A Hybrid Zero Trust Deployment Model for Securing O-RAN Architecture in 6G Networks
Abstract
1. Introduction
Motivation & Contributions
- Enclave-based segmentation to enforce macro-level isolation between logically grouped O-RAN functions,
- Device application sandboxing to isolate xApps/rApps, thereby limiting intra-enclave lateral movement at the micro-level,
- Distributed PEPs and a centralised PDP, aligned with NIST ZTA tenets and O-RAN Alliance specifications,
- A Kubernetes and Istio-based Proof of Concept (PoC) implementation, leveraging the NIST Policy Machine (PM) to demonstrate technical feasibility,
- A comprehensive mapping of ZT deployment approaches (i.e., agent/gateway-based, enclave, resource portal, and sandboxing) to their applicability in O-RAN contexts, and
- A performance analysis based on the PoC implementation that considers latency, CPU/memory impact, scalability, and trade-offs of the proposed hybrid ZT model.
2. Related Works
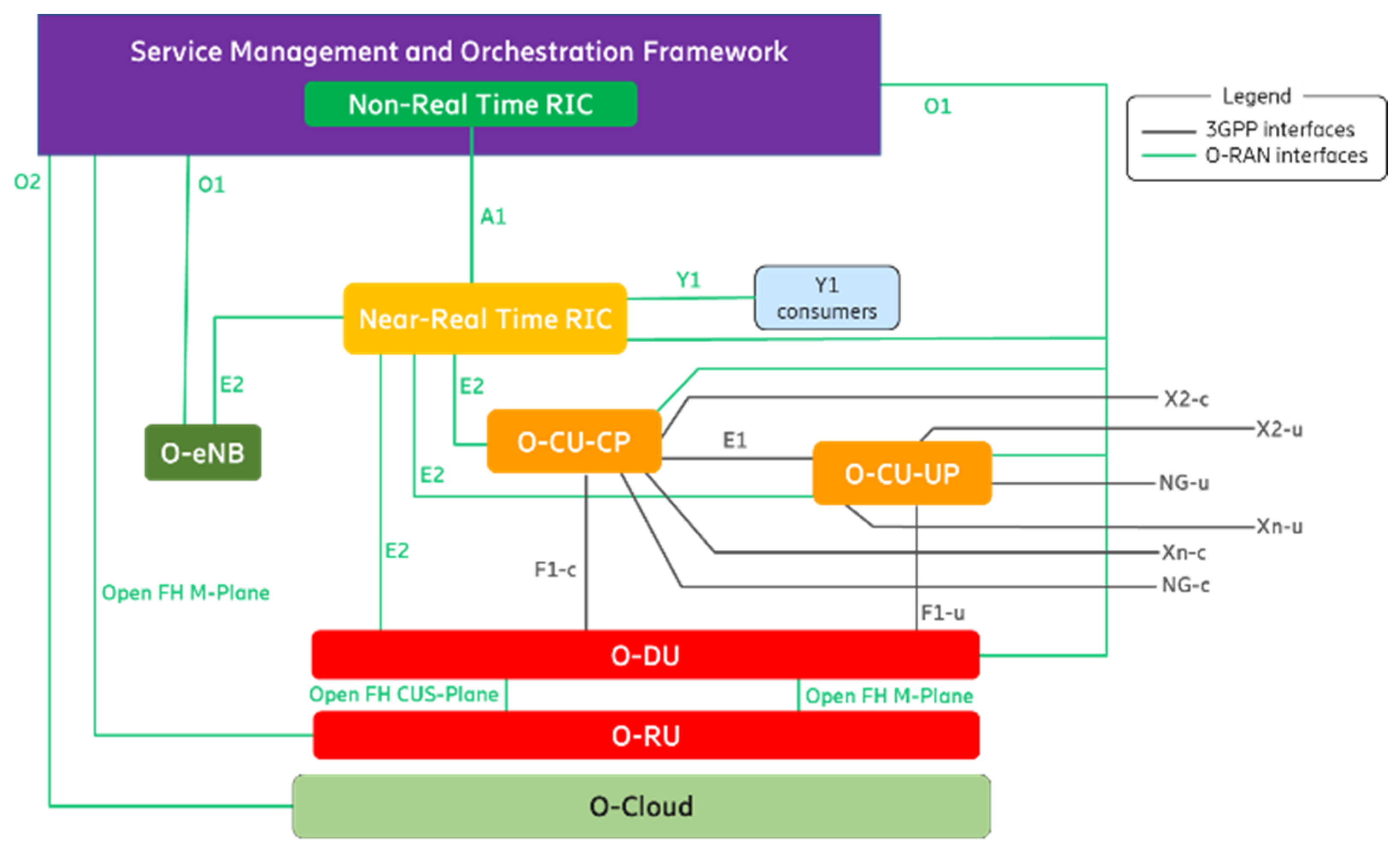
2.1. O-RAN Architecture
2.2. O-RAN Security Challenges & Standards
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise/operator resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise/operator monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorisation are dynamic and strictly enforced before access is allowed.
- The enterprise/operator collects information about the current state of assets, network infrastructure and communications and uses it to improve its security posture.
