Abstract
The medical industry has made significant advancements in recent years. However, the lack of accountability in medical management has resulted in systemic deficiencies, which have adversely affected patient trust and contributed to an increase in medical disputes. As a result, there is a growing emphasis on managing the quality of medical services, particularly in enhancing patient experience. To address these challenges, we propose a new system for evaluating health services. This system will allow patients to anonymously rate the services they receive while also providing doctors the opportunity to appeal specific reviews. The hospital handles the evaluations and appeals through the management of the cloud platform. We propose a new scheme to assist the work of the platform, which is a lattice-based group signature with verifier-local revocation (VLR-GS). Most of the work on VLR-GS has focused on the random oracle model (ROM) or using non-interactive zero-knowledge proofs (NIZKs). Our construction is anonymous and traceable in the standard model under the hardness of the learning with errors problem and short integer solution problem. Furthermore, theoretically analyzing it has practical significance in both security and efficiency. In conclusion, the proposed scheme establishes a secure and privacy-oriented platform for an anonymous medical service evaluation system, with the goal of fostering patient trust and improving hospital service quality within the healthcare sector.
1. Introduction
The World Health Organization (WHO) has made the improvement of healthcare quality a global priority, urging countries around the world to take active measures to continuously improve the quality of medical services [1]. Quality is essential to healthcare operations and serves as the fundamental standard for testing and measuring medical service work. In 1986, the United States introduced the concept of “patient-centered”, to provide quality medical services. This approach aims to create an environment that prioritizes the needs of patients and their families as much as possible. In addition, countries such as the United Kingdom, Switzerland, Sweden, and Germany have conducted patient experience surveys. These surveys are valuable tools for government oversight and help guide patient choices in healthcare facilities. Management of medical service quality includes all components that influence healthcare quality, such as planning, organization, coordination, and service assurance. This is critical for effective hospital management and is an important symbol of scientific management. The quality and management of medical services are completed through the evaluation of patients. Management has become an important work that modern hospitals must do to improve and improve the quality of medical services. However, due to the lack of medical management, medical deficiencies have been caused, patient trust has been reduced, and medical disputes have intensified.
To solve these problems and address privacy concerns, this article designs an anonymous medical service evaluation system for patients. The system is built on a cloud platform and emphasizes a “patient-centered” approach. Its design prioritizes safety, fosters a positive service culture, streamlines the service process, enhances the service environment, and maintains cost control. In this system, as Figure 1, patients make appointments on a cloud platform. After describing your condition to the doctor, the doctor returns the diagnosis. Patients who have completed the consultation on the same day will be anonymously evaluated as a group and uploaded to the cloud platform through a secure channel. Doctors can also appeal questionable reviews. The hospital utilizes a cloud platform to manage patient evaluations and gather feedback from doctors, then revokes malicious or erroneous evaluations of medical services. The system ensures the quality of medical services and helps improve the level of medical and health technology.
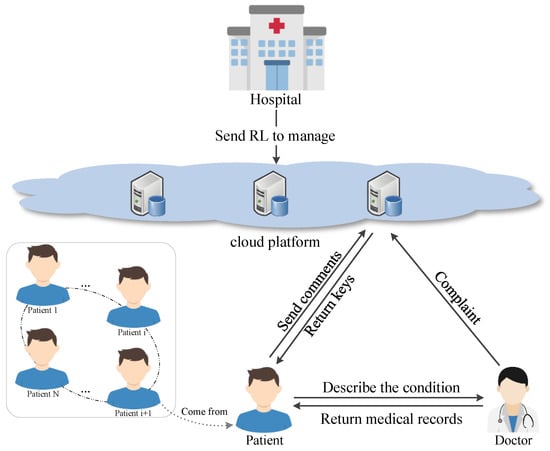
Figure 1.
System model diagram.
Actively use cloud computing technology to optimize the service process, improve the long-term mechanism to resolve medical disputes, and build a harmonious doctor–patient relationship. For this threat, we propose a novel VLR-GS scheme to improve the performance of the system’s cloud platform. Group signature is a type of cryptographic tool that enables group users to sign messages anonymously while ensuring traceability. “Who the signature came from” is secret, but the manager might use some information to find out who, if necessary, thus demonstrating the responsibility of the group members for the signature.
Many group signatures based on number theory assumptions exhibit significant vulnerabilities when confronted with the capabilities of quantum computers. In contrast, lattice-based GS schemes have gradually gained attention because of their immunity to quantum adversaries, high computational efficiency, and provable security. The first such scheme was constructed through the pioneering work of Gordon et al. [2]. The emergence of lattice-based cryptography signifies a compelling alternative to the traditional, which excels in simple algebraic operations and a strong mathematical foundation. It demands exponential time for quantum adversaries to breach, positioning it as a formidable choice for secure communication and data protection, even in the worst case.
