Abstract
Digital signature technology is essential for ensuring the authenticity and unforgeability of transactions in a private blockchain framework. In some scenarios, transactions require verification from multiple parties, each of whom needs to authenticate different parts of the transaction. To address this issue, researchers have developed multi-party ECDSA (Elliptic Curve Digital Signature Algorithm) signature schemes. However, these schemes either need to consider the authentication of different parts of the transaction or generate an aggregated signature. This paper proposes a novel solution that combines functional signatures and multi-party ECDSA signatures to create a multi-party functional signature for private blockchains. Compared to previous constructions, the proposed scheme ensures that each part of the transaction is verified. Furthermore, when the aggregate signature of the entire transaction cannot be verified, this scheme identifies the specific part of the transaction for which the signature authentication fails instead of rejecting the entire transaction. This paper uses a smart contract to securely deploy the proposed scheme and authenticate the f in functional signatures. The constructed scheme also provides security under the existential unforgeability of the ECDSA signature, even if parties are corrupted, assuming a total of n parties. The scheme of this paper successfully conducted experiments on a personal computer, with three users taking approximately 343 ms, six users taking 552 ms, and nine users taking 791 ms.
1. Introduction
Recently, blockchain has played a significant role in various fields, including finance [1,2,3], IoT [4,5], and decentralized storage [6] due to its decentralization, immutability, and traceability properties. The development of blockchain in cryptocurrency has made it a modern network technology [7]. Bitcoin [8], as blockchain 1.0, has successfully deployed and applied the ECDSA (Elliptic Curve Digital Signature Algorithm scheme), gaining wider attention and gradually becoming the default signature mechanism of current mainstream blockchain platforms and projects. Some blockchains, such as Ethereum [9] as Blockchain 2.0 and Hyperledger Fabric, have been proposed to make blockchain more flexible and perform better. Smart contracts, as the core technology of Ethereum [9], can be seen as computer programs that perform all contract-related operations autonomously, with corresponding results. The validity and authenticity of the contract operations can be checked on the Ethereum account. Deploying smart contracts can realize some special operations in the blockchain system. A private blockchain is a permission-based network that limits usage to specific organizations or individuals. Unlike public blockchains, private blockchains allow only authorized users or organizations to join, and their transaction data are restricted to authorized viewing. The efficient development of any network technology must consider its network security factors [10,11,12,13,14,15], and the signature technology of cryptography can effectively solve some security problems in the blockchain.
Functional signatures, a new type of signature introduced by Boyle, Goldwasser, and Ivan [16], have some properties that standard signatures do not have. In a functional signatures scheme, there are two private keys, a private key that can sign any message belonging to the message space called the master private key, and another one that can sign information defined in the scope of the function f. The owner of the master private key can use the master private key to generate a functional signing private key for function f. The owner can allow others to use the functional signing private key to sign messages in the range of f. The above gives the functional signatures the property of fine-grained access control, and the property is beneficial for multiple users. For example, there is a document that can be noted as message m. The primary user with the master private key can sign the m. The primary user only allows other users to modify some of the information in the document. It issues some functions f for other users, and others can sign the to modify part of the document. Based on [16], Backes [17] proposed delegatable functional signatures and achieved the application of delegation using functional signatures. In the functional signatures scheme, the master key and the signing key of function f are generated by one user. Once this user is corrupted, it will cause much damage. The new scheme called decentralized multi-authority functional signatures, which supports non-monotone access structures using inner-product relations, was introduced by Okamoto and Takashima [18] to address this type of problem.
In private blockchain systems, private keys are essential for users to control their cryptocurrency and are the basis for implementing privacy protection schemes. If a malicious attacker illegally steals a private blockchain user’s signature private key, they can transfer the user’s cryptocurrency arbitrarily or impersonate the user to publish illegal transaction information. This can lead to severe economic loss problems [19]. Some multiple signature schemes have been proposed to solve this problem. MacKenzie [20] initially proposed a two-party signature scheme for DSA that enables two signing parties to generate a valid DSA signature for a given public key. Neither party can complete the signature alone, and no reconstruction of the private key is required during the signing process. Lindell [21] proposed a two-party ECDSA signature scheme based on the Paillier homomorphic encryption algorithm. This scheme utilizes the Paillier homomorphic property to complete the signature process and improve efficiency directly. Castagnos [22] introduced hash proof systems technology to replace the Paillier homomorphic of Lindell [21] and completed the security proof. In addition to the two-party ECDSA signature scheme, multi-party threshold ECDSA signature schemes have also been proposed. Lindell [23] designed a secure privacy multiplication protocol for extending the original two-party signature scheme into a multi-party threshold signature scheme. Doerner [24] also designed a multi-party threshold signature scheme by extending the two-party signature. Gennaro [25] designed the MtA protocol based on Paillier homomorphic encryption and proposed a new multi-party threshold ECDSA signature scheme based on this protocol. However, these schemes use a homomorphic encryption algorithm or oblivious transfer (OT) protocol used in two-party signature schemes, so they have high computational and communication overheads. The above-distributed signatures are all multiple parties signing the same message, and none can solve the problem of fine-grained authentication of partial information. For example, in a technology company, various departments may need to authenticate specific project parts before uploading them to the company’s private blockchain. However, the methods noted above do not allow for this level of fine-grained authentication, as they only produce an aggregated signature. This paper uses the ECDSA scheme as a standard signature in functional signatures and constructs a system model based on functional signatures with multiple parties for private blockchain. The proposed scheme enables multiple parties to sign different parts of the message and collaborate to produce a signature for the message. It can effectively solve the example described above. It can solve some real problems about fine-grained security authentication of multiple parties. The contributions of this paper are as follows:
- This paper proposes a novel scheme that combines functional signatures and multi-party ECDSA signatures to create a multi-party functional signature for private blockchains. Compared to the previous scheme, the proposed scheme ensures that each part of the transaction is verified. Moreover, in cases where the aggregate signature of the entire transaction cannot be verified, this scheme identifies the precise portion of the transaction where signature authentication fails rather than rejecting the transaction in its entirety.
