Abstract
Secret image sharing is a hot issue in the research field of data hiding schemes for digital images. This paper proposes a general threshold secret image sharing scheme, which distributes secret data into meaningful image shadows based on a non-full rank linear model. The image shadows are indistinguishable from their corresponding distinct cover images. Any combination of the shares can perfectly restore the secret data. In the proposed scheme, the integer parameters , with , can be set arbitrarily to meet the application requirement. The experimental results demonstrate the applicability of the proposed general scheme. The embedding capacity, the visual quality of image shadows, and the security level are satisfactory.
1. Introduction
With the rapid development of portable devices and wireless communication, a huge amount of information is transmitted via the Internet in daily life. To protect the security of private information, encryption techniques are applied [1,2], which transform the private data into a meaningless ciphertext with a secret key. However, the meaningless ciphertext may arouse the eavesdropper’s suspicion. Researchers turn to develop some techniques which hide private data into meaningful media such as digital images or videos. The technique of embedding secret data in a digital cover image to produce a stego image is called image steganography. Conventional methods for image steganography include the least significant bits (LSB) substitution [3], the exploiting modifying direction (EMD) method [4], the difference expansion (DE) [5], the histogram shifting (HS) [6], and some other approaches [7,8]. The secret data are transmitted under the cover of a meaningful digital image, without attracting the eavesdropper’s suspicion.
The current image steganography techniques suffer from a problem that the stego images are vulnerable to tampering attack. Slight changes to a stego image may completely disrupt the decryption result. To improve the flexibility of decryption, in 1995, Naro and Shamir [9] proposed the visual secret sharing (VSS), also called visual cryptography, in which they encrypted a secret image into n shares and recovered the secret image through stacking not less than t shares. Later, many improved versions of visual secret sharing were proposed [10,11,12,13]. The main weakness of such schemes is the low quality of the restored secret image.
As a result, a series of secret image sharing schemes was proposed [14,15,16,17,18,19] that used mathematical computation to recover the secret image instead of stacking. A common approach is to apply the polynomial-based secret sharing scheme. In a (k, n) polynomial-based secret image sharing scheme, the dealer divides a pixel or a pixel block of the secret image into n shadows via a polynomial function. In such schemes, we can consider that the secret image is encrypted with polynomial-based secret sharing into n noise-like images. Due to the continuous feature of a polynomial, the reconstructed secret image is distorted by numerical errors.
Another series of secret image sharing schemes focusing on sharing secret into multiple image shadows were proposed [20,21,22]. The image shadows are indistinguishable from the cover images and the secret can be perfectly recovered. In 2007, Chang et al. [20] introduced the first version of such schemes. The secret message is transmitted through two meaningful image shadows, and it can be recovered only when both image shadows are obtained. Although these schemes distribute the secret data into multiple image shadows, all shadows are required in the secret extraction phase.
Some works on -threshold secret image sharing have been proposed [23,24,25,26], in which the secret data can be completely recovered by no less than shares. However, shadow images are vulnerable to the steganalysis because they are generated based on the same cover image. Recently, some secret image sharing schemes using different meaningful cover images have been proposed [27,28]. In these methods, is a fixed pair of predefined constants.
The motivation of this research is to find a general secret image sharing scheme, in which parameters with can be arbitrarily chosen according to different application requirements, and the distinct cover images can be arbitrarily assigned too. We first present a -threshold secret sharing scheme based on a non-full rank linear model. A secret segment of entries is used to generate a solution vector of entries. By using any combination of entries from the solution vector, the complete solution vector can be recovered and the secret segment can be restored.
Then, this scheme is applied to a digital image transmission system. In the first step, the secret data is divided into secret vectors too. Then, the solution vectors are generated in the same way as the proposed secret sharing scheme. To implement it on the image transmission system, each solution vector is further applied to modulate a vector constituted by pixel values collected from different cover images. In the final step, the resulting modulated vector is recorded to the image shadows. In the recovery phase, only a predefined number of shadows are required to restore the complete secret.
