Development of a Modified Medical Data Transmission over the Cellular Network System to Secure Health-Related Data from Changes in Environmental Parameters †
Abstract
1. Introduction
2. Literature Review
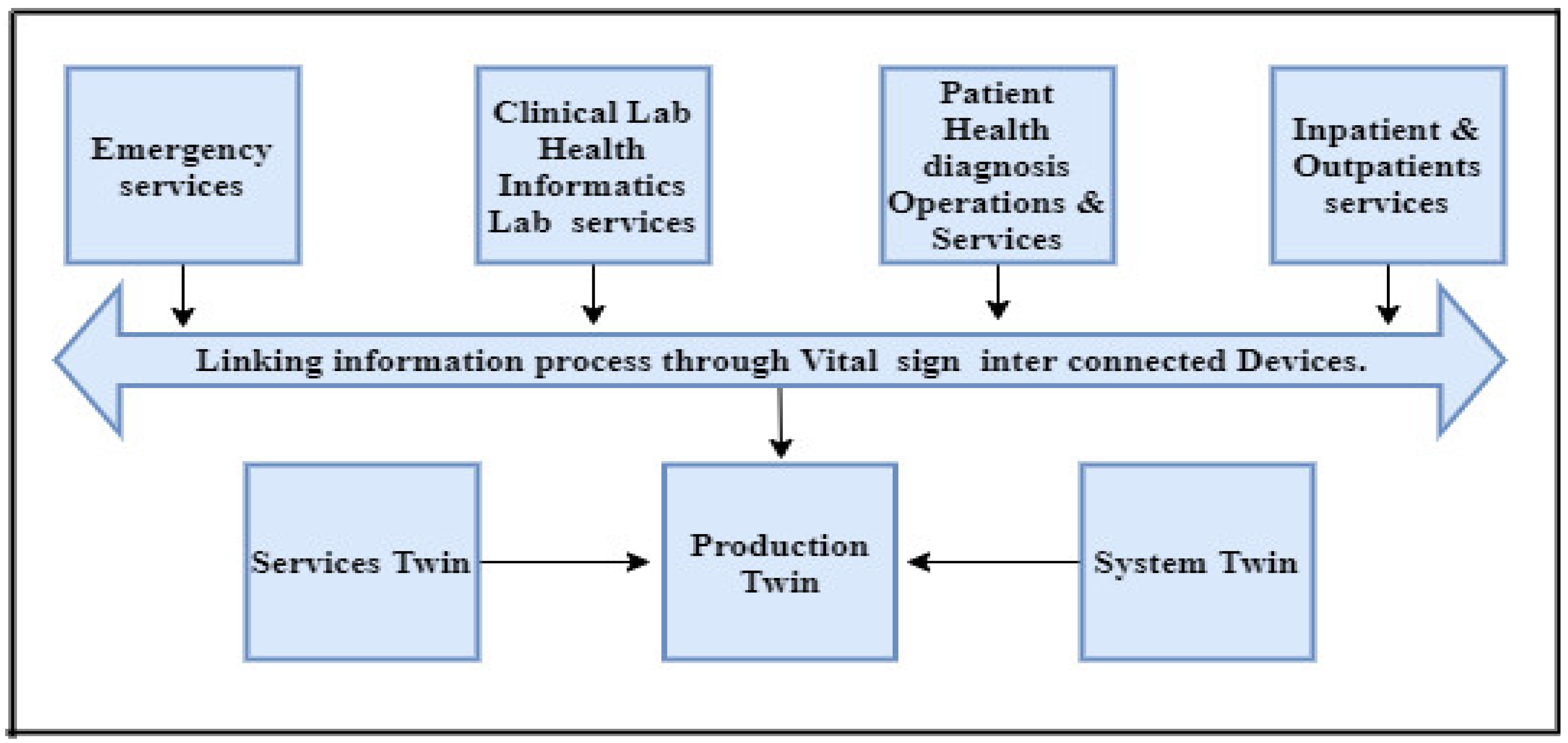
3. Methodology for Modified Secure IoT Healthcare System
- Ambulatory Vital Sign monitoring functional platform board.
