Abstract
The roaming service enables a remote user to get desired services, while roaming in a foreign network through the help of his home network. The authentication is a pre-requisite for secure communication between a foreign network and the roaming user, which enables the user to share a secret key with foreign network for subsequent private communication of data. Sharing a secret key is a tedious task due to underneath open and insecure channel. Recently, a number of such schemes have been proposed to provide authentication between roaming user and the foreign networks. Very recently, Lu et al. claimed that the seminal Gopi-Hwang scheme fails to resist a session-specific temporary information leakage attack. Lu et al. then proposed an improved scheme based on Elliptic Curve Cryptography (ECC) for roaming user. However, contrary to their claim, the paper provides an in-depth cryptanalysis of Lu et al.’s scheme to show the weaknesses of their scheme against Stolen Verifier and Traceability attacks. Moreover, the analysis also affirms that the scheme of Lu et al. entails incorrect login and authentication phases and is prone to scalability issues. An improved scheme is then proposed. The scheme not only overcomes the weaknesses Lu et al.’s scheme but also incurs low computation time. The security of the scheme is analyzed through formal and informal methods; moreover, the automated tool ProVerif also verifies the security features claimed by the proposed scheme.
1. Introduction
The emerging Internet of Things (IoT) is an infrastructure of all globally connected devices, including home appliances, vehicles, mobiles, tablets, surveillance systems, smart grids, etc. The IoT facilitate the heterogeneity of networks to seamlessly communicate with each other. The roaming service in IoT-based networks enables a remote user to enjoy seamless and scuffle free services during roaming outside the home network. A typical roaming scenario is shown in Figure 1. Involving three entities, namely mobile user, home network, and foreign network, the mobile user, using his digital communication device, like smart-phone, smart-vehicle, Laptop, PDA, etc., can access the services of his home network remotely in the coverage area of a foreign network. The roaming service extends the handover of connections from home network to foreign network, when both the networks belong to different types and are located at different geographical locations. The home and foreign network enter into a roaming agreement in order to facilitate their users. The user registers himself with the home network and, when he roams out of the coverage of his home network and enters into the coverage range of another network (foreign network having roaming agreement with home network), can access and enjoy the services of his home network through the foreign network. The roaming service is getting importance rapidly, due to millions of subscribers traveling abroad per year. The main issue restricting wide usage of roaming services is the security and privacy of the connecting parties. All the services provided are subject to communicate through an open/insecure wireless channel, causing an inherited effect on the security of such networks. The roaming process requires proper security mechanisms and is equally important for the three participants because the foreign networks cannot allow the user’s resources and services to be used illegitimately and without payment, whereas the home network avoids becoming a source of illegal access to foreign network, and the user does not want to be charged for the services used by some adversary. Moreover, as per user’s perspective, privacy and anonymity has gotten much importance. Without privacy and anonymity, the adversary can track user movements and current location [1,2]. The proper countering of security-related issues requires the development of customized authentication protocol, in which the authentication protocols not only verify the authenticity of the communicating parties but also ensure a session key for subsequent confidential data/services extended between the participating entities. The authentication is required when a user roams out of the coverage area of his home network and enters into the coverage area of a foreign network. The user has to get authenticated by the foreign network by the help of his home network. The successful authentication process can ensure that the access to the network is limited to legitimate users only [3].
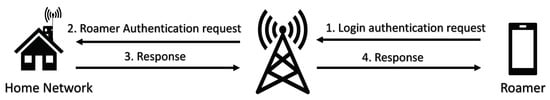
Figure 1.
Roaming user authentication.
In recent years, various authentication protocols were proposed [4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20] based on different cryptographic mechanisms. The schemes [15,16,17,18] are based on lightweight symmetric key primitives, as per the criteria laid down by Wang and Wang [21], the symmetric key mechanisms cannot provide privacy except for keeping a very large number of pseudo identities in smart-card with low memory or getting dynamic identity from home network at each login request. The schemes [4,5,6,7,12,13,14] based on bilinear pairing/modular exponentiation operations consume much more computation and in turn drains more battery power of already limited power wireless/mobile devices. Some of such schemes [8,9,10,11] are based on public but still low resource sucker Elliptic Curve Cryptography (ECC).
