Abstract
The coal gasifier is the core unit of the coal gasification system. Due to its exposure to high temperatures, high pressures, and aggressive media, it is highly susceptible to serious accidents in the event of failure. Therefore, it is important for the gasifier to perform failure-risk assessment to understand its safety status and provide safety measures. Bayesian networks (BNs) for risk analysis of process systems has received a lot of attention due to its powerful inference capability and its ability to reflect complex relationships between risk factors. However, the acquisition of basic probability data in a Bayesian network is always a great challenge. In this study, an improved Bayesian network integrated with a trapezoidal intuitionistic fuzzy number-based similarity aggregation method (TpIFN-SAM) is proposed for the failure-risk assessment of process systems. This approach used the TpIFN-SAM to collect and aggregate experts’ opinions for obtaining the prior probabilities of the root events in the BN. In the TpIFN-SAM, the intuitionistic fuzzy analytic-hierarchy-process method (IF-AHP) was adopted to assign the expert weights for reducing subjectivity or the bias caused by individual differences. To clarify the suitability of the proposed method, a case study of a coal gasifier was demonstrated, and both prediction and diagnosis analyses of the BN were performed; finally, the weak links of the gasifier were identified.
1. Introduction
The coal-gasification process is an essential part of the “clean coal” technology that can improve overall energy-conversion and -utilization efficiency [1]. This process is carried out in a gasifier (also known as a gasification furnace), in which the combustible parts of coal or coal coke are converted into gases like CO and H2 by chemical reactions at high temperatures and high pressures. In this condition, the gasifier needs to ensure safe operation. Fire and explosion are unimaginable consequences that may easily occur when equipment fails.
Equipment-failure-risk assessment is a necessary means to clarify the safety status of the equipment and ensure the normal operation of the chemical systems. There are numerous risk-assessment methods available in process systems, one group of which is based on a combination of logical/probabilistic diagrams and deductive reasoning, such as fault-tree analysis (FTA), event-tree analysis (ETA), the bow-tie model (BT), and Bayesian networks (BNs), and are very widely used for risk and reliability analysis due to their intuitiveness, expressiveness, ease of analysis, and reasoning [2,3,4,5]. Of these, BN is suitable for modelling and analyzing complex systems and has gained much attention compared to others, since it can handle the occurrence of multi-state variables, express conditional dependencies among events, and allow for bidirectional reasoning to identify the most failure-prone links of the system better [6,7,8]. As with other approaches, the limitation is that a BN cannot succeed without complete and accurate data (i.e., base-event probabilities and conditional-probability tables), and unfortunately in practice the required data are difficult to obtain. For this reason, a BN is often integrated with data-extraction technologies, particularly expert elicitation.
Currently, the common approaches to data acquisition for a BN include fuzzy set theory [9], rough set theory [10], evidence theory [11], the cloud model [12], and hybrid models [13]. Among them, the combination of fuzzy sets and a BN has been most extensively studied in process-safety engineering since fuzzy set theory is well recognized as a very effective mathematical tool for dealing with uncertain and incomplete information [14]. Kabir et al. [15] developed an O & G pipeline-failure model by assimilating a fuzzy set into a BN. In this model, the prior probability and conditional probability values in the BN can be interpreted according to the linguistic terms corresponding to the trapezoidal fuzzy numbers. Yazdi and Kabir [16] presented a comprehensive framework for risk evaluation of complex process systems through integrating fuzzy set theory with a BN. In this framework, the uncertainty problem of failure data was solved by expert knowledge with improved fuzzy AHP. Zhao et al. [17] also employed fuzzy AHP and BN to assess the domino effects in the coal-gasification process. Yan et al. [18] applied a BN with a fuzzy set to analyze biomass gasification when a gas leakage happens, and they confirmed the missing reliability failure probabilities by using expert judgments obtained based on linguistic terms corresponding to triangular and trapezoidal fuzzy numbers. Subsequently, Mostafa Pouyakian et al. [19] proposed a similar approach to analyze the possible risk factors of storage tanks with a floating roof. Akbar Rostamabadi et al. [20] integrated the fuzzy best–worst method (Fuzzy–BWM) with a BN for safety and reliability analysis of a process system that used Fuzzy–BWM for expert judgment to obtain the required fuzzy probabilities.
These research endeavors have contributed significantly to the successful utilization of BNs in the reliability and risk evaluation of process industries. However, the limitations are that the fuzzy set theory may cause deprivation and deformation of evaluation information because it uses only one membership function to represent the extent to which a particular target pertains to a set [21,22]. In reality, there are often situations where a person may suppose that a target pertains to a set to an extent, but they may not be quite sure about it, which means there may be indecision about the membership extent of the target in the set. For the purpose of resolving the challenge, Atanassov [23] proposed a intuitionistic fuzzy set (IFS) in 1986. In IFS theory there are two different functions, i.e., the membership and non-membership functions, to describe uncertain information. The difference between the two functions is called the degree of hesitation. The IFS theory extends the traditional fuzzy set theory, and it has a stronger ability to express and dispose of uncertainty than fuzzy set theory. In this light, Yu et al. [24] introduced triangular intuitionistic fuzzy numbers (a special case of IFS) to BNs for analysis of the fire damage and blast accident of a crude-oil-storage tank. This attempt showed the potential power of combining IFS with BNs. As far as intuitionistic fuzzy numbers (IFNs) are concerned, trapezoidal IFNs, as an extension of triangular IFNs, better accommodate for the description of non-deterministic information. This inspired us to try to integrate trapezoidal IFNs with BNs to analyze the failure risk of process systems so as to improve the feasibility and flexibility of BNs in engineering applications. Similarly, this is also the motivation for the new approach that is presented next.
When acquiring data using fuzzy set theory or intuitionistic fuzzy set theory, experts often need to be involved. Given the limitations of experts’ own knowledge and experience, certain means are required to deal with experts’ opinions to reduce subjective bias, usually through assigning different weights to the experts and then aggregating the different opinions [25]. Recently, the similarity aggregation method (SAM) [26] as an aggregation strategy for experts’ opinions has been of increasing interest in the safety analysis of process systems like storage tanks for hazardous chemicals [27,28,29] and oil and gas pipelines [30]; this is because it not only conforms to the custom of expert evaluation, but also enables the aggregation result to be more exact and workable [29,31].
The main contributions of this paper are as follows: (1) This study attempts to propose an improved framework integrating intuitionistic fuzzy AHP, trapezoidal intuitionistic fuzzy number-based SAM, and a Bayesian network for failure-risk assessment of a coal gasifier. (2) This framework uses intuitionistic fuzzy AHP to assign the expert weights for reducing subjectivity or the bias caused by individual differences and obtains the likelihood of occurrence of root events in the BN through trapezoidal intuitionistic fuzzy number-based SAM with experts’ judgment. (3) This strategy can more convincingly translate the judgments of all experts into a clear probability value by an intuitionistic fuzzy reasoning approach, thus overcoming the difficulty of obtaining the basic probability data in the BN.
For the remainder, the organization is arranged as follows: Section 2 introduces basic concepts of intuitionistic fuzzy sets, trapezoidal intuitionistic fuzzy numbers, and Bayesian networks. Section 3 presents the improved framework and provides the detailed implementation processes. In Section 4, an example of clarification is provided to demonstrate the specific analysis process and verify the feasibility of the method. Finally, the conclusions are described in Section 5.
2. Preliminaries
2.1. Intuitionistic Fuzzy Set
Definition 1
[23,32]: Let X be a general set, and the intuitionistic fuzzy set (IFS) is a set in
where and are membership and non-membership, respectively. Furthermore, the following requirements are fulfilled for all x ∈ X in the . An ordered interval pair consisting of and is an intuitionistic fuzzy set, written as .
For each intuitionistic fuzzy set in X, is the intuitionistic index of x in. This is a measure of the hesitancy of x to. Distinctly, for each x ∈ X, .
Definition 2
[33]: Let be an intuitionistic fuzzy number on a real number set R, and its membership and non-membership functions fulfill the following equations:
respectively, where , , and . a′, a, b, c, d, d′ ∈ R, such that and four functions , , , are known as the sides of intuitionistic fuzzy numbers. In addition, , , are non-decreasing continuous functions, and , are non-increasing continuous functions. A set of intuitionistic fuzzy numbers can be defined when the four functions are linear functions, as shown in Definition 3.
Definition 3
[34]: Let and be two intuitionistic fuzzy numbers , on a real number set R, then
2.2. Trapezoidal Intuitionistic Fuzzy Number
Definition 4
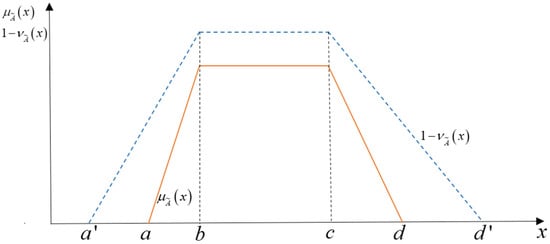
[33]: Let be a trapezoidal intuitionistic fuzzy number (TpIFN) with parameters and indicated as on a real number set R, then its membership and non-membership functions satisfy the following equations:
respectively, where , , . Figure 1 shows a general trapezoidal intuitionistic fuzzy number.

