Abstract
The model for a broadcast channel with confidential messages (BC-CM) plays an important role in the physical layer security of modern communication systems. In recent years, it has been shown that a noiseless feedback channel from the legitimate receiver to the transmitter increases the secrecy capacity region of the BC-CM. However, at present, the feedback coding scheme for the BC-CM only focuses on producing secret keys via noiseless feedback, and other usages of the feedback need to be further explored. In this paper, we propose a new feedback coding scheme for the BC-CM. The noiseless feedback in this new scheme is not only used to produce secret keys for the legitimate receiver and the transmitter but is also used to generate update information that allows both receivers (the legitimate receiver and the wiretapper) to improve their channel outputs. From a binary example, we show that this full utilization of noiseless feedback helps to increase the secrecy level of the previous feedback scheme for the BC-CM.
1. Introduction
Wyner, in his outstanding paper on the degraded wiretap channel [1], first studied secure transmission over a physically degraded broadcast channel in the presence of an additional wiretapper. Wyner showed that the secrecy capacity (the maximum transmission rate with perfect secrecy constraint) of the degraded wiretap channel model was given by
where X, Y and Z are the channel input, channel output for the legitimate receiver and channel output for the wiretapper, respectively, and they satisfy the Markov chain . Note here that the secrecy capacity defined in (1) can be viewed as the difference between the main channel capacity (the channel for the transmitter and the legitimate receiver) and the wiretap channel capacity (the channel for the transmitter and the wiretapper). Later, Csiszar and Korner [2] extended Wyner’s work [1] to a more general case: the broadcast channel with confidential messages (BC-CM), where common and confidential messages were transmitted through a discrete memoryless general broadcast channel (without the degradedness assumption ), and the common message was intended to be decoded by both the legitimate receiver and the wiretapper, while the confidential message was only allowed to be decoded by the legitimate receiver. The secrecy capacity region (the capacity region with the perfect secrecy constraint) of this generalized model is determined in [2], and it is given by
where U and V respectively represent the common message and the confidential message, and and are the transmission rates of the common message and the confidential message, respectively. Here note that from (2), it is not difficult to show that the secrecy capacity (the maximum transmission rate of the confidential message with the perfect secrecy constraint) of the BC-CM is given by
where the function if , else , and is also called the secrecy capacity of the general wiretap channel. The work of [1] and [2] lays the foundation of the physical layer security in modern communication systems.
Recently, Ahlswede and Cai [3] found that if the legitimate receiver sent his own channel output Y back to the transmitter through a noiseless feedback channel, the secrecy capacity region of the BC-CM could be expanded to an achievable secrecy rate region
where the auxiliary random variables U and V are defined similarly as those in (2). The coding scheme of the region combines Csiszar and Korner’s coding scheme for the BC-CM [2] with the idea of using a secret key to encrypt the transmitted message, where the secret key is generated from the noiseless feedback. Note here that the region is an inner bound on the secrecy capacity of the BC-CM with noiseless feedback, and to the best of the authors’ knowledge, remains unknown. Similar to the work of [2], using (4), Ahlswede and Cai also provided an achievable secrecy rate (lower bound on the secrecy capacity) of the general wiretap channel with noiseless feedback, and it is given by
where V is defined in the same way as in (2). In [3], Ahlswede and Cai further pointed out that for the degraded wiretap channel with noiseless feedback (the Markov chain holds), the secrecy capacity was given by
Here, note that the secrecy capacities in (5) and (6) can be viewed as a combination of two parts: the first part is the difference between the main channel capacity ( or ) and the wiretap channel capacity ( or ), and the second part is the rate () of a secret key generated by the noiseless feedback and shared between the legitimate receiver and the transmitter. Comparing (6) with (1) and (5) with (3), it is easy to see that by using the noiseless feedback to generate a secret key encrypting the transmitted message, the secrecy capacity of the wiretap channel can be enhanced. Besides the work of [3], other related works on the BC-CM or wiretap channel in the presence of noiseless feedback are in [4,5,6,7].