In 2009, Chang et al. [17] proposed an authentication scheme to secure GLOMONET. However, soon it was realized by Youn et al. [22] that the scheme proposed in Reference [17] could not achieve user anonymity. In 2012, Mun et al. [8] proposed and ECC based authentication scheme for roaming user on the principles of EC Diffie–Hellman problem (ECDHP). Soon after Mun et al.’s proposal, Reddy et al. [9] and Kim et al. [23] found various weaknesses in Mun et al.’s scheme, including insecurity against replay attacks. Reddy et al. [9] then proposed a slightly modified version to resist replay and other attacks against Mun et al.’s scheme. In 2017, another symmetric key based scheme for GLOMONET was proposed by Chaudhry et al. [18]. However, authors in Reference [24] found various weaknesses, including vulnerability to impersonation and related attacks in Chaudhry et al.’s scheme [18]. The scheme proposed by Lee et al. [24] is susceptible to traceability attack, as the dynamic identity is sent by the home agent during the session in plain text and this plain text dynamic identity sent through open channel can be used to trace future login requests. Recently, Gope and Hwang [25] proposed an authentication scheme for roaming user in GLOMONET using pseudo identity to counter DoS attack. Very recently in 2019, Lu et al. [26] pointed out various weaknesses in Gopi-Hwang’s scheme, including its insecurity against known session-specific parameters in leakage attacks. Moreover, Lu et al. claimed the Password Renewal Phase of Gopi-Hwang as faulty, and they proposed an ECC based new scheme.
1.1. The Contributions
Quite recently, in 2019, Lu et al. [26] found some weaknesses in Gopi-Hwang [25] authentication scheme for roaming users. To combat, Lu et al. proposed a new roaming user authentication scheme using ECC and claimed that their proposal extends required security features and resists known attacks. Contrary to their [26] claim, the cryptanalysis in this article shows that the roaming scheme presented in Reference [26] cannot protect the remote user against Stolen Verifier and Traceability attacks. Moreover, the analysis also affirms that the scheme of Lu et al. entails incorrect login and authentication phases and is prone to scalability issues. Therefore, an improved scheme based on ECC is designed by just modifying some of the steps in Lu et al.’s proposal. The scheme not only overcomes the weaknesses of Lu et al.’s scheme but also incurs low computation time. The proposed scheme entails following merits:
- The scheme provides provable security under the hardness of ECDLP (elliptic-curve discrete logarithm and elliptic-cure deffie-Hellman problems.
- The scheme provides security and anonymity under automated security model of ProVerif.
- The scheme provides authentication among user and foreign network with the help of home network.
- The scheme achieves low computation power as compared with baseline scheme presented in Reference [26].
1.2. Security Requirements
The user friendly security requirements for a roaming user authentication scheme are as follows:
- The mobile roaming user should have facility to change his password credentials in an easy manner and he should be facilitated not to memorize a complicated and/or long password.
- Along with traditional security requirements, The scheme should ensure user privacy and anonymity. Any insider/outsider, including foreign agents, should remain unaware regarding the original identity of the roaming user. Moreover, current location of the user should not be exposed to anyone with some previous knowledge.
- Home network should facilitate the authentication process between user and foreign network.
- The authentication should result into a shared secret key among user and foreign network for subsequent confidential communication over insecure link.
- The scheme should at least resist all known attacks.
1.3. Adversarial Model
The common model for adversary capabilities, as mentioned in Reference [27,28,29,30,31], is adopted and explained below:
- Adversary () fully controls the link and can listen, modify, replay a message from all the legal communicating parties. is also able to inject a self created false message.
- can easily get identity related information.
- knows all public parameters.
- Being an insider, can extract verifier table stored in home network database.
- Home Network’s private key is considered as secret and no other entity can extract the key.
- The pre-shared key between home and foreign networks is assumed to be secure.
2. Review of the Scheme of Lu et al.
A brief review of Lu et al.’s roaming user authentication scheme is explained here. Before moving further, please refer to Table 1 for understanding the notations used in this paper. The three main phases of Lu et al.’s scheme are detailed in below subsections:

Table 1.
Notations.
2.1. Home Network Agent Setup Phase
For system-setup purposes, Home Network Agent selects an Elliptic curve , where a, ∈ a finite field, such that , along with an infinite point O. HA then selects a base point P over . selects a secret key and computes public key . also selects irreversible Hash and keyed MAC functions , along with symmetric encryption/decryption algorithms .
2.2. Registration Phase
- Step LRP1:
- The mobile user selects identity/password pair , along with (generated randomly), and computes . sends the pair to .
- Step LRP2:
- Upon reception of to pair from , generates random and and stores and a sequence number against registration request of . then computes , , , and . then sends a smart-card containing to . stores in a verifier table maintained by .
- Step LRP3:
- Upon reception of smart-card, inserts . Finally, the smart-card contains: .
2.3. Login & Authentication Phase
- Step LLA1:
- After inserting smart-card, inputs and , the smart-card computes and verifies . Terminates the session if verification is unsuccessful. Otherwise, generates time-stamp , random and computes , , and . sends to .
- Step LLA2:
- upon reception of request, checks freshness of and generates fresh time-stamp , random . then computes , and sends to .