Figure 1.
A general trapezoidal intuitionistic fuzzy number.
Definition 5
[34]: Let and be two trapezoidal intuitionistic fuzzy numbers, then
2.3. The Expectation of a TpIFN
Heilpern [35] defined the expected interval and expected value of a fuzzy number. The expected interval and expected value can be applied to fuzzy-number ranking or comparison problems. The expected value as the center of the expected interval can be regarded as the expected payoff connected to a linguistic term. This can also be generalized for TpIFNs. It is assumed that that is a TpIFN, and EIμ and EIν denote the expected interval matching with membership and non-membership functions, respectively. The center of the expected interval of an intuitionistic fuzzy number is called the expected value of this number, denoted by , and EVμ and EVν denote the expected value corresponding to membership and non-membership functions, respectively. Its parametric form are = and = , where μ(α) and ν(α) are the parametric form of a TpIFN corresponding to membership and non-membership functions, respectively, and ; and ; [36].
Let , then
See Appendix A for the proof process.
2.4. Bayesian Network
A Bayesian network (BN), known as a probabilistic graphical model, is a directed acyclic graph (DAG) that binds graph theory with probability theory. A BN consists of nodes representing events (i.e., random variables) and oriented lines (from parent nodes to child nodes) connecting these nodes and representing their causal relationships. Each node and its set of parent nodes corresponds to a conditional probability distribution that indicates how much influence there is among the parent nodes and the child node. Given that a BN consists of n random variables X1, X2,…, Xn, according to the conditional independency and chain laws, the complete united probability distribution can be recorded as [37]
Figure 2 shows an illustration of a BN including six nodes. Node X1 is called the parent node of X2 and X3, whereas X2 and X3 are called the child nodes of X1. It is worth mentioning that X1 is also called the root node because it has no parent node. The complete united probability distribution of this can be expressed by Equation (16):
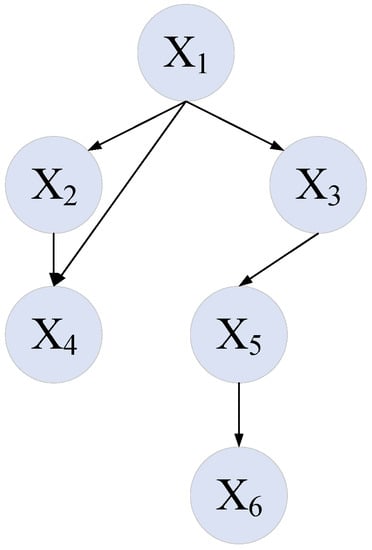
Figure 2.
Example of a Bayesian network.
In the BN model, it has a forward (predictive) and backward (diagnostic) ability of inference. The forward inference is the inference from the causes (root nodes) to their effects (leaf nodes). Under the circumstances, new beliefs about this effect are obtained by using information about causes. In contrast, the backward inference is the inference on the contrary side (i.e., from the effect back to the cause). In this inference, the process of obtaining a new belief about causes based on known effects is continuously estimated and upgraded. Bayes’ theorem can be used to advance the diagnosis analysis of the BN model (see Equation (18)) [37].
where A and B are two random events; P(A) and P(B) are the prior probability of event A and B, respectively; and P(A|B) is the posterior probability of event A occurring given after the occurrence of B.
2.5. Mapping to Bayesian Network from Fault Tree
The determination of a BN structure is the first step in using it for prediction and diagnosis. There are several ways of constructing BNs: (1) expert knowledge-based [38], (2) data-driven [39], and (3) mapped from other models like the fault-tree, event-tree, or bow-tie models [40,41,42]. The third approach is adopted in this study, where the potential accident scenarios of a system are first determined by a fault tree, which is then mapped into a BN according to the method shown in Figure 3.
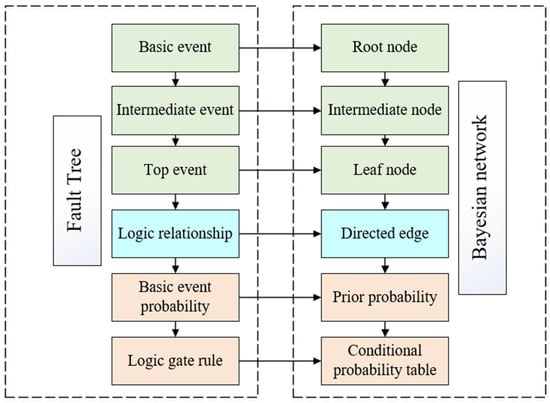
Figure 3.
Mapping rules from fault tree to Bayesian network.
The conditional probability table (CPT) is another key component of BNs for implementing inference. During this process, the logical gate of the fault tree (FT) is used to confirm the CPT of each node in the BN. The logic gate rules of the FT describe the fault–logic relationship between parent and child events. Table 1 and Table 2 show the rules of how to obtain a CPT according to the two most critical logic gates of FT: the “AND” gate and the “OR” gate [40].

Table 1.
CPT corresponding to the AND gate in FT (Occ: occurred; Non: non-occurred).

Table 2.
CPT corresponding to the OR gate in FT (Occ: occurred; Non: non-occurred).
3. Proposed Model for Failure-Risk Assessment Based on BN with TpIFN-SAM
3.1. General Framework
The proposed framework is mainly used to analyze the failure probability of process systems, which consists of five core parts—construction of the BN through FT, expert elicitation, aggregation of experts’ opinions by the TpIFN-SAM, the defuzzification process, and BN analysis—and is shown in Figure 4. The specific analysis process is described from Section 3.2, Section 3.3, Section 3.4, Section 3.5, Section 3.6 and Section 3.7.
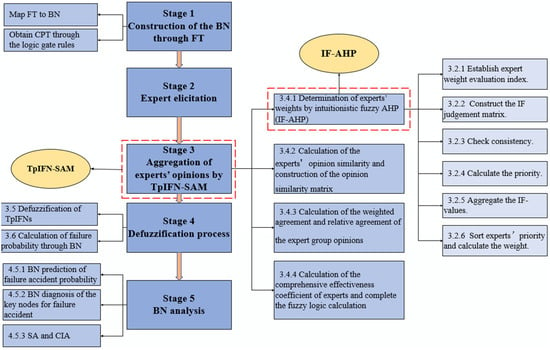
Figure 4.
The proposed analysis framework.
3.2. Construction of the BN through FT
The construction of a BN describing system-failure scenarios and paths is the first step in analyzing the probability of possible failures in a process system. Here, the FT is first drawn according to the system’s structural characteristics and associated risk factors, where the top event is generally set as the most undesired event. Then, the FT is mapped into a BN with CPTs using the mapping rules mentioned in Section 2.5.
3.3. Expert Elicitation
In this framework, expert elicitation is put to use for computing the probabilities of root events in the BN when the accurate probabilities of the events are lacking. In generally, the experts cannot give accurate probability values. This study therefore uses a method combining the TpIFNs and expert elicitation to elaborate the failure probabilities of each root node. Experts express their opinions on risk events in linguistic terms based on the practice or standards in the actual situation in this industry. In addition, the natural estimate of human memory capacity is 7 ± 2 grades [28,43]. Thus, 5–9 language terms scored by experts is most appropriate. Furthermore, heterogeneous expert judgment is adopted to reduce the prejudice of expert evaluation.
3.4. Aggregation of Experts’ Opinions by TpIFN-SAM
3.4.1. Determination of Experts’ Weights by Intuitionistic Fuzzy AHP (IF-AHP)
For the purpose of resolving the subjective preferences of experts and the incompleteness of individual knowledge and experience that may lead to biased results, the preference is usually to create an expert group of professionals and the relative importance of each expert’s opinion is represented by assigning weights to each expert. There are several expert-weighting methods, like the method of arithmetic average [22], the Delphi method [44], and AHP [45]. However, these methods are often criticized for failing to sufficiently solve the intrinsic ambiguity and subjectivity. As an extension of AHP, intuitionistic fuzzy AHP (IF-AHP) [46] can enhance the inconsistent intuitive-preference relationship without the involvement of decision-makers, thereby fundamentally solving the above-mentioned problems. As a result, this work employs the IF-AHP method to acquire the expert-weight coefficients. The specific calculation of the expert weights are as follows.
Step 1. Establish the evaluation indices of expert weights.
There are some general deviations in the experts’ judgements on the same event. This situation is affected by their professional position, educational background, and work experience. Therefore, a three-level hierarchical structure diagram of judging expert weights is established, as shown in Figure 5. Professional position, education level, and service time are accommodated as the evaluation indices of expert weights.
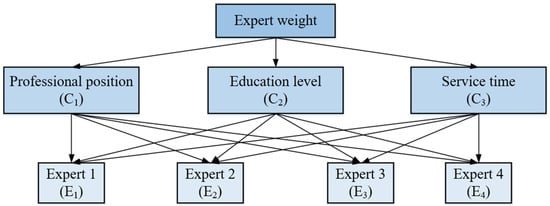
Figure 5.
Three-level hierarchical structure of judging expert weights.
Step 2. Construct the IF-judgment matrix.
The intuitionistic fuzzy judgment matrices for the three-level indices are then established. Factors belonging to the same level of each factor of the previous level are matched and compared to build an intuitionistic fuzzy judgment matrix: , with i, j representing the rows and columns of the matrix, respectively, where rij = (μij, νij); μij denotes the degree to which an expert prefers i when comparing the importance of factor i and factor j; νij denotes the degree to which an expert prefers j; and πij = 1 − μij − νij denotes the hesitation degree. To better identify the intuitionistic preference relationship, an evaluation scale table is constructed, as shown in Table 3.