In multi-user signature systems, being able to revoke membership is crucial for blocking signatures from members who have misbehaved or voluntarily left the group. For large-scale groups, the VLR mechanism is considered to be more flexible. Figure 2 illustrates the specific flow. It involves maintaining a revocation list (RL) containing tokens for revoked users. The list is regularly updated and only provided to the verifier. According to the list RL, the verifier can test the signature’s legitimacy. If unsuccessful, the verifier rejects the signature.
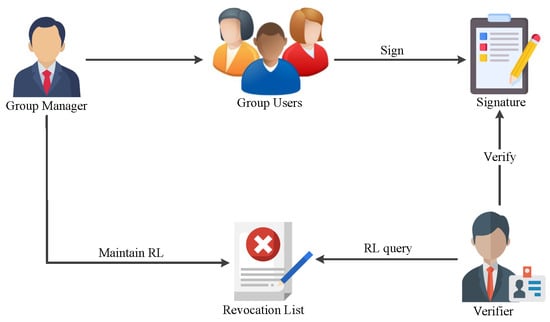
Figure 2.
The VLR mechanism.
1.1. Contribution
Our major contribution is threefold, which are as follows:
- (1)
- The quality management of medical services is the eternal theme of health work. The medical service evaluation system we propose enhances traditional management approaches. Patients can upload their evaluations to the cloud platform after consultation in this system. Hospitals can then use this platform to analyze patient data for improved management. When doctors have questions about reviews, hospitals can utilize the platform to assist.
- (2)
- To assist the platform to work better, we propose a novel scheme, which is a lattice-based VLR-GS. With this scheme, patients become part of a group that includes patients who have completed their care within a specific day and can anonymously evaluate their experiences. As a group manager, the hospital can verify and manage user-generated reviews. If any review is found to be illegitimate or malicious, appropriate actions can be taken. In addition, doctors can file complaints, and, if necessary, the hospital can use the group private key to identify the reviewer.
- (3)
- We instantiate the GS scheme into a concrete construction, using the framework of [3]. This scheme can be proven secure on the SIS and LWE problems, and we demonstrated that the scheme in the standard model (SM) ensures anonymity and unforgeability. And through proper analysis, our scheme performs well in the same type of scheme theoretically. This approach balances security with its efficiency.
1.2. Related Work
The initial security model presented by [4] outlines an anonymous static group signature. Their research demonstrated that trapdoor permutations are sufficient for constructing GS schemes, as these permutations imply NIZKs [5,6,7]. And [5] addresses two open problems related to NIZKs. Furthermore, their results also indicate that group signatures can be constructed from factoring-based assumptions. Moreover, Camenisch and Groth [8] established that one-way function (OWF) and NIZKs imply group signature schemes. Most current works, such as [9,10,11], construct group signature schemes with the help of NIZKs.
Gordon et al. [2] were the first to propose a lattice-based GS in ROM. The scheme was built upon [4] and further integrated zero-knowledge proof and lattice. However, this scheme had large key sizes and signatures. Several works [12,13,14,15,16] have proposed simpler and more efficient solutions. The majority of lattice-based schemes have been developed using two primary methods. The first method involves utilizing one access structure and knowledge argument, as identified in [13,14,17,18]. Despite extensive development, there are still no NIZKs specifically designed for GS in the standard model. The second method involves an ABS scheme with distinct properties utilized to build the GS scheme, as demonstrated in [3]. This method has the advantage of being more suitable for a lattice. The previous post-quantum security GS with a forward security scheme was established by Ling et al. [19] from the lattice in ROM and followed the classical framework, so it was proved using NIZKs. Through the framework of [3], ref. [20] realizes the first lattice FS-GS in SM, and its public key and signature length are linearly related to the number of users. Ref. [21] uses the Bonsai tree and proposes the first lattice-based fully dynamic GS scheme without NIZKs based on [3].
The mechanism of VLR for group signatures, originally formalized by Boneh and Shacham [22], provides signers with the benefit of not constantly updating information about revoked users, making it practical for large user populations. This concept has been further explored and expanded upon by [23,24,25,26,27]. Most existing VLR-GS schemes use bilinear maps and will become vulnerable once quantum computers are developed. The lattice-based VLR-GS was proposed in the work of [28], making it the first scheme to be considered quantum-resistant. Subsequently, many schemes were proposed, such as [18,29,30,31].
1.3. Outline of the Article
In Section 1, we review the related works, and in Section 2, we introduce the relevant notations and definitions. Section 3 presents a new VLR-GS scheme designed for the medical service evaluation system, along with its security proofs. Section 4.1 offers a detailed overview of the lattice-based construction of this scheme, which will serve as the foundation for our comparative analysis in Section 4.2. Finally, in the conclusion, we summarize the main points of the text and suggest potential directions for future research.