- Modified Medical Data Transmission over the Cellular Network (MEDTOC) system.
- Data Encryption algorithm for health-related data security and simulation results.
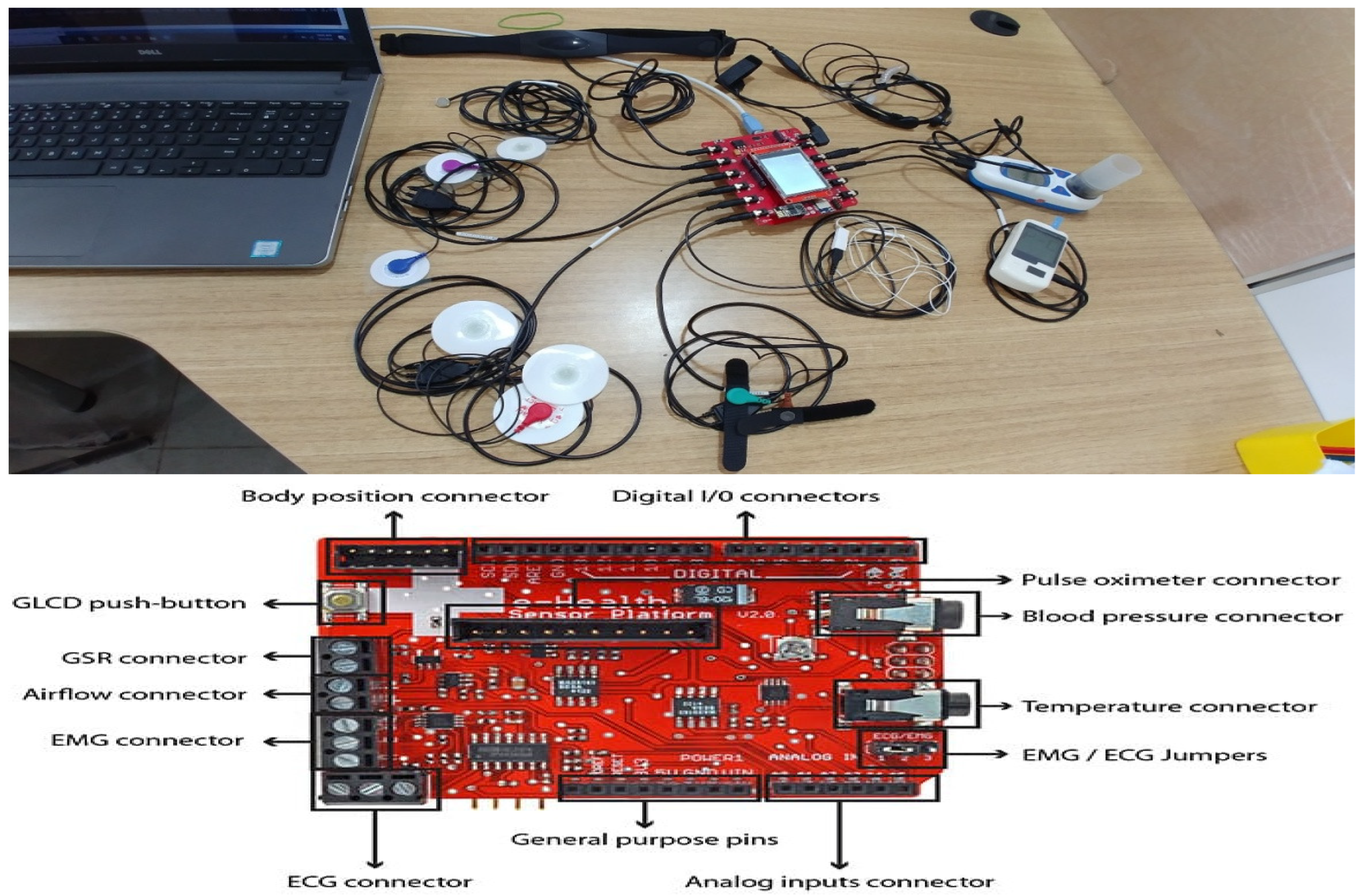
3.1. Development of Ambulatory Vital Sign Monitoring System Functional Platform Board
- Monitoring of Vital Signs (patient vital signs data, patient vital signs references, physician scheduled at a base)
- Given: vital signs data for N patients, database for M physicians, capacity L patients per physician
- For (i = 1 to N)
- Receive vital signs data of patient I and display it in a graphical reference scale;
- Connect it to the physician schedule database = D
- For (j = 1 to M)
- Search for an available physician by status (P, Q, NA)
- If (i = 1, i = M, i++) i.e., physician found with status P, alert the physician before the arrival of the data with an audible beep. Start sending the vital signs data of patient “i” to the physician with status (P), or go to step 1.
