Abstract
Digital evidence is a critical component in today’s organizations, as it is the foundation on which any certification is based. This paper presents a risk assessment of evidence in the certification domain to identify the main security risks. To mitigate these risks, it also proposes an adaptation of an existing Blockchain-based audit trail system to create an evidence trustworthiness system enhancing security and usability. This system covers specific additional requirements from auditors: evidence confidentiality and integrity verification automation. The system has been validated with cloud service providers to increase the security of evidence for a cybersecurity certification process. However, it can be also extended to other certification domains.
1. Introduction
Certifications have become increasingly important as a formal recognition of specific characteristics, skills, or knowledge []. They are a proof that some regulations or standards have been met and the necessary competencies are possessed, achieving a commitment to quality and excellence. For organizations, certifications can generally enhance customer confidence and satisfaction []; they are more likely to trust and choose certified products and services, knowing that they meet high standards of quality and safety. That is why the number of certifications has greatly increased in recent years. For example, the International Organization for Standardization (ISO) has presented a survey [] in which the number of ISO-based issued certifications is presented for 2023.
Auditors play a critical role in certification processes by ensuring that organizations comply with specific standards and regulations. One of their primary tasks is to assess the effectiveness of organization systems based on various evidence. Evidence is essential for certification for the following reasons [,]:
- Evidence offers solid confirmation that an entity complies with the specific requirements of a regulation or standard. This verification is essential to ensure that the certification is grounded in factual and precise information.
- The presentation of evidence fosters trust and credibility among stakeholders, such as auditors, regulators, or even customers. It demonstrates that a given certification is more than a formality, being supported by verifiable data.
- Evidence guarantees transparency in any certification process, enabling all involved parties to understand the foundation upon which the certification was awarded, fostering openness and accountability.
- Evidence is essential during audits and reviews to demonstrate compliance with standards. It helps auditors verify that processes and practices comply with the required criteria.
- In numerous industries, presenting evidence is a legal requirement to ensure that organizations adhere to all pertinent laws and regulations.
- Evidence-based certification eliminates subjectivity from the process. Decisions are grounded in objective data rather than opinions, ensuring both fairness and consistency.
In conclusion, evidence is crucial in a certification process as it provides the essential proof that specific requirements have been met. This includes documentation, records, test results, and other forms of verification that confirm compliance with the certification criteria. Without robust evidence, validating the authenticity and reliability of the certification would be difficult. However, nowadays, evidence refers to digital evidence. which raises a number of security issues that need to be addressed [,]:
- Digital evidence is particularly vulnerable to tampering, and any unauthorized modifications can undermine its integrity.
- Inherent volatility in digital evidence means that mishandling during collection, storage, or transfer can lead to data loss or corruption.
- Maintaining the long-term integrity of digital evidence is complex. Conventional storage solutions often fail to prevent data degradation and loss over time.
To mitigate these risks, it is crucial to follow strict protocols for the management, storage, and transfer of digital evidence. Thus, auditors are increasingly demanding digital audit trail systems as security measures to improve the integrity, traceability, and accessibility of crucial information related to the certification process, such as evidence []. At the same time, these systems streamline certification processes, simplifying auditing and saving time and effort. Thus, they play a crucial role in a certification process, as they result in greater acceptance and credibility for the certified entity.
This work analyses the main security risks of evidence for a certification process and presents how an already existing audit trail solution based on Blockchain technology can be adjusted to guarantee evidence trustworthiness. Blockchain inherently ensures integrity due to its resistance to tampering. Moreover, data on the Blockchain are immediately accessible to all authorized parties, which enhances transparency and reduces the costs and time associated with audits. For these reasons, it is a suitable technology for an evidence trustworthiness system in certification.
This paper is organized as follows: Section 1 describes the research methodology followed, which starts with the work gathered in Section 3, which describes a complete risk assessment of evidence in a certification process and identifies the main mitigation actions required. Then, Section 4 describes the proposed evidence trustworthiness system for certification, focusing on its architecture and novel features. The validation of the system and the main results are presented in Section 5, highlighting how the proposed evidence trustworthiness system outperforms existing solutions from the literature. Finally, Section 6 explains the main conclusions of the work.
2. Research Methodology
This paper tries to assist in the implementation of trustworthy certification processes through secure evidence. However, it is not yet clear how the evidence should be secured. That is why this research work attempts to clarify the requirements for evidence security and to propose an aligned security system. Figure 1 illustrates the methodology followed in this research work. As introduced in Section 1, current certification processes are based on evidence that must be secured in terms of integrity, traceability, and transparency to be trustworthy (objective definition). Thus, a security risk assessment of evidence is needed to identify their main risks and the corresponding required mitigation actions, which can be considered as the desirable features of an evidence trustworthiness system for certification (requirements identification). It is well known that Blockchain is a technology that provides several security features by design (useful technology). For this reason, Blockchain technology will backbone the creation of an evidence trustworthiness system. The solution is then validated in the cybersecurity domain (more details in Section 5).
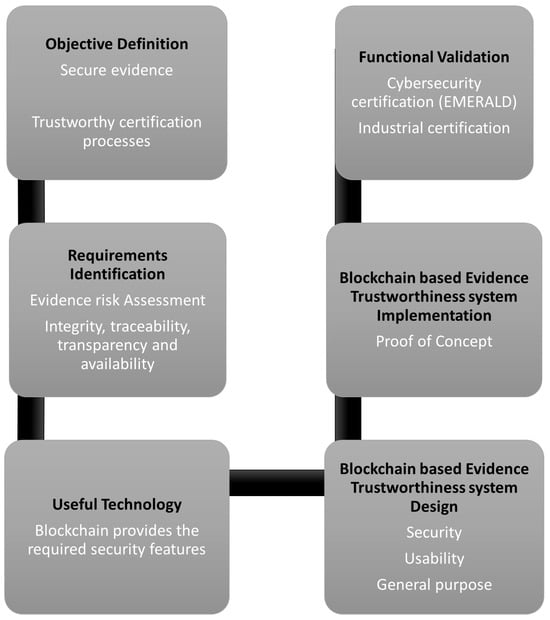
Figure 1.
Research methodology followed for this work.
3. Evidence Security
Ensuring trustworthiness in certification is particularly crucial for potentially vulnerable and sensitive information, such as evidence supporting certification. Several risk assessment studies have already been carried out in the literature [,] identifying potential threats and vulnerabilities that could affect evidence. However, these studies need to be extended, considering the particularities of the certification context. This paper analyzes the existing security risks in a certification process, identifying the main mitigation measures that should be considered. This research adheres to a standardized approach aligned with the NIST guidelines [].
3.1. Risk Assessment
Once the assets to be protected are clear (evidence supporting a certification process), it is necessary to identify the users and their permissions. Evidence for a certification should be provided manually by organization employees in charge of the certification process (e.g., compliance analyst, internal control owner, etc.), or even automatically by evidence gathering tools [,]. Once stored, the evidence must be accessible but not modifiable by the same organization employees or auditors in charge of the certification process (e.g., the Conformity Assessment Body (CAB)).
