Leveraging Towards Access Control, Identity Management, and Data Integrity Verification Mechanisms in Blockchain-Assisted Cloud Environments: A Comparative Study
Abstract
1. Introduction
- Decentralization: It is the core strength of a blockchain that each node maintains a record of all transaction data, which eliminates the need for a central authority. This mitigates the risk of a single point of failure, and the consensus algorithms ensure data consistency across the network [13].
- Hashing: This maintains the confidentiality and integrity of the stored transaction data in a particular block [14].
- Smart contracts: These are executable contract codes run on a blockchain network, which automatically execute transactions when predefined conditions are met. The set of conditions are written in if-then-else form [15].
- Merkle tree: To ensure data integrity, it concatenates the hashes of all transactions within a block in a chronological order to calculate a root hash, known as the hash of that block [14].
1.1. Contributions
- It performs a systematic review by using the PRISMA [36] guidelines to investigate the cloud security issues, and it classifies the issues in terms of security services such as confidentiality, integrity, availability, authentication, and privacy.
- It presents a thorough study on blockchain-enabled access control, IDM, and data integrity verification solutions for the cloud environment.
- Finally, it provides an in-depth comparative analysis of blockchain-assisted approaches for access control, IDM, and data integrity verification in the cloud environment.
1.2. Article Structure
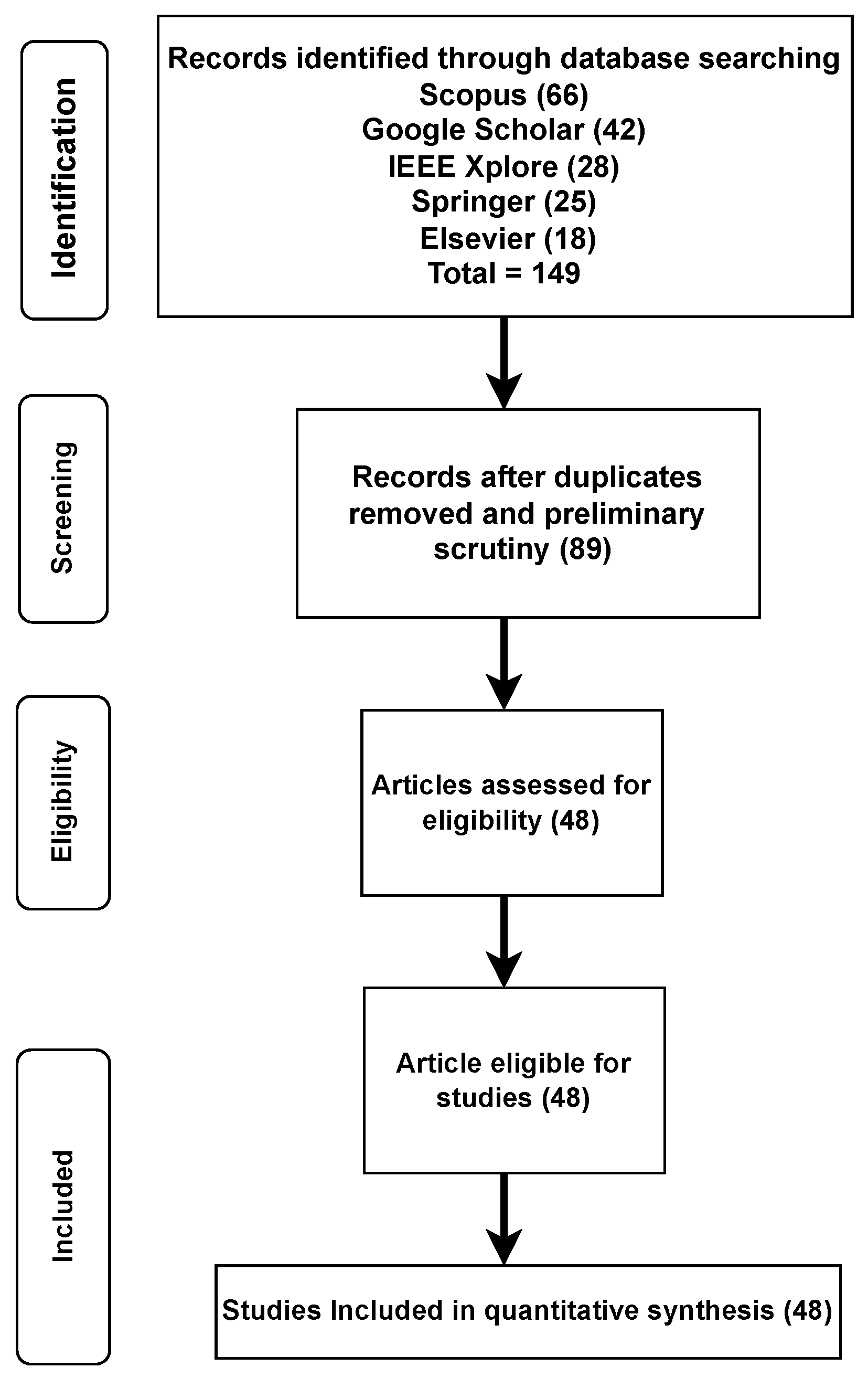
2. Literature Selection Methodology
2.1. Paper Inclusion Criteria
- The paper must discussed the challenges faced by cloud computing in one of the following areas: security and privacy, data management, or trust management.
- The paper must be an original research paper that introduces a novel blockchain-enabled cloud security solution.
- The proposal must aim to improve one of the following cloud security issues: access control, IDM, and data integrity verification.
2.2. Paper Exclusion Criteria
- The paper is not focused on cloud-related issues in any of the following areas: security and privacy, data management, trust management (11 papers).
- The paper does not focus on any of the following blockchain-enabled cloud security solutions: access control, IDM, and data integrity verification (13 papers).
- The blockchain-enabled cloud security solution article is not an original contribution, but rather a review paper (14 papers).
- The paper is not written in English (three papers).
2.3. Research Questions
- RQ1. What are the security challenges associated with cloud environments, and how we can categorize them in terms of security requirements, such as confidentiality, integrity, availability, authenticity, and privacy.
- RQ2. What are the different access control schemes proposed for cloud environments that use a blockchain, along with their workings?
- RQ3. What methodologies are used to address IDM issues in cloud environments using a blockchain, and their working procedure?
- RQ4. What are the existing blockchain-enabled models for cloud data integrity verification along with their workings?
- RQ5. Which security parameters are focused on by the existing models to make them secure and their limitations if any?