- If (i = 1, i = M, i++) i.e., physician found with status Q, stop accepting more patients capacity // is reached. Record physician ID (T, Z) where T = title or “ID” of the physician and Z = MAC address of the physician’s smart device.
- Or go to step 1.
- if (j = 0, j = M, j++) i.e., physician found with status NA, patient is sent to step 8.
3.2. Modified Medical Data Transmission over the Cellular Network (MEDTOC) System
3.3. A Data Encryption Algorithm for Data Security and Simulation Results
- Preimage resistance
- Second preimage resistance (weak collision resistance)
- Strong collision resistance
- Assumed lowercase letters in string format.
- A shifted integer between 0–25
- Traversed one character at a time throughout the specified text.
- Transformed the given character as per the rule for each character, depending on whether we are encrypting or decrypting the document. Return the newly produced string.
- At the end, received the value (integer) for the text (string) and shift, and returns the encrypted text.
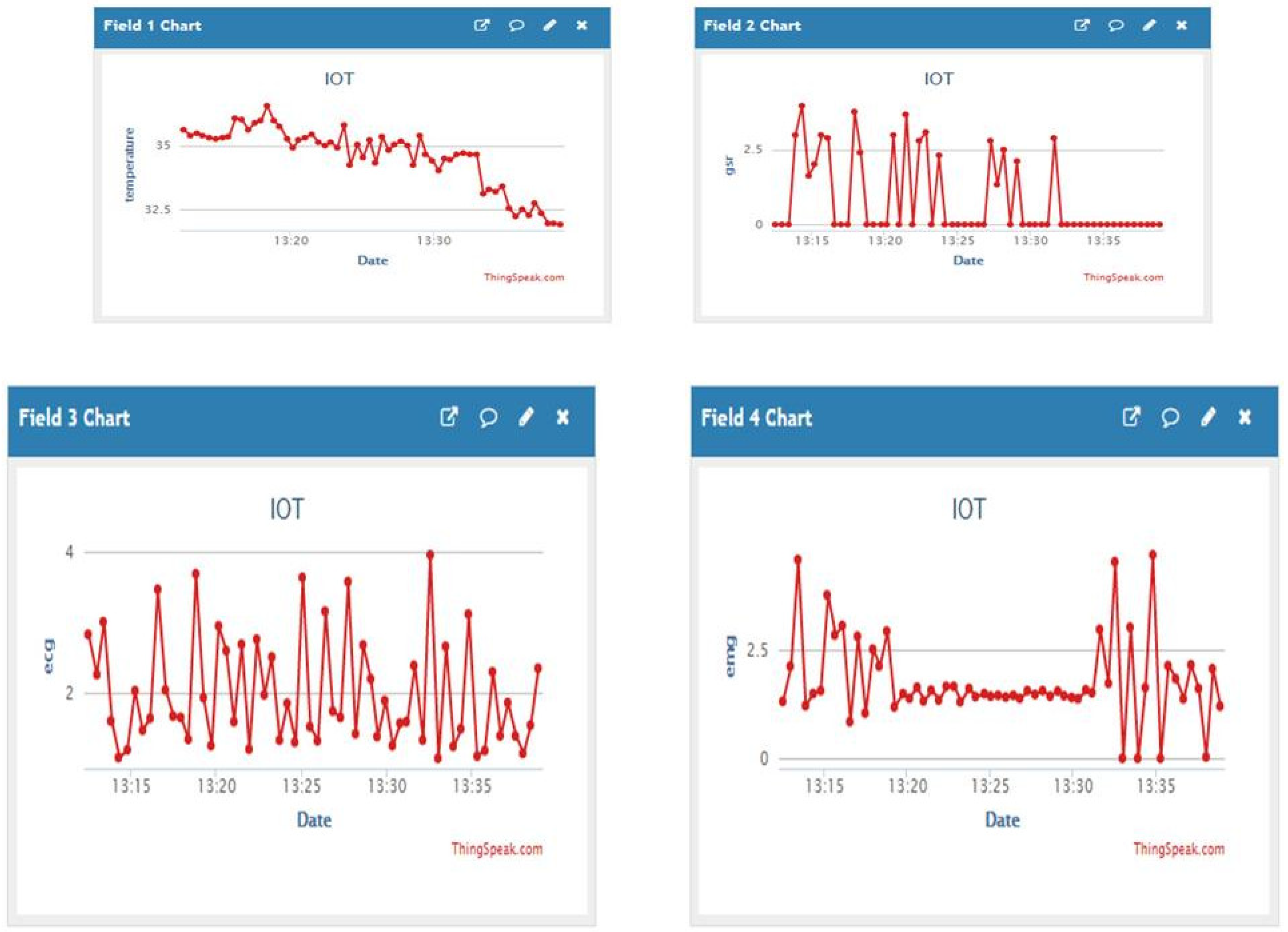
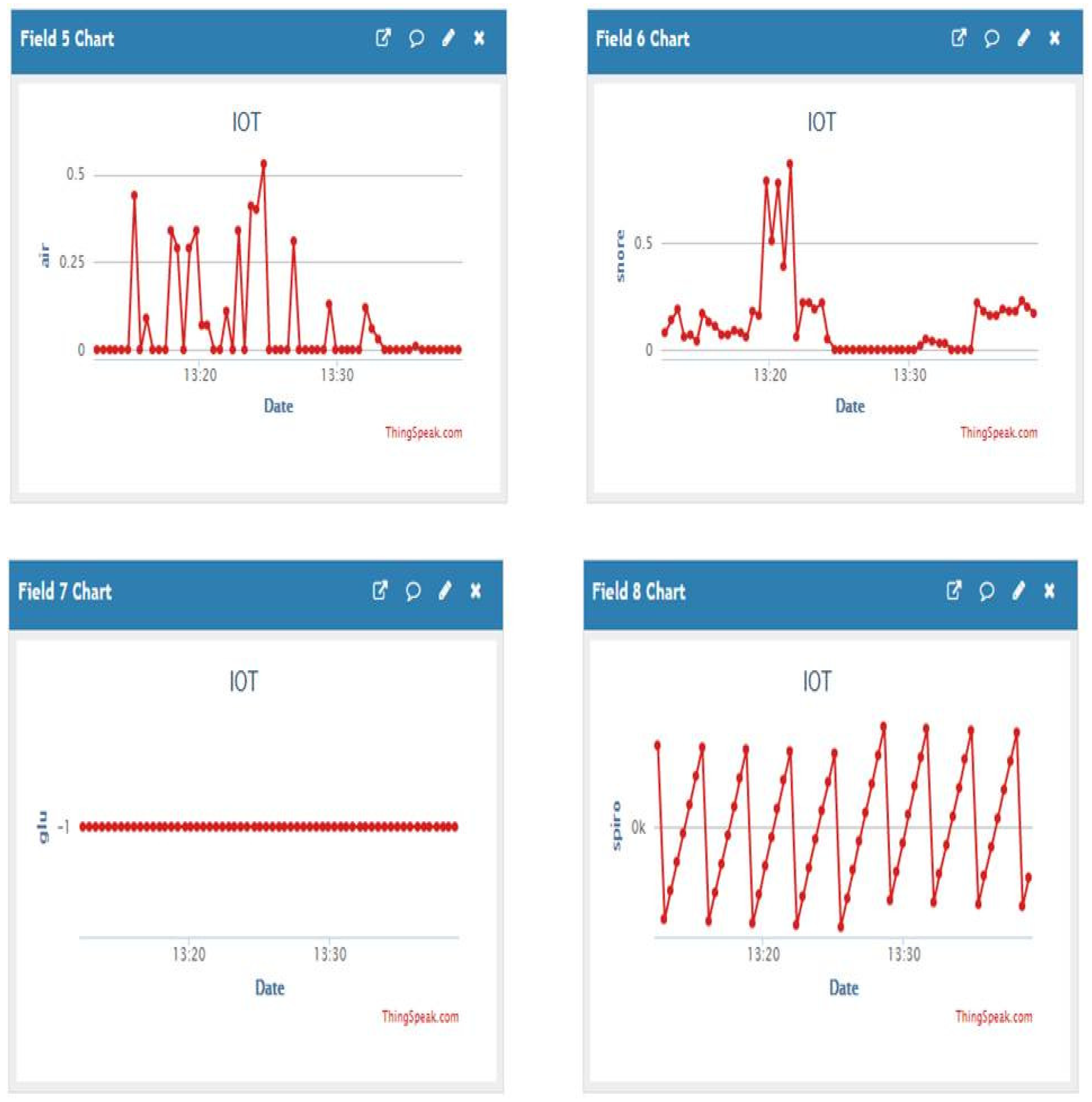
4. Results and Discussions
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Misbahuddin, S. IoT-Based Ambulatory Vital Signs Data Transfer System. J. Comput. Netw. Commun. 2018, 2018, 4071474. [Google Scholar] [CrossRef]
- Zubairi, J.A.; Idwan, S. Smart algorithms for patient assignment in disasters. ICT Express 2018, 4, 107–111. [Google Scholar] [CrossRef]
- Zanjal, S.V.; Talmale, G.R. Medicine reminder and monitoring system for secure health using IoT. Procedia Comput. Sci. 2016, 78, 471–476. [Google Scholar] [CrossRef]
- Deligiannidis, L.; Arabnia, H.R. Security Projects for Systems and Networking Professionals. In Emerging Trends in ICT Security; Elsevier: Amsterdam, The Netherlands, 2014. [Google Scholar]
- Islam, M.; Rahaman, A.; Islam, R. Development of smart healthcare monitoring system in IoT environment. SN Comput. Sci. 2020, 1, 1–11. [Google Scholar] [CrossRef]