The remainder of this paper is organized as follows. In Section 2, we introduce the secret sharing scheme based on a non-full rank linear model. The proposed -threshold secret image sharing scheme is described in Section 3. The experimental results and theoretic analysis are given in Section 4. Finally, we conclude this paper in Section 5.
2. -Threshold Secret Sharing Scheme Based on Non-Full Rank Linear Model
In this section, we first discuss the solution of a non-full rank linear model over a finite integer field. Then, an application of recovering a solution vector with missing entries is introduced. Based on this mathematical model, we propose a generalized -threshold secret sharing scheme based on a non-full rank linear model.
2.1. Non-Full Rank Linear Model over a Finite Integer Field
Assume is a prime number, is a field of integers modulo ; and are two positive integers with . The equations are linearly independent equations of n variables over the field , which are formulated as
Let
Then, the solution space of the linear equations Equation (1) is given by
This system of linear equations can also be written in matrix form as
According to linear algebra, a system of linearly independent equations with variables , a unique solution vector can be determined. The current non-full rank system of linearly independent equations leads to a solution space of rank .
We can manipulate the augmented matrix by using elementary row operations over field to obtain the simplest row form as
Then, we obtain an equivalent system of linearly independent equations
Let be a particular solution for Equation (6). To solve the unknown entries, we substitute into Equation (6) and obtain
To solve a set of linearly independent homogeneous solutions of Equation (6), let the homogeneous solutions be
To solve the unknown entries of each solution , we can substitute them into the homogeneous equation that corresponds to Equation (6) and obtain
The solution space can be defined by using the homogeneous and particular solutions as
Suppose a particular solution vector with missing entries is given, where entries of a solution are missing. We can recover the missing entries by the following procedures.
Without the loss of generality, let us assume the available entries are the first entries. We first manipulate the original augmented matrix with elementary row operations into the following form
Then, the missing entries can be obtained by
Each solution vector can be represented as
By substituting the obtained particular and homogeneous solutions into Equation (13), we can get
By expanding the last rows, we can also get the coefficients of the given vector .
From the above analysis, Equations (5)–(7) give the solution steps to obtain a particular solution, and Equations (8) and (9) give the solution steps to obtain a set of linearly independent homogeneous solutions. Thus, any solution vector of the given linearly independent equations of n variables can be represented with a linear combination of homogeneous and particular solutions as Equation (10). In addition, Equations (11) and (12) give the solution steps to recover the missing entries of a solution vector from available entries; Equations (13)–(15) give a one-to-one mapping between a solution vector and the coefficients of the linear combination. Based on this model, suppose coefficients are the secret, we can produce a vector , which includes secret shares, using Equation (13). When shares among are available, we can restore the remaining shares and calculate the secret from the restored complete set of shares.
2.2. . -Threshold Secret Sharing Scheme Based on the Non-Full Rank Linear Model
A general scheme for threshold secret sharing based on a non-full rank linear model is proposed in this section. It is divided into three phases: the setup, the share generation, and the secret extraction with authentication.
2.2.1. Setup
The scenario is that a dealer embeds secret data S into n shares and distributes them to n participants. To recover secret data, at least k participants should cooperate by providing their shares. The dealer first selects linearly independent equations with variables over the field as
Then, a set of linearly independent homogeneous solutions and a particular solution can be obtained by applying Equations (5)–(9).
2.2.2. Share Generation
The secret data S to be shared is divided into secret segments of k entries denoted by , where . For each secret message segment , a solution vector can be generated by
where is a series of integers over generated by a pre-shared data hiding key. This integer series encrypt each secret entry by adding a random offset. By rearranging the collection of synthesized vectors (), the dealer generates secret shares as
where denotes the -th entry of the -th synthesized vector . Finally, these shares are distributed to the participants.
2.2.3. Secret Extraction with Authentication
Suppose k faithful participants provide their shares as . The combiner first rearranges the k shares into vectors as
where denotes the -th entry of the -th share. Then, the vector with missing entries can be restored into the complete solution by using Equations (11) and (12).
