Abstract
Target threat assessment provides support for combat decision making. The multi-target threat assessment method based on a three-way decision can obtain threat classification while receiving threat ranking, thus avoiding the limitation of traditional two-way decisions. However, the heterogeneous situation information, attribute relevance, and adaptive information processing needs in complex battlefield environment bring challenges to existing methods. Therefore, this paper proposes a new multi-target three-way threat assessment method with heterogeneous information and attribute relevance. Firstly, dynamic assessment information is represented by heterogeneous information, and attribute weights are calculated by heterogeneous Criteria Importance Through Intercriteria Correlation (CRITIC). Then, the conditional probability is calculated by the heterogeneous weighted Technique for Order Preference by Similarity to Ideal Solution (TOPSIS), and the adaptive risk avoidance coefficients are constructed by calculating the uncertainty of the assessment value, and then the relative loss function matrices are constructed. Finally, the comprehensive loss function matrices are obtained by the weighted Heronian mean (HM) operator, and the comprehensive thresholds are calculated to obtain the three-way rules. The case study shows that compared with the existing methods, the proposed method can effectively handle the heterogeneous information and attribute relevance, and obtain the risk avoidance coefficients without presetting or field subjective settings, which is more suitable for the complex mission environment.
Keywords:
heterogeneous information; three-way decision; threat assessment; attribute relevance; risk avoidance coefficient MSC:
90B50; 90C70
1. Introduction
The research and application of military technology is an important part of the development of science and technology. Modern war is a highly informationised and even intelligent systems’ confrontation [1,2]. It involves many operational elements. Typically, to gain an operational advantage, both sides need to focus their superior forces on the other side’s high-value targets in combat decision making [3]. In the course of combat, targets with a higher threat degree are usually considered to be high-value targets, which need to allocate more resources to attack or interfere first [4,5]. Therefore, target threat assessment is an important issue in modern military combat decision making [6,7].
A typical implementation process of target threat assessment is shown in Figure 1. Briefly, in complex mission scenarios, first determine the threat assessment attributes, then normalize the assessment data, select appropriate threat assessment methods, and finally obtain the threat ranking of the targets. Often, it is desirable to minimize human involvement in the above processes in order to improve timeliness.
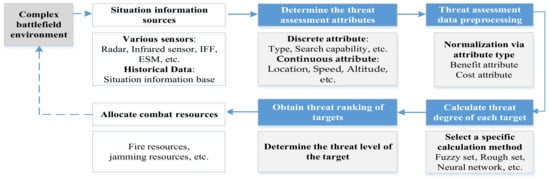
Figure 1.
The implemented process of target threat assessment.
With the increasing complexity of the combat environment and the increasing variety of combat forms, the study object of target threat assessment gradually includes air targets, ground targets, radiation source targets, group targets, and so on. The selection of target threat assessment attributes needs to consider the scenarios, and usually there are discrete attributes, such as the target type; continuous attributes, such as the target location; etc., and the target information comes from the situation information base (historical data), various types of sensors, and so on. Due to the different sources and accuracy of target situation information, different forms of information representation are justified, i.e., the assessment information is heterogeneous. The choice of evaluation methods is crucial. Target threat assessment methods include methods based on multi-attribute decision making (MADM), neural-network-based assessment, Bayesian-network-based estimation, and methods based on fuzzy set theory [8,9,10,11,12]. The characteristics and deficiencies of these methods are listed in Table 1.

Table 1.
The comparison among target threat assessment methods.
Although the research objects of each method in Table 1 are not the same, the methods are universal. The advantages and disadvantages of each method are caused by its theoretical basis, which is detailed in Table 1. Among them, dynamic target threat assessment methods based on fuzzy MADM, which have a good ability to represent uncertainty and to directly calculate the threat degree, have received extensive attention [13,14,15,16,17]. Follow-up studies are also based on this model. However, there are common problems with these methods or models:
(1) Ranking results vary between different assessment methods. Different methods have different focuses and often give different results in threat ranking. This increases the difficulty of selecting high-threat targets reasonably.
(2) These methods usually are two-way decisions and can cause misjudgment. For the threat value that is higher than a certain threshold value, take the priority of the combat strategy, and for the lower value than the threshold value, take the strategy of abandoning the combat. The result of such a decision is an either/or, and if the information is insufficient to support the decision, false judgements are often made, leading to an irrational allocation of combat resources.
To address the above problems, a target threat assessment method that objectively realizes multi-target threat classification is needed. Three-way decision, based on the decision–theoretic rough sets model, was proposed by Yao et al. [18]. It succeeds in rationally assigning semantic interpretations to the positive, negative, and boundary domains of rough sets, which correspond to acceptance, rejection, and delay decisions, respectively, in practical decision making. Since the proposal of the three-way decisions, many scholars have refined and extended it, and it has been widely used in many fields [19,20,21,22,23,24,25].
We first introduced three-way decision into multi-target dynamic threat assessment under an intuitionistic fuzzy MADM environment [26,27], which can obtain threat classification while receiving threat ranking. The application of three-way decision in the field of target threat assessment can be notated as multi-target three-way threat assessment. Subsequently, the literature [28,29,30,31,32] conducted improvement studies, whose main concerns are the optimization calculation of conditional probability and decision thresholds. However, the above methods still cannot meet the practical needs in complex combat scenarios well, which are manifested in the following aspects:
(1) The evaluation information coming from different sources is usually heterogeneous and uncertain. For example, different sensors provide information with different accuracies and it is not reasonable to use the same representation. Discrete and continuous attributes should be represented differently. The representation and processing of assessment information are relatively simple in [26,27,28,29]. A single form of fuzzy numbers, such as intuitionistic fuzzy set, is usually used, which ignores the differences of assessment attributes and is inconsistent with the actual situation.
(2) The attribute relevance is often ignored in existing methods of multi-target three-way threat assessment. Among the existing methods, many weight calculation methods are used, including subjective, objective, and comprehensive weight methods, but the influence of attribute relevance on weight calculation is rarely considered. At the same time, when aggregating information, its influence is usually also ignored.
