Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments
Abstract
1. Introduction
- A brief vehicular network background is presented.
- The existing inter- and intra-vehicular network communication datasets are introduced.
- A detailed taxonomy of possible intra-vehicular and inter-vehicular communication dataset categories is proposed.
- A guide to selecting suitable vehicular network security datasets for research needs is provided.
2. Existing Surveys on Vehicular Networks Datasets
3. Vehicular Networks: Background
3.1. Vehicular Networks Environments
3.2. Vehicular Network Architecture
3.3. Communication Layer
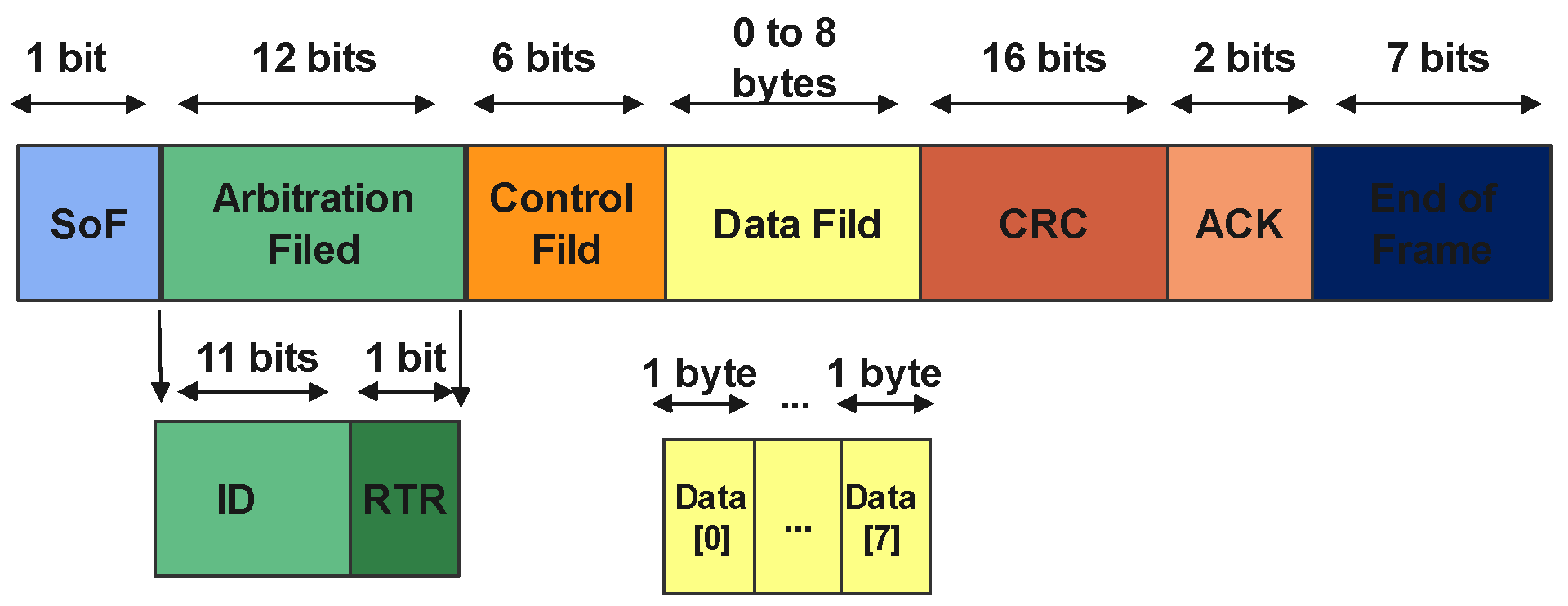
3.3.1. Intra-Vehicular Communication Protocols
3.3.2. Inter-Vehicular Communication
3.4. Vehicular Network Sensors Used for Data Collection
- In-vehicle sensors: In-vehicle sensors are located within the car and measure various aspects of a vehicle’s performance, such as acceleration, braking, and impacts, using accelerometers [53]. Gyroscopes measure a vehicle’s orientation and movement, while ABS sensors detect wheel lockup during braking. Additionally, engine speed sensors measure the engine’s rotational speed, while lane departure warning sensors monitor the vehicle’s position within a lane. Blind spot monitor sensors, another type of in-vehicle sensor, detect the blind spots of other vehicles in the car.
- Road Sensors: Road sensors are located on the road and measure traffic and environmental conditions to improve vehicular security [54]. Road sensors include traffic cameras that capture images of traffic flow, traffic light sensors that detect the presence of vehicles at intersections, and weather sensors that measure environmental conditions such as temperature and precipitation. In addition, road surface sensors detect road surface conditions such as temperature and friction, while pedestrian sensors detect the presence of pedestrians at crosswalks. These sensors work together to generate datasets that can improve the safety of drivers, passengers, and pedestrians by detecting hazardous conditions and warning drivers to take caution. In summary, in-vehicle and road sensors are crucial components of vehicular security. Their data are essential in creating datasets that can improve the safety of vehicles on the road.
3.5. Vehicular Network Security Challenges
4. Intra-/Intra-Vehicular Communication Datasets for Vehicular Network Security: Taxonomy
- Objective of the dataset: We list the dataset’s goal and usability aspects. There are four significant usage objectives in vehicular network communication datasets: datasets for intrusion detection, datasets for misbehavior detection, datasets for vehicle trajectory prediction, and datasets for traffic scenario analysis.
- Data Nature: We highlight the general nature of the data used, which mainly belong to two types: real data from real-life scenarios and a simulated dataset, named “synthetic”, from the simulation frameworks.
- Data Format: We describe all of the existing data structures within the database. There are different types, including comma-separated values (CSV)s, JavaScript Object Notation (JSON), and image format. In addition, various datasets may encompass different types of data or multi-formats in one global file.