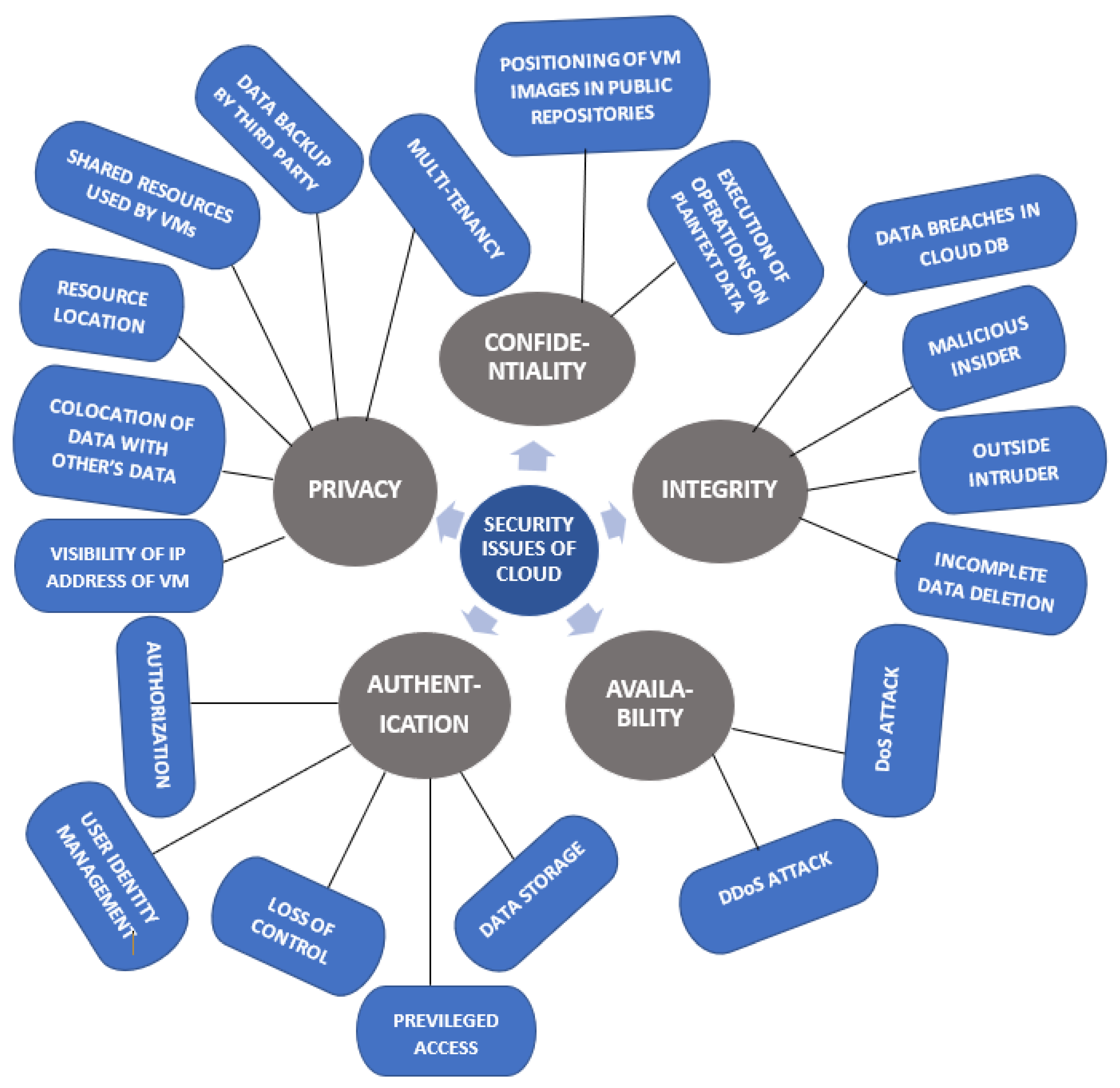
3. Security Issues in the Cloud
3.1. VMs
3.2. Cloud Data Storage
3.3. Cloud IAM
3.4. Cloud Threats
4. Blockchain-Assisted Cloud Frameworks: Security Perspective
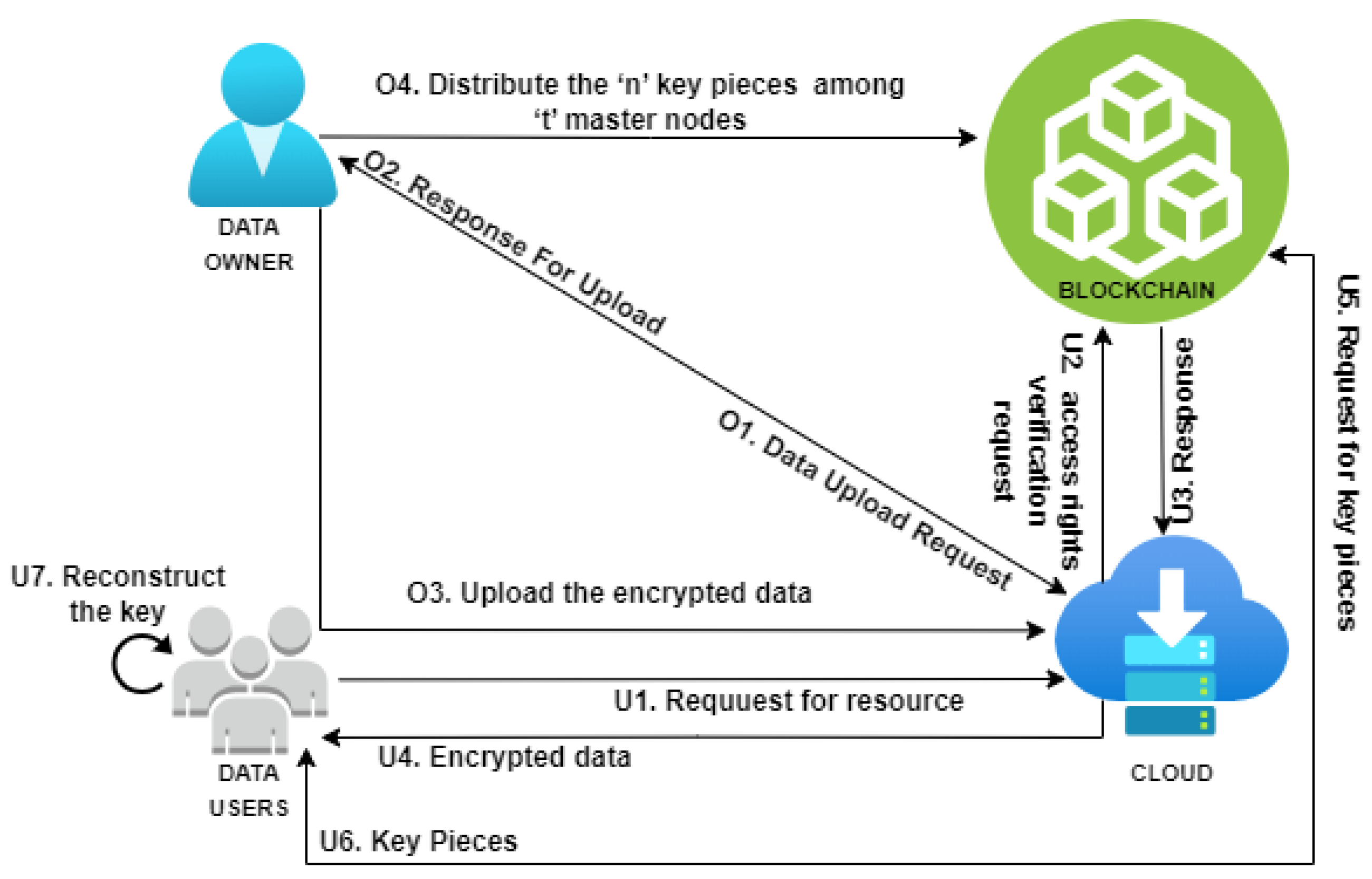
4.1. Decentralized Access Control Mechanisms
- Dependency on the SA can cause a single point of failure.