- Olson, R.; Zubairi, J.A.; Biliciler, A. A software framework for patient data handling in emergencies and disasters. In Proceedings of the 2014 International Conference on Collaboration Technologies and Systems (CTS), Minneapolis, MN, USA, 19–23 May 2014; pp. 553–557. [Google Scholar]
- Kliem, A.; Hovestadt, M.; Kao, O. Security and Communication Architecture for Networked Medical Devices in Mobility-Aware eHealth Environments. In Proceedings of the 2012 IEEE First International Conference on Mobile Services, MS 2012, Honolulu, HI, USA, 24–29 June 2012; pp. 112–114. [Google Scholar]
- Pavlopoulos, S.; Kyriacou, E.; Berler, A.; Dembeyiotis, S.; Koutsouris, D. A novel emergency telemedicine system based on wireless communication technology–AMBULANCE. IEEE Trans. Inf. Technol. Biomed. Spec. Issue Emerg. Health Telemat. Appl. Eur. 1998, 2, 261–267. [Google Scholar] [CrossRef] [PubMed]
- Islam, S.M.R. The Internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Idwan, S.; Zubairi, J. Load balancing for disaster recovery and management. Springer Wirel. Pers. Commun. J. 2016, 90, 369–379. [Google Scholar] [CrossRef]
- Nateghizad, M.B.M.; Maarof, M.A. Secure searchable based asymmetric encryption in cloud computing. Int. J. Adv. Soft Comput. Its Appl. 2014, 6, 1–13. [Google Scholar]
- Saini, N.; Pandey, N.; Singh, A.P. Enhancement of security using cryptographic techniques. In Proceedings of the 4th International Conference on Reliability, Infocom Technologies and Optimization, ICRITO 2015, Noida, India, 2–4 September 2015. [Google Scholar]
- Masood, I. Towards smart healthcare: Patient data privacy and security in sensor-cloud infrastructure. Wirel. Commun. Mob. Comput. 2018, 2018, 2143897. [Google Scholar] [CrossRef]
- Sadek, I. Privacy and Security of IoT Based Healthcare Systems: Concerns, Solutions, and Recommendations. In Proceedings of the International Conference on Smart Homes and Health Telematics, New York, NY, USA, 14–16 October 2019; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Haghi, M. A Flexible and Pervasive IoT-Based Healthcare Platform for Physiological and Environmental Parameters Monitoring. IEEE Internet Things J. 2020, 7, 5628–5647. [Google Scholar] [CrossRef]