2. Preliminaries
Notations. We say that denotes the main security parameter throughout this scheme, while the maximum number of members . If matrix and denotes the concatenation as . Then denotes the euclidean norm , and denotes the infinity norm . Table 1 lists other symbols.

Table 1.
Notations.
2.1. Lattice
This section we introduce some facts on lattices that are needed [32,33].
Definition 1.
For positive integers , a randomly chosen matrix from , a lattice known as the m-dimensional q-ary orthogonal lattice, can be characterized:
For a positive scale parameter s, a vector ∈, and a given point c in the m-dimensional real space , the Gaussian function , the discrete Gaussian distribution, can be rephrased:
2.1.1. Hard Problems
We recall two assumptions of SIS and LWE. Their definition is from the work of [32,34]:
Definition 2 (The SIS Assumption).
Given a modulus q, assume a matrix ∈, which lacks full column rank modulo q. Additionally, a positive real number β is provided. Find the minimum non-zero integer solution to the modular q homogeneous linear equation system, , such that .
Definition 3 (The LWE Assumption).
Here, we define the LWE problem in the following manner. First, randomly select a vector ∈, a random distribution χ over . Let denote a distribution generated by selecting ∈ uniformly at random, then outputting , where .
What can already be confirmed for SIS is that the problems are equally difficult as a certain worst-case problem, which means that with a nonnegligible probability, solving the problem is as challenging as solving the and problems, with high probability in the worst-case situation. Regarding LWE, it follows that there exists an efficient sampleable -bounded distribution such that the problem is as challenging as the problem.
2.1.2. Trapdoor
Hereafter, assume SampZ() is a sampling algorithm designed for discrete Gaussian distribution over , with greater than zero.
Definition 4 (Trapdoor).
Given a matrix . For all , We designate to be the distribution of under the condition that . For any , a γ-trapdoor for is a trapdoor that samples from in polynomial time and denote this trapdoor by .
Here, we require a special gadget matrix , which is constructed by padding with additional zero columns. Many research studies have confirmed the validity of these properties [32,35,36,37,38].
Lemma 1 (Trapdoor Properties).
These properties are demonstrated by lattice trapdoors:
- If is known, can be obtained for any .
- If is known, and can be obtained.
- For and , can be obtained for .
- The statistical closeness of the distributions is shown to hold for any :In the above, and .
2.2. Fully Homomorphic Computation
We also introduce a pair of deterministic algorithms: and .
Lemma 2 (Fully Homomorphic Computation).
The algorithms exist and possess these important facts [39]:
- : The algorithm takes as input a vector and a circuit , then gets a matrix .
- : The algorithm accepts a vector which , a circuit F, and a binary vector , it outputs a matrix . In particular, we have , where .
2.3. One-Time Signatures
This section presents the lattice-based OTS constructions from chameleon hash functions built on preimage samplable (trapdoor) functions. Consider as the chameleon hash functions family and let as a target collision-resistant function and as evaluation keys.
- : Perform the following steps to generate :
- (1)
- Sample two pairs of matrices and , where . Then, define , and the trapdoor is a short basis for the lattice whose parity-check matrix is .
- (2)
- Sample and from a discrete Gaussian over .
- (3)
- Calculate , where and . In this context, represents an arbitrary message in , which may differ among signers.
- (4)
- Output , where and .
- : Upon receiving m, computes the signature . The calculation process is as follows:
- (1)
- Sample such that . Then sample using . We have .
- (2)
- Sample such that . Then sample using . We have and .
- : Given the input , accept if the conditionis satisfied, which is . Otherwise, reject.
It should be emphasized that the OTS scheme satisfies the SUF-CMA security, this concrete proof from [40].
2.4. VLR-GS
The definition in this section is based on Boneh and Shacham [22]. A VLR-GS includes the following algorithms:
- : Input the security parameter n, group size N. Then outputs the manager’s keys .
- : The group manager uses to generate group public key , user’s secret keys and revocation tokens . Note, the manager transmits to user i in confidence.
- : The signing algorithm works with , , and message M. Finally, the user gets their own signature .
- : As given in the , the revocation list (RL) is along with message–signature pairs . Finally, outputs a result ⊤, which means that the signature is valid. Otherwise outputs ⊥.
The VLR-GS scheme is required to meet correctness, anonymity, and traceability.
Correctness: For the above scheme, we need to prove that the correctly generated signature passes the verification algorithm. For all outputted by and , outputted by , pairs , we have
It should be emphasized that this scheme satisfies selfless anonymity and traceability, as shown by this concrete proof from [31].
3. VLR-GS for Medical Service Evaluation System
Focusing on the challenges currently existing schemes face, this article introduces an innovative lattice-based VLR-GS scheme designed to resist quantum attacks for a medical service evaluation system with a cloud platform.