- This paper ensures the security and authenticity of function f in the function signature by embedding it in a smart contract using blockchain’s smart contract technology.
- This paper provides proof of the security of the constructed scheme. Under the existence of the unforgeability of ECDSA signatures, the proposed scheme is secure even if it is corrupted in parties (assuming a total of n parties).
2. Related Work
The security of network technology has always been a frontier worthy of research. Shaukat [26,27] summarized the cyber security issues regarding the rapidly evolving technologies. For the development of blockchain security, Halpin [28] proposed an introduction to security and privacy on the blockchain. As blockchain technology evolves, many researchers have recognized cryptography as essential for analyzing and addressing blockchain security concerns. Li [29] utilized puncturable signatures in cryptography to resolve the issue of long-range attacks in the blockchain’s Proof of Stake protocol. Signature technology is the core of cryptography. It can effectively solve many blockchain security problems.
The use of signature technology to protect the security and privacy of the blockchain has been studied by many scholars. Zhu et al. [30] proposed an interactive incontestable signature for transactions of blockchain, which ensures that the transactions were certified by the dealer and are non-repudiable. Mercer [31] applied ring signatures to the blockchain, enabling privacy protection for the blockchain users themselves. Gong et al. [32] proposed an anonymous traceability protocol based on group signature; the protocol guaranteed the anonymity of blockchain transactions. The design of multiple signatures in blockchain can effectively solve the problem of multi-party verification and decentralization of blockchain transactions. Kogias et al. [33] proposed a collective signing scheme to improve the security and performance of Bitcoin, but it was not very efficient. Zhou et al. [34] proposed a distributed account management scheme for Bitcoin, which aims to protect the private key of a user’s account. Alangot et al. [35] introduced a spanning-tree topology to scale Schnorr multi-signature, which could enhance the consistency of the blockchain. Yu [36] proposed a method to combine Schnorr multi-signature and blockchain to ensure privacy and security of data in the Internet of Things. Maxwell [37] constructed a new Schnorr multi-signature scheme, which could improve both performance and user privacy in Bitcoin. Yu [38] also proposed an elliptic curve threshold signature scheme for blockchain, which has relatively high efficiency compared to other multi-party signatures of elliptic curves. Xiao [39] proposed a secure and efficient multi-signature scheme for Fabric, and Uganya [40] proposed a modified elliptic curve cryptography multi-signature scheme to enhance security in cryptocurrency. The detailed comparison is shown in Table 1.

Table 1.
Comparison of different multi-signatures.
All of the above blockchain multi-signature schemes only generate one signature collaboratively by multiple parties, without considering the fine-grained authentication of partial transaction data by a single party before collaboratively generating a single signature. So far, no scheme has considered fine-grained authentication of transactions in the private blockchain along with multiple signatures. This paper proposes a multi-party functional signatures scheme based on ECDSA signature that can solve the aforementioned problems.
3. Preliminaries
Some basic definitions and notational concepts are as follows.
3.1. ECDSA Signature
ECDSA signature is divided into four steps, which include Setup, KeyGen, SigGen, and Verify. Setup is responsible for generating the system parameters, KeyGen generates the public–private key pairs of the scheme, SigGen represents the signing process, and Verify represents the verification process of the signature. The detailed steps are shown below.
- Setup: On inputting the security parameter, the system outputs public parameters param = {E, , G, P, p, q, H}, where E is an elliptic curve defined over a finite field , p is a prime and G is an additive cyclic group consisting of all points in E; P is the generator of the group G, and q is the prime order of the group G. Finally, H is a cryptographic hash function denoted as and Z is the field consisting of the set of integers {1, 2, …, q − 1}.
- KeyGen: On inputting the public parameter param, the following two steps generate the signed public–private key pair.
- Choose a random integer as secret key.
- Compute the as public key.
- SigGen: On inputting the public parameter param, the signing secret key d, and the message m, output the signature of message m . The steps for generating a signature are as follows.
- Randomly select integer .
- Compute , where R is a point on the elliptic curve E.
- Compute , and if/when r is 0, return to the first step to reselect k.
- Compute , where .
- Output the generated signature , where .
- Verify: On inputting the message m to be verified and it’s signature , output 0 or 1 (0 means failure, 1 means success). The steps for verifying a signature are as follows.
- Check whether the integers r and s belong to . If they do not belong, terminate the verification; otherwise, execute next step.
- Compute .
- Compute to verify signature.
- When , output 1, otherwise output 0.
3.2. Functional Signatures
Definition 1.
Functional signatures (FS) scheme for a message space and a function family ; it has four algorithms as follows.
