Abstract
Networked nonlinear systems (NNSs) have great potential security threats because of malicious attacks. These attacks will destabilize the networked systems and disrupt the communication to the networked systems, which will affect the stability and performance of the networked control systems. Therefore, this paper aims to deal with the resilient control problem for NNSs with dynamically triggering mechanisms (DTMs) and malicious aperiodic denial-of-service (DoS) attacks. To mitigate the impact from DoS attacks and economize communication resources, a resilient dynamically triggering controller (RDTC) is designed with DTMs evolving an adaptive adjustment auxiliary variable. Thus, the resulting closed-loop system is exponentially stable by employing the piecewise Lyapunov function technique. In addition, according to the minimum inter-event time, the Zeno behavior can be excluded. Finally, the merits of the proposed controllers and theory are corroborated using the well-known nonlinear Chua circuit.
1. Introduction
Recently, due to the irreplaceable position of communication in the network, many scholars have devoted their attention to the study of networked control systems. More specifically, they are focusing on the data transmission of networked control systems because of the advantages of the information interaction based on the interconnection of the different systems. Naturally, communication-based issues of control and optimization are emerging and developing rapidly [1,2,3]. Although the advantages of communication technology have brought seismic shocks to academia and industry, there exists a problem. The limitations of the periodic sampling technique subject to guaranteeing desired system performance by reducing the sampling period create a large amount of redundant sampled data, resulting in network congestion and executing control tasks periodically after the system is stabilized, which results in wasting network bandwidth and computation resources. To tackle these limitations, an event-triggering technique has emerged at this historical moment and developed rapidly based on supervising the controller’s update [4,5]. Herein, it is worth noting that the event triggering techniques not only ensure the desired performance from control tasks but also decrease the update frequency of the controller, resulting in energy saving in system communication. In the past decades, different types of the event triggering techniques have been proposed, such as the static event-triggering technique [6,7,8], dynamic event-triggering technique [9,10,11], stochastic event-triggering technique [12,13,14], and switched event-triggering technique [15,16].
In addition, unreliable communication channels cause much concern in the discussion of the stability and performance maintenance for networked control systems. In this regard, there exist some innovative works [17,18,19]. In particular, security-based networked control systems resisting malicious attacks have been given attention in the past years [20,21]. Herein, it is worth noting that on the premise of ensuring system stability and desired performance, the so-called security is the elasticity of resisting malicious cyber attacks. Although there exist a few innovative and groundbreaking results for networked control systems with co-design of the event triggering techniques and DoS attacks [22,23,24], the co-design with dynamically triggering techniques and DoS attacks for NNSs is still a challenging problem.
Up to now, although many innovative and groundbreaking results have sprung up for the control and optimization in the framework of co-design of dynamically triggering techniques and DoS attacks [25,26,27], they primarily focus on linear systems. Moreover, some research results of nonlinear systems with DTMs and DoS attacks appear sporadically [28,29,30,31], the existing DTMs have shown certain limitations in theorem research and industrial practice. Inspired by the aforementioned discussion, this paper deals with the resilient control problem for NNSs with DTMs and DoS attacks. More specifically, a DTRC is designed with DTMs with an adaptive adjustment auxiliary variable, which can result in the closed-loop system being exponentially stable by employing the piecewise Lyapunov function technique. Meanwhile, a minimal inter-event time is obtained to ensure it is Zeno-free under aperiodic DoS attacks. In addition, the innovations of this paper are as follows:
- Different from the static trigger strategy in [22,23,24], a novel dynamically triggering strategy is proposed for NNSs with aperiodic DoS attacks. Because of the longer trigger intervals compared with the static trigger intervals, this strategy further reduces the sampling data transmission rate and improves the usage of network resources.
- Compared with the trigger strategy in [23], the dynamically triggering resilient control strategy is introduced into nonlinear systems to obtund the influence of aperiodic DoS attacks. In addition, the sampled data cannot be transmitted even if condition (7) is satisfied since aperiodic DoS attacks will result in the loss of control input during the DoS attacks range.
- Compared with [23], a new piecewise Lyapunov function is designed to ensure the exponential stability of the networked control system under DoS attacks. In particular, the minimum inter-event time excludes Zeno behavior in the resilient controller. Moreover, the proposed method not only releases Assumption 4 in [23] but also reduces the conservative of the system.