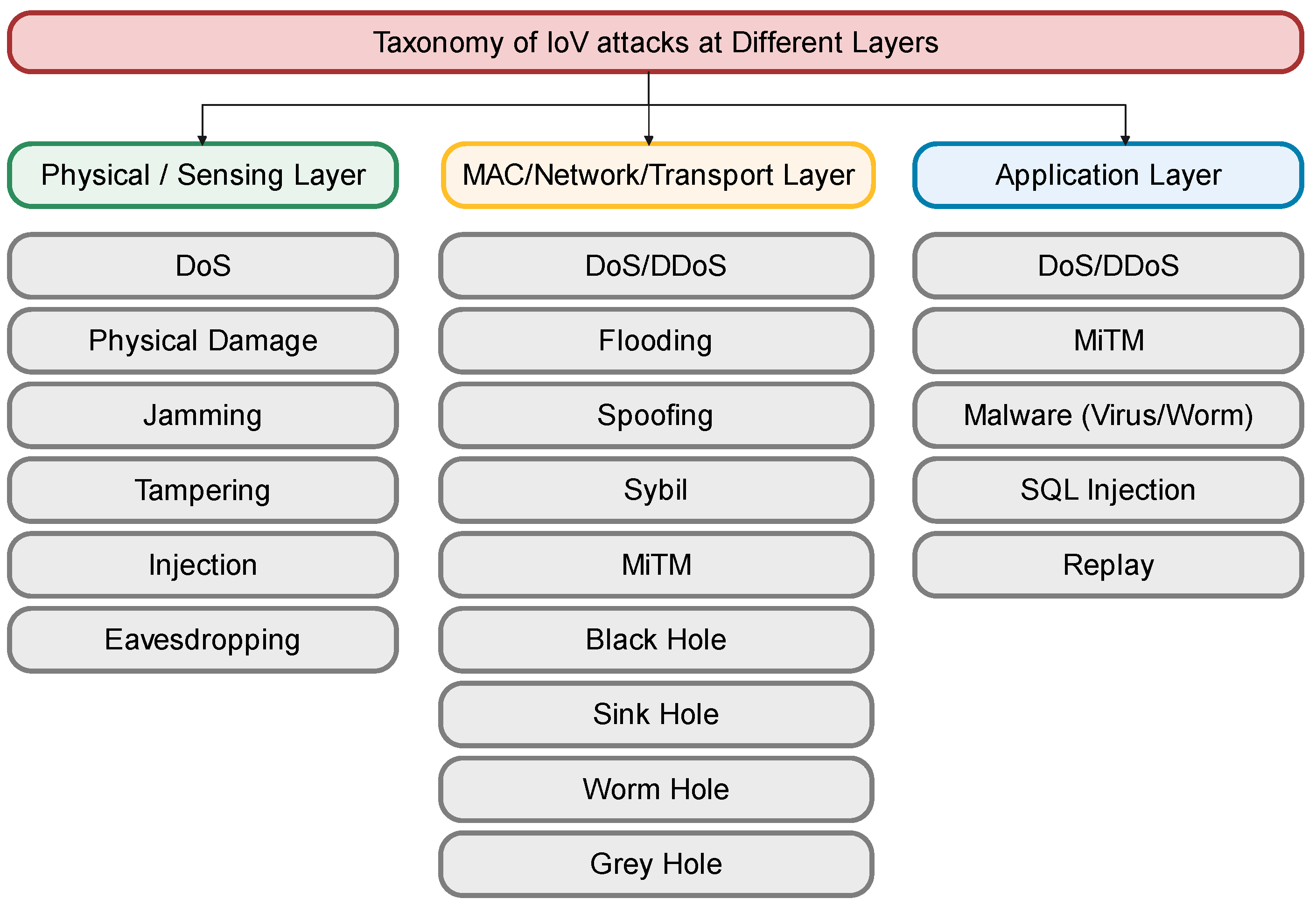
- Cyber Threats: We discuss various types of attacks in three major sectors, including all possible attacks in inter-vehicular, intra-vehicular, and hybrid communications.
- Communication Types: We describe three types of communications: V2X, V2V, and V2I. These three communication types are the most prone to connectivity in vehicular network communication links. They represent an easy medium between the vehicle and the attacker, so there are different datasets for vehicular network communication security for all three communications types.
- Communication Protocols: We list the different serial port communication protocols in the existing datasets, including DSRC, IEEE 802.11 g, 5G(C-V2X), AODV, WI-FI, and ARP.
5. Inter-Vehicular Communication Datasets
5.1. VeReMi Dataset
5.2. VeReMi Extension Dataset
5.3. NGSIM Datasets
5.4. PeMS Dataset
5.5. HighD Dataset
5.6. Warrigal Dataset
5.7. The DeepSense 6G Dataset
5.8. VDoS-LRS Dataset
5.9. Iqbal’s Dataset
5.10. VDDD Dataset
5.11. Synthetic Datasets Generation for VANET Intrusion Detection
6. Intra-Vehicular Communication Datasets
6.1. Car-Hacking Dataset
6.2. OTIDS Dataset
6.3. Survival Dataset
6.4. SynCAN
6.5. TUe v2 Dataset
6.6. ORNL Dynamometer CAN Intrusion Dataset
6.7. CrySyS Dataset
6.8. SIMPLE Dataset
6.9. Bi’s Dataset
7. Potential Features Used in Vehicular Datasets for Attack Detection
7.1. Inter-Vehicular Features
- Vehicle Dynamics and Positioning: This category explores the core aspects of vehicular motion, encompassing GPS coordinates, speed, acceleration, and directional information. Such data are indispensable for deciphering vehicle behavior and analyzing movement patterns on the road. For instance, the HighD dataset is exemplary in this context. It offers a wide range of information with its detailed vehicle trajectories, speeds, and acceleration data, providing deep insights into how vehicles move and interact on highways.
- Temporal Data: Temporal data capture the chronological aspects of vehicular movements and events. They include critical timestamps of various events and the durations of specific activities or states. Data of this type are instrumental in understanding and analyzing temporal patterns and sequences over time. A notable example is the VDDD dataset, which includes event time and previous event time, allowing researchers to analyze the sequences and durations of events in a detailed manner.
- Vehicle Identification and Characteristics: This type of feature is essential for distinguishing and characterizing vehicles. It includes data on vehicle types, physical attributes, and unique identifiers. Such information is fundamental for classifying vehicles and conducting a detailed analysis of vehicle-specific behavior. The NGSIM dataset, for example, provides vehicle identification numbers and vehicle types, enabling a comprehensive study of various vehicle behaviors.
- Traffic and Congestion Analysis: In this class, the focus is on assessing traffic flow, volume, and congestion. Features include vehicle counts, traffic density measurements, and analyses of peak traffic periods. These features are vital for understanding and managing traffic congestion. The PeMS dataset, for instance, offers rich data on traffic volume, flow rate, and traffic density, which are crucial for comprehensive traffic congestion analysis.
- Network and Communication Data: This category encompasses data related to the communication networks within vehicular systems. It includes information about data packet transmissions and metrics evaluating network performance. For example, the VDoS-LRS dataset is rich in network data, including detailed metrics like packet sizes, throughput, and packet transmission times, which are key to understanding vehicular communication networks.
- Sensor and Device Data: Sensor data involve readings from various devices installed in or around vehicles, such as cameras, GPS, and radar. This data category is increasingly important for environment sensing and enabling advanced vehicle functionalities. The DeepSense 6G dataset, with its inclusion of GPS data and radar measurements, is a prime example, offering crucial data for the development and enhancement of advanced driver-assistance systems.
- Driver and Behavioral Data: This category provides insights into driver behavior and actions. It includes data on driver identification, as well as actions like turns or signal usage. For instance, the Warrigal dataset includes data such as instantaneous speed and turn information, reflecting various aspects of driver behavior in a detailed manner.
- Safety and Incident Reporting: Safety metrics and incident data are key to understanding the safety aspects of vehicular travel. This includes information on vehicle safety systems and reports of road incidents. The PeMS dataset, for example, contributes significantly in this area with its incident reports that provide information on road accidents or construction work affecting traffic flow.
- Advanced Data Processing and Analysis: Features under this category include noise-added data for robustness testing and advanced signal processing for sophisticated data analysis. The VeReMi and the VeReMi extension exemplify this category with features like and , which introduce artificial noise to positional and speed data, thereby enabling the testing of algorithms under varied and challenging conditions.