- Karthik, G.V.S.; Fathima, S.Y.; Rahman, M.Z.U.; Ahamed, S.R.; Lay-Ekuakille, A. Efficient signal conditioning techniques for brain activity in remote health monitoring network. IEEE Sens. J. 2013, 13, 3276–3283. [Google Scholar] [CrossRef]
- Gayathri, N.B.; Thumbur, G.; Kumar, P.R.; Rahman, Z.U.; Reddy, P.V.; Lay-Ekuakille, A. Efficient and secure pairing-free certificateless aggregate signature scheme for healthcare wireless medical sensor networks. IEEE Internet Things J. 2019, 6, 9064–9075. [Google Scholar] [CrossRef]
- Aparna, P.; Kishore, P.V.V. Biometric-based efficient medical image watermarking in E-healthcare application. IET Image Process. 2019, 13, 421–428. [Google Scholar] [CrossRef]
- Soumya, I.; Rahman, M.Z.U.; Reddy, D.V.R.K.; Lay-Ekuakille, A. Efficient block processing of long duration biotelemetric brain data for health care monitoring. Rev. Sci. Instrum. 2015, 86, 035003. [Google Scholar] [CrossRef] [PubMed]
- Prasad, C.; Bojja, P. A reliable, energy aware and stable topology for bio-sensors in health-care applications. J. Commun. 2019, 14, 390–395. [Google Scholar] [CrossRef]
- Shinde, S.A.; Rajeswari, P.R. Intelligent health risk prediction systems using machine learning: A review. Int. J. Eng. Technol. 2018, 7, 1019–1023. [Google Scholar] [CrossRef]
- Krishna, C.V.P.; Kiran, K.V.D.; Kim, T.-H. Integrated Distributed Architecture to Integrate Wireless Sensor Networks (WSN) with Grid for Healthcare. Int. J. Bio-Sci. Bio-Technol. 2015, 7, 243–250. [Google Scholar] [CrossRef]
- Radhika, R.C.; Rao, M.R.N.; Venkateswarlu, S. Review on the security issues in human sensor networks for healthcare applications. Int. J. Eng. Technol. 2018, 7, 269–274. [Google Scholar]
- Mubarakali, A.; Ashwin, M.; Mavaluru, D.; Kumar, A.D. Design an attribute-based health record protection algorithm for healthcare services in cloud environment. Multimed. Tools Appl. 2020, 79, 3943–3956. [Google Scholar] [CrossRef]