- FS.Setup () On inputting a parameter , it can output the master signing key Msk and the master verification key Mvk.
- FS.KeyGen(Msk,f) On inputting the master signing key and a function , it outputs the signing key for f.
- FS.Sign(f,,m) On inputting the function , generated signing key , and the message that needs to be signed, it outputs the pair signature .
- FS.Verify(Mvk,,) On inputting the master verification key Mvk, a message and a signature , where , it outputs 1 or 0, where 1 indicates that the signature is valid.
3.3. Security Definition
Definition 2.
Unforgeability: The functional signatures is unforgeable if the advantage of any PPT algorithm in the following game is negligible:
- The challenger runs FS.Setup() and sends Mvk to adversary .
- Adversary is allowed to query the key generation oracle and a signing oracle; they are noted as and . The challenger initializes a dictionary indexed by tuples , which contained the signing keys: FS.KeyGen(Msk,f). This dictionary records the keys that were previously generated in the Unforgivability game. and are defined as follows:
- -
- : On inputting , the challenger runs as follows:
- 1.
- If there is an entry for in the dictionary, then the corresponding key is output.
- 2.
- Otherwise, by FS.KeyGen(Msk,f) sample a fresh key, add the to the dictionary in order to update it, and output .
- -
- : On inputting , the challenger runs as follows:
- 1.
- If there is an entry for in the dictionary, then the corresponding signature FS.Sign(f,,m) is output.
- 2.
- Otherwise, by FS.KeyGen(Msk,f) sample a fresh key, add the to the dictionary, and the corresponding signature FS.Sign(f,,m) is output.
- -
- The adversary wins the game if it can output a signature such that:
- 1.
- FS.Verify(Mvk,) = 1.
- 2.
- There does not exist m such that for any f that was sent as a query to the key generation oracle .
- 3.
- There does not exist a that was queried to the signing oracle and .
3.4. Smart Contract
In a private blockchain system, the smart contract is compiled by the Solidity language and each different node represents a different private blockchain account. The smart contract is a type of computer protocol that can be executed through the account. Briefly, the smart contract is a computer program that has been compiled and deployed on the private blockchain. The process of deploying smart contracts is shown in Figure 1.
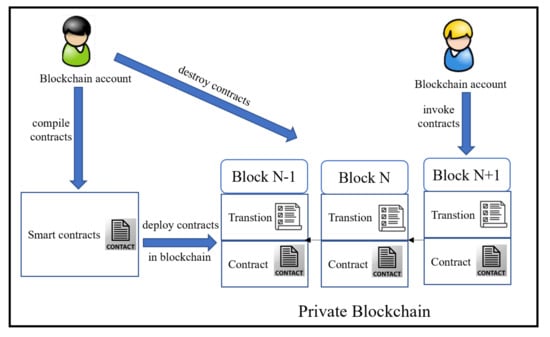
Figure 1.
Smart contract deploy and invoke process on the private blockchain.
4. Proposed System Model and Multi-Party Functional Signatures Method
This section gives the concrete system architecture framework proposed in this paper. Moreover, it gives the specific setup of the scheme and the construction of smart contracts to run.
4.1. System Model Framework
The concrete system model is shown in Figure 2. When a transaction in the private blockchain requires fine-grained collaborative authentication by multiple nodes, the full nodes prefer to send the parameter of the signature scheme to each mining node. A complete transaction is recorded as , and a partial transaction is recorded as . The detailed steps are described below:
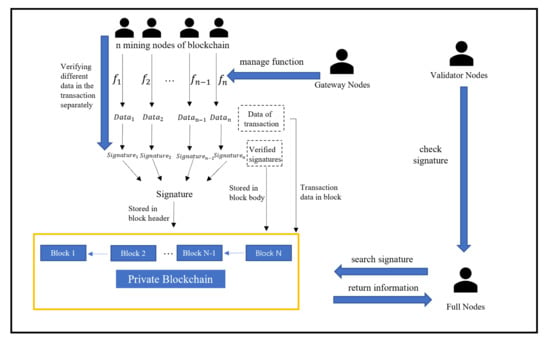
Figure 2.
The framework of the system model.
- Gateway nodes manage the function f of functional signatures using smart contracts.
- Each mining node checks different of , divided by function f of functional signatures. After that, the signature corresponding to the respective is generated. Gateway nodes manage the function f of functional signatures using smart contracts.
- After receiving all partial transaction signatures , an aggregated signature is generated and stored in the block header.
- Full nodes can search for all the transaction signatures stored in the blockchain.
- Validator nodes check the correctness of the queried signature. Once an error occurs in the signature stored in the block header, the partial transaction signature stored in the block body can be queried and checked.
As is shown in Figure 3, the final aggregated signature is stored in the block header, and the signatures generated for different transactions are stored in the respective transactions. The validator nodes can query the signatures of the different transactions from full nodes and verify that the signatures are valid.
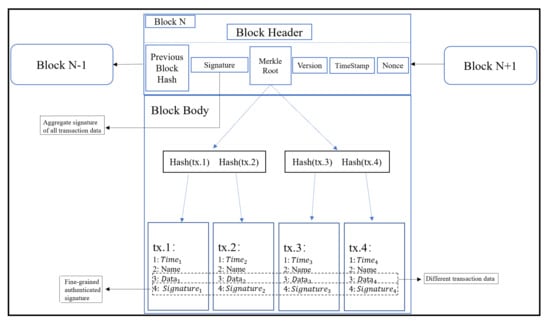
Figure 3.