- When symmetric key encryption is used, storing both the encrypted data and their decryption key in the cloud can lead to an eavesdropping attack.
- Cloud access control schemes must ensure accountability to trace any malicious activities performed by users.
4.2. Decentralized IDM Approaches
- In isolated IDM, the service provider is responsible for providing service and identity as well. Hence, a single point of failure/centralization issue may be possible [69].
- Centralized IDM is also based on the centralization concept. Here, the service provider is responsible for providing service and all the identity credentials, which are stored in IDP. Due to this, privacy protection issues can arise here [70].
- Anonymous IDM keeps the entities’ identities secret from others. In this scenario, trust issues can arise [73].
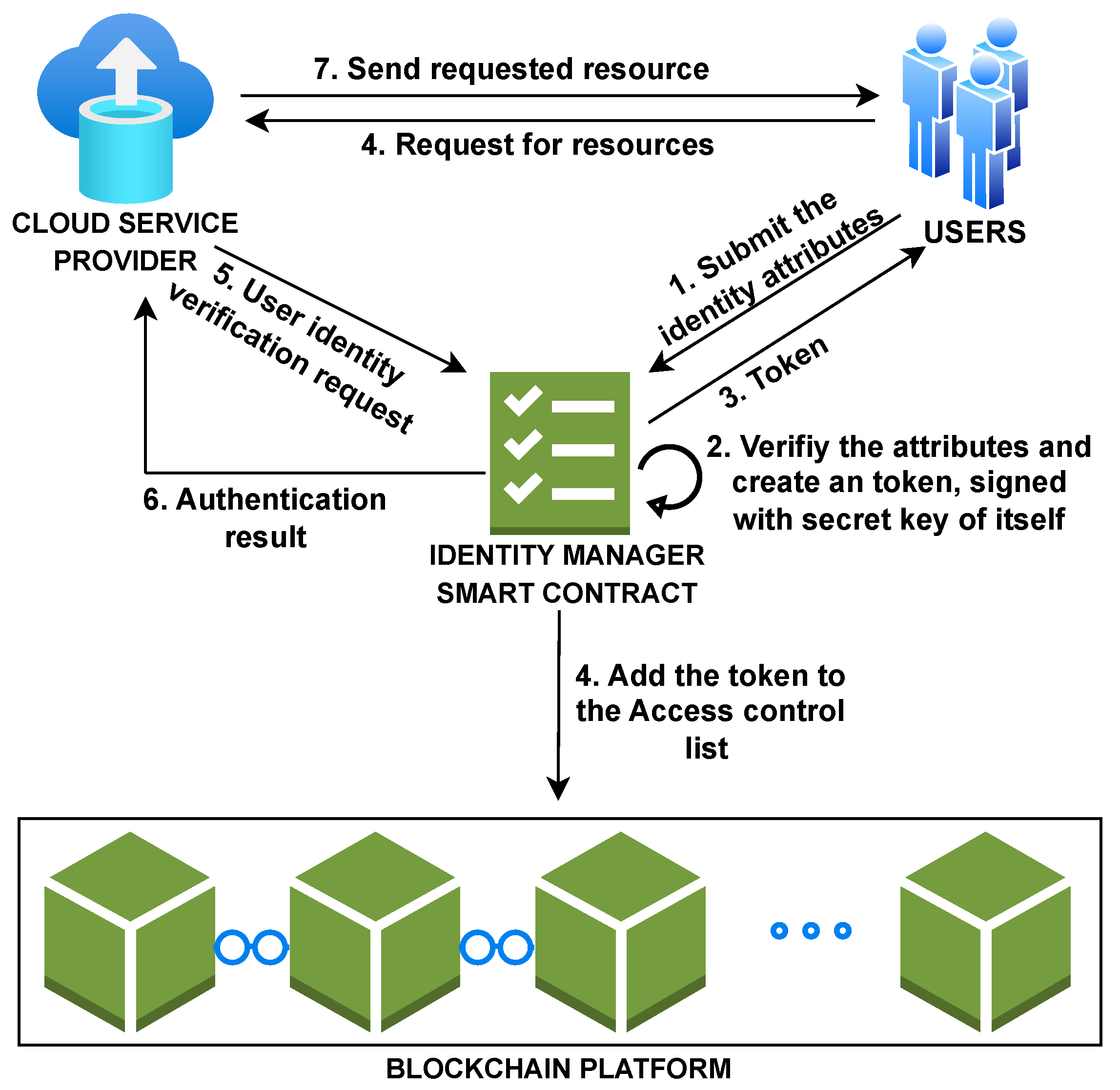
- The cloud user requests protected data from the CSP.
- If the CSP is a foreign CSP for the requested user, then it send the user to its home CSP for authentication purposes.
- The home CSP generates an access token for the user and keeps it in a blockchain.
- The foreign CSP allows the user to access the data, after verifying the access token stored in the blockchain.
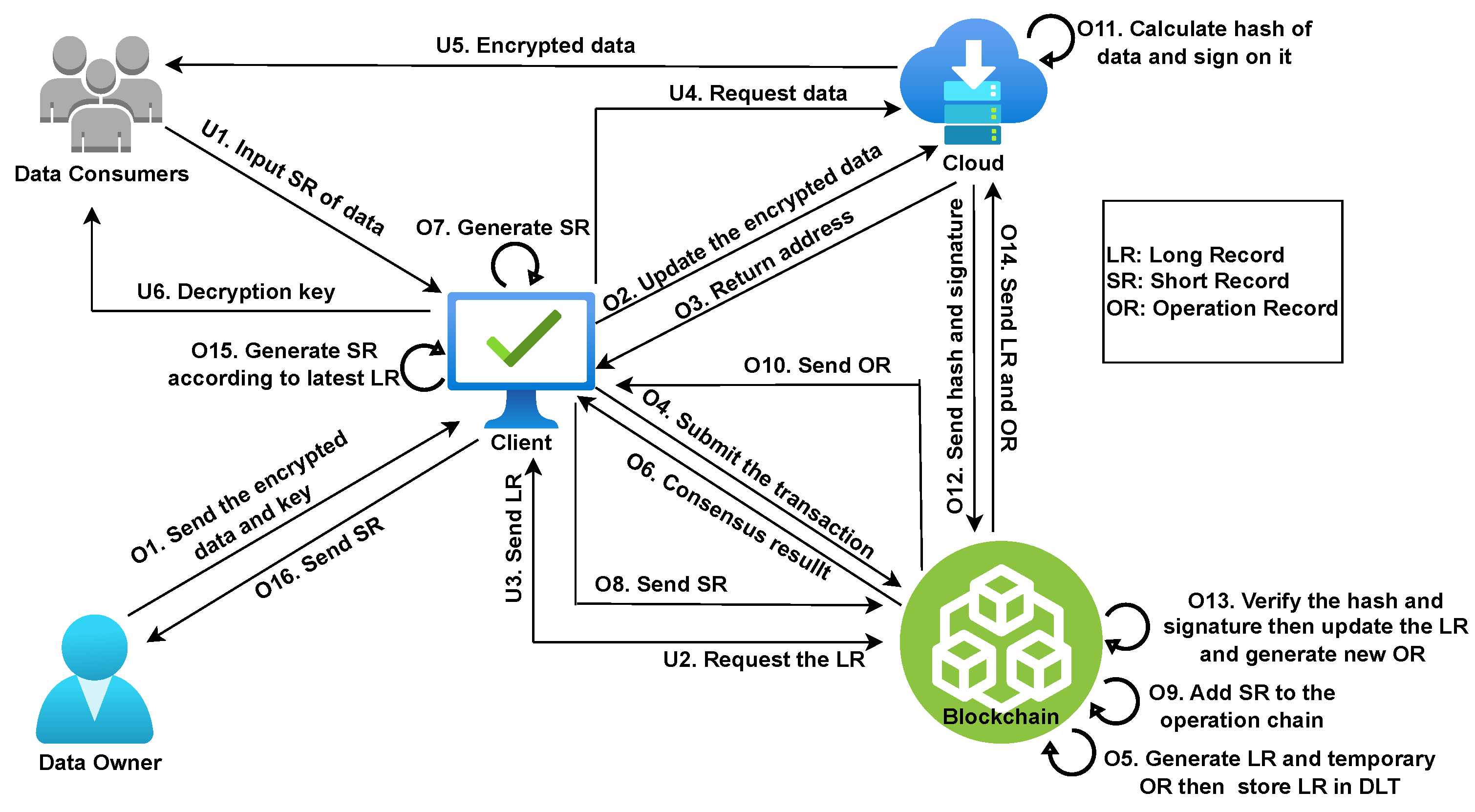
4.3. Decentralized Data Integrity Verification Techniques
- This integrity verification method is controlled by the TPA; hence, centralization/single point of failure is one of the possible problems.