3.1. Definition of the Scheme
Here, we give a generic definition from an OTS in Section 2.3 with strong unforgeability, an OWF scheme with the underlying hard problem, and a secret key encryption scheme and indexed ABS scheme requested in [3]. We need this ABS scheme that can handle the function class , which serves to hardwire to and . See the circuit design in Figure 3.
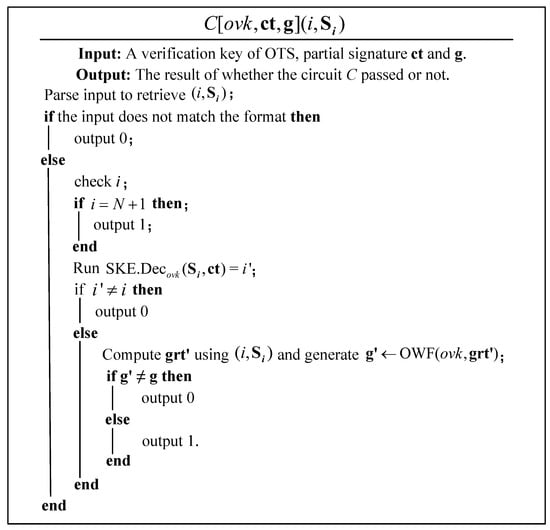
Figure 3.
The design of the circuit.
The general construction of the VLR-GS scheme for the system is as follows:
- : Input the security parameters, run , . Output the public parameters and the group manager’s keys .
- : For group member i, group manager runs:
- 1.
- Compute and .
- 2.
- Generate the revocation token using .
Finally, group manager securely transmits and to user over secure channels. - : Before signing message M, parse and sample . Compute , then generate . Next, sample . Given and run . Finally, the user outputs .
- : Firstly, parse and validate using RL. Then verify whether the given is valid on M using and .
The above ABS scheme is no-signing-query unforgeability, then it can be transformed into a new that ensures co-selective unforgeability, following in [3].
The design of the system mainly focuses on “patient-centered”, and this scheme could significantly enhance the functionality of the evaluation platform. After a consultation, users have the opportunity to rate the doctor and the consultation process anonymously, ensuring their information remains confidential. This reflects the anonymity of the scheme. Hospitals, acting as administrators, can utilize the VLR feature of the solution to revoke access for users who post inappropriate comments. This reflects the revocable feature. Doctors have the ability to challenge questionable reviews, and hospitals can employ traceability to identify the individuals who left these reviews, thereby safeguarding the rights and interests of doctors. This reflects the traceability.
3.2. Security Analysis
The scheme meets the group signature security requirements set forth in [4].
3.2.1. Correctness
For the scheme in Section 3.1, we first need to prove that correctly generated passes . For , and group public key by , we have . We can confirm the correctness of by observing that . Additionally, is supported by , which stems out of the correctness of SKE and OWF.
3.2.2. Anonymity
We demonstrate anonymity through a series of theorems.
Theorem 1.
Suppose offers privacy and unforgeability, ensures IND-CCA security and key robustness, (underlying LWE problem) is hard, and provides strong unforgeability. In that case, the VLR-GS achieves selfless anonymity.
Proof of Theorem 1.
We prove using a series of corresponding games between the challenger and , where is the original game and the value of is chosen by the challenger. Let denote the probability of winning the game in , and as the challenge signature.
- :
- We define as the original game between adversary :
- 1.
- The challenger executes and to acquire for . Then sends to .
- 2.
- If queries about M from member i, response . For corruption queries, return . For revocation queries, return .
- 3.
- sends and , such that they never asked for their secret keys and tokens before.
- 4.
- The challenger selects secret , then returns to .
- 5.
- makes queries as before. But is not allowed to inquire about and for , .
- 6.
- Finally, outputs as its guess.
The probability of wins is . - :
- In this game, after running the , the challenger runs to obtain . Then, all signatures generated by the challenger utilizing . Note .
- :
- In , we alter how the challenge query responses. If queries and , the challenger maintains the same execution style. If , the challenger runs and computes . We define as the pseudorandom sampling algorithm that is related to . Next, it runs . Then, it runs , also . After that, note .
- :
- We incorporate a further refinement to the method by which the challenge query addresses. When querying for , by the challenger is conducted independently of . After that, we have .
- :
- In , we alter how the challenge query responses. If queries and , the challenger maintains the same execution style. If , the challenger runs and computes . Next, runs for . Then, it runs , also . Finally, it returns to . After that, note .
- :
- For , we are redefining the process for addressing the challenge query. Once submits the challenge query for , the generation process of by the challenger is conducted independently of . Note that .
In , this challenge signature is sampled without the value, the probability . Based on these indistinguishable games, we obtain is negligible. This concludes the proof. □
3.2.3. Traceability
Theorem 2.