Table 3.
IF-AHP preference scale.
Step 3. Check consistency.
The consistency-test formula shown below is given for distance measurement based on the intuitionistic fuzzy information [46]:
where is the intuitionistic fuzzy judgment matrix obtained by pairwise comparison of indices at each layer , is the intuitionistic fuzzy consistency-judgment matrix calculated from the intuitionistic fuzzy judgment matrix, and n represents the number of experts.
Let when j > i + 1, where
Let when j = i + 1; let when j < i + 1.
Substitute , into , if , then pass the consistency check; if , the parameters σ will be set to iterate—that is, to transform the matrix by regulating the iterative parameters σ until it passes. Given parameters σ (σ ∈ [0, 1]), let
Substitute the adjusted matrix into , and then we can get
Step 4. Calculate the priority.
After obtaining the intuitionistic fuzzy consistency-judgment matrix, the priority of the indices of the previous layer is calculated by
where i denotes the number of experts.
Step 5. Aggregate the IFNs.
According to the priority ԑi, the aggregated priority value of each expert Wi can be calculated by
Step 6. Sort experts’ priority and calculate their weights.
The crisp value of the priority of each expert is obtained by
where a smaller ρ(Wi) represents stronger priority from the expert. The relative weight of each expert can be calculated by
where
3.4.2. Calculation of the Experts’ Opinion Similarity and Construction of the Opinion Similarity Matrix
When the weights of all experts in the expert group are determined, the experts will be consulted to give the probability of occurrence of the root events in the BN as regards linguistic terms. These opinions are converted into the corresponding TpIFNs. The experts’ opinion similarity can then be given by Equation (30).
where is the expectation of the TpIFN converted from the ith expert’s linguistic opinion on the probability of a certain root event’s occurrence, and it can be calculated by Equation (10) in Section 2.3. is the opinion similarity between the ith expert and the jth expert. If there are m experts in the group, the similarity matrix Sm is
where when i ≠ j, and Sij = 1 when i = j.
3.4.3. Calculation of the Weighted Agreement and Relative Agreement of Each Expert
The weighted agreement degree of each expert’s opinion can be calculated by
where Ei (i = 1,2, …, m) is the ith expert, and then the relative agreement degree of each expert can be obtained by
3.4.4. Calculation of the Consensus Degree Coefficient of Experts and Aggregation of the Opinions
Since the relative importance of experts is variable, each expert has their own weight coefficient wi. The consensus degree coefficient (CDCi) of the ith expert can be considered as
where β (0 < β < 1) is defined as the relaxation factor, which represents the importance of the average agreement of experts compared to the relative agreement. After that, the , which means the result of aggregation, can be confirmed as
where (·) is the multiplication operator of the TpIFNs.
3.5. Defuzzification of TpIFNs
After the occurrence possibility of each root event expressed as a TpIFN is obtained through TpIFN-SAM, the defuzzification process is required in order to gain the clear value of the possibility, which is called the possibility score (PS). In this work, the centroid method (see Equation (36)) is adopted to perform the defuzzification of a TpIFN .
3.6. Calculation of Failure Probability of the System through BN
For the purpose of launching the analysis of the failure probability of the system using the BN, it is essential here to convert the PSs of the root nodes into conventional failure-probability values (FPs). In general, the formula proposed by Onisawa [47] can be adopted to translate PS into FP. However, this approach is not widely applicable due to the distinction in failure-probability classification standards in different industries, as well as the difference in the definition of linguistic scale for the failure probability [48]. Therefore, a corresponding further calculation method is adopted to convert PS into FP, and the formula is as follows [24]:
where
3.7. Sensitivity Analysis (SA) and Critical Importance Analysis (CIA)
Besides calculating the failure probability of a system using BNs, the identification and analysis of critical events affecting the system failure is also an important task in failure assessment. However, the results may be inaccurate if merely relying on prior or posterior probabilities to identify the most critical events. Therefore, this work presents several analysis methods, such as the ratio of variation (RoV), sensitivity analysis (SA), and criticality-importance analysis. RoV is used to measure the degree of the effect of root events in terms of system failure, and it can be calculated by [24]
where and indicate the posterior and prior probability of the ith event, respectively.
SA can provide a great degree of help in verifying the probabilistic parameters of BN. This is achieved by researching the influence of tiny changes in numerical parameters on the posterior probability. Highly sensitive parameters have a more significant effect on reasoning results. The sensitivity value is the partial derivative of the posterior output result of the hypothesis relative to the likelihood of a particular state of the evidence. From a mathematical perspective, for a hypothesis θ given evidence e as a function of a probabilistic likelihood x, the posterior probability is the sensitivity function f(x) of x. The sensitivity function is as follows [49]:
where the coefficients J, K, M, and N originate from the original (unvaried) parameters of the BN.
The absolute value of the first derivative of the sensitivity function at the original-likelihood value can be used to express the sensitivity of the likelihood value, which can be represented by the SV (sensitivity value),
The influence of the root events can also calculate the criticality importance of the roots in a fault-tree framework [29].
where ICR(i|t) is the criticality importance of the ith root event when time t is reached. Pi(t) and Q0(t) are the probabilities when the ith event and the top event occur, respectively. Q0(0i,t) is the probability of the top event when the non-occurrence of the ith root event is known, and Q0(1i,t) is the probability of top event when the occurrence of ith root event is known.
4. Application for Failure Assessment of a Coal Gasifier
This section demonstrates the specific analysis process of the proposed method by taking a coal gasifier as an example. Figure 6 shows the process of the coal-gasification system. Firstly, the coal–water slurry is broken up, atomized, and sprayed into the gasifier under the action of a high-speed oxygen stream passing through the nozzle. The oxygen and the atomized water–coal slurry are subjected to high temperatures in the gasifier and then rapidly undergo a series of complex processes such as preheating, water evaporation, coal dry distillation, volatile pyrolysis combustion, and carbon gasification to produce wet gas with CO, H2, CO2, and water vapor as the main components. Finally, the wet gas, slag, and unreacted carbon leave the reaction zone together and enter the cooling chamber. The molten slag is trapped in the water, falls into the slag tank, and is discharged periodically via the slag-discharge system, whereas the gas and saturated steam go to the next treatment system. In this system the gasifier is the central piece of equipment for the realization of the gasification process.
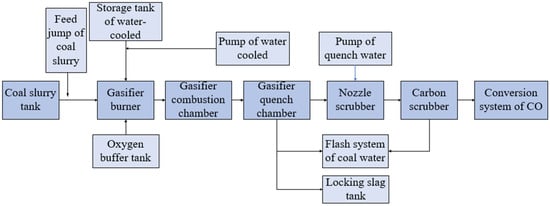
Figure 6.
Flow chart of the coal-gasification system.
4.1. Construction of the BN for Analyzing the Failure Risk of the Gasifier
Based on the experts’ suggestions and relevant literature, the FT of the gasifier was instituted. The failure of the gasifier was set as the top event, and it was primarily leaded by the abnormality of gasifier, equipment-corrosion, and human organization factors. Further analysis was executed due to the above sub-top events till all possible root events were considered. The FT of the gasifier and the corresponding event symbols in the FT are shown in Figure 7 and Table 4. The FT of the gasifier was then converted into the corresponding BN through the method presented in Section 2.5. The CPTs were determined for all the intermediate nodes according to the logic-gate rules and the BN model illustrated in Figure 8.
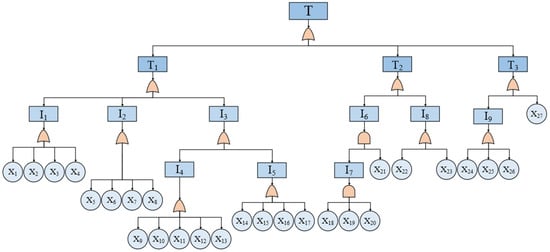
Figure 7.
The fault-tree model of the coal gasifier.