The protection goals of the evidence need to be defined. Information assurance involves managing the risks associated with the use, processing, storage, and transmission of evidence. The primary protection goals are confidentiality, integrity, and availability (CIA) []. Additionally, authenticity, authorization, and nonrepudiation can also be considered. Table 1 summarizes the main weaknesses and threats for the different protection goals that might facilitate potential attacks to breach the security of evidence.

Table 1.
Description of the main potential attacks to evidence.
- Confidentiality ensures that the information remains inaccessible and undisclosed to unauthorized entities. Maintaining the confidentiality of evidence is crucial in a certification process, as such evidence often contains sensitive information.
- Integrity involves maintaining the accuracy and consistency of the evidence, ensuring that it remains unchanged. During the certification process, auditors depend on the integrity of the evidence to issue certificates and, therefore, require total confidence in it.
- Availability refers to the accessibility and usability of evidence when auditors require it. Although not mandatory for a certification process, ensuring high availability of evidence is highly recommended.
- Authenticity ensures that the evidence is authentic and comes from a verified source. This is related to the authentication of the evidence sources.
- Authorization refers to access levels or user privileges for different assets, including information. In a certification context, it is essential to control who can provide or access the evidence.
- Non-repudiation is the ability to prove that an event has occurred and to identify its originating entities. In certification, non-repudiation is crucial, as sources providing evidence should not be able to deny their involvement.
Once threats have been identified, it is crucial to recognize potential attackers []. These attackers are generally classified into two main groups: outsiders and insiders. Outsiders, who refer to actors outside the organization, are usually classified into three categories according to their experience: organized attackers (well trained, well funded, and with considerable scientific capabilities), hackers (highly skilled malicious intruders seeking monetary gain or with political motives) and amateurs (limited skills, and less dangerous). Alternatively, insiders are usually within or closely associated with the organization. They have expertise, knowledge, resources, and access to the organizational systems, and they may also have detailed knowledge of the security measures in place for evidence storage. Table 2 summarizes the main motivations of the different attackers to gain access to evidence related to a certification process.

Table 2.
Overview of main motivations for different attackers.
The likelihood of the weaknesses from Table 1 resulting in success in an attack against the evidence storage has been measured in Table 3. It depends mainly on the motivation and capacity of the attackers, the nature of the vulnerability, and the existence of countermeasures in the system. The likelihood has been ranked as follows:

Table 3.
Likelihood of different attacks to happen.
- High: The attacker is highly motivated and sufficiently capable; current controls to prevent the vulnerability are inefficient.
- Moderate: The attacker is motivated and capable, but controls are in place.
- Low: The attacker lacks motivation and/or capability, or controls are in place to prevent or at least significantly impede the vulnerability.
The different attacks have variable impacts on the organization, affecting it to a greater or lesser extent, as gathered in Table 4. The impact has been ranked as follows:

Table 4.
Overview of effect and impact of the potential attacks.
- High: There is a strong need for corrective measures.
- Moderate: Corrective actions are needed, and a plan must be developed to incorporate these actions over a reasonable period of time.
- Low: It must be decided whether corrective actions are required or whether the risk can be accepted.
The impact of the identified attacks is considered moderate when only access to data is obtained, or high when it is also possible to modify or remove them, making it impossible to carry out a proper audit and obtain a certificate. The combination of the likelihood of an attack and its impact on the organization determines the security risk, following the risk matrix of Table 5 and based on the risk level guide in []. The higher a risk ranks for both factors, the greater threat it poses to the evidence, and its mitigation is essential (very high). In contrast, low likelihood and low impact mean low risk and priority for mitigation. For intermediate combinations, the impact has been considered to be more relevant than the likelihood of the attack, so that even with low likelihood, if the impact is moderate, the risk is also moderate. As the probability increases, so does the risk of the same impact.

Table 5.
Risk matrix.
Based on the risk matrix, Table 6 defines the risk value for the potential attacks identified in Table 3.

Table 6.
Overview of the risk of the potential attacks.
Taking into account the risk values in Table 6, some important mitigation techniques have been identified to reduce or even eliminate the identified risks.
- Strong user access control techniques are required to limit access to evidence only to authorized users.
- Encryption and anonymization techniques are employed to protect the privacy of evidence [].
- Integrity must be guaranteed to detect evidence manipulation.
Taking these security requirements into account, a trustworthiness system is required to secure evidence for a trusted certification process. It provides access control to evidence and guarantees its accuracy and trustworthiness while avoiding its disclosure.
3.2. Risk Mitigation
Blockchain technology is increasingly being recognized as a suitable technology for auditing due to its key features: decentralization, transparency, traceability, immutability, and integrity protection [,,]. However, traditional databases and replicated databases are also worth considering.
Blockchain and traditional databases might seem similar, as both are used to store information in a distributed or centralized manner. However, Blockchain offers more than just data storage []. Here are several key differences between the two technologies.
- Authority:
- -
- In Blockchain, each node participates in a consensus mechanism to verify transactions, providing equal access and capabilities, thus democratizing the system.
- -
- Traditional databases, on the other hand, are controlled by a central authority (administrator), making Blockchain advantageous as it eliminates the need for trust by design.
- Architecture:
- -
- Blockchain distributes data across all nodes, and each node stores a copy of the entire Blockchain. This setup ensures that even if some nodes are compromised, the system remains operational, making single-point failure infeasible.
- -
- Traditional databases store data centrally on a server, which is more vulnerable to attacks.
- Data Handling:
- -
- In Blockchain, data cannot be deleted; once recorded, it remains forever. For an audit trail, updating evidence is not necessary, as any update is considered new evidence. Deleting existing information is also not a requirement for an audit trail; in fact, not being able to remove information is beneficial to the transparency and trustworthiness of the audit solution.
- -
- Traditional databases offer more functionalities, such as updating and deleting data.
- Integrity:
- -
- Blockchain ensures data integrity through a consensus mechanism where all nodes validate transactions and store a copy of the entire Blockchain, making it nearly impossible for a malicious actor to alter the data.
- -
- Traditional databases are more vulnerable if the administrator is compromised.
- Transparency:
- -
- In Blockchain, all nodes have the same access and capabilities, ensuring transparency by design.
- -
- In traditional databases, the administrator controls who can access the data and what actions they can perform.
- Implementation and Maintenance Costs:
- -
- Blockchain is a relatively new technology, and its implementation and maintenance are generally more expensive than traditional databases. However, as Blockchain technology becomes more widespread, these costs are decreasing.
- -
- Traditional databases have more contained and predictable costs.
- Performance:
- -
- Blockchain is slow due to additional operations like signature verifications and consensus mechanisms. However, although desired, high performance on audit trails is not an essential requirement.
- -
- Traditional databases, however, are known for their fast execution times and the ability to handle large volumes of data.