7.2. Intra-Vehicular Features
- Timestamp: This feature records the exact moment when a data point is logged, providing a temporal reference that is crucial for tracking the sequence and timing of events within the vehicle’s network.
- CAN ID: This identifier is required for distinguishing the myriad types of messages and commands transmitted across the vehicle’s network. It is essential to categorize and understand the different communications occurring within the vehicle’s systems.
- Data Length Code (DLC): Representing the length of the data field in a message, this feature is key to understanding the size and format of the transmitted data, giving insight into the complexity and nature of the messages.
- DATA[0] to DATA[7]: These data bytes form the core content of the CAN message. Each byte, up to eight in total, can carry crucial information ranging from sensor outputs, like speed or temperature readings, to control commands directed at various vehicle electronic components.
8. A Guide to Selecting Suitable Vehicular Datasets Depending on the Research Requirements
- Attack-Type Selection: Researchers should carefully consider the metrics and objectives of their study when choosing a dataset for research on IoV attacks. This includes the types of attacks involved in the dataset and whether to use a single-attack or multi-attack dataset. A single attack dataset would focus on a particular attack type, such as DoS (e.g., VDoS-LRS Dataset, VDDD Dataset). This dataset helps analyze a specific countermeasure’s efficacy or assess a certain attack’s impact on a network. On the other hand, a multi-attack dataset includes representations of different types of attacks and is effective for assessing the network’s resilience to a range of attack scenarios. These datasets include VeReMi/VeReMi Extention Datasets, Iqbal’s Dataset, Synthetic Dataset, Car-Hacking Dataset, OTIDS dataset, Survival Dataset, CrySyS Dataset, SynCAN Dataset, TU/e v2 Dataset, ORNL Dataset, SIMPLE Dataset, and BI Dataset. The research objectives and the threat environment of vehicle networks should guide the selection of attack types. For instance, researchers can choose to concentrate on attacks that exploit vulnerabilities in certain communication protocols or on attacks that target the network’s physical components. In addition, they can take into account the severity and frequency of attacks in the real world and the possible effects on the safety and privacy of connected vehicles. There are other datasets without attacks like GSIM Dataset, PeMS Dataset, HighD Dataset, Warrigal Dataset, and DeeepSense 6G Dataset.
- Area-Type Selection: IoV researchers looking for security datasets should consider the type of area that the dataset is focused on. The area type can be divided into three main categories: rural, highway, and urban. First, rural areas are less densely populated than urban areas, making them more challenging to secure. In this type, the researchers consider the usage of the VDoS-LRS Dataset. However, researchers can develop and test security mechanisms that are robust enough to ensure IoV security in various situations by simulating attacks in these areas. Accidents, collisions, and congestion are the primary concerns for highway areas. Therefore, the dataset (e.g., VeReMi Dataset, NGSIM Dataset, highD Dataset, VDDD Dataset, CrySyS Dataset, Bi Dataset, and SIMPLE Dataset), including information on traffic flow, accidents, and congestion levels, maybe the best fit for researchers interested in highway areas. Finally, the focus is on security threats like unauthorized vehicle access in urban areas. It is easier for an attacker to gain vehicle access in densely populated urban areas. For this type, there are multiple datasets used, like NGSIM Dataset, PeMS Dataset, Warrigal Dataset, DeepSense 6G Dataset, Iqbal’s Dataset, and Synthetic Dataset. In addition, the density of people and vehicles can make it easier for hackers to intercept and steal sensitive data, such as location and personal information.
- Simulator-based Selection: The simulators used to create a dataset can be an essential consideration when choosing a dataset for IoV security research. Different simulators may generate datasets with diverse properties, such as the size of the network, the number, and the types of attacks that can be simulated. There are various datasets whose usage adapts to these simulators. For example, sumo is adapted with VeReMi/VeReMi extension Dataset, Iqbal’s Dataset, and VD Dataset. In the same context, using a Raspberry Pi3, multiple datasets might be used, such as the Car-Hacking Dataset, the OTIDS Dataset, the TU/e v2 Dataset, and the BI Dataset. Therefore, while choosing a dataset, examining which simulator was used to produce the dataset and whether it suits the research objectives is essential. For example, to design and test a test security method using the Veins simulator, it can be beneficial to select a dataset that was generated using Veins as this can guarantee that the dataset is compatible with the simulator and that the results are more relevant to the research.
- Supervised/Unsupervised Datasets: Another essential factor when selecting an IoV security dataset is whether the dataset is supervised or unsupervised. A supervised dataset (including VeReMi /VeRemi Extension Dataset, NGSIM Dataset, and High Dataset) labels known attacks and patterns, allowing ML models to be trained to identify and react to these attacks. This dataset helps develop security mechanisms that require previous knowledge of attack patterns. On the other hand, unsupervised datasets (such as PeMS Dataset, Warrigal Dataset, and DeepSense 6G Dataset, among others) are without pre-labeled attack patterns and rely on ML models to recognize anomalies or deviations from normal behavior. These datasets are used to develop and test security models that detect previously unknown attacks.
- Accessibility and Documentation: Accessible and well-documented IoV security datasets are essential for researchers who want to perform experiments and assess various security techniques and approaches. A dataset that is accessible should be simple to obtain and use, with clear instructions on how to access and download it. A well-documented dataset should also give researchers specific information on the data, such as the types of attacks included, the vehicle types, and the communication protocols. A well-documented dataset should also contain information on the limitations of the dataset, including any assumptions or simplifications made during the development of the dataset. This information can assist researchers in understanding the dataset and its possible applications and limits. In addition, a well-documented dataset should provide instructions on adequately utilizing the dataset, such as preprocessing the data, choosing good evaluation metrics, and comparing results across studies.
