Abstract
With the rapid development of geological blockchains and Internet of Things-based data acquisition technologies, massive amounts of heterogeneous data are constantly emerging. However, this data is stored in a distributed manner across different organizational or business blockchains. Data sharing among multiple geological blockchains faces numerous challenges, either exposing sensitive data during verification or lacking effective authorization mechanisms. Therefore, how to achieve fine-grained access control and privacy protection across multiple blockchains has become a critical issue that must be addressed in geological data sharing. In this paper, we propose GeoCross, a cross-chain geological data sharing framework that enables fine-grained authorization management and privacy protection. First, GeoCross provides a hierarchical hybrid encryption mechanism that uses symmetric encryption for geological data protection and ciphertext-policy attribute-based encryption to enable flexible cross-chain access policies. Second, we integrate a Groth16-based zero-knowledge proof mechanism, which allows a chain to verify the existence, integrity, and accessibility of off-chain data without revealing the content. Furthermore, we introduce a Reputation-based Non-interactive Relay node Selection protocol (RNRS), which enhances the trustworthiness and fairness of cross-chain routing. Finally, we implement GeoCross in a multi-chain Hyperledger Fabric environment and evaluate its performance under real-world workloads. Results show that Groth16 verification requires only three bilinear pairings, achieving a throughput of up to 390 tps on a single chain and 1550 tps in a concurrent multi-chain environment. Even with 50% malicious nodes, the RNRS protocol still maintains a success rate of over 91%. These results demonstrate that GeoCross provides an efficient and practical solution for secure and privacy-preserving cross-chain geological data sharing.
1. Introduction
Geological information, serving as fundamental data for natural resource surveys, energy exploration, and mineral development [1,2], directly influences industrial progress due to its authenticity and security. With the progress of geological information digitization, geological institutions and research institutes at various levels have accumulated massive data resources [3]. However, these data are distributed and stored in different bureaus or business systems, lacking effective collaboration mechanisms and serious data silos. Traditional cloud-based geological data sharing platforms rely on a centralized trust model, where a single service provider controls the storage, access management, and logging mechanisms. Even if cloud data is encrypted, this centralized architecture still creates a single point of failure and an attractive target for attacks or internal misuse. In addition, conventional authorization mechanisms typically grant users full data access once permission is issued, resulting in coarse-grained control and potential privacy exposure, especially in multi-organization geological data sharing.
Blockchain establishes a new trust foundation for geological data sharing [4]. Its decentralization and immutability enable multiple parties to achieve data sharing without relying on central authorities. Current research has attempted to apply blockchain to geological information management and research outcomes sharing scenarios, achieving data authorization and sharing through smart contracts [5]. However, the differences in trust models, access policies, and privacy-preserving mechanisms among different geological blockchain systems (such as scientific research chains, provincial bureau chains, and industry chains) pose challenges for data sharing among multiple blockchains.
Currently, some mainstream cross-chain schemes have been proposed [6,7,8,9], such as sidechain [10,11], notary mechanism [12,13], hash-locking [14,15], and relay chain [16]. These schemes achieve cross-chain collaboration by connecting independent blockchain networks, thereby alleviating the issues of single-chain performance and business interaction [17,18]. BitXHub [19], a cross-chain solution based on sidechain, supports asset transfer and information sharing across different blockchains. However, cross-chain data sharing requires exposing the data to all participants, which can lead to data privacy issues [20,21]. Wecross [22] proposed a simple and secure cross-chain scheme that adopts a gateway-like cross-chain architecture to enable interoperability. The gateway model still suffers from the drawbacks of centralized control [23], and the routing proxy node can access detailed information about cross-chain transactions, making its credibility a vulnerability that affects cross-chain security [24]. Therefore, most existing cross-chain solutions overlook the requirement for privacy protection and face the issue of sensitive data exposure [25,26], which may hinder business collaboration between multiple blockchains.
Since geological data involves national secrets, data privacy protection has become a key challenge in data sharing among multiple geological blockchains. On the one hand, the absence of a unified access control and authorization mechanism makes cross-chain data sharing subject to unauthorized access. On the other hand, the process of cross-chain data sharing may expose geological data and pose a risk of privacy leakage [27]. In addition, the proxy node that cross-chain communication relies on still faces issues such as trust opacity and unfair elections [28], making it difficult to ensure the security and reliability of data sharing.
In this work, to tackle the aforementioned issues, we propose GeoCross, a cross-chain geological data sharing scheme that enables fine-grained authorization and privacy protection. In contrast, GeoCross introduces zero-knowledge proofs (ZKP) based on Groth16, aiming to achieve privacy protection for cross-chain data. Furthermore, existing attribute-based encryption schemes are typically only applicable within a single governance domain and cannot directly handle cross-domain authorization needs between independent blockchains. Although some improved attribute-based encryption methods optimize performance, they still do not consider fine-grained authorization management for cross-chain access. GeoCross’s proposed hierarchical hybrid encryption mechanism decouples data encryption from authorization strategies, making it more suitable for cross-institutional and cross-chain data sharing environments. Moreover, existing cross-chain routing mechanisms generally employ fixed proxies or probabilistic selection strategies based on PoW/PoS, making them vulnerable to centralized, manipulated, or coordinated attacks. RNRS incorporates reputation values and verifiable random function (VRF) to achieve non-interactive agent election, improving the robustness and fairness of cross-chain routing. First, aiming at the complexities of cross-chain access authorization and the resulting privacy leakage, we propose a hierarchical access control mechanism for cross-chain geological data sharing. The hierarchical mechanism employs symmetric encryption (SE) at the data layer to secure data storage and sharing, and ciphertext-policy attribute-based encryption (CP-ABE) at the authorization layer to enable fine-grained management of cross-chain data access credentials, which effectively separates and coordinates data privacy protection and access policy control. Second, to balance trustworthiness and privacy protection during cross-chain data sharing, this paper proposes a cross-chain data verifiable mechanism based on ZKP. By constructing the Groth16 proof circuit [29], the owner chain can prove the existence, correctness, and accessibility of the data to the requester chain without revealing the plaintext data, thereby verifying the legitimacy of data before cross-chain interaction. This mechanism achieves “verifiable but invisible” privacy protection in cross-chain sharing, reducing the risk of privacy leakage and unnecessary communication overhead. Finally, to address the trust issues in cross-chain data sharing, this paper proposes RNRS. By combining node reputation with a random timer generation strategy, this mechanism autonomously elects proxy nodes without requiring interaction, thereby enhancing the trustworthiness of cross-chain relays. GeoCross facilitates secure and trustworthy data sharing between geological blockchains, fulfills the requirements for cross-chain collaboration with multi-source geological information. The main contributions of this paper are as follows:
- We propose a hierarchical hybrid encryption mechanism for cross-chain geological data sharing. At the data layer, SE is employed to enhance the efficiency of encrypting large-scale geological datasets, while at the authorization layer, CP-ABE is integrated to achieve fine-grained access control. By decoupling encryption from authorization, the mechanism enables fine-grained authorization and minimizes data exposure.
- We design a cross-chain data-verifiable and privacy-preserving scheme based on ZKP, which employs a Groth16 proof circuit to enable the requester chain to verify the existence, correctness, and availability of owner chain data during cross-chain interactions without accessing any data.
- We introduce a random RNRS based on reputation value and VRF. This mechanism utilizes dynamic updates of reputation and a VRF to achieve random and reliable agent election, improving the reliability of cross-chain routing.
- We conduct a security analysis focusing on data confidentiality and authorization correctness, and evaluate its performance in a multi-chain environment. The experimental results demonstrate the feasibility of GeoCross in geological data sharing scenarios.