Some of the main disadvantages of traditional databases can be mitigated through replication techniques, which involve copying data from one database to another, resulting in a distributed database system where all databases contain the same information []. However, Blockchain still differs from replicated databases in the following ways:
- Replication:
- -
- Blockchain replicates entire transactions, allowing each participant node to replay the execution. In addition, it operates without a trusted central entity, replicating entire transactions for replay by each node.
- -
- In contrast, distributed databases replicate the resulting log of read and write operations. A distributed database management system is required to ensure that updates, additions, and deletions in one database are automatically reflected in all others.
- Concurrency:
- -
- Most Blockchains support only serial execution because the consensus mechanism, rather than transaction execution, is typically the performance bottleneck. This ensures deterministic behaviour of smart contracts when transactions are replicated across many nodes, making ledger states easier to identify. Although concurrency is not a major concern for an audit trail, some Blockchains, like Hyperledger Fabric, have started adopting simple concurrency techniques, such as executing transactions in parallel against ledger states before ordering.
- -
- In contrast, distributed databases use sophisticated concurrency control mechanisms to maximize concurrency and improve performance.
As has been demonstrated, Blockchain outperforms databases in all aspects that are relevant to an evidence trustworthiness system: central authorities are not needed; the availability is higher due to the distribution of nodes; integrity and trustworthiness is enhanced as information cannot be updated or removed; and transparency is increased with equal capabilities for all users and complete replication of transactions in all nodes.
Moreover, although performance is usually limited, some Blockchain technologies, such as permissioned, already employ different techniques, such as novel consensus algorithms, larger block sizes, or some initial concurrency techniques, achieving quite appropriate performance values for a trustworthiness system, which is an application with not very demanding time requirements.
With regard to costs, Blockchain-based solutions require high initial costs, as specialized knowledge, infrastructure, and technology are needed. In addition, operational costs are also usually higher due to maintenance tasks, as well as energy consumption (although the consumption is reducing with novel consensus algorithms). However, although other solutions may initially be more cost-effective, they could result in higher expenses in the long term due to intermediaries, security issues, and less automation.
4. Secure Evidence Trustworthiness System
Several proposals are already being made in the literature to guarantee the reliability of evidence []. In fact, the use of Blockchain has recently been considered for audit purposes [,,]. However, there are solutions that have already been created with particular domains in mind, such as [,,,] for the pharmaceutical, health, banking, and trading sectors, respectively, that do not consider the particularities of evidence considered inside a certification process. In addition, technical details are not often fully explained, and usability is usually not taken into account in spite of its growing importance [] and the demand of auditors [,].
Not all Blockchain technologies are suitable [] for an evidence trustworthiness system. Public Blockchain networks, which are open to the public and that anyone can join without specific permission, are not suitable. In addition, all users who join the network can read, write, and participate in this network that is not controlled by anyone in particular. In contrast, permissioned Blockchains are based on invitation, and anyone who wants to access it must ask for permission from the governing body of the Blockchain. They allow different levels of access that determine which users can write, read, and audit the Blockchain. This control is required in an evidence trustworthiness system, in which the network should not be publicly accessible. Additionally, a permissioned Blockchain requires fewer nodes to be set up, making the network faster, more efficient, and more convenient in terms of time and energy consumption. Lastly, they can be free, which is highly beneficial for an evidence trustworthiness system in which numerous evidence records can be stored.
Currently, the European Commission is actively supporting the development of Blockchain technology through various public initiatives under the European Blockchain Strategy, recognizing its significant potential to transform industries and improve the lives of citizens across Europe. One such initiative is the European Blockchain Services Infrastructure (EBSI), a network of nodes distributed throughout Europe that provides cross-border digital public services in compliance with European regulations, ensuring the highest standards of security and privacy []. The primary goal of EBSI is to leverage Blockchain technology to enhance interactions between citizens, governments, and businesses. It is the first EU-wide Blockchain infrastructure, driven by the public sector to support cross-border applications such as traceability, verifiable credentials, trusted data exchange (as could be the case in an evidence trustworthiness system), or IP management across multiple domains. Thus, EBSI is a suitable Blockchain ecosystem where one can deploy a European evidence trustworthiness system. EBSI leverages Hyperledger Besu [], which is an Ethereum client suitable for not only public but also private permissioned Blockchain network use cases, such as the trustworthiness system. As EBSI is considered a suitable Blockchain ecosystem in which to deploy a European trustworthiness system, and it uses Hyperledger Besu, the suggested Blockchain-based evidence trustworthiness system for certification should be based on Ethereum-like technologies.
In this sense, the Blockchain-based audit trail system presented by the authors in [] has been considered as the basis for the evidence trustworthiness system. It is a multi-domain general purpose audit trail solution in which usability is prioritized, technical details are described, and several features that are really useful for an evidence trustworthiness system in certification are covered.
- Inalterability: Ensuring the integrity of evidence is crucial, and Blockchain guarantees this by design.
- Long-term maintenance: Evidence must remain accessible even years after certification expiration, which Blockchain ensures as long as the network is operational.
- Assurance of origin: Tracing the provider of evidence is essential, and permissioned Blockchain guarantees this through signed transactions.
- Adaptability: The audit trail solution can be adapted to the particularities of each application domain.
- High Usability: Trustworthiness systems must be user-friendly for non-technicians involved in certification processes. The Blockchain monitor included in the design to access evidence records via a browser makes the use of Blockchain transparent.
However, there are some aspects that need to be improved in the certification domain.
- Confidentiality: Evidence is usually considered sensitive information that should not be directly recorded on the Blockchain to avoid privacy issues. Integration with existing databases should be enabled.
- Automation: Auditors often require automatic processes to facilitate the certification process.
For these reasons, the audit trail solution considered has been adapted and extended to cover the particularities of an evidence trustworthiness system for certification. As a reminder, the Blockchain network considered by this audit trail solution is a private Quorum deployment in which smart contracts with administrative and auditing functionalities are provided. Quorum is a permissioned implementation of Ethereum, designed to support data privacy and alternative consensus mechanisms []. Although EBSI is based on Hyperledger Besu, implementations over Quorum are also consistent with EBSI. Quorum was specifically tailored for enterprise needs with a modular and secure design and optimized performance for private transactions. Hyperledger Besu, on the contrary, is more generalist and has a broader focus, which may lead to lower performance [,].
Additionally, Blockchain events are automatically emitted every time a piece of information is recorded. These events feed the Blockchain Monitor, based on Elastic stack, providing a mechanism for external users to access the information recorded on the Blockchain. This mechanism improves the usability of the Blockchain technology, but still requires manual interaction.
The architecture of the audit trail solution considered has been updated according to Figure 2, where the previously implemented components are shown in gray, while the extensions are shown in green.