- The verification process is not transparent to the user.
4.4. Comparison of Schemes Discussed in Section 4.1, Section 4.2 and Section 4.3
5. Future Research Directions
- In blockchain-enabled cloud storage schemes, there is a need for secure symmetric key distribution and the cheater detection approach.
- A blockchain-assisted cloud access control scheme should incorporate a privacy-preserving accountability framework while ensuring efficiency in both storage and cost.
- IDM smart contracts must include a privacy-preserving framework, ensuring minimal user token verification time, low execution costs, and storage efficiency.
- The reduction in the storage overhead in blockchain-based data integrity verification solutions for the cloud is a big concern.
- When it comes to a multi-cloud storage system, an important concern is the even distribution of data files among multiple clouds.
6. Summary
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AuthPrivacyChain | A Blockchain-Based Access Control Framework with Privacy Protection in the cloud |
| BACC | Blockchain-Based Access Control for Cloud Data |
| BC-ABAC | Attribute-Based Access Control for cloud services enforced using Blockchain |
| CBFF | Cloud–Blockchain Fusion Framework |
| CSPs | Cloud service providers |
| DF | Data file |
| DB | Database |
| DPoS | Delegated Proof of Stake |
| DoS | Denial of Service |
| DDos | Distributed Denial of Service |
| IDM | Identity management |
| IAM | Identity and access management |
| IDP | Identity provider |
| JWT | JSON Web Token |
| MHT | Merkle hash tree |
| PoW | Proof of Work |
| PoS | Proof of Stake |
| P2P CSS | P2P Cloud Storage Server |
| PT | Plaintext |
| PBFT | Practical Byzantine Fault Tolerance |
| RDB | Relational Database |
| TMP | Trust Management Platform |
| TPA | Third-party auditor |
| UID | User identification |
| VM | Virtual Machine |
References
- Qian, L.; Luo, Z.; Du, Y.; Guo, L. Cloud computing: An overview. In Cloud Computing: First International Conference, CloudCom 2009, Beijing, China, 1–4 December 2009. Proceedings 1; Springer: Berlin/Heidelberg, Germany, 2009; pp. 626–631. [Google Scholar]
- Zhang, Q.; Cheng, L.; Boutaba, R. Cloud computing: State-of-the-art and research challenges. J. Internet Serv. Appl. 2010, 1, 7–18. [Google Scholar] [CrossRef]
- Singh, S.; Jeong, Y.S.; Park, J.H. A survey on cloud computing security: Issues, threats, and solutions. J. Netw. Comput. Appl. 2016, 75, 200–222. [Google Scholar] [CrossRef]
- Subramanian, N.; Jeyaraj, A. Recent security challenges in cloud computing. Comput. Electr. Eng. 2018, 71, 28–42. [Google Scholar] [CrossRef]
- Wang, L.; Ranjan, R.; Chen, J.; Benatallah, B. Cloud Computing: Methodology, Systems, and Applications; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Hu, F.; Qiu, M.; Li, J.; Grant, T.; Taylor, D.; McCaleb, S.; Butler, L.; Hamner, R. A review on cloud computing: Design challenges in architecture and security. J. Comput. Inf. Technol. 2011, 19, 25–55. [Google Scholar] [CrossRef]
- Venters, W.; Whitley, E.A. A critical review of cloud computing: Researching desires and realities. J. Inf. Technol. 2012, 27, 179–197. [Google Scholar] [CrossRef]
- Park, J.H.; Park, J.H. Blockchain security in cloud computing: Use cases, challenges, and solutions. Symmetry 2017, 9, 164. [Google Scholar] [CrossRef]
- Murthy, C.V.B.; Shri, M.L.; Kadry, S.; Lim, S. Blockchain based cloud computing: Architecture and research challenges. IEEE Access 2020, 8, 205190–205205. [Google Scholar] [CrossRef]
- Li, W.; Wu, J.; Cao, J.; Chen, N.; Zhang, Q.; Buyya, R. Blockchain-based trust management in cloud computing systems: A taxonomy, review and future directions. J. Cloud Comput. 2021, 10, 35. [Google Scholar] [CrossRef]
- Habib, G.; Sharma, S.; Ibrahim, S.; Ahmad, I.; Qureshi, S.; Ishfaq, M. Blockchain Technology: Benefits, Challenges, Applications, and Integration of Blockchain Technology with Cloud Computing. Future Internet 2022, 14, 341. [Google Scholar] [CrossRef]
- Das, S.; Sahil, M.; Pandit, N.K.; Priyadarshini, R.; Gochhayat, S.P. BSCIAM: A Blockchain based Secure Cloud Identity and Access Management Framework. In Proceedings of the 2024 IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), Bhopal, India, 24–25 February 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 557–564. [Google Scholar]
- Das, S.; Rout, J.; Mishra, M. Blockchain Technology: Applications and Open Issues. In Proceedings of the 2022 International Conference on Communication, Computing and Internet of Things (IC3IoT), Chennai, India, 10–11 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Namasudra, S.; Deka, G.C.; Johri, P.; Hosseinpour, M.; Gandomi, A.H. The revolution of blockchain: State-of-the-art and research challenges. Arch. Comput. Methods Eng. 2021, 28, 1497–1515. [Google Scholar] [CrossRef]
- Wan, S.; Li, M.; Liu, G.; Wang, C. Recent advances in consensus protocols for blockchain: A survey. Wirel. Netw. 2020, 26, 5579–5593. [Google Scholar] [CrossRef]