(3) In combat, it is usually necessary to minimize the influence of humans in the decision process to improve timeliness. Therefore, it is desirable to reduce or avoid subjective settings of parameters in the evaluation process. In existing methods, the risk avoidance coefficients are usually presetting or field subjective settings. On the one hand, the reasonableness depends on the subjective experience, and how to select causing problems, and on the other hand, it may affect the timeliness of combat decision making.
To address the above problems, this paper proposes a new multi-target three-way threat assessment method with heterogeneous information and attribute relevance. In the study of the application of three-way decision, other scholars have considered heterogeneous information processing [33,34,35,36] and the attribute relevance [37,38] separately. Good attempts were indeed made, despite problems such as the potential loss of information during the conversion of heterogeneous information to a single format in some studies. However, in target threat assessment, there has not been a systematic study.
The main contributions are as follows:
(1) The dynamic threat assessment information is represented by heterogeneous forms, such as real numbers, interval numbers, three-parameter intervals, and four-parameter intervals. Which form to use is determined by the source and type of assessment information in a specific mission scenario.
(2) The conditional probabilities are estimated based on heterogeneous weighted TOPSIS, where the attribute weights are calculated by the heterogeneous CRITIC. Obviously, the CRITIC considers both the variability and relevance of attributes [39]. At the same time, the above calculations are performed directly on the heterogeneous assessment information without the need for information conversion.
(3) The adaptive risk avoidance coefficients are calculated by the uncertainty of the assessment value. Then, the relative loss function matrices can be obtained quickly. There is no need to set them subjectively or in advance, and they can objectively reflect the acquisition of situation information.
(4) The comprehensive loss function matrix is constructed by aggregating the relative loss function matrix under each attribute via the weighted HM operator, which can effectively reflect the correlation between the aggregated data.
(5) The proposed method can directly obtain threat ranking and threat classification based on the assessment information without additional parameter settings. It can meet the timeliness need for combat and can even be used directly in autonomous intelligent systems.
Through the heterogeneous representation and correlation processing of evaluation information, as well as the design of adaptive risk avoidance coefficients, the three-way threat assessment method proposed in this paper is more suitable for complex combat environment. The specific structure of this paper is as follows: Section 2 introduces the analytical ground. Section 3 introduces the proposed method. In Section 4, the case study and comparison analysis show that the proposed method is effective. Section 5 concludes this paper.
2. Analytical Ground
2.1. Fuzzy MADM
We first introduce the fuzzy MADM and its application to target threat assessment. In the implementation process, the assessment attributes are used as decision attributes and the targets are used as alternatives. The specific process is expressed as follows:
Assume that alternatives (targets) set consists of elements, consists of assessment attributes, is a set of assessment moments, and is the attribute weight vector, where . The assessment matrix can be denoted as , where is the assessed value for the attribute , of the target at moment . The value can be expressed in the form of fuzzy numbers, etc.
Remark 1.
As mentioned in the Introduction, what the symbols represent is determined by the specific mission scenario. More specifically, the targets can be air targets, ground targets, radiation source targets, group targets, and so on. The assessment attributes could be the type, distance, course angle, speed, height, interface ability, etc. As for the form of the assessed value, it depends on the source and type. In this paper, multi-parameter intervals are used to represent heterogeneous information, which does not mean that other forms, such as linguistic variables, are not allowed. If other types of data are used, a modification of the proposed method is sufficient.
Then, there are usually the following methods to receive ranking results:
(1) Arithmetic weighting method. The weight of each decision attribute is obtained through subjective expert experience or objective data methods. Using operators such as the arithmetic mean, the multi-attribute information is aggregated, and the multiple alternatives are ranked [40].
(2) Method based on ideal solutions. By calculating the distance of each option to the positive and negative ideal solutions, the closeness and other related indexes can be calculated, and the multiple alternatives are ranked by the closeness, such as the TOPSIS method and its improvement methods, the VIKOR method, and so on [41,42].
(3) Dominance decision method. Using decision attributes, a series of dominance relations are constructed, and the set of alternatives is narrowed down by the dominance relations to make the judgement of the superiority or inferiority of the alternatives [43].
As for heterogeneous fuzzy MADM, it usually means that the assessment attributes are not represented in the same form, i.e., some attributes are real numbers, some are interval numbers, and so on. Accordingly, there are two types of processing methods; one is to transform heterogeneous information into the same form, and the other is to extend the last two methods to heterogeneous information environments. The first type of transformation process involves information loss [33]. Therefore, in this paper, we use the second type of method, constructing heterogeneous weighted TOPSIS to estimate conditional probability.
2.2. Three-Way Decision
The study of three-way decision can be divided into three main categories: connotation, extension, and application. The connotation study focuses on the computation of conditional probability, loss function, and decision thresholds; the extension study focuses on the combination of three-way decision with other uncertainty theories, decision methods, etc.; and the application study focuses on the application to specific problems [44,45,46,47].
The three-way decision based on decision–theoretic rough sets is as follows:
Definition 1 ([48]).
Let
be a finite and non-empty set,
be an equivalence relation,
be a rough approximation space.
can be parted by
, expressed as
, and thresholds are set as
. For
, the lower and upper approximation sets of the probabilistic rough set can be defined:
where is the conditional probability, expressed as
.
The universe can be parted into three regions by thresholds, expressed as
Let be the state sets of targets, which means a target belongs to or not; actions are set as , where , , and denote , , and , respectively. The loss function regarding the risk of different actions is exhibited in Table 2. Usually, the loss functions satisfy and .

Table 2.
Loss function matrix.
Then, the three-way decision rules can be expressed as
where the thresholds are defined as
Further assuming that , we can obtain the following:
(P) If , decide ;
(B) If , decide ;
(N) If , decide .
For this study, its goal was to construct a three-way decision about whether the target should be attacked first or not. If the target is classified into the positive domain, it means that the threat level is high and the attack or interference needs to be given priority. If it is divided into negative areas, it means that the threat level is low and there is no need to attack or interfere first. Otherwise, more information is needed to make a judgement.