- Step LLA3:
- verifies freshness of after receiving message from . Rejects the message, if is not fresh. Otherwise, based on extracts corresponding shared key from verifier database and decrypts to get . verifies originality of by comparing with the once stored in verifier in a tuple consisting of , and . Upon successful verification, computes and verifies whether . Upon successful verification, computes and then checks . On success, updates and computes , . also updates and computes , . HA then sends to and increments .
- Step LLA4:
- checks freshness of after receiving response of . On success, computes . then verifies validity of and on success, computes .The session key is computed as . Then, sends to .
- Step LLA5:
- Upon reception, verifies freshness of and and on success, computes . further checks validity of and , if both holds, computes session key , and sends to .
- Step LLA6:
- verifies freshness of and checks validity of . If it holds, treats as legitimate user and now further communication between and may be carried out using the shared key .
3. Cryptanalysis of the Scheme of Lu et al.
In this section, cryptanalysis of the Lu et al.’s scheme is accomplished, under the realistic assumptions made in the adversarial model of Section 1.3. The following subsections show that the scheme of Lu et al. carries severe weaknesses, including in security against Stolen Verifier and known Session Specific variables attacks. Moreover, the scheme does not provide untraceability and has scalability issues. More seriously, the scheme also entails correctness issues, such incorrectness may stop authentication process before completion and legitimate user may experience denial of services. The following subsections explain the weaknesses:
3.1. Stolen Verifier Attack
Let be a dishonest insider and based on his capabilities, as mentioned in Section 1.3, can steal the verifier table with tuples . Using the verifier parameters, can impersonate as any roaming mobile user registered with home agent. The attack is simulated as follows:
- Step IA1:
- generates time-stamp , random , and computes:sends to .
- Step IA2:
- upon reception of request, checks freshness of , as well as generates fresh time-stamp and random . then computes:sends to .
- Step IA3:
- verifies freshness of after receiving message from and accepts the message as is fresh. based on extracts and from the verifier table and computes:compares the decrypted from Equation (6) with the one extracted from verifier table. The attacker will pass this test as both values are same. Now, computes:checks:authenticates on the basis of equality of Equation (8). will also pass this test, as all parameters in computation of were in access to and were correctly calculated at the time of computation of by . Now, computes:then checks:As is legitimate; therefore, it will pass the check of Equation (10). Hence, computes:then updates:Finally, HA sends to and increments .
- Step IA4:
- checks freshness of and computes:then verifies validity of and, on success, computes:Then, sends to .
- Step IA5:
- intercepts the message and computes:sends to .
- Step IA6:
- verifies freshness of and checks validity of . As is freshly generated, so it will pass the test. Similarly, has access to all parameters used for computation of , so it will also pass the test. Therefore, has also deceived the and passed the authentication. Now, can easily communicate with on behalf of using the shared key .
3.2. Traceability
Along with security, user anonymity/privacy is of vital interest, if compromised the attacker can foresee victim related important information, including his lifestyle, habits, shopping preferences, and sensitive location-related information of the mobile user. Ensuring (1) identity hiding and (2) untraceability are primary goals of privacy protection. Identity hiding refers to concealing original idntity of the user on public network, and untraceability ensures that no one can predict that two different sessions are requested by a single user. In the scheme of Lu et al., a static parameter is used as pseudo identity of , which remains the same for all sessions. Although it provides identity hiding, it lacks untraceability. Therefore, anyone just listening to the public channel can affirm whether or not different sessions are initiated by a single user.
3.3. Incorrectness
In Lu et al.’s scheme, the updates the pre-shared keys with and with during each session as shown in Equation (15) and (16), whereas these keys are not updated on other sides, i.e., and . Hence, the subsequent authentication request will fail and the scheme can work for a single time authentication, which is not required in any scenario, especially in IoT-based systems.
3.4. Scalability Problem
Due to storage of verifier table on , the scheme may suffer scalability issues. Moreover, finding corresponding entries from a large verifier table may cause delay in delay sensitive scenarios.
4. Proposed scheme
This section explains our improved authentication scheme for roaming user in IoT-based wireless networks, the reasons effecting Lu et al.’s security are considered in designing phase of our improved scheme. The storage of verifier table with entries consisting of tuple is the hitch giving space to insecurities. Moreover, the verifier also results in delaying the authentication process. In Lu et al.’s scheme, updates the pre-shared keys with and with during each session, whereas these keys () are not updated on other sides, i.e., and . Therefore, the authentication may fail in subsequent sessions. Proposed scheme handles this incorrectness by removing this step, as updation of these keys is an unnecessary step. The proposed scheme avoids usage of any verifier stored on to provide scuffle-free security. Moreover, the proposed scheme modifies some steps in registration and login/authentication phases. The working of the proposed scheme is shown in Figure 2. Following subsections explain the phases of the scheme:
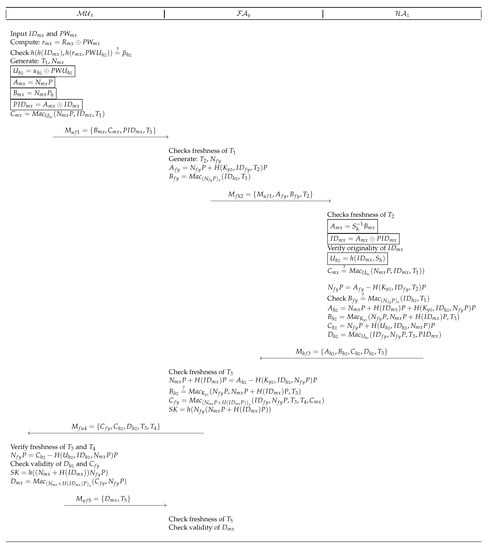
Figure 2.