To extract secret data, the combiner first reproduces the random sequence by the shared data hiding key. Then, the secret segments can be extracted by substituting the complete solution vectors back into Equation (17), as
By expanding the last rows, we can get the secret segments
When additional doubtful shares are available, they can be authenticated by using the restored missing entries based on the trustworthy shares.
2.3. Demonstration
Let us assume , , and . That is, we are going to demonstrate a (2,4)-threshold secret sharing scheme. The dealer selects two linearly independent equations with four variables, as
That is, and .
2.3.1. Particular and Homogeneous Solutions
Manipulate the augmented matrix with elementary row operations (see Appendix A) over the field Zp to obtain a row simplest augmented matrix as
Then, by applying Equation (7), we can get a particular solution . By applying Equations (8) and (9), we can get a set of linearly independent homogeneous solutions
2.3.2. Share Generation
For each secret segment , the solution vector can be generated by
Let the secret data be , and the random integer series generated by the data hiding key be , , then the generated vectors are
The dealer rearranges the vector entries into secret shares and distributes them to the participants.
2.3.3. Authentication
At the combiner side, suppose that only shares and are trustworthy, while and are doubtful. The combiner can reproduce the remaining shares and restore the secret data by using the faithful ones. He/she first manipulates by using elementary row operations, so that the submatrix constituted by column 3 and 4 becomes an identity matrix as
Then, the combiner rearranges the available entries into , , and . Finally, these vectors with missing entries are substituted into Equation (31) as
Therefore, the complete solution vectors are , , , and the remaining shares should be , . If a share provided by a suspicious participant does not match the result, then he/she is a cheater.
2.3.4. Secret Recovery
To restore secret data, the combiner first manipulates the given linear equations to obtain the particular and homogeneous solutions as the share generation phase. Thus, the solution vectors should be
Therefore, the secret segments can be obtained by substituting the restored shares and the integer series generated by the shared data hiding key into the last two rows of Equation (35), as
The recovered secret segments are , which are the same as embedded.
3. -Threshold Secret Image Sharing Scheme Based on Linear Model
In this section, the -threshold secret sharing scheme discussed above is applied to the platform of digital image transmission. By using the proposed secret sharing scheme, we can hide secret data in three distinct meaningful images and produce three shadows with imperceptible changes. While the shadow images are transmitted to different participants, the secret data can be recovered only if more than participants share their shadows. We present our scheme with the following subsections: system overview, setup, shadow image generation, secret data extraction with authentication, and a demonstration.
3.1. System Overview
The flowchart of the proposed scheme is shown in Figure 1. In the proposed scheme, secret data are converted into a sequence of -ary digits first. Then, this sequence is divided into segments denoted by , where is the total number of secret segments. We randomly choose distinct meaningful cover images with size . A vector sequence is produced from the cover images and denoted by , where each vector is a collection of pixel values retrieved from corresponding positions of the images. To embed secret data, we apply the proposed -threshold secret sharing scheme to generate a vector of digits using a secret segment of digits. After all secret segments are converted, the resulting vector sequence is applied to modulate and obtain the sequence , correspondingly. Finally, the secret image shadows are generated by distributing the modulated sequence back into meaningful images sized . In the secret data recovery phase, at least trustworthy shadows should be available. These shadows are rearranged into a vector sequence with missing entries . Then, a sequence of vectors with missing entries are demodulated. The missing entries can be recovered by using Equations (11) and (12). If there are suspicious participants, the one who provides a share that mismatches the reproduced shadow is a cheater. Finally, the secret data can be recovered using Equations (20) and (21).
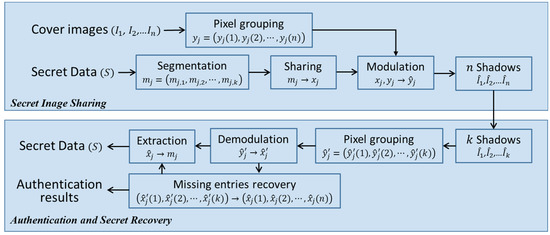
Figure 1.