The rest of this paper is organized as follows. Section 2 reviews related work. In Section 3, we present the system model, security model, and design goals. Section 4 presents the details of GeoCross. Section 5 and Section 6 discuss security analysis and performance evaluation, respectively. Finally, in Section 7, we conclude this paper.
2. Related Work
In recent years, blockchain technology has been gradually introduced into the field of geological data sharing due to its decentralization, immutability and traceability, to solve problems such as data silos, tampering risks and privacy leakage in centralized geological data management. Li et al. [30] investigated the application potential of blockchain in geological data sharing and believed that blockchain can effectively improve the credibility and tamper-resistance of geological data during storage and sharing processes. In response to the common problems of “duplicate collection” and “information silos” in current geological data sharing, Li et al. [31] proposed a sharing model that integrates geological data indexing and blockchain, putting an index on the chain to achieve secure sharing and traceable management. Zhou et al. [32] built a geological data sharing platform based on blockchain. By writing verified geological information and its ciphertext index into the blockchain and introducing a random competitive allocation mechanism, they ensured that the shared data could not be reverse-parsed under the premise of verifiability, thereby improving the security and fairness of the data sharing process.
Existing research indicates that blockchain has significant advantages in improving the security, transparency, and credibility of geological data sharing. Existing studies demonstrate that blockchain provides significant advantages in enhancing the security, transparency, and trustworthiness of geological data sharing. Razzaq et al. [33] proposed a decentralized blockchain-based architecture for managing remote-sensing big-data documents, supporting secure sharing, version control, and integrity protection without relying on a central authority. However, the framework is designed primarily for document-level remote-sensing data and focuses on immutability and availability, confidentiality is handled only via conventional encryption, and access policies cannot be defined or enforced in a fine-grained manner. Zhang et al. [34] developed a blockchain-based management scheme for Earth-observation products to improve decentralization, traceability, and tamper resistance of provenance metadata. Nevertheless, this solution is mainly concerned with provenance management rather than data privacy, and it does not address fine-grained authorization or cross-chain access, particularly in heterogeneous environments where different organizations operate independent blockchains and cloud platforms.
From a broader geospatial perspective, Chafiq et al. [35] conducted a comprehensive survey on blockchain applications in geospatial data sharing, highlighting its potential for secure storage, property rights management, and traceability, as well as key challenges such as scalability, privacy, interoperability, and regulatory constraints; however, most of these efforts remain conceptual. In more specific geological use cases, Aufaristama [36] explored the use of non-fungible tokens (NFTs) on public blockchains for geological data dissemination and digital asset management. Nevertheless, this work emphasizes openness and public dissemination rather than controlled sharing of sensitive geological information.
However, blockchain still has shortcomings in the field of geological data sharing [37,38]. First, most existing work focuses on data tamper-resistance and traceability, while paying insufficient attention to data confidentiality and access control mechanisms. Second, geological data often spans multiple departments and systems, and cross-institutional trust and privacy protection mechanisms remain not sound. The consensus efficiency and access permission of consortium blockchain under multi-node collaboration still exist. Furthermore, current research primarily focuses on on-chain data storage or indexing on chain, while further research is needed on the collaboration between encryption technologies and original data management methods such as blockchain and geological clouds.
3. System Overview
3.1. System Model
The architecture of GeoCross is illustrated in Figure 1, which includes four entities: the Owner Chain (Geoscience Institute Chain), the Requester Chain (Provincial Bureau Chain), the Relay Chain, and Geological Cloud Server (GCS). Furthermore, to enable cross-chain data sharing, each chain incorporates proxy nodes.
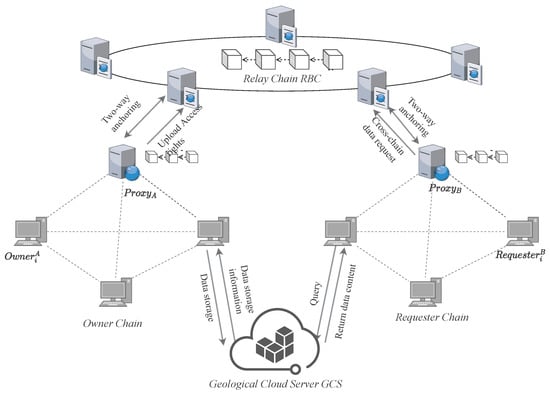
Figure 1.
System architecture of GeoCross.
- Owner Chain: Owner Chain consists of data owners, represented by the Geoscience Institute Chain that possess original data. It is responsible for responding to data requests and managing shared processing. Data owners encrypt the original data and issue data tokens to authorize cross-chain data sharing.
- Requester Chain: Requester Chain is a consortium chain (e.g., Provincial Bureau Chain) composed of data requesters. Data requesters seek to obtain and utilize correct data. They initiate access requests, verify data validity, request access permissions across the blockchain, and ultimately acquire the data ciphertext.
- Relay Chain: Relay Chain serves as the trust and collaboration hub of the cross-chain system. It is responsible for business chain registration, cross-chain message routing, and access policy verification, ensuring the credibility and privacy of cross-chain interoperability.
- Geological Cloud Server (GCS): GCS serves as a trusted storage service shared by all business chains, storing only ciphertexts and not any plaintext information [39].
- Proxy Nodes: Acting as cross-chain interfaces, proxy nodes are responsible for routing and forwarding cross-chain requests, data tokens, and ciphertexts, but do not perform any encryption operations or plaintext processing.
3.2. Design Goals
To address the Data Privacy Exposure (DPE) problem in cross-chain geological data sharing, this paper proposes GeoCross, a privacy-preserving cross-chain sharing scheme for geological blockchains that ensures secure data sharing, privacy protection, and verifiable access. Specifically:
- Cross-chain trust: To overcome the lack of inter-chain trust, GeoCross employs a Relay Chain and proxy node collaboration mechanism to implement policy verification and data authorization across multiple blockchains. The Relay Chain supports business chain registration, message routing, ensuring that cross-chain requests are legitimate and secure interactions. Proxy nodes within each Owner Chain and Requester Chain are selected randomly and with minimal trust using verifiable algorithms. They only handle message forwarding and token verification without accessing any plaintext data, achieving a minimal-trust proxy model.
- Cross-chain privacy protection: To mitigate Cross-chain Privacy Exposure (CPE), GeoCross integrates a zero-knowledge verification mechanism, enabling the Owner Chain to prove the existence and accessibility of geological data to the Requester Chain without revealing any original data.
- Cross-domain access control: To prevent Cross-domain Data Unauthorized Access (CDUA), the system adopts a multi-layered authorization encryption strategy, ensuring that only users whose attributes satisfy policies can perform hierarchical decryption. This design guarantees clear authority boundaries and controlled access throughout the cross-chain data sharing.
3.3. Threat Model
We assume that the central authority and attribute authorities are fully trustworthy [40,41], they are capable of correctly executing the system initialization algorithm, securely generating global system parameters and the master key, and distributing attribute private keys to authenticated users exclusively through secure channels. The data owner is assumed to be honest and authorizes data transmission exclusively to authorized users, but all on-chain communications are subject to potential monitoring. Data storage modules are honest-but-curious, they faithfully store data and respond to the requests from both the Owner Chain and the Requester Chain, but they are also curious about the stored data.
Potential attackers in the system include malicious data users, malicious proxy nodes, and the attacked Requester Chain. Malicious data users fall into two types: (1) unauthorized users, who attempt to bypass access control policies to directly access data ciphertext across chains; (2) authorized users, who may abuse their own attribute private keys or collude with proxy nodes to obtain data beyond their permissions. They attempt to obtain unauthorized data by cracking the symmetric key .
Malicious behaviors of proxy nodes include refusing to forward services, tampering or forging data tokens, and attempting to recover plaintext content from forwarded data tokens and ciphertext.