Table 4.
Description of the events in the fault tree of the coal gasifier.
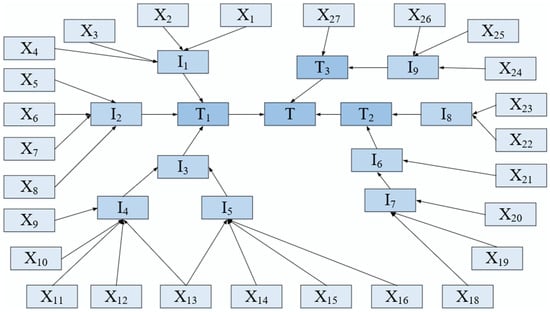
Figure 8.
The Bayesian network for the failure of the gasifier mapped from FT.
4.2. Collection of Experts’ Opinions on the Failure of the Coal Gasifier
4.2.1. Definition of the TpIFN–Probabilistic Linguistic Scales
Based on experts’ opinions and relevant literature, this study classified the failure probability of gasifiers into seven levels. Each level corresponds to a range of values for the failure probability of the gasifier, as Table 5 shows.

Table 5.
Failure-probability rating of the coal gasifier.
In linguistic terms, intuitionistic fuzzy membership functions come in many forms to address the uncertainty and inaccuracy of expert judgments. Triangular and trapezoidal intuitionistic fuzzy membership functions are more efficient for risk analysis. Still, a triangle is a particular case of a trapezoid. Therefore, in this study, the membership and non-membership functions of TpIFNs were used to quantitate the probability of gasifier-failure-accident risk. Seven sets of TpIFNs were determined according to the given probability interval in the gasifier-failure-accident risk. Transformation of linguistic variables into corresponding TpIFNs was carried out by mapping relationship of trapezoidal intuitionistic fuzzy sets. The trapezoidal intuitionistic fuzzy sets produced the qualitive failure probabilities of risk events to quantify, as Table 6 shows. The membership and non-membership function curves of TpIFNs matching with seven linguistic variables are illustrated in Figure 9.

Table 6.
Trapezoidal intuitionistic fuzzy number corresponding to failure possibility.
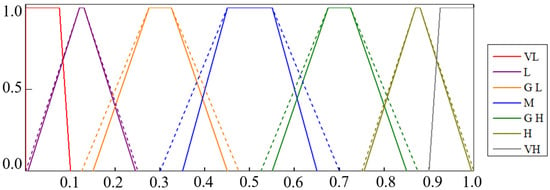
Figure 9.
Membership and non-membership functions of probabilistic-language scales.
4.2.2. Expert’s Opinions on Root Events of the BN
Four experts with different professional backgrounds were selected to establish an expert group. To match up to the failure-probability ratings mentioned in Table 5, a seven-level linguistic-term set (QL, LO, OL, MO, OH, HI, QH) was used to express the experts’ opinions on the occurrence possibility of each root event in the BN. Table 7 shows the experts’ judgments of all root nodes.

Table 7.
Experts’ opinions on root events of the BN for the gasifier failure.
4.3. Aggregation of the TpIFNs for Describing the Failure Probabilities of the Root Nodes
4.3.1. Calculation of the Experts’ Weights
The IF-AHP method mentioned above was used for the computation of the experts’ weights. The personal information of the experts is shown in Table 8.

Table 8.
Basic information of the experts.
The judgment matrix for the three indices of professional position (C1), education level (C2), and service time (C3) is shown in Table 9. The expert group’s intuitionistic-preference relationships for C1–C3 are shown in Table 10, Table 11 and Table 12.

Table 9.
The intuitionistic-preference relationship for the three indices (C1–C3).

Table 10.
The expert group’s intuitionistic-preference relationship for professional position (C1).

Table 11.
The expert group’s intuitionistic-preference relationship for education level (C2).

Table 12.
The expert group’s intuitionistic-preference relationship for service time (C3).
A consistency check of the preference relationships was then performed according to Equations (22) and (23). An example illustrated the consistency-test process of the intuitionistic preference relation R.
Through Equations (20) and (21), the intuitionistic fuzzy consistency judgment matrix was calculated according to R.
Take as an example:
The distance between R and calculated by Equation (19) was , indicating that the consistency check failed. We had to adjust the parameters with Equations (22) and (23) until the consistency test was passed. The fused intuitionistic preference relation was obtained.
where σ = 0.8. According to Equation (24), the distance between and R , and the consistency check was passed. The consistency checks for the intuitionistic-preference relationships Ri (i = 1, 2, 3) were also conducted according to the same process.
Next, the priority of each consistent intuitionistic-preference relationship was derived. For example, the priority vector of the was calculated as ε1 = (0.315, 0.602), ε2 = (0.176, 0.602), and ε3 = (0.265, 0.632) with Equation (25). Subsequently, all prioritization vectors were aggregated. Take W1 as an example:
Table 13 shows the aggregated intuitionistic fuzzy priority of Ci.

Table 13.
The aggregated intuitionistic fuzzy priority of Ci.
Per Equations (28) and (29), . Similarly, S(W2) = 0.478, and S(W3) = 0.486, S(W4) = 0.484. After normalization, the experts’ weights were finally obtained: w = (w1, w2, w3, w4) = (0.257, 0.245, 0.250, 0.248).
4.3.2. Aggregation of the Experts’ Opinions
After obtaining the experts’ weights and the TpIFNs were converted from the experts’ opinions on the occurrence possibilities of the events, the proposed TpIFN-SAM was used to aggregate the opinions. To elaborate the specific process of the TpIFN-SAM, the root node X18 was treated as an example, and the calculation process is shown in Table 14.

Table 14.
Detailed aggregation and FP calculation process of the node X18.
4.4. TpIFN-Defuzzification
4.4.1. Conversion of the TpIFNs into PSs
The aggregated results obtained by the TpIFN-SAM were still TpIFNs, so TpIFN Defuzzification was performed by Equation (36) to further convert the TpIFNs into PSs with crisp values.
4.4.2. Determination of the FPs of All Root Nodes
The PSs of the root nodes were not probability values. In order to implement probabilistic inference with the BN, the PSs were further converted into FPs according to Equations (37) and (38). Table 15 shows all root nodes of the FPs.

Table 15.
The aggregated expert opinions and the corresponding failure probabilities of the root events in the BN.
4.5. BN Analysis
4.5.1. Prediction of the Failure Probability of the Gasifier
Before the BN performs forward prediction, it is necessary to obtain the CPT of each relevant node. Each CPT in this case was obtained by expert evaluation. Table 16 shows the CPT of the intermediate node I1. The rest of the CPTs can be found in Appendix B.