Flowchart of the proposed scheme.
3.2. Setup
The dealer decides the number of the participants , the threshold, and the prime number . He/she selects linearly independent equations of variables over the field
We can rewrite them in matrix form as
Find a set of linearly independent homogeneous solutions and a particular solution by applying Equations (5)–(9).
3.3. Shadow Image Generation
Let us assume that the secret data to be embedded are denoted as and the distinct meaningful cover images with size are denoted as ,,,. The shadow images can be generated by the following steps.
Step 1. Rearrange the cover images ,,, into vector sequence as
Step 2. Convert the secret data stream into a sequence of -ary digits and divide them into segments denoted by , where is the total number of secret segments.
Step 3. Apply to generate vectors using Equation (17). Compute the residual vectors of by
Compute the stego vector sequence by
When overflow/underflow is encountered, do
Append the rest of the unmodulated vectors to constitute
Step 4. Distribute the modulated sequence back into meaningful shadow images sized .
3.4. Secret Data Extraction with Authentication
Suppose the meaningful shadow images sized are transmitted to participants and now faithful participants provide their shadow images to a combiner. The combiner can recover secret data and authenticate the rest shadows by the following steps. Without loss of generality, let us suppose that the trustworthy shadows are .
Step 1. Convert shadow images into vectors of -tuples as
Step 2. Compute the residual vectors
Step 3. Substitute each vector into Equations (11) and (12), the missing entries can be recovered to obtain its corresponding complete solution vector .
Step 4. Convert a doubtful shadow into sequence Then, compute its residual sequence If the authentication is passed; else, it is a tampered shadow.
Step 5. Extract the secret data by applying l to Equation (21).
3.5. Demonstration
We use the example model given in Section 2.3 to demonstrate how the proposed secret sharing scheme can be applied to image transmission applications. That is, , , , and the two linearly independent equations with four variables are
As analyzed in Section 2.3.1, and are two linearly independent homogeneous solutions, and is a particular solution.
Assume that and are two 5-ary secret segments, and the four cover images are , , , and . Two random segments and are generated by the data hiding key.
For the secret segments and , we generate their corresponding solution vectors by using Equation (17) and obtain
The residual vectors are
Then, the stego vectors are
Finally, the four shadow images are
The shares are distributed to the four participants, respectively.
If a combiner obtains trustworthy shadow images and , he/she first calculates the residual vectors as
Then, the missing entries can be recovered using Equations (11,12). For the current case, manipulations are demonstrated in Equation (31) as
To extract secret data, the random segments and are generated by the shared data hiding key first. The secret data can be extracted using Equation (21) as
4. Experimental Results and Discussions
In this section, we use two secret image sharing schemes with different combinations of values to demonstrate the applicability of the proposed approach. Performance evaluation based on the embedding capacity and the visual quality of image shadows are given. The security level of the proposed scheme is also analyzed.
4.1. Demonstration of Applicability
In this subsection, we implement a (2,4)-threshold and a (3,5)-threshold secret image sharing schemes to verify the applicability and the generalizability of the proposed approach.
4.1.1. (2,4)-Threshold Secret Image Sharing Scheme
In our first implementation, the parameter settings are , , , and the two linearly independent equations given in Equation (47) are applied. The secret data are assumed to be a secret image, as shown in Figure 2a, which is a grayscale image sized . The four distinct cover images are shown in Figure 2b–e, which are all grayscale images sized . All pixel values in our experiments are recorded in eight bits.
