Swap Test-Based Quantum Protocol for Private Array Equality Comparison
Abstract
1. Introduction
- (1)
- We propose a swap test-based quantum protocol for PAEC, in which two participants encode their array elements into qubits received from a semi-honest TP by performing rotation operations. They then return the encoded states to TP to derive the results without revealing any array elements.
- (2)
- The proposed protocol utilizes near-term feasible quantum technologies, including Bell states, rotation operations, and swap tests, as core components, which are easier to simulate on quantum platforms. To verify the feasibility of the proposed protocol, we simulate it using the IBM Quantum Composer.
- (3)
- Due to the use of decoy photon insertion for eavesdropping detection and rotation operations to obfuscate encoded information, the protocol exhibits robustness against quantum attacks from outsider eavesdroppers and attempts by curious participants.
- (4)
- Unlike existing QPC schemes that are typically limited to single-integer comparisons, the proposed protocol enables comparisons of two arrays.
2. Preliminaries
2.1. Rotation Operation
2.2. Swap Test
- Input states: Two quantum states and .
- Ancillary qubit: Initialized to .
- Hadamard gate: Applied to the ancillary qubit to create a superposition.
- Controlled-SWAP gate: The states and interact with the ancillary qubit via a controlled-SWAP operation.
- Measurement: The ancillary qubit is measured to determine the probability of being in state or .
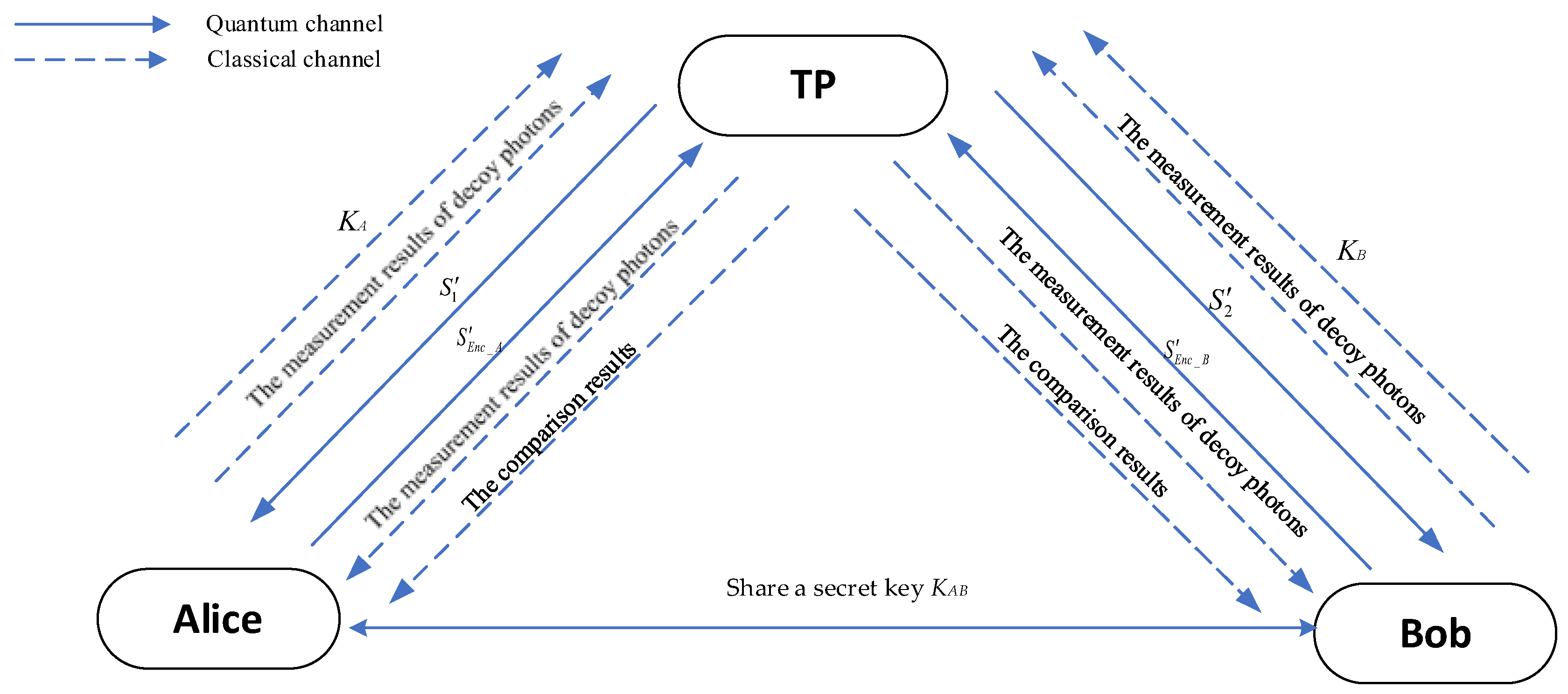
3. Design of the Proposed Protocol
- Correctness: If both Alice and Bob input their arrays honestly and comply with the protocol, TP will accurately announce the comparison result.