The Relay Chain or other business chains are at risk of being attacked. They may forge verification results for access control or incorrectly transmit data ownership proofs, thereby affecting the system’s cross-chain data sharing services.
To further analyze the system’s resistance to attacks, we define two types of typical adversaries:
- Type I (external attacker): Without a legitimate attribute key, they can only attempt to obtain tokens or data by cracking ciphertext, forging requests, or eavesdropping on communications.
- Type II (internal attackers): Include malicious data users, malicious proxy nodes, and compromised business chains. They may attempt to hinder data sharing and compromise data privacy by disrupting cryptographic algorithms or communication transmission.
4. Detail of Our Proposed Scheme
4.1. System Initialization
Trusted Setup Phase: In this phase, the authority (e.g., the China Geological Survey) generates the proving key and verification key for geological blockchains (both data owners and data users), which are related to the verification of geological data. The produced in this phase contains the bilinear group parameters and essential secret parameters . All these parameters are stored within the Relay Chain.
Applying the ABE scheme in inter-blockchain data sharing requires a Key Generation Center (KGC) to initialize system parameters. The KGC serves as a trusted third-party authority responsible for executing the initialization algorithm that generates the cryptographic parameters required.
The KGC employs a hash function H to compute the public parameters. The function H maps arbitrary binary strings to elements of group G:H:. In GeoCross, H takes two types of inputs: , where x is an arbitrary string; , where j is a positive integer. Here, and . For brevity, these inputs are denoted as and , respectively. The detailed process and resulting outputs of the KGC are as follows:
: The authority creates a bilinear pairing tuple and selects a hash function : involved in the encryption process to compute the public parameters, which maps any binary string to an element in group G. In this scheme, H has two types of inputs, namely and , where x is an arbitrary string, j is any positive integer, , and . We denote these two inputs as and . In the security analysis, these hash functions are regarded as random functions. Furthermore, by randomly selecting and , the global public parameters are obtained as .
: In this process, the initialization function randomly selects parameters and and from a cyclic group of prime order p, and parameters from . Then, Setup uses the global parameters to generate the public key and master private key for the ABE scheme [42].
. For each data user with attribute set , the authority uses the KeyGen algorithm to generate the attribute-based private key , taking the master private key and the node’s attribute set S as input. The KGC first randomly selects parameters and from , and then computes the partial private key .
Then, for each and , the authority uses the corresponding parameters from to compute the partial private keys for different attributes.
Then, compute the partial private key , where a random value is selected from . And authority computes , for t=1,2, , . Finally, the secret key of data user is .
4.2. Proxy Node Selection
To enable cross-chain data access, data sharing between geological blockchains and the Relay Chain is carried out through proxy nodes. The proxy’s public key is registered on the Relay Chain via a signed blockchain transaction. Since all chains obtain this public key directly from the immutable ledger rather than through off-chain message exchange, the process is inherently resistant to man-in-the-middle attacks. We propose RNRS to elect proxy nodes for each geological blockchain. All nodes are eligible to participate in the election. RNRS divides the election process into multiple epochs, each containing a fixed number blocks. A portion of these blocks ( to , ) is reserved for the election phase. Each candidate node combines its reputation value with the latest checkpoint block hash to generate a random number using a VRF, which determines its waiting timer length L. The node whose timer expires first becomes the proxy node for this epoch, broadcasts the election result, and other nodes stop their timers.
In RNRS, each node’s reputation value is maintained and updated uniformly on the blockchain. Initially, all nodes are assigned the same reputation value , a node’s reputation increases by 1 point each time it successfully participates in an intra-chain consensus. If a node is absent during consensus, 2 points are deducted. When a node’s reputation value drops to zero, it loses its eligibility to participate in subsequent elections. To prevent any single node from the proxy for extended periods, the reputation value of a node is immediately halved upon election, thereby increasing the likelihood that other nodes will be selected in future rounds.
Each candidate node i constructs a timer by first obtaining its own and the total reputation value of all nodes R. Using the latest checkpoint block in the election as a random seed, the node generates a VRF random number and its proof , where is the private key of node i and the corresponding public key is registered on the blockchain.
Each candidate proxy node then uses the function to find the smallest timer value L that satisfies the condition, where d is a difficulty parameter. Nodes with higher have a wider range of valid counters, making them more likely to be selected as proxy nodes. Assuming the first block height of the election period is , where i is elected when the block at height is added to the ledger. Upon receiving node i’s election, upper-layer nodes verify the following conditions before confirming the election result: (a) whether satisfies the inequality above; (b) whether the current block height has exceeded ; (c) whether the proof correctly verifies that y was generated from the random seed . If checks pass and no other node has already been elected, node i is designated as the proxy node for this epoch, responsible for cross-chain interoperability until a new representative is elected or the next epoch begins. In exceptional cases where all candidates produce excessively large values L and no suitable proxy can be selected, the election is considered timed out, and the node with the highest reputation value is assigned as the proxy node.
The reputation mechanism ensures fairness in proxy selection and gradually eliminates malicious or inactive nodes. This approach provides a reliable transmission process for cross-chain data sharing among geological blockchains. Subsequent cross-chain data exchanges are securely forwarded through the elected proxy nodes.
4.3. Cross-Chain Data Request
Phase 1: Cross-chain Request Initiation. When a provincial bureau user (i.e., data user) attempts to initiate a data access to another geological blockchain on their chain (Provincial Bureau Chain), the access request is processed by invoking a cross-chain smart contract. The user submits its desired data identifier () as the target parameter of the request. Upon detecting the cross-chain request, the provincial chain’s proxy node triggers the corresponding cross-chain data access. Specifically, the proxy node first collects and verifies the user’s attributes. These attributes include the user’s identity information, role permissions, and so on. The proxy node then signs the access request, which consists of the request identifier (), the data identifier (), and the user’s attributes with the Provincial Bureau Chain’s private key. Finally, the proxy node forwards the request to the Relay Chain through the routing interface configured by the Relay Chain.
Phase 2: Data Existence Verification. When the access contract on the Relay Chain receives a cross-chain request from the Provincial Bureau Chain, it first performs integrity and validity verification of the request message. The Relay Chain’s nodes use the public key of the Provincial Bureau Chain to verify the digital signature submitted by the proxy node, ensuring that the message has not been tampered with and it was indeed initiated by a legitimate provincial-chain entity. If the signature verification succeeds, the access contract further reviews the request based on the fine-grained access control policy. The contract compares the requester’s user attributes with the policy associated with the target data . If satisfied, the Relay Chain routes the access request to the target proxy node of the Geological Institute Chain, which serves as the entry point for cross-chain communication. Otherwise, if the access policy is not satisfied, the request is rejected.
Then, the proxy node of the Geoscience Institute Chain queries its local state to confirm that exists and is accessible. To further prove the existence and accessibility of the geological data to the Provincial Bureau Chain, a ZKP must be generated. The Geoscience Institute Chain’s proxy node collects the private witness (including the Merkle path , status value = 1, etc.) and runs the Groth16 algorithm to prove possession and accessibility without revealing any geological information. The prover first converts the data verification circuit into a Quadratic Arithmetic Program (QAP), then uses together with the private inputs to generate the proof , where is the commitment to , is the commitment to , and contains the cross-checking for all constraints.
To compute and verify the ZKP, the scheme designs a core constraint logic circuit. The circuit takes the current public Merkle root of the Geoscience Institute Chain and the as public inputs; private inputs include the leaf hash of , = SHA-256 (, ), the Merkle path indices , sibling hashes , and the data accessibility status. Circuit constraints and computation flow:
- Leaf verification: compute = SHA-256 and constrain = to ensure consistency with the leaf node.
- Merkle path verification: starting from and , recursively compute each level according to until obtaining , and constrain = to prove that belongs to the chain’s Merkle tree.
