Abstract
Blockchain has been widely proposed to strengthen data management security through decentralization, immutability, and auditable transactions, capabilities increasingly recognized as enablers of sustainable digital ecosystems and resilient institutions; however, existing studies remain dispersed across domains and rarely consolidate governance, interoperability, and evaluation criteria. This paper conducts a systematic literature review of 70 peer-reviewed studies published between 2018 and 2024, using IEEE Xplore, Scopus, Springer, ScienceDirect, and ACM Digital Library as primary sources and following Kitchenham’s guidelines and the PRISMA 2020 flow, to examine how blockchain has been applied to secure data in healthcare, IoT, smart cities, supply chains, and cloud environments. The analysis identifies four methodological streams—empirical implementations, cryptographic/security protocols, blockchain–machine learning integrations, and conceptual frameworks—and shows that most contributions are technology-driven, with limited attention to standard metrics, regulatory compliance, and cross-platform integration. In addition, the review reveals that very few works articulate governance models that align technical solutions with organizational policies, which creates a gap for institutions seeking trustworthy, auditable, and privacy-preserving deployments. The review contributes a structured mapping of effectiveness criteria (confidentiality, auditability, availability, and compliance) and highlights the need for governance models and interoperable architectures to move from prototypes to production systems. Future work should prioritize large-scale validations, policy-aligned blockchain solutions, and comparative evaluations across sectors.
1. Introduction
Blockchain technology has emerged as a transformative solution to enhance security, transparency, and trust in data management systems due to its decentralized and immutable structure. Nevertheless, its adoption faces important challenges related to efficiency, scalability, interoperability, and integration with existing data infrastructures. It is therefore necessary to analyze its actual impact on data management security, especially in sectors where information protection, traceability, and auditability are critical, such as healthcare, finance, education, supply chains, and smart cities. To ensure methodological rigor, this review focuses on peer-reviewed, English-language studies published between 2018 and 2024 with a minimum length of 10 pages, thereby prioritizing empirical depth over non-empirical or preliminary reports. By synthesizing evidence from multiple application domains, we aim to clarify how blockchain contributes to data management security, which security criteria are most frequently evaluated, what computational supports and architectures are employed, how research topics are organized thematically, and where gaps remain for sustainable, large-scale deployments.
Authors [1,2] proposed frameworks such as EdgeMediChain, which combines edge computing with blockchain to manage healthcare data more efficiently and securely, achieving an 84.75% reduction in execution time compared with traditional approaches. This design leverages proximity-based processing to minimize latency and improve overall performance. In the field of data privacy and security, other studies [2,3] employed smart contract-based architectures, such as the SeMF framework, to manage user data consent and to enhance the protection of sensitive information, while an additional contribution [4], highlighted the importance of user autonomy in the administration of personal data.
Studies [5,6] emphasized the relevance of frameworks such as ACE-BC in cybersecurity, where blockchain is integrated with advanced encryption techniques to improve secure data transmission and storage. This approach achieved outstanding results, with confidentiality levels of 98.9% and overall system efficiency of 97.4%, demonstrating that combining blockchain with modern cryptography can offer higher protection than traditional solutions. A complementary study [7] confirmed that this integration is suitable for environments that require continuous data exchange. Research on the integration of IoT and blockchain [3,8] also reported improvements in data security and system scalability through techniques such as ChaCha20-Poly1305 encryption and Proof of Authority (PoA). Another study [9] showed that these solutions ensure secure access and data integrity, reducing risks associated with unauthorized access and data manipulation in industrial IoT networks.
In the healthcare sector, studies [10,11] showed that blockchain has optimized the management of electronic health records (EHRs) by overcoming the limitations of centralized systems and providing a distributed infrastructure that enhances interoperability and medical data security. An additional contribution [12] confirmed the relevance of blockchain in contexts where the privacy, integrity, and traceability of information are crucial. Furthermore, the combination of blockchain with Artificial Intelligence (AI), machine learning (ML), and Big Data [13,14] has proven effective for addressing cybersecurity challenges and for managing large data volumes in smart cities and Industry 4.0. A related work [15] indicated that this integration enables more efficient and secure large-scale information management.
Other authors [16,17] underlined the importance of using advanced cryptographic techniques, such as zero-knowledge proofs (ZKPs), in blockchain-based systems to protect privacy and guarantee controlled access to data. A further study [18] demonstrated that these techniques allow for user authentication without disclosing sensitive information, achieving a balance between privacy and system usability. In the supply chain domain, studies [19,20] have demonstrated that blockchain adoption has significantly improved process traceability and transparency, thereby increasing stakeholder trust and optimizing operational efficiency through reliable tracking of products and materials. Another contribution [21] reinforced the role of blockchain in coordinating distributed actors along the supply chain. In the education sector, research [22,23] has highlighted blockchain’s capacity to securely verify academic credentials and to manage student records, identifying benefits in terms of security and cost reduction; an additional study [24] pointed out, however, that technical and institutional adaptation remains a challenge.
Compliance with eIDAS and GDPR, together with the interoperability of blockchain technologies, has been identified as a crucial topic in several reviews [23,25]. Complementary analyses [26,27] proposed approaches for blockchain-based solutions to meet privacy and auditing standards, thereby improving transparency, accountability, and data control. In building lifecycle management, studies [9,15] showed that integrating blockchain with digital twins (DTs), AI, and cloud computing optimizes the management and security of built environments, providing a unified system to efficiently and securely handle large data volumes and complex processes. Another work [14] confirmed that this integration is suitable for complex, data-intensive infrastructures. Research [12,28] has also emphasized how blockchain can transform healthcare through decentralization and enhanced security, addressing interoperability challenges and presenting effective solutions that can be applied globally. Overall, blockchain has been proposed as a means to strengthen data management security through decentralization and verifiable transactions, potentially reducing reliance on trusted intermediaries—though most evidence remains limited to simulations or small-scale pilots [24].
Finally, decentralized frameworks leveraging Ethereum and consensus mechanisms such as Proof of Authority (PoA) [29,30] have been proposed and implemented to ensure data integrity and transparency across sectors ranging from aviation component manufacturing to intellectual property rights management. An additional study [31] extended these ideas to content protection and rights tracking. These advances demonstrate how blockchain has evolved from its initial use in financial transactions to a broader role in secure data management, adding value across diverse sectors and fostering new lines of research and development [24,28] as well as subsequent implementations [13].
While several systematic and bibliometric reviews have explored blockchain in specific domains—such as healthcare [10,11,12,28], supply chains [21], or business management [26,27]—they tend to focus on isolated sectors or technical architectures, often overlooking cross-cutting evaluation criteria, governance models, and interoperability challenges. Moreover, existing reviews rarely integrate cryptographic, AI-driven, and empirical implementation trends into a unified analytical framework. This review fills that gap by conducting a comprehensive, cross-domain SLR that (1) maps and compares effectiveness criteria across sectors, (2) identifies dominant computational supports and their trade-offs, (3) reveals a critical imbalance between technology-driven experimentation (57.4%) and conceptual/governance research (3.3%), and (4) proposes a structured taxonomy to guide future work toward interoperable, regulation-aware, and sustainable blockchain ecosystems.
Accordingly, this paper will describe the systematic review as follows: Section 2 details the theoretical background, while Section 3 outlines the methods and materials. Section 4 presents the results and discussions of the systematic review. Finally, Section 5 offers conclusions and recommendations for future research.
2. Theoretical Background
With the continuous advancement of blockchain technology and its growing integration across sectors, it is essential to understand not only its structural components but also how its core properties directly enable, or constrain, security in data management. This section expands the theoretical foundation by linking blockchain’s architectural features to specific security mechanisms, governance models, and regulatory challenges.
2.1. Core Blockchain Properties and Their Role in Data Security
Blockchain’s value in data management stems from four interrelated properties:
- Immutability, achieved through cryptographic hashing (e.g., SHA-256) and chained block structures, suggests that once data are recorded, they cannot be altered without detection. This directly supports data integrity and auditability, critical for compliance with standards like ISO/IEC 27001 [32,33,34].
- Decentralization distributes data across nodes, eliminating single points of failure and reducing risks of centralized breaches [1]. However, full decentralization may conflict with data minimization principles under GDPR [23].
- Consensus mechanisms (e.g., PoA and PBFT) validate transactions before inclusion in the ledger, enforcing authenticity and resilience against tampering, especially in permissioned environments like healthcare or supply chains [8,9].
- Transparency with pseudonymity allows for transaction verification while masking user identities through cryptographic addresses, balancing traceability and privacy [2,35].
These properties do not merely enhance technical security; they fundamentally reshape data governance. Immutability shifts accountability from reactive auditing to proactive integrity assurance. Decentralization redistributes control from central authorities to network participants, challenging traditional hierarchical data stewardship models.
2.2. Blockchain Architectures and Security Trade-Offs
The choice between public (e.g., Ethereum) and permissioned (e.g., Hyperledger Fabric) blockchains entails fundamental security trade-offs. Public chains offer censorship resistance but face scalability and privacy limitations due to open participation. In contrast, permissioned blockchains enable fine-grained access control and higher throughput, making them suitable for enterprise data management where confidentiality is paramount [29,36]. However, they often rely on semi-trusted authorities, which may reintroduce centralization risks and undermine the “trustless” premise of blockchain [1]. This trade-off reflects a broader tension between operational efficiency and governance autonomy: permissioned blockchains may offer better performance, but at the cost of reintroducing gatekeepers whose policies dictate data access and lifecycle management.
2.3. Smart Contracts and Cryptographic Enhancements for Data Governance
Beyond the ledger, blockchain leverages smart contracts to automate data governance policies, such as consent management [2] or role-based access control [4], reducing human error and ensuring consistent rule enforcement. Additionally, advanced cryptographic tools like zero-knowledge proofs (ZKPs) enable the verification of data attributes without revealing underlying information, supporting GDPR-compliant identity systems [17]. Hybrid storage models (e.g., IPFS + blockchain) further preserve integrity by anchoring data hashes on-chain while storing payloads off-chain [7,37]. Smart contracts thus act as executable governance policies, embedding organizational rules directly into the infrastructure. However, their rigidity can hinder adaptability in dynamic regulatory environments, raising questions about who controls contract upgrades and how disputes are resolved when code conflicts with legal intent.
2.4. Tensions Between Blockchain Design and Data Protection Regulations
Despite its security benefits, blockchain faces inherent conflicts with data protection laws. The right to erasure (GDPR) clashes with blockchain’s immutability. Proposed solutions include off-chain storage of personal data or mutable sidechains [23]. Similarly, data minimization is challenged by ledger replication across nodes; techniques like sharding or selective disclosure can mitigate this [26]. These tensions highlight that blockchain is not a “plug-and-play” security solution but requires careful alignment with legal and organizational requirements. These tensions reveal a deeper epistemological conflict: blockchain assumes data as immutable truth, while modern data protection frameworks treat data as contextual, temporal, and subject to individual agency. Bridging this gap requires not just technical workarounds, but new governance models that reconcile cryptographic permanence with legal fluidity.