Table 16.
The CPT of event I1 in the BN model (Occ: occurred; Non: non-occurred).
The GeNIe software was used to analyze the established BN model of the coal gasifier. Figure 10 shows the prior probability of the failure of the gasifier through the forward inference of the BN. The failure probability of the gasifier (FPT) was 0.036. To contrast the variations between the FT and the BN, the FPT was also calculated through FT analysis, and the results show that the FPT in the FT was 0.013, which is nearly three times higher than that in the BN. This is because the BN takes into account the conditional dependencies between events and can more objectively report the features of the system.
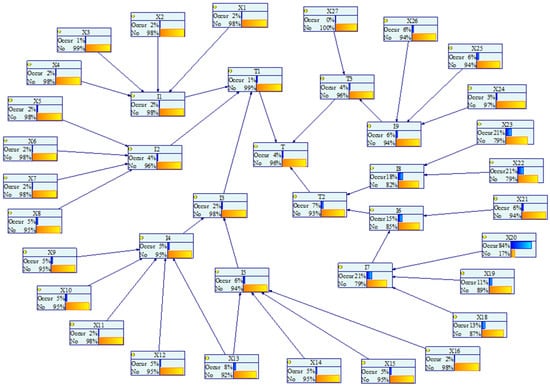
Figure 10.
The prior probability of each node in the BN of the coal gasifier.
4.5.2. Diagnosis of the Key Nodes for the Failure of the Coal Gasifier
The backward inference of the BN was executed to update the occurrence probabilities of the root nodes to assess the extent to which the root nodes affect the failure of the gasifier. Figure 11 shows the posterior probability of each root node P (Xi = Occur | T = Occur) obtained by backward inference of the BN. In the case that the leaf node must occur, the posterior probability of the root nodes X20 (High H2O content), X22 (Anti-corrosion layer damaged), and X23 (Insulation layer damaged) are the most worrying ones. Therefore, the key nodes can be preliminarily determined.
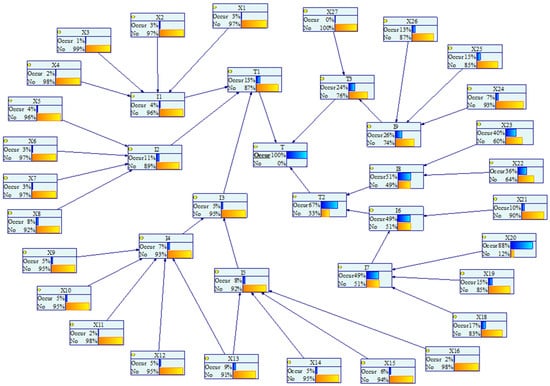
Figure 11.
The posterior probability of each node in the BN of the coal gasifier.
By comparing the prior and the posterior probability regarding each root node, as shown in Figure 12, the root nodes with large changes in occurrence probability can be obtained as X22 (Anti-corrosion layer damaged), X23 (Insulation layer damaged) and X25 (Improper operation), indicating that these three root events have a large contribution to the failure probability of the gasifier. The acquisition of the prior and the posterior probability shows the forward-inference (prediction) ability and backward-inference (diagnosis) ability of the BN, respectively, which completely reflects the superiority of the BN’s bidirectional-inference ability. Meanwhile, this ability can be used to provide preliminary judgments and lay the foundation for subsequent analysis and determination of key nodes.
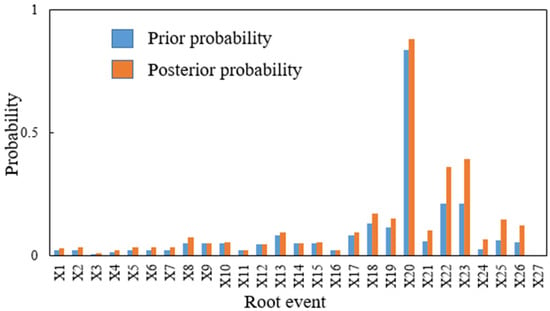
Figure 12.
Prior and posterior probabilities of root nodes of the BN model.
4.5.3. SA and CIA
The RoV of each root node was calculated with Equation (39). Figure 13 displays the calculation results of the importance of all basic events. The top six key root nodes were X25 (Improper operation), X24 (Pre-job training is not up to standard), X26 (Unattended/unsafe supervision), X27 (Deliberately damaged), X23 (Insulation layer damaged), and X21 (High flow rate).
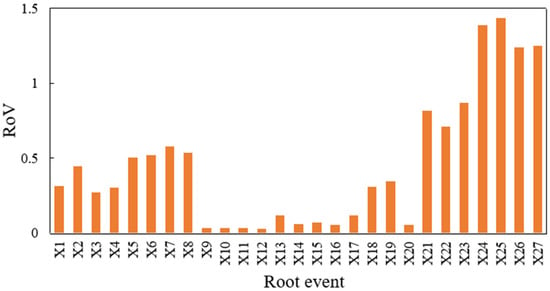
Figure 13.
RoV of the root node probability using the BN model for the coal gasifier.
For the purpose of further elucidating the devotion of all root nodes to the occurrence of accidents and identify the critical factors, SA and CIA were performed. Figure 14 shows the sensitivity value and the critical importance of each root node. For the BN, X25 (Improper operation), X24 (Pre-job training is not up to standard), X26 (Unattended/unsafe supervision), X27 (Deliberately damaged), X23 (Insulation layer damaged), and X22 (Anti-corrosion layer damaged) were the top six key events for the gasifier failure. For the FT, the top six key factors included X22 (Anti-corrosion layer damaged), X23 (Insulation layer damaged), X13, X17 (Temperature sensor damaged), X25 (Improper operation), and X21 (High flow rate). The results obtained by the two methods are discrepant. The reason for this is that the BN still considered conditional dependencies between events, whereas the FT did not capture them.
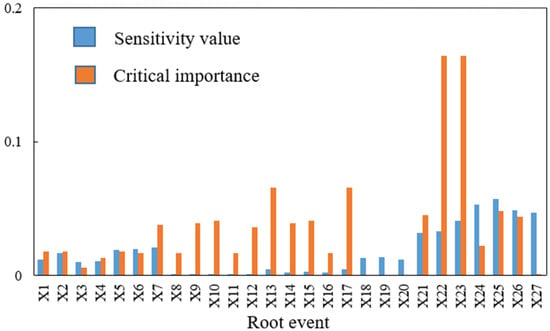
Figure 14.
Comparison of sensitivity value and critical importance of the root nodes of the BN model for the coal gasifier.
From the results of the SA and CIA, it can be found that X25 (Improper operation) was considered the most critical factor on the failure of the coal gasifier. In addition, damage to anti-corrosion measures (X22 and X23) was also a very important influencing factor. Therefore, more attention should be allocated to the management and training of operators, and special attention should be paid to regular inspection of the integrity of insulation and anti-corrosion layers to minimize the failure of the gasifier.
5. Conclusions
In this study, a new integration framework was proposed to assess the failure risk of the process system. The improvements of this method compared with the previous method are as follows:
- This framework combined the Bayesian network with the TpIFN-SAM to provide an alternative strategy for obtaining the prior probabilities of the root events in BNs.
- A set of TpIFNs was defined to quantify the linguistic terms for describing the failure possibilities of the events in BNs, which are more general and expressive than TpIFNs.
- The TpIFN-SAM can effectively aggregate the expert opinions on the prior probabilities of the root events in BNs and reduce the uncertain cumulative effect of the aggregation process by taking the effect of individual discrepancies into account for the consistency. The bidirectional reasoning of the BN coupled with sensitivity analysis can accurately calculate the system-failure probability and identify the key influencing factors that may lead to accidents.
Limitations also exist in this work. The basic probabilities of the root events in the BN were assumed to be constant in the proposed framework, but in many cases they are time dependent. Therefore, developing a BN approach for dynamic systems will be covered in future research work.
Author Contributions
Data curation, Q.L.; Software, Q.L.; Formal analysis, D.L.; Investigation, Y.Y.; Methodology, Y.L. and S.W.; Resources, Y.D. and W.W.; Writing-original draft, Y.L.; Writing-review and editing, Y.L. and W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Natural Science Foundation of China (No. 51605368) and Scientific Research Project of Shaanxi Provincial Department of Education (No. 20JK0944).
Data Availability Statement
Not applicable.
Acknowledgments
We appreciate the National Nature Science Foundation of China and the Northwest University.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
If satisfies the following five fundamental theorems, then prove that is workable.
If b1 = a1, b4 = a4, then
If a2 − a1 = a4 − a3, a2 − b1 = b4 − a3, then
EV(λ) = λ
Proof
- When k = 0, empty.
- When k > 0, let be a trapezoidal intuitionistic fuzzy number, and k is a real number, which we can know by Definition 2:The expected value of is
- When k < 0, same result as B. □
Proof:
Let be two trapezoidal intuitionistic fuzzy numbers, which can be known by Definition 5:
The expected value of is
□
Proof:
Let be a set of trapezoidal intuitionistic fuzzy numbers; if b1 = a1 and b4 = a4, then
□
Proof:
By , if (a2 − a1 = a4 − a3) → (a2 + a3 = a1 + a4) and (a2 − b1 = b4 − a3) → (a2 + a3 = b1 + b4),
□
Proof:
Let λ be a real number, then λ = (λ, λ, λ, λ; λ, λ, λ, λ), and
Specially, if λ = 0, then EV(λ) = EV(0) = 0. □
The above five theorems are proven, so is workable.
Appendix B