- Security: The arrays A and B remain confidential from both other participants and potential attackers, ensuring the confidentiality of the participants’ inputs.
- Fairness: Each party receives the comparison result simultaneously, preventing any asymmetric information advantages.
- (1)
- TP prepares L Bell states in the state and organizes the first and second particles into two quantum sequences and , respectively.
- (2)
- To mitigate eavesdropping risks, TP prepares decoy photons from the set , inserts decoy photons into to create , and inserts another decoy photons into to create .
- (3)
- TP records the positions and states of the decoy photons, and sends and to Alice and Bob via quantum channels, respectively.
- (1)
- Upon receiving and , Alice and Bob send confirmation information to TP via an authenticated classical channel.
- (2)
- TP announces the positions and measurement bases for the decoy photons. If the decoy photon is in states or , the Z basis is used; otherwise, the X basis is applied.
- (3)
- (1)
- Alice and Bob remove the decoy photons from and to recover and , respectively.
- (2)
- Alice encodes each element in array A as (notably, if , then ). Bob encodes each element in array B using the same method.
- (3)
- Alice applies to the -th qubit in , and Bob applies to the -th qubit in , generating sequences and , respectively.
- (4)
- Alice generates an encrypted key , and Bob generates .
- (5)
- Alice and Bob apply the rotation operations and to the i-th qubit in and , resulting in encrypted sequences and , respectively.
- (6)
- Both Alice and Bob prepare decoy photons and insert them into their respective encrypted sequences, forming and , and send these to TP via quantum channels.
- (1)
- When TP receives and , he interacts with Alice and Bob to check for eavesdropping.
- (2)
- Alice and Bob compute the error rate as in Step 2. If the error rate is acceptable, they publish their secret keys and to TP.
- (1)
- TP removes decoy photons from and to recover and , respectively.
- (2)
- TP applies and to the i-th qubit in and , respectively, to obtain sequences and .
- (3)
- TP conducts swap tests on each i-th qubit in sequences and .
- (4)
- TP measures the ancilla qubits from the swap tests to obtain measurement results.
- (1)
- By performing the above steps times, TP collects multiple measurement results.