2.5. Operational Definitions of Evaluation Criteria
To ensure consistent coding during data extraction, we adopted the following operational definitions for the security criteria listed in Table 3:
- Confidentiality: Protection of data from unauthorized access, typically enforced through encryption, access control, or zero-knowledge proofs.
- Availability: Guaranteed access to data and services under normal and adverse conditions (e.g., DDoS resilience and fault tolerance).
- Authentication and Authorization: Verification of user identity (authentication) and enforcement of access rights (authorization), often via digital signatures or role-based policies.
- Auditability: Ability to trace and verify all transactions or data modifications through an immutable, time-stamped ledger, enabling forensic analysis and accountability.
- Compliance: Adherence to legal or regulatory frameworks (e.g., GDPR and eIDAS), including data minimization, purpose limitation, and right-to-erasure mechanisms.
- Network Security: Protection of data in transit and infrastructure integrity (e.g., secure P2P communication, resistance to Sybil, or eclipse attacks).
- Physical Security: Safeguards against hardware tampering or physical access to nodes (rarely addressed in the blockchain literature).
- Education: Inclusion of training, awareness, or usability components to support secure adoption.
These definitions guided the coding of all 70 studies and ensured alignment between theoretical constructs and empirical evidence.
3. Review Method
A systematic literature review (SLR) approach was employed based on the guidelines of B. Kitchenham (2009) [38] and the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) 2020 guidelines [28] (see Supplementary Materials). This approach involved a comprehensive analysis of the impact of blockchain on data management security to address the research questions posed. To ensure the reproducibility and credibility of the results, a detailed record of the applied procedure was maintained, which included the creation of a database documenting search equations, inclusion and exclusion criteria, and the quality assessment applied during the review. This systematic method ensures the consistency and robustness of the obtained results.
3.1. Research Problems and Objectives
Considering the relevance of research on the impact of blockchain on data management security, it is crucial to design a search strategy that enables the efficient collection of data from each study for proper analysis. The research questions (RQs) are essential to guide this review. Below are four research questions along with their respective objectives:
- RQ1: What criteria are used to evaluate the effectiveness of blockchain technology?
- RQ2: What types of computational supports, such as frameworks and software architectures, are available for implementing blockchain?
- RQ3: What keywords commonly co-occur in research on the impact of blockchain on data management security?
- RQ4: What are the thematic categories of blockchain and their impact on data management security in organizations?
3.2. Information Sources and Search Strategies
To conduct this review, several high-impact academic databases were consulted, including Scopus, Springer, ScienceDirect, ACM Digital Library, and IEEE Xplore. All databases were last searched on 15 July 2025. Search strings were crafted from the two core constructs in the title—blockchain and data management security—and expanded with controlled terms (thesauri/MeSH when applicable) and free-text synonyms. The keywords and variants used included the following:
- Blockchain/blockchain technology.
- Data management security/data security/data protection/data administration/data management.
The search process was conducted using various keywords, allowing for the extraction and analysis of relevant information. These combinations of terms, known as search equations, were adjusted according to the specific characteristics of each database consulted. Table 1 presents these search equations and the number of documents obtained, adapted to the particularities of each information source.

Table 1.
Information sources and search equations.
3.3. Study Selection
To accurately evaluate the quality of the collected literature, specific exclusion criteria were established. The papers selected for the research underwent an analysis based on an objective list of exclusion criteria. Eight exclusion criteria were implemented, as detailed below, to ensure the inclusion of relevant and high-quality studies:
- EC1: Papers published before 1 July 2018.
- EC2: Papers not written in English.
- EC3: Papers not published in peer-reviewed journals or conferences.
- EC4: Papers that are systematic or bibliometric reviews.
- EC5: Papers with irrelevant titles and keywords.
- EC6: Papers without full-text availability.
- EC7: Papers that are not original.
- EC8: Papers classified as short papers (less than 10 pages).
The study selection process was conducted following the PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) diagram, which provides a visual representation of the filtering and reduction in papers as the defined exclusion criteria were applied. Figure 1 illustrates the PRISMA diagram used in this review.
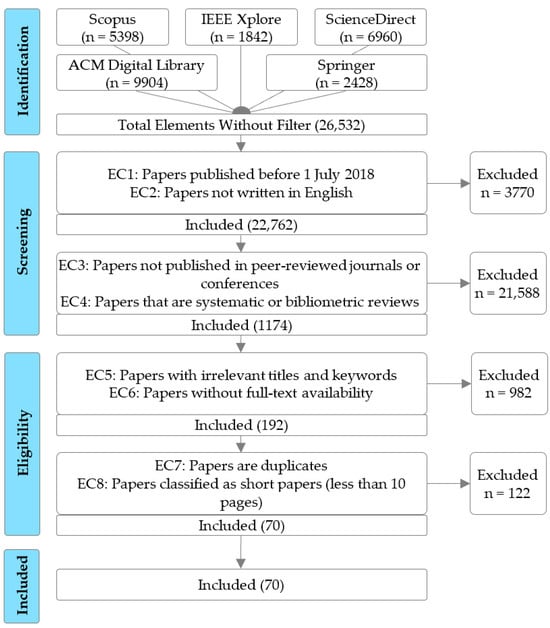
Figure 1.
PRISMA 2020 flow diagram for the study selection process.
The study selection process was conducted independently by two reviewers (J.G. and C.A.), who screened titles, abstracts, and full texts in parallel using the predefined exclusion criteria. Disagreements at any stage were resolved through discussion, and in cases of persistent divergence, a third reviewer (J.C.) was consulted to reach consensus. This dual-reviewer approach ensured methodological rigor and minimized selection bias, in alignment with the PRISMA 2020 recommendations for systematic reviews. As a result of this stage, 70 papers were selected.
3.4. Quality Assessment
At this stage, the selected papers were analyzed using seven quality criteria (QA). This final selection and filtering process consolidated the official list of papers included in the review.
- Are the research objectives clearly specified?
- Was the study designed to achieve these objectives?
- Are the techniques used clearly described, and is their selection justified?
- Are the data collection methods adequately described?
- Are the collected data adequately described?
- Are statistical techniques appropriately applied for data analysis, and are their uses justified?
- How clear are the links between the data, interpretation, and conclusions?
The application of these quality criteria facilitated a thorough evaluation of the selected papers, ensuring they met the established standards and were suitable for inclusion in the review. All the papers met the quality criteria, presenting clear objectives, appropriate design, well-founded methods and analysis, and transparent results. The 70 primary studies were independently assessed by two reviewers using a 7-item quality checklist, with each item scored on a binary scale (0 = not met, 1 = met). The total score per paper ranged from 0 to 7. To ensure methodological rigor, only studies scoring 5 or higher were included in the final synthesis. All 70 papers met this threshold, with scores distributed as follows: 12 papers scored 7/7, 38 scored 6/7, and 20 scored 5/7. No studies were excluded at this stage, as even borderline cases (score = 5) demonstrated sufficient methodological soundness after consensus discussion. Discrepancies in scoring were resolved through discussion between the two reviewers, with arbitration by a third reviewer when needed. Cohen’s kappa was not computed since disagreements were resolved through discussion, which we explicitly acknowledge as a limitation of this SLR.
Furthermore, all retained studies complied with the exclusion criteria (EC1–EC8) and demonstrated operational relevance by explicitly addressing at least one key dimension of data-management security—confidentiality, auditability/integrity, availability, or regulatory compliance. This ensured that the final corpus of 70 papers was both methodologically rigorous and thematically aligned with the objectives of this systematic review. While this checklist assessed methodological soundness, it did not evaluate the risk of bias in the traditional Cochrane sense (e.g., selection, performance, and detection bias), as most studies are design-science prototypes or proof-of-concept implementations rather than controlled experimental trials.
3.5. Data Extraction Strategies
In this phase, the necessary information was extracted from the final list to address the set of research questions. The data collected from each article included the following: article title, URL, source, year, country, ISSN, type of publication, name of the publication, authors, affiliation, quartile, H-index, number of citations, methodology, abstract, and keywords. It should be noted that not all papers addressed all the research questions. Data management was performed using the Mendeley desktop application (v1.19.8). The full data extraction sheet, including all coded variables and operational definitions, is provided in Appendix A (Only the first five and last five rows are shown due to space constraints).
Outcomes: (1) effectiveness criteria (counts, %); (2) computational supports/platforms (counts, %); (3) keyword co-occurrences (weights); and (4) thematic categories (density/centrality). All compatible results per study were sought.
When a study spanned multiple methodological approaches (e.g., combining ML and cryptography), it was assigned to the category that represented its primary contribution, as determined by the research objective and evaluation methodology. Disagreements were resolved through discussion and, if needed, arbitration by a third reviewer (J.C.).
3.6. Synthesis Approach and Heterogeneity Considerations
Given the substantial methodological and contextual diversity of the included studies—spanning simulation-based prototypes and real-world deployments across Big Data, blockchain, and data management (cloud, distributed storage/auditing, HDFS/IPFS, provenance, and integrity verification) a narrative–thematic synthesis approach was adopted, following the framework proposed by Popay et al. [12] for qualitative evidence. This approach integrates the following:
- Descriptive numerical summary (frequencies and percentages) to map the distribution of methods, criteria, and tools (RQ1–RQ2);
- Thematic coding and co-occurrence analysis (using Callon’s centrality–density method and cosine similarity) to identify conceptual clusters (RQ3–RQ4);
- Critical interpretive synthesis to uncover field-level patterns, such as the tension between technology-driven experimentation and governance-oriented research.
A statistical meta-analysis was not feasible due to the absence of comparable effect sizes, heterogeneous evaluation metrics (e.g., execution time, gas consumption, and accuracy), and the exploratory nature of most primary studies. Because primary studies used non-comparable benchmarks (e.g., custom simulators, proprietary datasets, or ad hoc baselines), we did not compute pooled effect sizes. Instead, we report extreme and representative values with explicit citation to their source studies, acknowledging the inherent heterogeneity as a key limitation of the current literature. However, study heterogeneity was explicitly acknowledged and analyzed: 68.5% of studies rely on simulated or small-scale environments and evaluation criteria vary widely across domains—limiting cross-study comparability.
Regarding publication bias, the predominance of engineering-oriented venues (68.5% from IEEE Xplore) may favor positive results and technical feasibility over negative findings, socio-technical critiques, or policy-oriented analyses. While funnel plots or Egger’s test are not applicable in this qualitative context, this potential bias is acknowledged as a limitation in Section 5.
4. Results and Discussion
This section presents and analyzes the results obtained, contextualizing them within the existing literature and the objectives established in the research. The findings are discussed in detail, compared with previous studies to highlight contributions, similarities, and differences, and their relevance and applicability to data security management using blockchain technology are evaluated.