The structure of this article is as follows. First, NNSs and problem statements are presented in Section 2. Then, the conditions for the stability of NNSs under DoS attacks are driven in Section 3. Furthermore, the satisfactory and better performance of the RDET controller designed than the existing ones is provided in Section 4. Finally, the conclusion is shown in Section 5.
Notations: and represent the set of the positive real numbers and the set of the positive integer numbers, respectively. and indicate the space of real n-vectors and matrices. is the inverse of x (function or matrix). means the 2-norm.
2. Problem Formulation
Figure 1 shows wireless NNSs under aperiodic DoS attacks. First, aperiodic DoS attack scenarios are typically depicted by the sleeping intervals and DoS attack intervals in Figure 2. Then, the dynamically triggering resilient control strategy and switching controller are designed for NNSs, respectively. Next, based on these descriptions, we give out the problem statement.
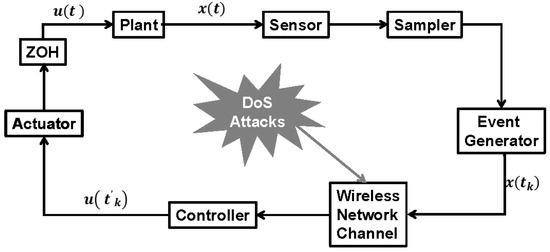
Figure 1.
Schematic representation of dynamic event-triggered control for nonlinear systems under DoS attacks.
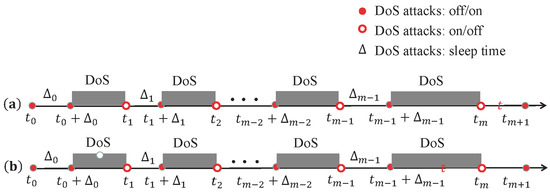
Figure 2.
Situation of aperiodic DoS attacks. (a) presents the current instant in the sleeping interval, and (b) presents the current instant in the DoS attack interval.
2.1. Networked Nonlinear Systems
Consider the following class of NNSs
where is the system state; represents the control input; denotes the initial condition; the Lipschitz continuous function satisfies for all .
For the sake of later analysis, we provide the following definitions and assumptions.
Definition 1
([32]).
- 1.
- A function is called a class of if it is continuous, strictly increasing and . If and also as , then it is said to be of class .
- 2.
- A function is called a class of if the function for all fixed and the function is decreasing and as for all fixed .
Definition 2
([32]). System (1) is said to be globally weakly exponentially stable (GWES) if there exist functions and constants such that for any initial value , the solution satisfies . In particular, when , it is said to be globally exponentially stable (GES).
Definition 3
([32]). A function is an ISS-Lyapunov function if there exist some functions , and γ that satisfy
where .
Definition 4
([32]). Given a local Lipschitz function , the upper left-hand Dini derivative of V along system (1) is defined by
2.2. Aperiodic DoS Attacks
In this section, for the convenience of analysis and design, we assume that the DoS attacks only occur on the measurement channel and that no packet loss or no delay occurs during the sleeping intervals. As shown in Figure 2, and represent the sequence of DoS on/off transitions times and the duration of the mth sleep status, respectively. Correspondingly, for simplicity, let and present the sleeping interval and the attack interval, respectively.
In addition, let and represent, respectively, all single sleeping ranges and all single attack ranges
To characterize the constraints of limited energy on DoS attacks, it is necessary to give the following two assumptions for the frequency and the duration of DoS attacks, respectively.
Assumption 1
(DoS Duration [22]). There exist and for all , which makes the following inequality hold
Assumption 2
(DoS Frequency [22]). There exist , and for all , which makes the following inequality hold
Remark 1.
The intent of the DoS attack is not generally sporadic and periodic, but aperiodic (stochastic). Therefore, the periodic DoS attack is not realistic in theoretical research and practical industrial production. To tackle this issue, this paper focuses on the more realistic aperiodic DoS attacks in the following part. In addition, Assumption 1 excludes the situation of continuous DOS attacks, which makes the considered system open-loop and uncontrollable.