Simple block structure.
4.2. Smart Contract Settings and Proposed Concrete Scheme
This subsection gives the specific smart contract setup and scheme construction.
4.2.1. Smart Contract Design
This section introduces the concrete process of deployment and invocation of smart contracts and related algorithms. Some special variables are used in the algorithm of smart contracts: authorizeAccount is a set of trusted private blockchain accounts (nodes of private blockchain), functionSet stores all functions f of functional signatures, ct.sender is the account, and f.Set stores the account of who can use f. The specific definitions of these variables are as follows:
- authorizeAccount: When deploying the smart contract, the gateway nodes collect all legal account identity information. All these accounts consist of authorizeAccount.
- functionSet: The set stores all the functions f of functional signatures. Functions f of functional signatures that do not belong to functionSet are prohibited from being invoked.
- ct.sender: This invokes the contract’s account.
- f.Set: All functions that are stored in functionSet have a set f.Set, and some accounts are stored in it. If ct.sender does not belong to f.Set, it cannot use f.
The concrete algorithm for the contract is as follows:
invokeF(): Algorithm 1 can be executed by legitimate accounts. The gateway nodes determine whether the function f invoked by this node is legitimate by the returned value.
addUser(,): Algorithm 2 shows that the system model can dynamically endow nodes with the use of function f.
deleteUser(,): Algorithm 3 shows that the system model can dynamically reject the node’s use of the function f.
| Algorithm 1: invokeF |
Input: f Output: bool if ct.sender does not exist in authorizeAccount then throw;end if f does not exist in functionSet then return false;else
if ct.sender does not exist in f.Set then return false; else return true; end end |
| Algorithm 2: addUser(f,) |
Input: f, Output: bool if f does not exist in functionSetthen return false; else
if ct.sender has exist in f.Set then return false; else f.set[ct.sender] ⇐ true return true; end end |
| Algorithm 3: deleteUser(f,) |
Input: f, Output: bool if f does not exist in functionSet then return false; else
if ct.sender has not exist in f.Set then return false; else f.set[ct.sender] ⇐ false return true; end end |
4.2.2. Concrete Multi-Party Functional Signatures Scheme
This paper now describes the details of the multi-party functional signatures (MFS) scheme. This paper denotes the setup phase, the key generation phase, the signature phase, and the verification phase of the scheme as MFS.Setup, MFS.KeyGen, MFS.Sign, and MFS.Verify.
- MFS.Setup: The full node first selects the security parameter and runs the Setup algorithm of the ECDSA signature to generate public parameters = {E, , G, P, p, q, H}, then randomly selects as the master private key Msk and computes the master public key as Mvk. The full node chooses n random numbers and computes , where satisfies .
- MFS.KeyGen: Each mining node initiates a request to the full node, and then the full node sends the to mining node by a secure channel. Each mining node selects randomly to send to the full node by Diffie–Hellman key exchange. The full node computes and , where k is stored in the full node and is sent to each mining node . Let be chosen randomly by the full node, and is computed byEach mining node sends H() to the full node, where is the identification information of node . The full node stores securely. The full node randomly selects and computes . Two nodes and receive and , respectively, by Diffie–Hellman key exchange, where they satisfyEach mining node computesThe public key of mining node is . Each mining node gets by Diffie–Hellman key exchange as a part of the private key sk and invokes a smart contract to verify the authenticity of . The full node signs for by the Msk and SigGen algorithms of the ECDSA signature, the signature of is noted as . Creating the certificate , the private key of node is .
- MFS.Sign: To sign the message m, all the nodes start to get e = H(m) and computeThe signature generated by each mining node is , where . The full node receives from all nodes and calculates using the internally saved . Finally, the output is the .
- MFS.Verify: For overall transactions, the data of the transactions verifier can verify signature Sig by using the Verify algorithm of the ECDSA signature. If the data of transactions verifier needs to check the authenticity of the signature of node , he can check that:
- 1.
- ;
- 2.
- Whether is valid by the Verify algorithm of the ECDSA signature and Mvk.
- Correctness: The correctness of the signature for node is guaranteed by the ECDSA signature algorithm. The following equation determines the correctness of Sig:
5. Security Analysis
This section uses the security model of [10] and give proof of the security of the multi-party functional signatures scheme and system model.
Theorem 1.
If the signature scheme ECDSA is existentially unforgeable under chosen message attacks, then the proposed multi-party functional signatures scheme as specified above satisfies the unforgeability requirement for functional signatures.
Proof of Theorem 1.
In the unforgeability game, one can define a PPT adversary noted as , who can be allowed to make a query to the two random oracles denoted and . Then create a set [N] to represent all nodes. Let be the subset of [N] and satisfy that the nodes in are honest. The set of corrupted nodes is denoted as :=. Assume that () is the polynomial number and only can query () times in the oracles and . This game can use as a subroutine to construct another adversary such that, if adversary wins in the unforgeability game for multi-party functional signatures with non-negligible probability, then it can show that can break the unforgeability game of the ECDSA signature scheme, which is assumed to be unforgeable against the chosen message attack.
For to win the unforgeability game of multi-party functional signatures, either it can generate a final signature Sig by corrupting a dishonest node or simply produce the signature of honest node , where such that:
- For each , is a valid signature of m under the verification key .