4.1. Overview of the Studies
Figure 2 shows the distribution of papers by year and source of publication. This figure provides an overview of the temporal evolution of publications and highlights the main journals in which research on blockchain and its impact on data management security has been disseminated. The graphical representation facilitates the identification of trends and patterns in scientific productions related to this topic.
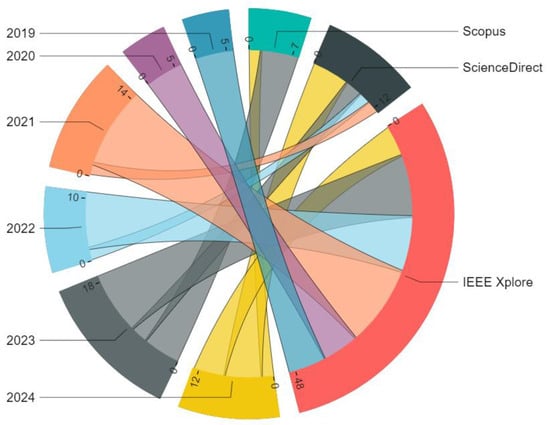
Figure 2.
Distribution of the 70 primary studies by year (2019–2024) and source database.
The Chord diagram illustrates the distribution of papers published between 2019 and 2024 across different academic sources. It is observed that IEEE Xplore is the predominant source, especially in 2023, indicating an increase in the publication of research on blockchain in that year. ScienceDirect shows a more moderate trend, with consistent but smaller contributions over the years. Scopus, on the other hand, experienced a notable increase in 2022, although its contributions are smaller in other years.
It is worth noting that IEEE Xplore accounts for 68.5% of the final corpus (48 out of 70 papers), which may introduce a technological and engineering bias toward infrastructure-oriented solutions, potentially underrepresenting socio-organizational, legal, or policy-oriented perspectives. This selection bias should be carefully considered when generalizing the findings of this research, and future research should actively incorporate interdisciplinary and diversified sources to mitigate such imbalances.
According to Kianoush Kiania and collaborators [10], their research highlights that the main databases for searching academic papers related to blockchain include IEEE Xplore, Elsevier, Springer, and Wiley. These platforms are recognized for their vast collections of high-quality, peer-reviewed research covering various technological and scientific disciplines.
The predominance of publications in IEEE Xplore suggests that studies on blockchain and its influence on data management are gaining relevance in technological and academic sectors, with a particular focus on engineering and information systems. This trend may imply applications and benefits in other areas such as healthcare, finance, and public administration, underscoring the importance of integrating professionals from various disciplines to leverage blockchain technologies for improving processes and data security.
Table 2 synthesizes the findings of the most relevant reviewed studies, methodologically categorized to identify patterns of development, performance, and limitations in the use of blockchain applied to data management security. This taxonomy enables the visualization of the distribution of approaches, ranging from conceptual frameworks to empirical implementations, thus facilitating the recognition of both the scientific maturity of the field and the existing technical and socio-organizational gaps. Its comprehensive structure supports a cross-sectional interpretation of trends and shortcomings that shape the future research agenda.

Table 2.
Synthesis of findings by methodological category.
It should be noted that performance metrics are highly heterogeneous across studies and often reported in isolation. For instance, “execution time” is mentioned in only 6 of the 70 studies (8.6%), while “accuracy” appears in 8 (11.4%). Given that experimental setups differ, these figures are presented as study-level counts and percentages without pooling; where applicable, single-study extrema were identified in the text. This fragmentation prevents meta-analytic synthesis and limits generalizability—reinforcing the need for cross-domain evaluation standards, as discussed in Section 5.
Method Category: The taxonomy shows a clear dominance of empirical implementations (57.4%), reflecting the field’s orientation toward applied solutions in IoT, healthcare, smart cities, supply chain management, and VANETs. Cryptographic and security protocol research accounts for 24.6%, reaffirming the centrality of confidentiality and integrity guarantees. Machine learning and deep learning hybrids (14.8%) indicate an emergent shift toward intelligent, adaptive blockchain-based systems. Conversely, theoretical and conceptual frameworks (3.3%) remain scarce, evidencing that regulatory, governance, and conceptual foundations advance more slowly than technical experimentation. Blockchain for data management is still at a technology-proving stage, most venues are engineering-oriented (68.5% from IEEE Xplore), and researchers prioritize demonstrating feasibility (security, latency, and audit trails) over developing governance or interoperability theories.
Methods used: Methodological diversity ranges from advanced cryptographic protocols (AES, RSA, PoI, and ZKP) to distributed architectures (IPFS, HDFS, MQTT, and RFID), often combined with AI techniques such as LSTM, Seq2Seq, Capsule Networks, and federated learning. This hybridization illustrates a field where blockchain is consistently integrated with consensus algorithms, encryption schemes, and predictive analytics. The prevalence of IoT-oriented and healthcare-focused solutions underscores the critical role of interoperability, traceability, and privacy preservation in sensitive data environments.
Performance: Reported outcomes demonstrate significant efficiency gains (execution time reduced by up to 84.75%), high accuracy levels (95–99%), and reduced energy consumption and latency compared to conventional systems. AI-driven approaches report robust language metrics (BLEU ≈ 0.85), while distributed frameworks validate throughput and cost improvements in data-intensive contexts. However, the lack of standardized benchmarks, heterogeneous evaluation metrics, and reliance on simulated or small-scale environments limit cross-study comparability and hinder external generalizability. This heterogeneity in evaluation approaches—ranging from latency benchmarks to compliance checklists—prevents statistical pooling and underscores the need for standardized, cross-domain metrics in future research. It should be noted that performance metrics (e.g., 84.75% faster execution [1] and 95–99% accuracy [16,18,49]) are not aggregated across studies but represent peak results reported in individual papers, often under controlled or simulated conditions. Due to heterogeneous evaluation contexts (e.g., different baselines, datasets, and hardware), cross-study normalization was not feasible—hence our reliance on descriptive synthesis rather than meta-analysis (see Section 3.6).
Limitations: Recurring constraints include scalability bottlenecks, high computational and resource costs, and interoperability challenges across heterogeneous systems. Many studies rely on semi-trusted or centralized intermediaries, undermining full decentralization. AI-based studies exhibit overemphasis on threat scenarios, with limited focus on usability and end-user experience. Furthermore, the absence of large-scale real-world validations and cross-sector case studies highlights a maturity gap between proof-of-concept deployments and production-ready solutions.
Qty. (%): The distribution indicates that over half of the studies (57.4%) fall into empirical implementations, signaling a practice-driven field. Cryptographic/security protocols (24.6%) represent a consolidated methodological stream, while AI integration (14.8%) emerges as a promising but still peripheral domain. The marginal share of conceptual studies (3.3%) reveals insufficient theoretical and policy-level consolidation. This asymmetry illustrates a fragmented ecosystem in which technological progress outpaces regulatory frameworks, adoption models, and external evaluations. This empirical dominance reflects broader trends in emerging technology research, where proof-of-concept prototypes are prioritized over governance or policy frameworks due to funding incentives, publication pressures, and the rapid pace of technical innovation. The scarcity of theoretical contributions (3.3%) is particularly concerning because it suggests a field advancing without foundational principles for interoperability, accountability, or regulatory alignment. Without conceptual scaffolding, even the most efficient empirical solutions risk becoming isolated silos that cannot scale across organizational or jurisdictional boundaries. This pattern aligns with the “technology-first” bias observed in early stage digital innovation, where engineering feasibility often overshadows socio-technical sustainability.
Collectively, these patterns reveal a field at a crossroads: technically vibrant but conceptually undernourished. The overwhelming focus on empirical validation—while valuable—has come at the expense of critical reflection on governance, standardization, and long-term viability. Until this imbalance is addressed, blockchain-based data security solutions will remain fragmented, context-bound, and ill-equipped for institutional adoption at scale.
The findings confirm that blockchain research in data management security is heavily technology-driven, with robust experimentation yet limited theoretical consolidation. The imbalance between applied implementations and conceptual foundations constrains interoperability and standardization. The increasing convergence of AI and cryptographic protocols underscores a trajectory toward hybrid intelligent systems. Nevertheless, the fragmented performance metrics and lack of real-world validations remain critical barriers to scalability and adoption. Future research must prioritize large-scale pilots, governance models, and compliance frameworks to bridge the gap between innovation and institutional integration.
Taken together, these patterns have direct implications for data management practice and digital sustainability. In operational terms, blockchain-based data security frameworks can reduce dependence on central intermediaries, provide tamper-evident audit trails for regulatory reporting, and support cross-organizational data sharing in supply chains, healthcare consortia, and smart-city infrastructures. When combined with interoperable architectures and clear governance rules, these properties can contribute to more resilient and transparent digital ecosystems, aligning with sustainable development goals related to trustworthy institutions and responsible data use. However, the predominance of small-scale prototypes and heterogeneous evaluation metrics means that many reported benefits remain difficult to generalize, underscoring the need for standardized benchmarks and longitudinal, multi-stakeholder deployments.
4.2. Answers to the Research Questions
The responses to the research questions posed in this study are presented below, considering relevant comments, derived discussions, and implications for future research. A thorough search of papers in relevant journals and conferences regarding the impact of blockchain on data management security was conducted. Recognized databases were used, and only the most relevant papers were selected after a meticulous review.
RQ1: What criteria are used to evaluate the effectiveness of blockchain technology?
Table 3 and Figure 3 present the security criteria used to evaluate blockchain’s effectiveness, along with the corresponding references and the percentages represented. The table provides a detailed view of the various security aspects considered in the literature and their frequency of occurrence in the reviewed studies.

Table 3.
Criteria for measuring blockchain’s effectiveness.
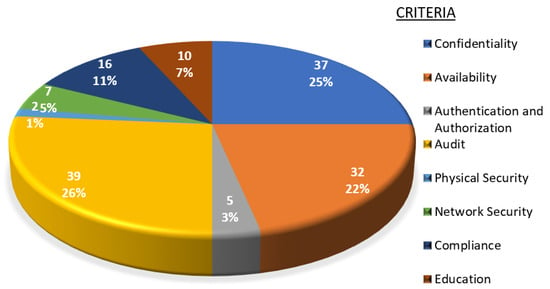
Figure 3.
Number of primary studies addressing each security evaluation criterion.
The findings show that the most common criteria for evaluating blockchain’s effectiveness are Confidentiality (37 papers, 25%) and Auditability (39 papers, 26%), indicating that the ability to protect information and maintain a transparent record are key aspects. Availability is also relevant (32 papers, 22%), reflecting the importance of ensuring that blockchain-based systems are always operational. Other criteria, such as Compliance and Education, are less represented, suggesting that these are still being explored in more specific and less frequent areas. Physical Security is the least represented criterion, showing that it is less addressed in the blockchain literature.