In this subsection, we will illustrate the proposed procedures for a resilient dynamically triggering strategy in favor of the aperiodic DoS attacks. To achieve this goal, denote e the difference between the last successfully transmission state and the current state
where is determined by the upcoming DTM (7).
Herein, similar to [9], using the trigger function . Additionally, the internal dynamic variable is to be defined before a new dynamic triggering strategy sprung up, which is
where is a locally Lipschitz continuous function. Intuitively, may be regarded as a filtered value of (refers to [5]). In particular, the filter (8) is possibly nonlinear if the is nonlinear. The dynamic event-triggered strategy (7) reduces to event-triggered strategy in [29] when goes to (detailed analysis refers to [9]).
Based on the discussion before, the following lemma is needed to guarantee .
Lemma 1.
Proof.
According to (8), which corresponds to the following inequality:
First, if , then is true.
Second, if by combing (8) and (9), one has
Then, solve (10) for , one has
which means that is lower bound by a positive exponential signal, so one can obtain □
In addition, taking DoS attacks into consideration, as we all know, the measurement data will be lost even if the condition (7) is satisfied. To alleviate the effects of DoS attacks, a resilient strategy will be presented in the following. In particular, combining with (7), one defines a novel RDET communication strategy as follows:
Remark 2.
With the opening of network control system communication, the system is more vulnerable to all kinds of malicious attacks. In order to eliminate the adverse effects of the attack and ensure better performance of the system, the elastic control technology based on dynamic event triggering plays an important role. This is especially true in many industrial controls, such as power systems [27], Chua circuits [30], and vehicle systems [31].
Next, we use the following DoS attacks as follows:
In this paper, the state-dependent control input under DoS attacks can be represented as
Based on the above analysis, in what follows, combining (1), (12), and (13), the switched version of system (1) can be represented as
In the following sections, the conditions for the exponential stability of system (14) with DoS attacks will be provided.
3. Main Result
This section aims to develop a piecewise Lyapunov function for NNS under DoS attacks. The resilient analysis of nonlinear switched system (14) is discussed, and the related parameters are obtained. Theorem 1 is presented to guarantee the RDET control for NNS under DoS attacks. In addition, it is worth noting that the Zeno behavior is excluded in Theorem 2.
Theorem 1.
Consider the NNSs (1) under DoS attacks satisfying Assumptions 1 and 2, under the switched controller (13) with dynamic event-triggered condition (7). If some functions and γ hold, then the switched Lyapunov function of (14) satisfies the following inequality
where , and the parameters in (6) and T in (4) satisfy
Proof.
To show the complete theoretical analysis of the above theorem, we will deal with it in two steps.
Case 1: Assume there are no DoS attacks.
For , according to (16) and DTM (11), the derivative of is subject to
where and .
Case 2: Assume there are DoS attacks.
For , based on (17), it is easy to obtain the derivative of as follows
Hence, combing (21) with (22) gives a piecewise Lyapunov functional, and , respectively, can be found as below
First, assume , according to definition 4, one has
where .
Then, assume , according to definition 4 again, one has
where .
In what follows, using (15), the above inequality (25) can be modified as
where . Based on (26), if DoS attacks satisfy , then, system (1) with control input (11) under DoS attacks is GWES. Further, one has
The proof is completed. □
Remark 3.
This theorem characterizes the system’s resilience issue. Moreover, shows that the stability of NNSs can be guaranteed in the event they suffer from more DoS attacks that satisfy some constraints of attack interval and attack frequency.
Remark 4.
It is worth pointing out that the inequality constraint on and γ in Assumption 4 in [23] is unnecessary in our work. More specifically, in this article, with the aid of introducing a piecewise Lyapunov function, Assumption 4 in [23] is removed, which reduces the conservatism of the system.
Next, we will give the conditions that void the Zeno behavior. Before continuing the discussion, we impose an assumption.
Assumption 3
([5]). Because of the Lipschitz continuity of the function , there exists a constant which satisfies the following inequality
where .
Theorem 2.
Proof.