- Das, S.; Rout, J.; Priyadarshini, R.; Mishra, M. A Comparative Analysis of the Consensus Algorithms in Blockchain Technology. In Proceedings of the International Conference on Innovative Computing and Communications: Proceedings of ICICC, Delhi, India, 19–20 February 2022. [Google Scholar]
- Zhang, W. The Current Situation and Trend of Blockchain Technology in the Financial Field. Mob. Inf. Syst. 2022, 2022, 7908625. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Mallick, S.R.; Lenka, R.K.; Goswami, V.; Sharma, S.; Dalai, A.K.; Das, H.; Barik, R.K. Bcgeo: Blockchain-assisted geospatial web service for smart healthcare system. IEEE Access 2023, 11, 58610–58623. [Google Scholar] [CrossRef]
- Dunphy, P.; Petitcolas, F.A. A first look at identity management schemes on the blockchain. IEEE Secur. Priv. 2018, 16, 20–29. [Google Scholar] [CrossRef]
- Awadallah, R.; Samsudin, A. Using blockchain in cloud computing to enhance relational database security. IEEE Access 2021, 9, 137353–137366. [Google Scholar] [CrossRef]
- AlShamsi, M.; Salloum, S.A.; Alshurideh, M.; Abdallah, S. Artificial intelligence and blockchain for transparency in governance. In Artificial Intelligence for Sustainable Development: Theory, Practice and Future Applications; Springer: Berlin/Heidelberg, Germany, 2020; pp. 219–230. [Google Scholar]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 19–22 February 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 464–467. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Loukil, F.; Abed, M.; Boukadi, K. Blockchain adoption in education: A systematic literature review. Educ. Inf. Technol. 2021, 26, 5779–5797. [Google Scholar] [CrossRef]
- Kandpal, M.; Goswami, V.; Pritwani, Y.; Barik, R.K.; Saikia, M.J. BS-GeoEduNet 1.0: Blockchain-Assisted Serverless Framework for Geospatial Educational Information Networks. ISPRS Int. J. Geo-Inf. 2024, 13, 274. [Google Scholar] [CrossRef]
- Mallick, S.; Goswami, V.; Dash, R.N.; Lenka, R.; Sharma, S.; Barik, R. A priority-reservation queueing-based approach for blockchain-assisted smart-grid system. In Proceedings of the 2023 International Conference on Power Electronics and Energy (ICPEE), Bhubaneswar, India, 3–5 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Kandpal, M.; Pritwani, Y.; Misra, C.; Yadav, A.S.; Barik, R.K. Towards Data Storage Scheme in Blockchain Based Serverless Environment: Aes Encryption and Decryption Algorithm Approach. Facta Univ. Ser. Electron. Energetics 2024, 37, 317–342. [Google Scholar] [CrossRef]
- Ressi, D.; Romanello, R.; Piazza, C.; Rossi, S. AI-enhanced blockchain technology: A review of advancements and opportunities. J. Netw. Comput. Appl. 2024, 225, 103858. [Google Scholar] [CrossRef]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security services using blockchains: A state of the art survey. IEEE Commun. Surv. Tutor. 2018, 21, 858–880. [Google Scholar] [CrossRef]
- Kandpal, M.; Goswami, V.; Priyadarshini, R.; Barik, R.K. Towards Data Storage, Scalability, and Availability in Blockchain Systems: A Bibliometric Analysis. Data 2023, 8, 148. [Google Scholar] [CrossRef]
- Yang, C.; Tan, L.; Shi, N.; Xu, B.; Cao, Y.; Yu, K. AuthPrivacyChain: A blockchain-based access control framework with privacy protection in cloud. IEEE Access 2020, 8, 70604–70615. [Google Scholar] [CrossRef]
- Habiba, U.; Masood, R.; Shibli, M.A.; Niazi, M.A. Cloud identity management security issues & solutions: A taxonomy. Complex Adapt. Syst. Model 2014, 2, 5. [Google Scholar]
- Yue, D.; Li, R.; Zhang, Y.; Tian, W.; Peng, C. Blockchain based data integrity verification in P2P cloud storage. In Proceedings of the 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 561–568. [Google Scholar]
- Stefanescu, D.; Montalvillo, L.; Galán-García, P.; Unzilla, J.; Urbieta, A. A systematic literature review of lightweight blockchain for IoT. IEEE Access 2022, 10, 123138–123159. [Google Scholar] [CrossRef]
- Ghanam, Y.; Ferreira, J.; Maurer, F. Emerging issues & challenges in cloud computing—A hybrid approach. J. Softw. Eng. Appl. 2012, 5, 923–937. [Google Scholar]
- Rong, C.; Nguyen, S.T.; Jaatun, M.G. Beyond Lightning: A Survey on Security Challenges in Cloud Computing. J. Comput. Electr. Eng. 2012, 39, 47–54. [Google Scholar] [CrossRef]
- Kshetri, N. Privacy and security issues in cloud computing: The role of institutions and institutional evolution. Telecommun. Policy 2013, 37, 372–386. [Google Scholar] [CrossRef]
- Hashizume, K.; Rosado, D.; Fernández-Medina, E.; Fernandez, E. An analysis of security issues for cloud computing. J. Internet Serv. Appl. 2013, 4, 5. [Google Scholar] [CrossRef]
- Li, T.J.; Singh, M.M. Hybrid trust framework for loss of control in cloud computing. In Advances in Computer Science and Its Applications, Proceedings of the CSA 2013, Lucknow, India, 21–22 June 2013; Springer: Berlin/Heidelberg, Germany, 2014; pp. 669–675. [Google Scholar]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, A.; Rajarajan, M. A survey on security issues and solutions at different layers of Cloud computing. J. Supercomput. 2013, 63, 561–592. [Google Scholar] [CrossRef]