Proposed Scheme.
4.1. System Setup Phase
For system-setup purposes, Home Network Agent selects an Elliptic curve , where a finite field, such that , along with an infinite point O. HA then selects a base point P over . selects a secret key and computes public key . also selects two hash functions , as well as a keyed MAC functions , along with symmetric encryption/decryption algorithms .
Note: The details of cryptographic primitives, including Hash, keyed MAC, etc., can be found in Reference [32].
4.2. Proposed Registration Phase
- Step PRP1:
- The mobile user selects identity/password pair , along with (generated randomly), and computes . sends the pair to .
- Step PRP2:
- Upon reception of to pair from , . then computes , , and . then sends a smart-card containing to .
- Step PRP3:
- Upon reception of smart-card, computes inserts . Finally, the smart-card contains: .
4.3. Login & Authentication Phase
- Step PLA1:
- After inserting smart-card, inputs and ,the smart-card computes and . The smart-card then verifies . Terminates the session if verification is unsuccessful. Otherwise, generates time-stamp , random and computes , , , and . sends to .
- Step PLA2:
- upon reception of request, checks freshness of and generates fresh time-stamp , random . then computes , and sends to .
- Step PLA3:
- verifies freshness of after receiving message from . Rejects the message, if is not fresh. Otherwise, computes and . verifies originality of stored in subscribers identity table. Upon successful verification, computes and verifies . Upon successful verification, computes and then checks . On success, computes , . computes , . HA then sends to .
- Step PLA4:
- checks freshness of after receiving response of . On success, computes . then verifies validity of and on success, computes .The session key is computed as . Then, sends to .
- Step PLA5:
- Upon reception, verifies freshness of and and on success, computes . further checks validity of and , if both holds, computes session key , and sends to .
- Step PLA6:
- verifies freshness of and checks validity of . If it holds, treats as legitimate user and now further communication between and may be carried out using the shared key .
5. Security Analysis
This section explains the automated formal security validation of the proposed algorithm using popular tool ProVerif, as well as under the hardness assumptions of ECDLP, collision resistant property of one-way hash, and hardness of symmetric encryption algorithm. The section then solicits the informal discussion on required security, supplemented by the security features comparisons with existing related schemes.
5.1. Formal Security Analysis
For the purpose of formal security analysis of our protocol, we define formal interpretations of repetition and chose the cipher-text attack (IDN-CCA) of the symmetric cryptographic algorithm, secure hash collision-resistant function, and ECDLP as follows:
Definition 1.
Given is the algorithm of symmetric key and cipher-text , the IDN-CCA’s definition is considered as hard problem if , in which describes an ’s benefit in finding the string (the set of plain-texts) of antecedent messages from the given (the set of cipher-texts) also algorithm of symmetric key with key (the set of enc/dec keys) which is unknown, for any small enough [32].
Definition 2.
Given an elliptic curve based point over , the interpretation of the ECDLP is considered as hard problem if , in which describes the benefit of an in discovering the integer from G and P which are given, for any small enough [32].
Definition 3.
Given the output , the interpretation of the function of hash is considered as hard problem if , in which describes the benefit of an in extracting the input from which is given, for any small enough [32].
For the formal analysis of security, we have defined random oracles [33] which are as follows:
- : This oracle will output plain-text k unconditionally from cipher-text that is given.
- : This oracle will output integer y unconditionally from and P that are publicly given values.
- : This oracle will output the input y from O that is the corresponding value of hash.
Theorem 1.
On the basis of supposition Security of Symmetric Cryptography algorithm, the enhanced protocol is provably protected in the arbitrary oracle model across a probabilistic polynomial time restricted attacker for extracting mobile user.
Proof.