- Kishore, K.H.; Nath, K.V.S.; Krishna, K.V.N.H.; Kumar, D.P.; Manikanta, V.; Basha, F.N. IOT Based Smart Health Monitoring Alert Device. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2019, 8, 157–160. [Google Scholar]
- Khan, M.M.; Alanazi, T.M.; Albraikan, A.A.; Almalki, F.A. IoT-based health monitoring system development and analysis. Secur. Commun. Netw. 2022, 2022, 9639195. [Google Scholar] [CrossRef]
- Abdulmalek, S.; Nasir, A.; Jabbar, W.A.; Almuhaya, M.A.M.; Bairagi, A.K.; Khan, M.A.-M.; Kee, S.-H. IoT-Based Healthcare-Monitoring System towards Improving Quality of Life: A Review. Healthcare 2022, 10, 1993. [Google Scholar] [CrossRef] [PubMed]
- Islam, R.; Kabir, M.; Mridha, M.F.; Alfarhood, S.; Safran, M.; Che, D. Deep Learning-Based IoT System for Remote Monitoring and Early Detection of Health Issues in Real-Time. Sensors 2023, 23, 5204. [Google Scholar] [CrossRef] [PubMed]


| S. No. | Procedure |
|---|---|
| 1 | Create a Disaster Area (Location, Hospital, GPS) |
| 2 | Establish Secure Connection (Server(hi),Disaster Area Coordinates) |
| 3 | Form = 1……….n, 3.1 Retrieve (hospID, physID, Server(hi),DispatchpatID |
| 4 | Establish Secure Connection (physID) |
| S. No. | Procedure |
|---|---|
| 1 | Alert = Wait(H1); //Wait for the disaster management algorithm to start on server side |
| 2 | Retrieve info Disaster (disaster ID, GPS) |
| 3 | For each hospital “hi” in the list |
| 4 | Dmax = max distance (list) |
| 5 | Retrieve Info Patient (patID, RTS) |
| RTS Range | Hosp1 | Hosp2 | Hosp3 | Improved Hosp N |
|---|---|---|---|---|
| 0.0–0.5 | 0 | 0 | 67 | Identified the near-end hospital in the RTS range |
| 0.5–1.0 | 2 | 23 | 28 | |
| 1.0–1.5 | 24 | 44 | 83 | |
| 1.5–2.0 | 26 | 16 | 53 | |
| 2.0–2.5 | 60 | 23 | 37 | |
| 2.5–3.0 | 42 | 16 | 25 | |
| 3.0–3.5 | 41 | 11 | 25 | |
| Grand Total | 225 | 142 | 333 |
| Monitored Day and Time | Entry_Id | Humidity (g/m3) in % | Temperature in Degrees Celsius | Encrypted Data | Data Recovered | ||
|---|---|---|---|---|---|---|---|
| 2021-05-13 05:40:11 UTC | 1 | 73 | 28 | Okfh | jpfh | 73 | 28 |