- Accessibility verification: constrain = 1 to confirm the data is accessible.
When all constraints hold, the circuit outputs 1, indicating that the verification passes and the proof is valid.
Then, the Geoscience Institute Chain routes the generated proof tuple to the Provincial Bureau Chain via the Relay Chain. In this process, the Relay Chain only performs message forwarding, ensuring the privacy of geological data. The proxy node of the Provincial Bureau Chain uses issued by the Geoscience Institute Chain to verify the validity of the proof .
After receiving the proof, the proxy of the Provincial Bureau Chain first extracts the target data identifier and the published Merkle root from the request, along with other public inputs provided by the Geoscience Institute Chain.
It uses the verification parameters contained in , the verifier encodes these public inputs into a group element , where each corresponds to a specific public input value. Finally, the verifier uses the verification function to check the proof correctness: .
If , the Provincial Bureau Chain confirms that the geological data exists and is accessible on the Geoscience Institute Chain, without learning any private information.
The proxy node of the Provincial Bureau Chain verifies the proof with by performing three bilinear pairing computations. First, it computes , then separately evaluates , , and . Only generated by the legitimate data owner satisfy , which confirms that the prover indeed possesses the claimed data. If the verification succeeds, the Provincial Bureau Chain is assured that the Geoscience Institute Chain truly holds the geological data and the data status is valid. If the verification fails, the Provincial Bureau Chain rejects the cross-chain request.
Phase 3: Owner-side Encryption and Token Issuance. After confirming that the requested data exists and is accessible, the data owner must ensure data confidentiality and fine-grained access control in cross-chain sharing. GeoCross employs a two-stage encryption mechanism combined with a defined access control policy to generate the corresponding access token.
First, the DO encrypts the original geological data using a symmetric key to produce the ciphertext , which is stored in a GCS. Then, to protect the , the DO encrypts it using an ABE scheme. Using , the access policy matrix M, the DO computes:
This process ensures that only users whose attributes satisfy the access policy can decrypt and use the .
The specific steps are:
- Step 1: Randomly select parameters from and compute the corresponding values used for key encryption.
- Step 2: Given an attribute matrix M with and , compute that can be derived for each attribute dimension.
- Step 3: Finally, compute , which represents the encryption of . Thus, the cross-chain ciphertext can be expressed as: .
This ciphertext is embedded in the cross-chain message and forwarded through the Relay Chain, ensuring data confidentiality and fine-grained access in the GeoCross.
After two stage encryption, the system designs a Data Ticket mechanism to enable controlled authorization. The Owner Chain issues a = {, , , }, where represents the identifier of the cross-chain request, represents the identifier of the target data, defines the token’s validity period, and represents the ciphertext location stored in the GCS.
4.4. Cross-Chain Data Access
Once the Requester Chain possesses a valid, unexpired data token (Data Ticket), it can retrieve the corresponding ciphertext from GCS based on the storage location provided in the token. Furthermore, the proxy node also retrieves from the Relay Chain. After data retrieval, the requesting proxy node packages the request result {, , , signature verification record} and writes it to the Requester Chain for on-chain recording. The actual DU attempt to decrypt with the corresponding to its own attributes. Only if its attributes satisfy the access control conditions can the DU recover the key and decrypt the original data; otherwise, the request is terminated.
Step 1: When the attribute sets accessing the blockchain satisfy the attribute matrix used for encryption, there will be a constant .
Step 2: According to the constant, we can compute:
The cross-chain data can be decrypted. Finally, can use to decrypt the original geological data. The process of cross-chain data sharing is shown in Figure 2.
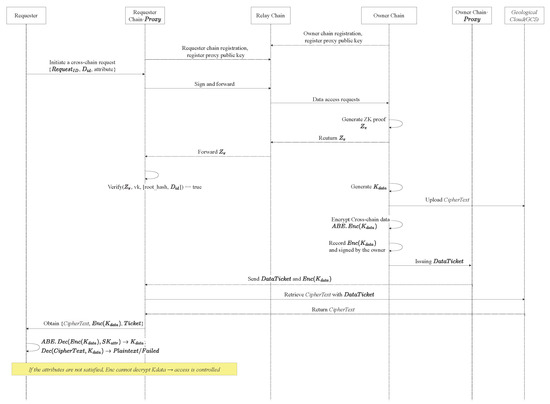
Figure 2.
The overall process of cross-chain data sharing in GeoCross.
5. Security Analysis
5.1. Data Confidentiality
Theorem 1.
Data Confidentiality: GeoCross ensures data confidentiality and authorized access through a hybrid encryption policy combining symmetric encryption (SE) and attribute-based encryption (ABE). Specifically, the data owner encrypts the plaintext M using a randomly generated symmetric key to produce = . Then, is encrypted with an access policy Policy using ABE, get = . The ciphertext is expressed as ,), where is maintained off-chain, and is transferred across blockchains through the Relay Chain.
Proof.
To demonstrate that no probabilistic polynomial-time (PPT) adversary can compromise data confidentiality with a non-negligible advantage, we construct a security game between the adversary and the challenger . This game models the confidentiality guarantees of GeoCross under adaptive attacks. Assume that achieves a non-negligible advantage in this game. The adversary selects a challenge matrix with each dimension bounded by q. is allowed to query any secret key that cannot be directly employed to decrypt the challenge ciphertext generated by . The detailed procedure is described as follows.
- Setup: executes ABE.Setup to generate the public parameters and publishes the system configuration.
- Query Phase I: Attribute Key Queries. may adaptively request the private key associated with any attribute set . If , provides the corresponding key .
- Challenge Phase: submits a pair of equal-length plaintexts (,). selects a random bit , generates a random symmetric key , and computes: , . It returns the ciphertext pair to .
- Query Phase II: may continue to request private keys for attribute sets that do not satisfy , and responds as before.
- Guess Phase: Finally, outputs a guess . The adversary’s advantage is defined as: .
The scheme is IND-CPA secure under the chosen-policy model if is negligible for all PPT adversaries .
Hybrid Experiments
To verify the security of the proposed scheme, we employ a hybrid experiment to reduce the security of the algorithm.
- : Real Game. The hybrid corresponds to the real security game , which accurately models the confidentiality properties of GeoCross under the defined threat model.
- : In , the symmetric encryption operation is replaced by an ideal random oracle. If can distinguish and with non-negligible probability, it can be used to break the IND-CPA security of the ABE scheme under the chosen-policy attack. Therefore, .
- : In , the ABE process is idealized. Instead of encrypting the symmetric key , the challenger encrypts a uniformly random value under a random policy : . If the adversary can distinguish and , an adversary can be built to break the security of the ABE scheme under the CPA model, which contradicts the security assumption.
- : In , the ciphertext becomes statistically independent of the challenge plaintext . Finally, the adversary’s distinguishing advantage is zero. Therefore, the advantage of any PPT adversary against the GeoCross confidentiality model satisfies: , indicating that GeoCross achieves semantic security under standard cryptographic assumptions.
□
Lemma 1.
In the GeoCross, any entity that fails to satisfy the predefined access policy, including passive eavesdroppers, off-chain storage servers (GCS), relay/proxy nodes, and unauthorized users, are unable to recover the or M, even with full access to both the off-chain ciphertext and cross-chain metadata.
Collusion-Resistance: If an attribute set does not satisfy the access policy Policy, the ABE scheme satisfying selective-policy IND-CPA security ensures that is indistinguishable to unauthorized entities, making pseudorandom to them. Furthermore, collusion among multiple users’ attribute private keys still cannot satisfy the access control policy, and thus cannot be recovered. Therefore, unauthorized users or colluding parties cannot compromise the ABE scheme.