2.3. Multi-Target Three-Way Threat Assessment Method
Multi-target three-way threat assessment is an application of three-way decision to the area of multi-target threat assessment. The key problems are how to obtain conditional probability and comprehensive decision thresholds via assessment information.
First, the conditional probability usually can be calculated by ideal solutions, being inspired by the literature [49]. More specifically, decision methods based on ideal solutions, such as TOPSIS and VIKOR, can be used to compute conditional probability. Relative closeness and compromise ranking values are used to represent the conditional probability of a target being prioritized for attack, respectively.
Then, the relative loss function matrix of each target under each attribute is constructed by the fuzzy evaluation information [50,51] and risk avoidance coefficient. The comprehensive loss function matrix of the target under the attribute set is aggregated based on the attribute weight and arithmetic mean operator.
Finally, the thresholds are calculated by the comprehensive loss function matrix. The three-way decision rules can also be obtained by conditional probability and decision thresholds.
The above process is analyzed and improved as follows:
- (1)
- In the above process, assessment information is usually represented by a class of fuzzy numbers, such as intuitionistic fuzzy numbers, and conditional probabilities are obtained through intuitionistic fuzzy TOPSIS. In this paper, we consider the heterogeneous representation of situation information and extend the calculation of conditional probability to heterogeneous weighted TOPSIS, whose attribute weights are calculated by the CRITIC method.
- (2)
- In the construction of the relative loss function matrix, the risk avoidance coefficients usually need to be set subjectively and set to the same value, which is not only difficult to determine, but also inconsistent with the actual situation. In this paper, adaptive risk avoidance coefficients are designed based on the uncertainty of the evaluation values.
- (3)
- In the aggregation of relative loss function matrices, the correlation among the assessment attributes is ignored. In this paper, the HM operator is used to aggregate the relative loss function matrices.
Remark 2.
Although there can be many ways to calculate conditional probability and decision thresholds, such as the dominance relation in study [52], the method based on an ideal solution is widely used due to its simplicity and ease of implementation in the existing target threat assessment based on three-way decision.
3. The Proposed Multi-Target Three-Way Threat Assessment Method
In this section, we will describe how the proposed method is realized. The evaluation process is shown in Figure 2. It should be noted that the representation of targets, assessment attributes, etc., is the same as above. Table 3 gives a quick reference to the symbols and acronyms.
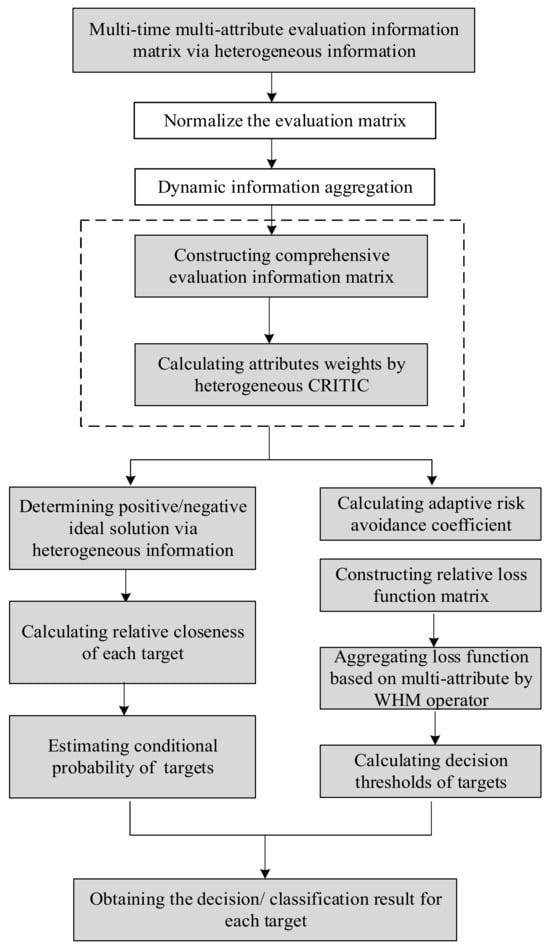
Figure 2.
The evaluation process of proposed method.

Table 3.
Main nomenclature.
3.1. Multi-Time Multi-Attribute Evaluation Information Matrix via Heterogeneous Information
Due to the complexity of the combat environment, it is difficult to effectively interpret the uncertainty using a single fuzzy number form. Therefore, the value of the assessment attribute is expressed by heterogeneous fuzzy information. More specifically, is mainly based on four different forms of information: (1) real numbers (); (2) interval numbers (); (3) three-parameter interval numbers (); and (4) four-parameter interval numbers (). denotes the set of the assessment values, and (), where is an empty set.
Remark 3 ([53]).
A non-negative three-parameter interval number is expressed by
, where
. And a non-negative four-parameter interval number
is expressed by
, where
.
The basic operations on multi-parameter interval numbers are added here. Given two non-negative multi-parameter interval numbers and and a positive real number , some operations are as follows:
- (1)
- ;
- (2)
- ;
- (3)
- ;
- (4)
- .
3.2. Constructing Comprehensive Evaluation Information Matrix
3.2.1. Normalize the Evaluation Information Matrix
In the target threat assessment, the attributes may be usually given by benefit or cost criteria. The magnitude and type of evaluation attributes affect subsequent calculations. Usually, this impact is eliminated by standardizing the evaluation information matrix. There are a number of standardized and normalized calculation methods that will not be repeated here; please refer to [6,36]. Through the normalized process of [6,36], we can obtain a normalized evaluation information matrix, denoted as .
3.2.2. Dynamic Information Aggregation
The target threat assessment should combine the multi-time heterogeneous fuzzy evaluation information. We can obtain the time series weight based on the Poisson distribution method with an inverse form. The closer to the current time, the more important the situation information is. Thus, the series weight vector of K times can be calculated by
where and . Usually, the setting of is 1.5.
Then, combined with time series weights, we can obtain a comprehensive evaluation information matrix, denoted as , where and .