| 2021-05-13 05:40:38 UTC | 2 | 73 | 28 | Okfh | jpfh | 73 | 28 |
| 2021-05-13 05:41:04 UTC | 3 | 84 | 29 | Plfh | jqfh | 84 | 29 |
| 2021-05-13 05:41:31 UTC | 4 | 86 | 29 | Pnfh | jqfh | 86 | 29 |
| 2021-05-13 05:42:00 UTC | 5 | 78 | 29 | Opfh | opfh | 78 | 29 |
| 2021-05-13 05:42:25 UTC | 6 | 84 | 30 | Plfh | plfh | 84 | 30 |
| 2021-05-13 05:42:52 UTC | 7 | 84 | 29 | Plfh | plfh | 84 | 29 |
| 2021-05-13 05:43:45 UTC | 8 | 80 | 29 | Phfh | phfh | 80 | 29 |
| 2021-05-13 05:44:10 UTC | 9 | 77 | 28 | Oofh | jpfh | 77 | 28 |
| 2021-05-13 05:44:37 UTC | 10 | 77 | 28 | Oofh | jpfh | 77 | 28 |
| 2021-05-13 05:45:04 UTC | 11 | 76 | 28 | Onfh | jofh | 76 | 28 |
| 2021-05-13 05:45:31 UTC | 12 | 77 | 28 | Oofh | jpfh | 77 | 28 |
| 2021-05-13 05:45:56 UTC | 13 | 77 | 28 | Oofh | jpfh | 77 | 28 |
| 2021-05-13 05:46:06 UTC | 14 | 76 | 27 | Onfh | jofh | 76 | 27 |
| 2021-05-13 05:46:36 UTC | 15 | 76 | 28 | Onfh | jofh | 76 | 28 |
| Health-Related Data Monitoring Parameters | Encrypted Outputs for the Monitored Health-Related Data | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Temperature | Glucose | SPo2 | ECG | Spiro Meter | Airflow | Snore | Temperature | Glucose | SPo2 | ECG | Spiro Meter | Airflow | Snore |
| 100.1 | 70 | 94 | 120 | 80 | 18 | 145 | ggdf | gffdg | Mfdf | ojdf | ghfdf | nfdf | Gndf |
| 98 | 71 | 95 | 120 | 80 | 20 | 145 | gmdf | ondf | Mgdf | okdf | ghfdf | nfdf | Hfdf |
| 97 | 72 | 96 | 120 | 80 | 22 | 145 | gkdf | omdf | Mhdf | oldf | ghfdf | nfdf | Hhdf |
| 99.3 | 83 | 97 | 120 | 80 | 21 | 145 | godf | oodi | Nidf | omdf | ghfdf | nfdf | Hgdf |
| 98.2 | 84 | 98 | 119 | 80 | 20 | 145 | gndf | ondh | Njdf | ondf | ggodf | nfdf | Hfdf |
| 100 | 85 | 99 | 120 | 80 | 19 | 145 | gidf | gffdf | Nkdf | oodf | ghfdf | nfdf | Godf |
| 102 | 86 | 99 | 118 | 80 | 12 | 145 | gidf | gfhdf | Nldf | oodf | ggodf | nfdf | Ghdf |
| 98.2 | 87 | 98 | 120 | 80 | 12 | 100 | hgdf | omdh | Nmdf | ondf | ghfdf | nfdf | Ghdf |
| 98.6 | 88 | 97 | 118 | 80 | 12 | 110 | hhdf | omdl | Nndf | omdf | ggndf | nfdf | Ghdf |
| 98.6 | 89 | 96 | 120 | 81 | 13 | 120 | hidf | ondi | Nodf | oldf | ghfdf | ngdf | Gidf |