2.3. Zero Trust in 6G & O-RAN
2.4. Comparative Analysis of O-RAN Security Methodologies
3. The Hybrid Zero Trust Deployment Model for O-RAN Architecture
3.1. ZT Approaches & Potential Implementation in O-RAN
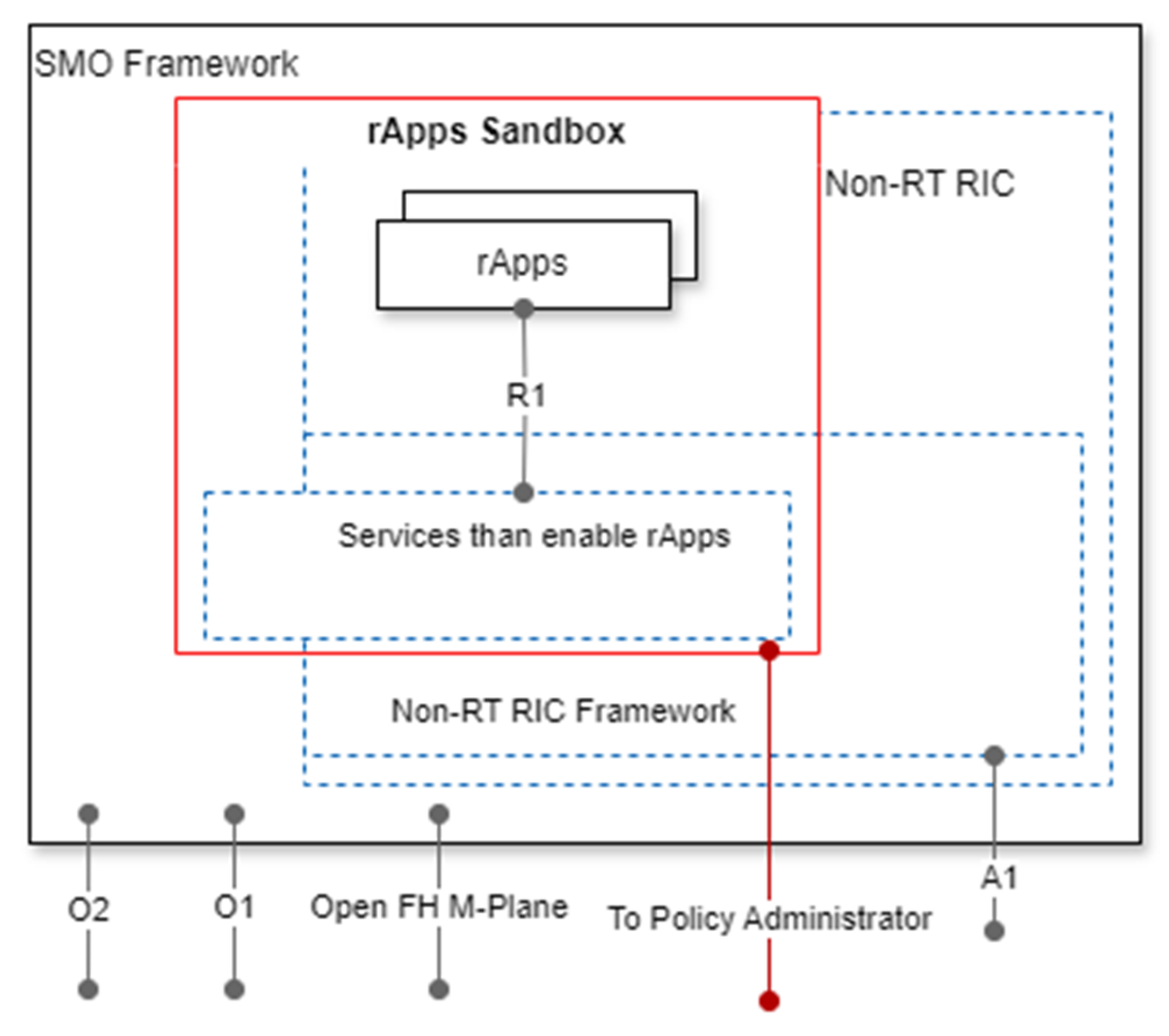
3.1.1. Enhanced Identity Governance-Driven Approach
3.1.2. Logical Micro-Segmentation
3.1.3. Network-Based Segmentation
3.2. ZT Deployment Variations for O-RAN
3.2.1. Device Agent/Gateway-Based Deployment
3.2.2. Enclave-Based Deployment
3.2.3. Resource Portal-Based Deployment
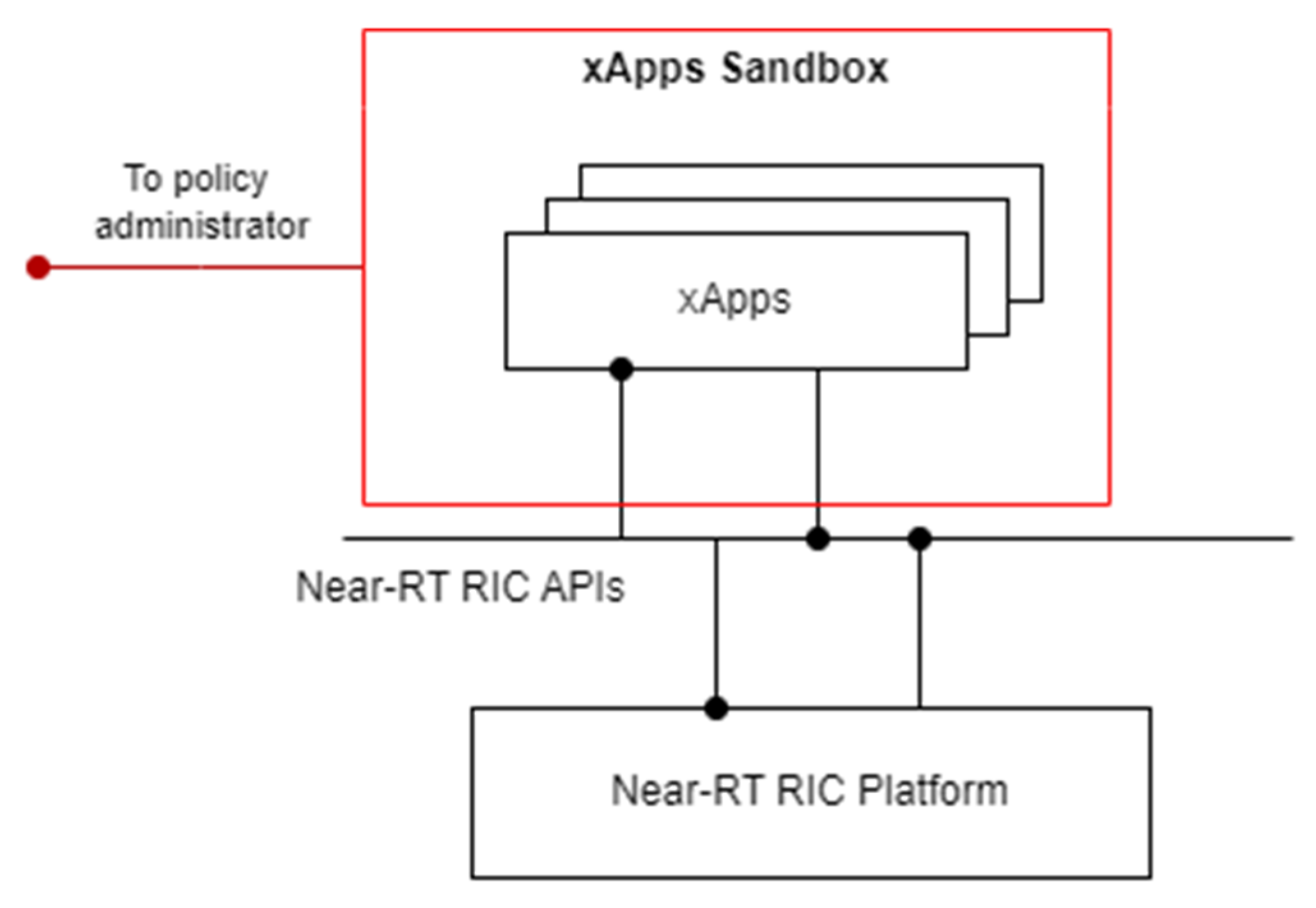
3.2.4. Device Application Sandboxing
3.3. The Hybrid ZT Deployment for O-RAN
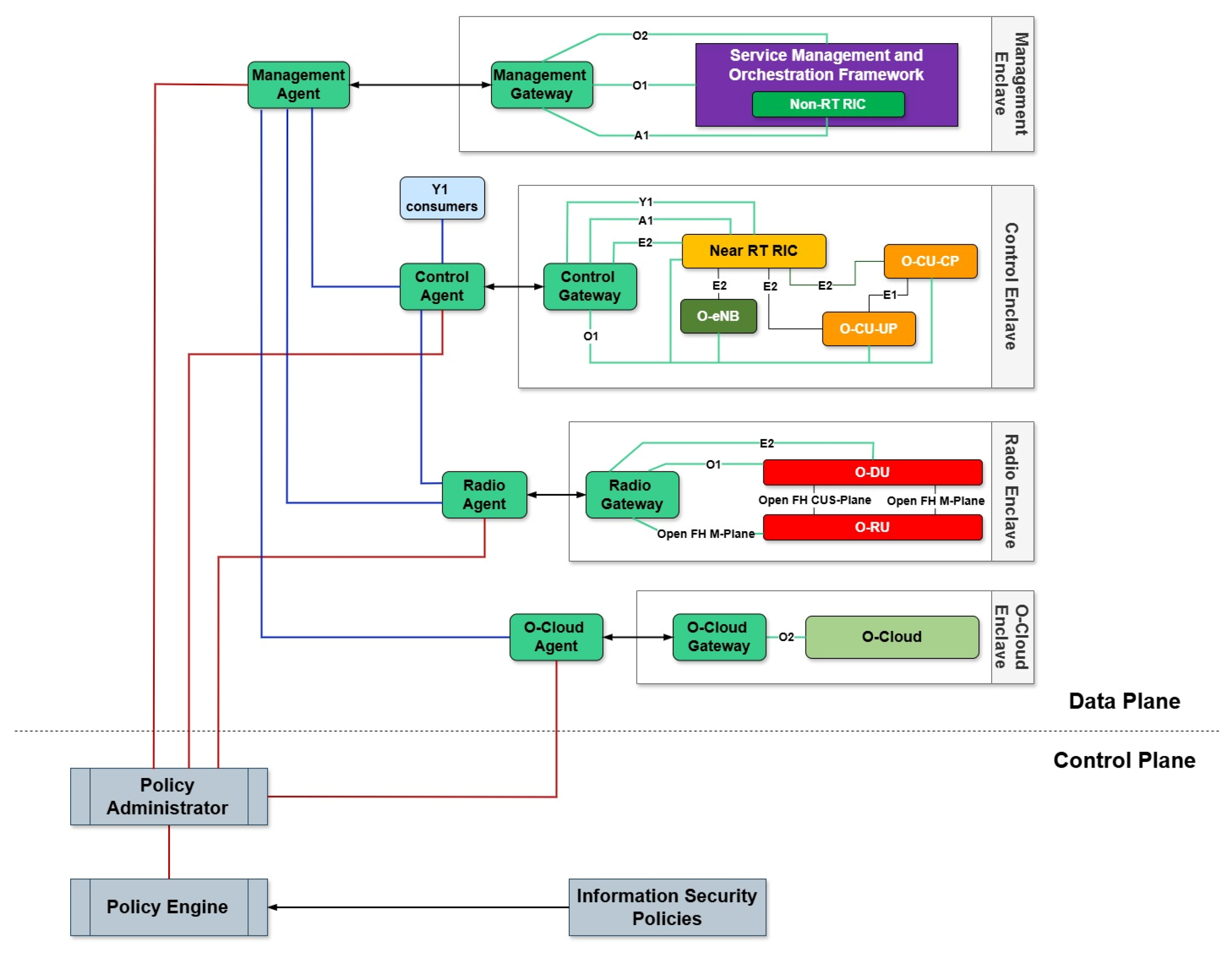
- Enclaves: These are collections of resources, comprising elements of the O-RAN architecture that share similar functionalities and support comparable control loops. Enclaves provide isolation and resource management for these services.
- Agents: These software agents facilitate connections and communication between different enclaves. An agent is responsible for directing a portion (or all) of the traffic to the policy administrator for evaluation.
- Gateways: These act as intermediaries for resources in their respecting enclaves, ensuring that ingress and egress traffic (i.e., communications) between resources across different enclaves occur exclusively through the gateways. The gateway communicates with the PA, via its dedicated agent, enforcing approved communication paths as configured by the PA.
3.3.1. Management Enclave
3.3.2. Control Enclave