3.3. Calculating Assessment Attribute Weights
In order to take into account the variability and relevance of the attributes, the CRITIC model is applied to calculate the attribute weights of a heterogeneous comprehensive evaluation information matrix, which can be called heterogeneous CRITIC. The main difference with other CRITIC methods [38] is that, through the definition of the distance function, it is suitable for heterogeneous information environments with multi-parameter interval numbers. The main steps are as follows:
(1) Calculate the standard deviation of , where
(2) Calculate the correlation coefficient between and , where
(3) Further, the conflictual relationship of can be expressed by
(4) Calculate the information load of , where
(5) Finally, the weight of can be expressed by
3.4. Estimating Conditional Probability by Heterogeneous Weighted TOPSIS
The conditional probability of each target can be estimated by heterogeneous weighted TOPSIS.
(1) For the comprehensive information matrix, define the heterogeneous positive ideal solution (HPIS) and heterogeneous negative ideal solution (HNIS) as follows:
implies the evaluation of the state , and implies the evaluation of the state .
(2) Calculate relative closeness of each target.
The distance between the target and HPIS is calculated by
The distance between the target and HNIS is calculated by
The relative closeness of each target is expressed as
(3) Estimate conditional probabilities of targets.
Obviously, represents the probability of the target being in the state [26,49]. Thus,
3.5. Calculating Decision Thresholds by Evaluation Values
Firstly, define the absolutely maximum value and minimum value for the attribute, where
(1) Calculate the uncertainty of multi-parameter interval numbers, expressed as
(2) Calculate the adaptive risk avoidance coefficient of , expressed as
where .
Remark 4.
The risk avoidance coefficients reflect the acquisition of situation information. The more sufficient the situation information that can be obtained, the bigger the value of the risk avoidance coefficient [26,50]. We use the uncertainty of the assessed value to indicate the extent of acquisition. The greater the uncertainty, the less adequate the access. The relative magnitude of uncertainty in the assessed value is measured by the range of the upper and lower limits of the interval.
(3) Construct relative loss function matrices via the adaptive risk avoidance coefficient.
The relative loss function matrix of each target under each attribute is expressed as
(4) Aggregate loss function based on multi-attribute information by weighted HM operator.
Since there is correlation in the assessment attributes, there is also correlation in the relative loss function constructed from the attribute values. Therefore, the relative loss function matrices of the target across attributes are aggregated using the weighted HM operator.
Definition 2 ([54]).
Let be a collection of non-negative numbers,
is the weight vector of
,
,
, and
do not take the value 0 simultaneously. If
satisfies
then
is the weighted HM operator with a parameter. Usually, we can set
.
The comprehensive loss function matrix of each target under multi-attribute information via the weighted HM operator is expressed as
(5) Calculate the comprehensive decision threshold.
The corresponding decision thresholds of each target are calculated by
3.6. Obtaining Three-Way Decision Rules
The three-way decisions rules are as follows:
(P1) If , decide , which means that the target threat level is high and there is a need to attack or interfere first;
(B1) If , decide , which means that the target needs more situation information to be analyzed;
(N1) If , decide , which means that the target threat level is low and there is not a need to attack or interfere first.
4. Case Study
The case is from [6], which is about dynamic threat assessment of an unmanned aerial vehicle (UAV) swarm against ground targets. Assume there are three UAVs in the swarm, four ground targets in the combat area, six evaluation attributes, and three moments’ information, i.e., , , and . More specifically, the six evaluation attributes are the number of fire units, reliability, viability, searching ability, damage ability, and anti-jamming ability.
The evaluation process in study [6] is divided into consensus process and selection process. For the multiple UAV consensus-reaching process, we do not need to pay attention to it. We just compare the threat assessment method used in its selection process with our method. As for dynamic heterogeneous information processing, the two papers are similar.
4.1. Three-Way Threat Assessment Based on Heterogeneous Information Processing
The comprehensive evaluation matrix of study [6] is exactly the comprehensive evaluation information matrix of this paper, as listed in Table 4.

Table 4.
Comprehensive evaluation information matrix.
The key steps are as follows:
(1) Based on Formulas (10)–(14), we can obtain the conflictual relationship of evaluation attributes.
then, the weight vector of evaluation attributes is calculated as .
(2) Based on Formulas (15)–(22) of heterogeneous weighted TOPSIS, we can obtain and , which are calculated as
Then, the conditional probabilities of the target are calculated as
(3) The adaptive risk avoidance coefficients can be calculated by Formula (24), expressed as
(4) Based on Formulas (25)–(27), the comprehensive loss function matrix of each target based on multi-attribute information is listed in Table 5.

Table 5.
Comprehensive loss function matrix.
(5) We can further calculate the decision thresholds based on Table 5 via Formulas (28) and (29). The results of each target are shown in Table 6.

Table 6.
Conditional probability and decision thresholds.
(6) From Table 6, we can obtain the ranking results based on conditional probability, i.e., . We can further obtain the classification results based on decision rules P(1)–N(1): and . They imply that we should attack or interfere with first and need more information to analyze , , and .
Here, the comparison of the proposed method with study [6] is shown in Figure 3. For comparison, the threat degree of our method is represented by and the threat degree from study [6] is converted to
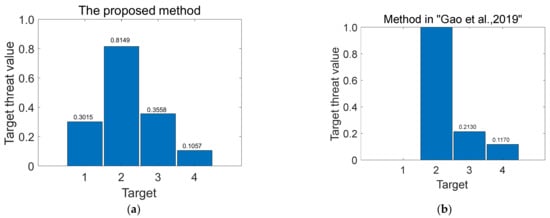
Figure 3.
The results of the proposed method (a) and method in [6] (b).
From Figure 3, we can see that the ranking results are basically the same. They all agree that and have the highest and second highest threat levels. For the difference between and , which is due to the difference in the calculation of attribute weights, this paper uses a data-based objective weighting method, whereas the AHP used in [6] is based on subjective judgement. The weight vector in [6] is .