| 98.3 | 80 | 95 | 140 | 82 | 14 | 130 | hmdf | ondi | Nfdf | okdf | gjfdf | ngdf | Gjdf |
| 99 | 81 | 94 | 122 | 85 | 15 | 140 | hodf | oodf | Ngdf | ojdf | ghhdf | nkdf | Gkdf |
| 100 | 82 | 94 | 123 | 90 | 16 | 110 | ifdf | gffdf | Nhdf | ojdf | ghidf | ofdf | Gldf |
| 98.3 | 73 | 95 | 150 | 89 | 17 | 119 | ihdf | ondi | Midf | okdf | gkfdf | nodf | Gdf |
| 98.1 | 74 | 96 | 160 | 88 | 18 | 128 | iodf | ondg | Mjdf | oldf | glfdf | nndf | Gndf |
| Factors | DES | 3DES | AES | EDES | BCHASH |
|---|---|---|---|---|---|
| Key Length (bits) | 56 | 112, 168 | 128, 192 or 256 | 1024 | 56 |
| Cipher Type | Symmetric | Symmetric | Symmetric | Symmetric | Symmetric |
| Block Bits | 64 | 64 | 128 | 128 | 64 |
| Possible Key | |||||
| Time to Encrypt real-time data | 7 s | 21 s | 13 s | 2 s | 0.6 ms |
| Security | Passing | Passing | Secure | Secure | Secure |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kommuri, K.; Kolluru, V.R. Development of a Modified Medical Data Transmission over the Cellular Network System to Secure Health-Related Data from Changes in Environmental Parameters. Eng. Proc. 2023, 59, 153. https://doi.org/10.3390/engproc2023059153
Kommuri K, Kolluru VR. Development of a Modified Medical Data Transmission over the Cellular Network System to Secure Health-Related Data from Changes in Environmental Parameters. Engineering Proceedings. 2023; 59(1):153. https://doi.org/10.3390/engproc2023059153
Chicago/Turabian StyleKommuri, Krishnaveni, and Venkata Ratnam Kolluru. 2023. "Development of a Modified Medical Data Transmission over the Cellular Network System to Secure Health-Related Data from Changes in Environmental Parameters" Engineering Proceedings 59, no. 1: 153. https://doi.org/10.3390/engproc2023059153
APA StyleKommuri, K., & Kolluru, V. R. (2023). Development of a Modified Medical Data Transmission over the Cellular Network System to Secure Health-Related Data from Changes in Environmental Parameters. Engineering Proceedings, 59(1), 153. https://doi.org/10.3390/engproc2023059153