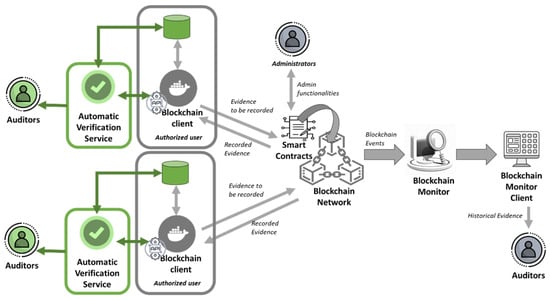
Figure 2.
Evidence trustworthiness system for certification (extended []).
4.1. Sensitive Evidence
Although the audit trail considered was based on directly recording the raw information on the Blockchain, this is not an option for evidence. Evidence is considered sensitive information, and consequently, it should not be recorded on the Blockchain. Even in permissioned networks with highly secure access solutions, information recorded on the Blockchain can never be removed, which contravenes current data protection laws, such as the General Data Protection Regulation (GDPR) []. To ensure data integrity without revealing any input data, evidence is not directly stored in the Blockchain. Instead, evidence remains in a secure local storage and just hashes of the pieces of evidence are stored in the Blockchain.
A hash function is a mathematical algorithm that converts any input data into a unique string of characters []. It is important to note that even the smallest change in the input data will generate a completely different hash. Moreover, reversing the process to return to the original input data is practically impossible. These features make this method secure for various sensitive applications, such as digital certificates, unique signatures for sensitive or secret documents, digital identification, and key storage. In this sense, hashes help verify that the information has not been tampered with, while keeping the information private by design. SHA2-256 is considered a suitable hashing function due to its wide standardization, robust security, and balanced performance [].
However, the deterministic nature of hashing increases the likelihood of identifying the original data when it has a low degree of order (it contains little information and the range of possible values is limited), making re-identification easier through brute force and dictionary attacks []. This degree of order in the data is known as entropy. Higher entropy means a dataset contains more information and the range of possible values is wider, reducing the risk of re-identification. In the context of evidence, high entropy is virtually guaranteed, as it usually contains raw data which do not adhere to any specific format or schema and have no specific size (any kind of evidence could be included), so its entropy is considered high by default. Moreover, details such as timestamps, usually included as information related to the evidence, also have a high variability. If there were some low-entropy pieces of evidence whose hash values could be easily broken, the entropy would have to be increased by adding a random number. This random number needs to be locally stored and associated with the evidence itself in order to allow the recalculation of the correct hash to be compared with the one recorded on the Blockchain and be able to determine if evidence has been tampered with.
Thus, the information to be recorded in the Blockchain is, at least, the hash of the raw evidence (considering the random number, if applicable) and an identifier of the piece of evidence. Moreover, any additional non-sensitive contextual information such as evidence origin, evidence gathering tool, timestamp, etc., can be also recorded in the Blockchain to increase the utility of the system (i.e., filters application). The information recorded on the Blockchain is accessible in a user-friendly way through the Blockchain monitor from the considered audit trail solution. It provides dashboards accessible through the browser to obtain the recorded evidence hashes from the Blockchain by the evidence identifier. In contrast, raw evidence remains stored in any existing local storage of the organization as long as the information is accessible by auditors in a manual way to be able to verify its integrity. This registration process is shown in the sequence diagram in Figure 3.
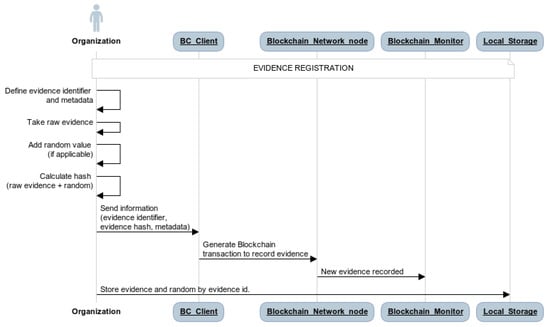
Figure 3.
Registration of evidence in the evidence trustworthiness system.
Taking everything into account, the process for verifying the integrity of evidence is as follows:
- Any authorized user defines an evidence identifier, calculates the evidence hash, and records it in the Blockchain. The raw evidence is securely stored in the local storage of the organization that prepares the certification process.
- -
- If the evidence is considered easy to deduce, a random number should also be added to the evidence before calculating the hash. This random number is also stored in secure local storage, linked to the value of the raw evidence.
- Subsequently, when an auditor needs to verify the integrity of evidence, he retrieves the recorded hash of the evidence by the evidence identifier through the Blockchain monitor.
- The auditor can also retrieve the current evidence value (and the random number, if applicable) using the evidence identifier from local storage, apply the hash function, and manually compare the result with the hash value from the Blockchain. If the hash remains unchanged, the evidence value is intact; if the hash differs, the evidence has been tampered with and cannot be trusted.
Although the Blockchain monitor makes the use of Blockchain transparent to the auditors, they still need perform do manual work to compare local hashes of evidence with recorded hashes of evidence. Moreover, every manual process can lead to intentional or unintentional errors, which could seriously affect the certification process. This manual integrity verification process is shown in Figure 4.
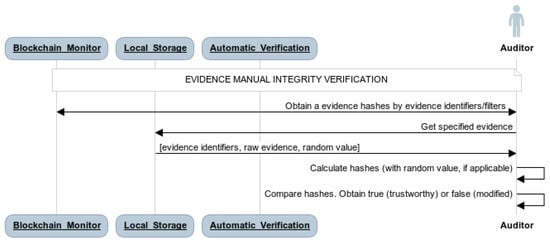
Figure 4.
Manual integrity verification in the evidence trustworthiness system.
4.2. Automatic Integrity Verification
Auditors need an automated method to verify the integrity of evidence, complementing manual access to hashes and additional information available through the Blockchain monitor, and reducing the possibility of errors. For this reason, an automatic verification service has been included to enhance usability and provide automatic evidence integrity checks.
The automatic verification service allows automatic integrity verification of: (i) all the pieces of evidence locally stored; (ii) a portion of them according to the application of specific filters based on the defined metadata; or (iii) a given piece of evidence identified by the evidence identifier. It provides a graphical interface to define the pieces of evidence whose integrity is to be verified. It automatically executes the manual process explained in Section 4.1, as can be shown in the sequence in Figure 5.
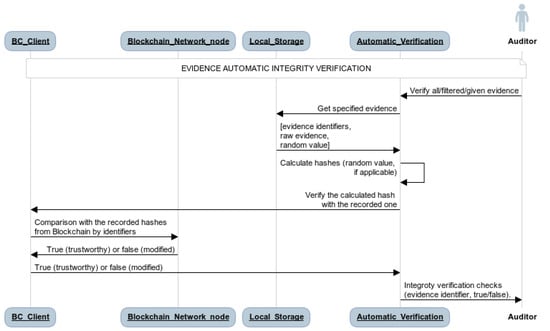
Figure 5.
Automatic integrity verification in the evidence trustworthiness system.
- Obtain the desired raw evidence (and the random values, if applicable) and the evidence identifiers from the local storage and calculate the corresponding hashes.