In this paper, we re-visit the BC-CM with noiseless feedback investigated by Ahlswede and Cai [3] (see Figure 1), and we propose a new achievable secrecy rate region for this feedback model. The coding scheme for this achievable region combines the previous Ahlswede and Cai’s scheme [3] with the Wyner-Ziv scheme for lossy source coding with side information [8], i.e., compared with Ahlswede and Cai’s scheme, in our new scheme, the noiseless feedback is not only used to produce the secret key but also used to generate an update information that allows the legitimate receiver to improve his channel output. From a binary example, we show that this full utilization of noiseless feedback helps to obtain a larger achievable secrecy rate of the confidential message.
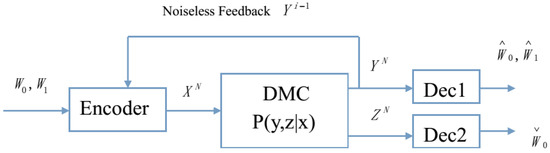
Figure 1.
Broadcast channel with confidential messages and noiseless feedback.
2. Problem Formulation and New Result
Notations: In this paper, random variables are written in upper case letters (e.g. V), real values are written in lower case letters (e.g. v), and members of the alphabet are written in calligraphic letters (e.g. ). Random vectors and their values are written in a similar way. The probability is shortened to . In addition, for the remainder of this paper, the base of the logarithm is 2.
Model description: Suppose that the common message is chosen to be transmitted, and it is uniformly distributed over its alphabet . Analogously, the confidential message is chosen to be transmitted, and it is uniformly distributed over its alphabet . The channel is discrete and memoryless with input , outputs , , and has transition probability . At time i (), the legitimate receiver receives the channel output , and he sends the previous channel outputs ,..., back to the transmitter via a noiseless feedback channel. Hence at time i, the channel encoder is denoted by
Here we should note that does not need to be deterministic and stochastic encoding is also allowed. For the legitimate receiver, after receiving , he uses a decoding mapping to obtain and , which are estimations of the transmitted messages and , respectively. The legitimate receiver’s decoding error probability is defined by
For the wiretapper, after receiving , he uses a decoding mapping to obtain , which is an estimation of the transmitted message . Moreover, the wiretapper also tries to decode the transmitted message via his own channel output , and his equivocation (uncertainty) about is denoted by
The wiretapper’s decoding error probability is defined by
Finally, using similar criteria in [1] and [2], if for any small positive number , there exists an encoding-decoding scheme with parameters , , N, and such that
we say that the rate pair is achievable with perfect secrecy. The secrecy capacity region is composed of all achievable secrecy rate pairs satisfying (5), and the following Theorem 1 provides an inner bound on .
Theorem 1.
The secrecy capacity region of the discrete memoryless BC-CM with noiseless feedback satisfies
where
the joint probability mass function is denoted by
and the auxiliary random variables , , , V, U take values in finite alphabets.
Proof.
The coding scheme for the inner bound combines the previous Ahlswede and Cai’s scheme of the model of Figure 1 with a “generalized” Wyner-Ziv scheme for lossy source coding with side information [8], and the details of the proof of Theorem 1 are in Appendix A. ☐
Remark 1.
There are some notes on Theorem 1; see the following.
- Comparing our new inner bound with the previous Ahlswede and Cai’s inner bound , in general, we do not know which one is larger. In the next section, we consider a binary case of the BC-CM with noiseless feedback, and compute these inner bounds for this binary case. From this binary example, we show that the maximum achievable (the transmission rate of the confidential message with perfect secrecy constraint) in is larger than that in , however, the enhancement of is at the cost of reducing the transmission rate of the common message .
- Note here that in , the auxiliary random variable U represents the encoded sequence for the common message and V represents the encoded sequence for both the common and confidential messages. The auxiliary random variable is both the legitimate receiver and the wiretapper’s estimation of U, and the index of is related to the update information generated by the noiseless feedback. The auxiliary random variable is the legitimate receiver’s estimation of V, and is the wiretapper’s estimation of V. Both the indexes of and are with respect to the update information. The inner bound is constructed by using the feedback to generate a secret key shared between the legitimate receiver and the wiretapper, and generate update information used to construct estimation of the transmitted sequences U and V. The estimation of U and V helps both the legitimate receiver and the wiretapper to improve their own received symbols Y and Z.