Honest-but-Curious GCS/Relay/Proxy: Although the GCS, Relay Chain, and proxy nodes participate in the cross-chain data sharing, they can only observe (,) and the metadata. The proxy node merely forwards or authorized content generated through the relay process, while the GCS only stores encrypted data. They cannot recover or M. From the hybrid experiment, it follows that for any adversary A, the following holds: . Therefore, cross-chain data confidentiality is guaranteed under the unauthorized adversary model.
5.2. Data Correctness
Theorem 2.
Cross-chain Data Correctness: To prove that owner chains (e.g., geological institute chains) can access data without revealing any content, GeoCross uses a ZKP-based method. In this section, we verify the completeness, knowledge soundness, and zero-knowledge properties of this method. The requesting chain can determine whether other chains possess accessible data solely from the tuple , while learning nothing about any private information contained in . Prove that the cross-chain data is verifiable and not exposed, which means the requester chain can determine whether owner chains possess accessible data based on , without obtaining any private information from the proof .
Assume are the trusted parameters of the zero-knowledge proof system. Let be the zero-knowledge defined in GeoCross, where the public input is and the private witness is w = (, , , , ). The relation holds if the following conditions are satisfied: (1) compute from ; (2) using and , reconstruct bottom-up the Merkle root and ensure ; (3) “” = 1. If and only if , the Groth16 proof could be verified, i.e., ; and it satisfies: completeness, knowledge soundness, and zero-knowledge.
Completeness: The data owner acts as the prover, possessing data access rights, and can successfully respond to verification requests initiated by a requester. To verify the completeness, we define a security game : the challenger generates , and the prover holds a relation . If outputs a proof such that , then wins the game, it possesses legitimate data access rights.
Proof.
When the QAP constraints are satisfied, there exists a polynomial such that , where F (,) denotes the combination term of public input polynomials. If the GeoCross circuit correctly compiles the Merkle hash constraints and , then exists and the equality holds. Thus, the probability that the verification succeeds is: . Therefore, the verification is passed, the scheme completeness is proved. □
Knowledge-Soundness. The prover (i.e., the Owner Chain) must hold a correct witness to convince the verifier (i.e., the Requester Chain) that it holds a valid Merkle path with , which guarantees that the verifier accepts only when a valid witness w satisfying exists. To verify the knowledge soundness, we define the security game : A malicious forger attempts to generate a fake proof that convinces the verifier of the existence or accessibility of data with a invalid witness w. If can compute with such that , while no witness w exists for which , the forger wins the game.
Proof.
Groth16 guarantees the existence of an efficient extractor , whenever a malicious adversary can generate a valid proof , can extract the corresponding witness w. We construct a reduction algorithm as follows: simulates the Setup phase, generates , and sends to . The adversary outputs a forged pair such that , implying that it has created an apparently valid proof. uses the extractor to derive a witness . If , then has successfully broken the soundness, hence:
This proof shows that if the verifier accepts , the system guarantees the existence of a Merkle proof path and a valid state. A malicious geological blockchain cannot forge proofs of false data existence or unauthorized access to deceive data requesters. □
Zero Knowledge. In GeoCross, the prover (e.g., a geological blockchain) can convince the verifier that a specific data exists and is in an accessible state without revealing any geological data. For any verifier V, there exists an efficient simulator capable of generating a simulated proof that is computationally indistinguishable from real proof , without accessing any private data. To verify the zero-knowledge, we define the security game : The challenger generates and selects a random bit b. If , the proof is generated by ; if , the simulator generates . The adversarial verifier is given and outputs a guess . The advantage of is defined as: .
Proof.
Only the values (,) are publicly revealed, while all private inputs, such as the Merkle path and status are hidden. The proof consists of the . For any external observer, these commitments are indistinguishable from those generated in a real execution. According to the zero-knowledge of Groth16, the probability can be expressed as . Therefore, the adversarial verifier’s distinguishing advantage is negligible, namely . □
The proof demonstrates that the prover (the Owner Chain) can convincingly prove to the verifier (the Requester Chain) the existence and accessibility of geological data without disclosing any original data, achieving data privacy protection in cross-chain sharing. Furthermore, ZKP verification is a cubic bilinear pairing operation that can be completed with low latency, providing privacy protection for geologically sensitive data and adapting to the verification-authorization workflow in high-privacy scenarios such as geological results and remote sensing data.
5.3. Security Analysis of RNRS
GeoCross uses RNRS to elect proxy nodes for cross-chain relay. To verify the security of the proposed reputation-based non-interactive random node selection method, this section evaluates node behavior and election results. The experimental environment consists of 20 nodes, one-third of which are malicious and the rest are honest. The initial reputation of all nodes is set to 100. Each experiment runs for 20 epochs and each consisting of 100 blocks. The election is triggered after consensus is reached on the 50th block. We compare the proposed RNRS with three other selection methods: random selection, round-robin election, and proof of wait stake-based selection.
As shown in Figure 3a, during the initial epochs, the election success rates of the various schemes varied little. As the number of epochs increased, the election success rate of this scheme increased rapidly, stabilizing at after 20 epochs. This result demonstrates that RNRS can distinguish between honest and malicious nodes: honest nodes accumulate reputation through active participation in consensus, making them more likely to be elected as representatives in subsequent elections, while malicious nodes experience a decline in reputation due to refusal to participate or voting errors. This approach ensures the trust and secure selection of proxy nodes.
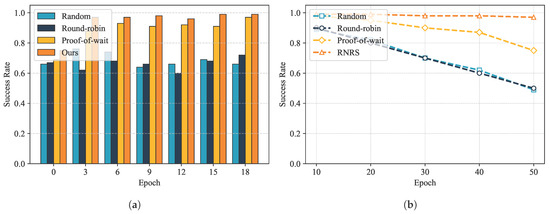
Figure 3.
(a) The change in success rate with increasing Epochs; (b) the change in success rate with increasing proportion of malicious nodes.
To further verify the security of RNRS, we simulated election results with a higher proportion of malicious nodes. As shown in Figure 3b, with the proportion of malicious nodes increased from to , the RNRS election success rate only dropped from approximately to . Its reputation accumulation, combined with the random function mechanism, effectively prevents malicious nodes from gaining an unfair advantage through computing power or frequent participation, maintaining the randomness and decentralization of this election method.
6. Performance Evaluation
In this section, we evaluate the performance of GeoCross from three perspectives: computational overhead, communication overhead, cross-chain interoperability latency, and compare it with existing approaches to demonstrate the feasibility of the proposed system.
6.1. Experimental Environment
For performance analysis, we selected three q-order groups, G, H, and , whose bilinear pairings are defined as . These groups are defined on the 256-bit Edwards curve MNT224, with the equation , which provides 96-bit security. Table 1 lists the computational time of various encryption operations on groups G and H. It can be seen that the cost of multiplication, exponentiation and hash computation on group G is significantly better than that on group H. Furthermore, GeoCross chooses AES-256 as the symmetric encryption algorithm and SHA-256 as the universal hash function. We deployed three blockchains (Hyperledger Fabric V2.2, Docker containers executing chaincode, and Raft as the consensus algorithm): two functional blockchains represent the Requester Chain (Provincial Bureau Chain) and Owner Chain (Geoscience Institute Chain), which simulate participants to implement cross-chain transactions; the other serves as a Relay Chain to implement cross-chain forwarding.

Table 1.
Comparison of the number of operations in different encryption algorithms.
6.2. Computational Overhead
In GeoCross, cross-chain data privacy and authorized data access are achieved using ABE. This section evaluates this approach from both theoretical complexity and experimental performance. We focus on analyzing the impact of attribute quantity and access policy complexity on system performance, and compare our scheme with two typical CP-ABE schemes.