- Send the calculated hash to the Blockchain in order to be securely compared with the recorded one based on the evidence identifier. The comparison result is securely obtained in the smart contract, indicating true (trustworthy) or false (modified). In this case, the information is obtained through the REST API of the Blockchain client (instead of using the Blockchain monitor).
In this case, local storage requires the exposing of a REST API for easy interaction with the automatic verification service, as well as the definition of filters based on the defined metadata for the identification of pieces of evidence of interest.
5. Validation and Results
5.1. Cybersecurity Certification
The evidence trustworthiness system was included and validated within the MEDINA framework developed within the H2020 MEDINA project [] for the cybersecurity certification of cloud services. The MEDINA framework is currently being evolved within the EMERALD Horizon Europe project, currently under development [].
EMERALD is a security framework for continuous audit-based certification in compliance with European cloud security certification schemes. It is based on a continuous and automatic gathering and evaluating process of evidence in order to have a secure operational service certifiable through a given conformity assessment method. EMERALD includes a local evidence storage where raw evidence is saved. However, this storage cannot be considered secure since, as introduced in Section 3, the stored information could be modified. In this context, the trustworthiness system improves the trustworthiness of the evidence collected, providing a reliable and transparent source of evidence for the auditors. In EMERALD, not only evidence but also conformity assessment results are stored in the trustworthiness system. The EMERALD framework is designed so that its assessment results are considered valid evidence for the auditors of cloud services security certification processes. Therefore, it was decided to prepare the trustworthiness system to store the assessment results as well. Figure 6 shows the data model of information to be recorded in the trustworthiness system.
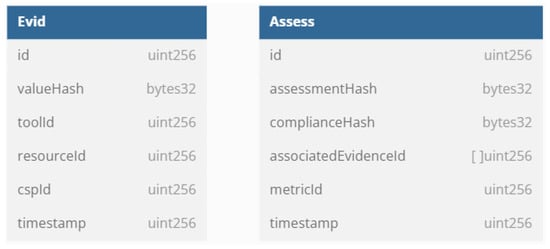
Figure 6.
Data model for the trustworthiness system.
As mentioned in Section 4.1, the evidence identifier (id), the timestamp, and the hash of the raw evidence (valueHash) are always stored. Raw evidence does not conform to any specific format or schema and has no fixed size (any type of evidence can be included), thus its entropy is inherently high. Additionally, EMERALD adds some contextual details such as the cloud service (cspId) and the resource (e.g., compute instances, databases, storage, networking, and auxiliary services) (resourceId) that the evidence refers to; it also adds the tool with which the evidence has been automatically gathered (toolId).
In the case of the assessment results, the assessment id (id), the timestamp, and two hashes are recorded. These hashes refer to the security assessment result from the EMERALD framework, as well as the compliance result. Similarly to the raw evidence, the assessment results do not follow any particular format or schema, and thus their entropy is considered high by default. However, the compliance result has a very low entropy. It refers to the positive or negative result of compliance with the assessment process. It is a Boolean value, so it can only have two possible values: true or false. This makes it relatively easy to compromise security. To mitigate this, the entropy is increased by appending a random 256-bit value to the positive or negative compliance result, as introduced in Section 4.1. As a result, entropy increases and security improves. Furthermore, the contextual details in this case are the metric against which the conformity assessment is executed (metricId) and the evidence that has been considered for the assessment (associatedEvidenceId).
All evidence values and evaluation results are recorded in the evidence trustworthiness system following the data models in Figure 6 to guarantee their integrity and transparency. The Blockchain monitor provides a graphical dashboard to access the information recorded on the system through a browser. The dashboard adapted to the context of EMERALD is shown in Figure 7, where the details of the recorded values of different pieces of evidence and assessment results are shown. Filters for different contextual details have been implemented to improve the usability of the tool for auditors. This tool allows the manual verification process described in Figure 4 by manually obtaining the hash of the evidence or the assessment result from the dashboard, accessing the local storage where the raw evidence or assessment result is stored, calculating its hash and comparing it with the one obtained from the Blockchain monitor.
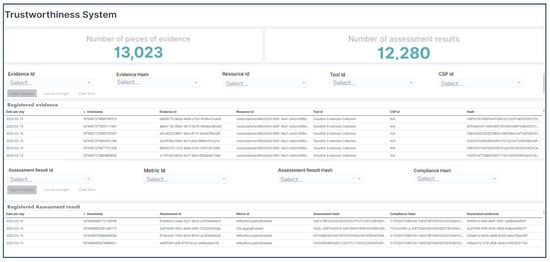
Figure 7.
Trustworthiness system dashboard.
Auditors also need an automated method to verify the integrity of evidence and assessment results, in addition to manually accessing their hashes and contextual information through the Blockchain monitor. The automatic verification service fulfils this requirement by providing a tool that allows auditors to automatically validate evidence and assessment results from the local storage against the Blockchain records.
The automatic verification service allows automatic verification of all locally recorded evidence and assessment results. As a result, the list of identifiers of the available evidence or assessment results is shown, as well as their integrity verification results. If the integrity verification is positive (hashes match), a green result is shown. In contrast, if the integrity verification is negative (hashes are different), a red result is shown, meaning that the evidence or the assessment result has been modified in some way and cannot be considered trustworthy. Moreover, if the hash of some of the evidence or assessment results cannot be found in the Blockchain because it has not been previously recorded (e.g., old evidence from before using the evidence trustworthiness system), a “Not found” message will be shown, meaning that the trustworthiness cannot be guaranteed for better or worse. Figure 8 shows an example of the complete list of recorded evidence where a negative integrity verification result has been detected.
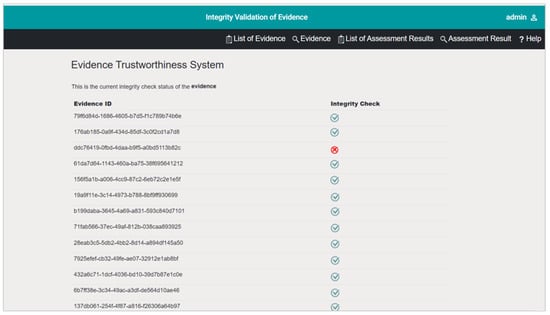
Figure 8.
Integrity verification service for recorded evidence.
This process is likely to take considerable time to complete and will grow with the number of pieces of evidence or assessment results to be validated. However, there are situations where it is not required to verify all of them (e.g., in cases of reassessment due to a particular nonconformity). For this reason, the integrity verification service also allows the application of filters based on the contextual information defined in the data model in Figure 6. Figure 9 shows an example in which two different filters have been created for the contextual information of the evidence: the cloud service identifier to which it refers (cspId in Figure 6), and the identifier of the tool used to gather the evidence (toolId in Figure 6). The application of these filters results in a reduction in the number of results from the list shown in Figure 8 to only those that meet the filters values. Thus, the execution time will be shorter. Any of the attributes considered in Figure 6 could be considered as filters.