- Fernandes, D.A.; Soares, L.F.; Gomes, J.V.; Freire, M.M.; Inácio, P.R. Security issues in cloud environments: A survey. Int. J. Inf. Secur. 2014, 13, 113–170. [Google Scholar] [CrossRef]
- Shariati, S.M.; Abouzarjomehri; Ahmadzadegan, M.H. Challenges and security issues in cloud computing from two perspectives: Data security and privacy protection. In Proceedings of the 2015 2nd International Conference on Knowledge-Based Engineering and Innovation (KBEI), Tehran, Iran, 5–6 November 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1078–1082. [Google Scholar]
- Tari, Z.; Yi, X.; Premarathne, U.S.; Bertok, P.; Khalil, I. Security and privacy in cloud computing: Vision, trends, and challenges. IEEE Cloud Comput. 2015, 2, 30–38. [Google Scholar] [CrossRef]
- Hussein, N.H.; Khalid, A. A survey of cloud computing security challenges and solutions. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 52. [Google Scholar]
- Almorsy, M.; Grundy, J.; Müller, I. An analysis of the cloud computing security problem. arXiv 2016, arXiv:1609.01107. [Google Scholar]
- Rao, B.T.; Vurukonda, N. A study on data storage security issues in cloud computing. Procedia Comput. Sci. 2016, 92, 128–135. [Google Scholar]
- Kumar, S.N.; Vajpayee, A. A survey on secure cloud: Security and privacy in cloud computing. Am. J. Syst. Softw. 2016, 4, 14–26. [Google Scholar]
- Radwan, T.; Azer, M.A.; Abdelbaki, N. Cloud computing security: Challenges and future trends. Int. J. Comput. Appl. Technol. 2017, 55, 158–172. [Google Scholar] [CrossRef]
- Sun, X. Critical security issues in cloud computing: A survey. In Proceedings of the 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing,(HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Omaha, NE, USA, 3–5 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 216–221. [Google Scholar]
- Wu, Z.; Xu, G.; Lu, C.; Chen, E.; Jiang, F.; Li, G. An effective approach for the protection of privacy text data in the CloudDB. World Wide Web 2018, 21, 915–938. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Suthar, F.; Khanna, S.; Patel, J. A survey on cloud security issues. Int. J. Comput. Sci. Eng. (IJCSE) 2019, 7, 120–123. [Google Scholar] [CrossRef]
- Tabrizchi, H.; Kuchaki Rafsanjani, M. A survey on security challenges in cloud computing: Issues, threats, and solutions. J. Supercomput. 2020, 76, 9493–9532. [Google Scholar] [CrossRef]
- Geng, Y.; Zhao E, M. Homomorphic encryption technology for cloud computing. Procedia Comput. Sci. 2019, 154, 73–83. [Google Scholar]
- Indu, I.; Anand, P.R.; Bhaskar, V. Identity and access management in cloud environment: Mechanisms and challenges. Eng. Sci. Technol. Int. J. 2018, 21, 574–588. [Google Scholar] [CrossRef]
- Charanya, R.; Aramudhan, M. Survey on access control issues in cloud computing. In Proceedings of the 2016 International Conference on Emerging Trends in Engineering, Technology and Science (ICETETS), Pudukkottai, India, 24–26 February 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–4. [Google Scholar]
- Rana, M.E.; Kubbo, M.; Jayabalan, M. Privacy and security challenges towards cloud-based access control. Asian. J. Inf. Technol. 2017, 16, 274–281. [Google Scholar]
- Wang, S.; Wang, X.; Zhang, Y. A secure cloud storage framework with access control based on blockchain. IEEE Access 2019, 7, 112713–112725. [Google Scholar] [CrossRef]
- Sohrabi, N.; Yi, X.; Tari, Z.; Khalil, I. BACC: Blockchain-based access control for cloud data. In Proceedings of the Australasian Computer Science Week Multiconference, Melbourne, Australia, 4–6 February 2020; pp. 1–10. [Google Scholar]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. A blockchain-based access control scheme with multiple attribute authorities for secure cloud data sharing. J. Syst. Archit. 2021, 112, 101854. [Google Scholar] [CrossRef]
- Li, Q.; Yang, Z.; Qin, X.; Tao, D.; Pan, H.; Huang, Y. CBFF: A cloud–blockchain fusion framework ensuring data accountability for multi-cloud environments. J. Syst. Archit. 2022, 124, 102436. [Google Scholar] [CrossRef]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain-based cloud storage system with CP-ABE-based access control and revocation process. J. Supercomput. 2022, 78, 7700–7728. [Google Scholar] [CrossRef]
- Ghorbel, A.; Ghorbel, M.; Jmaiel, M. Accountable privacy preserving attribute-based access control for cloud services enforced using blockchain. Int. J. Inf. Secur. 2021, 21, 489–508. [Google Scholar] [CrossRef]
- Yan, L.; Ge, L.; Wang, Z.; Zhang, G.; Xu, J.; Hu, Z. Access control scheme based on blockchain and attribute-based searchable encryption in cloud environment. J. Cloud Comput. 2023, 12, 61. [Google Scholar] [CrossRef]
- Zwattendorfer, B.; Zefferer, T.; Stranacher, K. An Overview of Cloud Identity Management-Models. WEBIST 2014, 1, 82–92. [Google Scholar]
- Saini, S.; Mann, D. Identity management issues in cloud computing. arXiv 2014, arXiv:1406.1033. [Google Scholar]