Table A1.
The CPT of event I2 (Abnormal liquid level; Occ: occurred; Non: non-occurred).
Table A1.
The CPT of event I2 (Abnormal liquid level; Occ: occurred; Non: non-occurred).
| X5 | X6 | X7 | X8 | I2 | |
|---|---|---|---|---|---|
| Occ | Non | ||||
| Occ | Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Occ | Non | 0.83 | 0.17 |
| Occ | Occ | Non | Occ | 0.86 | 0.14 |
| Occ | Non | Occ | Occ | 0.81 | 0.19 |
| Occ | Non | Occ | Non | 0.73 | 0.27 |
| Occ | Non | Non | Occ | 0.71 | 0.29 |
| Occ | Occ | Non | Non | 0.68 | 0.32 |
| Occ | Non | Non | Non | 0.35 | 0.65 |
| Non | Occ | Occ | Occ | 0.76 | 0.24 |
| Non | Occ | Occ | Non | 0.69 | 0.31 |
| Non | Occ | Non | Occ | 0.70 | 0.30 |
| Non | Occ | Non | Non | 0.36 | 0.64 |
| Non | Non | Occ | Occ | 0.69 | 0.31 |
| Non | Non | Occ | Non | 0.40 | 0.60 |
| Non | Non | Non | Occ | 0.38 | 0.62 |
| Non | Non | Non | Non | 0.00 | 1.00 |

Table A2.
The CPT of event I3 (Abnormal temperature; Occ: occurred; Non: non-occurred).
Table A2.
The CPT of event I3 (Abnormal temperature; Occ: occurred; Non: non-occurred).
| E4 | E5 | I3 | |
|---|---|---|---|
| Occ | Non | ||
| Occ | Occ | 1.00 | 0.00 |
| Occ | Non | 0.13 | 0.87 |
| Non | Occ | 0.17 | 0.83 |
| Non | Non | 0.00 | 1.00 |

Table A3.
The CPT of event I4 (Too-high temperature; Occ: occurred; Non: non-occurred).
Table A3.
The CPT of event I4 (Too-high temperature; Occ: occurred; Non: non-occurred).
| X9 | X10 | X11 | X12 | X13 | I4 | |
|---|---|---|---|---|---|---|
| Occ | Non | |||||
| Occ | Occ | Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Occ | Occ | Non | 0.75 | 0.25 |
| Occ | Occ | Occ | Non | Occ | 0.66 | 0.34 |
| Occ | Occ | Non | Occ | Occ | 0.60 | 0.40 |
| Occ | Non | Occ | Occ | Occ | 0.47 | 0.53 |
| Non | Occ | Occ | Occ | Occ | 0.45 | 0.55 |
| Occ | Occ | Occ | Non | Non | 0.53 | 0.47 |
| Occ | Occ | Non | Occ | Non | 0.49 | 0.51 |
| Occ | Non | Occ | Occ | Non | 0.43 | 0.57 |
| Non | Occ | Occ | Occ | Non | 0.39 | 0.61 |
| Occ | Occ | Non | Non | Occ | 0.51 | 0.49 |
| Occ | Non | Occ | Non | Occ | 0.43 | 0.57 |
| Non | Occ | Occ | Non | Occ | 0.40 | 0.60 |
| Occ | Non | Non | Occ | Occ | 0.38 | 0.62 |
| Non | Occ | Non | Occ | Occ | 0.34 | 0.66 |
| Non | Non | Occ | Occ | Occ | 0.30 | 0.70 |
| Oc | Occ | Non | Non | Non | 0.49 | 0.51 |
| Occ | Non | Occ | Non | Non | 0.42 | 0.58 |
| Non | Occ | Occ | Non | Non | 0.38 | 0.62 |
| Occ | Non | Non | Occ | Non | 0.37 | 0.63 |
| Non | Occ | Non | Occ | Non | 0.34 | 0.66 |
| Non | Non | Occ | Occ | Non | 0.29 | 0.71 |
| Occ | Non | Non | Non | Occ | 0.35 | 0.65 |
| Non | Occ | Non | Non | Occ | 0.33 | 0.67 |
| Non | Non | Occ | Non | Occ | 0.27 | 0.73 |
| Non | Non | Non | Occ | Occ | 0.25 | 0.75 |
| Occ | Non | Non | Non | Non | 0.19 | 0.81 |
| Non | Occ | Non | Non | Non | 0.21 | 0.79 |
| Non | Non | Occ | Non | Non | 0.24 | 0.76 |
| Non | Non | Non | Occ | Non | 0.20 | 0.80 |
| Non | Non | Non | Non | Occ | 0.25 | 0.75 |
| Non | Non | Non | Non | Non | 0.00 | 1.00 |

Table A4.
The CPT of event I5 (Too-low temperature; Occ: occurred; Non: non-occurred).
Table A4.
The CPT of event I5 (Too-low temperature; Occ: occurred; Non: non-occurred).
| X14 | X15 | X16 | X17 | I5 | |
|---|---|---|---|---|---|
| Occ | Non | ||||
| Occ | Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Occ | Non | 0.89 | 0.11 |
| Occ | Occ | Non | Occ | 0.83 | 0.17 |
| Occ | Non | Occ | Occ | 0.85 | 0.15 |
| Occ | Non | Occ | Non | 0.79 | 0.21 |
| Occ | Non | Non | Occ | 0.76 | 0.24 |
| Occ | Occ | Non | Non | 0.68 | 0.32 |
| Occ | Non | Non | Non | 0.32 | 0.68 |
| Non | Occ | Occ | Occ | 0.86 | 0.14 |
| Non | Occ | Occ | Non | 0.71 | 0.29 |
| Non | Occ | Non | Occ | 0.69 | 0.31 |
| Non | Occ | Non | Non | 0.37 | 0.63 |
| Non | Non | Occ | Occ | 0.42 | 0.58 |
| Non | Non | Occ | Non | 0.28 | 0.72 |
| Non | Non | Non | Occ | 0.26 | 0.74 |
| Non | Non | Non | Non | 0.00 | 1.00 |

Table A5.
The CPT of event I6 (Internal corrosion; Occ: occurred; Non: non-occurred).
Table A5.
The CPT of event I6 (Internal corrosion; Occ: occurred; Non: non-occurred).
| E7 | X21 | I6 | |
|---|---|---|---|
| Occ | Non | ||
| Occ | Occ | 1.00 | 0.00 |
| Occ | Non | 0.65 | 0.35 |
| Non | Occ | 0.33 | 0.67 |
| Non | Non | 0.00 | 1.00 |

Table A6.
The CPT of event I7 (Medium content; Occ: occurred; Non: non-occurred).
Table A6.
The CPT of event I7 (Medium content; Occ: occurred; Non: non-occurred).
| X18 | X19 | X20 | I7 | |
|---|---|---|---|---|
| Occ | Non | |||
| Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Non | 0.35 | 0.65 |
| Occ | Non | Occ | 0.36 | 0.64 |
| Occ | Non | Non | 0.15 | 0.85 |
| Non | Occ | Occ | 0.37 | 0.63 |
| Non | Occ | Non | 0.17 | 0.83 |
| Non | Non | Occ | 0.19 | 0.81 |
| Non | Non | Non | 0.00 | 1.00 |

Table A7.
The CPT of event I8 (External corrosion; Occ: occurred; Non: non-occurred).
Table A7.
The CPT of event I8 (External corrosion; Occ: occurred; Non: non-occurred).
| X22 | X23 | I8 | |
|---|---|---|---|
| Occ | Non | ||
| Occ | Occ | 1.00 | 0.00 |
| Occ | Non | 0.45 | 0.55 |
| Non | Occ | 0.36 | 0.64 |
| Non | Non | 0.00 | 1.00 |

Table A8.
The CPT of event I2 (Unintentional destruction; Occ: occurred; Non: non-occurred).
Table A8.
The CPT of event I2 (Unintentional destruction; Occ: occurred; Non: non-occurred).
| X24 | X25 | X26 | I9 | |
|---|---|---|---|---|
| Occ | Non | |||
| Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Non | 0.67 | 0.33 |
| Occ | Non | Occ | 0.71 | 0.29 |
| Occ | Non | Non | 0.35 | 0.65 |
| Non | Oc | Occ | 0.69 | 0.31 |
| Non | Occ | Non | 0.41 | 0.59 |
| Non | Non | Occ | 0.38 | 0.62 |
| Non | Non | Non | 0.00 | 1.00 |