First, we define the inter-execution time . According to the ZOH scheme, there is when . Meanwhile, with the inequality (27), one has
Furthermore, for , it is easy to get the following equation
Herein, using the comparison lemma, we have
4. Simulation
In this section, the practical merits of the proposed controllers and theory are corroborated using the well-known nonlinear Chua circuit, as shown in Figure 3. Considering the control input , its dynamics are generated as
where and are voltages across and , respectively. is current through the inductance. is characteristic of the nonlinear resistance .
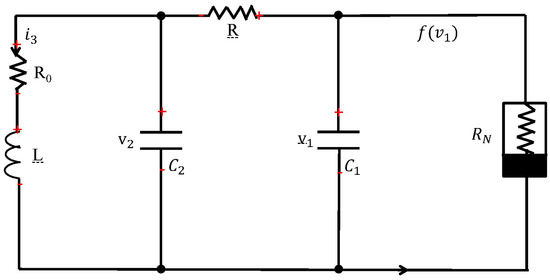
Figure 3.
Diagram of a nonlinear Chua circuit.
Next, let , and . Then, (32) can be transferred into the following as
According to [33], there exists a chaotic attractor (see Figure 4) when some parameters are fixed at ; . Meanwhile, system (33) is rewritten as
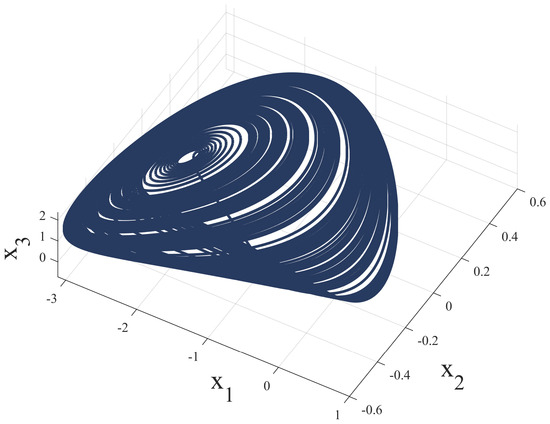
Figure 4.
The chaotic attractor for the Chua circuit.
Set the initial state . System (34) is unstable without the control input u. Then, set ; simulation time with sampling period .
Case 1: According to Theorem 1, one can design a controller under the RDET strategy (11) to stabilize system (34) without aperiodic DoS attacks. The state response of system (34) is shown in Figure 5. Moreover, the number of triggered packets to be transmitted is 82 times. The event interval time of the event generator is depicted in Figure 6. In particular, one can design another controller under event-triggered communication scheme (7) to stabilize system (34) without DoS attacks. Meanwhile, a stable periodic solution will be presented in Figure 7. The event intervals of the event generator are depicted in Figure 8.
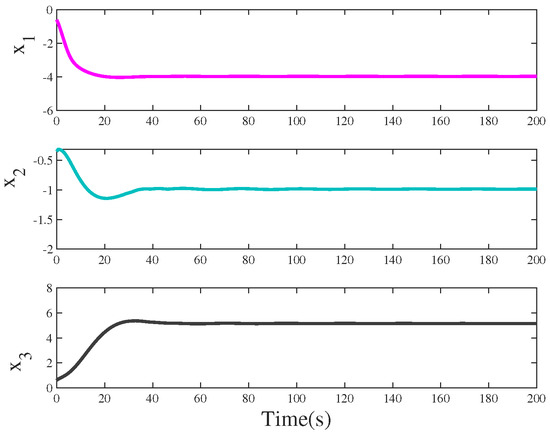
Figure 5.
State responses of triggering control systems without aperiodic DoS attacks.
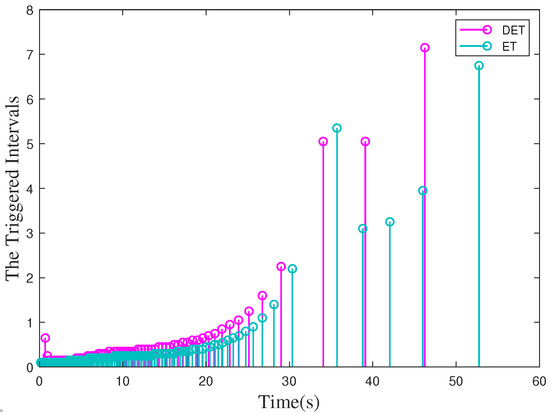
Figure 6.