Theoretical Analysis: In traditional ABE, the computational complexity of KeyGen and Encryption is affected by both the length of the encrypted data and the complexity of the access policy. In GeoCross, we designed a constant-size plaintext encapsulation encryption, making the computational overhead primarily related to the access control policy. To analyze the impact of access policy complexity, we set the following system parameters. M: the number of attributes; m, n: the number of rows and columns in the access policy matrix (MSP); N: the length of the attribute. The computational complexity of each phase is shown in Table 1.
As shown in Figure 4, as the number of attributes increases, the computational overhead of KeyGen, Encryption, and Decryption also increases. To further verify whether this computational overhead satisfies the requirements, we conducted an experimental performance analysis.
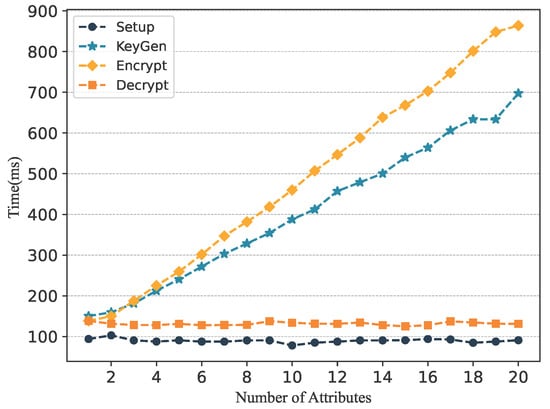
Figure 4.
The performance of ABE is affected by the number of attributes.
The experiment fixed the data length (1 kB) and gradually increased the attribute set size . The average computation time of the KeyGen, Encryption, and Decryption was tested. The experimental results are shown in Figure 5.
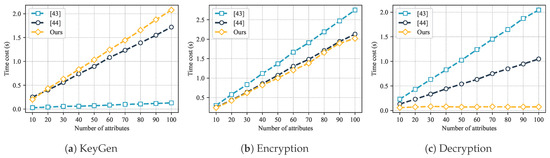
Figure 5.
Comparison of computational overhead of different ABE schemes: (a) KeyGen; (b) Encryption; (c) Decryption [43,44].
The results show that as the number of attributes increases, the computational overhead of each stage showed a linear upward trend. However, the growth rate of GeoCross in Encryption and Decryption operations is significantly lower than [45,46]. During the Encryption stage, the encryption time of GeoCross increased with the number of attributes, but the overall time consumption was reduced about and compared to [45] and [46], respectively. During the Decryption stage, GeoCross’s decryption process exhibits a significant advantage when the number of attributes is large. These experimental results are consistent with the theoretical analysis.
6.3. Communication Overhead
In GeoCross, cross-chain communication overhead comes from two aspects: the cross-chain overhead caused by granting authorization through the relay blockchain, and the overhead of establishing cross-chain proxies and relay forwarding. To obtain more realistic evaluation results, we simulated the cross-chain interaction process in a multi-chain environment to evaluate the cross-chain performance.
We analyzed the communication overhead incurred by cross-chain authorization through the Relay Chain. In GeoCross, cross-chain authorization is accomplished by collaborative blockchains using cross-chain contracts. The upload function and access request function within these contracts are key functions for cross-chain interaction and the source of communication overhead and latency. upload function is an invoke operation, requiring an execute-order-validate process, which increases latency in cross-chain communication and limits the efficiency of cross-chain authorization. This means the throughput of upload function determines the lower bound on cross-chain communication. The access request function does not require ordering, their throughput and latency are less affected by performance, determining the upper bound on cross-chain communication. Experimental results are shown in Figure 6. For the upload function, when the sending rate is below 200 tps, the Relay Chain’s throughput increases linearly with the sending rate, with average latency between 100 and 300 ms. When the sending rate exceeds 200 tps, throughput stabilizes at this level, while latency increases, indicating that the system is approaching its threshold. For access request function, the Relay Chain does not require consensus, resulting in better throughput performance than upload function. When the sending rate is within the range of 0–400 tps, the throughput maintains a linear relationship with the sending rate, with an average latency of approximately 10 ms. When the rate exceeds 400 tps, the system latency increases rapidly, the performance reaches a bottleneck. GeoCross offers an average latency of 10–20 ms for cross-chain read operations and 100–300 ms for cross-chain write operations, which satisfies the non-real-time but fast-response business requirements in geological operations.
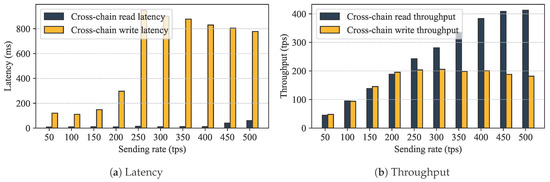
Figure 6.
Cross-chain communication performance evaluation: (a) latency; (b) throughput.
To further verify the performance of cross-chain data sharing, we set up two types of cross-chain data sharing scenarios: one-to-one unidirectional and many-to-one unidirectional. The cross-chain transaction load was set to 500, 1000, and 2000 transactions, and the sending rate range was 50–450 tps (the system reached the performance threshold when it exceeded 400 tps). We tested the actual performance of the GeoCross. The experimental results are shown in Figure 7.
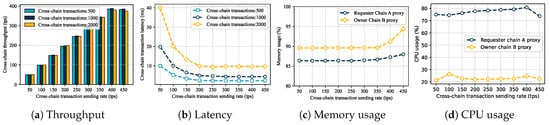
Figure 7.
Cross-chain data sharing performance evaluation.
One-to-one unidirectional. A Requester Chain (Provincial Bureau Chain) was designed to initiate access requests to the Owner Chain (Geoscience Institute Chain). The experimental results are shown in Figure 7. Cross-chain transaction throughput reached a system bottleneck at around 390 tps. When the sending rate was below 400 tps, the throughput increased linearly with the rate, slightly decreasing after exceeding the threshold. Cross-chain latency was high at low throughput levels, gradually decreasing as throughput increased. When the sending rate was too high, latency increased significantly. During the cross-chain requests, the Provincial Bureau Chain requests data from the Geoscience Institute Chain to perform write operations, resulting in higher CPU usage than the Geoscience Institute Chain requires for read operations. Conversely, the Geoscience Institute Chain’s memory usage increases when performing read operations. Overall memory and CPU usage remain stable as throughput increases, indicating manageable system resource consumption.
Many-to-one unidirectional. Multiple Requester Chains (Povincial Bureau Chains) were designed to simultaneously initiate access requests to the Owner Chain (Geoscience Institute Chain). The experimental results are shown in Figure 8. When the sending rate reached 400 tps, the system throughput was about 1550 tps, demonstrating the architecture’s excellent scalability with multi-chain access. As throughput increased, cross-chain relay latency stabilized, but increased after exceeding a threshold. Resource consumption for nodes in multi-requester chains was similar to the single chain. However, the Geoscience Institute Chain needs to respond to multiple requests simultaneously, increasing its memory and CPU usage and becoming one of the performance bottlenecks.
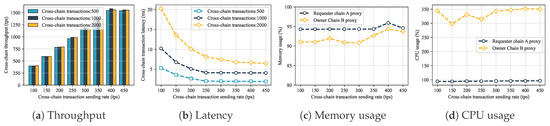
Figure 8.
Cross-chain data sharing performance evaluation.
To evaluate the communication performance of the proposed scheme, we further designed a relay node-based cross-chain interaction mechanism and incorporated two mainstream cross-chain frameworks, WeCross [22] and BitXHub [19], for comparative analysis. Similar to our design, the relay-node approach also requires reading and writing operations on functional contracts. However, its key limitation lies in the inability of relay nodes to persist with cross-chain transaction data; thus, cross-chain communication must be executed in real time. As a result, the performance ceiling of relay-based cross-chain interaction is determined by write-operation throughput. Due to the higher network complexity and consensus overhead of the service chain, the write throughput is approximately 140 tps. Using identical data payloads for cross-chain interaction, the performance comparison of the four schemes is shown in Figure 9. The results indicate that GeoCross achieves a higher performance upper bound than the mature cross-chain solutions WeCross and BitXHub, as well as the relay node scheme. Moreover, its lower-bound performance also exceeds that of BitXHub and the relay-node approach. Therefore, we conclude that the proposed scheme is capable of meeting the requirements of geological data sharing.