Table A9.
The CPT of event T1 (Gasifier abnormality; Occ: occurred; Non: non-occurred).
Table A9.
The CPT of event T1 (Gasifier abnormality; Occ: occurred; Non: non-occurred).
| E1 | E2 | E3 | T1 | |
|---|---|---|---|---|
| Occ | Non | |||
| Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Non | 0.22 | 0.78 |
| Occ | Non | Occ | 0.33 | 0.67 |
| Occ | Non | Non | 0.18 | 0.82 |
| Non | Occ | Occ | 0.32 | 0.68 |
| Non | Occ | Non | 0.19 | 0.81 |
| Non | Non | Occ | 0.13 | 0.87 |
| Non | Non | Non | 0.00 | 1.00 |

Table A10.
The CPT of event T2 (Corrosion failure; Occ: occurred; Non: non-occurred).
Table A10.
The CPT of event T2 (Corrosion failure; Occ: occurred; Non: non-occurred).
| E6 | E8 | T2 | |
|---|---|---|---|
| Occ | Non | ||
| Occ | Occ | 1.00 | 0.00 |
| Occ | Non | 0.17 | 0.83 |
| Non | Occ | 0.15 | 0.85 |
| Non | Non | 0.00 | 1.00 |

Table A11.
The CPT of event T3 (Human-organization factors; Occ: occurred; Non: non-occurred).
Table A11.
The CPT of event T3 (Human-organization factors; Occ: occurred; Non: non-occurred).
| E9 | X27 | T3 | |
|---|---|---|---|
| Occ | Non | ||
| Occ | Occ | 1.00 | 0.00 |
| Occ | Non | 0.66 | 0.34 |
| Non | Occ | 0.21 | 0.79 |
| Non | Non | 0.00 | 1.00 |