If ABS is co-selective unforgeable, SKE exhibits robustness, and the underlying LWE problem of OWF is difficult, then this GS has full traceability.
Proof of Theorem 2.
Suppose there is an adversary who successfully makes a forgery , yet this forgery such that and the implicit algorithm may either encounter failures or trace back to a user who is not part of the set . We define each of the above two cases as and , and the events outlined represent collectively exhaustive scenarios about the occurrence of a forgery. So we need to prove the probability of and winning is negligible.
Lemma 3.
If ABS is co-selective unforgeable, note that .
Proof of Lemma 3.
To avoid contradiction, assume that the probability is non-negligible. We subsequently construct a new adversary, referred to as , that can break the co-selective unforgeability in a comparable probability. The following outlines the procedure:
- 1.
- The challenger sends to .
- 2.
- runs and for . Then, transmit , to the challenger.
- 3.
- The challenger calculates and transmits and to .
- 4.
- transfers to and keeps secretly.
- 5.
- makes queries during the game. In this process, has to handle all queries without querying the challenger.
- Signing queries: When queries , runs , then transmits the signature to .
- Corruption queries: The corruption set, referred to as , is defined as an empty set. When queries information about i, adds the index to the set , then outputs .
- 6.
- Finally, outputs a forgery with the corresponding message and .
If and the implicit tracing algorithm fails, makes as forgery; else, aborts.
We note that as long as happens, will win. We note that made no signing queries, so wins with negligible probability. □
Lemma 4.
If ABS is co-selective unforgeable, SKE exhibits key robustness, and the problem underlying OWF is hard, note that .
Proof of Lemma 4.
To avoid contradiction, assume that the probability is non-negligible. We construct a new adversary, called , that can break ABS with non-negligible probability. The following outlines the procedure for :
- 1.
- The challenger sends to .
- 2.
- chooses its guess , runs and for . Then, it generates the revocation token using and transmits , and to the challenger.
- 3.
- The challenger calculates and transmits and to .
- 4.
- transfers to and keeps secretly.
- 5.
- conducts two queries during the game. In this process, has to handle all queries without querying the challenger. The difference is that if , runs . Then, it calculates and using . Later, queries for to the challenger, who transmits to . After that, computes . Finally, returns to .
- 6.
- Finally, output a forgery with the corresponding message and .
It aborts if or ; else, gets . If also either of or does hold, then aborts.
As long as happens, will win. Firstly, note that can pass by the result of is ⊤. And has made no prohibited key query, that is to say, causes and the LWE problem behind OWF. Then, never takes prohibited signing queries. Remember that has exclusively performed signing queries for . Once wins, we have . This concludes the proof. □
We demonstrate that cases and are collectively exhaustive for a successful forgery with negligible probability, which means that the above scheme is traceable. □
4. Lattice-Based VLR-GS Construction in the Standard Model
As demonstrated in this section, we introduce a new lattice-based VLR-GS construction in SM without NIZKs. We represent each user’s identity in binary as a string, denoted as . Based on n, we will fix other parameters as outlined below:
- is required to be large enough so that .
- Dimension and from trapdoor properties.
- so that can be extended to by Lemma 1, and .
- is hard and .
- and -bounded distribution makes hard to solve.
4.1. Construction of the Scheme
To illustrate easily, we omit the subscript of the message space collection and just write . The construction of the scheme is specified as follows:
- : Take and N as the inputs, then get public parameters . The algorithm proceeds as follows:
- Pick a random vector and run such that .
- Sample randomly matrices for and , then define the matrix .
Finally, the algorithm outputs , and . - : For group user , the group manager performs the following to generate group member’s token and signing key :
- Sample and and define .
- Compute , where .
- Compute and define . Note that .
Finally, it sends to user i over secure channels. - : Given , message , a group member’s signing key and revocation token , the signer runs this algorithm:
- Generate and , where and for . Sample and . Compute and . Finally, define and .
- Sample and . Next, compute and . Thus it outputs .
- Compute , where . Note that with overwhelming probability and output .
- Output 0 if , , and . Otherwise, compute and such that . It then computes and further computes from . Finally it outputs and .
- Given , signature and message , then compute , where and .
Finally, it outputs . - : Given , message , the signature , and a set of tokens in RL that are to be revoked, the verifier performs the steps below. First, parse , and there are three Conditions needed to check:
- Condition 1:For each token in , compute . If there exists i such that , returns 0; else, checks Condition 2.
- Condition 2:It outputs 0 if , , or . Otherwise, it first computes , then checks whether and . If one of the two is not satisfied, then output 0; else, check Condition 3.
- Condition 3:Given the public key and , . It checks whether . If they hold, output 1.