The triggered intervals of control systems without aperiodic DoS attacks.
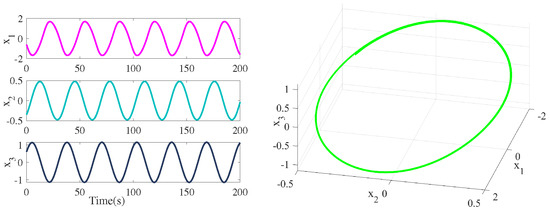
Figure 7.
Stable periodic solution of triggering control systems without aperiodic DoS attacks.
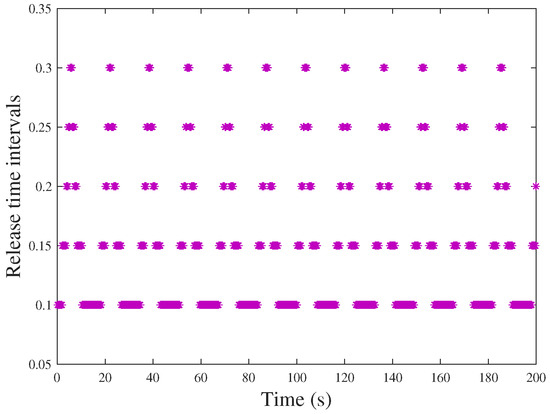
Figure 8.
Release time intervals corresponding to a stable periodic solution.
Case 2: In the sequence, under the same circumstances, once system (34) suffers from malicious aperiodic attacks, the system is unstable in Figure 9, where the gray areas represent the DoS attack time intervals. In addition, release time intervals are depicted in Figure 10 with 756 triggered packets to be successfully transmitted to the controller under the event-triggered communication scheme (7).
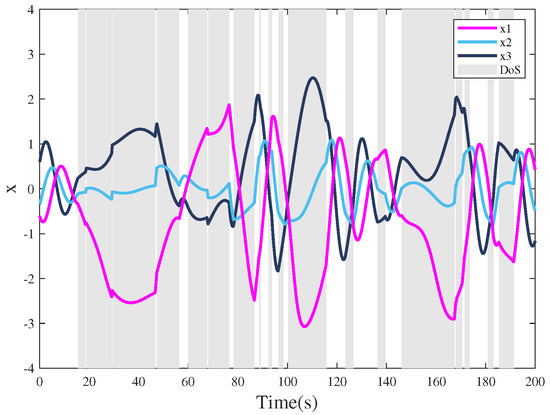
Figure 9.
The state trajectories of unstable triggering control systems under aperiodic DoS attacks.
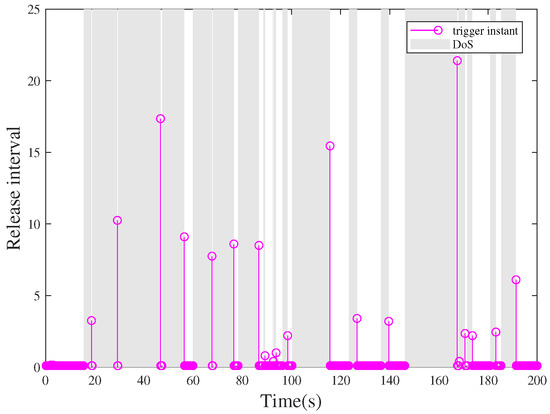
Figure 10.
Period of triggering control systems under aperiodic DoS attacks.
Case 3: The system is not GAS with . The stabilizing control law is . We select as a Lyapunov function when , so that the holds true if . Notice that
Next, We select as Lyapunov function when , so that the holds true if . Notice that
According to the aforementioned analysis, there exist and , which satisfy (15) in Theorem 1. Meanwhile, (35) and (36) allow , to satisfy (16) and (17) in Theorem 1, respectively. In addition, set , and , which satisfy (18) in Theorem 1. Let , , , and , one has and satisfy (19) and (20), respectively. Moreover, and .