- For each , is a valid signature of under the master public key Mvk.
- for all i.
- has not sent a query of form for all i to the oracle , and is in the range of the .
- has not sent a query of form for all i to the oracle .
Let us discuss the first situation, where the can be produced by , where . It can assume that there are n-1 corrupted nodes of which the only uncorrupted node is noted as . There are two types of forgery:
- Type I forgery: The tuples satisfy that has not already been signed under the master key Mvk for queries from to the oracles and .
- Type II forgery: The tuples satisfy that has been signed under the master key Mvk for queries from to the oracles and .
This game now can denote another adversary by the above. It first assumes that the all signatures with Mvk generated by oracles and can be used as intermediate steps for responding to the ’s queries. In the unforgeability game for the ECDSA scheme, it defines that wins the unforgeability game only if he can output forged signatures successfully for a message that was not queried , where is a oracle can use; is a verification key used by .
As a challenger, needs to interact with in the unforgeability game for multi-party functional signatures; must simulate the oracles and in order to interacting with , and tosses a coin b to guess the type of forgery will generate.
- Case 1: b = 1: guesses that will produce a Type I forgery:
During interacting with , sets the as the master verification key in this simulation; generates and maintains a dictionary indexed by tuples to simulate the oracles and . Adversary will respond to the ’s queries as follows:
- :
- -
- If there exists an entry for the tuple in the dictionary, then output the corresponding value .
- -
- Otherwise, randomly selects as , and computes as ; obtains from his oracle, and return to . He also updates the dictionary by adding the entry .
- :
- -
- If there exists an entry for the tuple in the dictionary, it has the . He can generate a signature . Because he knows all about the corrupted nodes, he can output , where and .
- -
- Otherwise, randomly selects as , and computes as ; obtains from his oracle, and updates the dictionary by adding the entry . He then generates Sig by , and outputs , where and .
Finally, outputs the signatures and Sig, where ; then outputs the as a forged signature in the unforgeability game for ECDSA scheme.
- Case 2: b = 0: guesses that will produce a Type II forgery:
Here, randomly selects as master private key Msk and computes dP as the master public key Mvk. Then generates , , , and , where and satisfy that and , respectively; can compute as and sends the of all nodes to along with the of the specified set of corrupt nodes. In addition, guesses a value between 1 and () as a special index of signing queries of multi-party functional signatures where the challenge verification key will be embedded. This game uses a variate denoted as to indicate the numbers of signing keys already generated and initializes . Adversary maintains a dictionary indexed by tuples for responding to the queries of ; responses to the queries issued by as follows:
- :
- -
- If there exists an entry for the tuple in the dictionary with the value CHA, abort.
- -
- If there exists an entry for the tuple in the dictionary with a value that is not CHA, output the key .
- -
- Otherwise, randomly selects as , and computes as ; generates the by himself and returns to . He also updates the dictionary by adding the entry .
- :
- -
- If there exists an entry for the tuple in the dictionary, . He generates a signature Sig by himself, and outputs , where and .
- -
- If there is no the tuple in the dictionary, and , generates a new key pair by randomly choosing the as and computing as ; signs to generate by using Msk, and sets tuple in his dictionary to . He then generates the signature Sig on message m by using Msk, outputs , where and , and sets .
- -
- If there is no tuple in the dictionary and , or if the tuple in the dictionary is set to CHA, then generates the signature of m under by oracle , , computes by using Msk, and outputs , where and . If there is no tuple in the dictionary, sets it to CHA. Then .
If does not abort, finally outputs a signature Sig on m; outputs as the forged signature in this unforgeability game for the ECDSA signature scheme.
It can indicate that, if breaks the multi-party functional signatures scheme with non-negligible probability, then can break ECDSA scheme with non-negligible probability. In this unforgeability game, has two different types of forgery.
For Type I forgery, this game can know that this forgery has a signature on the new message that was never signed under the master public key Mvk by the oracle. In Type I forgery, this game assumes that the probability of breaking the multi-party functional signatures scheme is Pr[I], and it is obvious that the probability of breaking the ECDSA scheme is greater than or equal to Pr[I].
For Type II forgery, when generates a Type II forgery, the corresponding should have been signed under the master public Mvk during the queries of to the oracles and . It shows that the tuple cannot be queried by to because the signature generated under the signing key is not a valid forgery in the multi-party functional signatures scheme if it is subsequently the signing key for the response. Therefore, the oracle already has been issued the tuple . It can note that if does abort, it must be that he embedded his challenge in a query with the form . In Type II forgery, it assumes that the probability of breaking the multi-party functional signatures scheme is Pr[II], and the probability of breaking the ECDSA scheme is greater than or equal to Pr[II].
Thus, if can generate a forgery in the multi-party functional signatures scheme with non-negligible probability Pr[I] + Pr[II], then can break the ECDSA scheme with non-unforgeability probability (Pr[II] + Pr[II]). However, the ECDSA scheme is existentially unforgeable under chosen message attacks, and the probability of the successfully breaking the ECDSA scheme is negligible. It can show that generates a forgery in the multi-party functional signatures scheme with negligible probability. □
Theorem 2.
The multi-party functional signatures in this paper have collision resistance.
Proof of Theorem 2.