Authors Terje Haugum et al. [25] note that the criteria for measuring effectiveness and quality are producer authority, methodology, and objectivity. On the other hand, Sejin Han and Sooyong Park [23] indicate that legality, purpose limitation, loyalty, and transparency are the criteria for evaluating blockchain’s effectiveness. Additionally, Ammar AL-Ashmori et al. [84] highlight in their review article that the criteria for measuring effectiveness include intention, perceived usefulness, perceived ease of use, trust, and security.
These results emphasize that Confidentiality and Auditability are priorities in evaluating blockchain’s effectiveness, reinforcing the importance of its implementation in sensitive sectors such as healthcare and finance. The low representation of Physical Security and Authentication suggests an opportunity for future research. These findings can guide researchers and practitioners in prioritizing critical aspects when evaluating or implementing blockchain-based solutions in their respective fields.
RQ2: What types of computational supports,such as frameworks and software architectures,are available for implementing blockchain?
Table 4 and Figure 4 provide an overview of development tools used in the blockchain domain, including frameworks and software architectures. The table highlights the main tools and their representation in the reviewed literature, offering a clear view of the computational supports available for developing blockchain-based solutions.

Table 4.
Blockchain development tools.
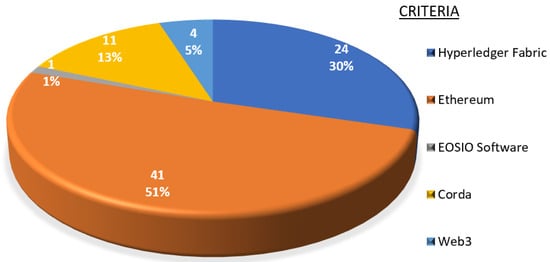
Figure 4.
Prevalence of computational supports and development frameworks in the reviewed studies.
The results show that Ethereum is the most used framework, appearing in 51% of the studies, highlighting its popularity and flexibility in blockchain development. Hyperledger Fabric is also prominently mentioned (30%), suggesting its relevance in corporate and private applications. Corda is present in 13% of the studies, indicating its use in implementations requiring greater control and privacy. Web3 and EOSIO Software have lower representation, reflecting more limited or specialized use in specific contexts.
According to Emeka Chukwu and Lalit Garg [11], the most commonly used frameworks and development tools in blockchain technology are data sharing and access control. Meanwhile, Maria Guzman Lizama and Jair Huesa y Brian Meneses Claudio [85] indicate that the technologies most involved in blockchain applications include cloud environment, smart contracts, and Ethereum.
The dominance of Ethereum and Hyperledger Fabric suggests that blockchain research and development favor technologies with extensive support and an active community, which can facilitate its adoption in financial, corporate, and decentralized application development sectors. The less-mentioned tools, such as Web3 and EOSIO, point to potential areas for future innovations and more specific studies. These findings are valuable for guiding developers and researchers toward the most relevant and applicable platforms for their projects.
RQ3: What keywords commonly co-occur in research on the impact of blockchain on data management security?
The bibliometric network presented in Figure 5 illustrates the co-occurrence of keywords in the reviewed studies. The network nodes represent high-impact keywords, and the connections between them show how frequently these terms appear together in publications. To construct the keyword co-occurrence network, we computed the association strength between terms to reveal conceptual coupling in the blockchain data management security literature. Candidate terms were derived from author keywords and normalized title/abstract n-grams (uni/bigrams) after lower-casing, tokenization, lemmatization, and domain stop-word removal. We formed a term–document matrix using binary or TF–IDF weights. Co-occurrence was defined as joint presence within the same document; the association strength between terms was quantified via cosine similarity of their document vectors:
where is the weight of term in document . A higher indicates a stronger co-occurrence and conceptual affinity. The resulting weighted graph was thresholded (minimum term frequency and similarity) and pruned to its giant component; communities were detected to identify thematic clusters.
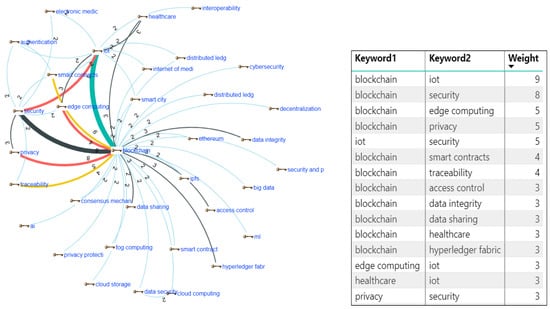
Figure 5.
Bibliometric network of keywords from 70 SLR articles, constructed using cosine similarity of term–document vectors. Minimum term frequency = 2, minimum association strength = 0.3.
Keyword co-occurrence analysis was performed using RAj (Research Assistant j), a Python-based (v3.12.11) NLP and bibliometric toolkit developed by the authors. The analysis used the following parameters: (i) minimum occurrence threshold = two (i.e., only keywords appearing in ≥2 studies were included), (ii) binary term-document weighting, (iii) association strength quantified via cosine similarity of term–document vectors, and (iv) network normalization with a minimum association strength threshold of 0.3. The full co-occurrence matrix is provided in Appendix B.
The results reveal that the bibliometric network shows that the nodes for “blockchain” and “security” have the broadest connections with other terms, indicating their central role in research on data management. “Blockchain” co-occurs most frequently with “IoT” (weight of nine) and “security” (weight of eight), highlighting the relevance of the intersection between these areas in the literature. The connection of “blockchain” with “edge computing,” “privacy,” and “security” (all with a weight of five) reflects an interest in integrating advanced technologies to enhance privacy and process automation. Other notable co-occurrences include “blockchain” with “traceability” and “smart contracts” (both with a weight of four), suggesting interest in ensuring transparency and access control in distributed systems.
Figure 6 shows the top 15 keywords by frequency, confirming the centrality of “blockchain” and “security” and the strong coupling with “IoT” and “privacy”.
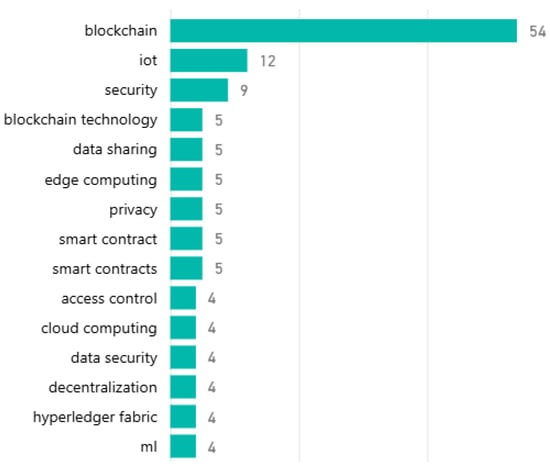
Figure 6.
Top 15 most frequent keywords in the reviewed papers.
According to Faheem Ahmad Reegu and colleagues [28], the most frequently occurring keywords in blockchain and data security research include blockchain, security, privacy, integrity, and scalability. In addition, Mohd Nishat Faisal and collaborators [21] identify blockchain, supply chain management, blockchain technology, and literature review as frequently co-occurring keywords in blockchain-related studies. Similarly, Reegu and his team [12] mention blockchain, records management, healthcare, and privacy as key terms in their paper, reinforcing the centrality of data protection and operational efficiency in blockchain research. Meanwhile, Habib Sadri and co-authors [15] emphasize blockchain, building industry, Internet of Things, and digital twin as the most frequent keywords, highlighting the integration of blockchain with smart technologies. Finally, Jinglang Yang and collaborators [86] highlight blockchain, technology, management, framework, security, and privacy as the keywords with the highest co-occurrence, confirming the consistency of these terms across diverse application domains.
These findings suggest that blockchain research focuses on applications that strengthen security and interoperability with IoT, as well as emerging technologies like edge computing to improve system efficiency. The lower representation of combinations such as “healthcare” and “IoT” (weight of three) indicates opportunities to expand research into specific sectors such as healthcare. The co-occurrence of terms like “privacy” and “security” underscores the importance of developing solutions that balance data protection with accessibility and transparency.
RQ4: What are the thematic categories of blockchain and their impact on data management security in organizations?
Figure 7 illustrates the thematic categories related to blockchain and their impact on data management security in organizations. The topics are classified based on their level of development (density) and relevance (centrality). Marginal topics, with low development and relevance, suggest emerging areas or those receiving less attention in the current literature.
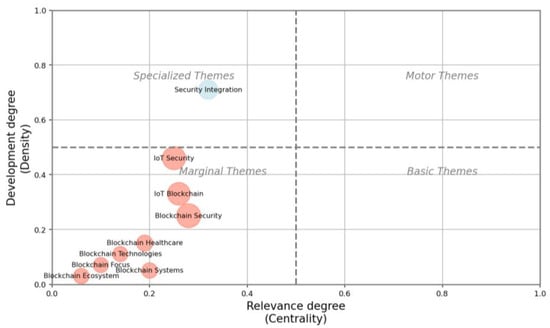
Figure 7.
Thematic map of blockchain and data management security research based on Callon centrality–density metrics.
To construct the thematic map, the Callon centrality–density method was used to determine the relevance and development of research themes on blockchain applied to data management security. This approach evaluates each cluster’s internal cohesion (density) and external connectivity (centrality) within the thematic network. The density (D) indicates the internal strength and development of a theme, while centrality (C) represents its degree of interaction with other clusters. Both metrics are calculated as follows:
where represents the link strength between keywords j and k within cluster i, is the number of keywords in cluster i, and indicates the link strength between cluster i and any other cluster j.
Thematic mapping applied the Callon centrality–density method via RAj, using the same co-occurrence matrix and thresholds as above.
The figure provides a visual analysis of the thematic map of the literature on blockchain and data security, categorizing research topics into specialized and marginal clusters. The accompanying table complements this visualization with quantitative indicators—including density, centrality, citation counts, and document frequencies—for each identified theme, thereby enabling a comprehensive analytical assessment. The theme “Security Integration” exhibits the highest density (0.71) and a moderate centrality (0.32), reflecting substantial thematic maturity and moderate structural relevance within blockchain-based data security research. In contrast, “IoT Security” and “Blockchain Security”, although classified as marginal, demonstrate high citation counts (2486 and 2686, respectively), and document volumes (78 and 84), indicate a strong research interest yet an emerging developmental stage. Themes such as “Blockchain Healthcare” and “Blockchain Ecosystem” show very low densities (0.15 and 0.03) and centralities below 0.2, highlighting highly specific but underdeveloped research areas within the current thematic structure.
Adeel Nasir and colleagues [26] emphasize topics such as “blockchain, bitcoin, and cryptocurrency” and “consensus proof of work” as the most relevant categories in their systematic review. Meanwhile, Min Xu, Xingtong Chen, and Gang Kou [27] identify the most influential disciplines in blockchain technology as “computer science,” “telecommunications,” and “management.”