If and only if all of these conditions are met, the verification algorithm outputs 1 (accept); in contrast, when any of them are unsatisfied, it outputs 0 (reject).
4.2. Comparisons and Analysis
Here, we compare the above scheme in detail with earlier lattice-based GS schemes as presented in Table 2. In our scheme, the bit size of is . And has of bit size . The signature is .

Table 2.
Comparison of existing lattice-based GS schemes.
After the above theoretical comparison in Table 2, we make a more detailed comparison of lattice-based group signature schemes in SM, and these three schemes utilize ABS instead of NIZKs. Because of the same group signature construction, the gap between the efficiency of the three is very small. That’s why we focus on the communication cost. We set the parameters as follows: = 8, , according to [3]. And then we consider the theoretical sizes of these schemes when the group number is .
The three articles are based on the framework of [3] in Table 3. Ref. [20] proposes a lattice-based GS with forward security, which has a larger secret key size than the proposed one. Ref. [21] uses the Bonsai tree structure to propose a new GS scheme with a larger and . We construct this scheme shown in Section 4. The size of is similar to [21], and the other two are significantly smaller than [20,21]. In Figure 4, the performance of our scheme is more clearly represented by a line chart.

Table 3.
Comparison of three schemes in SM in terms of , and .
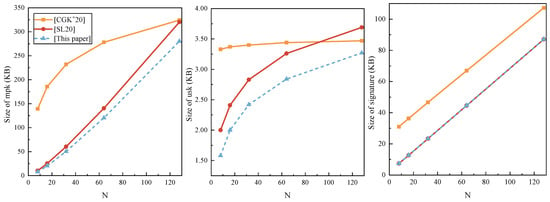
Figure 4.
Comparison of schemes in SM.
5. Conclusions
The medical service evaluation system we propose enhances traditional management approaches. To help the cloud platform work better, we propose a new scheme, which is a lattice-based VLR-GS. With this scheme, patients as part of a group can anonymously evaluate their experiences. The hospital can verify and manage the reviews uploaded by users. If any review is found to be illegitimate or malicious, appropriate actions can be taken. In addition, doctors can complain, and if necessary, the hospital can identify the reviewer. We instantiate the GS scheme for this system into a concrete construction. This scheme is proven secure under SIS and LWE problems, and we demonstrate that the scheme ensures anonymity and unforgeability. Such a scheme in SM is designed to take into account the balance between efficiency and security. And our scheme performs well in the same type of scheme. In the future, we need to find ways to enhance efficiency without compromising security.
Author Contributions
Conceptualization, W.G. and S.R.; methodology, W.G. and S.R.; software, Z.L. and B.Q.; validation, B.Q., X.D. and Z.Z.; formal analysis, W.G.; investigation, Z.L.; resources, W.G. and B.Q.; writing—original draft preparation, W.G., S.R. and Z.L.; writing—review and editing, W.G. and S.R.; visualization, X.D.; supervision, Z.Z.; project administration, B.Q. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Natural Science Foundation of China under Grant (Nos.62002288, 62372370, 62102299); the Key Research and Development Program of Shaanxi (No.2023-YBGY-015); the Henan Key Laboratory of Network Cryptography Technology under No.LNCT2022-A05; and the Youth Innovation Team of Shaanxi Universities (No.23JP160).
Data Availability Statement
The original contributions presented are included in the article; further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- World Health Organization. Quality of Care: A Process for Making Strategic Choices in Health Systems; World Health Organization: Geneva, Switzerland, 2006. [Google Scholar]
- Gordon, S.D.; Katz, J.; Vaikuntanathan, V. A group signature scheme from lattice assumptions. In Proceedings of the Advances in Cryptology-ASIACRYPT 2010: 16th International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 5–9 December 2010; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2010; pp. 395–412. [Google Scholar]
- Katsumata, S.; Yamada, S. Group signatures without NIZK: From lattices in the standard model. In Proceedings of the Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; Proceedings, Part III 38. Springer: Berlin/Heidelberg, Germany, 2019; pp. 312–344. [Google Scholar]
- Bellare, M.; Micciancio, D.; Warinschi, B. Foundations of group signatures: Formal definitions, simplified requirements, and a construction based on general assumptions. In Proceedings of the Advances in Cryptology—EUROCRYPT 2003: International Conference on the Theory and Applications of Cryptographic Techniques, Warsaw, Poland, 4–8 May 2003; Proceedings 22. Springer: Berlin/Heidelberg, Germany, 2003; pp. 614–629. [Google Scholar]