In the multi-party functional signatures scheme, it needs to be assumed that the full node is secure. The master private key of the scheme is ; therefore, even if n − 1 nodes are corrupted, the adversary cannot recover d by corrupted nodes. Furthermore, the nodes have , even if n-1 corrupted nodes provide , the adversary cannot compute that the honest node has, so it cannot get . The above illustrates this scheme resists n-1 corrupted nodes collusion attacks. □
6. Results
This section analyzes the computation complexity and implements the proposed system model on a personal computer.
6.1. Complexity Analysis
As shown in Table 2, this paper gives a theoretical analysis of the proposed scheme. Some notations of time complexity analysis are given as follows.

Table 2.
Theoretical cost analysis.
- : Time costs to run one hash function;
- : Time costs of running one multiplication operation in additive group G;
- : Time costs of running one multiplication operation in field ;
- : Time costs of running one addition operation in field ;
- : Time costs of running one ;
- : Time costs for full node to communicate with nodes;
- : Time costs of running one extended Euclidean algorithm;
- : Time costs of running one smart contract;
- : Time costs of running one Diffie–Hellman key exchange.
In the proposed scheme, each mining node must perform one hash function, three multiplications in the field , additions in the field , one multiplication in G, one , and n Diffie–Hellman key exchanges. Each mining node needs to invoke one smart contract to use function f. Excluding communication time, each mining node will cost
For the full node, it needs to run some random number generation algorithm and ordinary addition and multiplication operations several times (the time cost of these steps is negligible). In addition, it runs the n hash function, two multiplications in G, multiplications in the field , additions in field , extended Euclidean algorithms, and n Diffie–Hellman key exchanges. Therefore, the full node requires
For communication between the full node and mining node, it requires .
The scheme presented in this paper implements fine-grained authentication for certain transactions, which is highly significant. Additionally, for multi-party signature schemes, it is essential that they satisfy resistance to collusion attacks and can be proven secure. As is shown in Table 3, the proposed scheme has certain advantages compared to the previous scheme. The proposed scheme ensures that every part of the transaction is validated, reflecting the fine-grained nature of the scheme. Furthermore, the scheme is adapted to run on multiple nodes of the blockchain, and it is provably secure. For the collusion attack, the proposed scheme can effectively resist such attacks. Even if nodes are corrupted, the adversary cannot forge the signature generated by this scheme. The significant advantage of this paper’s scheme over previous schemes is that it can achieve fine-grained authentication of different parts of the transaction and resist collusion attacks.

Table 3.
Properties and disadvantages of the schemes.
6.2. Implement
This paper used a personal computer (RedmiBook with AMD CPU Ryzen 5 5600H with Radeon Graphics @ 3.30 GHz with 16.0 GB RAM and Windows 10 Home OS) implementing the proposed scheme in Python 3.9.6. This paper implements the scheme with different numbers of nodes.
This paper chose the secp256k1 curve that is used in Bitcoin for the simulation experiment. This paper implemented the experiments with different numbers of nodes. Each execution was run 1000 times, and this paper computed the average as the final result. The results of the experiment are shown in Figure 4. It can see that the running time of the scheme slows down as the number of nodes increases: about 343 ms for three nodes, about 552 ms for six nodes, and about 791 ms for nine nodes. Regarding time consumption, the scheme in this paper can be applied to the private blockchain.
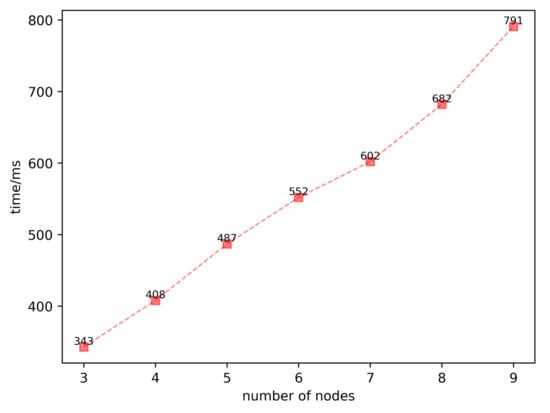
Figure 4.
Running times for different numbers of nodes.
This paper deployed smart contracts using Solidity language and Ropsten to test the network. The compiler of Solidity language is Remix IDE, and its version is 0.7.4.We. This paper used MetaMask to manage private blockchain accounts. In the experiment, the gasPrice was set to 1.49 , where 1 = = . This paper defines as the length of set functionSet. As shown in Table 4 and Table 5 and Figure 5, some costs of smart contracts were tested through this experiment.

Table 4.
Cost of deploying smart contract ( = 1.49 and 1 = $1026).

Table 5.
Cost of smart contract under different lengths of functionSet ( = 1.49 and 1 = $1026).
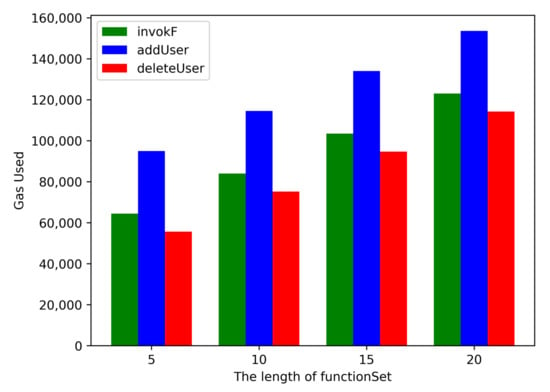
Figure 5.