- Alrodhan, W.A.; Mitchell, C.J. Enhancing user authentication in claim-based identity management. In Proceedings of the 2010 International Symposium on Collaborative Technologies and Systems, Chicago, IL, USA, 17–21 May 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 75–83. [Google Scholar]
- Cao, Y.; Yang, L. A survey of identity management technology. In Proceedings of the 2010 IEEE International Conference on Information Theory and Information Security, Beijing, China, 17–19 December 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 287–293. [Google Scholar]
- Hommel, W.; Reiser, H. Federated identity management: Shortcomings of existing standards. In Proceedings of the 9th IFIP/IEEE International Symposium on Integrated Management (IM 2005), Nice, France, 19 May 2005. [Google Scholar]
- Ferdous, M.S.; Norman, G.; Jøsang, A.; Poet, R. Mathematical modelling of trust issues in federated identity management. In Trust Management IX, Proceedings of the 9th IFIP WG 11.11 International Conference, IFIPTM 2015, Hamburg, Germany, 26–28 May 2015, Proceedings 9; Springer: Berlin/Heidelberg, Germany, 2015; pp. 13–29. [Google Scholar]
- Rastogi, G.; Sushil, R. A Review Paper on Cloud Identity Management Systems. In Proceedings of the International Conference on Cloud Computing and Big Data, Macau, China, 16–18 November 2016. [Google Scholar]
- Bendiab, K.; Kolokotronis, N.; Shiaeles, S.; Boucherkha, S. WiP: A novel blockchain-based trust model for cloud identity management. In Proceedings of the 2018 IEEE 16th International Conference on Dependable, Autonomic and Secure Computing, 16th International Conference on Pervasive Intelligence and Computing, 4th International Conference on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Athens, Greece, 12–15 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 724–729. [Google Scholar]
- Wang, S.; Pei, R.; Zhang, Y. EIDM: A ethereum-based cloud user identity management protocol. IEEE Access 2019, 7, 115281–115291. [Google Scholar] [CrossRef]
- Deep, G.; Mohana, R.; Nayyar, A.; Sanjeevikumar, P.; Hossain, E. Authentication protocol for cloud databases using blockchain mechanism. Sensors 2019, 19, 4444. [Google Scholar] [CrossRef]
- Fugkeaw, S. Achieving Decentralized and Dynamic SSO-Identity Access Management System for Multi-Application Outsourced in Cloud. IEEE Access 2023, 11, 25480–25491. [Google Scholar] [CrossRef]
- Prasad, S.N.; Rekha, C. Block chain based IAS protocol to enhance security and privacy in cloud computing. Meas. Sens. 2023, 28, 100813. [Google Scholar] [CrossRef]
- Tian, J.; Jing, X. Cloud data integrity verification scheme for associated tags. Comput. Secur. 2020, 95, 101847. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Lin, X.; Shen, X. Blockchain-based public integrity verification for cloud storage against procrastinating auditors. IEEE Trans. Cloud Comput. 2019, 9, 923–937. [Google Scholar] [CrossRef]
- Xie, G.; Liu, Y.; Xin, G.; Yang, Q. Blockchain-based cloud data integrity verification scheme with high efficiency. Secur. Commun. Netw. 2021, 2021, 9921209. [Google Scholar] [CrossRef]
- Zhang, C.; Xu, Y.; Hu, Y.; Wu, J.; Ren, J.; Zhang, Y. A blockchain-based multi-cloud storage data auditing scheme to locate faults. IEEE Trans. Cloud Comput. 2021, 10, 2252–2263. [Google Scholar] [CrossRef]
- Song, M.; Hua, Z.; Zheng, Y.; Huang, H.; Jia, X. Blockchain-based deduplication and integrity auditing over encrypted cloud storage. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4928–4945. [Google Scholar] [CrossRef]
- Wang, C.; Sun, Y.; Liu, B.; Xue, L.; Guan, X. Blockchain-based Dynamic Cloud Data Integrity Auditing via Non-leaf Node Sampling of Rank-based Merkle Hash Tree. IEEE Trans. Netw. Sci. Eng. 2024, 11, 3931–3942. [Google Scholar] [CrossRef]







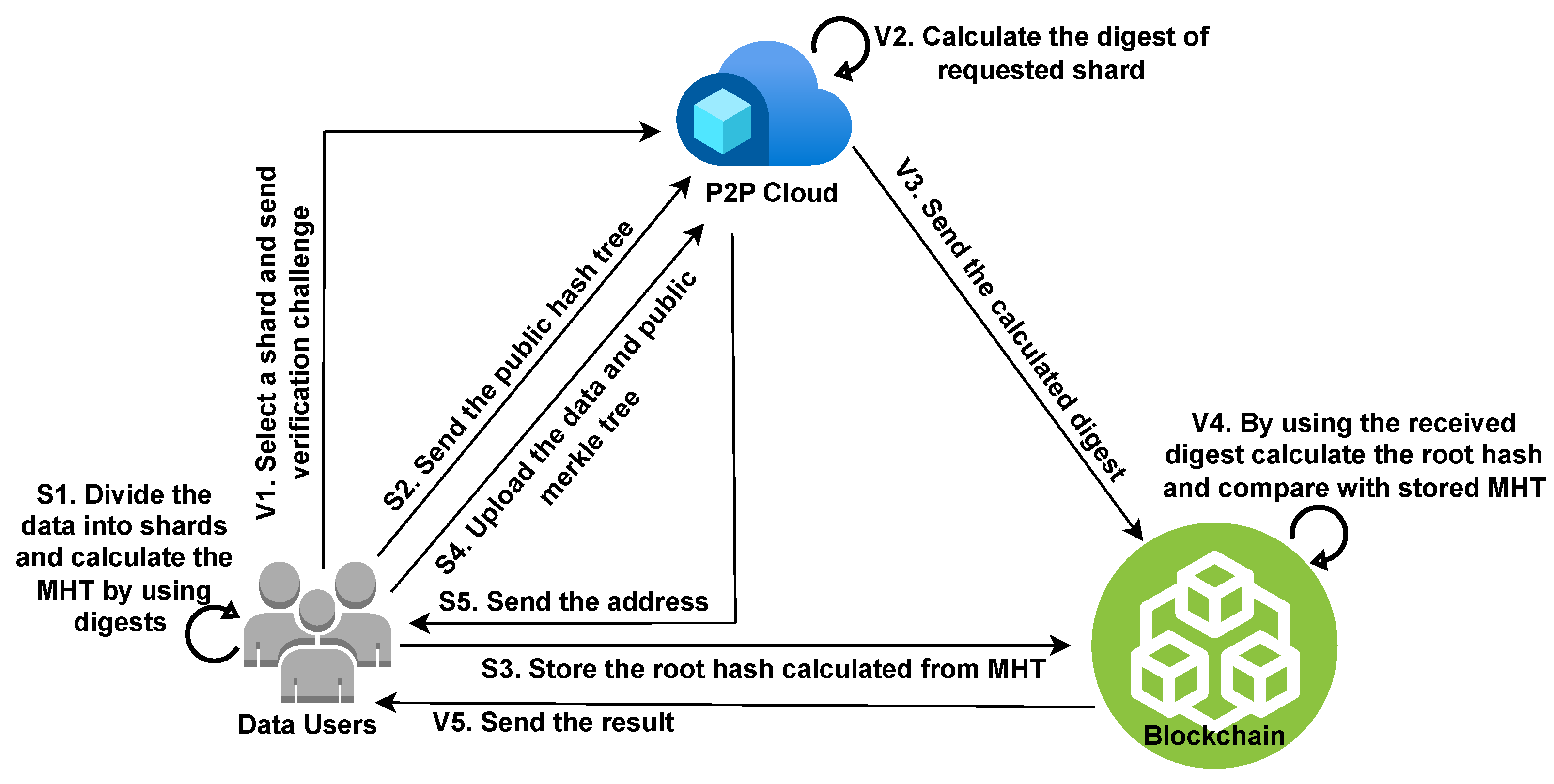
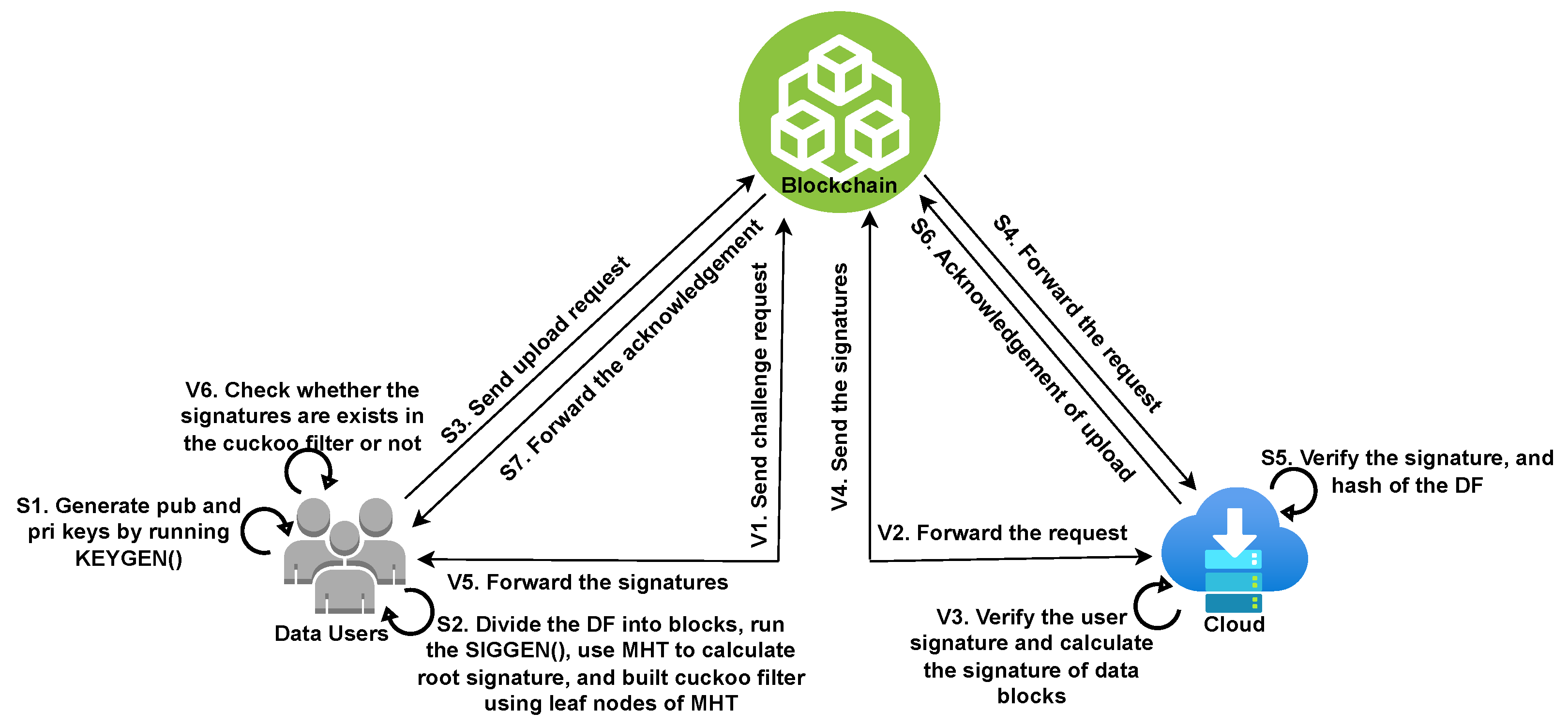

| Year, Ref. | Confidentiality | Authentication | Integrity | Availability | Accountability | Privacy |
|---|---|---|---|---|---|---|
| 2020, [33] | True | True | True | True | False | False |
| 2020, [61] | True | True | True | True | False | True |
| 2020, [62] | True | True | True | True | False | True |
| 2022, [63] | True | True | True | True | True | False |
| 2022, [64] | True | True | True | True | False | True |
| 2022, [65] | True | True | True | True | True | False |
| 2023, [66] | True | True | True | True | False | False |
| Year, Ref. | Availability | Access Control | Privacy | Method Used for Authentication | Time Taken for User Authentication Verification |
|---|---|---|---|---|---|
| 2018, [74] | True | True | False | Token | - |
| 2019, [75] | True | False | True | JWT and ask security question | 2 X time taken for hash (JWT, random number) + time for verification of both hashes |
| 2019, [76] | True | False | False | User signature and current index value verification | Time taken for calculation of x (x = last stored index AND current hash value AND time stamp AND nonce) + verification time for (current index value > x) |