- (2)
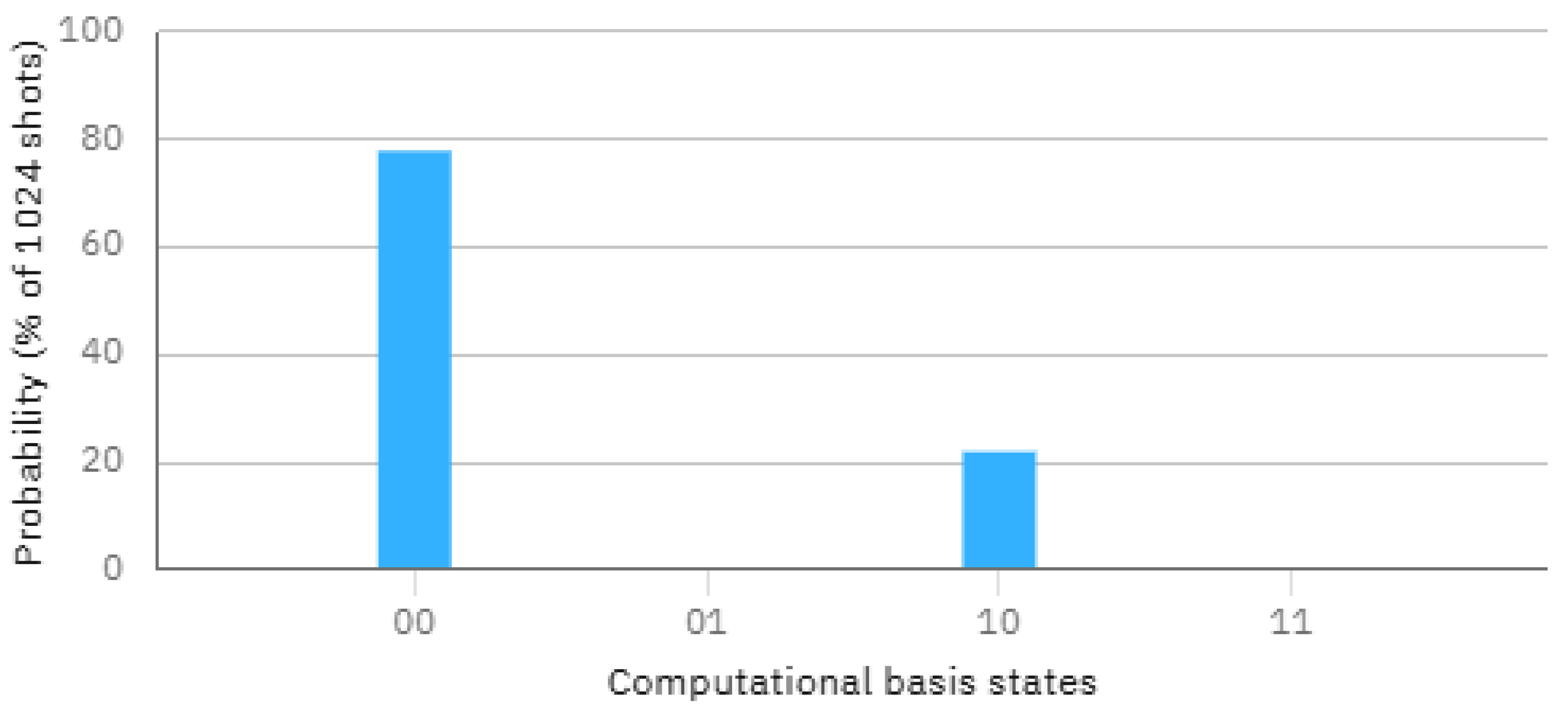
- If any measurement result indicates |1⟩, the arrays A and B are not identical. If all results indicate |0⟩, the arrays are the same.
- (3)
- TP announces the result to Alice and Bob simultaneously.
4. Simulation
5. Analysis
5.1. Correctness
5.2. Security
5.2.1. Outside Attacks
5.2.2. Participant Attacks
5.3. Fairness
6. Comparison
- (1)
- (2)
- The proposed protocol utilizes Bell states, rotation operations, and swap tests, avoiding the need for entanglement swapping [25,26,31,33] and d-level quantum states [33,34]. This simplification reduces the operational complexity of the protocol and enhances its compatibility with current quantum technologies, facilitating implementation.