Herein, Figure 11 depicts the state responses of system (34) under DoS attacks, and which shows that system (34) is stable. The release instants are depicted in Figure 12, and there are 716 sampled packets transmitted successfully Under the supervision of the DTM (11). Figure 13 presents the aperiodic DoS attack sequence. Next, Table 1 presents a comparison of the different triggering strategies.
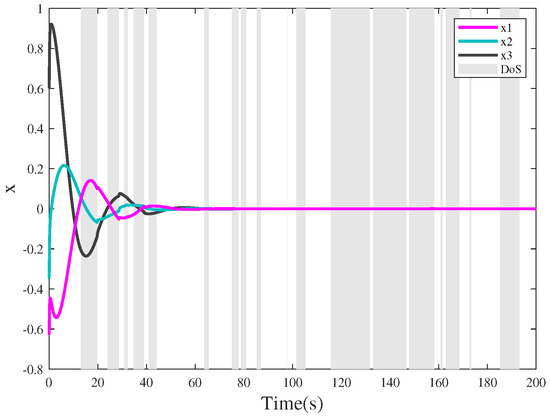
Figure 11.
The stable state trajectories under aperiodic DoS attacks.
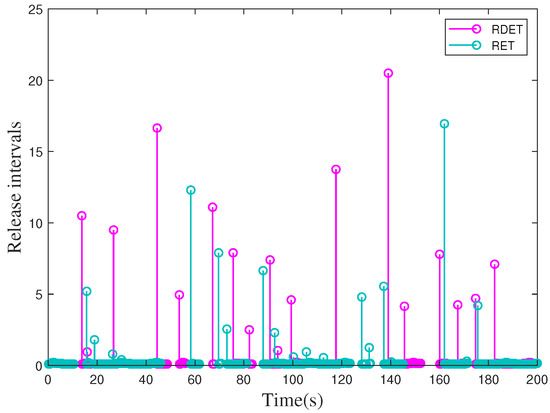
Figure 12.
Triggered instants and release intervals under aperiodic DoS attacks.
Figure 13.
Aperiodic DoS attacks.

Table 1.
Comparing different control schemes.
First, before analyzing Table 1, we give out design formulas on a triggering rate, which is expressed as . Second, from Table 1, it is obvious that once the system suffers from aperiodic DoS attacks, the number of triggering events and the triggering rate will add the same parameters designed before to the framework. On contrary, the average interval will become small to add the number of triggering events and compensate for lost packets due to DoS attacks.
Remark 5.
In the simulation, the modeling and generation of DoS attacks is similar to [22]. Since the attacks are affected by energy constraints, they are intermittent non-periodic attacks, and only focus on the single communication channels (sensor-to-controller).
Remark 6.
Figure 6 and Figure 12 display the triggered intervals of the four strategies. Figure 6 indicates RDET strategy can generate a bigger average interval than the ET strategy without aperiodic DoS attacks. Moreover, a similar result is presented in Figure 12, namely, the RDET strategy can generate a bigger average interval than the RET strategy suffering aperiodic DoS attacks. This result is consistent with Table 1.
5. Conclusions
In this paper, we have designed a DRTC to stabilize NNSs under malicious aperiodic DoS attacks. Furthermore, the stability criterion is obtained under malicious aperiodic DoS attacks based on Lyapunov theory. In addition, the minimal inter-event time excludes Zeno behavior for the controller (13) with dynamically triggering strategy (11). Finally, the merits of the proposed controllers and theory are corroborated using the well-known nonlinear Chua circuit. Based on our current work, in the future, we will consider security-based event-triggered learning control for NNSs subject to stochastic attacks.