In order to avoid the decision conflict caused by different methods, this paper introduces heterogeneous weighted TOPSIS into the multi-target threat assessment method, which can obtain the threat ranking along with the threat classification. With the above heterogeneous information processing, and are in the , which means that more information is needed to assess whether priority strikes or interference are required.
4.2. Analysis of Attribute Relevance
The attribute relevance is considered by the weight calculation and the aggregation of relative loss functions under multiple attributes, i.e., the heterogeneous CRITIC and weighted HM operators are used, respectively.
In order to analyze the advantages of the correlation processing, we compare the classification results of the proposed method with those methods without an HM operator, without CRITIC, etc. The specific methods are denoted and described as follows:
TH1: Instead of using the HM operator in our method, the weighted average operator is used.
TH2: Instead of using the HM operator and CRITIC in our method, the weighted average operator and equal weights are used.
TH3: Instead of using the HM operator and CRITIC in our method, the weighted average operator and weights from [6] are used.
TH4: Instead of using the CRITIC in our method, the weights from [6] are used.
The differences among these methods are listed in Table 7.

Table 7.
The differences among evaluation methods.
The conditional probability of targets under different methods is listed in Table 8.

Table 8.
The conditional probability.
The threat degree of TH1 is the same as the proposed method, and the threat degrees of TH2 and TH3 (TH4) are shown in Figure 4.
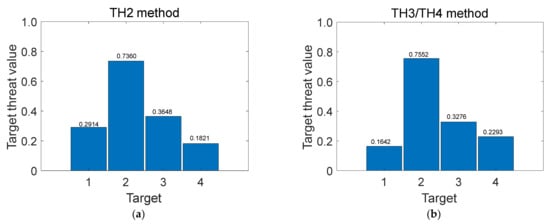
Figure 4.
The results of TH2 method (a) and TH3/TH4 method (b).
The comprehensive decision thresholds of different methods are listed in Table 9.

Table 9.
Comprehensive decision thresholds.
Accordingly, the , , and of different methods are listed in Table 10.

Table 10.
Decision domains of different methods.
In order to analyze the effectiveness of the attribute relevance, the above methods are discussed through the ranking results, the classification results, the relative magnitude of the threat degree of the target, and the relative magnitude of the decision domains. The ranking and classification results directly reflect the output of the methods. The relative magnitude of the threat degree of the targets can help analyze the reasonableness of target classification. The relative magnitude of the decision domains is obtained through the decision thresholds, representing the probability of classifying the target into this domain. For a target with a large threat degree, the larger the positive domain is, the more beneficial it is to divide it into the positive region, and the more reasonable it is.
More specifically, combining the analysis in Section 4.1 and the results in Table 9, we can see that
(1) and receive different ranking results under different decision-making methods; thus, they need more information to analyze. All the methods in Table 8 put them in the boundary domain. The results of the calculations are compatible with the theoretical analyses.
(2) From Figure 3 and Figure 4, in terms of the relative magnitude of the target’s threat degree, the relative difference between and , expressed as , is smaller than the relative difference between and , expressed as . When both and belong to the boundary domain, it is more reasonable that also belongs to the boundary domain. Therefore, the proposed method and the results of TH1 are more reasonable. The reason why their methods are more reasonable is that their attribute weights are calculated by heterogeneous CRITIC.
(3) The relative magnitudes of decision domains under different methods are shown in Figure 5. We can further compare the proposed method with the TH1 method, both of which use heterogeneous CRITIC. However, for , which has the significantly highest threat degree, the proposed method has a smaller boundary domain and a higher discrimination degree. This makes it easier to determine as the priority target in the proposed method. This effect is due to the further use of the HM operator in the proposed method.
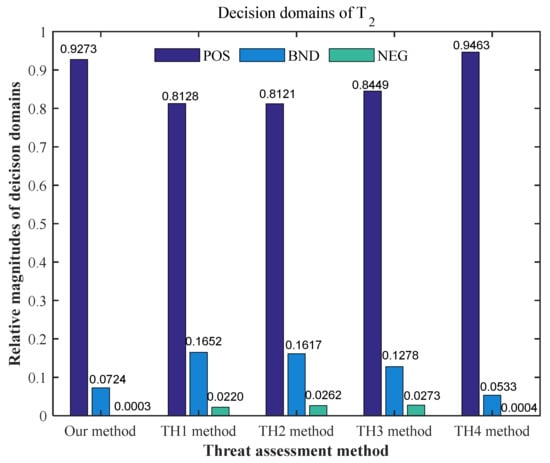
Figure 5.
The relative magnitude of decision domains of .
Combining the above analyses, the proposed method can achieve more reasonable three-way classification results by considering the attribute relevance.
4.3. Analysis of Risk Avoidance Coefficient
The risk avoidance coefficients are used in the construction of the relative loss function matrices. Compared with existing methods, this paper exploits adaptive risk avoidance coefficients, which can directly be calculated according to the uncertainty of the assessed values.
Based on the related content of Section 3.5, the adaptive risk avoidance coefficient curves via Formula (24) for different attributes are shown in Figure 6. Since the values of and are real numbers, we consider that there is no uncertainty. Thus, the curves in Figure 6 are only for , , , and .
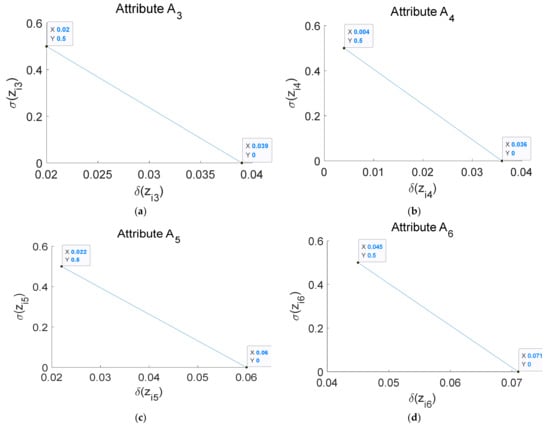
Figure 6.