Research on “Security Integration” indicates a substantial potential for implementing robust data security solutions through blockchain, applicable across multiple domains, including healthcare and IoT technologies. Given their increasing relevance, these themes are expected to achieve geographical adoption in highly digital environments within the next 3 to 5 years, evolving toward more specialized and segmented information security solutions as blockchain technology continues to advance and adapt to new applications and emerging challenges.
5. Conclusions and Future Research
This study synthesizes 70 peer-reviewed papers (2018–2024) to provide a comprehensive mapping of blockchain research in data management security. It offers a systematic review that evaluates the effectiveness of blockchain technologies, emphasizing critical dimensions such as confidentiality and auditability—core criteria for ensuring data protection in distributed systems and directly addressing Research Question 1 (RQ1). Regarding computational supports, Ethereum and Hyperledger Fabric emerge as the most utilized tools, reflecting their relevance in both business and academic developments (aligned with RQ2). Additionally, the co-occurrence of keywords like “blockchain” and “security” underscores the importance of security and the integration of complementary technologies, such as IoT and privacy, in the context of data management (aligned with RQ3). Lastly, the analyzed research categories indicate that topics like “IoT security” and “blockchain and Ethereum” require further exploration, suggesting potential areas for development and expansion (aligned with RQ4).
This pattern shows that research on blockchain for data management security is still predominantly implementation-driven. Most studies validate feasibility in IoT, healthcare, smart city, or supply chain scenarios, but only a small subset turns these prototypes into reusable governance, interoperability, or compliance models. In other words, technical mechanisms (smart contracts, access control, and edge/fog integration) are maturing faster than organizational, regulatory, and cross-platform frameworks.
Domain-specific implications for sustainable digital ecosystems: In fintech, blockchain contributes to sustainability through auditable transactions, immutable traceability, and automated compliance, reducing reconciliation overheads and enhancing institutional trust. In supply chain management, it fosters efficiency and sustainability via transparent provenance, waste reduction, and ethical sourcing, provided interoperability with ERP/MES platforms and consortium governance are achieved. In healthcare and public-sector data infrastructures, decentralized authorization and consent-based access strengthen accountability and regulatory compliance. Across all domains, blockchain’s sustainable potential emerges when interoperable architectures and standardized performance metrics are combined with transparent governance, aligning with SDG 9 and SDG 16.
Critically, we observe a persistent maturity gap between technical feasibility and sustainable implementation. While 57.4% of studies focus on empirical prototypes demonstrating 84.75% execution-time improvements and 95–99% accuracy in IoT, healthcare, and supply chain contexts, only 3.3% address governance frameworks necessary for long-term sustainability. This imbalance impedes blockchain’s contribution to UN Sustainable Development Goals 9 (industry, innovation, and infrastructure), 12 (responsible consumption), and 16 (peace, justice, and strong institutions), where transparent data management is essential.
Beyond methodological limitations, the primary studies also reveal practical challenges for real-world blockchain deployments. Many proofs-of-concept report difficulties integrating blockchain with legacy systems and heterogeneous databases, often resulting in duplicated data models and added complexity. Several works also note regulatory uncertainty regarding GDPR and eIDAS—particularly the right to erasure and cross-border data flows—which limits long-term adoption. Energy consumption and performance overheads remain significant in permissionless or hybrid settings. Overall, these issues indicate that sustainable blockchain-based data management requires not only robust technical architectures but also clearer governance, regulatory guidance, and organizational readiness.
The review, limited to studies in English from the past 7 years, could have been expanded to include work in other languages for a more comprehensive perspective. It is recommended to delve deeper into the exploration of marginal topics and the integration of blockchain with emerging technologies. Future research should therefore bridge this maturity gap by (i) proposing standardized effectiveness criteria that allow comparisons across sectors and (ii) designing interoperable, GDPR/eIDAS-aware architectures that reconcile blockchain immutability with data-protection rights. In methodological terms, future SLRs and replications should also compute inter-rater agreement (e.g., Cohen’s kappa) to quantify reviewer consistency, especially when borderline studies are included after consensus, and the use of a narrative–thematic synthesis approach, which, while appropriate for heterogeneous qualitative evidence, limits quantitative generalizability. Furthermore, future reviews should adopt a pre-registered, domain-specific evidence taxonomy—encompassing simulation/testbed studies, single-site pilots, and multi-site production deployments with externally verifiable service guarantees—and require explicit reporting to enable robust and comparable maturity analyses across studies.
Supplementary Materials
The following supporting information can be downloaded at: https://www.mdpi.com/article/10.3390/su18010185/s1. PRISMA Checklist [87].
Author Contributions
Conceptualization, J.G.-C., H.S.-M., and V.P.-D.; methodology, J.G.-C., C.A.R., and J.C.L.; software, V.P.-D. and M.N.-A.; validation, H.S.-M., V.P.-D., and M.N.-A.; investigation, J.G.-C., J.C.L., and C.A.R.; resources, C.A.R.; writing—original draft preparation, H.S.-M. and V.P.-D.; writing—review and editing, J.G.-C., M.N.-A., and C.A.R.; visualization, J.G.-C. and H.S.-M.; project administration, J.C.L. and C.A.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Universidad Nacional Federico Villarreal.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflicts of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Appendix A. Data Extracted from the Reviewed Papers
| Ref. | Title | Source | Year | Summary | Citation No. | Keywords |
| [1] | EdgeMediChain: A Hybrid Edge Blockchain-Based Framework for Health Data Exchange | IEEE Xplore | 2020 | Recently, researchers around the world in medical institutions and pharmaceutical companies are demanding wider access to healthcare data for secondary use in order to provide enhanced and personalized medical services. For this purpose, healthcare information exchange between health authorities can be leveraged as a fundamental concept to meet these demands and enable the discovery of new insights and cures. However, health data are highly sensitive and private information requires strong authentication and authorization procedures to manage access to them. In this regard, cloud paradigms have been used in these e-healthcare solutions, but they remain inefficient due to their inability to adapt to the expanding volume of data generated from body sensors and their vulnerability against cyberattacks. Hence, collaborative and distributed data governance supported by edge computing and blockchain promises enormous potential in improving the performance and security of the whole system. In this paper, we present a secure and efficient data management framework, named ‘EdgeMediChain’, for sharing health data. The proposed architecture leverages both edge computing and blockchain to facilitate and provide the necessary requirements for a healthcare ecosystem in terms of scalability, security, as well as privacy. The Ethereum-based testbed evaluations show the effectiveness of EdgeMediChain in terms of execution time with a reduction of nearly 84.75% for 2000 concurrent transactions, higher throughput compared to a traditional blockchain, and scalable ledger storage with a linear growth rate. | 87 | blockchain, iot, data sharing, edge computing, electronic medical records, healthcare, privacy, security, smart contracts |
| [78] | Blockchain for Global Vaccinations Efforts: State of the Art, Challenges, and Future Directions | Scopus | 2023 | The emergence of the coronavirus disease 2019 (COVID-19) global crisis negatively affected all aspects of human life. One of the most important methods used worldwide to survive this global crisis is the vaccination process to circumvent the proliferation of this pandemic. Many restrictions were alleviated in many countries such as access to public facilities and events. There is a huge amount of data about vaccination campaigns that are collected and maintained worldwide. The vaccination data can be analyzed to find out how the alleviation of restrictions can be applied if the data management process requires the preservation of key aspects like trust, transparency, and availability for easy and reliable access to such data. In this regard, blockchain technology is an excellent choice for meeting the requirements and providing a secure trusted framework for global verification. In this article, the related literature on blockchain technology is surveyed and summarized for all systems that embody solutions. The pros and cons of each solution are presented and provide a comparative summary. Furthermore, a detailed analysis is given to present the current problems and provide a promising mechanism to verify the vaccinated persons anywhere in the world, in a secure manner while retaining individual privacy. | 0 | blockchain, coronavirus disease 2019, decentralization, Ethereum, immunization, Merkle proof, vaccination |
| [2] | A Blockchain-Based Consent Mechanism for Access to Fitness Data in the Healthcare Context | IEEE Xplore | 2022 | Wearable fitness devices are widely used to track an individual’s health and physical activities to improve the quality of health services. These devices sense a considerable amount of sensitive data processed by a centralized third party. While many researchers have thoroughly evaluated privacy issues surrounding wearable fitness trackers, no study has addressed privacy issues in trackers by giving control of the data to the user. Blockchain is an emerging technology with outstanding advantages in resolving consent management privacy concerns. As there are no fully transparent, legally compliant solutions for sharing personal fitness data, this study introduces an architecture for a human-centric, legally compliant, decentralized, and dynamic consent system based on blockchain and smart contracts. Algorithms and sequence diagrams of the proposed system’s activities show consent-related data flow among various agents, which are used later to prove the system’s trustworthiness by formalizing the security requirements. The security properties of the proposed system were evaluated using the formal security modeling framework SeMF, which demonstrates the feasibility of the solution at an abstract level based on formal language theory. As a result, we have shown that blockchain technology is suitable for mitigating the privacy issues of fitness providers by recording individuals’ consent using blockchain and smart contracts. | 12 | blockchain, data protection, decentralized, fitness tracker, human-centric, privacy, regulation, security requirements, trust, wearable devices |