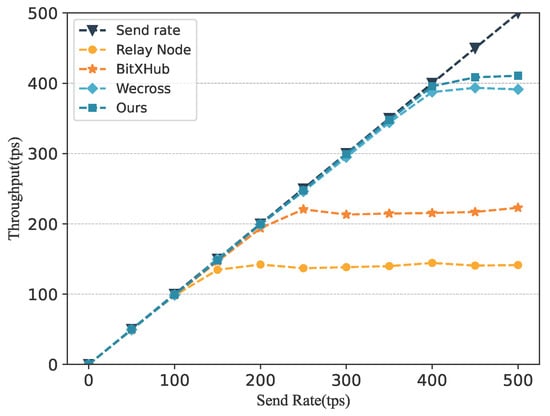
Figure 9.
The comparison of different cross-chain schemes on throughput.
To verify the architecture’s scalability, we further conducted experiments with increasing numbers of requester chains (2–20 chains). The results are shown in Figure 10. When the number of requester chains ranged from 2 to 16, the system throughput increased linearly. However, when the number of requester chains exceeded 16, the throughput decreased by approximately due to the bandwidth limitations in Relay Chain. In multi-chain access scenarios, GeoCross can achieve a total cross-chain throughput of approximately 1550 tps, which can satisfy the business scenarios where multiple provincial geological bureaus and research institutes simultaneously access cross-chain data.
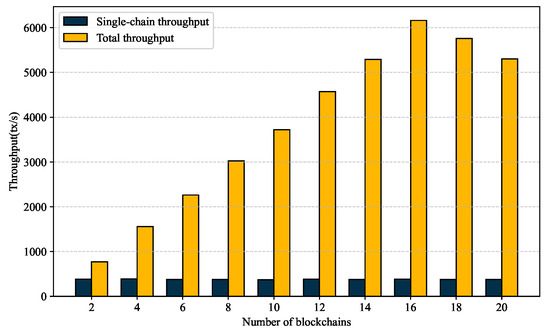
Figure 10.
Impact of the number of requester chains on throughput.
Experimental results demonstrate that GeoCross exhibits excellent performance stability and scalability in both one-to-one and many-to-one cross-chain data sharing scenarios. The system maintains high throughput and low latency under high concurrency conditions. The system is capable of satisfying the needs of large-scale geological data sharing scenarios.
7. Conclusions
This paper proposes GeoCross, a secure and privacy-preserving geological data sharing scheme supporting cross-heterogeneous blockchains. By coordinating hierarchical authorization, privacy-aware verification, and trusted relay selection, this scheme demonstrates that distributed geological data can be shared without disclosing sensitive information or relying on centralized trust. The system can meet the practical needs of information exchange between geological systems and supports controlled collaboration in multi-chain environments. Security analysis and experimental evaluation show that GeoCross maintains stable performance under various workloads and real-world geological data sharing environments, making it suitable for practical applications such as inter-institutional data collaboration.
However, GeoCross still has some limitations. It still relies on trusted initialization involving a central authority and property authorities, which may limit large-scale deployment. Furthermore, while Groth16 ensures efficient verification, its proof generation overhead and fixed circuit structure reduce flexibility in handling heterogeneous or dynamic geological data. Future work will explore decentralized or threshold-based authorization structures, scalable or transparent zero-knowledge proof frameworks, and large-scale evaluation in real-world geological information systems. These improvements aim to further enhance GeoCross’s scalability, adaptability, and trust decentralization capabilities, enabling its wider application in complex, data-intensive geological environments.
Author Contributions
Conceptualization, L.L. and B.F.; methodology, L.L.; software, B.F.; validation, L.L. and P.J.; formal analysis, P.J.; investigation, B.F.; resources, B.F.; data curation, B.F.; writing—original draft preparation, L.L.; writing—review and editing, L.L. and P.J.; visualization, P.J.; supervision, B.F.; project administration, P.J.; funding acquisition, B.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research work is supported by Deep Earth Probe and Mineral Resources Exploration—National Science and Technology Major Project (Grant No.2025ZD1008502) and Development of Capabilities in Deep Precision Detection Equipment and Imaging Technology (Grant No.AS2025P02).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding authors.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zhang, G.; Liu, X.; Zheng, F.; Sun, Y.; Liu, G. Geological disaster information sharing based on internet of things standardization. Environ. Earth Sci. 2024, 83, 148. [Google Scholar] [CrossRef]
- Onifade, M.; Adebisi, J.A.; Zvarivadza, T. Recent advances in blockchain technology: Prospects, applications and constraints in the minerals industry. Int. J. Min. Reclam. Environ. 2024, 38, 497–533. [Google Scholar] [CrossRef]
- Tenopir, C.; Christian, L.; Allard, S.; Borycz, J. Research data sharing: Practices and attitudes of geophysicists. Earth Space Sci. 2018, 5, 891–902. [Google Scholar] [CrossRef]
- Bertrand, Y.A.; Davy, A.M.P.; Edgard, N.; Samuel, O. A blockchain based platform to secure and track natural resource transactions in the central african republic. In Proceedings of the 2025 International Conference on Artificial Intelligence, Computer, Data Sciences and Applications (ACDSA), Antalya, Türkiye, 7–9 August 2025; pp. 1–6. [Google Scholar]
- Li, H.; Fu, D.; Yang, M.; Lin, S.; Zongzhong, S.; Liu, W.J.; Hu, Q. Research on improving the quality of groundwater self-monitoring via blockchain technology. Environ. Impact Assess. Rev. 2025, 112, 107811. [Google Scholar] [CrossRef]
- Ren, K.; Ho, N.-M.; Loghin, D.; Nguyen, T.-T.; Ooi, B.C.; Ta, Q.-T.; Zhu, F. Interoperability in blockchain: A survey. IEEE Trans. Knowl. Data Eng. 2023, 35, 12750–12769. [Google Scholar] [CrossRef]
- Belchior, R.; Vasconcelos, A.; Guerreiro, S.; Correia, M. A survey on blockchain interoperability: Past, present, and future trends. ACM Comput. Surv. (CSUR) 2021, 54, 1–41. [Google Scholar] [CrossRef]
- Augusto, A.; Belchior, R.; Correia, M.; Vasconcelos, A.; Zhang, L.; Hardjono, T. Sok: Security and privacy of blockchain interoperability. In Proceedings of the 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–23 May 2024; pp. 3840–3865. [Google Scholar]
- Wang, G.; Wang, Q.; Chen, S. Exploring blockchains interoperability: A systematic survey. ACM Comput. Surv. 2023, 55, 1–38. [Google Scholar] [CrossRef]
- Back, A.; Corallo, M.; Dashjr, L.; Friedenbach, M.; Maxwell, G.; Miller, A.; Poelstra, A.; Timón, J.; Wuille, P. Enabling Blockchain Innovations with Pegged Sidechains. 2014, Volume 72, pp. 201–224. Available online: https://scispace.com/papers/enabling-blockchain-innovations-with-pegged-sidechains-3dfarg8fby (accessed on 22 October 2014).