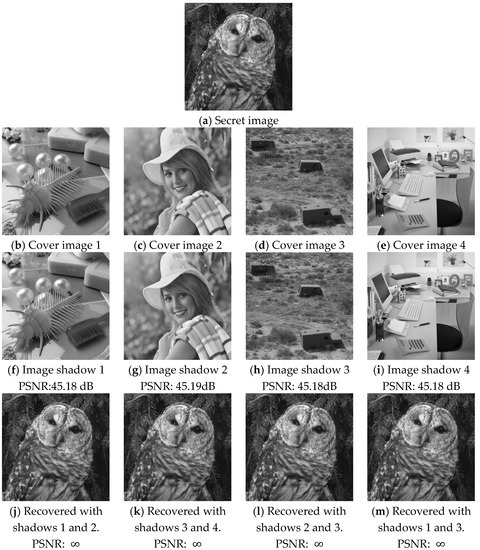
Figure 2.
The experimental results of the (2,4)-threshold secret image sharing.
To fit the parameter settings, the pixels of the secret image are divided into groups of four pixels each. Thirty-two bits of each pixel group are converted into fourteen 5-ary digits and then grouped into seven secret segments of two digits. Each secret segment is applied to generate a solution vector of four entries and used to modulate four cover pixels. Therefore, four pixel-values of the secret image are distributed in fourteen pixels for each cover image. The generated image shadows are shown in Figure 2f–i. The changes with respect to their corresponding cover images are imperceptible. The peak-signal-to-noise-ratio (PSNR) given below the figures is defined by
where denotes the mean-square-error between the cover image and the shadow image defined by
The recovered secret images by using different combinations of image shadow pairs are given in Figure 2j–m. In all cases, the secret image can be perfectly recovered.
4.1.2. (3,5)-Threshold Secret Image Sharing Scheme
In our second implementation, the parameter settings are , , and , and the two linearly independent equations are given by
The solution space of and over is formulated as
where , , . Then, solution vector generation function is given by
The secret image sized is given in Figure 3a; the five distinct cover images sized are given in Figure 3b–f. To fit the parameter settings, pixels of the secret image are divided into groups of six pixels each. Forty-eight bits of each pixel group are converted into twenty-one 5-ary digits, and then grouped into seven secret segments of three digits. Each secret segment is applied to generate a solution vector of five entries and is used to modulate five cover pixels. Therefore, six pixel-values of the secret image are distributed in thirty-five pixels for each cover image. The generated image shadows are shown in Figure 3g–k. The changes with respect to their corresponding cover images are again imperceptible. The recovered secret images using different combinations of image shadows are given in Figure 3l–p. In all cases, the secret image can be perfectly recovered.

Figure 3.
The experimental results of the (3,5)-threshold secret image sharing.
4.2. Performance Evaluation
In our threshold secret image sharing scheme, digits of -ary numbers are embedded in pixels of each image shadow. The embedding capacity (EC) can therefore be measured in bits per pixel (bpp) of an image shadow by
When the total number of shares increases, the total amount of image shadows to be transmitted also increases. However, an increase in the number of shares can improve the flexibility of secret recovery. Recall that any shares among the shadows can perfectly recover the secret.
For each cover pixel, Equation (43) always modulates the pixel value with an integer deviation within the range of . Suppose the deviation value is randomly distributed, the mean-square-error of modulation distortion can be estimated by
When the pixels of a cover image are not fully exploited to embed secret data, we define the payload ratio as
where and denote the number of pixels exploited and the number of total pixels, respectively. For the two schemes implemented in Section 4.1, the payload ratios can be calculated by
Under the payload ratio , the mean-square-error is proportionally corrected to . Thus, the expected PNSR value of an image shadow with a payload ratio is given by
The expected PSNR values with respect to different payload ratios and prime numbers are listed in Table 1. The corresponding evolution curves are plotted in Figure 4, where the curves for four different prime numbers are given. According to the theoretic analysis, the expected PSNR values of the two implemented cases are 45.1889 dB and 45.1290 dB, respectively, which sharply coincide with our experimental values.

Table 1.