- (3)
- The proposed protocol employs single-particle measurements rather than Bell-basis measurements [31], joint measurements [26], or d-level quantum state measurements [33,34]. Single-particle measurements require base vector projection of a single quantum state (e.g., Z-basis, X-basis), without the need for multi-particle cooperative operations. In contrast, joint measurements necessitate multi-particle interference, which is hindered by imperfections in light sources. Additionally, d-dimensional quantum state measurements require the design of d orthogonal basis vectors, and high-dimensional control is vulnerable to decoherence effects. For instance, in remote state preparation, d-level Bell state measurement demands customized quantum gates and entanglement sources, with experimental difficulty increasing exponentially with d. This approach reduces the measurement requirements, making the protocol more practical and easier to implement.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers Systems and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Li, Y.; Cai, W.Q.; Ren, J.G.; Wang, C.Z.; Yang, M.; Zhang, L.; Wu, H.Y.; Chang, L.; Wu, J.C.; Jin, B.; et al. Microsatellite-based real-time quantum key distribution. Nature 2025, 640, 47–54. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, W.-J.; Jiang, C.; Chen, J.-P.; Zhang, C.; Pan, W.-X.; Ma, D.; Dong, H.; Xiong, J.-M.; Zhang, C.-J.; et al. Experimental twin-field quantum key distribution over 1000 km fiber distance. Phys. Rev. Lett. 2023, 130, 210801. [Google Scholar] [CrossRef] [PubMed]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.-B.; Chang, Y.; Qiu, C.; Liu, D.-M.; Hou, M. Quantum key agreement protocol based on quantum search algorithm. Int. J. Theor. Phys. 2021, 60, 838–847. [Google Scholar] [CrossRef]
- Lin, S.; Zhang, X.; Guo, G.-D.; Wang, L.-L.; Liu, X.-F. Multiparty quantum key agreement. Phys. Rev. A 2021, 104, 042421. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Quantum multi-party private set intersection using single photons. Phys. A: Stat. Mech. Its Appl. 2024, 649, 129974. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Quantum Private Set Intersection Scheme Based on Bell States. Axioms 2025, 14, 120. [Google Scholar] [CrossRef]
- Chen, Y.; Situ, H.; Huang, Q.; Zhang, C. A novel quantum private set intersection scheme with a semi-honest third party. Quantum Inf. Process. 2023, 22, 429. [Google Scholar] [CrossRef]
- Sheng, Y.B.; Zhou, L.; Long, G.L. One-step quantum secure direct communication. Sci. Bull. 2022, 67, 367–374. [Google Scholar] [CrossRef]
- Zhang, H.; Sun, Z.; Qi, R.; Yin, L.; Long, G.-L.; Lu, J. Realization of quantum secure direct communication over 100 km fiber with time-bin and phase quantum states. Light Sci. Appl. 2022, 11, 83. [Google Scholar] [CrossRef] [PubMed]
- Ying, J.W.; Wang, J.Y.; Xiao, Y.X.; Gu, S.P.; Wang, X.F.; Zhong, W.; Du, M.M.; Li, X.Y.; Shen, S.T.; Zhang, A.L.; et al. Passive-state preparation for quantum secure direct communication. Sci. China Phys. Mech. Astron. 2025, 68, 240312. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.; Chang, Y.; Yang, F.; Hou, M.; Cheng, W. Quantum secure direct communication based on quantum homomorphic encryption. Mod. Phys. Lett. A 2021, 36, 2150263. [Google Scholar] [CrossRef]
- Lindell, Y. Secure multiparty computation. Commun. ACM 2020, 64, 86–96. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), Washington, DC, USA, 3–5 November 1982; p. 160. [Google Scholar]
- Boudot, F.; Schoenmakers, B.; Traore, J. A fair and efficient solution to the socialist millionaires’ problem. Discret. Appl. Math. 2001, 111, 23–36. [Google Scholar] [CrossRef]
- Lo, H.K. Insecurity of quantum secure computations. Phys. Rev. A. 1997, 56, 1154–1162. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Grover, L.K. Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 1997, 79, 325. [Google Scholar] [CrossRef]