- Singh, A.; Click, K.; Parizi, R.M.; Zhang, Q.; Dehghantanha, A.; Choo, K.K.R. Sidechain technologies in blockchain networks: An examination and state-of-the-art review. J. Netw. Comput. Appl. 2020, 149, 102471. [Google Scholar] [CrossRef]
- Yin, Z.; Zhang, B.; Xu, J.; Lu, K.; Ren, K. Bool network: An open, distributed, secure cross-chain notary platform. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3465–3478. [Google Scholar] [CrossRef]
- Sun, Y.; Yi, L.; Duan, L.; Wang, W. A decentralized cross-chain service protocol based on notary schemes and hash-locking. In Proceedings of the 2022 IEEE International Conference on Services Computing (SCC), Barcelona, Spain, 11–15 July 2022; pp. 152–157. [Google Scholar]
- Herlihy, M. Atomic Cross-Chain Swaps. In Proceedings of the 2018 ACM Symposium on Principles of Distributed Computing, Egham, UK, 23–27 July 2018; pp. 245–254. [Google Scholar]
- Zamyatin, A.; Harz, D.; Lind, J.; Panayiotou, P.; Gervais, A.; Knottenbelt, W. Xclaim: Trustless, interoperable, cryptocurrency-backed assets. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–22 May 2019; pp. 193–210. [Google Scholar]
- Guo, Y.; Xu, M.; Cheng, X.; Yu, D.; Qiu, W.; Qu, G.; Wang, W.; Song, M. zkCross: A novel architecture for Cross-Chain Privacy-Preserving auditing. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 6219–6235. [Google Scholar]
- Wood, G. Polkadot: Vision for a heterogeneous multi-chain framework. White Pap. 2016, 21, 4662. [Google Scholar]
- Kwon, J.; Buchman, E. Cosmos whitepaper. A Netw. Distrib. Ledgers 2019, 27, 1–32. [Google Scholar]
- Ye, S.; Wang, X.; Xu, C.; Sun, J. Bitxhub: Side-relay chain based heterogeneous blockchain interoperable platform. Comput. Sci. 2020, 47, 294–302. [Google Scholar]
- Westerkamp, M.; Eberhardt, J. zkrelay: Facilitating sidechains using zksnark-based chain-relays. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 16–18 June 2020; pp. 378–386. [Google Scholar]
- Tian, H.; Xue, K.; Luo, X.; Li, S.; Xu, J.; Liu, J.; Zhao, J.; Wei, D.S.L. Enabling cross-chain transactions: A decentralized cryptocurrency exchange protocol. IEEE Trans. Inf. Forensics Secur. 2021, 16, 3928–3941. [Google Scholar] [CrossRef]
- Ye, S.; Wang, X.; Xu, C.; Sun, J. Wecross Technical White Paper Blockchain Cross-Chain Collaboration Platform. Available online: https://wecross.readthedocs.io/zh-cn/dev/docs/introduction/introduction.html (accessed on 19 February 2020).
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Hu, Y. Hyperservice: Interoperability and programmability across heterogeneous blockchains. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 549–566. [Google Scholar]
- Ghosh, B.C.; Bhartia, T.; Addya, S.K.; Chakraborty, S. Leveraging public-private blockchain interoperability for closed consortium interfacing. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications, Virtually, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Jiang, P.; Zhu, J.; Zhu, L. Balancing privacy and regulation of cross-chain transaction systems via sok-assisted policy enhancement. IEEE Trans. Inf. Forensics Secur. 2024, 19, 5620–5629. [Google Scholar]
- Shao, S.; Chen, F.; Xiao, X.; Gu, W.; Lu, Y.; Wang, S.; Tang, W.; Liu, S.; Wu, F.; He, J.; et al. Ibe-bciot: An ibe based cross-chain communication mechanism of blockchain in iot. World Wide Web 2021, 24, 1665–1690. [Google Scholar] [CrossRef]
- Duan, P.; Ma, Z.; Gao, H.; Tian, T.; Zhang, Y. Multi-authority attribute-based encryption scheme with access delegation for cross blockchain data sharing. IEEE Trans. Inf. Forensics Secur. 2024, 20, 323–337. [Google Scholar] [CrossRef]
- Xie, T.; Zhang, J.; Cheng, Z.; Zhang, F.; Zhang, Y.; Jia, Y.; Boneh, D.; Song, D. zkbridge: Trustless cross-chain bridges made practical. arXiv 2022, arXiv:2210.00264. [Google Scholar]
- Groth, J. On the size of pairing-based non-interactive arguments. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2016; pp. 305–326. [Google Scholar]
- Li, M.; Fu, J.; Li, L.; Wang, X.-D.; Chen, A.-S.; Wang, G.-M. Geoscience data sharing from the perspective of blockchain. Geol. Resour. 2022, 31, 700–706. [Google Scholar]
- Li, Y.; Guo, J.; Wu, A. Feasibility analysis of applying blockchain technology in geoscience data sharing. Remote Sens. Technol. Appl. 2020, 35, 759–766. [Google Scholar]
- Zhou, Y.; Liu, N.; Chen, C.; Yang, W. Opening a new era of geological applications based on blockchain technology. Geol. Bull. China 2020, 39, 1–6. [Google Scholar]
- Razzaq, A.; Mohsan, S.A.H.; Ghayyur, S.A.K.; Alsharif, M.H.; Alkahtani, H.K.; Karim, F.K.; Mostafa, S.M. Blockchain-enabled decentralized secure big data of remote sensing. Electronics 2022, 11, 3164. [Google Scholar] [CrossRef]
- Zhang, F.; Wang, Z.; Guo, R.; Qu, G. Earth observation data provenance: A blockchain-based solution. IEEE Trans. Ind. Inform. 2024, 20, 9548–9556. [Google Scholar] [CrossRef]
- Chafiq, T.; Rida, A.; Fadil, A.; Mohammed, O. Investigating the potential of blockchain technology for geospatial data sharing: Opportunities, challenges, and solutions. Geomatica 2024, 76, 100026. [Google Scholar] [CrossRef]
- Aufaristama, M. Use case of non-fungible tokens (nfts): A blockchain approach for geological data dissemination. J 2025, 8, 1. [Google Scholar] [CrossRef]
- Agarwal, P.K.; Chadha, A.; Ghosh, B.C.; Ghosh, S.K.; Chakraborty, S. Geoblocks: Trustless geospatial data sharing with accountability and decentralized access control. In Proceedings of the 2024 6th Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Berlin, Germany, 9–11 October 2024; pp. 1–9. [Google Scholar]
- Wu, J.; Gan, W.; Chao, H.-C.; Yu, P.S. Geospatial big data: Survey and challenges. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2024, 17, 17007–17020. [Google Scholar] [CrossRef]
- Zhou, G.; Wang, X.; Chen, W.; Li, X.; Chen, Z. Realization and application of geological cloud platform. Big Earth Data 2020, 4, 464–478. [Google Scholar] [CrossRef]
- Li, W.; Xue, K.; Xue, Y.; Hong, J. Tmacs: A robust and verifiable threshold multi-authority access control system in public cloud storage. IEEE Trans. Parallel Distrib. Syst. 2015, 27, 1484–1496. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. A blockchain-based access control scheme with multiple attribute authorities for secure cloud data sharing. J. Syst. Archit. 2021, 112, 101854. [Google Scholar] [CrossRef]
- Xiong, H.; Huang, X.; Yang, M.; Wang, L.; Yu, S. Unbounded and efficient revocable attribute-based encryption with adaptive security for cloud-assisted internet of things. IEEE Internet Things J. 2022, 9, 3097–3111. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Wang, M.; Cao, Z.; Dong, X.; Du, R.; Chen, J. Decentralized multi-authority kp-abe scheme without bilinear pairings. IEEE Internet Things J. 2024, 12, 726–738. [Google Scholar] [CrossRef]
- Chen, S.; Li, J.; Zhang, Y.; Han, J. Efficient revocable attribute-based encryption with verifiable data integrity. IEEE Internet Things J. 2023, 11, 10441–10451. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).