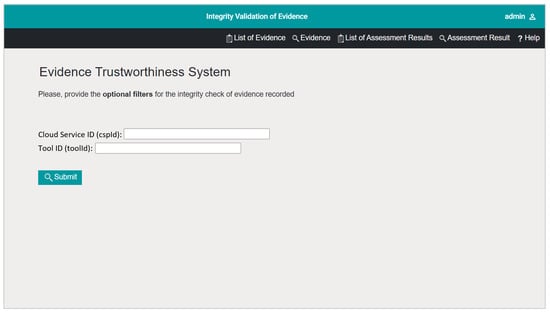
Figure 9.
Integrity verification service filters definition.
It is also possible to verify the integrity of a particular evidence or assessment result. For this purpose, a filter for the identifier of the evidence or the assessment result is defined to limit the results of Figure 8 to the single evidence or assessment result of interest. This execution is virtually instantaneous.
As a result, the evidence trustworthiness system offers a way to securitize evidence and assist in a trustworthy certification process, providing the following benefits:
- Improves the integrity, reliability and transparency of the evidence in 100% of cases.
- Increases auditor confidence, and certifications are completed in a shorter time, as auditors do not need to manually verify evidence, and thus, costs are reduced.
- Enhances problem detection. The automatic integrity check functionality provides an easy way to detect evidence tampering.
The proposed system is based on the existing audit trail solution from the literature [] which already outperformed existing solutions in terms of deep technical details, usability, and adaptability. This audit trail has been particularized to the certification domain considering the main particularities of evidence risk management (integrity, transparency, availability) and the essential requirements of a certification process (sensitive information confidentiality, contextual information, and automation). In this way, the risks identified in Section 3 are mitigated as explained in Table 7.

Table 7.
Mitigation justification of evidence risks in certification.
Regarding the performance, this will mainly depend on the specific features of the underlying Blockchain network. In particular, the following aspects are significant:
- Consensus mechanisms: These have traditionally been time-consuming, such as the Proof of Work used in Bitcoin. However, current solutions include simpler and faster alternatives, especially in permissioned networks such as that suggested for the trustworthiness system [,]. In this validation, the Raft consensus algorithm was considered with the default configuration []. Raft is well adopted in private networks such as Quorum due to its good performance and scalability [].
- Network Congestion: A congested network can cause high delays. However, permissioned networks are usually less congested because only a group of authorized participants can join the network, which reduces the number of nodes that need to validate transactions. This reduces overhead and improves efficiency []. In this validation, the deployment of a dedicated Quorum network ensures no congestion. However, in real-world implementations, such as the potential deployment in EBSI where the Blockchain network is shared by multiple services, some level of congestion is anticipated.
- Block size: A larger block can contain more transactions, but it can also increase processing time and latency. This is a configurable parameter determined by the Blockchain technology that needs to be optimized []. In this validation, the 64 kB default value for Quorum was considered. As the data to be recorded in the trustworthiness system (evidence and assessment result) is always lower than 1 kB considering the data model in Figure 6, a block can contain several transactions, improving the performance.
As can be seen, the fact that the proposed trustworthiness system is based on a permissioned network improves the performance and avoids unnecessary delays. In a real-world deployment, the configuration parameters need to be optimized in order to achieve improved performance.
5.2. Applicability to Other Domains
Although the evidence trustworthiness system has been implemented for cloud services cybersecurity certification, it can also be adapted to other certification domains that require the integrity and transparency of information to make it more reliable and compliant with specific standards []. Certifications are performed in a variety of domains such as health [], education [], information quality [], and environment []. All of these domains require an evidence trustworthiness system to help auditors rely on evidence and speed up and facilitate certification processes. The proposed evidence trustworthiness system has been designed in such a way that adaptations to other domains require simply to update the considered data model in two ways:
- Decide whether the evidence to be secured is sensitive information and only the hash of the information can be recorded on the Blockchain as explained in Section 4.1. In contrast, information can be directly recorded on the trustworthiness system, making verification even more user-friendly. For example, health-related evidence will almost always be considered sensitive, as it often involves personal data that must be protected according to the GDPR. In this case, the use of hashes as proof of integrity is recommended. However, there may be cases where the evidence relates to anonymized patient information, aggregated disease information, or even public information about drugs or treatments that do not require confidentiality. In these cases, the evidence can be recorded directly in the trustworthiness system, avoiding subsequent calculation and verification of hashes.
- Identify the metadata or contextual information to be considered for each domain, depending on its particularities. Following with the example in the health certification domain, the following contextual information are examples that could be considered to characterize health evidence:
- -
- Date and time of evidence collection.
- -
- Data source, identifying the source of the data, such as clinical records, research studies, or medical devices.
- -
- Collection method, defining how evidence was obtained, ensuring reproducibility and validity.
- -
- Environmental conditions, including location or specific conditions, if applicable.
6. Conclusions
This paper discusses the importance of evidence in certification, as it is crucial to verify compliance, foster trust, and ensure transparency. However, current digital evidence is vulnerable to several security attacks. Thus, a risk assessment has been carried out to identify the main security needs of evidence in the certification domain. Digital evidence is vulnerable to manipulation, loss, and integrity issues. To address these challenges, the authors have adapted an existing general-purpose Blockchain-based audit trail solution to the certification domain, as Blockchain features such as decentralization, transparency and immutability make it suitable for securing evidence for certification.
The trustworthiness system is based on storing hashes of evidence on the Blockchain while keeping the raw evidence in a local and private storage. In this way, data integrity is guaranteed without revealing sensitive information. In addition, the system includes an automatic integrity verification service to enhance usability, allowing auditors to verify evidence integrity efficiently. The proposed solution has been validated within the EMERALD framework for cloud services cybersecurity certification, demonstrating its effectiveness in improving the trust and transparency of evidence and assessment results for cybersecurity certification processes.
In conclusion, this paper highlights the critical role of secure and reliable evidence management in certification and presents a robust solution that uses Blockchain technology to ensure the trustworthiness of evidence.
As future work, the evidence trustworthiness system should be deployed in a general-purpose Blockchain network, such as EBSI, to create the European evidence trustworthiness system for auditors where different types of evidence integrity proofs can be stored. The benefits over current certification processes should be measured for both auditors and certified entities. In addition, the system should be considered in other certification domains in addition to cybersecurity to validate its generalizability and improve its impact.
Author Contributions
Conceptualization C.R. and B.U.; Methodology C.R. and B.U.; Software C.R. and B.U.; Validation C.R. and B.U.; Formal analysis C.R. and B.U.; Investigation C.R. and B.U.; Resources C.R. and B.U.; Data-curation C.R. and B.U.; Writing—original draft preparation C.R.; Writing—review and editing C.R. and B.U.; Visualization C.R. and B.U.; Supervision C.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by European Commission, H2020 MEDINA project, Security framework to achieve a continuous audit-based certification in compliance with the EU-wide cloud security certification scheme (GA 952633); and Horizon Europe EMERALD project, Evidence Management for Continuous Certification as a Service in the Cloud (GA 101120688).