3.3.3. Radio Enclave
3.3.4. O-Cloud Enclave
4. Implementation Strategy of the Hybrid ZT Deployment Model for O-RAN
4.1. Multi-Layered Security Across Control & Data Planes
4.2. Agent/Gateway Security Controls
4.3. Systematic High-Level Implementation Plan for ZT Deployment in O-RAN
- Assets. These include O-RUs, O-DUs, O-CUs, Near-RT RIC, Non-RT RIC, SMO framework, and O-Cloud infrastructure.
- Interfaces. These include Open Fronthaul between O-RUs and O-DUs, E2 interface between Near-RT RIC and DUs/CUs, A1 interface between Non-RT RIC and Near-RT RIC, O1 interface between SMO and O-RAN nodes, and F1 interface between DUs and CUs.
- Software Components. These include xApps/rApps running on RICs for advanced control and optimisation, VNFs, and AI/ML algorithms for network management.
- Data Flows. This includes:
- Control data flows between non-RT RIC and near-RT RIC via A1 interface for policy and control information, and between near-RT RIC and DUs/CUs via E2 interface for real-time control and optimisation.
- User data flows from end devices to O-RUs, then to O-DUs, and finally to O-CUs before reaching the core network.
- Telemetry data flows from O-RUs/O-DUs/O-CUs to SMO for monitoring and orchestration via O1 interface.
- AI/ML data flows where data collected from network operations are fed into AI/ML models for training and inference.
- Human Subjects. This includes:
- Network Operators. Manage, monitor and maintain the O-RAN infrastructure by ensuring efficient operation, performing troubleshooting, applying configurations, and monitoring performance metrics.
- Service Providers. Offer telecommunication services and applications that utilise the O-RAN network. Their responsibilities include ensuring service quality, managing service delivery and addressing customer requirements.
- Vendors. Supply hardware and software components for the O-RAN ecosystem. They develop, deliver, and support network equipment and software solutions.
- Developers. Develop, maintain, and update xApps/rApps, and other O-RAN software components. This includes application development, testing, and ensuring compatibility with O-RAN specifications.
- Regulatory Bodies. Ensure compliance with telecommunication standards and regulations. Regulatory bodies also have responsibility to oversee network operations, ensure adherence to regulatory requirements, and protect consumer interests.
- End Users. Consumers and businesses use services provided over O-RAN networks. Use network services, report issues, and provide feedback on service quality.
- Non-person Entities. This includes:
- Service Accounts. These are automated accounts for managing and interacting with O-RAN resources. They perform routine tasks such as data collection, software updates and resource provisioning.
- AI/ML models deployed within xApps/rApps for network optimisation. They analyse data, predict network conditions and suggest or apply configurations for optimisation.
- VNFs and PNFs. These perform specific tasks in the network. Tasks related to data processing signal transmission and network management.
