, our scheme can resist various impersonation attacks. It is because one party can authenticate another by checking whether it knows the essential secret or not. And the integrity and the freshness of the transmitted data are verified at the same time. Thirdly, our scheme can resist replay attack. Different from Lee et al.’s scheme, random numbers instead of timestamps are used to verify the freshness. This approach also eliminates the burden of synchronization. Lastly, our scheme ensures user anonymity and untraceability. It is because the real identity is concealed with M3, and M3′s in different sessions differ from each other.
6. Conclusions
Lee et al. proposed a three-factor authentication scheme by using hash and bio-hash functions to ensure the security of IoT communications. With through analyses, we find that their scheme suffers from failure sensor node authentication, failure mobile node authentication, replay attack, denial-of-service attack, and compromised user untraceability. Only with proper improvements, Lee et al. scheme can ensure security, efficiency, and important properties as claimed. We propose an improvement with ECC to overcome the drawbacks that Lee et al.’s scheme suffers from and preserve the advantages. According to the corresponding analysis, it is ensured that the proposed scheme achieves the goal to be realized and utilized in the real world.
Author Contributions
Conceptualization, Y.-F.C. and W.-L.T.; methodology, P.-L.H.; validation, Y.-F.C.; formal analysis, Y.-F.C.; investigation, K.-Y.L.; writing—original draft preparation, P.-L.H. and K.-Y.L.; writing—review and editing, Y.-F.C. and W.-L.T.; supervision, Y.-F.C. and W.-L.T. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by Ministry of Science and Technology under the Grants MOST 109-2410-H-025-013- and MOST 108-2221-E-034-006-MY2.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kim, H.; Ben-Othman, J.; Mokdad, L.; Son, J.; Li, C. Research challenges and security threats to AI-driven 5G virtual emotion applications using autonomous vehicles, drones, and smart devices. IEEE Netw. 2020, 34, 288–294. [Google Scholar] [CrossRef]
- Yang, M.; Luo, J.; Ling, Z.; Fu, X.; Yu, W. De-anonymizing and countermeasures in anonymous communication networks. IEEE Commun. Mag. 2015, 53, 60–66. [Google Scholar] [CrossRef]
- Tai, W.L.; Chang, Y.F.; Li, W.H. An IOT notion-based authentication and key agreement scheme ensuring user anonymity for heterogeneous ad hoc wireless sensor networks. Inf. Secur. Appl. 2017, 34, 133–141. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, F.; Masouros, C.; Vincent Poor, H. Fundamentals of physical layer anonymous communications: Sender detection and anonymous precoding. arXiv 2020, arXiv:2010.09122. [Google Scholar]
- Chang, Y.F.; Tai, W.L.; Hsu, M.H. A secure mobility network authentication scheme ensuring user anonymity. Symmetry 2017, 9, 307. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.C.; Chang, Y.F.; Chang, C.C.; Zheng, Y.Z. A fair and secure reverse auction for government procurement. Sustainability 2020, 12, 8567. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Farash, M.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.; Biswas, G.; Khan, M.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy protection for e-health systems by means of dynamic authentication and three-factor key agreement. IEEE Trans. Ind. Electron. 2018, 65, 2795–2805. [Google Scholar] [CrossRef] [Green Version]
- Aghili, S.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in IoT. Future Gener. Comput. Syst. 2019, 96, 410–424. [Google Scholar] [CrossRef]
- Lee, H.; Kang, D.; Ryu, J.; Won, D.; Kim, H.; Lee, Y. A three-factor anonymous user authentication scheme for Internet of Things environments. J. Inf. Secur. Appl. 2020, 52, 102494. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).