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gyawali, S.; Xu, S.; Qian, Y.; Hu, R. Challenges and solutions for cellular based V2X communications. IEEE Commun. Surv. Tutor. 2020, 23, 222–255. [Google Scholar] [CrossRef]
- Fraiji, Y.; Azzouz, L.; Trojet, W.; Saidane, L. Cyber security issues of Internet of electric vehicles. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Khelil, A.; Soldani, D. On the suitability of device-to-device communications for road traffic safety. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Republic of Korea, 6–8 March 2014; pp. 224–229. [Google Scholar]
- Guille, C.; Gross, G. A conceptual framework for the vehicle-to-grid (V2G) implementation. Energy Policy 2009, 37, 4379–4390. [Google Scholar] [CrossRef]
- Karagiannis, G.; Altintas, O.; Ekici, E.; Heijenk, G.; Jarupan, B.; Lin, K.; Weil, T. Vehicular networking: A survey and tutorial on requirements, architectures, challenges, standards and solutions. IEEE Commun. Surv. Tutor. 2011, 13, 584–616. [Google Scholar] [CrossRef]
- Bernardini, C.; Asghar, M.; Crispo, B. Security and privacy in vehicular communications: Challenges and opportunities. Veh. Commun. 2017, 10, 13–28. [Google Scholar] [CrossRef]
- Haddaji, A.; Ayed, S.; Fourati, L. Artificial Intelligence techniques to mitigate cyber-attacks within vehicular networks: Survey. Comput. Electr. Eng. 2022, 104, 108460. [Google Scholar] [CrossRef]
- Sharma, N.; Chauhan, N.; Ch, N. Security challenges in Internet of Vehicles (IoV) environment. In Proceedings of the 2018 First International Conference on Secure Cyber Computing and Communication (ICSCCC), Jalandhar, India, 15–17 December 2018; pp. 203–207. [Google Scholar]
- Haddaji, A.; Ayed, S.; Fourati, L. A Transfer Learning Based Intrusion Detection System for Internet of Vehicles. In Proceedings of the 2023 15th International Conference on Developments In ESystems Engineering (DeSE), Baghdad & Anbar, Iraq, 9–12 January 2023; pp. 533–539. [Google Scholar]
- Boualouache, A.; Engel, T. A survey on machine learning-based misbehavior detection systems for 5g and beyond vehicular networks. IEEE Commun. Surv. Tutor. 2023, 25, 1128–1172. [Google Scholar] [CrossRef]
- Alalwany, E.; Mahgoub, I. Security and Trust Management in the Internet of Vehicles (IoV): Challenges and Machine Learning Solutions. Sensors 2024, 24, 368. [Google Scholar] [CrossRef] [PubMed]
- Boualouache, A.; Ghamri-Doudane, Y. Zero-X: A Blockchain-Enabled Open-Set Federated Learning Framework for Zero-Day Attack Detection in IoV. IEEE Trans. Veh. Technol. 2024, 1–16. [Google Scholar]
- Ahmad, J.; Zia, M.U.; Naqvi, I.H.; Chattha, J.N.; Butt, F.A.; Huang, T.; Xiang, W. Machine Learning and Blockchain Technologies for Cybersecurity in Connected Vehicles; Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery; Wiley: Hoboken, NJ, USA, 2024; Volume 14, p. e1515. [Google Scholar]
- Sun, P.; Boukerche, A. Security enhancing method in vehicular networks by exploiting the accurate traffic flow prediction. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar]
- Swessi, D.; Idoudi, H. A comparative review of security threats datasets for vehicular networks. In Proceedings of the 2021 International Conference on Innovation and Intelligence For Informatics, Computing, and Technologies (3ICT), Zallaq, Bahrain, 29–30 September 2021; pp. 746–751. [Google Scholar]
- Vahidi, A.; Rosenstatter, T.; Mowla, N. Systematic Evaluation of Automotive Intrusion Detection Datasets. In Proceedings of the 6th ACM Computer Science In Cars Symposium, Ingolstadt Germany, 8 December 2022; pp. 1–12. [Google Scholar]
- Lee, S.; Choi, W.; Kim, I.; Lee, G.; Lee, D.H. A Comprehensive Analysis of Datasets for Automotive Intrusion Detection Systems. Comput. Mater. Contin. 2023, 76. [Google Scholar] [CrossRef]
- Mom, A.; Jan, S.U.; Ramzan, N. A systematic and comprehensive survey of recent advances in intrusion detection systems using machine learning: Deep learning, datasets, and attack taxonomy. J. Sens. 2023, 2023, 6048087. [Google Scholar]
- Heijden, R.; Lukaseder, T.; Kargl, F. Veremi: A dataset for comparable evaluation of misbehavior detection in vanets. In Security and Privacy in Communication Networks: 14th International Conference, SecureComm 2018, Singapore, 8–10 August 2018; Proceedings, Part I; Springer: Berlin/Heidelberg, Germany, 2018; pp. 318–337. [Google Scholar]
- Kamel, J.; Wolf, M.; Van Der Hei, R.; Kaiser, A.; Urien, P.; Kargl, F. Veremi extension: A dataset for comparable evaluation of misbehavior detection in vanets. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Transportation Federal Highway Administration. U. Next Generation Simulation (NGSIM). 2016. Available online: https://ops.fhwa.dot.gov/trafficanalysistools/ngsim.htm,urldate=2023-02-24 (accessed on 23 May 2024).
- Chen, C. Freeway Performance Measurement System (PeMS). Ph.D. Thesis, University of California, Berkeley, CA, USA, 2002. [Google Scholar]
- Krajewski, R.; Bock, J.; Kloeker, L.; Eckstein, L. The highd dataset: A drone dataset of naturalistic vehicle trajectories on german highways for validation of highly automated driving systems. In Proceedings of the 2018 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 2118–2125. [Google Scholar]
- Ward, J.; Worrall, S.; Agamennoni, G.; Nebot, E. The warrigal dataset: Multi-vehicle trajectories and v2v communications. IEEE Intell. Transp. Syst. Mag. 2014, 6, 109–117. [Google Scholar] [CrossRef]
- Alkhateeb, A.; Charan, G.; Osman, T.; Hredzak, A.; Morais, J.; Demirhan, U.; Srinivas, N. DeepSense 6G: A large-scale real-world multi-modal sensing and communication dataset. arXiv 2022, arXiv:2211.09769. [Google Scholar]
- Rahal, R.; Amara Korba, A.; Ghoualmi-Zine, N. Towards the development of realistic dos dataset for intelligent transportation systems. Wirel. Pers. Commun. 2020, 115, 1415–1444. [Google Scholar] [CrossRef]
- Iqbal, S.; Ball, P.; Kamarudin, M.; Bradley, A. Simulating Malicious Attacks on VANETs for Connected and Autonomous Vehicle Cybersecurity: A Machine Learning Dataset. In Proceedings of the 2022 13th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2022; pp. 332–337. [Google Scholar]
- Alhaidari, F.; Alrehan, A. A simulation work for generating a novel dataset to detect distributed denial of service attacks on Vehicular Ad hoc NETwork systems. Int. J. Distrib. Sens. Netw. 2021, 17, 15501477211000287. [Google Scholar] [CrossRef]
- Belenko, V.; Krundyshev, V.; Kalinin, M. Synthetic datasets generation for intrusion detection in VANET. In Proceedings of the 11th International Conference on Security of Information and Networks, Cardiff, UK, 10–12 September 2018; pp. 1–6. [Google Scholar]
- Seo, E.; Song, H.; Kim, H. GIDS: GAN based intrusion detection system for in-vehicle network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; pp. 1–6. [Google Scholar]
- Lee, H.; Jeong, S.; Kim, H. OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 57–5709. [Google Scholar]
- Han, M.; Kwak, B.; Kim, H. Anomaly intrusion detection method for vehicular networks based on survival analysis. Veh. Commun. 2018, 14, 52–63. [Google Scholar] [CrossRef]