Smartcontract costs under different lengths of functionSet.
Costs of smart contract deployment and algorithms increase as the functionSet length increases. In this experiment, the cost of deploying smart contract for is $0.973. When the length of functionSet is 10, 15, and 20, the cost of deploying smart contract is $1.144, $1.315, and $1.486. As shown in Table 5 and Figure 5, when , gasPrice of invokeF, addUser, and deleteUser is 64,445 , 94,981 and 55,675 , respectively. Obviously, with the increase of the , the gasPrice required to invoke the smart contract also increases. GasPrice of addUser is always more than invokeF and deleteUser. All gasPrice consumption is reasonable, which indicates that binding function f of the function signature to a private smart contract is valid.
6.3. The Limitations of the Study
This paper is preconfigured to use the function signature of function f in the smart contract, which may limit the operability of this scheme. Additionally, this paper is directly combined with ECDSA signatures and does not apply to other elliptic curve signatures.
7. Conclusions
Although some researchers have proposed various multi-party signatures to tackle the issue of verifying private blockchain transactions by multiple parties, the previous construct still needs to address authenticating different parts of a transaction. This paper presents a novel approach that combines multi-party ECDSA signatures with functional signatures to enable fine-grained authentication of different parts of the entire transaction. In addition, the function f of the functional signature is safeguarded and implemented using a smart contract on a private blockchain. The research presented in this paper is motivated by the fact that previous multi-party signature schemes designed for blockchains cannot authenticate the entire transaction at a fine-grained level. Furthermore, when the final signature fails to pass the authentication, the whole transaction will be rejected, which greatly wastes time for the partly correct transaction to pass the authentication. Experimental results show that the proposed scheme is feasible to be applied to the blockchain.
Exploring how to design an efficient and multi-party signature with an automatic fine-grained division of blockchain transactions is an important research direction for the future. The multi-party functional signatures proposed in this paper will also find different applications outside of the private blockchain.
Author Contributions
Conceptualization, Y.Z. and Q.Z.; methodology, Y.Z.; software, Y.Z., K.W. and M.C.; validation, Y.Z., Q.Z. and Z.Z.; formal analysis, Y.Z.; investigation, Y.Z.; resources, Y.Z.; data curation, Y.Z.; writing—original draft preparation, Y.Z.; writing—review and editing, Y.Z. and Q.Z.; visualization, Y.Z.; supervision, Q.Z.; project administration, Q.Z.; funding acquisition, Q.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by The National Key R&D Program of China (grant number 2021YFA1000600) and National Natural Science Foundation of China (grant number 12171114).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Fanning, K.; Centers, D.P. Blockchain and its coming impact on financial services. J. Corp. Account. Financ. 2016, 27, 53–57. [Google Scholar] [CrossRef]
- Nguyen, Q.K. Blockchain-a financial technology for future sustainable development. In Proceedings of the 2016 3rd International Conference on Green Technology and Sustainable Development (GTSD), Kaohsiung, Taiwan, 24–25 November 2016; pp. 51–54. [Google Scholar]
- Treleaven, P.; Brown, R.G.; Yang, D. Blockchain technology in finance. Computer 2017, 50, 14–17. [Google Scholar] [CrossRef]
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A review on security challenges in internet of things (IoT). In Proceedings of the 2021 26th International Conference on Automation and Computing (ICAC), Portsmouth, UK, 2–4 September 2021; pp. 1–6. [Google Scholar]
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656. [Google Scholar] [CrossRef]
- Nasir, A.; Shaukat, K.; Khan, K.I.; Hameed, I.A.; Alam, T.M.; Luo, S. What is core and what future holds for blockchain technologies and cryptocurrencies: A bibliometric analysis. IEEE Access 2020, 9, 989–1004. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A peer-to-peer electronic cash system. Bitcoin 2008, 4. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 March 2023).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Shaukat, K.; Alam, T.M.; Luo, S.; Shabbir, S.; Hameed, I.A.; Li, J.; Abbas, S.K.; Javed, U. A review of time-series anomaly detection techniques: A step to future perspectives. In Advances in Information and Communication: Proceedings of the 2021 Future of Information and Communication Conference (FICC); Springer International Publishing: Vancouver, BC, Canada, 2021. [Google Scholar]
- Javed, U.; Shaukat, K.; Hameed, I.A.; Iqbal, F.; Alam, T.M.; Luo, S. A review of content-based and context-based recommendation systems. Int. J. Emerg. Technol. Learn. 2021, 16, 274–306. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V. A novel deep learning-based approach for malware detection. Eng. Appl. Artif. Intell. 2023, 122, 106030. [Google Scholar] [CrossRef]