3. Binary Example of the BC-CM with Noiseless Feedback
Now we consider a binary case of the model of Figure 1. In this case, the channel input is X and output Y, Z takes values in , and they satisfy
where () and () are the channel noises for the transmitter-legitimate receiver’s channel and transmitter-wiretapper’s channel, respectively, and they are independent of each other and the channel input X.
Without noiseless feedback, letting , , , , , using the fact that U is independent of V, and substituting (14) into (2), it is not difficult to calculate the secrecy capacity region of the binary BC-CM, and it is given by
where and . Here, note that the region (15) is achieved when .
With noiseless feedback, first, we compute Ahlswede and Cai’s achievable secrecy rate region for this binary case. Letting , , , , , using the fact that U is independent of V, and substituting (14) into (4), it is not difficult to calculate Ahlswede and Cai’s achievable secrecy rate region for this binary case, and it is given by
where if , else . Comparing (16) with (15), it is easy to see that the noiseless feedback enhances the secrecy capacity region of the binary BC-CM. Here the region (16) is achieved when .
Then, it remains to compute our new achievable secrecy rate region for this binary case. Letting , , , , , , , , using the fact that U is independent of V, and substituting (14) into of Theorem 1, it is not difficult to show that the achievable secrecy rate region of our new feedback scheme is given by
The achievability of can be explained by the following simple block length-(n) scheme.
- First note that in the following explanation, the channel input for the i-th block () is denoted by , and similar conventions are applied to , , , , , , , and . For each block, the transmitted message is composed of a common message, a confidential message, a dummy message and update information.
- (Encoding): In the i-th block (), after the transmitter receives the feedback channel output , he generates a secret key from and uses this key to encrypt the confidential message of the i-th block. In addition, since , the transmitter also knows the legitimate receiver’s channel noise at the i-th block, and thus he chooses as an estimation of , as the legitimate receiver’s estimation of , and as the wiretapper’s estimation of . Note that and the update information is part of the indexes of , and .
- (Decoding at the legitimate receiver): The legitimate receiver does backward decoding, i.e., the decoding starts from the last block. In block n, the legitimate receiver applies Ahlswede and Cai’s decoding scheme [3] to obtain his update information for block n. Then using the channel output as side information, the legitimate receiver applies Wyner-Ziv’s decoding scheme [8] to obtain and . Since , the legitimate receiver knows the legitimate receiver’s channel noise for block , and thus he computes to obtain and the corresponding transmitted message for block . Repeating the above decoding scheme, the legitimate receiver obtains the entire transmitted messages (including both confidential and common messages) for all blocks, and since he also knows the secret keys, the real messages are decrypted by him.
- (Decoding at the wiretapper): The wiretapper also does backward decoding. In block n, the wiretapper receives , and he applies Ahlswede and Cai’s decoding scheme [3] to obtain his update information for block n. Then using the channel output as side information, the wiretapper applies Wyner-Ziv’s decoding scheme [8] to obtain and . Since , the wiretapper knows the common message for block . Repeating the above decoding scheme, finally, the wiretapper obtains the entire common messages for all blocks.
The following Figure 2 shows the achievable secrecy rate region of our new scheme, Ahlswede and Cai’s achievable secrecy rate region and the secrecy capacity region of the binary BC-CM without feedback for and , which implies that the wiretapper’s channel noise is smaller than the legitimate receiver’s. From Figure 2, it is easy to see that when the wiretapper’s channel noise is smaller than the legitimate receiver’s, the secrecy rate of the binary BC-CM without feedback is 0, which implies that perfect secrecy can not be achieved, and the secrecy rate is enhanced by using noiseless feedback. Moreover, we see that our new scheme performs better than Ahlswede and Cai’s in enhancing the secrecy rate , however, we should notice that the boosting of the secrecy rate is at the cost of reducing the rate of the common message.
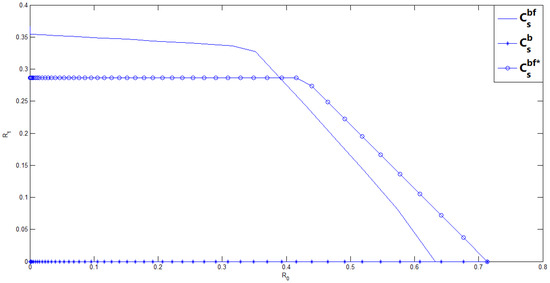
Figure 2.