Assume that experiment for the attacker who has capability to extract the user’s ID, be a probabilistic polynomial time restricted attacker. We determine success probability for like . Then, the benefit of is examined as , whereas the maximal is taken overall attacker with number of query and time of execution made the Reveal1 oracle. the enhanced protocol is provably protected in the arbitrary oracle model across attacker for extract the of mobile user if , for any appropriately small . Examine the experiment as described in , can successfully extract the of mobile user if he is able to break security of symmetric encryption description algorithm. Nevertheless, according to Definition 1, we could have , for any appropriately small . Thus, we get since depends on . So, concluded that the enhanced protocol is protected against an for extracting the of mobile user .□

Theorem 2.
Under the consideration that a hash function intently behaves as an arbitrary oracle model adjacent to a probabilistic polynomial time restricted attacker for extracting session key between user and foreign agent.
Proof.
Assume that experiment for the attacker who has capability to extract the arbitrary numbers in calculated the between user and foreign agent, be a probabilistic polynomial time restricted attacker. We determine success probability for as . After that, the benefit of is considered as , whereas the maximal is taken overall attacker with time of execution and number of queries made to Reveal2 and made to Reveal3 oracles. The enhanced protocol is provably protected in the random oracle model across for the values of hash of session key if ,for any appropriately small . Examine the experiment shown in , can successfully extract the values of hash of session key if he has the capability to convert the hash function and solve the . Though, as by the Definition 2 and Definition 3, , , for any appropriately small , . Thus, we get since depends on and . So, concluded that the enhanced protocol is provably protected against an attacker for extracting session key and foreign agent. □
5.2. Automated Security Analysis with ProVerif
We chose the prevailing software tool ProVerif [34,35] for performing an automated security perusal. The ProVerif is developed over the concept of applied calculus [36]. It is able to test and simulate many cryptographic operations, such as encryption/decryption, symmetric/asymmetric cryptosystems, hashes, signatures, etc. It can substantiate the characteristics of secrecy and authenticity. Complete protocol as given in Figure 2 is implemented and verified in ProVerif. Three channels as shown in Figure 3a are introduced in the implementation. The secure channel sch1 is dedicated for facilitating registration between mobile user and home agent, whereas two public channels pch2 and pch3 have been introduced for commencing communication between mobile user and home agent with foreign agent. Subsequently, variables and constants are also defined in Figure 3a. To keep the mobile user anonymous, its identity IDmx is kept private, whereas identities of home and foreign agents, i.e., IDhz and IDfy, respectively, are public. Mobile user’s password PWmx, shared keys Kxz, Kyz between mobile user-home agent and foreign agent-home agent, respectively, are assumed as private. Sh and Ph are considered as the private public key pairs of home agent. The Constructors are specified to simulate cryptographic operations and functions. Thereafter, destructor and equation are specified to simulate inverse and decryption.

Figure 3.
ProVerif Simulation.
Every participant can be described through two events a begin and an end event. The protocol authenticity is realized through exposing the respective relationship between begin and end interval of the related event initiated by the specific participant. If end event is not reached it simply means the protocol terminated unsuccessfully and scheme is incorrect. In Figure 3b, three distinct processes are implemented and simulated on behalf of three participants. These participants includes pMuser, pHagt, and pFagt, which are defined and implemented as shown in Figure 2 and described in Section 4. The proposed scheme is simulated as an unbounded parallel execution of user, home and foreign networks processes.
The subsequent four queries are defined in Figure 3c to substantiate the security and correctness of our protocol. The query attacker simulates an actual attack to expose the session key, whereas another 3 queries inj-event corresponds to begin and end event of 3 processes, i.e., user, home, and foreign networks. If any of these queries results false, it implies the scheme is incorrect. The abilities of an attacker are evaluated by executing the Not-attacker (SK) predicate, where is private. It is assumed that public parameters are accessible to the attacker. The Not-attacker is also applied over SK. Moreover, three successive queries on inj-event affirms the association between initiation and termination of events corresponding to each of these processes, i.e., user, home, and foreign networks. The outcome of the discussed queries are shown in Figure 3d.
It is observed through results 1, 2, and 3 in Figure 3d that each process initiated and terminated successfully, which substantiates the correctness of our scheme, whereas result 4 Not-attacker (SK) affirms that session key is secure against security threats. Hence, our protocol maintains authenticity and secrecy during its execution.
5.3. Security Requirements
The security requirement of the proposed scheme and a comparison of the proposed scheme with related competing schemes [9,12,14,25,26] is detailed in following subsections. Table 2 also illustrates the comparisons and confirms that only the proposed scheme provides all the required features and resists known attacks, whereas competing schemes lacks either some features or ensuring against some known attack.

Table 2.
Comparison of functional security.