- Yang, Y.G.; Wen, Q.Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 2009, 42, 055305. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.F.; Zhang, S.B. Efficient multiparty quantum private comparison protocol based on single photons and rotation encryption. Quantum Inf. Process. 2023, 22, 272. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Single-photon-based quantum secure protocol for the socialist millionaires’ problem. Front. Phys. 2024, 12, 1364140. [Google Scholar] [CrossRef]
- Ji, Z.; Zhang, H.; Wang, H. Quantum private comparison protocols with a number of multi-particle entangled states. IEEE Access 2019, 7, 44613–44621. [Google Scholar] [CrossRef]
- Fan, P.; Rahman, A.U.; Ji, Z.; Ji, X.; Hao, Z.; Zhang, H. Two-party quantum private comparison based on eight-qubit entangled state. Mod. Phys. Lett. A 2022, 37, 2250026. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.-B.; Chang, Y.; Hou, M.; Cheng, W. Efficient quantum private comparison based on entanglement swapping of bell states. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Jia, H.Y.; Wen, Q.Y.; Li, Y.B.; Gao, F. Quantum private comparison using genuine four-particle entangled states. Int. J. Theor. Phys. 2012, 51, 1187–1194. [Google Scholar] [CrossRef]
- Sun, Q. Quantum private comparison with six-particle maximally entangled states. Mod. Phys. Lett. A 2022, 37, 2250149. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Efficient Quantum Private Comparison with Unitary Operations. Mathematics 2024, 12, 3541. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. New Quantum Private Comparison Using Four-Particle Cluster State. Entropy 2024, 26, 512. [Google Scholar] [CrossRef]
- Xu, G.A.; Chen, X.B.; Wei, Z.H.; Li, M.J.; Yang, Y.X. An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quantum Inf. 2012, 10, 1250045. [Google Scholar] [CrossRef]
- Li, C.; Chen, X.; Li, H.; Yang, Y.; Li, J. Efficient quantum private comparison protocol based on the entanglement swapping between four-qubit cluster state and extended Bell state. Quantum Inf. Process. 2019, 18, 158. [Google Scholar] [CrossRef]
- Chang, Y.; Zhang, W.-B.; Zhang, S.-B.; Wang, H.-C.; Yan, L.-L.; Han, G.-H.; Sheng, Z.-W.; Huang, Y.-Y.; Suo, W.; Xiong, J.-X. Quantum private comparison of equality based on five-particle cluster state. Commun. Theor. Phys. 2016, 66, 621. [Google Scholar] [CrossRef]
- Guo, F.Z.; Gao, F.; Qin, S.J.; Zhang, J.; Wen, Q.Y. Quantum private comparison protocol based on entanglement swapping of d-level Bell states. Quantum Inf. Process. 2013, 12, 2793–2802. [Google Scholar] [CrossRef]
- Wang, B.; Gong, L.H.; Liu, S.Q. Multi-party quantum private size comparison protocol with d-dimensional Bell states. Front. Phys. 2022, 10, 981376. [Google Scholar] [CrossRef]
- Wu, W.Q.; Zhao, Y.X. Quantum private comparison of size using d-level Bell states with a semi-honest third party. Quantum Inf. Process. 2021, 20, 155. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum private magnitude comparison. Int. J. Theor. Phys. 2022, 61, 100. [Google Scholar] [CrossRef]
- Huang, X.; Chang, Y.; Cheng, W.; Hou, M.; Zhang, S.-B. Quantum private comparison of arbitrary single qubit states based on swap test. Chin. Phys. B 2022, 31, 040303. [Google Scholar] [CrossRef]
- Lin, P.H.; Hwang, T.; Tsai, C.W. Efficient semi-quantum private comparison using single photons. Quantum Inf. Process. 2019, 18, 207. [Google Scholar] [CrossRef]
- Wang, B.; Liu, S.Q.; Gong, L.H. Semi-quantum private comparison protocol of size relation with d-dimensional GHZ states. Chin. Phys. B 2022, 31, 010302. [Google Scholar] [CrossRef]
- Zhou, N.R.; Chen, Z.Y.; Liu, Y.Y.; Gong, L.H. Multi-Party Semi-Quantum Private Comparison Protocol of Size Relation with d-Level GHZ States. Adv. Quantum Technol. 2024, 8, 2400530. [Google Scholar] [CrossRef]