Author Contributions
Conceptualization, W.T.; methodology, W.T.; validation, W.T., H.W. and H.H.; formal analysis, H.W., H.H. and X.L.; investigation, W.T. and H.H.; writing—original draft preparation, W.T.; writing—review and editing, W.T., H.W. and H.H.; visualization, W.T., H.W., X.L. and M.Z.; supervision, H.W., H.H. and X.L.; project administration, H.W. and H.H.; funding acquisition, H.W., H.H., X.L. and M.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China under Grant Nos. 61673107, 62073076, 62203109, 62003218, and 62022088, International Partnership Program of Chinese Academy of Sciences under Grant 173321KYSB20200002, the Jiangsu Provincial Key Laboratory of Networked Collective Intelligence under Grant No. BM2017002, Guangdong Basic, Applied Basic Research Foundation under Grants 2019A1515110234 and 2020A1515110148, and Natural Science Foundation of Jiangsu Province under grant numbers BK20210216 and BK20220812.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chen, C.; Nagananda, K.G.; Xiong, G.; Kishore, S.; Snyder, L.V. A communication-based appliance scheduling scheme for consumer-premise energy management systems. IEEE Trans. Smart Grid 2013, 4, 56–65. [Google Scholar] [CrossRef]
- Saleh, M.; Esa, Y.; Mohamed, A.A. Communication-based control for DC microgrids. IEEE Trans. Smart Grid 2018, 10, 2180–2195. [Google Scholar] [CrossRef]
- Song, H.; Gao, S.; Li, Y.; Liu, L.; Dong, H. Train-centric communication based autonomous train control system. IEEE Trans. Intell. Vehicles 2022. [Google Scholar] [CrossRef]
- Heemels, W.P.M.H.; Johansson, K.H.; Tabuada, P. An introduction to event-triggered and self-triggered control. In Proceedings of the 2012 IEEE 51st IEEE Conference on Decision and Control (CDC), Maui, HI, USA, 10–13 December 2012; pp. 3270–3285. [Google Scholar]
- Tabuada, P. Event-triggered real-time scheduling of stabilizing control tasks. IEEE Trans. Autom. Control 2007, 52, 1680–1685. [Google Scholar] [CrossRef]
- Heemels, W.P.M.H.; Donkers, M.C.F.; Teel, A.R. Periodic event-triggered control for linear systems. IEEE Trans. Autom. Control 2012, 58, 847–861. [Google Scholar] [CrossRef]
- Wang, W.; Postoyan, R.; Nešić, D.; Heemels, W.P. Periodic event-triggered control for nonlinear networked control systems. IEEE Trans. Autom. Control 2019, 65, 620–635. [Google Scholar] [CrossRef]
- Sun, J.; Yang, J.; Zeng, Z. Predictor-based periodic event-triggered control for nonlinear uncertain systems with input delay. Automatica 2022, 136, 110055. [Google Scholar] [CrossRef]
- Girard, A. Dynamic Triggering Mechanisms for Event-Triggered Control. IEEE Trans. Autom. Control 2015, 60, 1992–1997. [Google Scholar] [CrossRef]
- Luo, S.; Deng, F.; Chen, W.H. Dynamic event-triggered control for linear stochastic systems with sporadic measurements and communication delay. Automatica 2019, 107, 86–94. [Google Scholar] [CrossRef]
- Dolk, V.S.; Borgers, D.P.; Heemels, W.P.M.H. Output-based decentralized dynamic event-triggered control with guaranteed -gain performance and zeno-freeness. IEEE Trans. Autom. Control 2017, 62, 34–49. [Google Scholar] [CrossRef]
- Demirel, B.; Leong, A.S.; Gupta, V.; Quevedo, D.E. Tradeoffs in stochastic event-triggered control. IEEE Trans. Autom. Control 2018, 64, 2567–2574. [Google Scholar] [CrossRef]
- Peng, C.; Wu, J.; Tian, E. Stochastic event-triggered H∞ control for networked systems under denial of service attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 52, 4200–4210. [Google Scholar] [CrossRef]
- Han, D.; Mo, Y.; Wu, J.; Weerakkody, S.; Sinopoli, B.; Shi, L. Stochastic event-triggered sensor schedule for remote state estimation. IEEE Trans. Autom. Control 2015, 560, 2661–2675. [Google Scholar] [CrossRef]