The expected PSNR value (dB) with specific ratio,
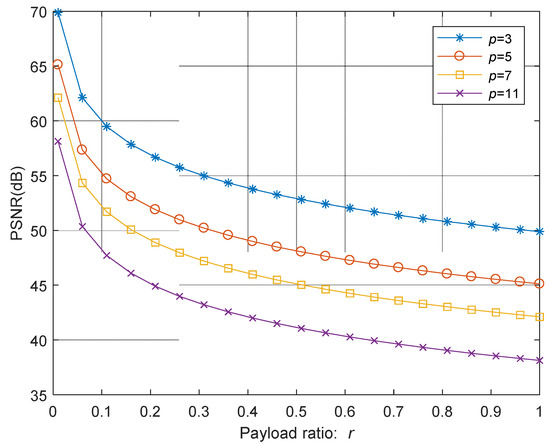
Figure 4.
The expected PSNR value of an image shadow with respect to the payload ratio.
4.3. Security Analysis
Various steganalysis techniques [29,30,31,32] have been proposed to detect the existence of secret information in a digital image. The general idea of steganalysis is to detect the abnormal statistical feature of a doubtful image. However, there are various types of data hiding methods for images. To successfully detect the embedding of secret, special steganalysis techniques are devised to deal with each target steganography. For example, the RS steganalysis [29] is applied to detect the LSB substitution. For data hiding in encrypted images, people usually use pixel value entropy or gray level histogram to analyze the existence of a secret message.
The data hiding method of the proposed secret sharing scheme is essentially based on the modulus function. Two steganalysis tools, relative entropy [30] and pixel-value differencing [31,32], are suitable for testing the security level of our scheme. The first tool is the relative entropy proposed by Cachin [30]. To measure the difference between cover image and image shadow , we accumulate their probability distributions and , respectively. Then, their relative entropy is calculated by
If , by definition, the data hiding scheme is -secure against passive attacking. A smaller value of means a better security level. We apply the relative entropy measure to our (3,5)-threshold secret image sharing scheme with . The experimental results are listed in Table 2, where the relative entropy values for half embedded and fully embedded cases are given. All values listed in the table are very close to zero, which implies the image shadows of the proposed scheme are robust under a passive attack.

Table 2.
Relative entropy values under half embedded and fully embedded cases.
The second steganalysis applied is the pixel-value differencing analysis [31,32]. The neighboring pixel-values of a natural image are highly continuous. The continuity is disrupted by most data hiding schemes. If the pixel-value differencing histogram (PDH) of an image is unusually flat, it is highly doubtful. To investigate the security level of the proposed scheme, we apply the PDH analysis to a set of five image shadows produced by our (3,5)-threshold secret image sharing scheme with . The secret image given in Figure 5a is embedded into five distinct cover images. The PDHs of the five pairs of cover images and their corresponding image shadows are plotted in Figure 5b–f. The PDH curves of image shadows are very close to their corresponding cover images, which indicates the proposed scheme is secure under PDH steganalysis.
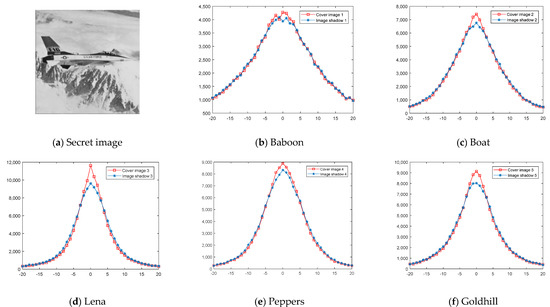
Figure 5.
The PVD histogram analysis between the cover images and image shadows.
5. Conclusions
In this paper, we propose a general -threshold secret image sharing scheme with meaningful image shadows. We first present a -theshold secret sharing scheme based on a non-full rank linear model. It is then applied to the platform of image transmission system. Using secret shares to modulate distinct cover images, we can produce image shadows. A combiner can completely recover the secret message by collecting at least image shadows.
To demonstrate the applicability to any combination of parameter values, we use two example models (2,4) and (3,5) to demonstrate our scheme. Experimental results confirm the applicability of the proposed scheme. Moreover, the embedding capacity and visual quality of image shadows are satisfactory. Embedding capacity and theoretic image quality under different parameter settings are also analyzed. Finally, we use two steganalysis tools to show the security level of our scheme.