- Perez, A.T.E.; Rossit, D.A.; Tohme, F.; Vasquez, O.C. Mass customized/personalized manufacturing in Industry 4.0 and blockchain: Research challenges, main problems, and the design of an information architecture. Inf. Fusion 2022, 79, 44–57. [Google Scholar] [CrossRef]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic review of security vulnerabilities in ethereum blockchain smart contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V. A novel method for improving the robustness of deep learning-based malware detectors against adversarial attacks. Eng. Appl. Artif. Intell. 2022, 116, 105461. [Google Scholar] [CrossRef]
- Boyle, E.; Goldwasser, S.; Ivan, I. Functional signatures and pseudorandom functions. In Proceedings of the Public-Key Cryptography–PKC 2014: 17th International Conference on Practice and Theory in Public-Key Cryptography, Buenos Aires, Argentina, 26–28 March 2014; Proceedings 17. pp. 501–519. [Google Scholar]
- Backes, M.; Meiser, S.; Schröder, D. Delegatable functional signatures. In Proceedings of the Public-Key Cryptography–PKC 2016: 19th IACR International Conference on Practice and Theory in Public-Key Cryptography, Taipei, Taiwan, 6–9 March 2016; Proceedings, Part I. pp. 357–386. [Google Scholar]
- Okamoto, T.; Takashima, K. Decentralized Attribute-Based Signatures. In Proceedings of the Public Key Cryptography, Nara, Japan, 26 Feburary–1 March 2013; pp. 125–142. [Google Scholar]
- Lu, H.; Jin, C.; Helu, X.; Zhu, C.; Guizani, N.; Tian, Z. AutoD: Intelligent blockchain application unpacking based on JNI layer deception call. IEEE Netw. 2020, 35, 215–221. [Google Scholar] [CrossRef]
- MacKenzie, P.; Reiter, M.K. Two-party generation of DSA signatures. In Proceedings of the Advances in Cryptology–CRYPTO 2001: 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Proceedings 21. pp. 137–154. [Google Scholar]
- Lindell, Y. Fast secure two-party ECDSA signing. In Proceedings of the Advances in Cryptology–CRYPTO 2017: 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Proceedings, Part II 37. pp. 613–644. [Google Scholar]
- Castagnos, G.; Catalano, D.; Laguillaumie, F.; Savasta, F.; Tucker, I. Two-party ECDSA from hash proof systems and efficient instantiations. In Proceedings of the Advances in Cryptology–CRYPTO 2019: 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; Proceedings, Part III 39. pp. 191–221. [Google Scholar]
- Lindell, Y.; Nof, A. Fast secure multiparty ECDSA with practical distributed key generation and applications to cryptocurrency custody. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1837–1854. [Google Scholar]
- Doerner, J.; Kondi, Y.; Lee, E.; Shelat, A. Threshold ECDSA from ECDSA assumptions: The multiparty case. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 1051–1066. [Google Scholar]
- Gennaro, R.; Goldfeder, S. Fast multiparty threshold ECDSA with fast trustless setup. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1179–1194. [Google Scholar]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A survey on machine learning techniques for cyber security in the last decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Halpin, H.; Piekarska, M. Introduction to Security and Privacy on the Blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 1–3. [Google Scholar]
- Li, X.; Xu, J.; Fan, X.; Wang, Y.; Zhang, Z. Puncturable signatures and applications in proof-of-stake blockchain protocols. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3872–3885. [Google Scholar] [CrossRef]
- Zhu, Y.; Guo, R.; Gan, G.; Tsai, W.T. Interactive incontestable signature for transactions confirmation in bitcoin blockchain. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; Volume 1, pp. 443–448. [Google Scholar]
- Mercer, R. Privacy on the blockchain: Unique ring signatures. arXiv 2016, arXiv:1612.01188. [Google Scholar]
- Gong, B.; Cui, C.; Hu, M.; Guo, C.; Li, X.; Ren, Y. Anonymous traceability protocol based on group signature for blockchain. Future Gener. Comput. Syst. 2022, 127, 160–167. [Google Scholar] [CrossRef]
- Kokoris Kogias, E.; Jovanovic, P.; Gailly, N.; Khoffi, I.; Gasser, L.; Ford, B. Enhancing Bitcoin Security and Performance with Strong Consistency via Collective Signing; USENIX Association: Berkeley, CA, USA, 2016. [Google Scholar]
- Zhou, X.; Wu, Q.; Qin, B.; Huang, X.; Liu, J. Distributed bitcoin account management. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 105–112. [Google Scholar]
- Alangot, B.; Suresh, M.; Raj, A.S.; Pathinarupothi, R.K.; Achuthan, K. Reliable collective cosigning to scale blockchain with strong consistency. In Proceedings of the Network and Distributed System Security Symposium (DISS’18), San Diego, CA, USA, 18–21 February 2018; pp. 1932–4537. [Google Scholar]
- Yu, M.; Zhang, J.; Wang, J.; Gao, J.; Xu, T.; Deng, R.; Zhang, Y.; Yu, R. Internet of Things security and privacy-preserving method through nodes differentiation, concrete cluster centers, multi-signature, and blockchain. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718815842. [Google Scholar] [CrossRef]
- Maxwell, G.; Poelstra, A.; Seurin, Y.; Wuille, P. Simple schnorr multi-signatures with applications to bitcoin. Des. Codes Cryptogr. 2019, 87, 2139–2164. [Google Scholar] [CrossRef]
- Yu, H.; Wang, H. Elliptic curve threshold signature scheme for blockchain. J. Inf. Secur. Appl. 2022, 70, 103345. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, P.; Liu, Y. Secure and efficient multi-signature schemes for fabric: An enterprise blockchain platform. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1782–1794. [Google Scholar] [CrossRef]
- Uganya, G.; Baskar, R. Modified Elliptic Curve Cryptography Multi-Signature Scheme to Enhance Security in Cryptocurrency. Comput. Syst. Sci. Eng. 2023, 45, 641–658. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).