Table A12.
The CPT of event T (Gasifier failure; Occ: occurred; Non: non-occurred).
Table A12.
The CPT of event T (Gasifier failure; Occ: occurred; Non: non-occurred).
| T1 | T2 | T3 | T | |
|---|---|---|---|---|
| Occ | N | |||
| Occ | Occ | Occ | 1.00 | 0.00 |
| Occ | Occ | Non | 0.28 | 0.72 |
| Occ | Non | Occ | 0.37 | 0.63 |
| Occ | Non | Non | 0.33 | 0.67 |
| Non | Occ | Occ | 0.38 | 0.62 |
| Non | Occ | Non | 0.34 | 0.66 |
| Non | Non | Occ | 0.23 | 0.77 |
| Non | Non | Non | 0.00 | 1.00 |
References
- Cao, C.; Zhang, Y.; Yu, T.; Gu, X.; Xin, Z.; Li, J. A Novel 3-Layer Mixed Cultural Evolutionary Optimization Framework for Optimal Operation of Syngas Production in a Texaco Coal-Water Slurry Gasifier. Chin. J. Chem. Eng. 2015, 23, 1484–1501. [Google Scholar] [CrossRef]
- Ashraf, A.M.; Imran, W.; Véchot, L. Analysis of the Impact of a Pandemic on the Control of the Process Safety Risk in Major Hazards Industries Using a Fault Tree Analysis Approach. J. Loss Prev. Process Ind. 2022, 74, 104649. [Google Scholar] [CrossRef] [PubMed]
- Hong, E.-S.; Lee, I.-M.; Shin, H.-S.; Nam, S.-W.; Kong, J.-S. Quantitative Risk Evaluation Based on Event Tree Analysis Technique: Application to the Design of Shield TBM. Tunn. Undergr. Space Technol. 2009, 24, 269–277. [Google Scholar] [CrossRef]
- Wang, W.; Mou, D.; Li, F.; Dong, C.; Khan, F. Dynamic Failure Probability Analysis of Urban Gas Pipeline Network. J. Loss Prev. Process Ind. 2021, 72, 104552. [Google Scholar] [CrossRef]
- George, P.G.; Renjith, V.R. Evolution of Safety and Security Risk Assessment Methodologies towards the Use of Bayesian Networks in Process Industries. Process Saf. Environ. Prot. 2021, 149, 758–775. [Google Scholar] [CrossRef]
- Khakzad, N.; Khan, F.; Amyotte, P. Safety Analysis in Process Facilities: Comparison of Fault Tree and Bayesian Network Approaches. Reliab. Eng. Syst. Saf. 2011, 96, 925–932. [Google Scholar] [CrossRef]
- Bhandari, J.; Abbassi, R.; Garaniya, V.; Khan, F. Risk Analysis of Deepwater Drilling Operations Using Bayesian Network. J. Loss Prev. Process Ind. 2015, 38, 11–23. [Google Scholar] [CrossRef]
- Yazdi, M.; Khan, F.; Abbassi, R.; Quddus, N. Resilience Assessment of a Subsea Pipeline Using Dynamic Bayesian Network. J. Pipeline Sci. Eng. 2022, 2, 100053. [Google Scholar] [CrossRef]
- Eleye-Datubo, A.G.; Wall, A.; Wang, J. Marine and Offshore Safety Assessment by Incorporative Risk Modeling in a Fuzzy-Bayesian Network of an Induced Mass Assignment Paradigm. Risk Anal. 2008, 28, 95–112. [Google Scholar] [CrossRef]
- Xu, B.; Hu, J.; Hu, T.; Wang, F.; Luo, K.; Wang, Q.; He, X. Quantitative Assessment of Seismic Risk in Hydraulic Fracturing Areas Based on Rough Set and Bayesian Network: A Case Analysis of Changning Shale Gas Development Block in Yibin City, Sichuan Province, China. J. Pet. Sci. Eng. 2021, 200, 108226. [Google Scholar] [CrossRef]
- Yazdi, M.; Kabir, S. Fuzzy Evidence Theory and Bayesian Networks for Process Systems Risk Analysis. Hum. Ecol. Risk Assess. Int. J. 2020, 26, 57–86. [Google Scholar] [CrossRef]
- Gao, P.; Li, W.; Sun, Y.; Liu, S. Risk Assessment for Gas Transmission Station Based on Cloud Model Based Multilevel Bayesian Network from the Perspective of Multi-Flow Intersecting Theory. Process Saf. Environ. Prot. 2022, 159, 887–898. [Google Scholar] [CrossRef]
- Zhu, M.; Chen, D.; Wang, J.; Wang, J.; Sun, Y. Analysis of Oceanaut Operating Performance Using an Integrated Bayesian Network Aided by the Fuzzy Logic Theory. Int. J. Ind. Ergon. 2021, 83, 103129. [Google Scholar] [CrossRef]
- Zarei, E.; Khakzad, N.; Cozzani, V.; Reniers, G. Safety Analysis of Process Systems Using Fuzzy Bayesian Network (FBN). J. Loss Prev. Process Ind. 2019, 57, 7–16. [Google Scholar] [CrossRef]
- Kabir, G.; Sadiq, R.; Tesfamariam, S. A Fuzzy Bayesian Belief Network for Safety Assessment of Oil and Gas Pipelines. Struct. Infrastruct. Eng. 2016, 12, 874–889. [Google Scholar] [CrossRef]
- Yazdi, M.; Kabir, S. A Fuzzy Bayesian Network Approach for Risk Analysis in Process Industries. Process Saf. Environ. Prot. 2017, 111, 507–519. [Google Scholar] [CrossRef]
- Zhao, D.; Wang, Z.; Song, Z.; Guo, P.; Cao, X. Assessment of Domino Effects in the Coal Gasification Process Using Fuzzy Analytic Hierarchy Process and Bayesian Network. Saf. Sci. 2020, 130, 104888. [Google Scholar] [CrossRef]
- Yan, F.; Xu, K.; Yao, X.; Li, Y. Fuzzy Bayesian Network-Bow-Tie Analysis of Gas Leakage during Biomass Gasification. PLoS ONE 2016, 11, e0160045. [Google Scholar] [CrossRef]
- Pouyakian, M.; Jafari, M.J.; Laal, F.; Nourai, F.; Zarei, E. A Comprehensive Approach to Analyze the Risk of Floating Roof Storage Tanks. Process Saf. Environ. Prot. 2021, 146, 811–836. [Google Scholar] [CrossRef]
- Rostamabadi, A.; Jahangiri, M.; Zarei, E.; Kamalinia, M.; Alimohammadlou, M. A Novel Fuzzy Bayesian Network Approach for Safety Analysis of Process Systems; An Application of HFACS and SHIPP Methodology. J. Clean. Prod. 2020, 244, 118761. [Google Scholar] [CrossRef]
- Uluçay, V.; Deli, I.; Şahin, M. Trapezoidal Fuzzy Multi-Number and Its Application to Multi-Criteria Decision-Making Problems. Neural Comput. Appl. 2018, 30, 1469–1478. [Google Scholar] [CrossRef]
- Uluay, V. A New Similarity Function of Trapezoidal Fuzzy Multi-Numbers Based on Multi-Criteria Decision Making. J. Inst. Sci. Tech. 2020, 2020, 1233–1246. [Google Scholar] [CrossRef]
- Atanassov, K.T. Intuitionistic fuzzy sets. J. Fuzzy Sets Syst. 1986, 20, 87–96. [Google Scholar] [CrossRef]
- Yu, J.; Wu, S.; Yu, Y.; Chen, H.; Fan, H.; Liu, J.; Ge, S. Process System Failure Evaluation Method Based on a Noisy-OR Gate Intuitionistic Fuzzy Bayesian Network in an Uncertain Environment. Process Saf. Environ. Prot. 2021, 150, 281–297. [Google Scholar] [CrossRef]
- Kumar, M.; Kaushik, M. System Failure Probability Evaluation Using Fault Tree Analysis and Expert Opinions in Intuitionistic Fuzzy Environment. J. Loss Prev. Process Ind. 2020, 67, 104236. [Google Scholar] [CrossRef]
- Hsu, H.-M.; Chen, C.-T. Aggregation of Fuzzy Opinions under Group Decision Making. Fuzzy Sets Syst. 1996, 79, 279–285. [Google Scholar] [CrossRef]
- Kim, H.; Koh, J.-S.; Kim, Y.; Theofanous, T.G. Risk Assessment of Membrane Type LNG Storage Tanks in Korea-Based on Fault Tree Analysis. Korean J. Chem. Eng. 2005, 22, 1–8. [Google Scholar] [CrossRef]
- Yazdi, M. Hybrid Probabilistic Risk Assessment Using Fuzzy FTA and Fuzzy AHP in a Process Industry. J. Fail. Anal. Prev. 2017, 17, 756–764. [Google Scholar] [CrossRef]
- Yin, H.; Liu, C.; Wu, W.; Song, K.; Liu, D.; Dan, Y. Safety Assessment of Natural Gas Storage Tank Using Similarity Aggregation Method Based Fuzzy Fault Tree Analysis (SAM-FFTA) Approach. J. Loss Prev. Process Ind. 2020, 66, 104159. [Google Scholar] [CrossRef]
- Yin, H.; Liu, C.; Wu, W.; Song, K.; Dan, Y.; Cheng, G. An Integrated Framework for Criticality Evaluation of Oil & Gas Pipelines Based on Fuzzy Logic Inference and Machine Learning. J. Nat. Gas Sci. Eng. 2021, 96, 104264. [Google Scholar] [CrossRef]
- Kabir, S.; Papadopoulos, Y. A Review of Applications of Fuzzy Sets to Safety and Reliability Engineering. Int. J. Approx. Reason. 2018, 100, 29–55. [Google Scholar] [CrossRef]
- Uluçay, V.; Deli, I.; Şahin, M. Intuitionistic Trapezoidal Fuzzy Multi-Numbers and Its Application to Multi-Criteria Decision-Making Problems. Complex Intell. Syst. 2019, 5, 65–78. [Google Scholar] [CrossRef]
- Li, X.; Chen, X. Multi-Criteria Group Decision Making Based on Trapezoidal Intuitionistic Fuzzy Information. Appl. Soft Comput. 2015, 30, 454–461. [Google Scholar] [CrossRef]
- Wang, J.; Zhong, Z. Aggregation operators on intuitionistic trapezoidal fuzzy number and its application to multi-criteria decision making problems. J. Syst. Eng. Elect. 2009, 20, 321–326. [Google Scholar] [CrossRef]
- Heilpern, S. The expected value of a fuzzy number. J. Fuzzy Sets Syst. 1992, 47, 81–86. [Google Scholar] [CrossRef]
- Bharati, S.K.; Malhotra, R. Two Stage Intuitionistic Fuzzy Time Minimizing Transportation Problem Based on Generalized Zadeh’s Extension Principle. Int. J. Syst. Assur. Eng. Manag. 2017, 8, 1442–1449. [Google Scholar] [CrossRef]
- Kabir, S.; Papadopoulos, Y. Applications of Bayesian Networks and Petri Nets in Safety, Reliability, and Risk Assessments: A Review. Saf. Sci. 2019, 115, 154–175. [Google Scholar] [CrossRef]
- Bulmer, R.H.; Stephenson, F.; Lohrer, A.M.; Lundquist, C.J.; Madarasz-Smith, A.; Pilditch, C.A.; Thrush, S.F.; Hewitt, J.E. Informing the Management of Multiple Stressors on Estuarine Ecosystems Using an Expert-Based Bayesian Network Model. J. Environ. Manag. 2022, 301, 113576. [Google Scholar] [CrossRef]
- Zhou, Y.; Li, C.; Zhou, C.; Luo, H. Using Bayesian Network for Safety Risk Analysis of Diaphragm Wall Deflection Based on Field Data. Reliab. Eng. Syst. Saf. 2018, 180, 152–167. [Google Scholar] [CrossRef]
- Bobbio, A.; Portinale, L.; Minichino, M.; Ciancamerla, E. Improving the Analysis of Dependable Systems by Mapping Fault Trees into Bayesian Networks. Reliab. Eng. Syst. Saf. 2001, 71, 249–260. [Google Scholar] [CrossRef]
- Zhang, C.; Wu, J.; Hu, X.; Ni, S. A Probabilistic Analysis Model of Oil Pipeline Accidents Based on an Integrated Event-Evolution-Bayesian (EEB) Model. Process Saf. Environ. Prot. 2018, 117, 694–703. [Google Scholar] [CrossRef]
- Dimaio, F.; Scapinello, O.; Zio, E.; Ciarapica, C.; Cincotta, S.; Crivellari, A.; Decarli, L.; Larosa, L. Accounting for Safety Barriers Degradation in the Risk Assessment of Oil and Gas Systems by Multistate Bayesian Networks. Reliab. Eng. Syst. Saf. 2021, 216, 107943. [Google Scholar] [CrossRef]
- Nicolis, J.S.; Tsuda, I. Chaotic dynamics of information processing: The “magic number seven plus-minus two” revisited. J. Bull. Math. Biol. 1985, 47, 343–365. [Google Scholar] [CrossRef]
- Ishikawa, A.; Amagasa, M.; Shiga, T.; Tomizawa, G.; Tatsuta, R.; Mieno, H. The Max-Min Delphi Method and Fuzzy Delphi Method via Fuzzy Integration. Fuzzy Sets Syst. 1993, 55, 241–253. [Google Scholar] [CrossRef]
- Saaty, T.L.; Vargas, L.G. Estimating Technological Coefficients by the Analytic Hierarchy Process. Socioecon. Plann. Sci. 1979, 13, 333–336. [Google Scholar] [CrossRef]
- Xu, Z.; Liao, H. Intuitionistic Fuzzy Analytic Hierarchy Process. IEEE Trans. Fuzzy Syst. 2014, 22, 749–761. [Google Scholar] [CrossRef]
- Onisawa, T. A Representation of Human Reliability Using Fuzzy Concepts. Inf. Sci. 1988, 45, 153–173. [Google Scholar] [CrossRef]
- Yu, J.; Chen, H.; Yu, Y.; Yang, Z. A Weakest T-Norm Based Fuzzy Fault Tree Approach for Leakage Risk Assessment of Submarine Pipeline. J. Loss Prev. Process Ind. 2019, 62, 103–968. [Google Scholar] [CrossRef]
- Kwan, M.; Overill, R.; Chow, K.-P.; Tse, H.; Law, F.; Lai, P. Sensitivity Analysis of Bayesian Networks Used in Forensic Investigations. In Advances in Digital Forensics VII; IFIP Advances in Information and Communication Technology; Peterson, G., Shenoi, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 361, pp. 231–243. ISBN 978-3-642-24211-3. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).