| [5] | Applying Access Control Enabled Blockchain (ACE-BC) Framework to Manage Data Security in the CIS System | Scopus | 2023 | Cybersecurity information sharing (CIS) is important in different business processes to secure data transmission because it comprises Internet of Things (IoT) connectivity, workflow automation, collaboration, and communication. The shared information is influenced by intermediate users and alters the originality of the information. Although risk factors such as confidentiality and privacy of the data are reduced when using a cyber defense system, existing techniques rely on a centralized system that may be damaged during an accident. In addition, private information sharing faces rights issues when accessing sensitive information. The research issues influence trust, privacy, and security in a third-party environment. Therefore, this work uses the Access Control Enabled Blockchain (ACE-BC) framework to enhance overall data security in CIS. The ACE-BC framework uses attribute encryption techniques to manage data security, while the access control mechanism limits unauthorized user access. The effective utilization of blockchain techniques ensures overall data privacy and security. The efficiency of the introduced framework was evaluated using experimental results, and the experimental outcome indicated that the recommended ACE-BC framework enhanced the data confidentiality ratio (98.9%), the throughput ratio (98.2%), the efficiency ratio (97.4%), and the latency rate (10.9%) when compared to other popular models. | 5 | access control enabled blockchain (ace-bc), blockchain, cyber information sharing, privacy, security, unauthorized users |
| [16] | DHT- and Blockchain-Based Smart Identification for Video Conferencing | ScienceDirect | 2022 | Video conferencing applications help people communicate via the Internet and provide a significant and consistent basis for virtual meetings. However, integrity, security, identification, and authentication problems are still universal. Current video conference technologies typically rely on cloud systems to provide a stable and secure basis for executing tasks and processes. At the same time, video conferencing applications are being migrated from centralized to decentralized solutions for better performance without the need for third-party interactions. This article demonstrates a decentralized smart identification scheme for video conferencing applications based on biometric technology, machine learning, and a decentralized hash table combined with blockchain technology. We store users’ information on a distributed hash table and transactional events on the distributed ledger after identifying users by implementing machine learning functions. Furthermore, we leverage distributed ledger technology’s immutability and traceability properties and distributed the hash table’s unlimited storage feature to improve the system’s storage capacity and immutability by evaluating three possible architectures. The experimental results show that an architecture based on blockchain and distributed hash tables has better efficiency but needs a longer time to execute than the two other architectures using a centralized database. | 7 | blockchain, decentralized web hosting, ipfs, ml, video conferencing |
| [73] | Blockchain-Based Decentralized Storage Design for Data Confidence Over Cloud-Native Edge Infrastructure | IEEE Xplore | 2024 | As the modern computing market experiences a surge in demand for efficient data management solutions, challenges posed by centralized storage systems become more pronounced, especially with the proliferation of Internet of Things devices. Centralized storage, although cost-effective, faces issues of scalability, performance bottlenecks, and security vulnerabilities. With decentralized storage, data are distributed across nodes, offering redundancy, data availability, and enhanced security. Unfortunately, decentralized storage introduces its own challenges, such as complex data retrieval processes, potential inconsistencies in data versions, and difficulties in ensuring data privacy and integrity in a distributed setup. Effectively managing these challenges calls for innovative techniques. In response, this paper introduces a decentralized storage system that melds cloud-native concepts with blockchain technology. The proposed design delivers enhanced scalability, data security, and privacy. When operating on a containerized edge infrastructure, this storage system provides higher data-transfer speeds than the interplanetary file system. This research thus blends the advantages of cloud-native frameworks with the security mechanisms of blockchain, crafting a storage system that addresses the present-day challenges of data management in decentralized settings. | 0 | edge computing, blockchain, cloud-native orchestration, distributed storage |
| [74] | Data Sharing Network Model and Mechanism of Power Internet of Things in Virtualized Environment | IEEE Xplore | 2022 | To solve the problems of low security and low reliability in data sharing, this paper proposes a data sharing network model and mechanism of power Internet of Things in a virtualized environment. Due to the different coverage of the power Internet of Things, this paper proposes a node model based on the node network theory of blockchain technology. This model divides network nodes into data consumer nodes, data storage nodes, routing nodes, and coordination nodes according to business requirements. Through the cooperation of the four types of nodes, data sharing between multiple power Internet of Things can be realized efficiently. To solve the problem of low security in data sharing, this paper constructs a data transmission contribution analysis model of network nodes and a data access authorization model. The data transmission contribution degree model can fairly evaluate the behavior of network nodes based on the contribution degree, so as to quickly find malicious nodes. The data access authorization model calculates the entropy weight of each Internet of Things according to the trust level, thereby calculating the credibility of data sharing. To solve the problem of low transmission reliability of network nodes, a set of alternative links is constructed for data sharing routes. With load balancing as the goal, a relative cost value evaluation model is constructed for each route. The shortest route with the best relative cost value is regarded as the optimal data sharing route. In the simulation experiment, the related mechanisms are first improved based on the mechanism of this paper, which verifies that the mechanism of this paper improves the utilization and reliability of network resources in terms of data sharing routing. Secondly, it is verified that the mechanism of this paper improves the success rate and availability rate of network resources in terms of data security sharing. | 3 | Power internet of things, data sharing, network model, sharing mechanism |
| [75] | Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad hoc Network | IEEE Xplore | 2019 | A vehicular ad hoc network (VANET) can improve the flow of traffic to facilitate intelligent transportation and to provide convenient information services, where the goal is to provide self-organizing data transmission capabilities for vehicles on the road to enable applications, such as assisted vehicle driving and safety warnings. VANETs are affected by issues such as identity validity and message reliability when vehicle nodes share data with other nodes. The method used to allow the vehicle nodes to upload sensor data to a trusted center for storage is susceptible to security risks, such as malicious tampering and data leakage. To address these security challenges, we propose a data security sharing and storage system based on the consortium blockchain (DSSCB). This digital signature technique based on the nature of bilinear pairing for elliptic curves is used to ensure reliability and integrity when transmitting data to a node. The emerging consortium blockchain technology provides a decentralized, secure, and reliable database, which is maintained by the entire network node. In DSSCB, smart contracts are used to limit the triggering conditions for preselected nodes when transmitting and storing data and for allocating data coins to vehicles that participate in the contribution of data. The security analysis and performance evaluations demonstrated that our DSSCB solution is more secure and reliable in terms of data sharing and storage. Compared with the traditional blockchain system, the time required to confirm the data block was reduced by nearly six times and the transmission efficiency was improved by 83.33%. | 208 | consortium blockchain, data sharing, data storage, signature verification, vehicular ad hoc network (vanet) |
| [76] | A Blockchain-Based Efficient Data Integrity Verification Scheme in Multi-Cloud Storage | IEEE Xplore | 2022 | The cloud storage service provides the storage and access function for massive data, reducing the management cost for large amounts of data. The data integrity verification scheme in cloud storage can be employed to help users confirm the integrity of outsourced data. Although public data integrity verification schemes allow users to outsource data integrity verification to third-party auditor (TPA), there are still many problems with centralized TPA in terms of security and efficiency. In recent years, researchers have tried to apply blockchain technology to solve the centralization problem of traditional methods, but these schemes do not pay attention to the problem of efficiency degradation caused by the use of blockchain technology. This paper proposes an efficient data integrity verification scheme for multi-cloud storage services by using blockchain technology. The overall verification can verify the integrity of multiple CSPs, which solves the problems of low computational efficiency. Local verification can trace the source to the specific damaged CSP, which is more secure and reliable. In addition, this paper puts the data verification process directly in the blockchain for public execution and provides data integrity verification services without the assistance of any third-party audit platform, avoiding the security problems caused by untrusted TPA. Theoretical analysis and experiments verify the safety and effectiveness of the scheme. | 8 | cloud computing security, blockchain, data integrity, data security |