5.3.1. Mutual Authentication
The proposed scheme, through (the home agent) provides mutual authentication between ( the mobile node) and (the foreign agent). authenticates by validating , computation of valid/legal requires an adversary to have access to the secret parameter of , i.e., , as well as valid/legal , which can only be extracted though by the use of secret key () of . Neither nor can be computed by any adversary, which implies that only valid can pass this test. Moreover, authenticates by validating . The computation of valid/legal requires an adversary to extract , which can by computed by public parameter sent by . The computation of requires an adversary to have access to the pre-shared secret key among and . No adversary, insider/outsider can have access to the pre-shared secret key. Therefore, only legal/valid can pass this test. Similarly, authenticates validating , the computation of valid requires an adversary to have access to pre-shared secret key between and . Moreover, the adversary also needs to compute the valid/legal, corresponding against the parameter sent on public channel earlier by to , the computation of again requires the use of pre-shared secret key . Therefore, only valid can pass this test. likewise, authenticates: 1) by validating and 2) by verifying . To generate a valid/legal , an adversary requires having access to secret parameter of , as well as computation of valid/legal , both of which can be performed only by legal . Likewise, to generate valid , an adversary requires to compute valid/legal , and . All the mentioned parameters can only be computed by legal . Hence, mutual authentication among and through is essential trait of the proposed scheme.
5.3.2. Correctness
The proposed scheme correctly accomplishes the process of authentication between and through . Unlike Lu et al.’s scheme, in the proposed scheme, does not unnecessarily updates () after each successful login. More precisely, the proposed schemes does not require any verifier table for any user; therefore, no entry can be modified by . Due to non-usage of verifier table by , the user request does not involve fining and comparing with verifier entries, which helps in minimizing the delay. Hence, the proposed scheme provides correct and secure authentication process.
5.3.3. User Anonymity/Untraceability
Unfortunately and despite their claim, in the scheme of Lu et al. the pseudo identity remains same not only for multiple but for all sessions. In the proposed scheme, on every login/authentication request selects a new random variable and computes the dynamic pseudo identity . Therefore, the proposed scheme not only provides identity hiding but also untraceability/unlinkability.
5.3.4. Perfect Forward Secrecy:
The session key computed after successful authentication among or contains the share from both, i.e., from and from . Both and are generated freshly for each session. Moreover, neither nor having full control on key generation. Even if one or more shared keys from previous session/s are compromised, the adversary may not be able to compute any future session key. Hence, the proposed scheme provides perfect forward secrecy.
5.3.5. User Forgery Attack
As described in Section 5.3.1, the authenticates the user by validating and valid/legal can only be computed by legal . Moreover, authenticates by validating , an adversary requires to compute , as well as . Only legal can compute it’s own secretly generated parameter and extract out of , which requires the usage of secret parameter of . Therefore, the proposed scheme strongly resists user forgery attack.
5.3.6. Stolen Verifier and Insider Attack
The home agent , in the proposed scheme does not store any information relating to the credentials of, including password, ; rather, is free of any verifier table. The only information stored is the public identities of the users. Moreover, during registration process, sends , along with , to . The password is concealed in one-way hash function, along with a random number. Therefore, no deceitful insider gets any information relating to password and is having no advantage. Hence, the proposed scheme resists insider attacks. Moreover, without verifier table, the stolen verifier is impossible in the proposed scheme.
5.3.7. Stolen Smart-Card Attack
In the proposed scheme, the smart-card contains , where, the user related information is stored in and parameters, where , and . Extracting password information from or requires inverse to hash function, which by definition is a hard problem. Moreover, user secret parameter is also concealed with , and without password information, it is computationally infeasible to compute . Therefore, the proposed scheme resists stolen smart-card attacks.
5.3.8. Known Session-Specific Parameters Attack
The adversary in the proposed scheme may not able to compute session key even if, he gets the session parameters and , as the session key also requires the hashed identity concealed in an elliptic curve point . Computation of needs to break on way property of hash, as well as elliptic curve discrete logarithm problem. Therefore, the proposed scheme resists known session-specific parameters attack.
6. Performance Comparisons
This section illustrates the performance comparisons of the proposed with competing schemes. For performance comparison purposes, following notations are used:
- : Computation time for hash/mac operations
- : Computation time for Symmetric Enc/Dec
- : Computation time for scalar multiplication of point over
- : Computation time for addition of points over
- : Computation time for modular exponentiation
- : Computation time for bilinear pairing
- : Computation time for map to point hash
Referring the results of Kilinic and Yanik [37], the experiment time computed over Ubuntu 12.04.1 LTS 32bit Operating system with version (0.5.12) of PBC library structured on the version (5.0.5) of the GMP Library on an Intel PC with Dual CPU E2200 2.20GHz and with memory of 2048 MB, the execution time for ms, ms, ms, ms, ms, ms, and ms, respectively. The computation costs of each scheme is presented in Table 3. The scheme of Reddy et al. completes the authentication by computing , the scheme of Li et al. requires operations for a successful authentication procedure, the scheme of Jiang et al. computes to accomplish the authentication process, and the scheme of Gope-Hwang performs during authentication, whereas Lu et al.’s scheme completes a round of authentication procedure with computation cost . The computation cost of the proposed scheme is , although the computation cost of the proposed scheme is bit higher than some competing schemes. However, while providing all security features, the proposed scheme reduced , , , and as compared with seminal Lu et al.’s scheme. Table 3 also shows execution time of all competing schemes; it is shown that proposed scheme completes roaming authentication in ms and reduced approximately ms as compared with Lu et al.’s scheme.