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Pinolini, M. The importance of certification. J. Prot. Coatings Linings 2020, 37, 8–9. [Google Scholar]
- Sutawidjaya, A.H.; Mochtar, I.; Nawangsari, L.C. Quality certification and customer satisfaction. Eur. Res. Stud. J. 2018, XXI, 266–279. [Google Scholar] [CrossRef]
- ISO. ISO Survey 2023. 2024. Available online: https://www.iso.org/the-iso-survey.html (accessed on 3 November 2024).
- Teo, Y.; Shringarpure, S.; Jeong, H.; Prasannan, N.; Brecht, B.; Silberhorn, C.; Evans, M.; Mogilevtsev, D.; Sánchez-Soto, L. Evidence-based certification of quantum dimensions. Phys. Rev. Lett. 2024, 133, 050204. [Google Scholar] [CrossRef]
- Nair, S.; De La Vara, J.L.; Sabetzadeh, M.; Briand, L. An extended systematic literature review on provision of evidence for safety certification. Inf. Softw. Technol. 2014, 56, 689–717. [Google Scholar] [CrossRef]
- Nikkel, B. Fintech forensics: Criminal investigation and digital evidence in financial technologies. Forensic Sci. Int. Digit. Investig. 2020, 33, 200908. [Google Scholar] [CrossRef]
- Shah, M.S.M.B.; Saleem, S.; Zulqarnain, R. Protecting digital evidence integrity and preserving chain of custody. J. Digit. Forensics Secur. Law 2017, 12, 12. [Google Scholar] [CrossRef]
- Guttman, B.; White, D.R.; Walraven, T. Digital Evidence Preservation. NIST Interagency Report 2022. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2022/NIST.IR.8387.pdf (accessed on 5 November 2024).
- Shlonsky, A.; Wagner, D. The next step: Integrating actuarial risk assessment and clinical judgment into an evidence-based practice framework in CPS case management. Child. Youth Serv. Rev. 2005, 27, 409–427. [Google Scholar] [CrossRef]
- Berk, R.; Heidari, H.; Jabbari, S.; Kearns, M.; Roth, A. Fairness in criminal justice risk assessments: The state of the art. Sociol. Methods Res. 2021, 50, 3–44. [Google Scholar] [CrossRef]
- Ross, R.S. Guide for Conducting Risk Assessments. 2012. Available online: https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-30r1.pdf (accessed on 2 November 2024).
- van den Bos, J. Gathering Evidence: Model-Driven Software Engineering in Automated Digital Forensics. Ph.D. Thesis, Universiteit van Amsterdam, Amsterdam, The Netherlands, 2014. [Google Scholar]
- Tang, L.; Sun, Z.; Idnay, B.; Nestor, J.G.; Soroush, A.; Elias, P.A.; Xu, Z.; Ding, Y.; Durrett, G.; Rousseau, J.F.; et al. Evaluating large language models on medical evidence summarization. NPJ Digit. Med. 2023, 6, 158. [Google Scholar] [CrossRef]
- Yee, C.K.; Zolkipli, M.F. Review on confidentiality, integrity and availability in information security. J. ICT Educ. 2021, 8, 34–42. [Google Scholar]
- Chng, S.; Lu, H.Y.; Kumar, A.; Yau, D. Hacker types, motivations and strategies: A comprehensive framework. Comput. Hum. Behav. Rep. 2022, 5, 100167. [Google Scholar] [CrossRef]
- Varshney, G.; Kumawat, R.; Varadharajan, V.; Tupakula, U.; Gupta, C. Anti-phishing: A comprehensive perspective. Expert Syst. Appl. 2024, 238, 122199. [Google Scholar] [CrossRef]
- Zhao, Z.; Li, Z.; Zhou, Z.; Yu, J.; Song, Z.; Xie, X.; Zhang, F.; Zhang, R. DDoS family: A novel perspective for massive types of DDoS attacks. Comput. Secur. 2024, 138, 103663. [Google Scholar] [CrossRef]
- Pratomo, A.B.; Mokodenseho, S.; Aziz, A.M. Data encryption and anonymization techniques for enhanced information system security and privacy. West Sci. Inf. Syst. Technol. 2023, 1, 1–9. [Google Scholar] [CrossRef]
- Ahmad, A.; Saad, M.; Al Ghamdi, M.; Nyang, D.; Mohaisen, D. Blocktrail: A service for secure and transparent blockchain-driven audit trails. IEEE Syst. J. 2021, 16, 1367–1378. [Google Scholar] [CrossRef]
- Tysebaert, S.; Lloreda Sanchez, H.; Riviere, E.; Rath, A. AuditTrust: A blockchain-based secure audit trail for data sharing in distributed environment. Commun. Comput. Inf. Sci. 2022. [Google Scholar]
- Pu, S.; Lam, J.S.L. The benefits of blockchain for digital certificates: A multiple case study analysis. Technol. Soc. 2023, 72, 102176. [Google Scholar] [CrossRef]
- Chowdhury, M.J.M.; Colman, A.; Kabir, M.A.; Han, J.; Sarda, P. Blockchain versus database: A critical analysis. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1348–1353. [Google Scholar]
- Nicola, M.; Jarke, M. Performance modeling of distributed and replicated databases. IEEE Trans. Knowl. Data Eng. 2000, 12, 645–672. [Google Scholar] [CrossRef]
- Carcary, M. Advancing the research audit trail: A ten year retrospective. In Proceedings of the European Conference on Research Methods for Business & Management Studies, Aveiro, Portugal, 18–19 June 2020; pp. 56–62. [Google Scholar]
- Gokoglan, K.; Cetın, S.; Bılen, A. Blockchain technology and its impact on audit activities. J. Econ. Financ. Account. 2022, 9, 72–81. [Google Scholar] [CrossRef]
- Vincent, N.E.; Skjellum, A.; Medury, S. Blockchain architecture: A design that helps CPA firms leverage the technology. Int. J. Account. Inf. Syst. 2020, 38, 100466. [Google Scholar] [CrossRef]
- Sakshi; Malik, A.; Sharma, A.K. A survey on blockchain based IoT forensic evidence preservation: Research trends and current challenges. Multimed. Tools Appl. 2024, 83, 42413–42458. [Google Scholar] [CrossRef]
- Oakley, J.; Worley, C.; Yu, L.; Brooks, R.R.; Özçelik, İ.; Skjellum, A.; Obeid, J.S. Scrybe: A Secure Audit Trail for Clinical Trial Data Fusion. Digit. Threat. Res. Pract. 2023, 4, 1–20. [Google Scholar] [CrossRef] [PubMed]
- Pattengale, N.D.; Hudson, C.M. Decentralized genomics audit logging via permissioned blockchain ledgering. BMC Med. Genom. 2020, 13, 1–9. [Google Scholar] [CrossRef]
- Hashem, R.; Mubarak, A.R.I.; Abu-Musa, A. The impact of blockchain technology on audit process quality: An empirical study on the banking sector. Int. J. Audit. Account. Stud. 2023, 5, 87–118. [Google Scholar]