- Hanselmann, M.; Strauss, T.; Dormann, K.; Ulmer, H. CANet: An unsupervised intrusion detection system for high dimensional CAN bus data. IEEE Access 2020, 8, 58194–58205. [Google Scholar] [CrossRef]
- Dupont, G.; Den Hartog, J.; Etalle, S.; Lekidis, A. Evaluation framework for network intrusion detection systems for in-vehicle can. In Proceedings of the 2019 IEEE International Conference on Connected Vehicles and Expo (ICCVE), Graz, Austria, 4–8 November 2019; pp. 1–6. [Google Scholar]
- Verma, M.; Iannacone, M.; Bridges, R.; Hollifield, S.; Kay, B.; Combs, F. Road: The real ornl automotive dynamometer controller area network intrusion detection dataset (with a comprehensive can ids dataset survey & guide). arXiv 2020, arXiv:2012.14600. [Google Scholar]
- Chiscop, I.; Gazdag, A.; Bosman, J.; Biczók, G. Detecting message modification attacks on the CAN bus with Temporal Convolutional Networks. arXiv 2021, arXiv:2106.08692. [Google Scholar]
- Foruheh, M.; Man, Y.; Gerdes, R.; Li, M.; Chantem, T. SIMPLE: Single-frame based physical layer identification for intrusion detection and prevention on in-vehicle networks. In Proceedings of the 35th Annual Computer Security Applications Conference, San Juan, PR, USA, 9–13 December 2019; pp. 229–244. [Google Scholar]
- Bi, Z.; Xu, G.; Xu, G.; Tian, M.; Jiang, R.; Zhang, S. Intrusion Detection Method for In-Vehicle CAN Bus Based on Message and Time Transfer Matrix. Secur. Commun. Netw. 2022, 2022, 2554280. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Ang, L.; Seng, K.; Ijemaru, G.; Zungeru, A. Deployment of IoV for smart cities: Applications, architecture, and challenges. IEEE Access 2018, 7, 6473–6492. [Google Scholar] [CrossRef]
- Uhlemann, E. Initial steps toward a cellular vehicle-to-everything standard [connected vehicles]. IEEE Veh. Technol. Mag. 2017, 12, 14–19. [Google Scholar] [CrossRef]
- Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A survey on vehicular cloud computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar] [CrossRef]
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of can bus security challenges. Sensors 2020, 20, 2364. [Google Scholar] [CrossRef] [PubMed]
- Sumorek, A.; Buczaj, M. New elements in vehicle communication “media oriented systems transport” protocol. Teka Kom. Motoryz. Energetyki Rol. 2012, 12, 275–279. [Google Scholar]
- Nalecz, A. Development and Validation of Light Vehicle Dynamics Simulation (LVDS); SAE Technical Paper; SAE: Warrendale, PA, USA, 1992. [Google Scholar]
- Huang, J.; Zhao, M.; Zhou, Y.; Xing, C. In-vehicle networking: Protocols, challenges, and solutions. IEEE Netw. 2018, 33, 92–98. [Google Scholar] [CrossRef]
- Cseh, C. Architecture of the dedicated short-range communications (DSRC) protocol. In Proceedings of the VTC’98. 48th IEEE Vehicular Technology Conference. Pathway To Global Wireless Revolution (Cat. No. 98CH36151), Ottawa, ON, Canada, 21 May 1998; Volume 3, pp. 2095–2099. [Google Scholar]
- Kenney, J. Dedicated short-range communications (DSRC) standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Sonis, V.; Soto, I.; Calderon, M.; Urueña, M. Vehicle to Internet communications using the ETSI ITS GeoNetworking protocol. Trans. Emerg. Telecommun. Technol. 2016, 27, 373–391. [Google Scholar] [CrossRef]
- Costantino, G.; De Vincenzi, M.; Matteucci, I. In-depth exploration of ISO/SAE 21434 and its correlations with existing standards. IEEE Commun. Stand. Mag. 2022, 6, 84–92. [Google Scholar] [CrossRef]
- Olivera, J.; Cortázar, I.; Pinart, C.; Los Santos, A.; Lequerica, I. VANBA: A simple handover mechanism for transparent, always-on V2V communications. In Proceedings of the VTC Spring 2009-IEEE 69th Vehicular Technology Conference, Barcelona, Spain, 26–29 April 2009; pp. 1–5. [Google Scholar]
- Fei, X.; Mahmassani, H.; Murray-Tuite, P. Vehicular network sensor placement optimization under uncertainty. Transp. Res. Part C Emerg. Technol. 2013, 29, 14–31. [Google Scholar] [CrossRef]
- Jo, K.; Chu, K.; Sunwoo, M. Interacting multiple model filter-based sensor fusion of GPS with in-vehicle sensors for real-time vehicle positioning. IEEE Trans. Intell. Transp. Syst. 2011, 13, 329–343. [Google Scholar] [CrossRef]
- Sun, Z.; Bebis, G.; Miller, R. On-road vehicle detection using optical sensors: A review. In Proceedings of the 7th International IEEE Conference on Intelligent Transportation Systems (IEEE Cat. No. 04TH8749), Washington, WA, USA, 3–6 October 2004; pp. 585–590. [Google Scholar]
- Raouf, I.; Khan, A.; Khalid, S.; Sohail, M.; Azad, M.; Kim, H. Sensor-Based Prognostic Health Management of Advanced Driver Assistance System for Autonomous Vehicles: A Recent Survey. Mathematics 2022, 10, 3233. [Google Scholar] [CrossRef]
- Sun, Y.; Wu, L.; Wu, S.; Li, S.; Zhang, T.; Zhang, L.; Xu, J.; Xiong, Y.; Cui, X. Attacks and countermeasures in the internet of vehicles. Ann. Telecommun. 2016, 72, 11. [Google Scholar] [CrossRef]
- Karim, S.; Habbal, A.; Chaudhry, S.; Irshad, A. Others Architecture, Protocols, and Security in IoV: Taxonomy, Analysis, Challenges, and Solutions. Secur. Commun. Netw. 2022, 2022, 1131479. [Google Scholar] [CrossRef]
- Zewdie, T.; Girma, A. An Evaluation framework for machine learning methods in detection of DoS and DDoS Intrusion. In Proceedings of the 2022 International Conference on Artificial Intelligence In Information and Communication (ICAIIC), Jeju Island, Republic of Korea, 21–24 February 2022; pp. 115–121. [Google Scholar]
- Benadla, S.; Merad-Boudia, O. The Impact of Sybil Attacks on Vehicular Fog Networks. In Proceedings of the 2021 International Conference on Recent Advances In Mathematics and Informatics (ICRAMI), Tebessa, Algeria, 21–22 September 2021; pp. 1–6. [Google Scholar]
- Alrefaei, F.; Alzahrani, A.; Song, H.; Alrefaei, S. A Survey on the Jamming and Spoofing attacks on the Unmanned Aerial Vehicle Networks. In Proceedings of the 2022 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 1–4 June 2022; pp. 1–7. [Google Scholar]
- Bagga, P.; Das, A.; Wazid, M.; Rodrigues, J.; Park, Y. Authentication protocols in internet of vehicles: Taxonomy, analysis, and challenges. IEEE Access 2020, 8, 54314–54344. [Google Scholar] [CrossRef]
- Samad, A.; Alam, S.; Mohammed, S.; Bhukhari, M. Internet of vehicles (IoV) requirements, attacks and countermeasures. In Proceedings of the 12th INDIACom; INDIACom-2018; 5th International Conference on “Computing For Sustainable Global Development” IEEE Conference, New Delhi, India, 14–16 March 2018; pp. 1–4. [Google Scholar]
- Tabassum, M.; Oliveira, A. Cyber-resilient Routing for Internet of Vehicles Networks during Black Hole Attack. Int. J. Wirel. Microw. Technol. 2022, 12, 1–14. [Google Scholar] [CrossRef]
- Abdul-Ghani, H.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar]
- Lampe, B.; Meng, W. Intrusion detection in the automotive domain: A comprehensive review. IEEE Commun. Surv. Tutorials. 2023, 25, 2356–2426. [Google Scholar] [CrossRef]
- Group, T. Eindhoven University of Technology. 2019. Available online: https://security1.win.tue.nl/doku.php?id=start (accessed on 23 May 2024).