Table 3.
Comparison of computation cost.
7. Conclusions
In this paper, we identified weaknesses of Lu et al.’ scheme against stolen verifier and traceability attacks. We also identified that their scheme has correctness issues besides scalability. To combat the weaknesses, we proposed an improved scheme for IoT-based wireless networks. The formal, informal, and automated security analysis has proven that our scheme with stands the known attacks, whereas the performance analysis has shown that our scheme is more efficient and practical as compared with Lu et al.’s scheme. The proposed scheme is more practical in roaming scenarios.
Author Contributions
B.A.A. wrote the initial draft, revision and was involved in ProVerif Simulation. S.A.C. conceptualized the idea and performed cryptanalysis and designed the new scheme. A.B., and A.A.-B. performed security and efficiency analysis. M.H.A. performed formal analysis and supervised the whole process. All authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
This Project was funded by the Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah, under Grant No. (RG-7-611-40). The author, therefore, gratefully acknowledge the DSR for technical and financial support.
Conflicts of Interest
The authors declare no conflict of interest.
References
- He, D.; Kumar, N.; Khan, M.K.; Lee, J. Anonymous two-factor authentication for consumer roaming service in global mobility networks. IEEE Trans. Consum. Electron. 2013, 59, 811–817. [Google Scholar] [CrossRef]
- Li, X.; Liu, S.; Wu, F.; Kumari, S.; Rodrigues, J.J.P.C. Privacy Preserving Data Aggregation Scheme for Mobile Edge Computing Assisted IoT Applications. IEEE Internet Things J. 2019, 6, 4755–4763. [Google Scholar] [CrossRef]
- Wei, F.; Vijayakumar, P.; Jiang, Q.; Zhang, R. A Mobile Intelligent Terminal Based Anonymous Authenticated Key Exchange Protocol for Roaming Service in Global Mobility Networks. IEEE Trans. Sustain. Comput. 2018, 1-1. [Google Scholar] [CrossRef]
- Jiang, Y.; Lin, C.; Shen, X.; Shi, M. Mutual Authentication and Key Exchange Protocols for Roaming Services in Wireless Mobile Networks. IEEE Trans. Wirel. Commun. 2006, 5, 2569–2577. [Google Scholar] [CrossRef]
- Jo, H.J.; Paik, J.H.; Lee, D.H. Efficient Privacy-Preserving Authentication in Wireless Mobile Networks. IEEE Trans. Mob. Comput. 2014, 13, 1469–1481. [Google Scholar] [CrossRef]
- Hsu, R.; Lee, J.; Quek, T.Q.S.; Chen, J. GRAAD: Group Anonymous and Accountable D2D Communication in Mobile Networks. IEEE Trans. Inf. Forensics Secur. 2018, 13, 449–464. [Google Scholar] [CrossRef]
- Alezabi, K.A.; Hashim, F.; Hashim, S.J.; Ali, B.M. An efficient authentication and key agreement protocol for 4G (LTE) networks. In Proceedings of the 2014 IEEE REGION 10 SYMPOSIUM, Kuala Lumpur, Malaysia, 14–16 April 2014; pp. 502–507. [Google Scholar]
- Mun, H.; Han, K.; Lee, Y.S.; Yeun, C.Y.; Choi, H.H. Enhanced secure anonymous authentication scheme for roaming service in global mobility networks. Math. Comput. Model. 2012, 55, 214–222. [Google Scholar] [CrossRef]
- Goutham Reddy, A.; Yoon, E.; Das, A.K.; Yoo, K. Lightweight authentication with key-agreement protocol for mobile network environment using smart cards. IET Inf. Secur. 2016, 10, 272–282. [Google Scholar] [CrossRef]
- El Idrissi, Y.E.H.; Zahid, N.; Jedra, M. An Efficient Authentication Protocol for 5G Heterogeneous Networks. In Ubiquitous Networking; Sabir, E., García Armada, A., Ghogho, M., Debbah, M., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 496–508. [Google Scholar]
- Su, C.; Santoso, B.; Li, Y.; Deng, R.H.; Huang, X. Universally Composable RFID Mutual Authentication. IEEE Trans. Dependable Secur. Comput. 2017, 14, 83–94. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Choo, K.K.R. A robust biometrics based three-factor authentication scheme for Global Mobility Networks in smart city. Future Gener. Comput. Syst. 2018, 83, 607–618. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J. Secure and Efficient Handover Authentication Based on Bilinear Pairing Functions. IEEE Trans. Wirel. Commun. 2012, 11, 48–53. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Li, G.; Yang, L. An enhanced authentication scheme with privacy preservation for roaming service in global mobility networks. Wirel. Pers. Commun. 2013, 68, 1477–1491. [Google Scholar] [CrossRef]