| [77] | A Blockchain Solution for Remote Sensing Data Management Model | Scopus | 2023 | A large number of raw data collected by satellites are processed by the production chain to obtain a large number of product data, of which the secure exchange and storage is of interest to researchers in the field of remote sensing information science. Authentic, secure data provide a critical foundation for data analysis and decision-making. Traditional centralized cloud computing systems are vulnerable to attack and, once the central server is successfully attacked, all data are be lost. Distributed ledger technology (DLT) is an innovative computer technology that can ensure information security and traceability, is tamper-proof, and can be applied to the field of remote sensing. Although there are many advantages to using DLT in remote sensing applications, there are some obstacles and limitations to its application. Remote sensing data have the characteristics of a large data volume, a spatiotemporal nature, global scale, and so on, and it is difficult to store and interconnect remote sensing data in the blockchain. To address these issues, this paper proposes a trustworthy and decentralized system using blockchain technology. The novelty of this paper is the proposal of a multi-level blockchain architecture in which the system collects remote sensing data and stores them in the Interplanetary File System (IPFS) network; after generating the IPFS hash, the network rehashes the value again and uploads it on the Ethereum chain for public query. The distributed data storage improves data security, supports the secure exchange of information, and improves the efficiency of data management. | 1 | blockchain, distributed ledger technology, remote sensing data management, security, trusted service |
Appendix B. Full Co-Occurrence Matrix
| Keyword1 | Keyword2 | Weight |
| blockchain | iot | 9 |
| blockchain | security | 8 |
| blockchain | edge computing | 5 |
| blockchain | privacy | 5 |
| iot | security | 5 |
| blockchain | smart contracts | 4 |
| blockchain | traceability | 4 |
| blockchain | access control | 3 |
| blockchain | data integrity | 3 |
| blockchain | data sharing | 3 |
| blockchain | healthcare | 3 |
| blockchain | hyperledger fabric | 3 |
| edge computing | iot | 3 |
| healthcare | iot | 3 |
| privacy | security | 3 |
| authentication | smart contracts | 2 |
| blockchain | ai | 2 |
| blockchain | big data | 2 |
| blockchain | cloud computing | 2 |
| blockchain | cloud storage | 2 |
| blockchain | consensus mechanism | 2 |
| blockchain | cybersecurity | 2 |
| blockchain | data security | 2 |
| blockchain | decentralization | 2 |
| blockchain | distributed ledger | 2 |
| blockchain | distributed ledger technology | 2 |
| blockchain | ethereum | 2 |
| blockchain | fog computing | 2 |
| blockchain | internet of medical things | 2 |
| blockchain | ipfs | 2 |
| blockchain | ml | 2 |
| blockchain | privacy protection | 2 |
| blockchain | security and privacy | 2 |
| blockchain | smart city | 2 |
| blockchain | smart contract | 2 |
| cloud computing | data security | 2 |
| edge computing | security | 2 |
| electronic medical records | iot | 2 |
| electronic medical records | security | 2 |
| iot | authentication | 2 |
| iot | distributed ledger technology | 2 |
| iot | internet of medical things | 2 |
| iot | interoperability | 2 |
| iot | smart city | 2 |
| iot | smart contracts | 2 |
| security | authentication | 2 |
| security | smart contracts | 2 |
| security | traceability | 2 |
References
- Akkaoui, R.; Hei, X.; Cheng, W. EdgeMediChain: A Hybrid Edge Blockchain-Based Framework for Health Data Exchange. IEEE Access 2020, 8, 113467–113486. [Google Scholar] [CrossRef]
- Alhajri, M.; Rudolph, C.; Shahraki, A.S. A Blockchain-Based Consent Mechanism for Access to Fitness Data in the Healthcare Context. IEEE Access 2022, 10, 22960–22979. [Google Scholar] [CrossRef]
- Deep, A.; Perrusquia, A.; Aljaburi, L.; Al-Rubaye, S.; Guo, W. A Novel Distributed Authentication of Blockchain Technology Integration in IoT Services. IEEE Access 2024, 12, 9550–9562. [Google Scholar] [CrossRef]
- Ezawa, Y.; Kakei, S.; Shiraishi, Y.; Mohri, M.; Morii, M. Blockchain-Based Cross-Domain Authorization System for User-Centric Resource Sharing. Blockchain Res. Appl. 2023, 4, 100126. [Google Scholar] [CrossRef]
- Alharbi, A. Applying Access Control Enabled Blockchain (ACE-BC) Framework to Manage Data Security in the CIS System. Sensors 2023, 23, 3020. [Google Scholar] [CrossRef]
- Alohali, M.A.; Aljebreen, M.; Al-Mutiri, F.; Othman, M.; Motwakel, A.; Alsaid, M.I.; Alneil, A.A.; Osman, A.E. Blockchain-Driven Image Encryption Process with Arithmetic Optimization Algorithm for Security in Emerging Virtual Environments. Sustainability 2023, 15, 5133. [Google Scholar] [CrossRef]
- Hao, K.; Xin, J.; Wang, Z.; Cao, K.; Wang, G. Blockchain-Based Outsourced Storage Schema in Untrusted Environment. IEEE Access 2019, 7, 122707–122721. [Google Scholar] [CrossRef]
- Bobde, Y.; Narayanan, G.; Jati, M.; Raj, R.S.P.; Cvitić, I.; Peraković, D. Enhancing Industrial IoT Network Security through Blockchain Integration. Electronics 2024, 13, 687. [Google Scholar] [CrossRef]
- Hanggoro, D.; Windiatmaja, J.H.; Muis, A.; Sari, R.F.; Pournaras, E. Energy-Aware Proof-of-Authority: Blockchain Consensus for Clustered Wireless Sensor Network. Blockchain Res. Appl. 2024, 5, 100211. [Google Scholar] [CrossRef]
- Kiania, K.; Jameii, S.M.; Rahmani, A.M. Blockchain-Based Privacy and Security Preserving in Electronic Health: A Systematic Review. Multimed. Tools Appl. 2023, 82, 28493–28519. [Google Scholar] [CrossRef]
- Chukwu, E.; Garg, L. A Systematic Review of Blockchain in Healthcare: Frameworks, Prototypes, and Implementations. IEEE Access 2020, 8, 21196–21214. [Google Scholar] [CrossRef]
- Popay, J.; Roberts, H.; Sowden, A.; Petticrew, M.; Arai, L.; Rodgers, M.; Britten, N.; Roen, K.; Duffy, S. Guidance on the Conduct of Narrative Synthesis in Systematic Reviews: A Product from the ESRC Methods Programme; Institute for Health Research, Lancaster University: Lancaster, UK, 2006. [Google Scholar] [CrossRef]
- El Bekkali, A.; Essaaidi, M.; Boulmalf, M. A Blockchain-Based Architecture and Framework for Cybersecure Smart Cities. IEEE Access 2023, 11, 76359–76370. [Google Scholar] [CrossRef]
- Bhattacharya, P.; Saraswat, D.; Dave, A.; Acharya, M.; Tanwar, S.; Sharma, G.; Davidson, I.E. Coalition of 6G and Blockchain in AR/VR Space: Challenges and Future Directions. IEEE Access 2021, 9, 168455–168484. [Google Scholar] [CrossRef]
- Sadri, H.; Yitmen, I.; Tagliabue, L.C.; Westphal, F.; Tezel, A.; Taheri, A.; Sibenik, G. Integration of Blockchain and Digital Twins in the Smart Built Environment Adopting Disruptive Technologies—A Systematic Review. Sustainability 2023, 15, 3713. [Google Scholar] [CrossRef]
- Alizadeh, M.; Andersson, K.; Schelén, O. DHT- and Blockchain-Based Smart Identification for Video Conferencing. Blockchain Res. Appl. 2022, 3, 100066. [Google Scholar] [CrossRef]
- Dieye, M.; Valiorgue, P.; Gelas, J.-P.; Diallo, E.-H.; Ghodous, P.; Biennier, F.; Peyrol, É. A Self-Sovereign Identity Based on Zero-Knowledge Proof and Blockchain. IEEE Access 2023, 11, 49445–49455. [Google Scholar] [CrossRef]
- Ghani, M.A.N.U.; She, K.; Rauf, M.A.; Khan, S.; Khan, J.A.; Aldakheel, E.A.; Khafaga, D.S. Enhancing Security and Privacy in Distributed Face Recognition Systems through Blockchain and GAN Technologies. Comput. Mater. Contin. 2024, 79, 2609–2623. [Google Scholar] [CrossRef]
- Cao, S.; Foth, M.; Powell, W.; Miller, T.; Li, M. A Blockchain-Based Multisignature Approach for Supply Chain Governance: A Use Case from the Australian Beef Industry. Blockchain Res. Appl. 2022, 3, 100091. [Google Scholar] [CrossRef]
- Cha, S.; Baek, S.; Kim, S. Blockchain-Based Sensitive Data Management by Using Key Escrow Encryption System from the Perspective of Supply Chain. IEEE Access 2020, 8, 154269–154280. [Google Scholar] [CrossRef]
- Faisal, M.N.; Bin Sabir, L.; Al Naimi, M.S.; Sharif, K.J.; Uddin, S.M.F. Critical Role of Coopetition Among Supply Chains for Blockchain Adoption: Review of Reviews and Mixed-Method Analysis. Glob. J. Flex. Syst. Manag. 2024, 25, 117–136. [Google Scholar] [CrossRef]
- Gottlieb, M.; Deutsch, C.; Hoops, F.; Pongratz, H.; Krcmar, H. Expedition to the Blockchain Application Potential for Higher Education Institutions. Blockchain Res. Appl. 2024, 5, 100203. [Google Scholar] [CrossRef]
- Han, S.; Park, S. A Gap Between Blockchain and General Data Protection Regulation: A Systematic Review. IEEE Access 2022, 10, 103888–103905. [Google Scholar] [CrossRef]
- Gamboa-Cruzado, J.; Mendoza-Chate, L.A.; Ventocilla-Sanchez, A.; López-Goycochea, J.; Ramirez Villacorta, J. UYAKUY-Blockchain-Based Software Application for Certificate Issuance: A Case Study in the IEEE Peru Section. J. Theor. Appl. Inf. Technol. 2023, 101, 20. [Google Scholar]
- Haugum, T.; Hoff, B.; Alsadi, M.; Li, J. Security and privacy challenges in blockchain interoperability—A multivocal literature review. In Proceedings of the 26th International Conference on Evaluation and Assessment in Software Engineering, Gothenburg, Sweden, 13–15 June 2022. [Google Scholar] [CrossRef]
- Nasir, A.; Shaukat, K.; Khan, K.I.; Hameed, I.A.; Alam, T.M.; Luo, S. What is Core and What Future Holds for Blockchain Technologies and Cryptocurrencies: A Bibliometric Analysis. IEEE Access 2021, 9, 989–1004. [Google Scholar] [CrossRef]
- Xu, M.; Chen, X.; Kou, G. A Systematic Review of Blockchain. Financ. Innov. 2019, 5, 27. [Google Scholar] [CrossRef]
- PRISMA: Preferred Reporting Items for Systematic Reviews and Meta-Analyses. Available online: https://www.prisma-statement.org/ (accessed on 18 July 2025).
- Awadallah, R.; Samsudin, A.; Sen Teh, J.; Almazrooie, M. An Integrated Architecture for Maintaining Security in Cloud Computing Based on Blockchain. IEEE Access 2021, 9, 69513–69526. [Google Scholar] [CrossRef]
- Cao, P.; Duan, G.; Tu, J.; Jiang, Q.; Yang, X.; Li, C. Blockchain-Based Process Quality Data Sharing Platform for Aviation Suppliers. IEEE Access 2023, 11, 19007–19023. [Google Scholar] [CrossRef]
- Ferro, E.; Saltarella, M.; Rotondi, D.; Giovanelli, M.; Corrias, G.; Moncada, R.; Cavallaro, A.; Favenza, A. Digital Assets Rights Management through Smart Legal Contracts and Smart Contracts. Blockchain Res. Appl. 2023, 4, 100142. [Google Scholar] [CrossRef]
- Hu, W.; Yao, W.; Hu, Y.; Li, H. Collaborative Optimization of Distributed Scheduling Based on Blockchain Consensus Mechanism Considering Battery-Swap Stations of Electric Vehicles. IEEE Access 2019, 7, 137959–137967. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.M.S.; Yoon, B. Blockchain Security Attacks, Challenges, and Solutions for the Future Distributed IoT Network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- ISO/IEC 27001; Information Security, Cybersecurity and Privacy Protection—Information Security management Systems—Requirements. ISO: Geneva, Switzerland, 2022.