- Lampe, B.; Meng, W. Can-train-and-test: A Curated CAN Dataset for Automotive Intrusion Detection. Comput. Secur. 2024, 140, 103777. [Google Scholar] [CrossRef]




| Abbreviation | Meaning |
|---|---|
| AI | Artificial Intelligence |
| ADUS | Archived Data User Service |
| BSM | Basic Safety Messages |
| CALM | Continuous Air-interface, Long and Medium range |
| CAN | Controller Area Network |
| CSV | comma-separated values |
| C-V2X | Cellular vehicle-to-everything |
| DL | Deep Learning |
| D2D | Device-to-Device |
| DSRC | Dedicated Short-Range Communication |
| ECUs | electronic control units |
| EDRs | Event Data Recorders |
| E/E | electrical and electronic |
| FCC | Federal Communications Commission |
| GN | GeoNetworking |
| HCRL | Human Centered Robotics Laboratory |
| IoT | Internet of Things |
| IoV | Internet of Vehicle |
| IETF | Internet Engineering Task Force |
| IDS | Intrusion Detection Systems |
| ITS | Intelligent Transportation Systems |
| LTE | Long-Term Evolution |
| LIN | Local Interconnect Network |
| ML | Machine Learning |
| OBU | onboard unit |
| OEMs | original equipment manufacturers |
| PeMS | Performance Measurement System |
| PSSCH | Physical Sidelink Shared Channels |
| QoS | Quality of Service |
| RCP | resource command processor |
| RSU | roadside units |
| SB-SPS | Sensing-Based Semi-Persistent Scheduling |
| TBs | Transport Blocks |
| TTC | Time to Collision |
| THW | Time Headway |
| V2B | Vehicle-to-Barrier |
| V2D | Vehicle-to-Driver |
| V2G | Vehicle-to-Grid |
| V2H | Vehicle-to-Home |
| V2I | Vehicle-to-Infrastructure |
| V2P | Vehicle-to-Pedestrian |
| V2R | Vehicle-to-Roadside |
| V2S | Vehicle-to-Sensors |
| V2V | Vehicle-to-Vehicle |
| V2X | Vehicle-to-Everything |
| VANETs | Vehicular ad-hoc networks |
| VCN | Vehicular Computing Networks |
| Study | Inter-Vehicular Datasets | Intra-Vehicular Datasets | Taxonomy | Recommnedation | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| VeReMi [19] | VeReMi Extension [20] | NGSIM [21] | PeMS [22] | highD [23] | Warrigal [24] | DeepSense 6G [25] | VDoS-LRS [26] | Iqbal’s Dataset [27] | VDDD [28] | Synthetic [29] | Car-Hacking [30] | OTIDS [31] | Survival [32] | SynCAN [33] | TU/e v2[34] | ORNL [35] | CrySyS [36] | SIMPLE [37] | Bi [38] | |||
| [14] | X | X | X | X | X | X | X | X | X | X | X | |||||||||||
| [15] | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | ||||||
| [16] | X | X | X | X | X | X | X | X | X | X | X | X | X | |||||||||
| [17] | X | X | X | X | X | X | X | X | X | X | ||||||||||||
| [18] | X | X | X | X | X | X | X | X | X | X | ||||||||||||
| Our Work | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X | X |
| Network Speed | Bandwidth | Topology | Max Supported Nodes | Advantages | Limitations |
|---|---|---|---|---|---|
| CAN | 25 Kbps–1 Mbps | Star, Ring, Linear bus | 30 | High reliability, low cost | Limited bandwidth, vulnerable to attacks |
| LIN | 25 Kbps–1 Mbps | Liner bus | 16 | Bus Low cost, low power | Limited data rate and distance |
| FlexRay | Up to 10 Mbps | Star, Linear bus, hybrid | 22 | High reliability, high bandwidth | Higher cost, limited interoperability |
| Ethernet | Up to 100 Mbps | Star, Linear bus | Depends on Switch ports | High bandwidth, scalable | Higher cost, high power consumption |
| MOST | Up to 150 Mbps | Ring | 64 | High bandwidth, low latency | Limited distance, higher cost |
| LVDS | Up to 3 Gbps | Point-to-point, multipoint | 2–3 | High data rate, low power, noise immunity | Shorter cable length, limited to simpler topologies |
| Attack Type | Target Layer | Primary Goal | Method of Attack | Potential Impact | Detection Difficulty | Attacker Sophistication Level | Attack Range | Persistence | Scalability | Required Access |
|---|---|---|---|---|---|---|---|---|---|---|
| DoS | Multiple | Disrupt service | Overloading requests | System failure | Medium | Low to Medium | Variable | Temporary | High | Network Access |
| Jamming | Physical | Block communication | Frequency interference | Data transmission blocked | Hard | Low to Medium | Local | Temporary | Low | Proximity |
| Injection | Multiple | Insert false data | Unauthorized data input | Misinformation | Medium | Medium | Variable | Varies | Medium | Network Access |
| Tampering | Physical | Alter system/data | Physical interference | Malfunctions | Easy | Low | Proximity | Persistent | Low | Physical Access |
| Eavesdropping | Physical | Intercept data | Passive data capture | Information theft | Hard | Low | Local | Varies | Low | Proximity |
| DDoS | Multiple | Disrupt service | Distributed sources | Service unavailability | Medium | Medium to High | Wide | Temporary | High | Remote Access |
| Following | Network | Track movements | Message monitoring | Stalking | Easy | Low | Local | Temporary | Low | Network Access |
| Sybil | Network | Subvert trust | Fake identities creation | Network unreliability | Medium | Medium | Wide | Varies | High | Network Access |
| Spoofing | Network | Masquerade identity | Impersonation | Unauthorized access | Medium | Medium | Variable | Temporary | Medium | Network Access |
| MiTM | Network | Intercept/alter data | Communication interception | Data manipulation | Hard | High | Local | Temporary | Low | Network Access |
| Black Hole | Network | Data disruption | Data packet dropping | Communication breakdown | Medium | Medium | Local | Temporary | Low | Network Access |
| Sink Hole | Network | Selective disruption | Selective packet dropping | Unreliable communication | Medium | Medium | Local | Temporary | Low | Network Access |
| Worm Hole | Network | Data tunneling | Tunnel creation | Security bypass | Hard | High | Wide | Persistent | Medium | Network Access |
| Grey Hole | Network | Partial disruption | Intermittent dropping | Unreliable reliability | Medium | Medium | Local | Varies | Medium | Network Access |
| Phishing | Application | Steal credentials | Deceptive communication | Financial loss | Medium | Low | Wide | Temporary | High | User Interaction |
| Malware | Application | Disrupt/Control system | Software installation | System damage | Medium | Medium to High | Variable | Persistent | High | User Interaction |
| Replay | Application | Unauthorized access | Data retransmission | Security bypass | Easy | Low | Local | Temporary | Low | Network Access |
| Dataset | Ref./Year | Objective | Attacks | Nature of Data | Number of Vehicles | Format | Label | Protocol |
|---|---|---|---|---|---|---|---|---|