Adaptive risk avoidance threshold curves of (a), (b), (c), and (d).
As we can see from Figure 6, the corresponding risk avoidance coefficients can be obtained directly based on the uncertainty of the assessed attribute values. Table 11 gives the comparison between the proposed method and the existing threat assessment methods on setting the risk avoidance coefficient.

Table 11.
The comparison among different methods.
It can be seen from Table 10 that, in the construction of risk avoidance coefficients, existing methods usually preset or subjectively set the risk avoidance coefficients. And for the convenience of calculation, they set the same coefficient for each evaluation value. This is not in line with the actual situation. Accordingly, the advantages of constructing it objectively in this paper are as follows:
(1) As mentioned in Remark 4, the risk avoidance coefficient reflects the acquisition of information. Each assessment attribute has a different source, and it is not reasonable to set its risk avoidance coefficient as the same value. We set it via the uncertainty of information, which is more in line with the reality.
(2) The risk avoidance coefficients are calculated directly and do not need to be set by a human. Timeliness and objectivity of target threat assessment can be guaranteed.
Remark 5.
The mainstream trend of multi-target three-way threat assessment methods is to construct a relative loss function matrix through risk avoidance coefficients and ultimately calculate decision thresholds. However, there are still some methods that do not use risk avoidance coefficients, such as subjectively constructing loss function matrices, which are not within the scope of discussion.
5. Conclusions
For the problem of multi-target threat assessment with heterogeneous information and attribute relevance, we propose a new multi-target three-way threat assessment method. First, the dynamic assessment information is represented by heterogenous forms. The comprehensive evaluation information matrix can be obtained by the normalization and aggregation. Based on the comprehensive evaluation information matrix, attribute weights are calculated by heterogeneous CRITIC. The conditional probability is calculated by the heterogeneous weighted TOPSIS. Then, the adaptive risk avoidance coefficients are constructed by the uncertainty of the assessment value, and the relative loss function matrices are constructed. Subsequently, the comprehensive loss function matrices are obtained by the weighted HM operator. The three-way decision rules are obtained via decision thresholds. The case study shows that the proposed method can effectively handle the heterogeneous information and attribute relevance, which is more suitable for the combat environment. Compared with existing methods, this study has the following features and benefits:
(1) It expands the research of three-way decision and target threat assessment. In particular, both the heterogeneity and the relevance of information have been considered in target threat assessment. This is rare in the study of existing multi-target threat assessment based on three-way decision. Therefore, this study is more in line with an actual combat mission environment.
(2) For the representation and processing of heterogeneous information, there is no loss of information. Neither the calculation of conditional probabilities by heterogeneous weighted TOPSIS nor the calculation of weights by heterogeneous CRICTIC involves the conversion of heterogeneous information formats. Whereas in some of the existing studies, the conversion of heterogeneous information into the same format may result in information loss.
(3) The treatment of attribute correlation is relatively comprehensive and includes both weight calculation and information aggregation. The proposed method considers the attribute relevance in terms of both in the weights’ calculation and in the aggregation of relative loss function matrices, which is rarely considered by the other three-way threat assessment methods. The consideration of attribute relevance makes the results of target threat classification more reasonable and credible.
(4) The adaptive risk avoidance coefficients can be calculated based on the uncertainty of the attribute information. Compared with other methods in which the risk avoidance coefficients are set subjectively, it is more reasonable and effective, and avoids subjective experience limitations. It can meet the timeliness need for a wartime decision.
However, despite the above-mentioned advantages, there are still some issues that need further investigation. First, the diversity of heterogeneous information representations deserves further study. For example, heterogeneous information is represented by linguistic variables, hesitant fuzzy numbers, etc. Second, when the decision makers are groups, how can the method of this paper be generalized to three-way group decision making [55]? Finally, adaptive risk aversion function curves can be optimized in conjunction with human psychological decision theories such as regret theory [56].
Author Contributions
Conceptualization, Methodology, Writing—original draft, Writing—review and editing, Y.G.; Investigation, N.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Project funded by China Postdoctoral Science Foundation (2021M693940).
Data Availability Statement
Data are contained within the article.
Acknowledgments
Support by colleagues and the university is acknowledged.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Lives, I.V.; Joseph, M.; Robbins, M.J.; Lunday, B.J. Solving nonstationary Markov decision processes via contextual decomposition: A military air battle management application. Eng. Appl. Artif. Intell. 2023, 233, 120949. [Google Scholar]