- Feige, U.; Lapidot, D.; Shamir, A. Multiple non-interactive zero knowledge proofs based on a single random string. In Proceedings of the Proceedings [1990] 31st Annual Symposium on Foundations of Computer Science, St. Louis, MO, USA, 22–24 October 1990; IEEE: Piscataway, NJ, USA, 1990; pp. 308–317. [Google Scholar]
- Bellare, M.; Yung, M. Certifying cryptographic tools: The case of trapdoor permutations. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 1992; Springer: Berlin/Heidelberg, Germany, 1992; pp. 442–460. [Google Scholar]
- Goldreich, O. Foundations of Cryptography: Volume 2, Basic Applications; Cambridge University Press: Cambridge, UK, 2001; Volume 2. [Google Scholar]
- Camenisch, J.; Groth, J. Group signatures: Better efficiency and new theoretical aspects. In Proceedings of the International Conference on Security in Communication Networks, Amalfi, Italy, 8–10 September 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 120–133. [Google Scholar]
- Rompel, J. One-way functions are necessary and sufficient for secure signatures. In Proceedings of the Twenty-Second Annual ACM symposium on Theory of Computing, Baltimore, MA, USA, 13–17 May 1990; pp. 387–394. [Google Scholar]
- Naor, M. Bit commitment using pseudorandomness. J. Cryptol. 1991, 4, 151–158. [Google Scholar] [CrossRef]
- Pass, R.; Shelat, A.; Vaikuntanathan, V. Construction of a non-malleable encryption scheme from any semantically secure one. In Proceedings of the Advances in Cryptology-CRYPTO 2006: 26th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2006; Proceedings 26. Springer: Berlin/Heidelberg, Germany, 2006; pp. 271–289. [Google Scholar]
- Camenisch, J.; Neven, G.; Rückert, M. Fully anonymous attribute tokens from lattices. In Proceedings of the Security and Cryptography for Networks: 8th International Conference, SCN 2012, Amalfi, Italy, 5–7 September 2012; Proceedings 8. Springer: Berlin/Heidelberg, Germany, 2012; pp. 57–75. [Google Scholar]
- Libert, B.; Ling, S.; Nguyen, K.; Wang, H. Zero-knowledge arguments for lattice-based accumulators: Logarithmic-size ring signatures and group signatures without trapdoors. In Proceedings of the Advances in Cryptology–EUROCRYPT 2016: 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Proceedings, Part II 35. Springer: Berlin/Heidelberg, Germany, 2016; pp. 1–31. [Google Scholar]
- Rafaël, D.P.; Lyubashevsky, V.; Seiler, G. Lattice-based group signatures and zero-knowledge proofs of automorphism stability. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 574–591. [Google Scholar]
- Laguillaumie, F.; Langlois, A.; Libert, B.; Stehlé, D. Lattice-based group signatures with logarithmic signature size. In Proceedings of the Advances in Cryptology-ASIACRYPT 2013: 19th International Conference on the Theory and Application of Cryptology and Information Security, Bengaluru, India, 1–5 December 2013; Proceedings, Part II 19. Springer: Berlin/Heidelberg, Germany, 2013; pp. 41–61. [Google Scholar]
- Nguyen, P.Q.; Zhang, J.; Zhang, Z. Simpler efficient group signatures from lattices. In Proceedings of the IACR International Workshop on Public Key Cryptography, Gaithersburg, MD, USA, 30 March–1 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 401–426. [Google Scholar]
- Zhang, Y.; Hu, Y.; Zhang, Q.; Jia, H. On new zero-knowledge proofs for lattice-based group signatures with verifier-local revocation. In Proceedings of the International Conference on Information Security, New York, NY, USA, 16–18 September 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 190–208. [Google Scholar]
- Zhang, Y.; Liu, X.; Hu, Y.; Gan, Y.; Jia, H. Verifier-local revocation group signatures with backward unlinkability from lattices. Front. Inf. Technol. Electron. Eng. 2022, 23, 876–892. [Google Scholar] [CrossRef]
- Ling, S.; Nguyen, K.; Wang, H.; Xu, Y. Forward-secure group signatures from lattices. In Proceedings of the Post-Quantum Cryptography: 10th International Conference, PQCrypto 2019, Chongqing, China, 8–10 May 2019; Revised Selected Papers 10. Springer: Berlin/Heidelberg, Germany, 2019; pp. 44–64. [Google Scholar]
- Canard, S.; Georgescu, A.; Kaim, G.; Roux-Langlois, A.; Traoré, J. Constant-size lattice-based group signature with forward security in the standard model. In Proceedings of the Provable and Practical Security: 14th International Conference, ProvSec 2020, Singapore, 29 November–1 December 2020; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2020; pp. 24–44. [Google Scholar]
- Sun, Y.; Liu, Y. A lattice-based fully dynamic group signature scheme without nizk. In Proceedings of the International Conference on Information Security and Cryptology, Ankara, Turkey, 3–4 December 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 359–367. [Google Scholar]