- Management and orchestration systems. Systems within the SMO that manage network resources and orchestrate services. They coordinate the deployment and operation of network components, ensure resource allocation, and maintain service quality.
- Monitoring and Analytics tools. These collect, process, and analyse network data. Their responsibilities include providing insights into network performance, detect anomalies and support decision making process.
- Security systems that enforce security policies and detect threats. They monitor network activities, identify security breaches and apply countermeasures when needed to protect the O-RAN network.
- Preparation. This phase has been outlined earlier where assets are identified. It also includes defining the scope and objectives of ZT deployment in O-RAN, assessing the current security posture, and identifying gaps.
- Design. Develop a detailed ZT implementation plan, including policies, procedures, and tools required. It also includes designing the architecture for integrating IAM, PEPs, segmentation, monitoring, and encryption within O-RAN architecture.
- Deployment. This phase includes deploying IAM solutions, PEPs, monitoring tools, and encryption mechanisms across O-RAN components and interfaces. Besides that, the configuration of access policies, segmentation rules, and encryption protocols.
- Testing. Conduct thorough testing to ensure all ZT principles are effectively implemented and integrated. In addition, penetration testing and vulnerability assessments to identify and address any security weaknesses.
- Monitoring & Maintenance. Continuously monitor the network for security threats and policy violations. Moreover, regularly update security policies, tools, and configurations based on evolving threats and network changes.
- Review & Improvement. Periodically review the effectiveness of the ZT hybrid model implementation and make necessary improvements.
4.4. Policy Machine-Based Implementation—Proof of Concept
- Pod. Following the terms used in Kubernetes, a pod acts as a logical boundary (i.e., enclave) encapsulating one or more related services. Pods provide isolation and resource management for these services. Each pod can contain multiple containers (i.e., services) that work together. These services are protected from external interference through policies and proxies in front or within the pod.
- Proxy. In this case, a proxy could serve as an agent, gateway and policy enforcer. The benefits of combining these components into a proxy include easier management, dynamic policy implementation, and reducing the attack surface. Each proxy serves as an intermediary between services within the enclaves and the outside world, or between internal services, enforcing policies. Proxies receive policy details from the control plane (i.e., the PA) and are responsible for applying them at the pod level, ensuring security and access control. The proxy functionality can be further split into ingress and egress proxies. An ingress proxy handles all incoming traffic to the pod, applying policies to ensure only authorised requests are allowed into the enclave. On the other hand, egress proxy handles traffic exiting the pod. It ensures that any data leaving the pod (i.e., enclave) complies with outbound security policies, preventing unauthorised data transmission or data leaks.
| Policy 1. AuthorisationPolicy: allow-ru-to-vdu |
| apiVersion: security.istio.io/v1beta1 kind: AuthorisationPolicy metadata: name: allow-ru-to-vdu namespace: ran spec: selector: matchLabels: app: vdu # apply to the vDU workload only action: ALLOW rules: - from: - source: principals: - spiffe://cluster.local/ns/radio/sa/ru-service-account |
| Policy 2. AuthorisationPolicy: deny-bad-cidr |
| # 1) Expose the ingress gateway apiVersion: networking.istio.io/v1beta1 kind: Gateway metadata: name: public-gw namespace: istio-system spec: selector: istio: ingressgateway servers: - port: number: 80 name: http protocol: HTTP hosts: - “*” --- # 2) Route all “/” traffic to core-nework apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: route-to-core namespace: istio-system spec: hosts: - “*” gateways: - public-gw http: - match: - uri: prefix: / route: - destination: host: core-nework.core.svc.cluster.local port: number: 80 --- # 3) Block traffic from a bad CIDR apiVersion: security.istio.io/v1beta1 kind: AuthorisationPolicy metadata: name: deny-bad-cidr namespace: istio-system spec: selector: matchLabels: istio: ingressgateway action: DENY rules: - from: - source: ipBlocks: - 192.0.2.0/24 # replace with the CIDR to block |
5. Performance & Trade-Off Analysis of the Hybrid ZT Deployment Model for O-RAN
5.1. Baseline Performance from Published ZT Approaches
5.1.1. Latency
5.1.2. CPU/Memory Usage
5.2. Trade-Offs of Our Hybrid ZT Model
5.2.1. Latency Overhead vs. Granular Isolation
5.2.2. CPU/Memory Overhead vs. Scalable Policy Enforcement
5.2.3. Operational Complexity vs. End-to-End Visibility
5.2.4. Single PDP vs. Policy Scalability
5.2.5. Power & Bandwidth Consideration
5.3. Adapting Security Policies Under Non-Ideal Channel Conditions
5.4. Robustness in Extreme Network Conditions
- High Mobility: simulate UE moving at speeds up to 120 km/h in an urban environment, causing rapid channel variations and beam misalignment. We will measure policy decision latency and impact on PEP session establishment success rate.
- Strong Interference: introduce controlled interference sources (e.g., at 2.4/5 GHz bands) to SINR levels from 0 to 10 dB. We will measure channel estimation error impact on policy update delays and security policy violation rates (e.g., expired tokens due to delayed PDP responses). Channel estimation errors will be mitigated by integrating robust algorithms such as MIMO-FBMC sparse channel estimation [51] and the training channel-based method for mmWave systems [52].