| 2023, [77] | True | True | True | SSO token | Verification time for user’s authentication credential |
| 2023, [78] | True | True | True | User’s attribute token | Verification time for user’s identity attribute |
| Year, Ref. | Type of Cloud Storage | Mechanism Used | Computation Cost | Communication Cost | Storage Overhead |
|---|---|---|---|---|---|
| 2018, [35] | Single | Merkle tree | 1. Shard Verification: Merkle tree generation X time for each shard hash calculation 2. Merkle tree generation (in a blockchain): sum of output of each leaf node | Merkle tree generation (at user side): sum of output of each leaf node | not addressed |
| 2019, [80] | Single | Tag | 1. Server side: exponent in group (G) + group operations in G + multiplication in + addition in 2. TPA side: computing e(g,q), where g,q ∈ G + exponent in G + group operations in G + mapping a value into G + hash a value into + multiplication in | TPA to cloud: number of challenged data blocks X size of each block (here the cost is constant) | not addressed |
| 2021, [81] | Single | Merkle tree and cuckoo filter data structure | 1. Client side: 3nMMul + 2nMAdd + nMMod + nMHash 2. CSP side: 2cMul + cAdd + cMod + cHash | CSP’s response on challenge: (no of blocks X signature length of each) + (no. of blocks X size of each file block) | addressed |
| 2021, [82] | Multi | Homomorphic verifiable tag | Analyzed in the form of gas cost for each operation | 1. User to organizer: no. of challenged blocks X size of each 2. Organizer to CSPs: no. of challenged blocks X size of each | not addressed |
| 2023, [83] | Single | Tag-based challenge, response method | Analyzed in the form of gas cost for each operation | 1. Encryption and signing key generation: (2n + 2) X no. of key servers 2. For auditing: (n tags X size) + (n public keys X size) | not addressed |
| 2024, [84] | Single | Rank-based Merkle hash tree | Tag generation: no. of blocks X (multiplication in G + 2 X exponentiation in G + (no. of sectors in each block X multiplication in )) | Audit challenge: (no. of sampled blocks X size) + (no. of sample leaf nodes X size) + (no. of sampled blocks in the sampled files X size) | not addressed |
| Year, Ref. | Management Type | Type of Blockchain | Consensus Method Used | Data Encryption Algorithm | Digital Signature |
|---|---|---|---|---|---|
| 2020, [33] | Decentralized | Public | - | AES | - |
| 2020, [61] | Decentralized | Ethereum | PoW | AES-128 | ECDSA |
| 2020, [62] | Not fully Decentralized | Hyperledger Fabric | - | Multiauthority CP-ABE | - |
| 2022, [63] | Not fully Decentralized | Hyperledger Fabric | Etcdraft | CP-ABE | - |
| 2022, [64] | Not fully Decentralized | Java-based blockchain network | - | CP-ABE | - |
| 2022, [65] | Not fully Decentralized | Quorum Ethereum | Raft and IBFT | DEA | - |
| 2023, [66] | Decentralized | Ethereum | - | AES | - |
| 2018, [74] | Implementation details not found | Implementation details not found | PoS | - | ECDSA |
| 2019, [75] | Decentralized | Ethereum | - | AES and RSA | HMACSHA256 |
| 2019, [76] | Implementation details not found | Implementation details not found | - | - | - |
| 2023, [77] | Decentralized | Ethereum | - | - | - |
| 2023, [78] | Implementation details not found | Implementation details not found | - | Hyper Elliptic Curve Cryptography | Hyper Elliptic Curve Cryptography |
| 2018, [35] | Decentralized | Ethereum | - | - | - |
| 2019, [80] | Decentralized | Ethereum | - | - | - |
| 2021, [81] | Not fully Decentralized | Hyperledger Fabric | - | - | Lattice |
| 2021, [82] | Semi decentralized | Consortium | - | - | - |
| 2023, [83] | Decentralized | Ethereum | PoW | AES-256 | Blind signature |
| 2024, [84] | Semi decentralized | Hyperledger Fabric | - | - | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Das, S.; Priyadarshini, R.; Mishra, M.; Barik, R.K. Leveraging Towards Access Control, Identity Management, and Data Integrity Verification Mechanisms in Blockchain-Assisted Cloud Environments: A Comparative Study. J. Cybersecur. Priv. 2024, 4, 1018-1043. https://doi.org/10.3390/jcp4040047
Das S, Priyadarshini R, Mishra M, Barik RK. Leveraging Towards Access Control, Identity Management, and Data Integrity Verification Mechanisms in Blockchain-Assisted Cloud Environments: A Comparative Study. Journal of Cybersecurity and Privacy. 2024; 4(4):1018-1043. https://doi.org/10.3390/jcp4040047
Chicago/Turabian StyleDas, Swatisipra, Rojalina Priyadarshini, Minati Mishra, and Rabindra Kumar Barik. 2024. "Leveraging Towards Access Control, Identity Management, and Data Integrity Verification Mechanisms in Blockchain-Assisted Cloud Environments: A Comparative Study" Journal of Cybersecurity and Privacy 4, no. 4: 1018-1043. https://doi.org/10.3390/jcp4040047
APA StyleDas, S., Priyadarshini, R., Mishra, M., & Barik, R. K. (2024). Leveraging Towards Access Control, Identity Management, and Data Integrity Verification Mechanisms in Blockchain-Assisted Cloud Environments: A Comparative Study. Journal of Cybersecurity and Privacy, 4(4), 1018-1043. https://doi.org/10.3390/jcp4040047