The proposed scheme is based on the pixel-value modification in the spatial domain, which is suitable for digital images of a bitmap format. Our future work will focus on the implementation of the general secret sharing scheme to different cover media, such as JPEG images, encrypted images, and QR code images, which are more commonly applied in Internet applications.
Author Contributions
Conceptualization, J.-H.H. and C.-C.C.; methodology, S.-S.C.; software, S.-S.C.; validation, J.-H.H., S.-S.C. and C.-C.C.; formal analysis, S.-S.C. and J.-H.H.; investigation, S.-S.C.; resource, C.-C.C.; data curation, S.-S.C.; writing—original draft preparation, S.-S.C.; writing—review and editing, J.-H.H. and S.-S.C.; visualization, J.-H.H., S.-S.C. and C.-C.C.; supervision, C.-C.C.; project administration, C.-C.C.; funding acquisition, J.-H.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Science and Technology of Taiwan, grant number MOST 110-2221-E-507-003.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
The elementary row operations over the field include row switching, row multiplication, and row addition as in conventional linear algebra, except that each resulting integer number should be modulated by as
For the addition operation, if and , then ; for the multiplication operation, if and , then . Next, we use the derivation of Equation (23) in Section 2.3.1 to demonstrate the details of the elementary row operations. The two linearly independent equations are
That is, and . The corresponding augmented matrix is
To transfer the first two columns into an identity matrix, first multiply row 1 by 3 and add to row 2 as
where above the operation arrow denotes the operation detail. Then, scale row 2 by 2 as
Finally, multiply row 2 by 2 and add to row 1 as
Thus, the final row simplest augmented matrix over the field is
References
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Zhu, Z.L.; Zhang, W.; Wong, K.W.; Yu, H. A chaos-based symmetric image encryption scheme using a bit-level permutation. Inf. Sci. 2011, 181, 1171–1186. [Google Scholar] [CrossRef]
- Chan, K.C.; Cheng, L.M. Hiding data in images by simple LSB substitution. Pattern Recognit. 2004, 37, 469–474. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, S. Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett. 2006, 10, 781–783. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef] [Green Version]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–361. [Google Scholar] [CrossRef]
- Chang, C.C. Neural Reversible steganography with long short-term memory. Secur. Commun. Netw. 2021, 2021, 5580272. [Google Scholar] [CrossRef]
- Chang, C.C.; Li, C.T.; Shi, Y.Q. Privacy-Aware reversible watermarking in cloud computing environments. IEEE Access 2018, 6, 70720–70733. [Google Scholar] [CrossRef]
- Naor, M.; Shamir, A. Visual cryptography. Lect. Notes Comput. Sci. 1995, 950, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Nakajima, M.; Yamaguchi, Y. Extended visual cryptography for natural images. WSCG 2002, 10, 303–310. [Google Scholar] [CrossRef]
- Patil, S.; Rao, J. Extended visual cryptography for color shares using random number generators. Int. J. Adv. Res. Comput. Commun. Eng. 2012, 1, 399–410. [Google Scholar]
- Blundo, C.; De Santis, A.; Naor, M. Visual cryptography for grey level images. Inf. Process. Lett. 2000, 75, 255–259. [Google Scholar] [CrossRef]
- Liu, Z.; Zhu, G.; Wang, Y.G.; Yang, J.; Kwong, S. A Novel (t, s, k, n)-Threshold Visual Secret Sharing Scheme Based on Access Structure Partition. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 16, 1–21. [Google Scholar] [CrossRef]