6. Conclusions & Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Larsson, D.C.; Grövlen, A.; Parkvall, S.; Liberg, O. 6G Standardization—An Overview of Timeline and High-Level Technology Principles. 22 March 2024. Available online: https://www.ericsson.com/en/blog/2024/3/6g-standardization-timeline-and-technology-principles (accessed on 1 September 2024).
- O-RAN Alliance. O-RAN Specifications. Available online: https://www.o-ran.org/specifications (accessed on 10 September 2024).
- 6G Smart Networks and Services Industry Association (6G-IA). Open RAN and 6G Future Networks Development. 6G SNS IA. 2024. Available online: https://6g-ia.eu/wp-content/uploads/2024/05/6g-ia-open-sns_open-networks-status-and-future-development_ran-final.pdf (accessed on 5 August 2024).
- O-RAN Next Generation Research Group (nGRG). O-RAN Towards 6G Report ID: RR-2023-01. O-RAN Alliance. 2023. Available online: https://mediastorage.o-ran.org/ngrg-rr/nGRG-RR-2023-01-O-RAN-Towards-6G-v1_3.pdf (accessed on 22 September 2024).
- O-RAN Next Generation Research Group (nGRG). Architecture Principles for a Cloud-Friendly Future 6G RAN Architecture Report ID: RR-2024-01. ORAN Alliance, 2024. Available online: https://mediastorage.o-ran.org/ngrg-rr/nGRG-RR-2024-01-O-RAN%20Cloud%20Friendly%20Future%206G%20RAN-v1.2.1.pdf (accessed on 11 August 2024).
- Alevizos, L.; Ta, V.; Eiza, M.H. Augmenting Zero Trust Architecture to Endpoints Using Blockchain: A State-Of-The-Art Review. Secur. Priv. 2022, 5, e191. [Google Scholar] [CrossRef]
- US Government. National Cybersecurity Strategy; The White House: Washington, DC, USA, 2023. [Google Scholar]
- National Cyber Security Centre (NCSC). Zero Trust Architecture Design Principles; NCSC: London, UK, 2021. [Google Scholar]
- RAN Alliance. Zero Trust Architecture for Secure O-RAN v1.0. O-RAN Alliance, May 2024. Available online: https://mediastorage.o-ran.org/white-papers/O-RAN.WG11.ZTA%20for%20Secure%20O-RAN%20White%20Paper-2024-05.pdf (accessed on 21 July 2024).
- National Institute of Standards and Technology (NIST). Advanced Security Architectures for Next Generation Wireless. 15 April 2024. Available online: https://www.nist.gov/programs-projects/advanced-security-architectures-next-generation-wireless (accessed on 13 September 2024).
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; NIST Special Publication 800-207; NIST: Gaithersburg, MD, USA, 2020. Available online: https://csrc.nist.gov/pubs/sp/800/207/final (accessed on 15 September 2024).
- Cybersecurity & Infrastructure Security Agency (CISA), Enduring Security Framework (ESF), Security Guidance for 5G Cloud Infrastructures, Volumes 1–4. US DHS CISA, October-November 2021. Available online: https://www.cisa.gov/resources-tools/groups/enduring-security-framework-esf (accessed on 11 August 2025).
- US DHS CISA. Zero Trust Maturity Model (ZTMM), Version 2.0. CISA, April 2023. Available online: https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf (accessed on 26 May 2024).
- O-RAN Alliance. O-RAN Architecture Description v14.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=862 (accessed on 11 August 2025).
- Polese, M.; Bonati, L.; D’Oro, S.; Basagni, S.; Melodia, T. Understanding O-RAN: Architecture, Interfaces, Algorithms, Security, and Research Challenges. IEEE Commun. Surv. Tutor. 2023, 25, 1376–1411. [Google Scholar] [CrossRef]
- O-RAN Alliance. The O-RAN ALLIANCE Security Working Group Continues to Advance O-RAN Security. 9 February 2024. Available online: https://www.o-ran.org/blog/the-o-ran-alliance-security-working-group-continues-to-advance-o-ran-security (accessed on 27 September 2024).
- Liyanage, M.; Braeken, A.; Shahabuddin, S.; Ranaweera, P. Open RAN security: Challenges and opportunities. J. Netw. Comput. Appl. 2023, 214. [Google Scholar] [CrossRef]
- Groen, J.; D’Oro, S.; Demir, U.; Bonati, L.; Villa, D.; Polese, M. Securing O-RAN Open Interfaces. IEEE Trans. Mob. Comput. 2024, 23, 11265–11277. [Google Scholar] [CrossRef]
- O-RAN Alliance. O-RAN Security Threat Modelling and Risk Assessment 6.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=918 (accessed on 11 August 2025).
- O-RAN Alliance. O-RAN Security Requirements and Controls Specification 12.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=914 (accessed on 11 August 2025).
- O-RAN Alliance. O-RAN Security Protocols Specifications 12.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=917 (accessed on 11 August 2025).
- O-RAN Alliance. O-RAN Security Test Specifications 10.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=920 (accessed on 11 August 2025).
- O-RAN Alliance. O-RAN Study on Security for Service Management and Orchestration (SMO) 6.0. O-RAN Alliance. 2025. Available online: https://specifications.o-ran.org/download?id=852 (accessed on 11 August 2025).