The comparison of our new scheme with Ahlswede-Cai’s scheme and Csiszar-Korner’s scheme of the BC-CM without feedback for and .
The following Figure 3 shows the achievable secrecy rate region of our new scheme, Ahlswede and Cai’s achievable secrecy rate region , and the secrecy capacity region of the binary BC-CM without feedback for and , which implies that the wiretapper’s channel noise is larger than the legitimate receiver’s. From Figure 3, it is easy to see that noiseless feedback enhances the secrecy rate of the BC-CM without feedback. However, we also should notice that the enhancement of the secrecy rate is at the cost of reducing the rate of the common message.
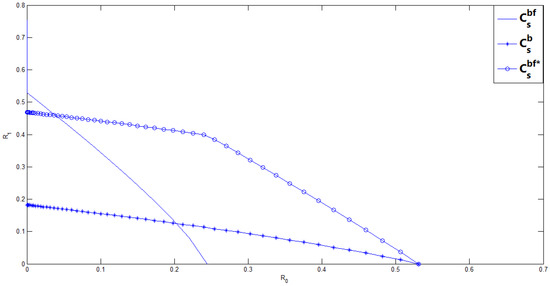
Figure 3.
The comparison of our new scheme with Ahlswede-Cai’s scheme and Csiszar-Korner’s scheme of the BC-CM without feedback for and .
4. Conclusions
In this paper, we propose a new coding scheme for the BC-CM with noiseless feedback. From a binary example, we show that our new feedback scheme performs better than the existing feedback scheme in enhancing the secrecy level of the BC-CM. However, we should notice that this enhancement of the secrecy level is at the cost of reducing the rate of the common message.
Acknowledgments
This work was supported by the National Natural Science Foundation of China under Grants 61671391, 61301121, 61571373 and the Open Research Fund of the State Key Laboratory of Integrated Services Networks, Xidian University (No. ISN17-13).
Author Contributions
Bin Dai, Xin Li and Zheng Ma did the theoretical work; Xin Li performed the experiments; Bin Dai and Xin Li analyzed the data; Xin Li wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| MDPI | Multidisciplinary Digital Publishing Institute |
| DOAJ | Directory of open access journals |
| TLA | Three letter acronym |
| LD | linear dichroism |
| BC-CM | broadcast channel with confidential messages |
Appendix A. Proof of Theorem 1
Appendix A.1. Preliminary
For a given probability , the identical independent distributed (i.i.d.) generated sequence is called -typical if
where is the frequency of symbol x appearing in the sequence . The set, which is composed of all -typical , is denoted by , and it is called the typical set. The following four lemmas about the typical set are extensively used in information theory.
Lemma A1. (Covering Lemma [9]):
Let satisfy as . Also let M be an integer larger than for some , and let be a set composed of i.i.d. generated sequences (according to the probability ) such that are mutually independent. Then, for any probability with marginal probabilities and , there exists a such that
if , where as .
Lemma A2. (Packing Lemma [9]):
Let be an i.i.d. generated random vector with distribution . Also let M be an integer smaller than for some , and let be a set composed of i.i.d. generated sequences according to the probability , and each in the set is independent of . Then for any probability with marginal probabilities and , there exists a such that
if , where as .
Lemma A3. (Generalized Packing Lemma [9]):
For some , let , , be integers satisfying , and , respectively. Also let () be a set composed of i.i.d. generated sequences (with respect to the distribution ) such that are mutually independent for any , , . Then for any probability with marginal probabilities , and , there exists a such that
if , where as .
Lemma A4. (Balanced coloring lemma [3]):
For any , sufficiently large N and all i.i.d. generated according to the distribution , there exists a γ- coloring
of such that for all joint distribution with marginal distribution and , ,
for , where is the inverse image of c.
Lemma A4 implies that if , , , and are jointly typical, for given , , and , the number of for a certain color k (), which is denoted by , is upper bounded by . By using Lemma A1, it is easy to see that the typical set maps into at least
colors. On the other hand, the typical set maps into at most colors.