- Tian, X.; Zhu, J.; Zhao, X.; Wu, J. Improving operational efficiency through blockchain: Evidence from a field experiment in cross-border trade. Prod. Plan. Control 2024, 35, 1009–1024. [Google Scholar] [CrossRef]
- Ferreira, J.M.; Acuña, S.T.; Dieste, O.; Vegas, S.; Santos, A.; Rodríguez, F.; Juristo, N. Impact of usability mechanisms: An experiment on efficiency, effectiveness and user satisfaction. Inf. Softw. Technol. 2020, 117, 106195. [Google Scholar] [CrossRef]
- Sobrino-Duque, R.; Carrillo-de Gea, J.M.; López-Jiménez, J.J.; Nicolás Ros, J.; Fernández-Alemán, J.L. Usevalia: Managing Inspection-Based Usability Audits. Int. J. Hum. Comput. Interact. 2024, 40, 719–743. [Google Scholar] [CrossRef]
- Chen, F.; Meng, F.; Xiang, T.; Dai, H.; Li, J.; Qin, J. Towards usable cloud storage auditing. IEEE Trans. Parallel Distrib. Syst. 2020, 31, 2605–2617. [Google Scholar] [CrossRef]
- Miller, A. Permissioned and permissionless blockchains. In Blockchain for Distributed Systems Security; IEEE: Piscataway, NJ, USA, 2019; pp. 193–204. [Google Scholar]
- Williams, I. Cross-chain blockchain networks, compatibility standards, and interoperability standards: The case of european blockchain services infrastructure. In Cross-Industry Use of Blockchain Technology and Opportunities for the Future; IGI Global: Hershey, PA, USA, 2020; pp. 150–165. [Google Scholar]
- Fan, C.; Lin, C.; Khazaei, H.; Musilek, P. Performance analysis of hyperledger besu in private blockchain. In Proceedings of the 2022 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Newark, CA, USA, 15–18 August 2022; pp. 64–73. [Google Scholar]
- Regueiro, C.; Seco, I.; Gutiérrez-Agüero, I.; Urquizu, B.; Mansell, J. A blockchain-based audit trail mechanism: Design and implementation. Algorithms 2021, 14, 341. [Google Scholar] [CrossRef]
- Melissari, F.; Papadakis, A.; Chatzitheodorou, D.; Tran, D.; Schouteten, J.; Athanasiou, G.; Zahariadis, T. Experiences Using Ethereum and Quorum Blockchain Smart Contracts in Dairy Production. J. Sens. Actuator Netw. 2024, 13, 6. [Google Scholar] [CrossRef]
- Capocasale, V.; Gotta, D.; Perboli, G. Comparative analysis of permissioned blockchain frameworks for industrial applications. Blockchain Res. Appl. 2023, 4, 100113. [Google Scholar] [CrossRef]
- Pavlovics, A. JPMorgan’s Quorum Blockchain Performance Testing. 2018. Available online: https://scandiweb.com/blog/jpmorgan-s-quorum-blockchain-performance-testing/ (accessed on 17 December 2024).
- Voigt, P.; Von dem Bussche, A. The eu general data protection regulation (gdpr). In A Practical Guide, 1st ed.; Springer International Publishing: Cham, Switzerland, 2017; Volume 10, pp. 10–5555. [Google Scholar]
- Chi, L.; Zhu, X. Hashing techniques: A survey and taxonomy. ACM Comput. Surv. 2017, 50, 1–36. [Google Scholar] [CrossRef]
- Rawal, B.S.; Kumar, L.S.; Maganti, S.; Godha, V. Comparative Study of Sha-256 Optimization Techniques. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 387–392. [Google Scholar]
- Alkhwaja, I.; Albugami, M.; Alkhwaja, A.; Alghamdi, M.; Abahussain, H.; Alfawaz, F.; Almurayh, A.; Min-Allah, N. Password cracking with brute force algorithm and dictionary attack using parallel programming. Appl. Sci. 2023, 13, 5979. [Google Scholar] [CrossRef]
- Orue-Echevarria, L.; Garcia, J.L.; Banse, C.; Alonso, J. MEDINA: Improving Cloud Services trustworthiness through continuous audit-based certification. In Proceedings of the CEUR Workshop Proceedings, CEUR-WS, St. Petersburg, Russia, 23–26 June 2021. [Google Scholar]
- EMERALD. Evidence Management for Continuous Certification as a Service in the Cloud. 2024. Available online: https://cordis.europa.eu/project/id/101120688 (accessed on 5 November 2024).
- Zhou, S.; Li, K.; Xiao, L.; Cai, J.; Liang, W.; Castiglione, A. A systematic review of consensus mechanisms in blockchain. Mathematics 2023, 11, 2248. [Google Scholar] [CrossRef]
- Mazzoni, M.; Corradi, A.; Di Nicola, V. Performance evaluation of permissioned blockchains for financial applications: The ConsenSys Quorum case study. Blockchain Res. Appl. 2022, 3, 100026. [Google Scholar] [CrossRef]
- Ongaro, D.; Ousterhout, J. The raft consensus algorithm. Lect. Notes CS 2015, 190, 2022. [Google Scholar]
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1809.03421. [Google Scholar]
- Gupta, M.K.; Dwivedi, R.K.; Sharma, A.; Farooq, M. Performance Evaluation of Blockchain Platforms. In Proceedings of the 2023 International Conference on IoT, Communication and Automation Technology (ICICAT), Gorakhpur, India, 23–24 June 2023; pp. 1–6. [Google Scholar]
- Singh, N.; Vardhan, M. Computing optimal block size for blockchain based applications with contradictory objectives. Procedia Comput. Sci. 2020, 171, 1389–1398. [Google Scholar] [CrossRef]
- Hoerbst, A.; Ammenwerth, E. Quality and Certification of Electronic Health Records. Appl. Clin. Inform. 2010, 1, 149–164. [Google Scholar]
- Georgieva, P.; Nikolova, E.; Orozova, D.; Jecheva, V. Certification in Teaching Information Technologies for Engineering Graduates. In Proceedings of the ICERI2019 Proceedings, IATED, Seville, Spain, 11–13 November 2019; pp. 4564–4573. [Google Scholar]
- Bian, Y.; Yan, S.; Yi, Z.; Guan, X.; Chen, Y.J. Quality certification in agricultural supply chains: Implications from government information provision. Prod. Oper. Manag. 2022, 31, 1456–1472. [Google Scholar] [CrossRef]
- Heras-Saizarbitoria, I.; Boiral, O.; Díaz de Junguitu, A. Environmental management certification and environmental performance: Greening or greenwashing? Bus. Strategy Environ. 2020, 29, 2829–2841. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).