- Abdalla, A.; Moore, J.; Adhikari, N.; Marojevic, V. ZTRAN: Prototyping Zero Trust Security xApps for Open Radio Access Network Deployments. IEEE Wirel. Commun. 2024, 31, 66–73. [Google Scholar] [CrossRef]
- Jiang, H.; Chang, H.; Mukherjee, S.; Van der Merwe, J. OZTrust: An O-RAN Zero-Trust Security System. In Proceedings of the IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Dresden, Germany, 7 November 2023. [Google Scholar]
- Zaheer, Z.; Chang, H.; Mukherjee, S.; Van der Merwe, J. eZTrust: Network-Independent Zero-Trust Perimeterization for Microservices. In Proceedings of the 2019 ACM Symposium on SDN Research (SOSR ‘19), San Jose, CA USA, 3 April 2019. [Google Scholar]
- The Kubernetes Authors. Using RBAC Authorization. 28 June 2024. Available online: https://kubernetes.io/docs/reference/access-authn-authz/rbac/ (accessed on 11 October 2024).
- The Cilium Authors. Cilium—Cloud Native eBPF-Based Networking, Observability, Security. Available online: https://cilium.io/ (accessed on 11 October 2024).
- Tigera, Inc. Calico. Available online: https://docs.tigera.io/calico/latest/about/ (accessed on 11 October 2024).
- Chen, X.; Feng, W.; Ge, N.; Zhang, Y. Zero Trust Architecture for 6G Security. IEEE Netw. 2024, 38, 224–232. [Google Scholar] [CrossRef]
- Dumitru, I.-A. Zero Trust Security. In Proceedings of the International Conference on Cybersecurity and Cybercrime (IC3), Bucharest, Romania, 30 April 2022. [Google Scholar] [CrossRef]
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A Survey on Zero Trust Architecture: Challenges and Future Trends. Wirel. Commun. Mob. Comput. 2022, 6476274. [Google Scholar] [CrossRef]
- Basta, N.; Ikram, M.; Kaafar, M.; Walker, A. Towards a Zero-Trust Micro-segmentation Network Security Strategy: An Evaluation Framework. In Proceedings of the NOMS 2022—2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25 April 2022. [Google Scholar]
- Sheikh, N.; Pawar, M.; Lawrence, V. Zero trust using Network Micro Segmentation. In Proceedings of the IEEE INFOCOM 2021—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Vancouver, BC, Canada, 10 May 2021. [Google Scholar]
- Mhaskar, N.; Alabbad, M.; Khedri, R. A Formal Approach to Network Segmentation. Comput. Secur. 2021, 103. [Google Scholar] [CrossRef]
- NIST; Computer Security Resource Centre (CSRC). Policy Machine|CSRC . 6 June 2016. Available online: https://csrc.nist.gov/Projects/Policy-Machine (accessed on 10 February 2025).
- The Kubernetes Authors. Kubernetes. 2025. Available online: https://kubernetes.io/ (accessed on 25 April 2024).
- Istio Authors. The Istio Service Mesh. 2025. Available online: https://istio.io/latest/ (accessed on 25 April 2024).
- Kiali. Kiali—The Console for Istio Service Mesh. 2025. Available online: https://kiali.io/ (accessed on 25 April 2024).
- Paul, B.; Rao, M. Zero-Trust Model for Smart Manufacturing Industry. Appl. Sci. 2023, 13, 221. [Google Scholar] [CrossRef]
- Ruambo, F.A.; Zou, D.; Yuan, B. Securing SDN/NFV-Enabled Campus Networks with Software-Defined Perimeter-Based Zero-Trust Architecture. SSRN 2023. [Google Scholar] [CrossRef]
- Bello, Y.; Hussein, A.; Ulema, M.; Koilpillai, J. On Sustained Zero Trust Conceptualization Security for Mobile Core Networks in 5G and Beyond. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1876–1889. [Google Scholar] [CrossRef]
- Barr, A.; Lavi, O.; Naor, Y.; Rampal, S.; Tavori, J. Technical Report: Performance Comparison of Service Mesh Frameworks: The MTLS Test Case. arXiv 2024, arXiv:2411.02267. [Google Scholar]
- Rodigari, S.; O’Shea, D.; McCarthy, P.; McCarry, M.; McSweeney, S. Performance Analysis of Zero-Trust multi-cloud. In Proceedings of the IEEE 14th International Conference on Cloud Computing (CLOUD), Chicago, IL, USA, 5 September 2021. [Google Scholar]
- Cunningham, C.; Holmes, D.; Pollard, J. The Eight Business and Security Benefits of Zero Trust Business Case: The Zero Trust Security Playbook. Forrester Research, 2019. Available online: https://www.kennisportal.com/wp-content/uploads/2022/06/Akamai-the-eight-business-and-security-benefits-of-zero-trust-report.pdf (accessed on 27 August 2024).