- Boneh, D.; Shacham, H. Group signatures with verifier-local revocation. In Proceedings of the 11th ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 168–177. [Google Scholar]
- Nakanishi, T.; Funabiki, N. Verifier-local revocation group signature schemes with backward unlinkability from bilinear maps. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Springer: Berlin/Heidelberg, Germany, 2005; pp. 533–548. [Google Scholar]
- Nakanishi, T.; Funabiki, N. A short verifier-local revocation group signature scheme with backward unlinkability. In Proceedings of the Advances in Information and Computer Security: First International Workshop on Security, IWSEC 2006, Kyoto, Japan, 23–24 October 2006; Proceedings 1. Springer: Berlin/Heidelberg, Germany, 2006; pp. 17–32. [Google Scholar]
- Libert, B.; Vergnaud, D. Group signatures with verifier-local revocation and backward unlinkability in the standard model. In Proceedings of the Cryptology and Network Security: 8th International Conference, CANS 2009, Kanazawa, Japan, 12–14 December 2009; Proceedings 8. Springer: Berlin/Heidelberg, Germany, 2009; pp. 498–517. [Google Scholar]
- Bichsel, P.; Camenisch, J.; Neven, G.; Smart, N.P.; Warinschi, B. Get shorty via group signatures without encryption. In Proceedings of the Security and Cryptography for Networks: 7th International Conference, SCN 2010, Amalfi, Italy, 13–15 September 2010; Proceedings 7. Springer: Berlin/Heidelberg, Germany, 2010; pp. 381–398. [Google Scholar]
- Perera, M.N.S.; Koshiba, T. Almost fully secured lattice-based group signatures with verifier-local revocation. Cryptography 2020, 4, 33. [Google Scholar] [CrossRef]
- Langlois, A.; Ling, S.; Nguyen, K.; Wang, H. Lattice-based group signature scheme with verifier-local revocation. In Proceedings of the International Workshop on Public Key Cryptography, Buenos Aires, Argentina, 26–28 March 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 345–361. [Google Scholar]
- Zhang, Y.; Hu, Y.; Gao, W.; Jiang, M. Simpler efficient group signature scheme with verifier-local revocation from lattices. KSII Trans. Internet Inf. Syst. (TIIS) 2016, 10, 414–430. [Google Scholar]
- Gao, W.; Hu, Y.; Zhang, Y.; Wang, B. Lattice-based group signature with verifier-local revocation. J. Shanghai Jiaotong Univ. (Sci.) 2017, 22, 313–321. [Google Scholar] [CrossRef]
- Ling, S.; Nguyen, K.; Roux-Langlois, A.; Wang, H. A lattice-based group signature scheme with verifier-local revocation. Theor. Comput. Sci. 2018, 730, 1–20. [Google Scholar] [CrossRef]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, British Columbia, 17–20 May 2008; pp. 197–206. [Google Scholar]
- Micciancio, D.; Regev, O. Lattice-based cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 147–191. [Google Scholar]
- Micciancio, D.; Regev, O. Worst-case to average-case reductions based on Gaussian measures. SIAM J. Comput. 2007, 37, 267–302. [Google Scholar] [CrossRef]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient lattice (H) IBE in the standard model. In Proceedings of the Advances in Cryptology–EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Proceedings 29. Springer: Berlin/Heidelberg, Germany, 2010; pp. 553–572. [Google Scholar]
- Cash, D.; Hofheinz, D.; Kiltz, E.; Peikert, C. Bonsai trees, or how to delegate a lattice basis. J. Cryptol. 2012, 25, 601–639. [Google Scholar] [CrossRef]
- Micciancio, D.; Peikert, C. Trapdoors for lattices: Simpler, tighter, faster, smaller. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 700–718. [Google Scholar]
- Brakerski, Z.; Langlois, A.; Peikert, C.; Regev, O.; Stehlé, D. Classical hardness of learning with errors. In Proceedings of the Forty-Fifth Annual ACM Symposium on Theory of Computing, Palo Alto, CA, USA, 1–4 June 2013; pp. 575–584. [Google Scholar]
- Gorbunov, S.; Vinayagamurthy, D. Riding on asymmetry: Efficient ABE for branching programs. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 550–574. [Google Scholar]
- Mohassel, P. One-time signatures and chameleon hash functions. In Proceedings of the Selected Areas in Cryptography: 17th International Workshop, SAC 2010, Waterloo, ON, Canada, 12–13 August 2010; Revised Selected Papers 17. Springer: Berlin/Heidelberg, Germany, 2011; pp. 302–319. [Google Scholar]
- Ling, S.; Nguyen, K.; Stehlé, D.; Wang, H. Improved zero-knowledge proofs of knowledge for the ISIS problem, and applications. In Proceedings of the International Workshop on Public Key Cryptography, Nara, Japan, 26 February–1 March 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 107–124. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).