Appendix A.2. Code Construction
Definitions:
- Transmission takes place over n blocks, and each block is of length N. Define the confidential message by , where () is for block i and takes values in . Further divide into , where () takes values in , and .
- Define the common message by , where () is for block i and takes values in .
- Let be a randomly generated dummy message transmitted over all blocks, and it is denoted by , where () is for block i and it takes values in .
- Let and be update information transmitted over all blocks, and they are respectively denoted by and , where and () are for block i and take values in and , respectively. Further divide into , where () takes values in , and . Moreover, further divide into , where () takes values in , and .
- Let , , , , , , and be the random vectors for block i (). Define , and similar convention is applied to , , , , , and . The specific values of the above random vectors are denoted by lower case letters.
Code construction:
- In each block i (), randomly produce i.i.d. sequences according to the probability , and index them as , where , , and . Here note that .
- For a given , randomly produce i.i.d. sequences according to the conditional probability , and index them as , where , , , and . Here note that and .
- The sequence is i.i.d. produced according to a new discrete memoryless channel (DMC) with transition probability . The inputs and output of this new DMC are , and , respectively.
- In each block i (), generate in two ways: the first way is to produce i.i.d. sequences according to the probability , and index them as , where 1 represents the first way to define , , and ; the second way is to produce i.i.d. sequences according to the probability , and index them as , where 2 represents the second way to define , , and .
- In each block i (), produce i.i.d. sequences according to the probability , and index them as , where , and .
- In each block i (), produce i.i.d. sequences according to the probability , and index them as , where and .
Encoding scheme:
- In block 1, the transmitter chooses and to transmit.
- In block i (), the transmitter receives the feedback , and he tries to select a pair of sequences such that are jointly typical sequences. If there are more than one pair , randomly choose one; if there is no such pair, an error is declared. Based on Lemma A1, it is easy to see that the error probability goes to 0 ifMoreover, the transmitter also tries to select a pair of sequences such that are jointly typical sequences. If there are more than one pair , randomly choose one; if there is no such pair, an error is declared. Based on Lemma A1, it is easy to see that the error probability goes to 0 if (A3) andhold. Once the transmitter selects such pairs and , he chooses to transmit.Before choosing the transmitted codeword , produce a mapping . Furthermore, we define as a random variable uniformly distributed over , and it is independent of all the random vectors and messages of block i. Here note that is the secret key known by the transmitter and the legitimate receiver, and is a specific value of . Reveal the mapping to the transmitters, legitimate receiver and the wiretapper. Once the transmitter finds a pair such that are jointly typical sequences, and finds a pair such that are jointly typical sequences, he chooses to transmit.
- In block n, the transmitter receives , and he finds a pair such that are jointly typical sequences. Moreover, he also finds a pair such that are jointly typical sequences. Then he chooses and to transmit.
Decoding scheme for the legitimate receiver: The legitimate receiver does backward decoding after the transmission of all n blocks is finished. For block n, first, he tries to select a unique such that are jointly typical. If there is no or multiple ones exist, an decoding error is declared. Using Lemma A2, the error probability goes to 0 if
Then, he tries to select a unique such that are jointly typical. If there is no or multiple ones exist, an decoding error is declared. Using Lemma A2, the error probability goes to 0 if
When and are successfully decoded, the legitimate receiver extracts , , , , from them. Then using Wyner-Ziv’s decoding scheme [8] for the source coding with side information, the legitimate receiver tries to find unique and such that given , , , and , are jointly typical sequences. If there is no or multiple ones exist, an decoding error is declared. Based on Lemma A2 and Lemma A3, the error probability goes to 0 if
For block , after is successfully decoded, the legitimate receiver tries to select a unique such that are jointly typical. Based on Lemma A2, the error probability goes to 0 if
Then he tries to select a unique such that are jointly typical. If there is no or multiple ones exist, an decoding error is declared. Using Lemma A2, the error probability goes to 0 if
When and are successfully decoded, the legitimate receiver extracts , , , , , , , and from it. Since the legitimate receiver knows the key , the transmitted messages , and for block are obtained. Repeat the above decoding scheme, the entire transmitted messages for all blocks are obtained by the legitimate receiver.