- Nalin, A.; Tripodi, P. Future warfare and responsibility management in the AI-based military decision-making process. J. Adv. Mil. Stud. 2023, 14, 83–97. [Google Scholar] [CrossRef]
- Li, Y.F.; Shi, J.P.; Jiang, W.; Zhang, W.G.; Lyu, Y.X. Autonomous maneuver decision-making for a UCAV in short-range aerial combat based on an MS-DDQN algorithm. Def. Technol. 2022, 18, 1697–1714. [Google Scholar] [CrossRef]
- Li, S.; He, X.Y.; Xu, X.; Zhao, T.; Song, C.Y.; Li, J.B. Weapon-target assignment strategy in joint combat decision-making based on multi-head deep reinforcement learning. IEEE Access 2023, 11, 113740–113751. [Google Scholar] [CrossRef]
- Barlas, M.A.; Gözde, H.; Özden, S. Modelling and optimization of UHF-band EW base WTA problem within the scope of threat assessment. Def. Sci. J. 2022, 72, 73–82. [Google Scholar] [CrossRef]
- Gao, Y.; Li, D.S. Consensus evaluation method of multi-ground-target threat for unmanned aerial vehicle swarm based on heterogeneous group decision making. Comput. Electr. Eng. 2019, 74, 223–232. [Google Scholar] [CrossRef]
- Li, S.Y.; Chen, M.; Wang, Y.H.; Wu, Q.X. Air combat decision-making of multiple UCAVs based on constraint strategy games. Def. Technol. 2022, 18, 368–383. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, Q.L.; Deng, X.Y.; Jiang, W. A multi-source information fusion method for ship target recognition based on Bayesian inference and evidence theory. J. Intell. Fuzzy Syst. 2022, 42, 2331–2346. [Google Scholar] [CrossRef]
- Luo, R.N.; Huang, S.C.; Zhao, Y.; Song, Y.F. Threat assessment method of low altitude slow small (LSS) targets based on information entropy and AHP. Entropy 2021, 23, 1292. [Google Scholar] [CrossRef]
- Ma, S.D.; Zhang, H.Z.; Yang, G.Q. Target threat level assessment based on cloud model under fuzzy and uncertain conditions air combat simulation. Aerosp. Sci. Technol. 2017, 67, 49–53. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, S.Y.; Niu, W. Threat assessment method based on intuitionistic fuzzy similarity measurement reasoning with orientation. China Commun. 2014, 6, 119–128. [Google Scholar]
- Yu, X.J.; Wei, S.; Fang, Y.Y.; Sheng, J.L.; Zhang, L. Low altitude slow small target threat assessment algorithm by exploiting sequential multifeatured with long short-term memory. IEEE Sens. J. 2023, 23, 21524–21533. [Google Scholar] [CrossRef]
- Fan, C.; Fu, Q.; Song, Y.; Lu, Y.; Li, W.; Zhu, X. A newmodel of interval-valued intuitionistic fuzzy weighted operators and their application in dynamic fusion target threat assessment. Entropy 2022, 24, 1825. [Google Scholar] [CrossRef] [PubMed]
- Zhao, R.J.; Yang, F.B.; Ji, L.N. An extended fuzzy CPT-TODIM model based on possibility theory and its application to air target dynamic threat assessment. IEEE Access 2022, 10, 21655–21669. [Google Scholar] [CrossRef]
- Kong, D.P.; Chang, T.Q.; Wang, Q.D. A threat assessment method of group targets based on interval-valued intuitionistic fuzzy multi-attribute group decision-making. Appl. Soft. Comput. 2018, 67, 350–369. [Google Scholar] [CrossRef]
- Zhang, Q.; Hu, J.H.; Feng, J.F. Air multi-target threat assessment method based on improved GGIFSS. J. Intell. Fuzzy Syst. 2019, 36, 4127–4139. [Google Scholar]
- Zhang, K.; Kong, W.R.; Liu, P.P. Assessment and sequencing of air target threat based on intuitionistic fuzzy entropy and dynamic VIKOR. J. Syst. Eng. Electron. 2018, 29, 305–310. [Google Scholar] [CrossRef]
- Yao, Y.Y. The Dao of three-way decision and three-world thinking. Int. J. Approx. Reason. 2023, 162, 109032. [Google Scholar] [CrossRef]
- Zhang, C.; Zhang, M.; Yang, G.; Xue, T.; Zhang, Z.; Liu, L.; Wang, L.; Hou, W.; Chen, Z. Three-way selection random forest optimization model for anomaly traffic Detection. Electronics 2023, 12, 1788. [Google Scholar] [CrossRef]
- Chen, X.; Zou, L. Three-way decision models based on ideal relations in multi-attribute decision-making. Entropy 2022, 24, 986. [Google Scholar] [CrossRef] [PubMed]
- Wang, H.; Cui, Z.W.; Liu, R.G.; Fang, L.; Sha, Y. A multi-type transferable method for missing link prediction in Heterogeneous social networks. IEEE Trans. Knowl. Data Eng. 2023, 35, 10981. [Google Scholar] [CrossRef]
- Song, J.K.; He, Z.G.; Jiang, L.N.; Liu, Z.C.; Leng, X.L. Research on hybrid multi-attribute three-way group decision making based on improved VIKOR model. Mathematics 2022, 10, 2783. [Google Scholar] [CrossRef]
- Jia, F.; Wang, Y.; Su, Y. GRA-based dynamic hybrid multi-attribute decision-making for the performance evaluation of elderly-care services. Mathematics 2023, 11, 3176. [Google Scholar] [CrossRef]
- Ali, A.; Rehman, N.; Ali, M.; Hila, K. A novel approach to three-way decision model under fuzzy soft dominance degree relations and emergency situation. Expert Syst. Appl. 2024, 239, 122369. [Google Scholar] [CrossRef]
- Blundo, C.; Loia, V.; Orciuoli, F. A time-aware approach for MOOC dropout prediction based on rule induction and sequential three-way decisions. IEEE Access 2023, 11, 113189–113198. [Google Scholar] [CrossRef]
- Gao, Y.; Li, D.S.; Zhong, H. A novel target threat assessment method based on three-way decisions under intuitionistic fuzzy multi-attribute decision making environment. Eng. Appl. Artif. Intell. 2020, 87, 103276. [Google Scholar] [CrossRef]
- Gao, Y.; Huang, Y.C.; Cheng, G.B.; Duan, L. Multi-target threat assessment method based on VIKOR and three-way decisions under intuitionistic fuzzy information. Acta Electron. Sin. 2021, 49, 542–549. [Google Scholar]
- Yin, T.F.; Zhang, R.T.; Su, Q.R. Threat assessment of aerial targets based on improved GRA-TOPSIS method and three-way decisions. Math. Biosci. Eng. 2023, 20, 13250–13266. [Google Scholar] [CrossRef] [PubMed]