| VeReMi | [19] 2018 | Misbehavior Detection | constant attacker, constant offset attacker, random attacker, random offset attacker, eventual stop attacker. | Synthetic | 225 | JSON | Yes | DSRC |
| VeReMi Extension | [20] 2020 | Misbehavior Detection | DoS, DoS Random, Data Replay, Disruptive, Eventual Stop, Traffic congestion Sybil | Synthetic | 2846 scenario 1, 1179 scenario 2, 7399 scenario 3 | JSON | Yes | DSRC |
| NGSIM | [21] 2016 | vehicle trajectory prediction | NA | Real | 9206 Vehicles, 8860 cars, 278 Trucks | Different Formats | Yes | NA |
| PeMS | [22] 2002 | Traffic Detection, Incident detection | NA | Real | 400,000 | NA | No | NA |
| highD | [23] 2018 | Vehicle trajectories | NA | Real | 110,000 Vehicles, 90,000 cars, 20,000 Trucks | CSV | Yes | NA |
| Warrigal | [24] 2014 | road mapping, driver intent prediction, collision avoidance | NA | Real | NA | CSV | No | NA |
| DeepSense6G | [25] 2022 | Blockage identification and prediction, object detection/classification | NA | Real | NA | Different Formats | No | NA |
| VDoS-LRS | [26] 2020 | Intrusion Detection | DoS | Real | 2 | NA | Yes | IEEE 802.11 g |
| Iqbal’sDataset | [27] | Misbehavior Detection | Replay attack, Bogus information attack | Synthetic | 5 | CSV | Yes | DSRC, 5G (C-V2X) |
| VDDD | [28] 2021 | Intrusion Detection | DDoS | Synthetic | 20 Vehicles in low traffic rate, 60 vehicles in high traffic rate | different formats | Yes | Ethernet, IEEE 802.11, |
| Synthetic | [29] 2018 | Intrusion Detection | DoS, DDoS Grayhole, Blackhole, Wormhole, Sybil | Synthetic | 30 (Vehicles and Hots) | NA | Yes | WiFi, IPv4 AODV, ARP |
| Dataset | Ref./Year | Objective | Attacks | Nature of Data | Format | Labeled Data | Protocol |
|---|---|---|---|---|---|---|---|
| Car-Hacking | [30] 2018 | Intrusion Detection | DoS, Fuzzy, Spoofing | Real | CSV | Yes | CAN protocol |
| OTIDS | [31] 2017 | Intrusion Detection | DoS, Fuzzy, Impersonation | Real | CSV | No | CAN protocol |
| Survival | [32] 2018 | Intrusion Detection | Flooding, Fuzzy, Malfunction | Real | CSV | Yes | CAN protocol |
| SynCAN | [33] 2019 | Intrusion Detection | Suspension, Fabrication, Masquerade | synthetic | CSV | No | CAN protocol |
| TU/e v2 | [34] 2019 | Intrusion Detection | DoS, Fuzzy, Diagnostic, Replay, Suspension | synthetic | CSV | No | CAN protocol |
| ORNL | [35] 2020 | Intrusion Detection | Masquerade, Fabrication targeted ID, Accelerator | Real | CSV | Yes | CAN protocol |
| CrySyS | [36] 2021 | Intrusion Detection | Plateau attack, Continuous change attack, Playback attack, Suppression attack, Flooding attack | Real data and synthetic attacks | CSV | No | CAN protocol, GPS |
| SIMPLE | [37] 2019 | Intrusion Detection | Dominant Impersonation, Complete Impersonation | Real | NA | Yes | CAN protocol |
| Bi | [38] 2022 | Intrusion Detection | Dos, Fuzzy, Ulterior Fuzzy, Replay | Real | NA | No | CAN protocol |
| Category | Feature | Metric Type | Description | Use Case |
|---|---|---|---|---|
| Vehicle Dynamics and Positioning | Lateral (X) and Longitudinal (Y) Coordinates | Coordinate Data | Position of the vehicle on the road | Traffic pattern analysis |
| Instantaneous Velocity | Speed Measurement | Speed of the vehicle at a given moment | Speed regulation enforcement | |
| Instantaneous Acceleration | Acceleration Rate | Rate at which vehicle speed changes | Driving behavior analysis | |
| Temporal Data | Timestamps | Time Duration | Exact date and time for data capture | Event sequencing |
| Duration | Time Interval | Time elapsed for specific events or states | Congestion analysis | |
| Vehicle Identification and Characteristics | Vehicle Identification Numbers | Identifier | Unique ID for each vehicle | Vehicle-specific analysis |
| Vehicle Types | Classification | Type of vehicle (car, truck, etc.) | Traffic management | |
| Traffic and Congestion Analysis | Traffic Volume | Count | Number of vehicles passing a point | Traffic flow analysis |
| Traffic Density | Density Measurement | Vehicles per mile/kilometer | Congestion assessment | |
| Network and Communication Data | Packet Transmission Data | Data Transmission | Information on data packets in network | Network performance analysis |
| Sensor and Device Data | Camera Feeds | Images or Video | Visual data from cameras | Collision avoidance |
| Radar Data | Proximity Data | Detection of objects and distances | Object detection | |
| Driver and Behavioral Data | Speed Patterns | Speed Measurement | Consistent speeding, frequent stops | Driver behavior monitoring |
| Lane Change Frequency | Behavioral Data | Frequency of changing lanes | Traffic pattern analysis | |
| Safety and Incident Reporting | Incident Reports | Descriptive Data | Reports of road incidents | Safety assessment and response |
| Infrastructure and Environmental Factors | Road Type and Condition | Infrastructure Data | Physical condition of the road | Infrastructure planning |
| Traffic Signal Status | Operational Data | Status of traffic lights | Traffic control | |
| Advanced processing and Analysis | Noise-Added Data | Analytical Data | Data with added noise for robustness testing | Algorithm testing |
| Dataset | Attack type | Area type | Simulator | Supervised | Documentation |
|---|---|---|---|---|---|
| VeReMi | Multi-attacks | Congested highways, free-flowing traffic | Sumo, Veins, Omnet++ | Supervised | Clear |
| VeReMi Extension | Multi-attacks | Urban | Sumo, Veins, Omnet++ | Supervised | Clear |
| NGSIM | No attacks | Highway, Uban | - | Supervised | Clear |
| PeMS | No attacks | Urban Area Freeways | PeMS Tool | Unsupervised | Unclear |
| highD | No attacks | highways | - | Supervised | Clear |
| Warrigal | No attacks | Urban | - | Unsupervised | Unclear |
| DeepSense 6G | No attacks | Urban | - | Unsupervised | Clear |
| VDoS-LRS | One attack | Rural | - | supervised | Not available |
| Iqbal’s Dataset | Multi-attacks | Urban | Sumo, Veins, Omnet++ | Supervised | Not available |
| VDDD | One attack | Highway | Sumo, Veins, Omnet++ | Supervised | Not available |
| Synthetic | Multi-attacks | Urban | NS-3 | Supervised | Not available |
| Car-Hacking | Multi-attacks | - | Raspberry Pi3 | Supervised | Clear |
| OTIDS | Multi-attacks | Raspberry Pi and Arduino | Unsupervised | Clear | |
| Survival | Multi-attacks | - | - | Supervised | Clear |
| SynCAN | Multi-attacks | - | Unsupervised | Clear | |
| TU/e v2 | Multi-attacks | - | two Arduino boards | Unsupervised | Clear |
| ORNL | Multi-attacks | - | Supervised | Clear | |