Decoding scheme for the wiretapper: The wiretapper also does backward decoding after the transmission of all n blocks is finished. For block n, first, he tries to select a unique such that are jointly typical. If there is no or multiple ones exist, an decoding error is declared. Using Lemma A2, the error probability goes to 0 if
When is successfully decoded, the wiretapper extracts , and from them. Then using Wyner-Ziv’s decoding scheme [8] for the source coding with side information, the wiretapper tries to find unique and such that given , and , are jointly typical sequences. If there is no or multiple ones exist, an decoding error is declared. Based on Lemma A2 and Lemma A3, the error probability goes to 0 if
For block , after is successfully decoded, the wiretapper tries to select a unique such that are jointly typical. Based on Lemma A2, the error probability goes to 0 if
When is successfully decoded, the legitimate receiver extracts , , and from it. Repeat the above decoding scheme, the entire common messages for all blocks are obtained by the wiretapper.
Appendix A.3. Equivocation Analysis
For all blocks, the equivocation is bounded by
where (a) is from the definitions and .
The first part of (A16) can be lower bounded by
where (b) is from , (c) is from , (d) is from the construction of and , (e) is from the fact that the channel is memoryless, and (f) is from the fact that given , , and , the wiretapper tries to select unique such that are jointly typical, and based on Lemma A2, the wiretapper’s decoding error probability tends to 0 if
then using Fano’s inequality, we have , where as .
Moreover, the second part of (A16) can be lower bounded by
where (e) is from the Markov chain , (f) is from . Now it remains to bound in (A19), see the followings.
From Lemma A4 and (A2), we know that the typical set maps into at least colors. Choosing and notice that
where as , thus we can conclude that
Substituting (A21) into (A19), we have
Finally, substituting (A17) and (A22) into (A16), we have
The bound (A23) implies that if
we can prove that by choosing sufficiently large n and N.
The achievable secrecy rate region can be obtained from (A3), (A4), (A5), (A6), (A7), (A8), (A9), (A10), (A11), (A12), (A13), (A14), (A15), (A18) and (A24). To be specific, first, using , , the Markov chain , and applying Fourier-Motzkin elimination to eliminate , , , , , , and from (A3), (A4), (A5), (A6), (A7), (A8), (A9), (A12), (A13) and (A14), we have
Then, using , , and applying Fourier-Motzkin elimination to eliminate , , , , from (A10), (A11), (A15), (A18), (A24), (A25) and (A26), the achievable secrecy rate region in Theorem 1 is obtained. The proof of Theorem 1 is completed.
References
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast channels with confidential messages. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar]
- Ahlswede, R.; Cai, N. Transmission, identification and common randomness capacities for wire-tap channels with secure feedback from the decoder. Gen. Theory Inf. Trans. Comb. 2006, 258–275. [Google Scholar]
- Ardestanizadeh, E.; Franceschetti, M.; Javidi, T.; Kim, Y. Wiretap channel with secure rate-limited feedback. IEEE Trans. Inf. Theory 2009, 55, 5353–5361. [Google Scholar] [CrossRef]
- Lai, L.; El Gamal, H.; Poor, V. The wiretap channel with feedback: encryption over the channel. IEEE Trans. Inf. Theory 2008, 54, 5059–5067. [Google Scholar] [CrossRef]
- Yin, X.; Xue, Z.; Dai, B. Capacity-equivocation regions of the DMBCs with noiseless feedback. Math. Probl. Eng. 2013, 2013, 102069. [Google Scholar] [CrossRef]
- Dai, B.; Han Vinck, A.J.; Luo, Y.; Zhuang, Z. Capacity region of non-degraded wiretap channel with noiseless feedback. In Proceedings of the 2012 IEEE International Symposium on Information Theory (ISIT), Cambridge, MA, USA, 1–6 July 2012. [Google Scholar]
- Wyner, A.; Ziv, J. The rate-distortion function for source coding with side information at the decoder. IEEE Trans. Inf. Theory 1976, 22, 1–10. [Google Scholar] [CrossRef]
- El Gamal, A.; Kim, Y.H. Information measures and typicality. In Network Information Theory; Cambridge University Press: Cambridge, UK, 2011; pp. 17–37. [Google Scholar]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).