- Huang, Y.; Liu, Y. Switching event-triggered control for a class of uncertain nonlinear systems. Automatica 2019, 108, 108471. [Google Scholar] [CrossRef]
- Fan, Y.; Huang, X.; Shen, H. Switching event-triggered control for global stabilization of delayed memristive neural networks: An exponential attenuation scheme. Neural Netw. 2019, 117, 216–224. [Google Scholar] [CrossRef]
- Li, H.; Chen, Z.; Wu, L.; Lam, H.K. Event-triggered control for nonlinear systems under unreliable communication links. IEEE Trans. Fuzzy Syst. 2016, 25, 813–824. [Google Scholar] [CrossRef]
- Li, Z.; Hu, B.; Li, M.; Luo, G. String stability analysis for vehicle platooning under unreliable communication links with event-triggered strategy. IEEE Trans. Veh. Technol. 2019, 68, 2152–2164. [Google Scholar] [CrossRef]
- Wang, J.; Ma, F.; Yang, Y.; Nie, J.; Bilin, A.G.; Guvenc, L. Adaptive event-triggered platoon control under unreliable communication links. Trans. Intell. Transp. Syst. 2020, 23, 1924–1935. [Google Scholar] [CrossRef]
- Xiao, S.; Han, Q.L.; Ge, X.; Zhang, Y. Secure distributed finite-time filtering for positive systems over sensor networks under deception attacks. IEEE Trans. Cybern. 2020, 50, 1220–1229. [Google Scholar] [CrossRef]
- Liu, J.L.; Yin, T.T.; Yue, D.; Karimi, H.R.; Cao, J.D. Event-based secure leader-following consensus control for multi-agent systems with multiple cyber-attacks. IEEE Trans. Cybern. 2020, 51, 162–173. [Google Scholar] [CrossRef]
- Persis, C.D.; Tesi, P. Input-to-state stabilizing control under denial-of-service. IEEE Trans. Autom. Control 2015, 60, 2930–2944. [Google Scholar] [CrossRef]
- Persis, C.D.; Tesi, P. Networked control of nonlinear systems under Denial-of-Service. Syst. Control Lett. 2016, 96, 124–131. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Han, Q.L.; Xie, X.; Chen, X.; Dou, C. Observer-based event-triggered control for networked linear systems subject to denial-of-service attacks. IEEE Trans. Cybern. 2020, 50, 1952–1964. [Google Scholar] [CrossRef] [PubMed]
- Zhao, N.; Shi, P.; Xing, W. Dynamic event-triggered approach for networked control systems under denial of service attacks. Int. J. Robust Nonlinear Control 2021, 31, 1774–1795. [Google Scholar] [CrossRef]
- Amini, A.; Asif, A.; Mohammadi, A. A Unified Optimization for Resilient Dynamic Event-Triggering Consensus Under Denial of Service. IEEE Trans. Cybern. 2020, 52, 2872–2884. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Wang, D.; Su, L.; Park, J.H.; Shen, H. Dynamic Event-Triggered H∞ Load Frequency Control for Multi-Area Power Systems Subject to Hybrid Cyber Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2022. [Google Scholar] [CrossRef]
- Dolk, V.S.; Tesi, P.; Persis, C.D.; Heemels, W.P.M.H. Event-Triggered Control Systems under Denial-of-Service Attacks. IEEE Trans. Control Netw. Syst. 2017, 4, 93–105. [Google Scholar] [CrossRef]
- Liu, F.; Zhao, C.; Wang, C.; Chen, T. Dynamic Event-triggered Control for Nonlinear NCSs Subject to DoS Attacks. J. Frankl. Inst. 2022, 359, 5385–5411. [Google Scholar] [CrossRef]
- Ai, Z.; Peng, L.; Zong, G.; Shi, K. Impulsive Control for Nonlinear Systems Under DoS Attacks: A Dynamic Event-Triggered Method. IEEE Trans. Circuits Syst. II Exp. Briefs 2022, 69, 3839–3843. [Google Scholar] [CrossRef]
- Chen, X.; Chang, X. Resilient filter of nonlinear network systems with dynamic event-triggered mechanism and hybrid cyber attack. Appl. Math. Comput. 2022, 434, 127419. [Google Scholar] [CrossRef]
- Khalil, H.K. Nonlinear Systems, 3rd ed.; Prentice-Hall: Englewood Cliffs, NJ, USA, 2003. [Google Scholar]
- Galias, Z. Continuation-Based Method to Find Periodic Windows in Bifurcation Diagrams With Applications to The Chua’s Circuit With A Cubic Nonlinearity. IEEE Trans. Circuits Syst. I Reg. Papers 2021, 68, 3784–3793. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).