- Lian, J.Y.; Li, X.; Ye, T.Y. Multi-party semiquantum private comparison of size relationship with d-dimensional Bell states. EPJ Quantum Technol. 2023, 10, 207. [Google Scholar] [CrossRef]
- Gong, L.H.; Li, M.L.; Cao, H.; Wang, B. Novel semi-quantum private comparison protocol with Bell states. Laser Phys. Lett. 2024, 21, 055209. [Google Scholar] [CrossRef]
- Gong, L.H.; Ye, Z.J.; Liu, C.; Zhou, S. One-way semi-quantum private comparison protocol without pre-shared keys based on unitary operations. Laser Phys. Lett. 2024, 21, 035207. [Google Scholar] [CrossRef]
- Buhrman, H.; Cleve, R.; Watrous, J.; de Wolf, R. Quantum fingerprinting. Phys. Rev. Lett. 2001, 87, 167902. [Google Scholar] [CrossRef] [PubMed]
- Kang, M.S.; Choi, H.W.; Pramanik, T.; Han, S.W.; Moon, S. Universal quantum encryption for quantum signature using the swap test. Quantum Inf. Process. 2018, 17, 254. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, Y.-H.; Shao, C.-P.; Wu, Y.-C.; Guo, G.-C.; Guo, G.-P. Building quantum neural networks based on a swap test. Phys. Rev. A 2019, 100, 012334. [Google Scholar] [CrossRef]
- Li, P.; Wang, B. Quantum neural networks model based on swap test and phase estimation. Neural Netw. 2020, 130, 152–164. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.; Zhang, W.; Zhang, S. Practical quantum protocols for blind millionaires’ problem based on rotation encryption and swap test. Phys. A Stat. Mech. Its Appl. 2024, 637, 129614. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Quantum Privacy Comparison with Ry Rotation Operation. Mathematics 2025, 13, 1071. [Google Scholar] [CrossRef]
- Beale, S.J.; Wallman, J.J.; Gutiérrez, M.; Brown, K.R.; Laflamme, R. Quantum error correction decoheres noise. Phys. Rev. Lett. 2018, 121, 190501. [Google Scholar] [CrossRef]
- Jennewein, T.; Simon, C.; Weihs, G.; Weinfurter, H.; Zeilinger, A. Quantum cryptography with entangled photons. Phys. Rev. Lett. 2000, 84, 4729. [Google Scholar] [CrossRef]
- Hughes, R.J.E.; Nordholt, J.; Derkacs, D.; Peterson, C.G. Practical free-space quantum key distribution over 10 km in daylight and at night. New J. Phys. 2002, 4, 43. [Google Scholar] [CrossRef]
- Li, Z.H.; Wang, L.; Xu, J.; Yang, Y.; Al-Amri, M.; Zubairy, M.S. Counterfactual trojan horse attack. Phys. Rev. A 2020, 101, 022336. [Google Scholar] [CrossRef]


| Protocol | Quantum Resources | Unitary Operation | Entanglement Swapping Operation | Quantum Measurement | Comparison Object |
|---|---|---|---|---|---|
| Ref. [25] | 2L Bell states | No | Yes | GHZ-basis | Binary representation of integer |
| Ref. [26] | L + 4m χ-type entangled states | Yes | Yes | Joint | Binary representation of integer |
| Ref. [31] | 2L Four-qubit cluster state and extended Bell state | No | Yes | Bell basis and extended Bell basis | Binary representation of integer |
| Ref. [33] | (1 + δ) d-level Bell state | Yes | Yes | d-level Bell basis | Integer |
| Ref. [34] | 2L d-level Bell state | No | No | d-level single-particle | Integer |
| Ours | 2λL Bell states | Yes | No | Single-particle (Z basis) | Array |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hou, M.; Zhang, S. Swap Test-Based Quantum Protocol for Private Array Equality Comparison. Mathematics 2025, 13, 2425. https://doi.org/10.3390/math13152425
Hou M, Zhang S. Swap Test-Based Quantum Protocol for Private Array Equality Comparison. Mathematics. 2025; 13(15):2425. https://doi.org/10.3390/math13152425
Chicago/Turabian StyleHou, Min, and Shibin Zhang. 2025. "Swap Test-Based Quantum Protocol for Private Array Equality Comparison" Mathematics 13, no. 15: 2425. https://doi.org/10.3390/math13152425
APA StyleHou, M., & Zhang, S. (2025). Swap Test-Based Quantum Protocol for Private Array Equality Comparison. Mathematics, 13(15), 2425. https://doi.org/10.3390/math13152425