| CrySyS | Multi-attacks | Highway | CAN Log Infector tool | Unsupervised | Clear |
| SIMPLE | Multi-attacks | Highway | TivaC microcontroller, SN65HVD230 CAN transceiver | Supervised | Clear |
| Bi | Multi-attacks | country roads, highways, and congested city roads | Raspberry Pi | Unsupervised | Not available |
| Dataset | Advantages | Limitations |
|---|---|---|
| VeReMi | A high number of vehicles used for data collection. It takes into consideration the attacker probability. | Few simulated attacks. Synthetic data used to train IDS are unreliable and representative of IoV properties. |
| VeReMi Extension | The dataset includes a high number of simulated attacks. It includes physical error models. | Synthetic data used to train IDS are unreliable and representative of IoV properties. |
| NGSIM | High recorded Distance (500–640 m). High number of lanes (5–6 per direction). | The dataset does not include vehicular attacks. The dataset includes erroneous trajectory behavior. NGSIM data also have a few varieties. |
| PeMS | It integrates a wide variety of information | |
| highD | highD data have a wide variety. highD includes data of more than 16.5 h of recordings. | Few maneuvers detected for use in safety validation. highD dataset does not include vehicular attacks. |
| Warrigal | High number of data collected. The dataset contains a variety of information, including vehicle state information, communication logs, and received strength measurements for radio communications | The dataset does not include vehicular attacks. |
| DeepSense 6G | It is a large-scale real-world dataset comprising co-existing and synchronized multi-modal sensing and communication data. High number of scenarios (more than 40). | The dataset does not include vehicular attacks. |
| VDoS-LRS | This dataset was generated and labeled based on a realistic testbed. It takes into consideration different types of environments (urban, rural, and highway) | It includes a few attack scenarios. Only two vehicles are used for data collection. |
| Iqbal’s Dataset | The proposed scenarios mimic the real-world scenarios. | Synthetic data used to train IDS are unreliable and representative of IoV properties. |
| VDDD | VDDD dataset is generated based on complete traffic captured from all the nodes. The simulation scenario contains all the VANET components (RSU, vehicles and routers) | Synthetic data used to train IDS are unreliable and representative of IoV properties. The dataset does not satisfy heterogeneity and attack diversity. |
| Synthetic | It takes into consideration different attacks that are not considered in the other dataset (Black Hole, Gray Hole, Wormhole). | Unavailable dataset.Synthetic data used to train IDS are unreliable and representative of IoV properties. |
| Dataset | Advantages | Limitations |
|---|---|---|
| Car-Hacking | The attack captures are very long and contain a large number of instances per attack. This dataset seems to be the most widely used in the CAN IDS research community. | All the attack captures contain a significant artifact of data collection that may pose a problem for researchers using this data. Ambient and attack data are in different formats. |
| OTIDS | It is the only open dataset that includes remote frames and responses. The fuzzing attack is unique in being the sole example of this kind of fuzzing attack in an open dataset. | The documentation on the injection message intervals needs to be clarified. The “impersonation attack” is not a real masquerade attack because the legitimate node’s message transmission is suspended. |
| Survival | It contains real attacks on multiple vehicles. This dataset provides evidence for the importance of the duration during which the bus is occupied by a message. | All of the attacks are basic and can be detected with a very simple frequency-based detector. only 60–90 s of data are provided per vehicle, which is likely not sufficient for robust training. the ambient data and attack data are in differently formatted CSVs, which is undesirable. |
| SynCAN | This is the only dataset (other than ours) that contains attacks targeting a single signal. This dataset contains the most nuanced masquerade attacks currently available. | Synthetic data are clearly an imperfect proxy for real data. Simulated attacks are inherently problematic since their effect on a vehicle cannot be verified. |
| TU/e v2 | This dataset includes the only diagnostic protocol attack publicly available and the only suspension attack (simulated) in real CAN data. The same set of attacks is available for testing on multiple vehicles/CANs. | Attack labels are in an unstructured text file, so there is no way of programmatically reading what/when packets were injected. Most of the attacks are unrealistic. |
| ORNL | The published data have been obfuscated in a way that maintains the anonymity of the vehicle while preserving all important aspects of the data for an IDS. | Unlabeled data. |
| CrySyS | This dataset can be easily extended to add new attacks. This is the only dataset furnished with descriptions of the driver’s actions during ambient captures, which is highly valuable for training and testing an IDS. | Attacks are added in post-processing, there is no guarantee that these attacks would actually affect vehicle function. Can-Log-Infector’s implementation can cause many problems. |
| SIMPLE | The dataset handles both periodic and aperiodic messages. | Documentation needs to be clarified. |
| Bi | Provides a robust foundation for IDS under challenging conditions and comprehensive evaluation of detection capabilities. | Unavailable dataset (Private and not accessible) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Haddaji, A.; Ayed, S.; Chaari Fourati, L.; Merghem Boulahia, L. Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments. Sensors 2024, 24, 3431. https://doi.org/10.3390/s24113431
Haddaji A, Ayed S, Chaari Fourati L, Merghem Boulahia L. Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments. Sensors. 2024; 24(11):3431. https://doi.org/10.3390/s24113431
Chicago/Turabian StyleHaddaji, Achref, Samiha Ayed, Lamia Chaari Fourati, and Leila Merghem Boulahia. 2024. "Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments" Sensors 24, no. 11: 3431. https://doi.org/10.3390/s24113431
APA StyleHaddaji, A., Ayed, S., Chaari Fourati, L., & Merghem Boulahia, L. (2024). Investigation of Security Threat Datasets for Intra- and Inter-Vehicular Environments. Sensors, 24(11), 3431. https://doi.org/10.3390/s24113431