- Ulutas, M.; Ulutas, G.; Nabiyev, V.V. Medical image security and EPR hiding using Shamir’s secret sharing scheme. J. Syst. Softw. 2011, 84, 341–353. [Google Scholar] [CrossRef]
- Charoghchi, S.; Mashhadi, S. Three (t,n)-secret image sharing schemes based on homogeneous linear recursion. Inf. Sci. 2021, 552, 220–243. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C. Scalable secret image sharing scheme with essential shadows. Signal Process. Image Commun. 2017, 58, 49–55. [Google Scholar] [CrossRef]
- Yan, X.; Li, J.; Pan, Z.; Zhong, X.; Yang, G. Multiparty verification in image secret sharing. Inf. Sci. 2021, 562, 475–490. [Google Scholar] [CrossRef]
- Ding, W.; Liu, K.; Yan, X.; Liu, L. Polynomial-based secret image sharing scheme with fully lossless recovery. Int. J. Digit. Crime Forensics 2018, 10, 120–136. [Google Scholar] [CrossRef]
- Liu, L.; Lu, Y.; Yan, X.; Ding, W.; Xuan, Q. A Lossless Polynomial-Based Secret Image Sharing Scheme Utilizing the Filtering Operation. Adv. Intell. Syst. Comput. 2020, 895, 129–139. [Google Scholar] [CrossRef]
- Chang, C.-C.; Kieu, T.; Chou, Y.-C. Reversible data hiding scheme using two steganographic images. In Proceedings of the TENCON 2007–2007 IEEE Region 10 Conference, Taipei, Taiwan, 30 October–2 November 2007; pp. 1–4. [Google Scholar] [CrossRef]
- Chen, S.; Chang, C.C. Reversible data hiding based on three shadow images using rhombus magic matrix. J. Vis. Commun. Image Represent. 2021, 76, 103064. [Google Scholar] [CrossRef]
- Qin, C.; Chang, C.C.; Hsu, T.J. Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimed. Tools Appl. 2015, 74, 5861–5872. [Google Scholar] [CrossRef]
- Lin, P.Y.; Lee, J.S.; Chang, C.C. Distortion-free secret image sharing mechanism using modulus operator. Pattern Recognit. 2009, 42, 886–895. [Google Scholar] [CrossRef]
- Lin, P.Y.; Chan, C.S. Invertible secret image sharing with steganography. Pattern Recognit. Lett. 2010, 31, 1887–1893. [Google Scholar] [CrossRef]
- Yadav, M.; Singh, R. Essential secret image sharing approach with same size of meaningful shares. Multimed. Tools Appl. 2021. [Google Scholar] [CrossRef]
- Gao, K.; Horng, J.H.; Chang, C.C. A novel (2, 3) reversible secret image sharing based on fractal matrix. IEEE Access 2020, 8, 174325–174341. [Google Scholar] [CrossRef]
- Chang, C.C.; Chen, Y.H.; Wang, H.C. Meaningful secret sharing technique with authentication and remedy abilities. Inf. Sci. 2011, 181, 3073–3084. [Google Scholar] [CrossRef]
- Gao, K.; Horng, J.H.; Chang, C.C. An authenticatable (2, 3) secret sharing scheme using meaningful share images based on hybrid fractal matrix. IEEE Access 2021, 9, 50112–50125. [Google Scholar] [CrossRef]
- Fridrich, J.; Goljan, M.; Du, R. Reliable detection of LSB steganography in color and grayscale images. In Proceedings of the 2001 Workshop on Multimedia and Security: New Challenges, Ottawa, ON, Canada, 5 October 2001; pp. 27–30. [Google Scholar] [CrossRef]
- Cachin, C. An information-theoretic model for steganography. Lect. Notes Comput. Sci. 1998, 1525, 306–318. [Google Scholar] [CrossRef]
- Arabia, S. Pixel-Value Differencing Steganography: Attacks and Improvements. In Proceedings of the ICCIT 2012, Chittagong, Bangladesh, 22–24 December 2012; pp. 757–762. [Google Scholar]
- Joo, J.C.; Lee, H.Y.; Bui, C.N.; Yoo, W.Y.; Lee, H.K. Steganalytic measures for the steganography using pixel-value differencing and modulus function. Lect. Notes Comput. Sci. 2008, 5353 LNCS, 476–485. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).