- Li, B.; Tian, L.Y.; Han, Y.; Chen, D.Q. Three-way decision of target threat decision making based on adaptive threshold algorithms. J. Eng. 2020, 13, 293–297. [Google Scholar] [CrossRef]
- Li, W.H.; Gao, P.X.; Chen, J.; Lu, Y.Q. Unmanned aerial vehicle situation assessment based on cumulative prospect theory and three-way decision. J. ShangHai Jiao Tong Univ. 2022, 56, 1479–1490. [Google Scholar]
- Li, T.C.; Ye, J.; Lu, K. Air combat threat assessment based on improved three-way decision-Topsis method. J. Gun Launch Control 2022, 43, 1–8, 20. [Google Scholar]
- Peng, L.; Zhang, T.; Zhang, X. Threat assessment for aerial targets based on three-way multi-criteria decision making. In Proceedings of the 2021 IEEE International Conference on Networking, Sensing and Control (ICNSC), Xiamen, China, 3–5 December 2021; Volume 1, pp. 1–6. [Google Scholar]
- Tan, R.P.; Zhang, W.D.; Yang, L.H. Decision-making method based on set pair analysis and VIKOR under heterogeneous information environment and application to typhoon disaster assessment. Soft. Comput. 2023, 27, 8289–8314. [Google Scholar] [CrossRef]
- Wu, J.M.; Huang, Z.H.; Li, J.J.; Liu, D.Y. Three-way multi-attribute decision-making with multiple decision makers in heterogeneous incomplete decision systems. J. Amb. Intel. Hum. Com. 2023, 14, 7469–7483. [Google Scholar] [CrossRef]
- Liang, D.C.; Wang, M.W.; Xu, Z.S. Heterogeneous multi-attribute nonadditivity fusion for behavioral three-way decisions in interval type-2 fuzzy environment. Inf. Sci. 2019, 496, 242–263. [Google Scholar] [CrossRef]
- Li, G.; Kcou, G.; Peng, Y. A group decision making model for integrating heterogeneous information. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 982–992. [Google Scholar] [CrossRef]
- Mondal, A.; Roy, S.K. Behavioural three-way decision making with Fermatean fuzzy Mahalanobis distance: Application to the supply chain management problems. Appl. Soft Comput. 2024, 151, 111182. [Google Scholar] [CrossRef]
- Modal, A.; Roy, S.K.; Deveci, M. Regret-based domination and prospect-based scoring in three-way decision making using q-rung orthopair fuzzy Mahalanobis distance. Artif. Intell. Rev. 2023, 56, S2311–S2348. [Google Scholar] [CrossRef]
- Diakoulaki, D.; Mavrotas, G.; Papayannakis, L. Determining objective weights in multiple criteria problems: The CRITIC method. Comput. Oper. Res. 1995, 22, 763–770. [Google Scholar] [CrossRef]
- Kumar, K.; Chen, S.M. Multi-attribute decision making based on q-ring orthopair fuzzy Yager prioritized weighted arithmetic aggregation operator of q-rung orthopair fuzzy numbers. Inf. Sci. 2024, 657, 119984. [Google Scholar] [CrossRef]
- Chakraborty, S. TOPSIS and modified TOPSIS: A comprehensive analysis. Decis. Anal. J. 2022, 2, 100021. [Google Scholar] [CrossRef]
- Zhu, G.N.; Ma, J.; Hu, J. A fuzzy rough number extended AHP and VIKOR for failure mode and effects analysis under uncertainty. Adv. Eng. Inform. 2022, 51, 101454. [Google Scholar] [CrossRef]
- Qin, H.W.; Peng, Q.W.; Ma, X.Q. A novel interval-valued Fermatean fuzzy three-way decision making method with probability dominance relations. Expert Syst. Appl. 2024, 242, 122727. [Google Scholar] [CrossRef]
- Ye, J.; Sun, B.Z.; Bai, J.C.; Bao, Q.; Chu, X.L.; Bao, K. A preference-approval structure-based non-additive three-way group consensus decision-making approach for medical diagnosis. Inform. Fusion 2024, 101, 102008. [Google Scholar] [CrossRef]
- Xu, T.; Luo, F. Interval-value based movement strategy of three-way decisions. Inform. Sci. 2024, 652, 119761. [Google Scholar] [CrossRef]
- Yang, X.; Li, Y.H.; Li, T.R. A review of sequential three-way decision and multi-granularity learning. Int. J. Approx. Reason. 2023, 152, 414–433. [Google Scholar] [CrossRef]
- Yin, L.J.; Zhang, Q.H.; Zhao, F.; Liu, D.; Wang, G.Y. Superiority of three-way decisions from the perspective of probability. Artif. Intell. Rev. 2023, 56, 1263–1295. [Google Scholar] [CrossRef]
- Yang, Y.Y. Three-way decision: An interpretation of rules in rough set theory. Rough Sets Knowl. Technol. 2009, 5589, 642–649. [Google Scholar]
- Liang, D.C.; Xu, Z.S.; Liu, D. Method for three-way decisions using ideal TOPSIS solutions at Pythagorean fuzzy information. Inf. Sci. 2018, 435, 282–295. [Google Scholar] [CrossRef]
- Jia, F.; Liu, P.D. A novel three-way decision model under multiple-criteria environment. Inf. Sci. 2019, 471, 29–51. [Google Scholar] [CrossRef]
- Jia, F.; Liu, P.D. Multi-attribute three-way decisions based on ideal solutions under interval-valued intuitionistic fuzzy environment. Int. J. Approx. Reason. 2021, 138, 12–37. [Google Scholar] [CrossRef]
- Modal, A.; Roy, S.K.; Pamucar, D. Regret-based three-way decision making with possibility dominance and SPA theory in incomplete information system. Expert Syst. Appl. 2023, 211, 118688. [Google Scholar] [CrossRef]
- He, X.; Chang, J.; Liu, W. Harmonic averaging operators of four parameters interval numbers and applications to decision making. Fuzzy Syst. Math. 2017, 31, 135–143. [Google Scholar]
- Gao, Y.; Li, D.S. UAV swarm cooperative situation perception consensus evaluation method based on three-parameter interval number and Heronian mean operator. IEEE Access 2018, 6, 73328–73340. [Google Scholar] [CrossRef]
- Modal, A.; Roy, S.K.; Zhan, J.M. A reliability-based consensus model and regret theory-based selection process for linguistic hesitant-Z multi-attribute group decision making. Expert Syst. Appl. 2023, 228, 120431. [Google Scholar] [CrossRef]
- Lei, W.J.; Ma, W.M.; Li, X.N.; Sun, B.Z. Three-way group decision based on regret theory under dual hesitant fuzzy environment: An application in water supply alternatives selection. Expert Syst. Appl. 2024, 237, 121249. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).