- Junaid, L.; Bilal, K.; Shuja, J.; Balogun, A.O.; Rodrigues, J.J.P.C. Blockchain-Enabled Framework for Transparent Land Lease and Mortgage Management. IEEE Access 2024, 12, 54005–54018. [Google Scholar] [CrossRef]
- Paik, H.Y.; Xu, X.; Bandara, H.M.N.D.; Lee, S.U.; Lo, S.K. Analysis of Data Management in Blockchain-Based Systems: From Architecture to Governance. IEEE Access 2019, 7, 186091–186107. [Google Scholar] [CrossRef]
- Mothukuri, V.; Cheerla, S.S.; Parizi, R.M.; Zhang, Q.; Choo, K.K.R. BlockHDFS: Blockchain-Integrated Hadoop Distributed File System for Secure Provenance Traceability. Blockchain Res. Appl. 2021, 2, 100032. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic Literature Reviews in Software Engineering-A Systematic Literature Review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Hsiao, S.J.; Sung, W.T. Employing Blockchain Technology to Strengthen Security of Wireless Sensor Networks. IEEE Access 2021, 9, 72326–72341. [Google Scholar] [CrossRef]
- Itoo, S.; Khan, A.A.; Kumar, V.; Alkhayyat, A.; Ahmad, M.; Srinivas, J. CKMIB: Construction of Key Agreement Protocol for Cloud Medical Infrastructure Using Blockchain. IEEE Access 2022, 10, 67787–67801. [Google Scholar] [CrossRef]
- Miao, Y.; Huang, Q.; Xiao, M.; Li, H. Decentralized and Privacy-Preserving Public Auditing for Cloud Storage Based on Blockchain. IEEE Access 2020, 8, 139813–139826. [Google Scholar] [CrossRef]
- Na, D.; Park, S. Blockchain-Based Dashcam Video Management Method for Data Sharing and Integrity in V2V Network. IEEE Access 2022, 10, 3307–3319. [Google Scholar] [CrossRef]
- Sasikumar, A.; Ravi, L.; Devarajan, M.; Vairavasundaram, S.; Selvalakshmi, A.; Kotecha, K.; Abraham, A. A Decentralized Resource Allocation in Edge Computing for Secure IoT Environments. IEEE Access 2023, 11, 117177–117189. [Google Scholar] [CrossRef]
- Sasikumar, A.; Ravi, L.; Kotecha, K.; Abraham, A.; Devarajan, M.; Vairavasundaram, S. A Secure Big Data Storage Framework Based on Blockchain Consensus Mechanism with Flexible Finality. IEEE Access 2023, 11, 56712–56725. [Google Scholar] [CrossRef]
- Shakor, M.Y.; Khaleel, M.I.; Safran, M.; Alfarhood, S.; Zhu, M. Dynamic AES Encryption and Blockchain Key Management: A Novel Solution for Cloud Data Security. IEEE Access 2024, 12, 26334–26343. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, A.; Zhang, P.; Wang, H. Cloud-Assisted EHR Sharing with Security and Privacy Preservation via Consortium Blockchain. IEEE Access 2019, 7, 136704–136719. [Google Scholar] [CrossRef]
- Zaidi, T.; Usman, M.; Aftab, M.U.; Aljuaid, H.; Ghadi, Y.Y. Fabrication of Flexible Role-Based Access Control Based on Blockchain for Internet of Things Use Cases. IEEE Access 2023, 11, 106315–106333. [Google Scholar] [CrossRef]
- Iqbal, N.; Jamil, F.; Ahmad, S.; Kim, D. A Novel Blockchain-Based Integrity and Reliable Veterinary Clinic Information Management System Using Predictive Analytics for Provisioning of Quality Health Services. IEEE Access 2021, 9, 8069–8098. [Google Scholar] [CrossRef]
- Umran, S.M.; Lu, S.; Abduljabbar, Z.A.; Tang, X. A Blockchain-Based Architecture for Securing Industrial IoTs Data in Electric Smart Grid. Comput. Mater. Contin. 2023, 74, 5389–5416. [Google Scholar] [CrossRef]
- Mantey, E.A.; Zhou, C.; Anajemba, J.H.; Hamid, Y.; Arthur, J.K. Blockchain-Enabled Technique for Privacy-Preserved Medical Recommender System. IEEE Access 2023, 11, 40944–40953. [Google Scholar] [CrossRef]
- Mohammad, F.; Al-Ahmadi, S.; Al-Muhtadi, J. Block-Deep: A Hybrid Secure Data Storage and Diagnosis Model for Bone Fracture Identification of Athlete from X-Ray and MRI Images. IEEE Access 2023, 11, 142360–142370. [Google Scholar] [CrossRef]
- Rathore, S.; Park, J.H.; Chang, H. Deep Learning and Blockchain-Empowered Security Framework for Intelligent 5G-Enabled IoT. IEEE Access 2021, 9, 90075–90083. [Google Scholar] [CrossRef]
- Rawlins, C.C.; Jagannathan, S. An Intelligent Distributed Ledger Construction Algorithm for IoT. IEEE Access 2022, 10, 10838–10851. [Google Scholar] [CrossRef]
- Wu, F.; Zhou, B.; Jiang, J.; Lei, T.; Song, J. Blockchain Privacy Protection Based on Post Quantum Threshold Algorithm. Comput. Mater. Contin. 2023, 76, 957–973. [Google Scholar] [CrossRef]
- Jin, L.; Liu, L.; Song, J. Delegated Computation Architecture and Implementation for Numerical Simulation of Electromagnetic Comprehensive Performance Under the Framework of Blockchain. IEEE Access 2023, 11, 61786–61799. [Google Scholar] [CrossRef]
- Kamal, R.; Hemdan, E.E.D.; El-Fishway, N. Care4U: Integrated Healthcare Systems Based on Blockchain. Blockchain Res. Appl. 2023, 4, 100151. [Google Scholar] [CrossRef]
- Khan, A.U.R.; Ahmad, R.W. A Blockchain-Based IoT-Enabled E-Waste Tracking and Tracing System for Smart Cities. IEEE Access 2022, 10, 86256–86269. [Google Scholar] [CrossRef]
- Li, H.; Pei, L.; Liao, D.; Chen, S.; Zhang, M.; Xu, D. FADB: A Fine-Grained Access Control Scheme for VANET Data Based on Blockchain. IEEE Access 2020, 8, 85190–85203. [Google Scholar] [CrossRef]
- Li, L.; Jin, D.; Zhang, T.; Li, N. A Secure, Reliable and Low-Cost Distributed Storage Scheme Based on Blockchain and IPFS for Firefighting IoT Data. IEEE Access 2023, 11, 97318–97330. [Google Scholar] [CrossRef]
- Li, X.; Huang, X.; Li, C.; Yu, R.; Shu, L. EdgeCare: Leveraging Edge Computing for Collaborative Data Management in Mobile Healthcare Systems. IEEE Access 2019, 7, 22011–22025. [Google Scholar] [CrossRef]
- Liu, Y.; Shan, G.; Liu, Y.; Alghamdi, A.; Alam, I.; Biswas, S. Blockchain Bridges Critical National Infrastructures: E-Healthcare Data Migration Perspective. IEEE Access 2022, 10, 28509–28519. [Google Scholar] [CrossRef]
- Luo, Z.; Zhang, H. Blockchain-Based Engine Data Trustworthy Swarm Learning Management Method. Blockchain Res. Appl. 2024, 5, 100185. [Google Scholar] [CrossRef]
- Padma, A.; Ramaiah, M. Blockchain-Based an Efficient and Secure Privacy Preserved Framework for Smart Cities. IEEE Access 2024, 12, 21985–22002. [Google Scholar] [CrossRef]
- Regueiro, C.; Gómez-Goiri, A.; Pedrosa, N.; Semertzidis, C.; Iturbe, E.; Mansell, J. Blockchain-Based Refurbishment Certification System for Enhancing the Circular Economy. Blockchain Res. Appl. 2024, 5, 100172. [Google Scholar] [CrossRef]
- Shynu, P.G.; Menon, V.G.; Kumar, R.L.; Kadry, S.; Nam, Y. Blockchain-Based Secure Healthcare Application for Diabetic-Cardio Disease Prediction in Fog Computing. IEEE Access 2021, 9, 45706–45720. [Google Scholar] [CrossRef]
- Stockburger, L.; Kokosioulis, G.; Mukkamala, A.; Mukkamala, R.R.; Avital, M. Blockchain-Enabled Decentralized Identity Management: The Case of Self-Sovereign Identity in Public Transportation. Blockchain Res. Appl. 2021, 2, 100014. [Google Scholar] [CrossRef]
- Tran, T.H.; Pham, H.L.; Nakashima, Y. A High-Performance Multimem SHA-256 Accelerator for Society 5.0. IEEE Access 2021, 9, 39182–39192. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Data Trading Certification Based on Consortium Blockchain and Smart Contracts. IEEE Access 2021, 9, 3482–3496. [Google Scholar] [CrossRef]
- Yang, R.; Dong, G.; Xu, Z.; Ning, J.; Du, J. A Privacy-Preserving Data Aggregation System Based on Blockchain in VANET. Blockchain Res. Appl. 2024, 5, 100210. [Google Scholar] [CrossRef]
- Yang, Y.; Idris, N.B.; Yu, D.; Liu, C.; Wu, H. Decentralized Deepfake Task Management Algorithm Based on Blockchain and Edge Computing. IEEE Access 2024, 12, 86456–86469. [Google Scholar] [CrossRef]
- Yele, S.; Litoriya, R. Blockchain-Based Secure Dining: Enhancing Safety, Transparency, and Traceability in Food Consumption Environment. Blockchain Res. Appl. 2024, 5, 100187. [Google Scholar] [CrossRef]
- Yongjoh, S.; So-In, C.; Kompunt, P.; Muneesawang, P.; Morien, R.I. Development of an Internet-of-Healthcare System Using Blockchain. IEEE Access 2021, 9, 113017–113031. [Google Scholar] [CrossRef]
- Zang, H.; Kim, H.; Kim, J. Blockchain-Based Decentralized Storage Design for Data Confidence Over Cloud-Native Edge Infrastructure. IEEE Access 2024, 12, 50083–50099. [Google Scholar] [CrossRef]
- Zhang, S. Data Sharing Network Model and Mechanism of Power Internet of Things in Virtualized Environment. IEEE Access 2022, 10, 4252–4260. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad-Hoc Network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Zhang, Y.; Geng, H.; Su, L.; Lu, L. A Blockchain-Based Efficient Data Integrity Verification Scheme in Multi-Cloud Storage. IEEE Access 2022, 10, 105920–105929. [Google Scholar] [CrossRef]
- Zou, Q.; Yu, W.; Bao, Z. A Blockchain Solution for Remote Sensing Data Management Model. Appl. Sci. 2023, 13, 9609. [Google Scholar] [CrossRef]
- Al-Muhtadi, J.; Hasan, A.; Saleem, K.; Gawanmeh, A.; Rodrigues, J.J.P.C. Blockchain for Global Vaccinations Efforts: State of the Art, Challenges, and Future Directions. Int. J. Electr. Comput. Eng. 2023, 13, 5576–5587. [Google Scholar] [CrossRef]
- Murthy, C.H.V.N.U.B.; Shri, M.L.; Kadry, S.; Lim, S. Blockchain-Based Cloud Computing: Architecture and Research Challenges. IEEE Access 2020, 8, 205190–205205. [Google Scholar] [CrossRef]
- Ramasamy, L.K.; Khan, F.K.P.; Imoize, A.L.; Ogbebor, J.O.; Kadry, S.; Rho, S. Blockchain-Based Wireless Sensor Networks for Malicious Node Detection: A Survey. IEEE Access 2021, 9, 128765–128785. [Google Scholar] [CrossRef]
- Indumathi, J.; Shankar, A.; Ghalib, M.R.; Gitanjali, J.; Hua, Q.; Wen, Z.; Qi, X. Block Chain Based Internet of Medical Things for Uninterrupted, Ubiquitous, User-Friendly, Unflappable, Unblemished, Unlimited Health Care Services (BC IoMT U6HCS). IEEE Access 2020, 8, 216856–216872. [Google Scholar] [CrossRef]
- Nicolas, K.; Wang, Y.; Giakos, G.C.; Wei, B.; Shen, H. Blockchain System Defensive Overview for Double-Spend and Selfish Mining Attacks: A Systematic Approach. IEEE Access 2021, 9, 3838–3857. [Google Scholar] [CrossRef]
- Truong, V.T.; Le, L.; Niyato, D. Blockchain Meets Metaverse and Digital Asset Management: A Comprehensive Survey. IEEE Access 2023, 11, 26258–26288. [Google Scholar] [CrossRef]
- AL-Ashmori, A.; Basri, S.B.; Dominic, P.D.D.; Capretz, L.F.; Muneer, A.; Balogun, A.O.; Gilal, A.R.; Ali, R.F. Classifications of Sustainable Factors in Blockchain Adoption: A Literature Review and Bibliometric Analysis. Sustainability 2022, 14, 5176. [Google Scholar] [CrossRef]
- Lizama, M.G.; Huesa, J.; Claudio, B.M. Use of Blockchain Technology for the Exchange and Secure Transmission of Medical Images in the Cloud: Systematic Review with Bibliometric Analysis. ASEAN J. Sci. Eng. 2024, 4, 71–92. [Google Scholar] [CrossRef]
- Yang, J.; Ma, C.; Li, D.; Liu, J. Mapping the Knowledge on Blockchain Technology in the Field of Business and Management: A Bibliometric Analysis. IEEE Access 2022, 10, 60585–60596. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.