- Brasser, F.; Gens, D.; Jauernig, P.; Sadeghi, A.; Stapf, E. SANCTUARY: ARMing TrustZone with User-space Enclaves. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium, San Diego, CA, USA, 24 February 2019. [Google Scholar]
- Vomvas, M.; Ludant, N.; Noubir, G. Establishing Trust in the Beyond-5G Core Network using Trusted Execution Environments. arXiv 2024, arXiv:2405.12177. [Google Scholar]
- Zhang, J.; Zheng, J.; Zhang, Z.; Chen, T.; Qiu, K.; Zhang, Q.; Li, Y. Hybrid isolation model for device application sandboxing deployment in Zero Trust architecture. Int. J. Intell. Syst. 2022, 37, 11167–11187. [Google Scholar] [CrossRef]
- Zheng, D.; Xing, H.; Cao, X.; Xu, J. Efficient Zero-Trust-enabled Service Function Chain Deployment in Multi-Vendor Networks. TechRxiv 2024. [Google Scholar] [CrossRef]
- Nadeem, A.; Hussain, M.; Iftikhar, A.; Aslam, S. Narrowband IoT Device to Device Pairing Scheme to Save Power. In Proceedings of the IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5 November 2020. [Google Scholar]
- Wang, H.; Xu, L.; Yan, Z.; Gulliver, T.A. Low-Complexity MIMO-FBMC Sparse Channel Parameter Estimation for Industrial Big Data Communications. IEEE Trans. Ind. Inform. 2020, 17, 3422–3430. [Google Scholar] [CrossRef]
- Wang, H.; Xiao, P.; Li, X. Channel Parameter Estimation of mmWave MIMO System in Urban Traffic Scene: A Training Channel-Based Method. IEEE Trans. Intell. Transp. Syst. 2024, 25, 754–762. [Google Scholar] [CrossRef]
| Methodolgoy | Key Techniques | Advantages | Disadvantages |
|---|---|---|---|
| Cryptographic | IPSec, MACsec, mTLS | Provable security, Standardised | High compute overhead, Key management complexity |
| Signature Based | IDS/IPS that match network traffic against a database of known threat signatures | High accuracy for known attacks, Low false-positive rate on familiar patterns | Ineffective against zero-day exploits, Signature database must be constantly updated |
| AI/ML Based | Supervised or unsupervised models trained on normal operations to flag anomalies | Adapts to new threats, Real-time response | Training data vulnerability, May suffer false positives under traffic shifts |
| Hardware Assisted | TEEs, Trust zones | Tamper-proof execution, Low latency | Limited to supported platforms, Additional cost, Does not address network-level threats |
| Blockchain Based | Distributed Ledger Technology (DLT), Decentralised identity | Immutable audit trails, No single Point of Failure, Transparent compliance | High latency, Energy intensive, Scalability concerns |
| Zero Trust Based (Proposed) | Dynamic PEP/PDP, Micro-segmentation | Least-privilege enforcement, full interface coverage, Fully adaptive | Policy management complexity, ~1–10ms latency overhead |
| Related Work | Approach | Security Methodology | Key Limitations | Our Work |
|---|---|---|---|---|
| Liyanage et al. [17] |
|
|
|
|
| Groen et al. [18] |
|
|
|
|
| O-RAN WG11 (Threats, Security Requirements, and White Paper) [9,19,20,21,22,23] |
|
|
|
|
| Abdalla et al. (ZTRAN) [24] |
|
|
|
|
| Jiang et al. (OZTrust) [25] |
|
|
|
|
| Chen et al. [26] |
|
|
|
|
| Caller UA (SPIFEE) | Target (Namespace/App) | Operation | Decision |
|---|---|---|---|
| spiffe://.../ns/radio/sa/ru-service-account | ran, app: vdu | any | Allow |
| any other principal (implicit) | ran, app: vdu | any | Deny |
| any source IP ∈ 192.0.2.0/24 | istio-system ingressgateway | any | Deny |
| any source IP ∉ 192.0.2.0/24 (implicit) | istio-system ingressgateway | any | Allow |
| Feature | Advantages | Limitations |
|---|---|---|
| Isolation Granularity |
|
|
| Policy Enforcement |
|
|
| Security Coverage |
|
|
| Operational Visibility |
|
|
| Scalability/Manageability |
|
|
| Performance Overhead |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hashem Eiza, M.; Akwirry, B.; Raschella, A.; Mackay, M.; Maheshwari, M.K. A Hybrid Zero Trust Deployment Model for Securing O-RAN Architecture in 6G Networks. Future Internet 2025, 17, 372. https://doi.org/10.3390/fi17080372
Hashem Eiza M, Akwirry B, Raschella A, Mackay M, Maheshwari MK. A Hybrid Zero Trust Deployment Model for Securing O-RAN Architecture in 6G Networks. Future Internet. 2025; 17(8):372. https://doi.org/10.3390/fi17080372
Chicago/Turabian StyleHashem Eiza, Max, Brian Akwirry, Alessandro Raschella, Michael Mackay, and Mukesh Kumar Maheshwari. 2025. "A Hybrid Zero Trust Deployment Model for Securing O-RAN Architecture in 6G Networks" Future Internet 17, no. 8: 372. https://doi.org/10.3390/fi17080372
APA StyleHashem Eiza, M., Akwirry, B., Raschella, A., Mackay, M., & Maheshwari, M. K. (2025). A Hybrid Zero Trust Deployment Model for Securing O-RAN Architecture in 6G Networks. Future Internet, 17(8), 372. https://doi.org/10.3390/fi17080372