- Zhu, J.; Ma, J. A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 2004, 50, 231–235. [Google Scholar]
- Tsai, J.L.; Lo, N.W.; Wu, T.C. Secure Handover Authentication Protocol Based on Bilinear Pairings. Wirel. Pers. Commun. 2013, 73, 1037–1047. [Google Scholar] [CrossRef]
- Chang, C.C.; Lee, C.Y.; Chiu, Y.C. Enhanced authentication scheme with anonymity for roaming service in global mobility networks. Comput. Commun. 2009, 32, 611–618. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Albeshri, A.; Xiong, N.; Lee, C.; Shon, T. A privacy preserving authentication scheme for roaming in ubiquitous networks. Clust. Comput. 2017, 20, 1223–1236. [Google Scholar] [CrossRef]
- Chen, C.M.; Xiang, B.; Liu, Y.; Wang, K.H. A secure authentication protocol for internet of vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Chen, C.M.; Wang, K.H.; Yeh, K.H.; Xiang, B.; Wu, T.Y. Attacks and solutions on a three-party password-based authenticated key exchange protocol for wireless communications. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3133–3142. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Youn, T.; Park, Y.; Lim, J. Weaknesses in an Anonymous Authentication Scheme for Roaming Service in Global Mobility Networks. IEEE Commun. Lett. 2009, 13, 471–473. [Google Scholar] [CrossRef]
- Kim, J.S.; Kwak, J. Improved secure anonymous authentication scheme for roaming service in global mobility networks. Int. J. Secur. Its Appl. 2012, 6, 45–54. [Google Scholar]
- Lee, H.; Lee, D.; Moon, J.; Jung, J.; Kang, D.; Kim, H.; Won, D. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13, e0193366. [Google Scholar] [CrossRef] [PubMed]
- Gope, P.; Hwang, T. Lightweight and energy-efficient mutual authentication and key agreement scheme with user anonymity for secure communication in global mobility networks. IEEE Syst. J. 2015, 10, 1370–1379. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, G.; Li, L.; Yang, Y. Robust Privacy-Preserving Mutual Authenticated Key Agreement Scheme in Roaming Service for Global Mobility Networks. IEEE Syst. J. 2019, 1–12. [Google Scholar] [CrossRef]
- Eisenbarth, T.; Kasper, T.; Moradi, A.; Paar, C.; Salmasizadeh, M.; Shalmani, M. On the Power of Power Analysis in the Real World: A Complete Break of the KeeLoq Code Hopping Scheme. In Advances in Cryptology, CRYPTO 2008; Wagner, D., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5157, pp. 203–220. [Google Scholar]
- Dolev, D.; Yao, A.C. On the security of public key protocols. Inf. Theory, IEEE Trans. 1983, 29, 198–208. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.H. Anonymous Authentication for Wireless Body Area Networks With Provable Security. IEEE Syst. J. 2016, 11, 2590–2601. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Shen, H.; Lee, J.H. One-to-many authentication for access control in mobile pay-TV systems. Sci. China Inf. Sci. 2016, 59, 052108. [Google Scholar] [CrossRef][Green Version]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Arshad, H.; Khan, M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Future Gener. Comput. Syst. 2016, 63, 56–75. [Google Scholar] [CrossRef]
- Hoffstein, J. An introduction to cryptography. In An Introduction to Mathematical Cryptography; Springer: Berlin/Heidelberg, Germany, 2008; pp. 1–523. [Google Scholar]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, CCS93, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Xie, Q.; Hwang, L. Security enhancement of an anonymous roaming authentication scheme with two-factor security in smart city. Neurocomputing 2019, 347, 131–138. [Google Scholar] [CrossRef]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A.; Shamshirband, S.; Ghayyur, S.A.K.; Mosavi, A. Securing IoT-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef]
- Ghani, A.; Mansoor, K.; Mehmood, S.; Chaudhry, S.A.; Rahman, A.U.; Najmus Saqib, M. Security and key management in IoT-based wireless sensor networks: An authentication protocol using symmetric key. Int. J. Commun. Syst. 2019, 32, e4139. [Google Scholar] [CrossRef]
- Kilinc, H.; Yanik, T. A Survey of SIP Authentication and Key Agreement Schemes. Commun. Surv. Tutorials IEEE 2014, 16, 1005–1023. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).